LitCTF2023
[LitCTF 2023]梦想是红色的 (初级)
题目描述:
1 | 曾经我有个梦想。 |
下载附件
1 | 自由友善公正公正敬业法治自由自由和谐平等自由自由公正法治诚信民主诚信自由自由诚信民主爱国友善平等诚信富强友善爱国自由诚信民主敬业爱国诚信民主友善爱国平等爱国爱国敬业敬业友善爱国公正敬业爱国敬业和谐文明诚信文明友善爱国自由诚信民主爱国爱国诚信和谐友善爱国自由友善平等爱国友善平等友善自由诚信自由平等爱国爱国敬业敬业友善爱国敬业敬业友善自由友善平等诚信自由法治诚信和谐 |
社会核心价值观解密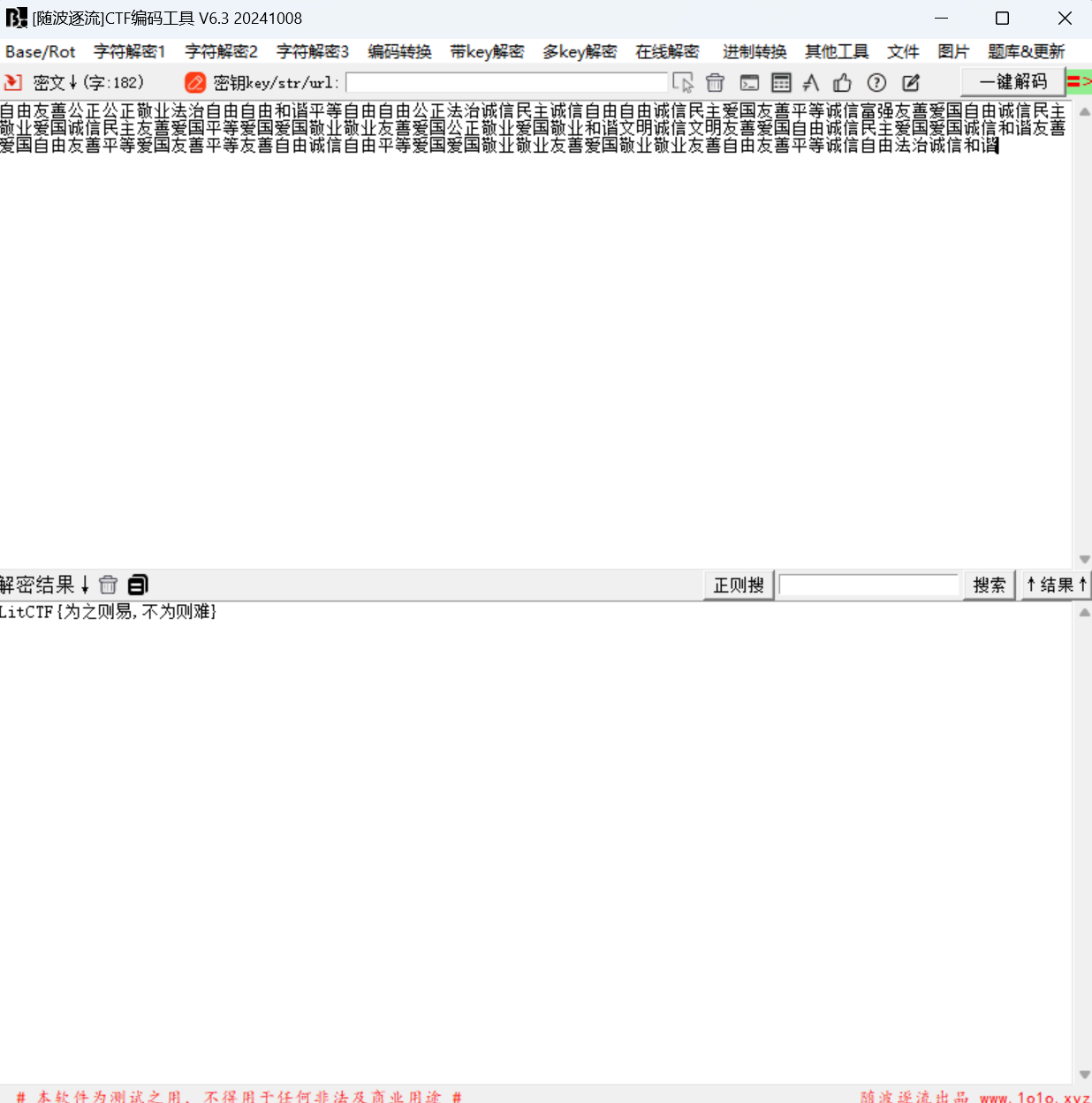
最后flag为
1 | LitCTF{为之则易,不为则难} |
[LitCTF 2023]Hex?Hex!(初级)
题目描述:
1 | 如果你也和我一样知道hex的话,那我觉得,这件事,太酷啦! |
下载附件
1 | 4c69744354467b746169313131636f6f6c6c616161217d |
hex解密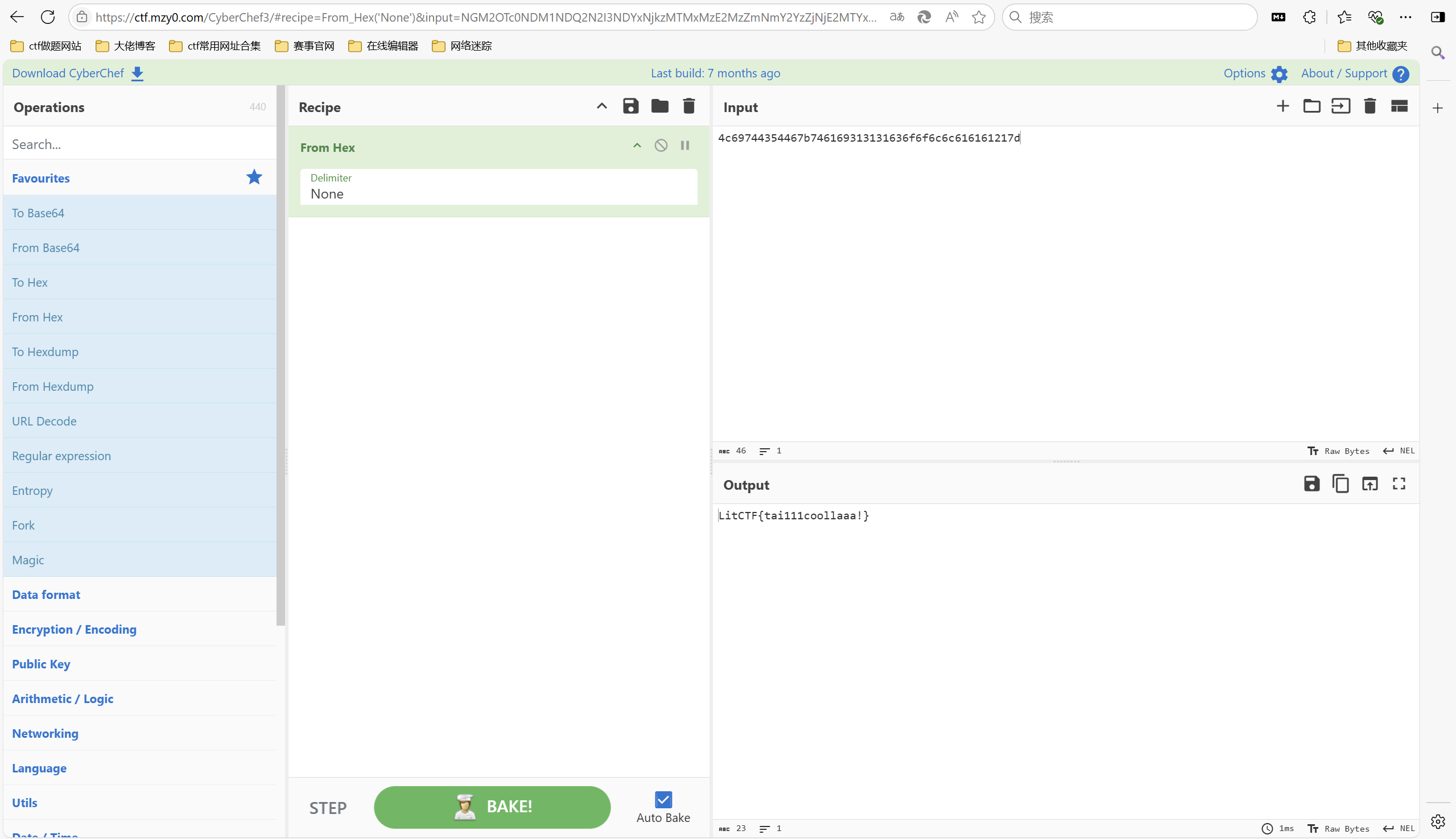
最后flag为
1 | LitCTF{tai111coollaaa!} |
[LitCTF 2023]家人们!谁懂啊,RSA签到都不会 (初级)
题目描述:
1 | 最最最最最基础的RSA! |
下载附件
1 | from Crypto.Util.number import * |
已知p,q,c,e类型的rsa题
直接套板子
exp:
1 | import gmpy2 |
运行得到flag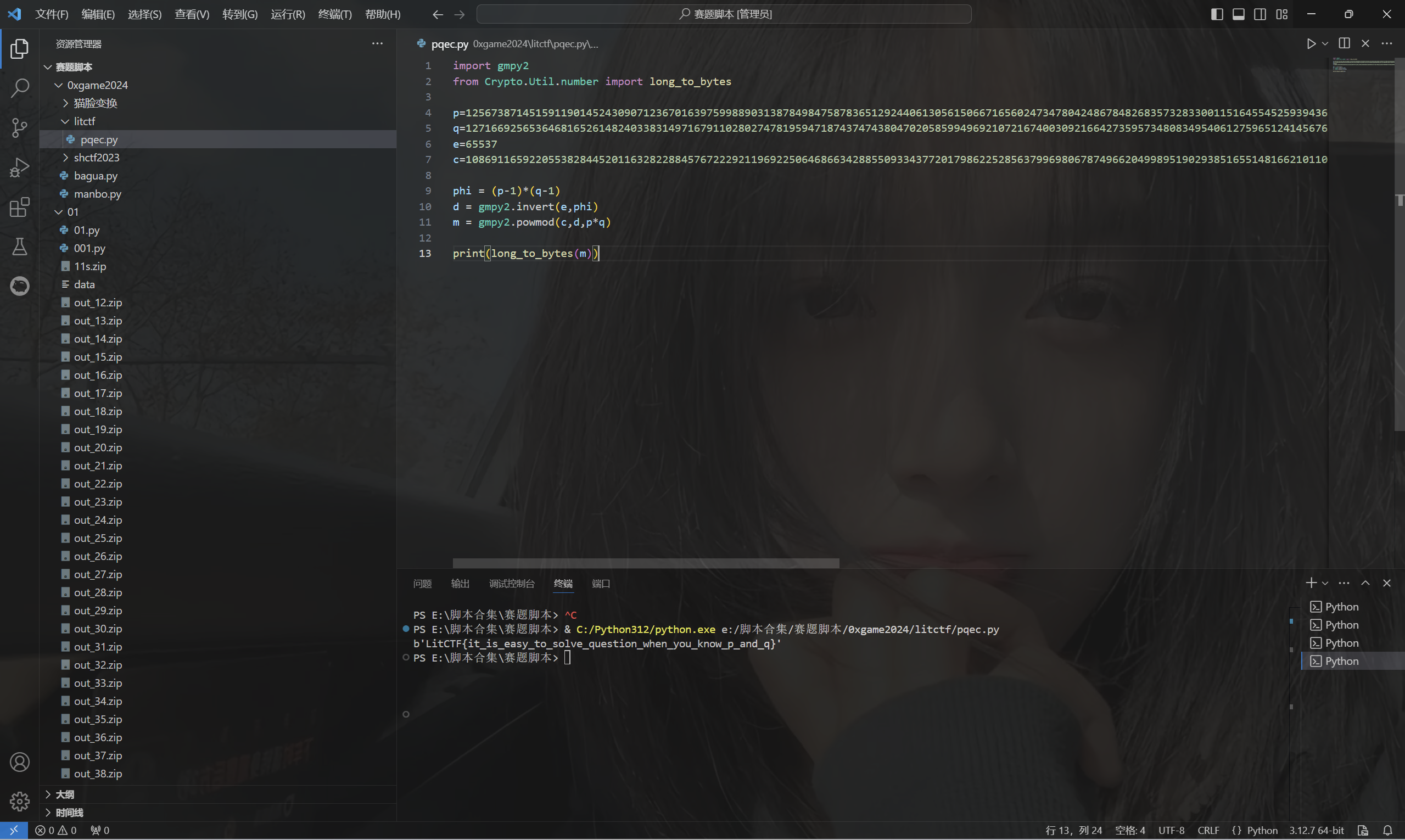
最后flag为
1 | LitCTF{it_is_easy_to_solve_question_when_you_know_p_and_q} |
[LitCTF 2023]你是我的关键词(Keyworld) (初级)
题目描述:
1 | YOU are my keyworld |
下载附件
1 | IFRURC{X0S_YP3_JX_HBXV0PA} |
题目描述发现YOU全是大写,作为密钥,关键词解密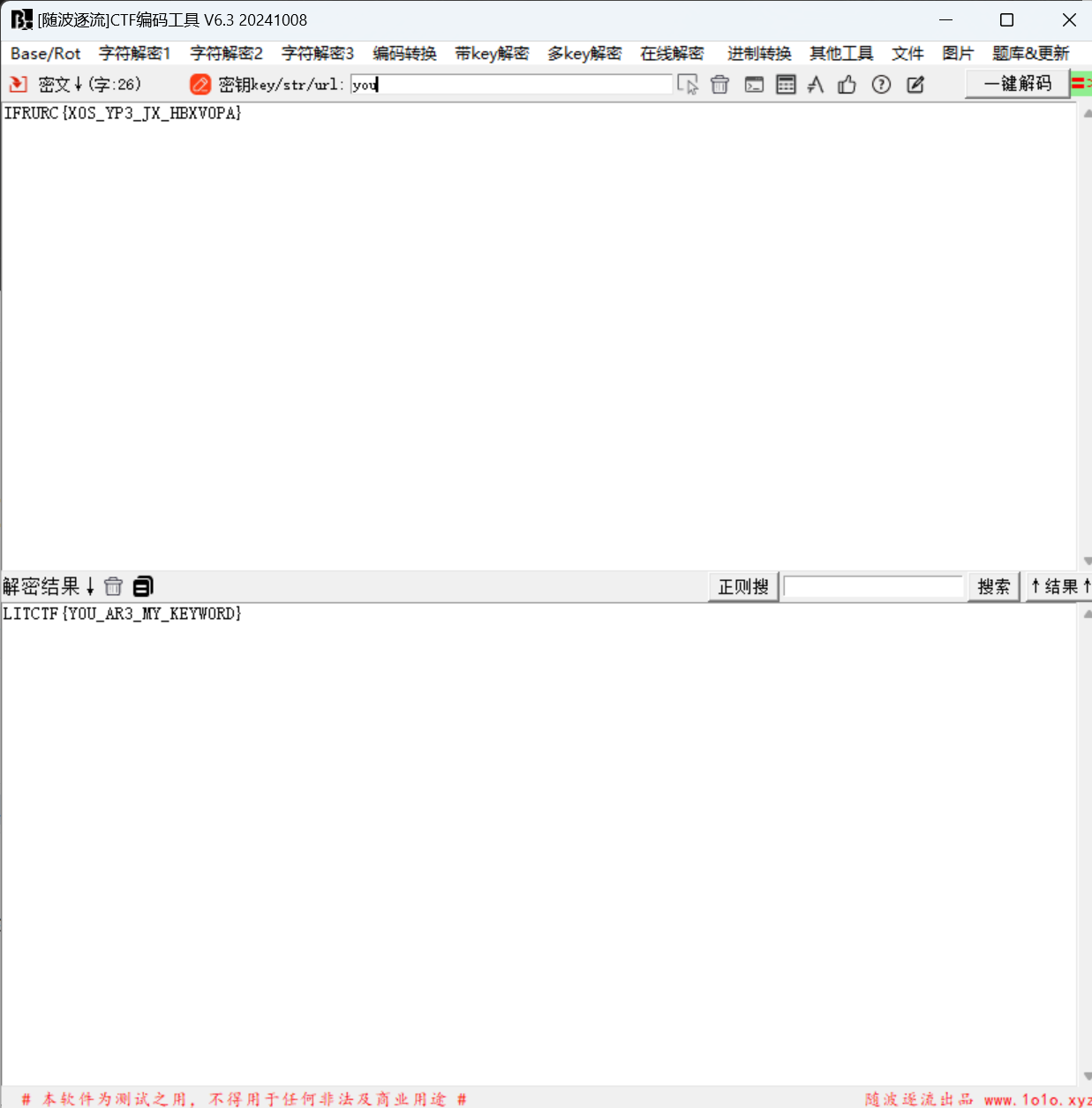
最后flag为
1 | LitCTF{Y0U_AR3_MY_KEYW0RD} |
[LitCTF 2023]Is this only base?
下载附件
1 | SWZxWl=F=DQef0hlEiSUIVh9ESCcMFS9NF2NXFzM |
W型栅栏 key=23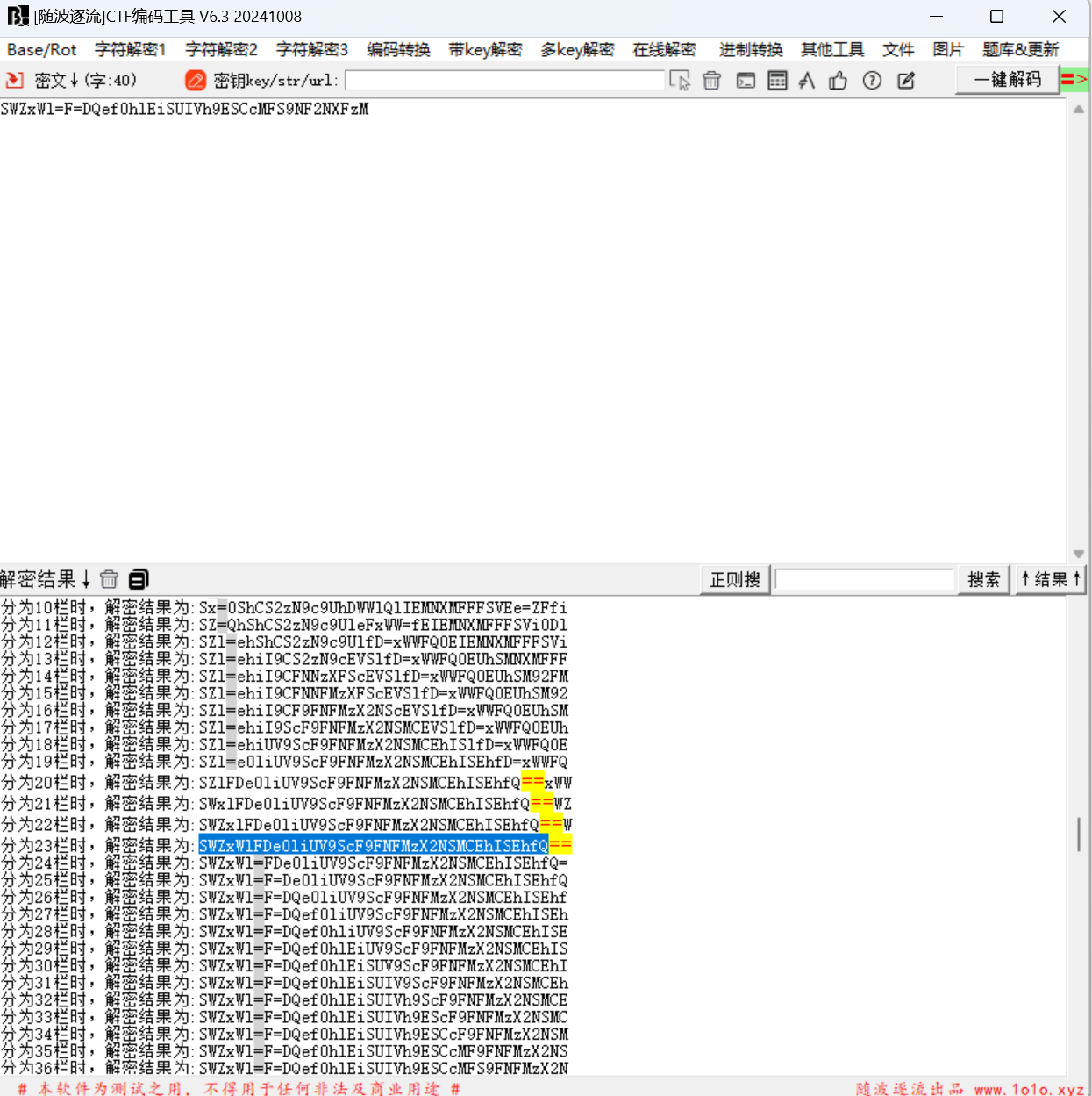
base64解密+rot3解密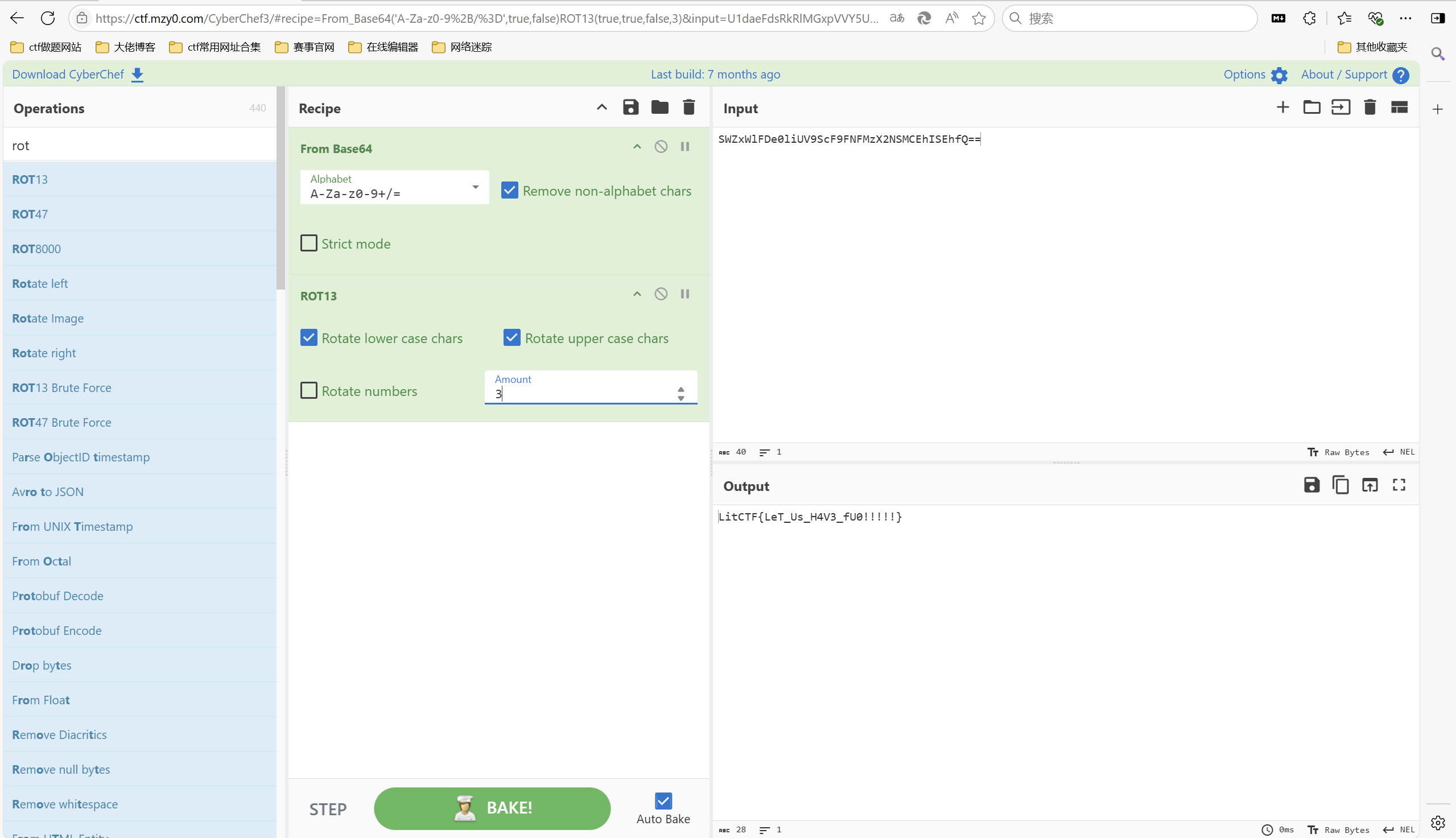
最后flag为
1 | LitCTF{LeT_Us_H4V3_fU0!!!!!} |
[LitCTF 2023]原来你也玩原神 (初级)
题目描述:
1 | 旅行者收到了一封奇怪的来信,是提瓦特大陆的语言! |
下载附件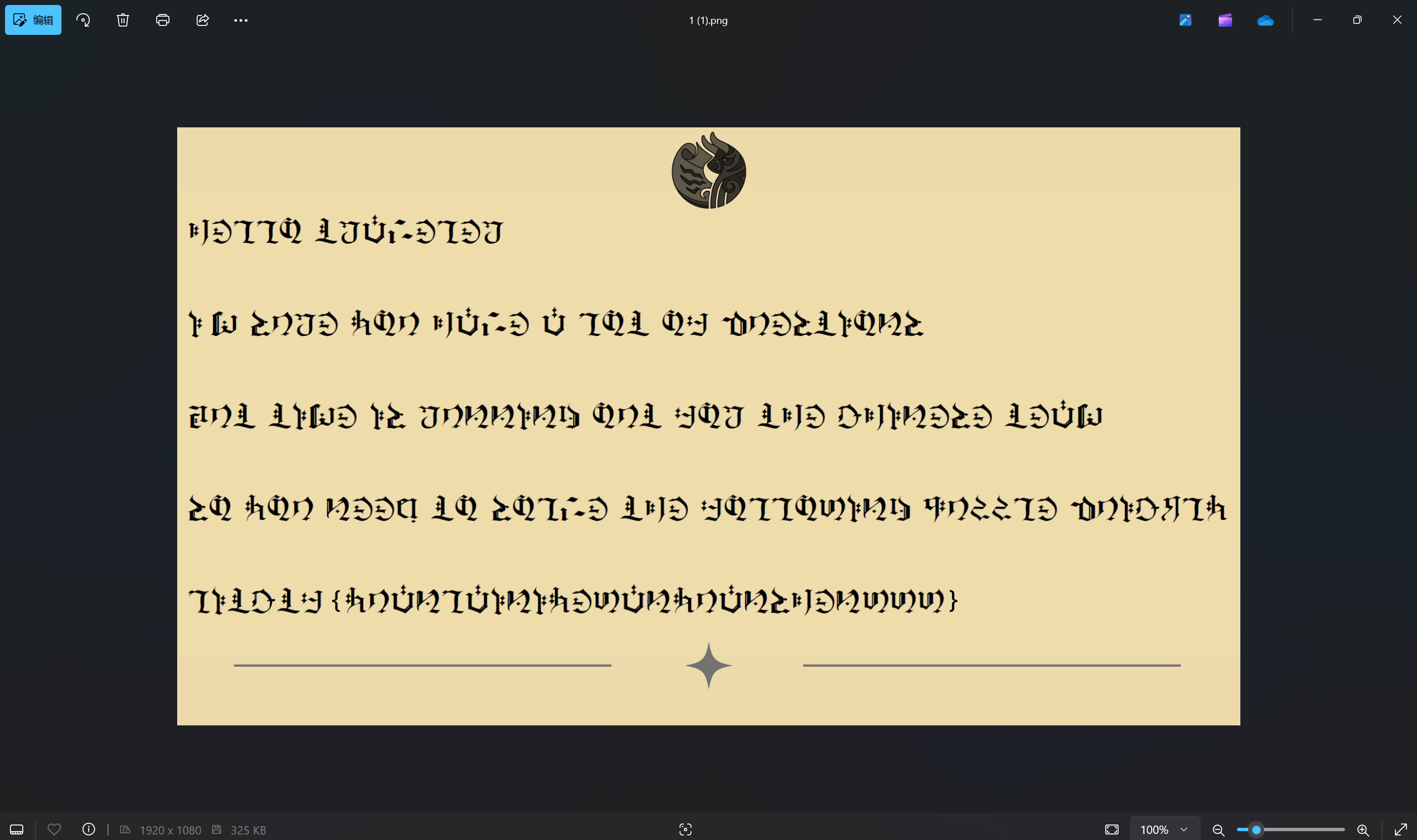
搜索原神文字对照表
v
对照最后得到flag为
1 | LitCTF{YUANLAINIYEWANYUANSHENWWW} |
[LitCTF 2023]md5的破解
下载附件
1 | from Crypto.Util.number import * |
md5爆破
exp:
1 |
|
运行得到flag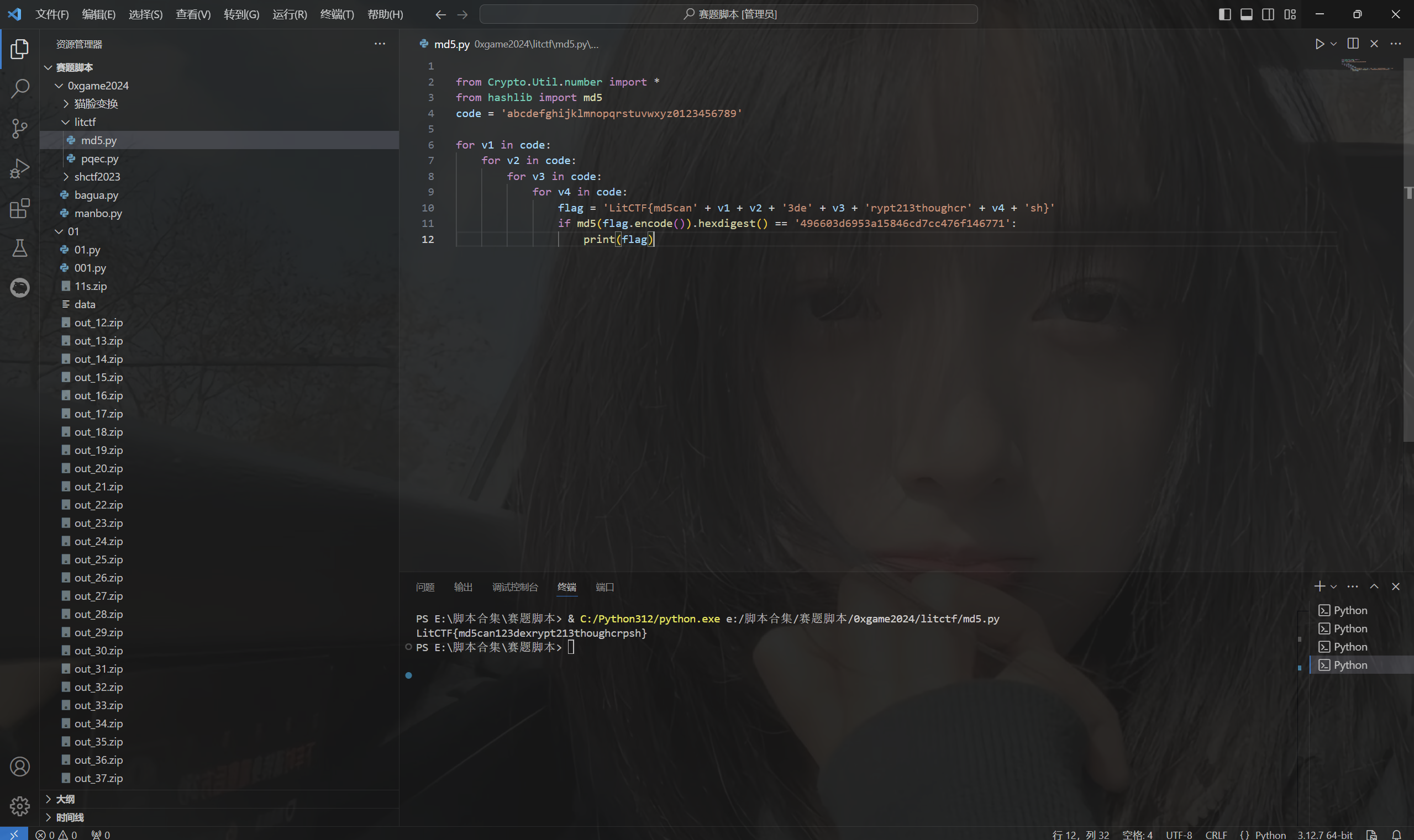
最后flag为
1 | LitCTF{md5can123dexrypt213thoughcrpsh} |
[LitCTF 2023]yafu (中级)
题目描述:
1 | 你知道yafu分解吗? |
下载附件
1 | from Crypto.Util.number import * |
yafu分解
1 | yafu-x64.exe factor(15241208217768849887180010139590210767831431018204645415681695749294131435566140166245881287131522331092026252879324931622292179726764214435307) |
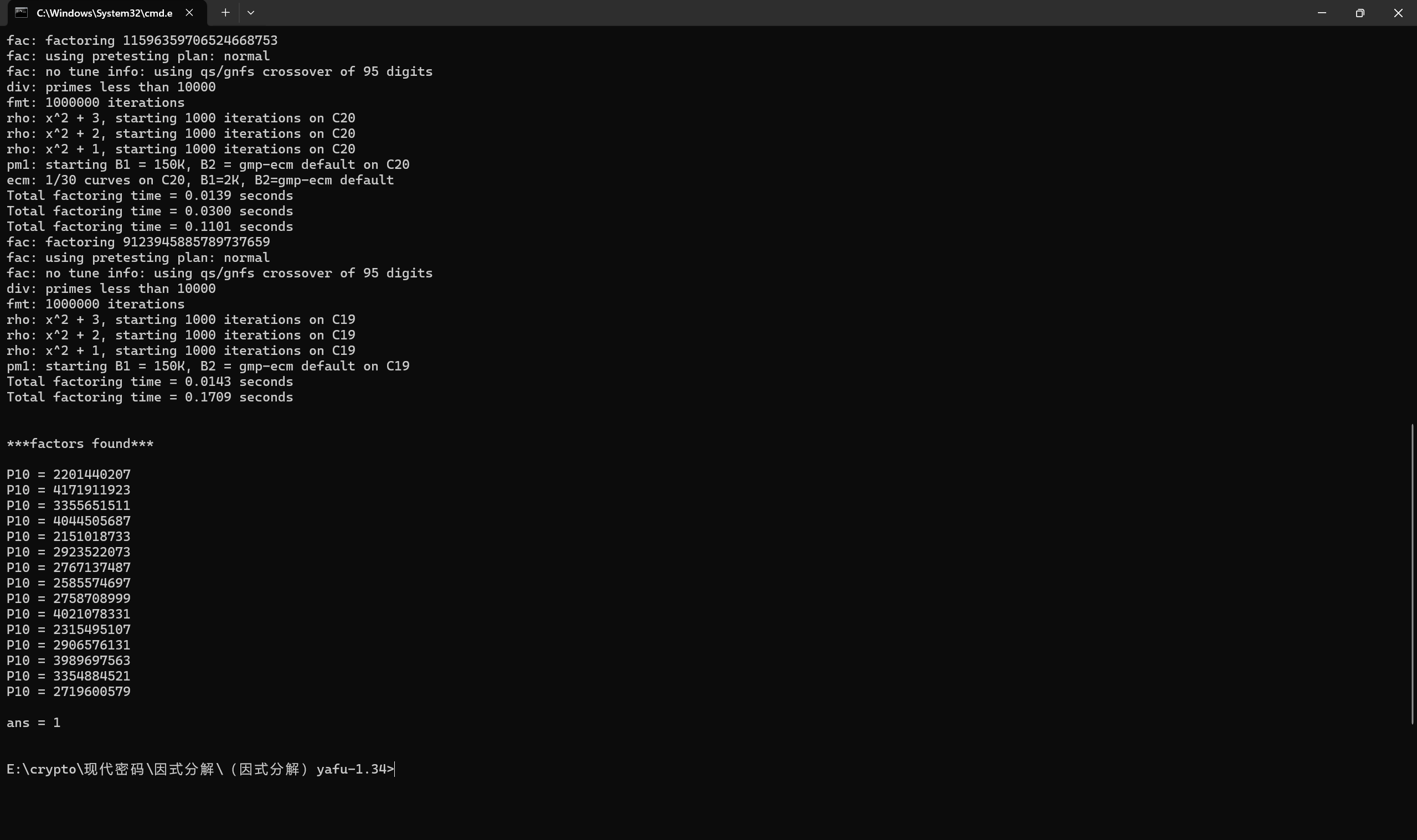
这么多p,一眼欧拉函数解题
exp:
1 | import gmpy2 |
运行得到flag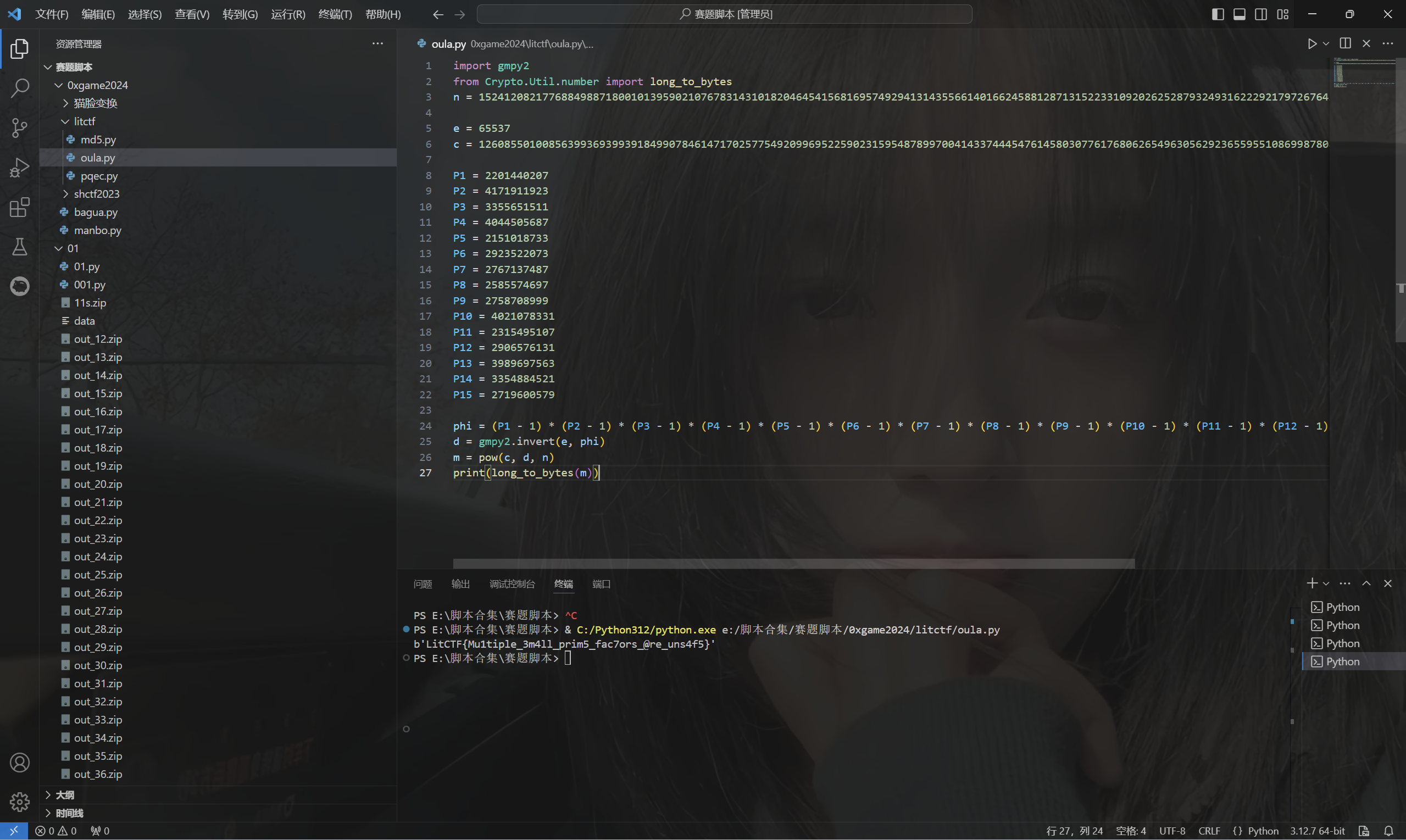
最后flag为
1 | LitCTF{Mu1tiple_3m4ll_prim5_fac7ors_@re_uns4f5} |
[LitCTF 2023]factordb (中级)
题目描述:
1 | 能分解n不仅仅只有yafu哦,还有factordb!!!! |
下载附件
1 | e = 65537 |
factordb分解n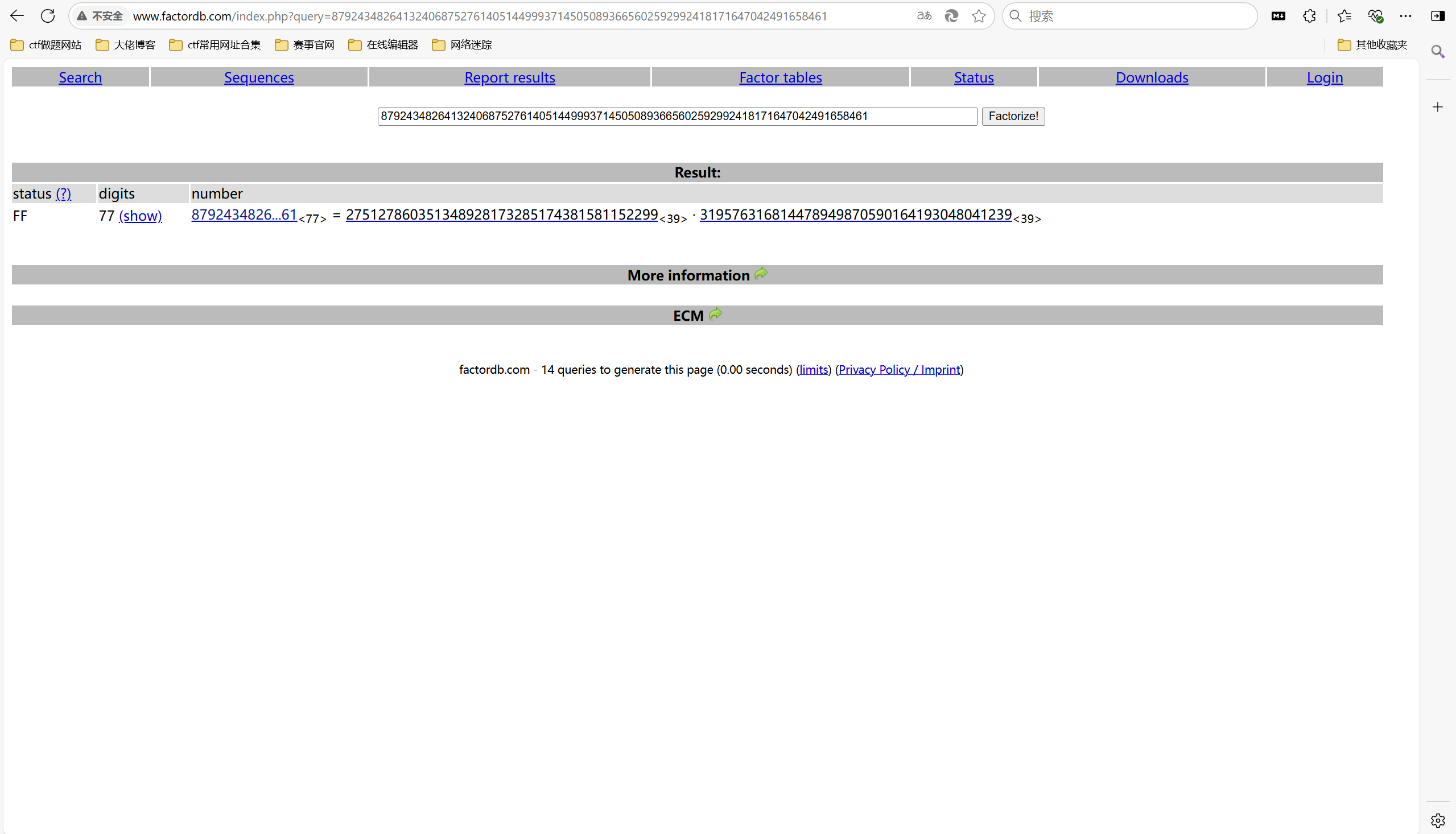
常规rsa,套板子
exp:
1 | import gmpy2 |
运行得到flag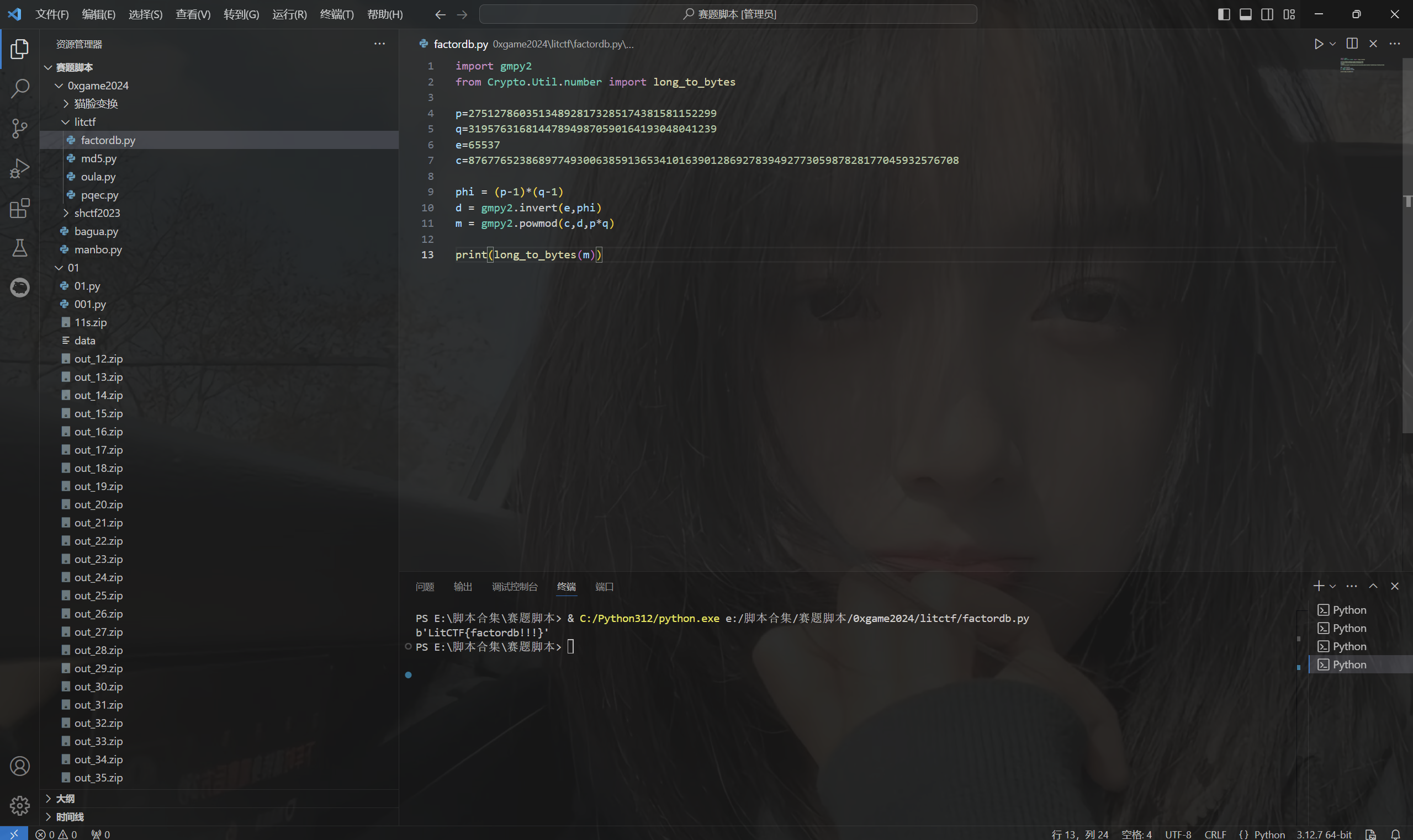
最后flag为
1 | LitCTF{factordb!!!} |
[LitCTF 2023]P_Leak
题目描述:
1 | 很简单的泄露!!! |
下载附件
1 | from Crypto.Util.number import * |
dp泄露,直接套板子
exp:
1 | import gmpy2 |
运行得到flag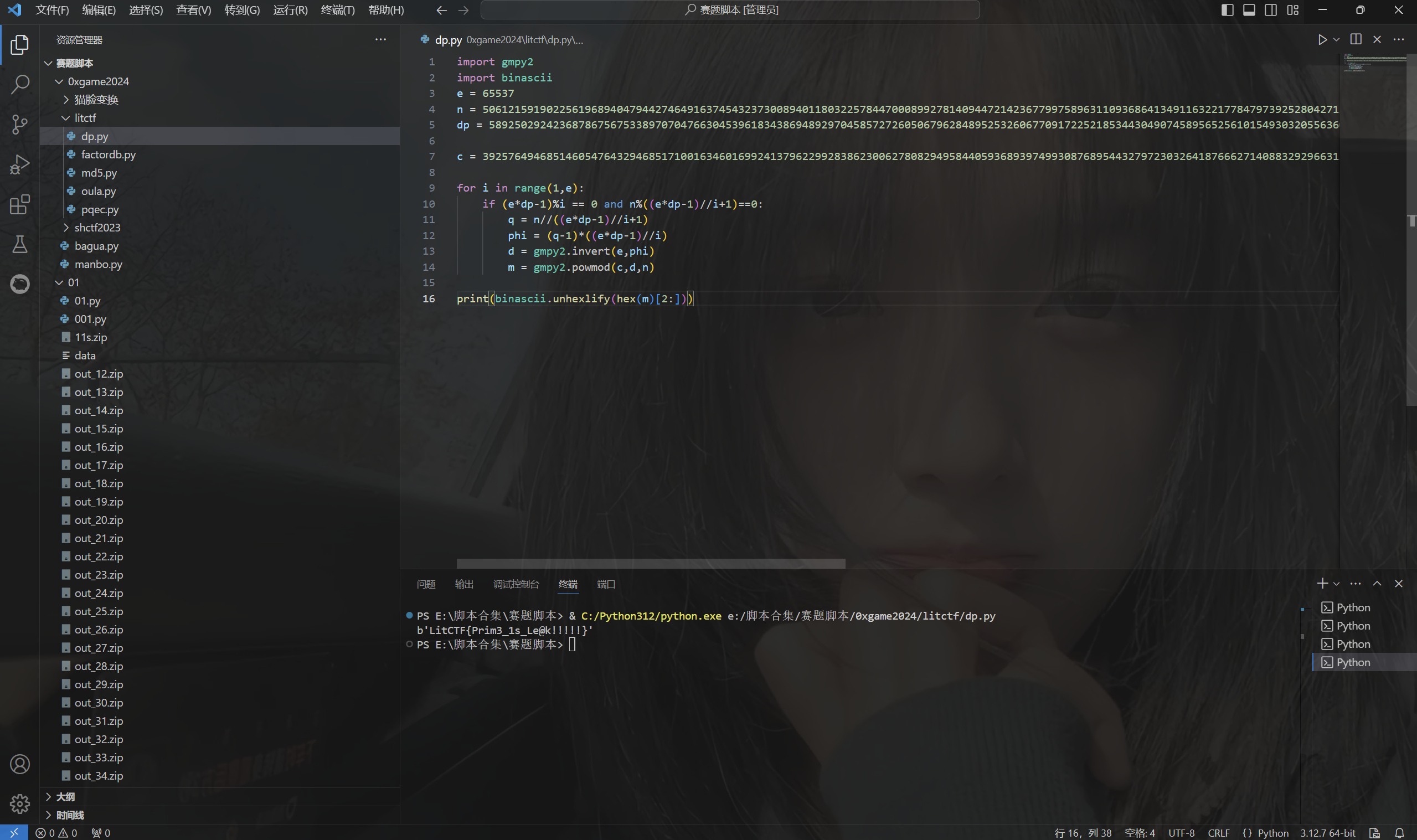
最后flag为
1 | LitCTF{Prim3_1s_Le@k!!!!!} |
[LitCTF 2023]e的学问
题目描述:
1 | 当e不是65537了,该怎么办呢? |
下载附件
1 | from Crypto.Util.number import * |
e与phi_n不互素
exp:
1 | import gmpy2 |
运行得到flag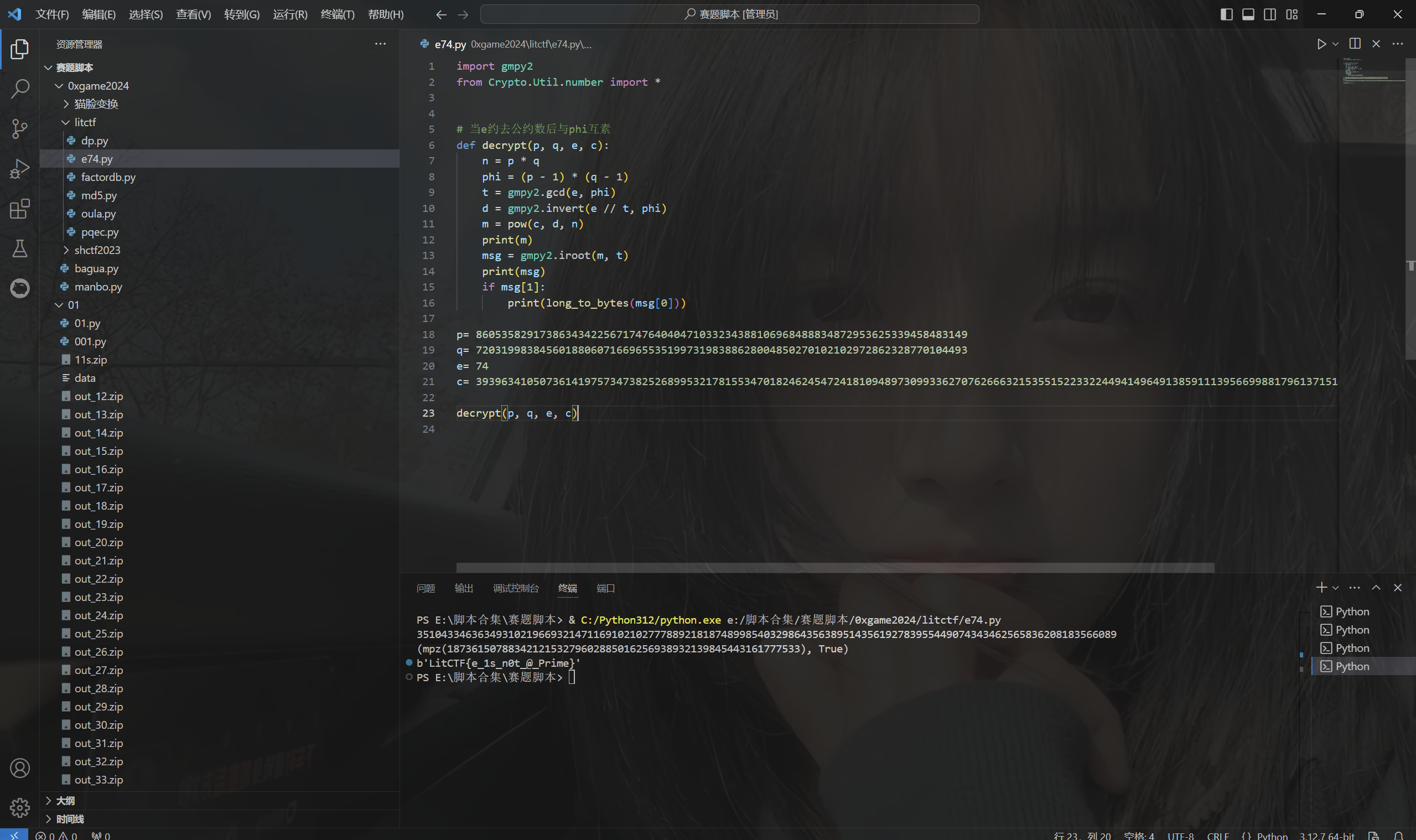
最后flag为
1 | LitCTF{e_1s_n0t_@_Prime} |
[LitCTF 2023]Virginia
下载附件
1 | Ysexj lrk rzmkses os wilj hhks joa rtsy xzmktye yt xuim ehgy joa ofsz blnz yz pohv tnjx fxtx yuzc dxjlmy fyd nzr tnjx fuw cegq! Orkfx wnfe yuz haty eo jwpas;lz wnjce etf wgse tu lz;bk bsaz dzu cfyt zt me,hjnaaxp yuz sabj znrd znk qtfk fyd usp cnfyck yz du fwl zmp tnnygy dzu cfyt zt oo.Sfj yuz sabj pnuzrh nfapospsy yz mgpp yuz dwkje,ettfgn ycigqd tu rlkk dzu yycotl,pnuzrh ytcrub eo qjpp etf harln,kszumm sovj eo sfve etf hguay? Gqhaex auz dzuxxpll ny ozmpry’xsokx.Tf etf fkjw tnfe iz mfrzx joa,ne pxtmahqj hawes zmp ozmpr vjcsus, eou.Yse nfapojdt uk aeuuwe jty’t tjneyxlroqj hgap tnj meyy zf kapreysitl;ehkd uuyy xaqj ehk rzsz tq ebjcyzmtnm ysaz hzmkx llusr tnjtr cfj.Hguaitjds rnps ltc tntde cmz cxd,ehuxp wnt suxy, ehuxp wnt sabj degwnhki,lnj ysoyj hhu mlvk yciki,qox tyle ysee hln guarkhtazj ehk nxpuweathp ol upovqp,wnt sabj eoahsej yseow wibjd.Luap bkltny bttn f dmoqp,gxths cneh g ptsy fyd ksos cneh g ypax.Yse hwtgnypsz kftawp woqw arblyy gp bgxpd us l fuwrozypn vfdt, etf cgs’e gu ty wkqw it qtfkzytoq joa qpt mt zf etfr vfdt lftlawps gso hkfctghsey.Bset dzu cjce htcn,etf wkwp cxdtnm fyd kapretye gwzuti joa bls yrtlosr.Loap yuzc lokp su ysaz bset dzu jnp,yuz'ce zmp otj hhu nd ssnwitl lnj jgexdznk fcoaso yuz ts iwjitl. |
维吉尼亚解码但没有key就爆破key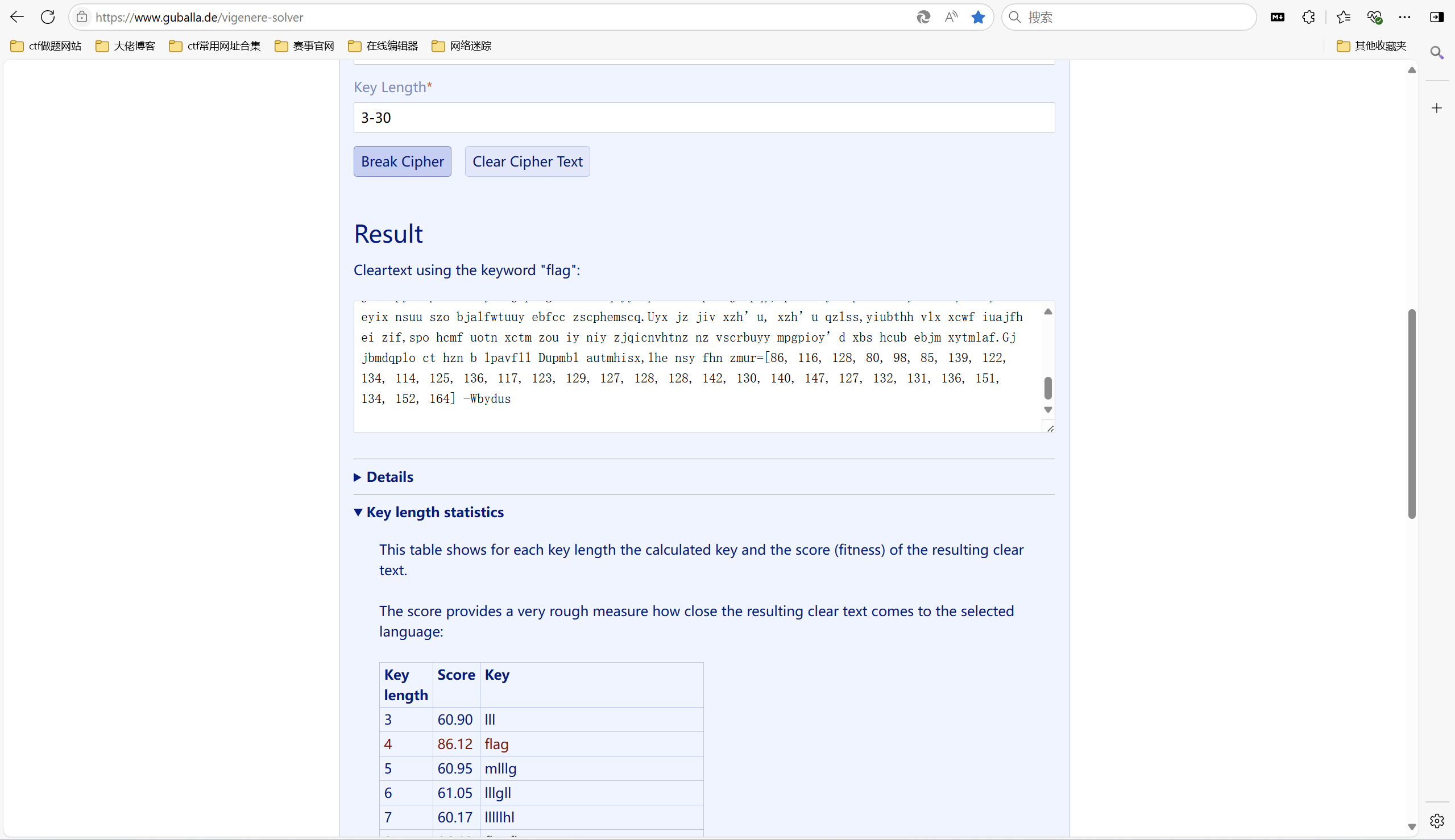
key=flag
将部分乱码再次进行爆破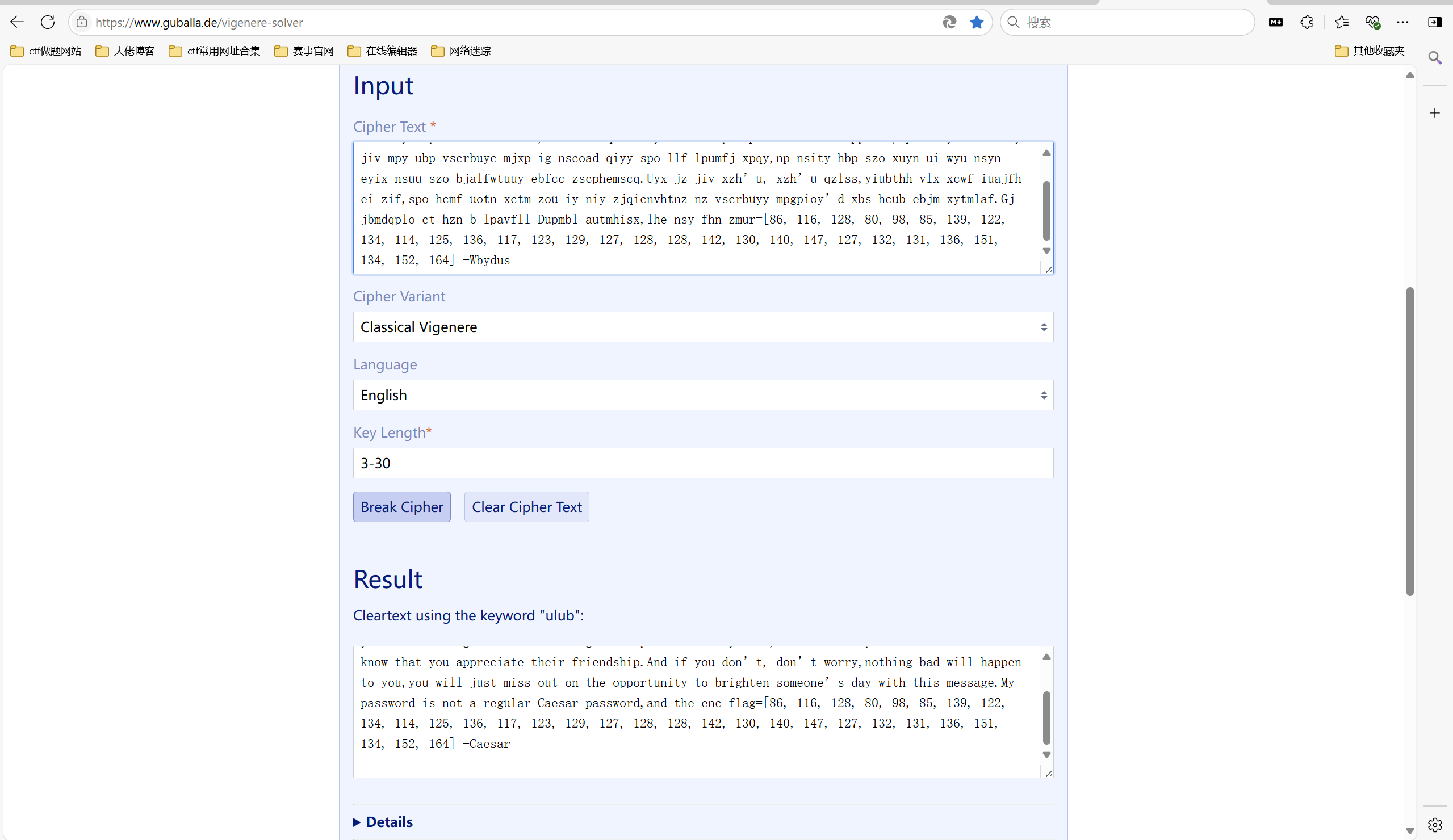
变异凯撒
exp:
1 | a = [86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164] |
运行得到flag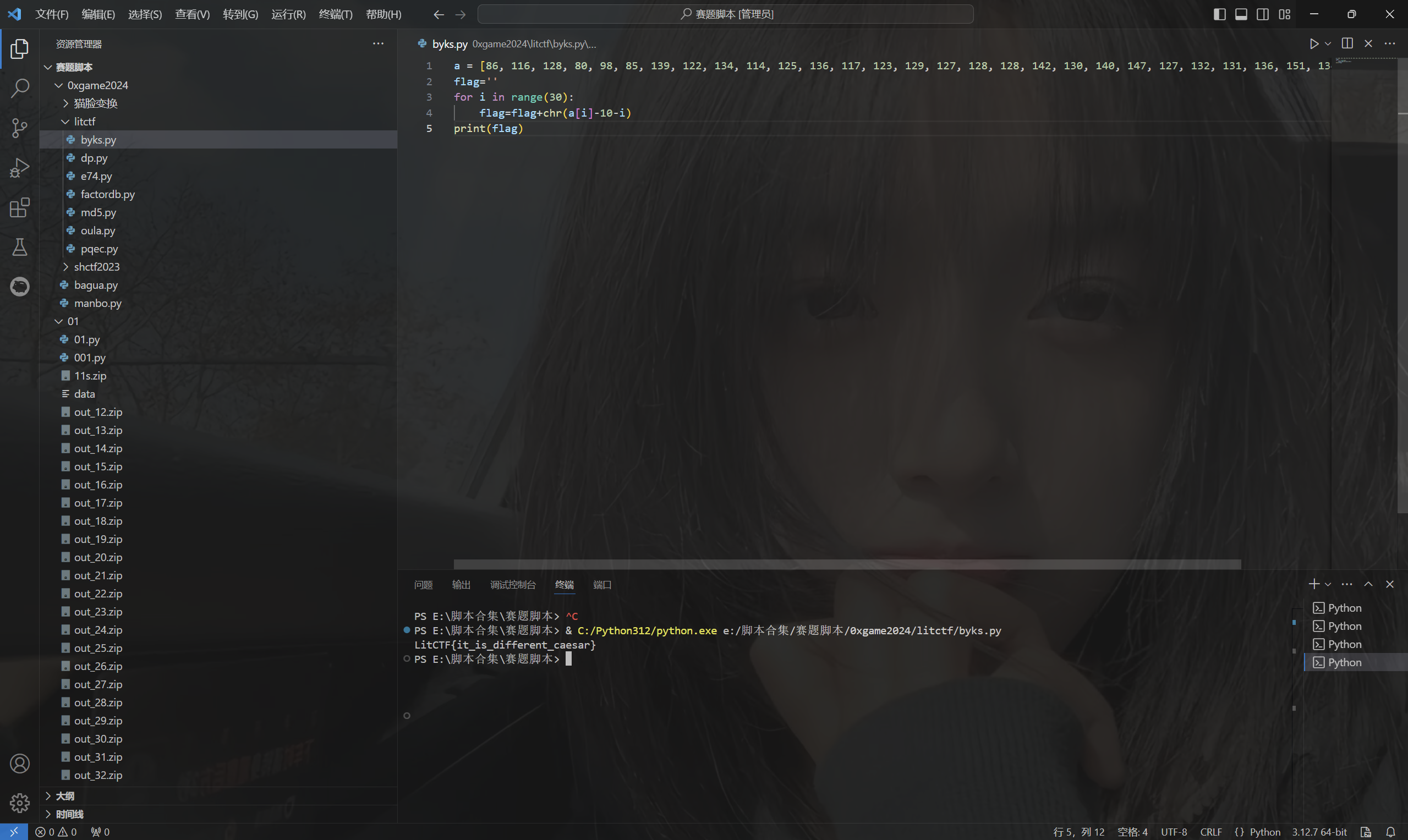
最后flag为
1 | LitCTF{it_is_different_caesar} |
[LitCTF 2023]easy_math (中级)
题目描述:
1 | 中学生看了都得说一句眼熟!!! |
下载附件
1 |
|
利用n和hint建立两个方程
exp:
1 | from Cryptodome.Util.number import* |
运行得到flag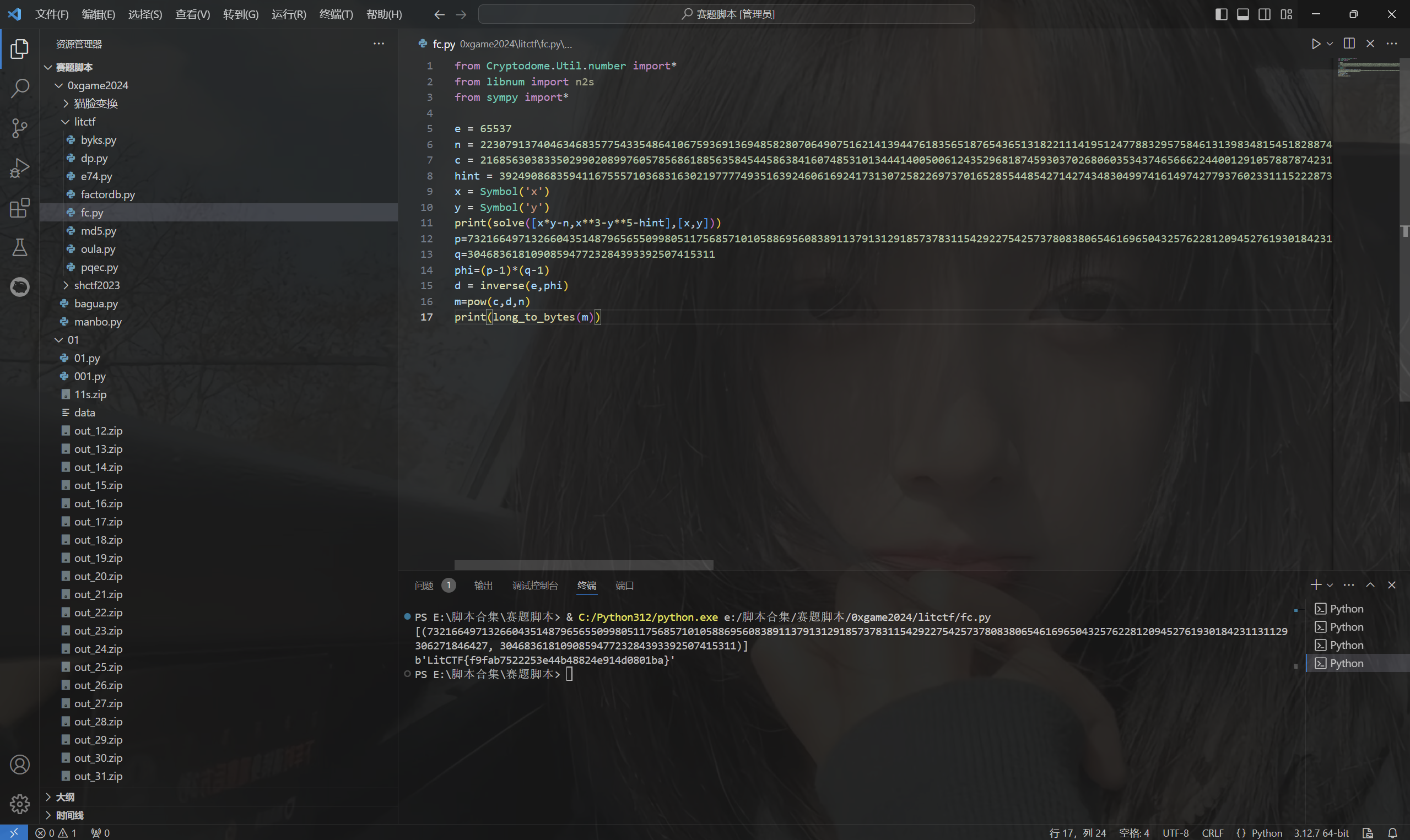
最后flag为
1 | LitCTF{f9fab7522253e44b48824e914d0801ba} |
[LitCTF 2023]Euler
题目描述:
1 | 神秘北极圈,阿拉斯加的山巅 |
下载附件
1 | from Crypto.Util.number import * |
c = pow(m,n-p-q+3,n) 其中, n=pq, n-p-q+3=(p-1)(q-1)+2 故有: c = m^( (p-1)(q-1)+2 )%n 根据欧拉定理,m^( (p-1)(q-1) ) = m^phi = 1%n 故有: c = m^2%n 因此,可以直接对c进行开方,爆破求解得到m。
exp:
1 | from Crypto.Util.number import * |
运行得到flag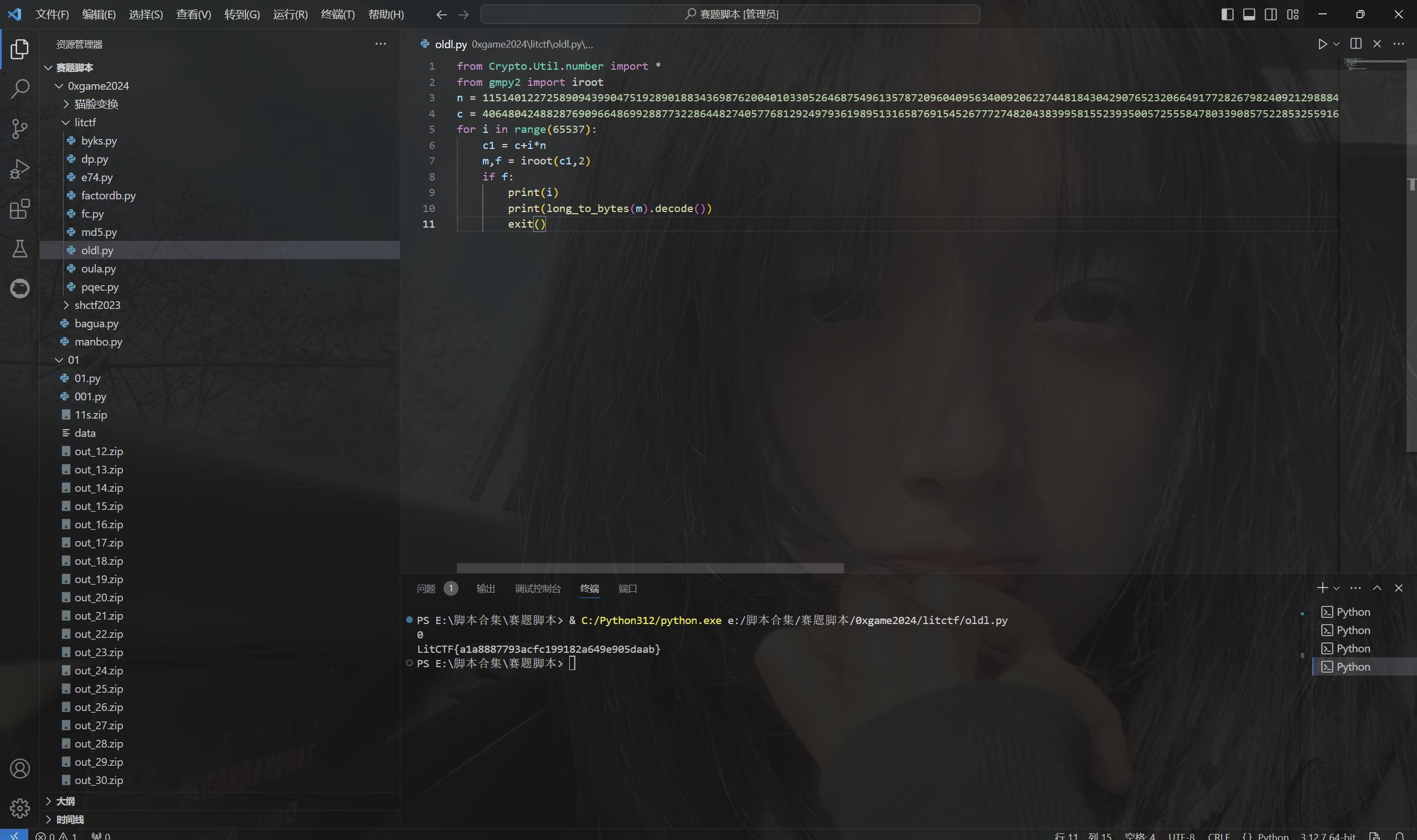
最后flag为
1 | LitCTF{a1a8887793acfc199182a649e905daab} |
[LitCTF 2023]The same common divisor (高级)
题目描述:
1 | 一眼丁真,鉴定为疑惑 |
下载附件
1 | from Crypto.Util.number import * |
两组数中e相同,n,c不同,求出n1与n2的最大公因数即为p,之后就可以得到q和d,从而求解m
exp:
1 | # 解码 |
运行得到flag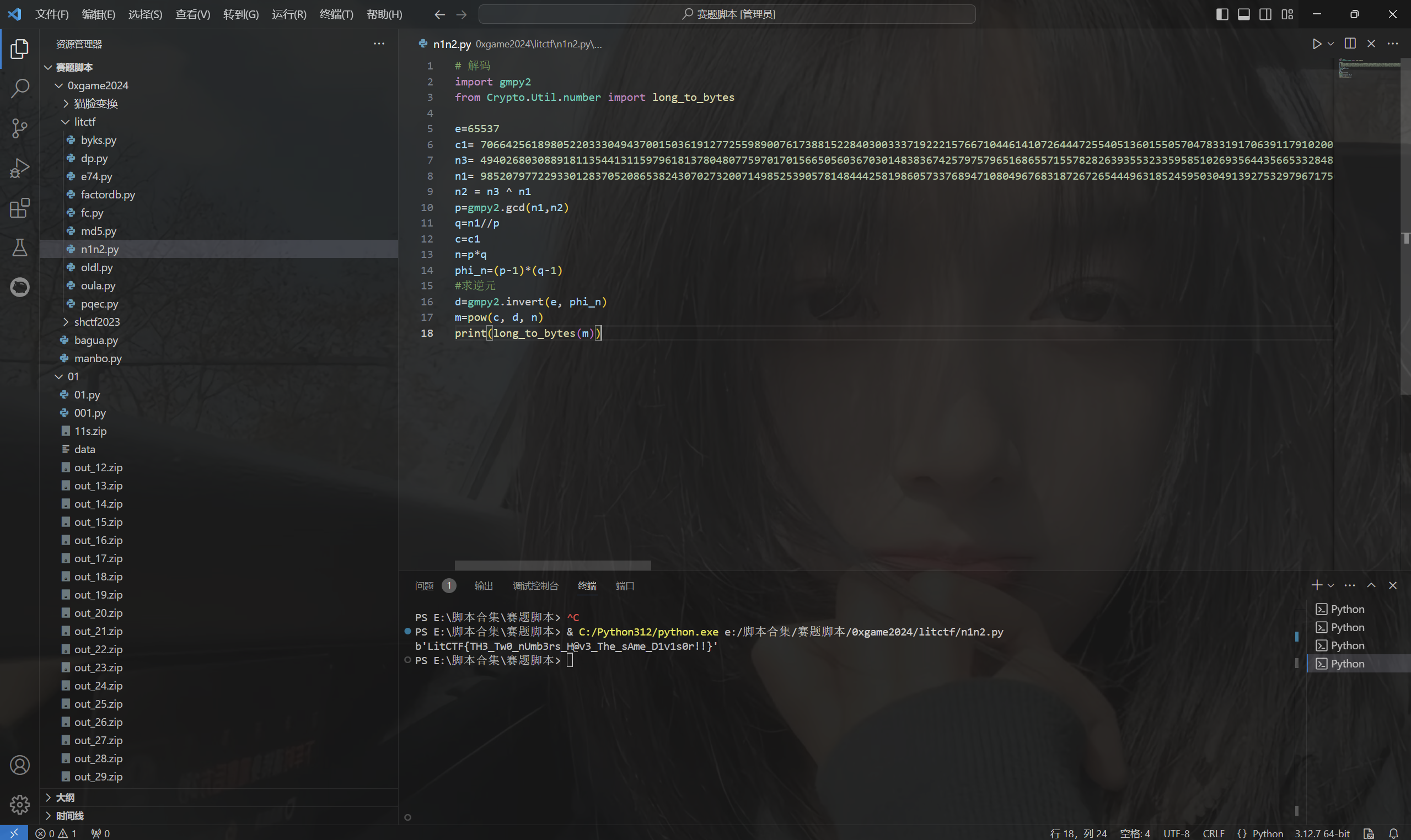
最后flag为
1 | LitCTF{TH3_Tw0_nUmb3rs_H@v3_The_sAme_D1v1s0r!!} |
[LitCTF 2023]Where is P?
题目描述:
1 | 浅浅的搞一下p |
下载附件
1 | from Crypto.Util.number import * |
e=3,先进行小明文攻击恢复P
1 | import gmpy2 |
已知p高位,sage高位攻击
1 | n = 24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721 |
恢复p,正常rsa解密
1 | p = 66302204855869216148926460265779698576660998574555407124043768605865908069722142097621926304390549253688814246272903647124801382742681337653915017783954290069842646020090511605930590064443141710086879668946 |
[LitCTF 2023]隐晦的聊天记录
题目描述:
1 | 这是出题人和一个朋友的几条聊天记录,里面的加密方式似乎是OPT捏 |
下载附件
1 | 出题人:6c73d5240a948c86981bc294814d |
密文和明文异或得到key,和另一个明文异或即可
1 | a = [0x6c,0x73,0xd5,0x24,0x0a,0x94,0x8c,0x86,0x98,0x1b,0xc2,0x94,0x81,0x4d] |
[LitCTF 2023]babyLCG
题目描述:
1 | 主打一个baby难度的LCG |
下载附件
1 | from Crypto.Util.number import * |
线性同余
1 | from Crypto.Util.number import * |
[LitCTF 2023]baby_xor
题目描述:
1 | 探姬姐姐也很疑惑捏! |
下载附件
1 | from Crypto.Util.number import * |
只泄露了高256位,需要爆破8位
exp:
1 | from tqdm import * |
[LitCTF 2023]我测你vva
题目描述:
1 | 听说你会Java?那这题你应该能做出了叭?逆推一下算法就行啦! |
下载附件
1 | public class Encrypto{ |
exp:
1 | def decrypt(ciphertext): |
LitCTF 2024
[LitCTF 2024]small_e
题目描述:
1 | I spilt the flag into several blocks,can you solve the problem? |
下载附件
1 | from Crypto.Util.number import * |
根据c_list,对每个字符进行爆破即可
exp:
1 | n = 19041138093915757361446596917618836424321232810490087445558083446664894622882726613154205435993358657711781275735559409274819618824173042980556986038895407758062549819608054613307399838408867855623647751322414190174111523595370113664729594420259754806834656490417292174994337683676504327493103018506242963063671315605427867054873507720342850038307517016687659435974562024973531717274759193577450556292821410388268243304996720337394829726453680432751092955575512372582624694709289019402908986429709116441544332327738968785428501665254894444651547623008530708343210644814773933974042816703834571427534684321229977525229 |
[LitCTF 2024]common_primes_plus
题目描述:
1 | It’s not hard,trust me |
下载附件
1 | from Crypto.Util.number import * |
hint1hint2%n1=kn2,那么k*n2和n1做gcd就是p
exp:
1 | n1=72619153900682160072296441595808393095979917106156741746523649725579328293061366133340736822282117284050717527134297532031234706715551253283030119063143935874516054785948327252045453986903379262257406260016876625891582923191913450785482873961282498295762698500898694660964018533698142756095427829906473038053 |
[LitCTF 2024]common_primes
题目描述:
1 | OK,it’s your common primes |
下载附件
1 | from Crypto.Util.number import * |
简单的共享素数。用GCD求出来的最大公约数即是p
exp:
1 | n1=63306931765261881888912008095340470978772999620205174857271016152744820165330787864800482852578992473814976781143226630412780924144266471891939661312715157811674817013479316983665960087664430205713509995750877665395721635625035356901765881750073584848176491668327836527294900831898083545883834181689919776769 |
[LitCTF 2024]真·EasyRSA
题目描述:
1 | 怎么说呢,就……真的挺简单的 |
下载附件
1 | from Crypto.Util.number import * |
解两段
exp:
1 | from Crypto.Util.number import * |
[LitCTF 2024]small_e_plus
题目描述:
1 | You need to change your mind |
下载附件
1 | from Crypto.Util.number import * |
爆破e
exp:
1 | import string |
[LitCTF 2024]little_fermat
题目描述:
1 | Do you know fermat? |
下载附件
1 | from Crypto.Util.number import * |
费马小定理a^(p-1)≡1(mod p),那么可以得到x=p-1
exp:
1 | from Crypto.Util.number import * |
[LitCTF 2024]男人,什么罐头我说!
题目描述:
1 | 全是0和1?我能说啥? |
下载附件
1 | 00001010 00110000 00110001 00110000 00110001 00110001 00100000 00110000 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110001 00110000 00110001 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110000 00110000 00110000 00110000 00110000 00100000 00110001 00110000 00110000 00110001 00110000 00100000 00110000 00110000 00110000 00110001 00110000 00100000 00110000 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110001 00100000 00110000 00110000 00110000 00110000 00110000 00100000 00110001 00110000 00110001 00110001 00110000 |
二进制转ascll
1 | 01011 00000 01100 10100 00111 00000 10010 00010 00000 01100 01010 10001 00000 10110 |
培根解密
1 | LitCTF{MANWHATCANLSAY} |
[LitCTF 2024]little_fermat_plus
题目描述:
1 | caution difference |
下载附件
1 | from Crypto.Util.number import * |
两边同时乘方1024
exp:
1 | n = 169522900072954416356051647146585827691225327527086797334523482640452305793443986277933900273961829438217255938808371865341750200444086653241610669340348513884285892043530862971785487294831341653909852543469963032532560079879299447677636753647721541724969084825510405349373420839032990681851700075554428485967 |
[LitCTF 2024]真·签到!!!
下载附件
1 | from enc import flag |
爆破指数,然后解密
exp:
1 | from tqdm import * |
[LitCTF 2024]CRT
题目描述:
1 | 有物不知其数,三三数之剩二,五五数之剩三,七七数之剩二。问物几何? |
下载附件
1 | from Crypto.Util.number import * |
简单的crt
exp:
1 | n=[] |
[LitCTF 2024]Polynomial
题目描述:
1 | Give you three polynomials,please get unknown number. |
下载附件
1 | from Crypto.Util.number import * |
解方程
exp:
1 | from sympy import symbols, Eq, solve |
[LitCTF 2024]Polynomial_plus
题目描述:
1 | p is a polynomial,q too. |
下载附件
1 | from Crypto.Util.number import * |
还是解方程
exp:
1 | n = 343424787688946710828788193478518340184635630498236346907606509763011890082198311173501834898393322176325060349656021994088578448585570427399686920253145504431065451412326430233084073651599248661762036671841142048573051549474182586297565046285161375600990596119448538118327240405957845178956427810835797220204485242640945891970398041508724313442375608608662117158013 |
[LitCTF 2024]CRT_plus
题目描述:
1 | 也许要在老祖宗留下来的基础上改变一下 |
下载附件
1 | from Crypto.Util.number import * |
线性填充广播攻击
exp:
1 | from gmpy2 import * |
[LitCTF 2024]midRSA
题目描述:
1 | mid!!!mid!!!mid!!! |
下载附件
1 | from enc import flag |
p的高位和低位泄露
exp:
1 | n = 10912724749357317040117295175340915836309117326481842971911576002816136982982366412133127436929465794389631046998036509363047557873155846920275327196471118680559431161116535588318645353317739214770132790445807395653916337747136630775427171105596048281228718048314706544665819996610453587925745842345926654572410324847927833437471701176403031302117052425160845583678182335391697596801106017558494065612842298945201720733418994561321697012416704574891516720606917736854915347853341353358814869449590841870866128113400765492223847582506991200050368263722438854522124807397499067048911261448546634778788867555039834459211 |
[LitCTF 2024]你是capper,还是copper?
题目描述:
1 | er攻击就是神中神 |
下载附件
1 | from Crypto.Util.number import * |
把p右移100位,然后用p求解
exp:
1 | e = 13072237795424057999129127027979234989717137387957646486113645675299547455876355434346547808746552482965795288244687521108647998478307740108159933821771239011129296482617888480397978257432977308896431711182794340987048211178166823842422554472231405752077101111017727678497340027900077855145324567076470130835 |
[LitCTF 2024]暗号-pailler
1 | nc node4.anna.nssctf.cn 28006 |
Pillier加密



