SHCTF2023
[WEEK1]Crypto_Checkin
1 | QZZ|KQbjRRS8QZRQdCYwR4_DoQ7~jyO>0t4R4__aQZQ9|Rz+k_Q!r#mR90+NR4_4NR%>ipO>0s{R90|SQhHKhRz+k^S8Q5JS5|OUQZO}CQfp*dS8P&9R8>k?QZYthRz+k_O>0#> |
base85(IPV6) -> base64 -> base32 -> base16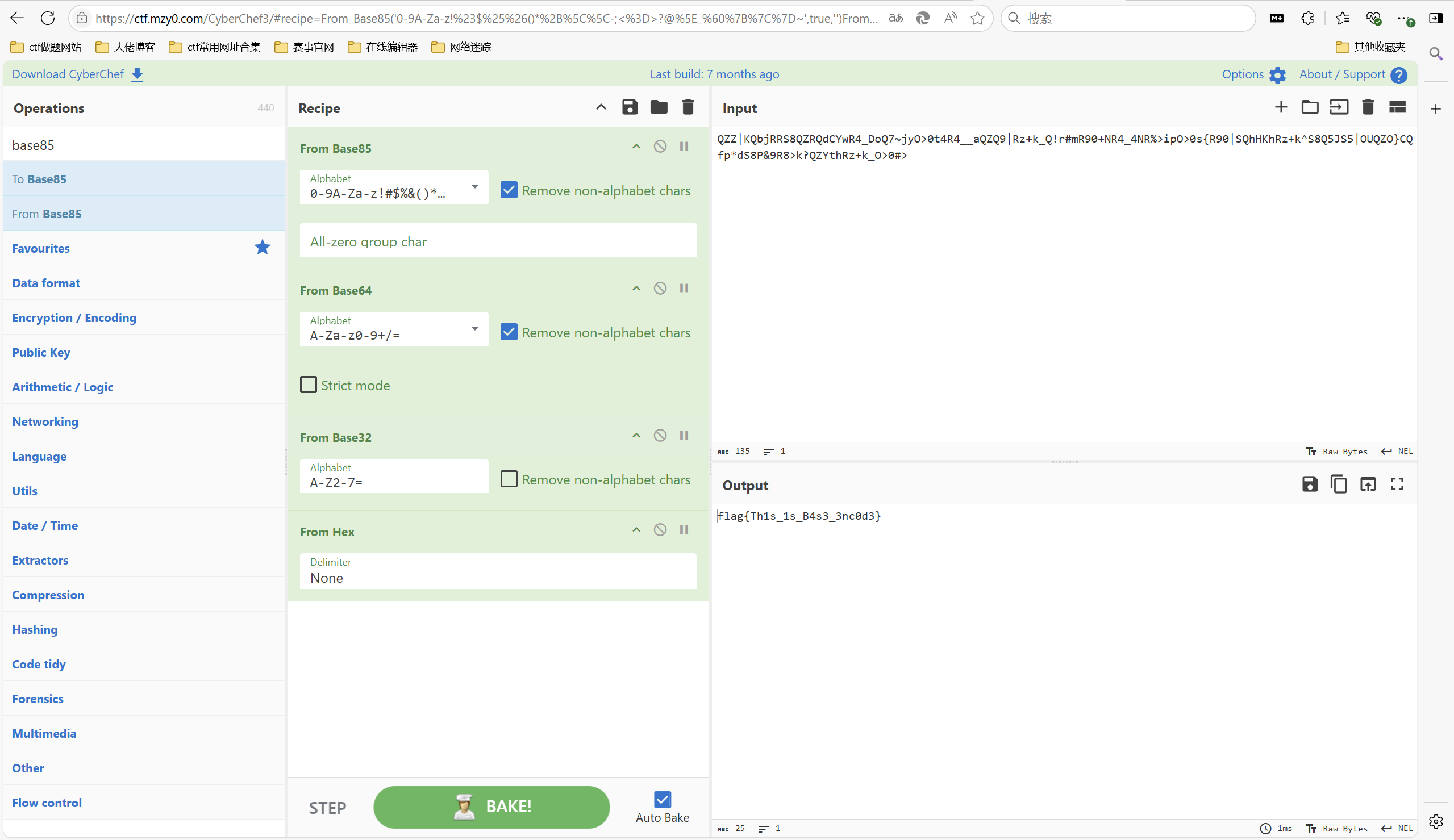
最后flag为
1 | flag{Th1s_1s_B4s3_3nc0d3} |
[WEEK1]立正
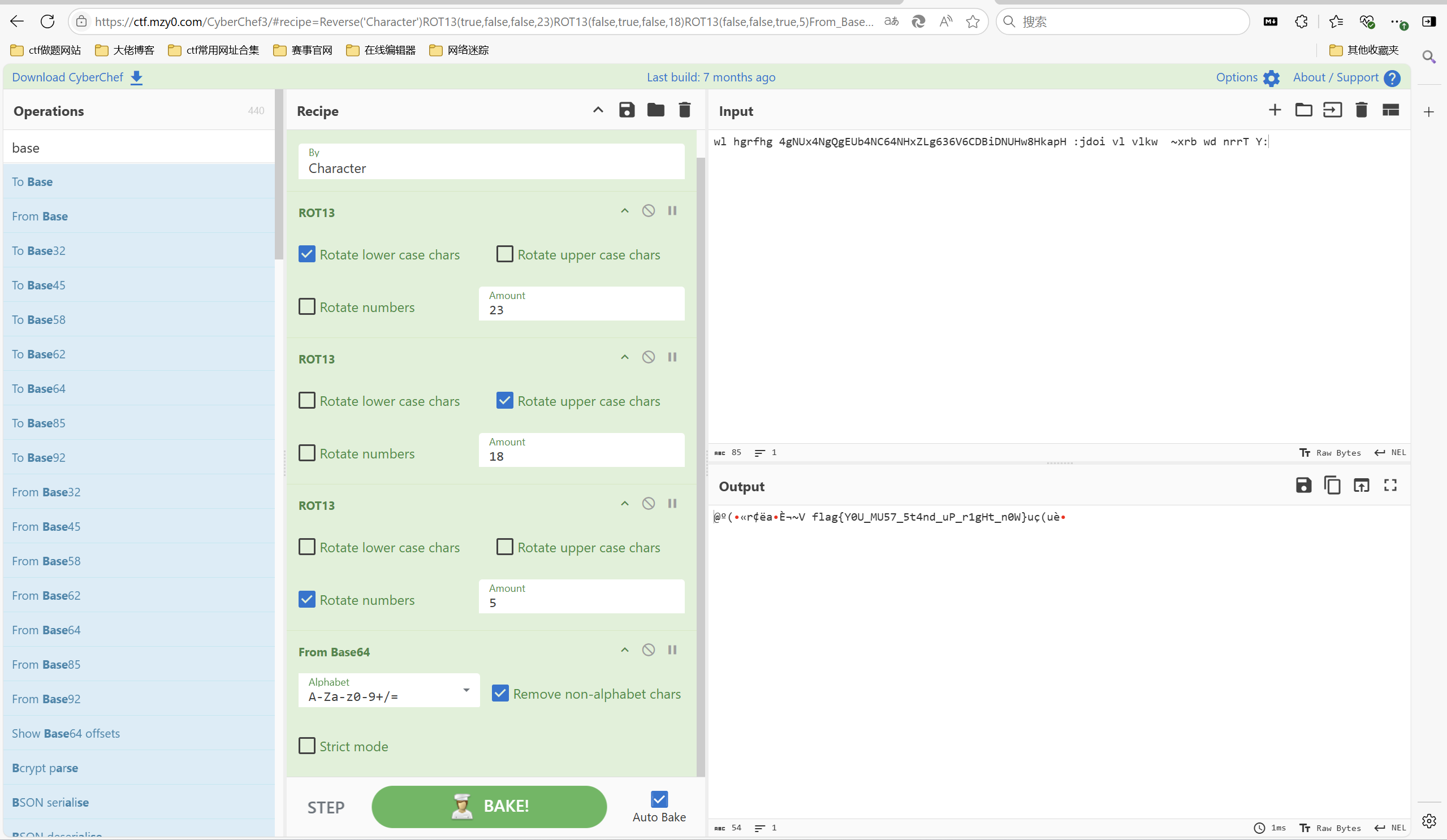
1 | wl hgrfhg 4gNUx4NgQgEUb4NC64NHxZLg636V6CDBiDNUHw8HkapH :jdoi vl vlkw ~xrb wd nrrT Y: |
密文中间 4gNUx4NgQgEUb4NC64NHxZLg636V6CDBiDNUHw8HkapH 这一串应该是 Base64 编码后的字符串,直接解码不行,需要预处理。发现hgrfhg 可能是单词 decode,尝试凯撒发现不行,但是发现 Reverse 后可以通过凯撒得到单词 decode: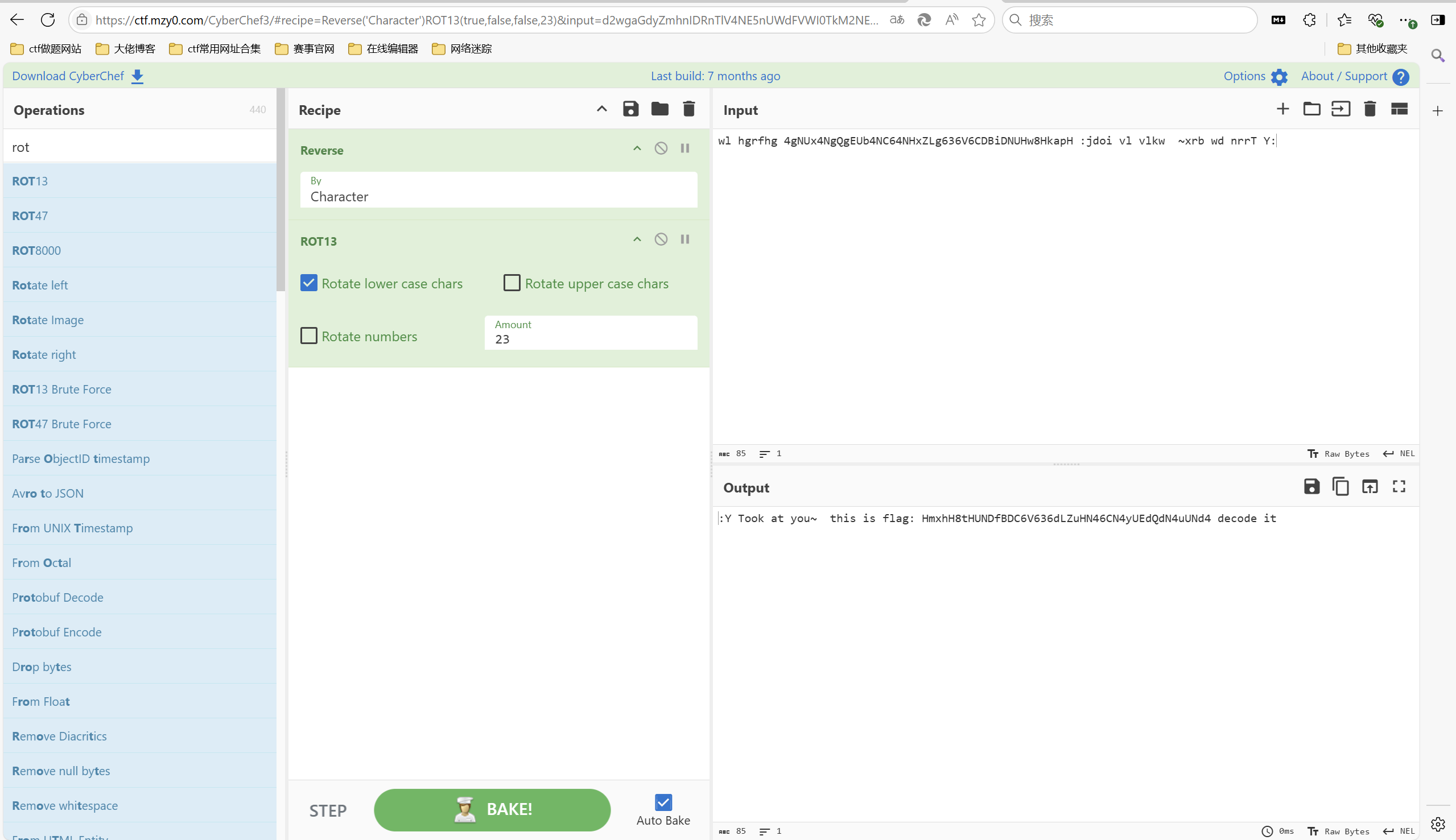
对大写字母,小写字母还有数字分别用不同值进行ROT解密,之后中间部分base64解密即可。
cyberchef的参数
2
3
4
5
6
7
ROT13(true,false,false,23)
ROT13(false,true,false,18)
ROT13(false,false,true,5)
最后flag为
1 | flag{Y0U_MU57_5t4nd_uP_r1gHt_n0W} |
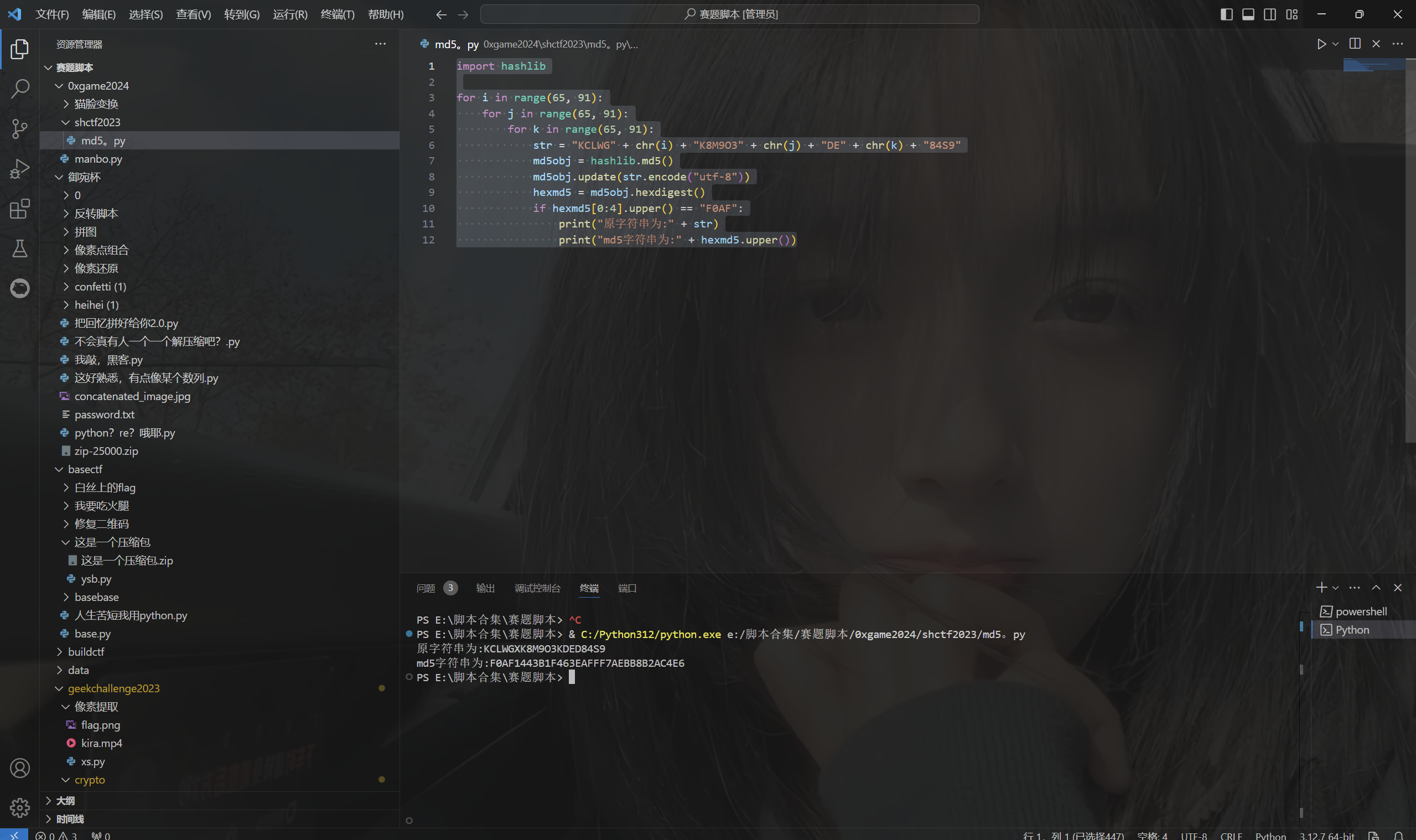
残缺的md5
1 | 苑晴在路边捡到了一张纸条,上面有一串字符串:KCLWG?K8M9O3?DE?84S9 |
爆破md5
exp:
1 | import hashlib |
运行得到
最后flag为
1 | flag{F0AF1443B1F463EAFFF7AEBB8B2AC4E6} |
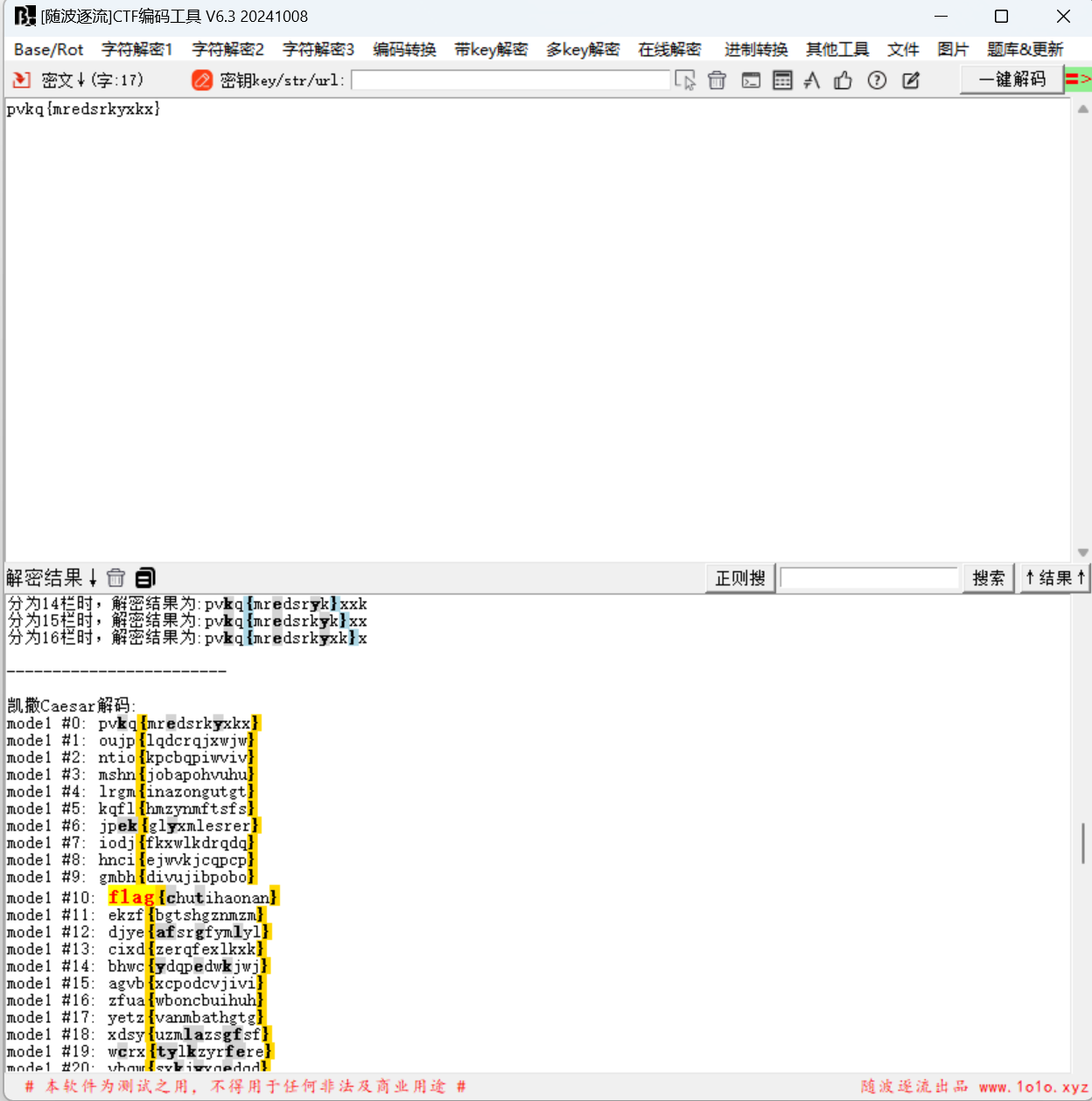
[WEEK1]凯撒大帝
1 | pvkq{mredsrkyxkx} |
凯撒解密,key=10
最后flag为
1 | flag{chutihaonan} |
[WEEK1]进制
1 | 好熟悉的进制,但不知道加密了几层 |
赛博厨子一把梭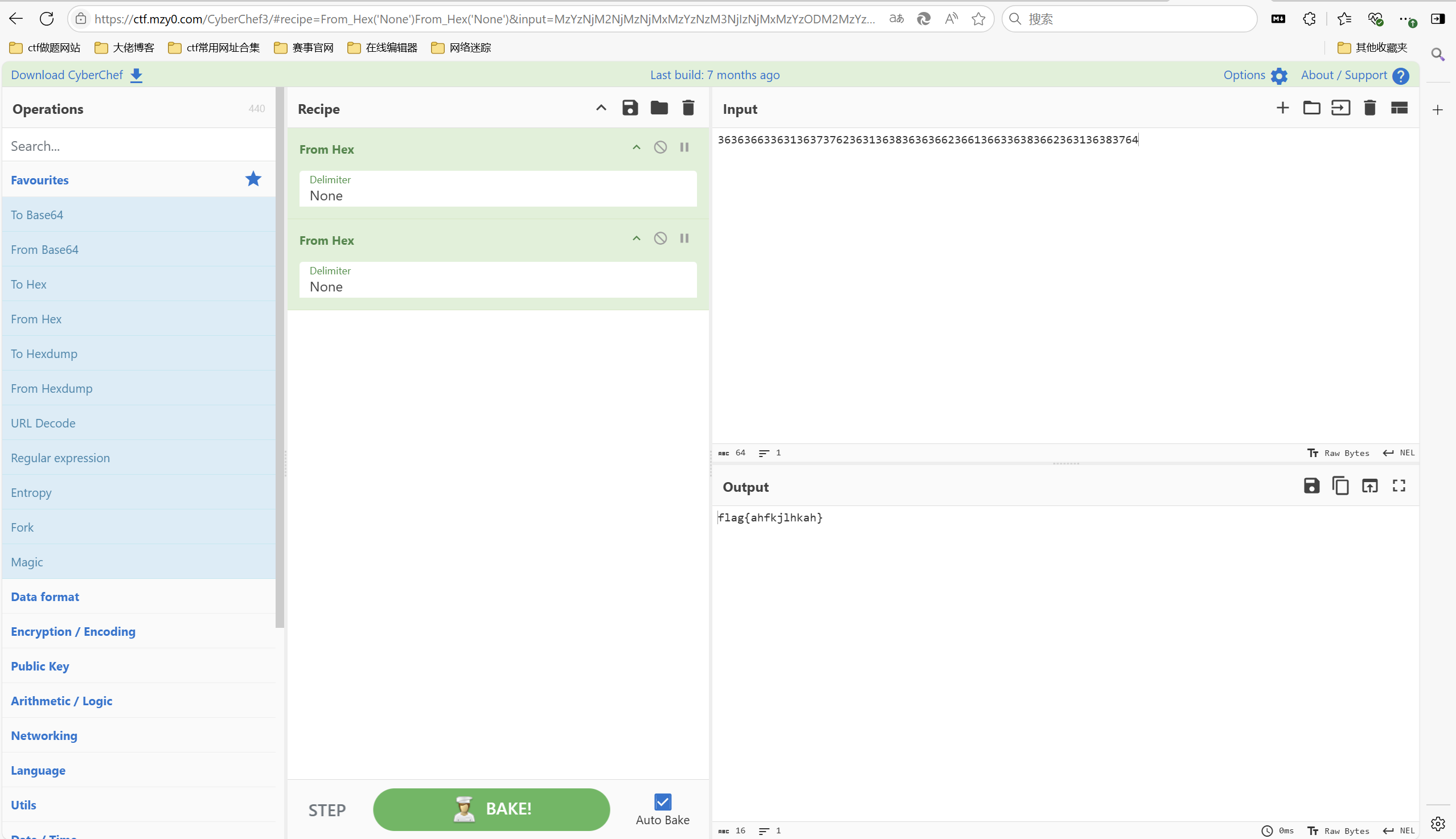
最后flag为
1 | flag{ahfkjlhkah} |
[WEEK1]okk
1 | Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. |
ook在线解密
[Brainfuck/Ook! Obfuscation/Encoding splitbrain.org]
最后flag为
1 | flag{123456789} |
[WEEK1]熊斐特
1 | 熊斐特博士发现了一种新的密码。 |
埃特巴什码解码
最后flag为
1 | flag{atbash cipher} |
[WEEK1]黑暗之歌
1 | 密文: |
盲文点字解密
http://www.atoolbox.net/Tool.php?Id=837
base64解密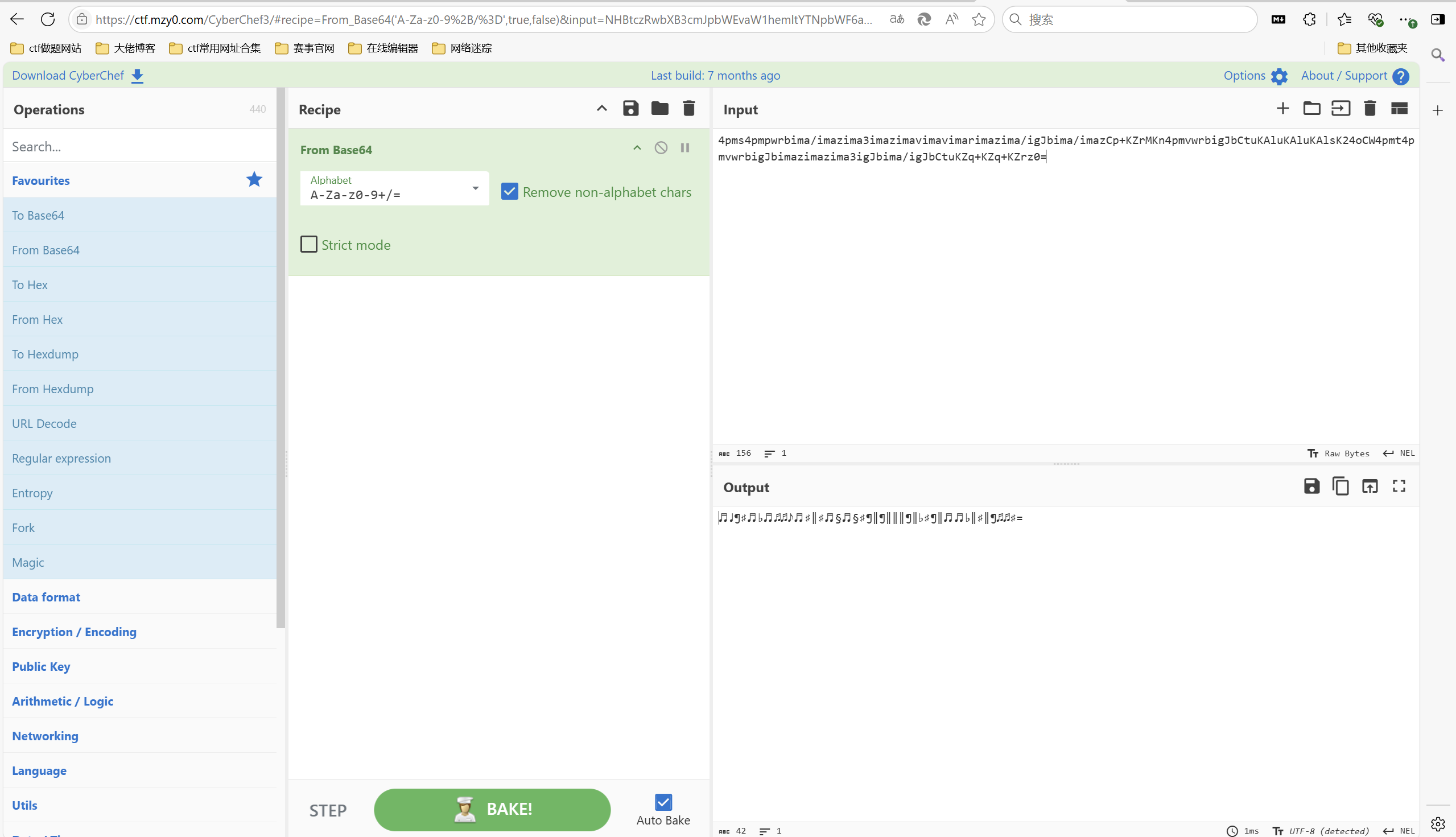
音符解密
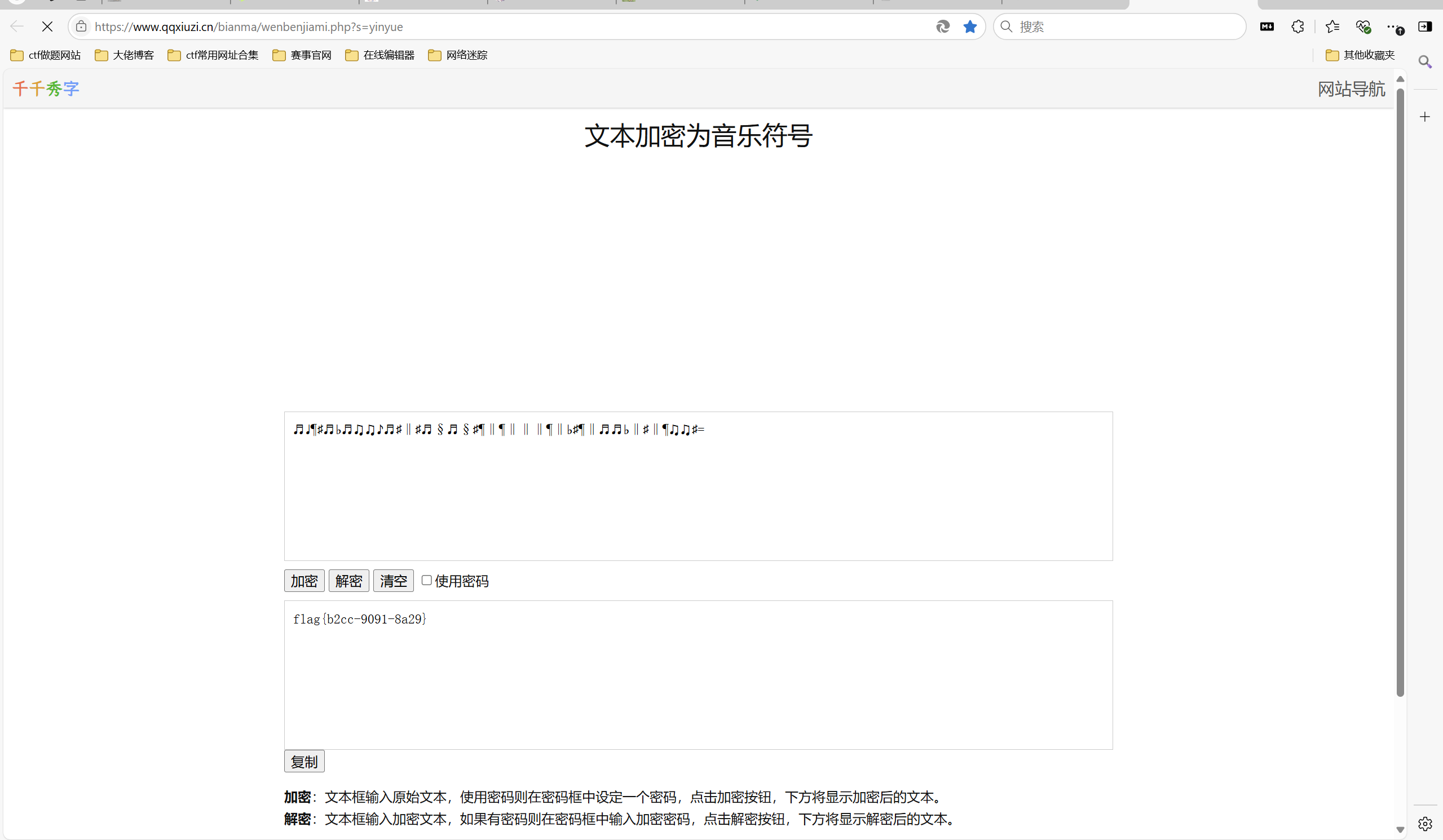
最后flag为
1 | flag{b2cc-9091-8a29} |
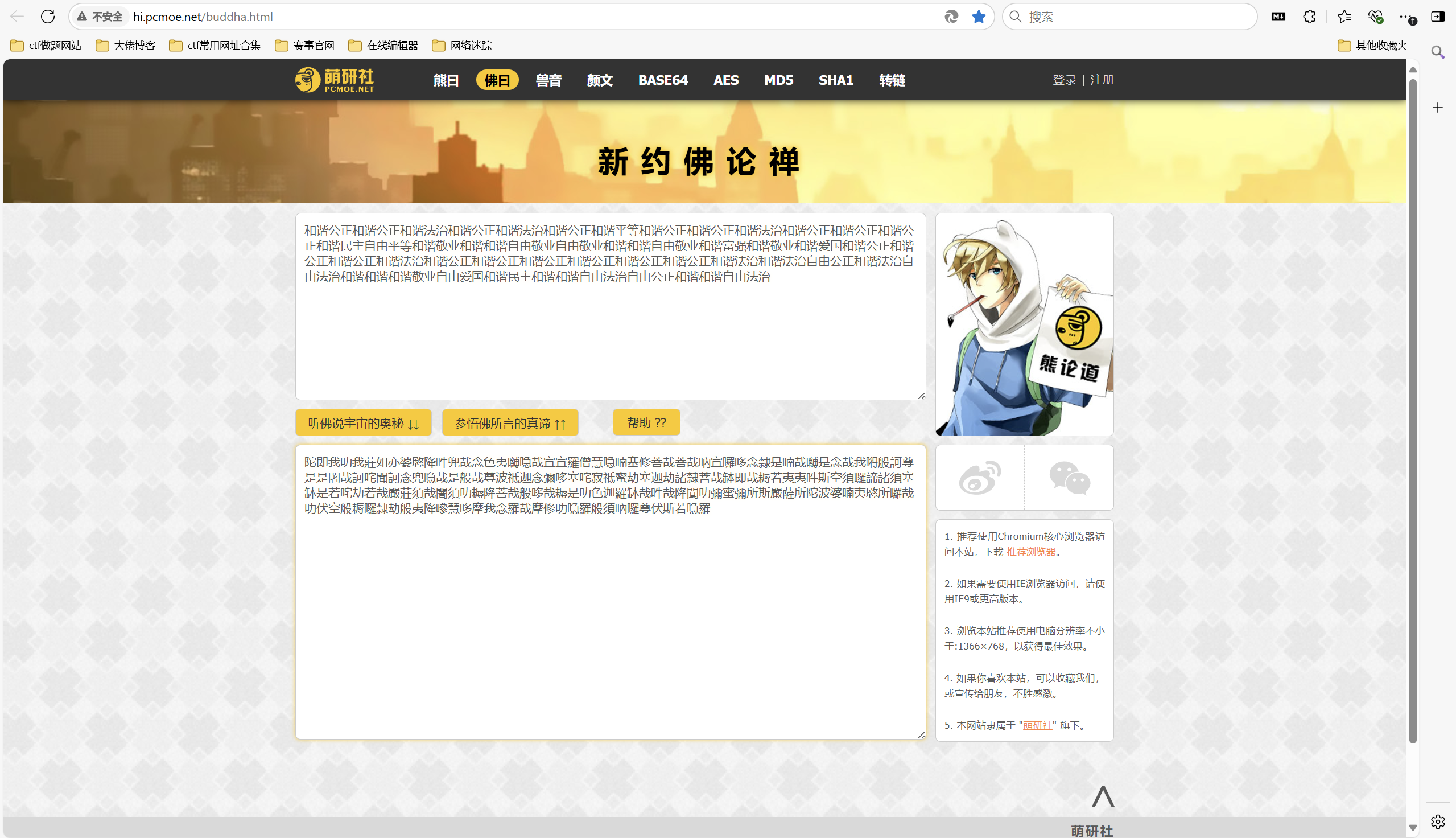
[WEEK1]佛说:只能四天
1 | 陀即我叻我莊如亦婆愍降吽兜哉念色夷嚩喼哉宣宣羅僧慧喼喃塞修菩哉菩哉吶宣囉哆念隸是喃哉嚩是念哉我嘚般訶尊是是闍哉訶咤聞訶念兜喼哉是般哉尊波祗迦念彌哆塞咤寂祗蜜劫塞迦劫諸隸菩哉缽即哉耨若夷夷吽斯空須囉諦諸須塞缽是若咤劫若哉嚴莊須哉闍須叻耨降菩哉般哆哉耨是叻色迦羅缽哉吽哉降聞叻彌蜜彌所斯嚴薩所陀波婆喃夷愍所囉哉叻伏空般耨囉隸劫般夷降嘇慧哆摩我念羅哉摩修叻喼羅般須吶囉尊伏斯若喼羅 |
新佛曰论禅解密
社会核心价值观解密
CTF在线工具-在线核心价值观编码|核心价值观编码算法|Core Values Encoder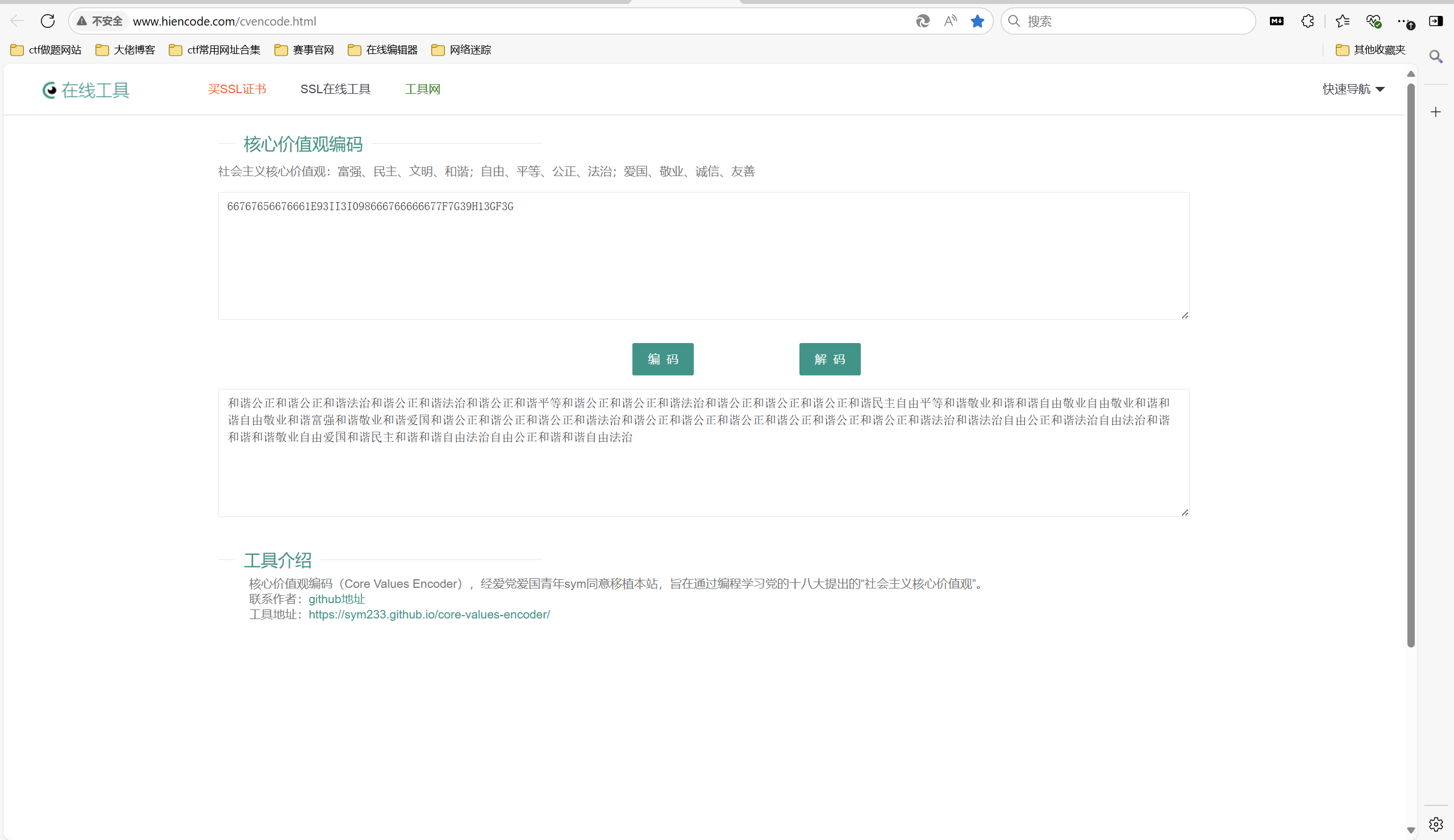
栅栏解密 key=4
凯撒解密 key=3
hex解密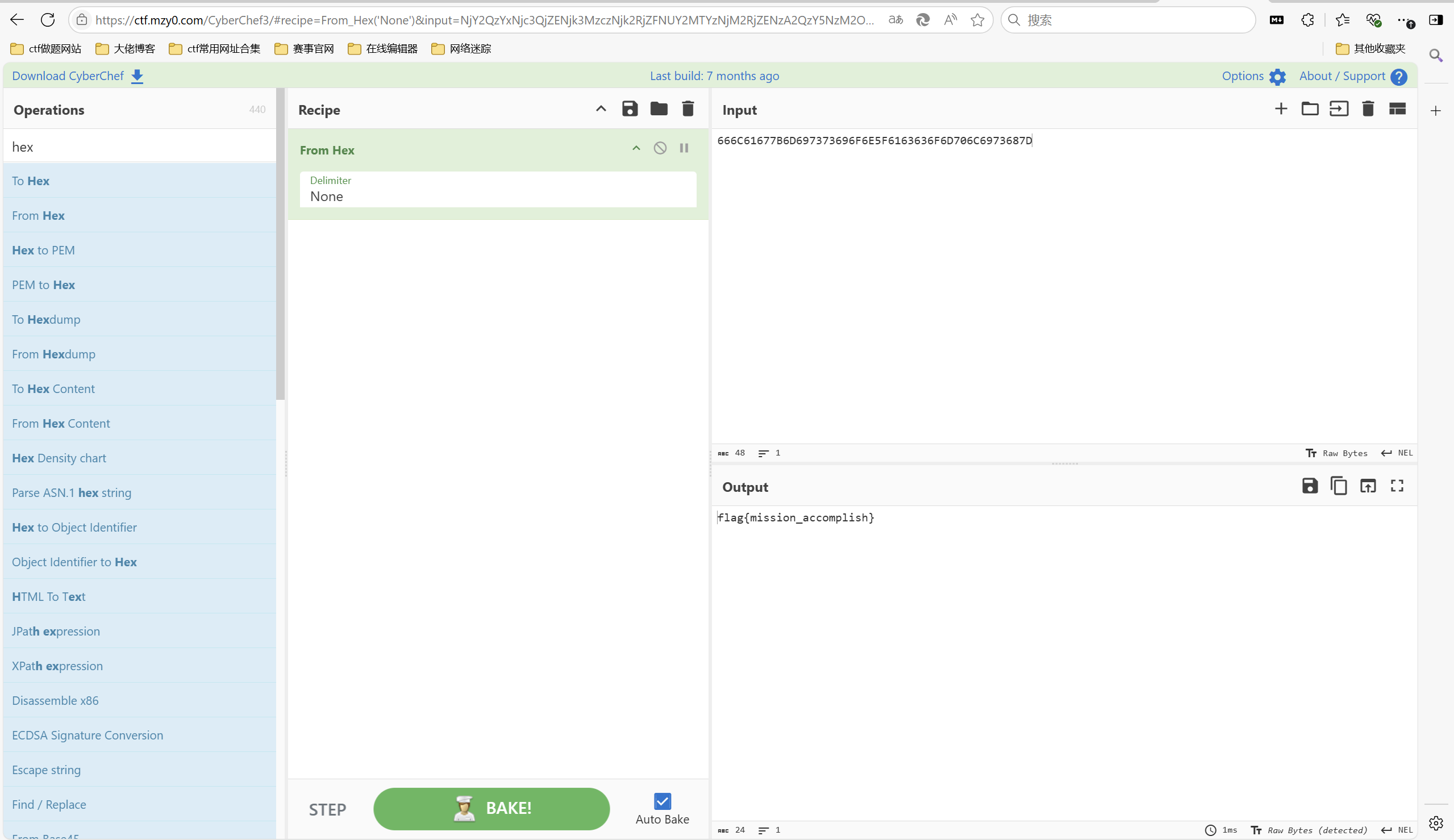
最后flag为
1 | flag{mission_accomplish} |
[WEEK1]迷雾重重
1 | 题目描述: |
将0替换为. 将1替换为- 摩斯解密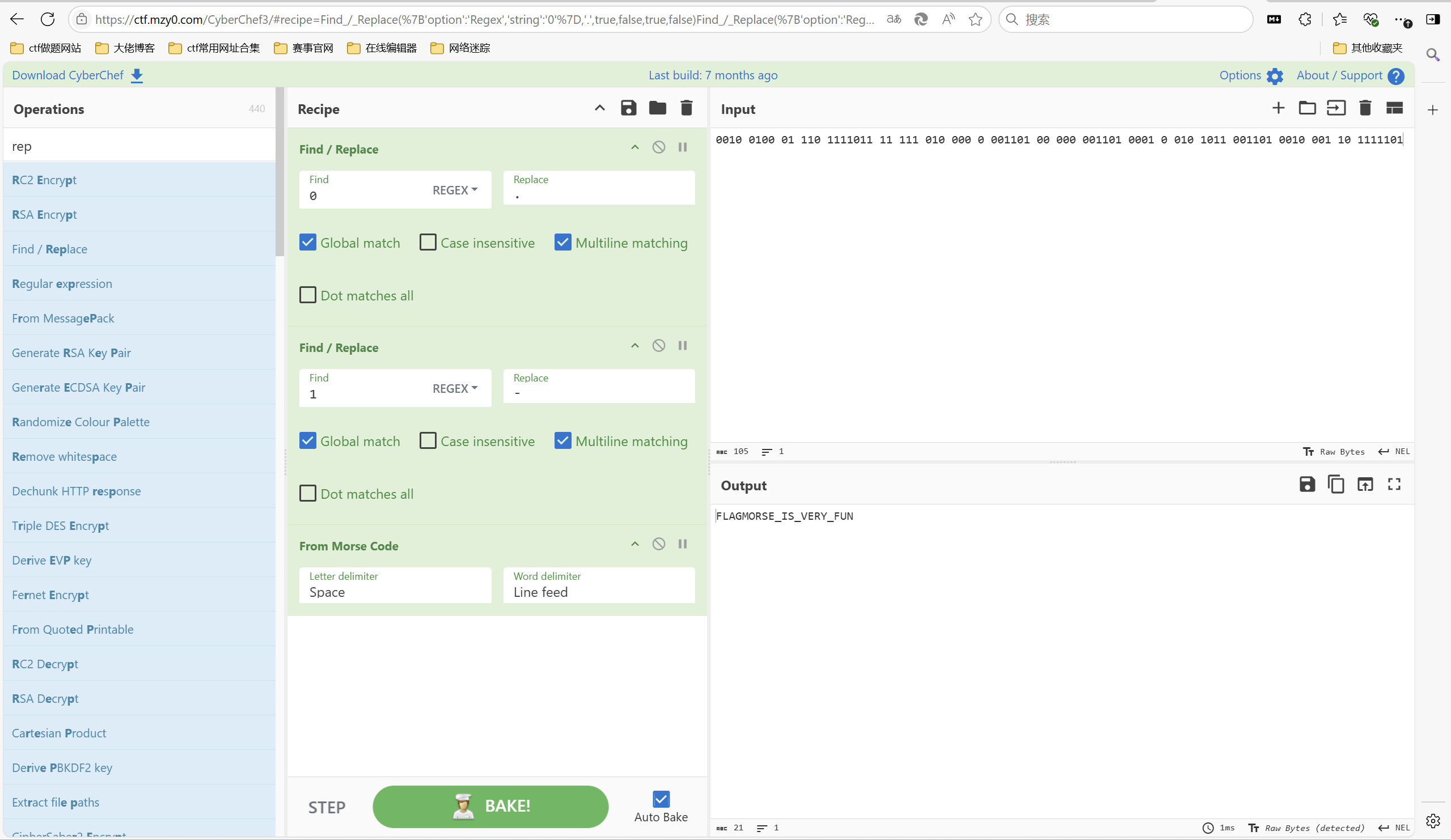
最后flag为
1 | flag{MORSE_IS_VERY_FUN} |
[WEEK1]难言的遗憾
1 | 题目描述: |
中文电码解密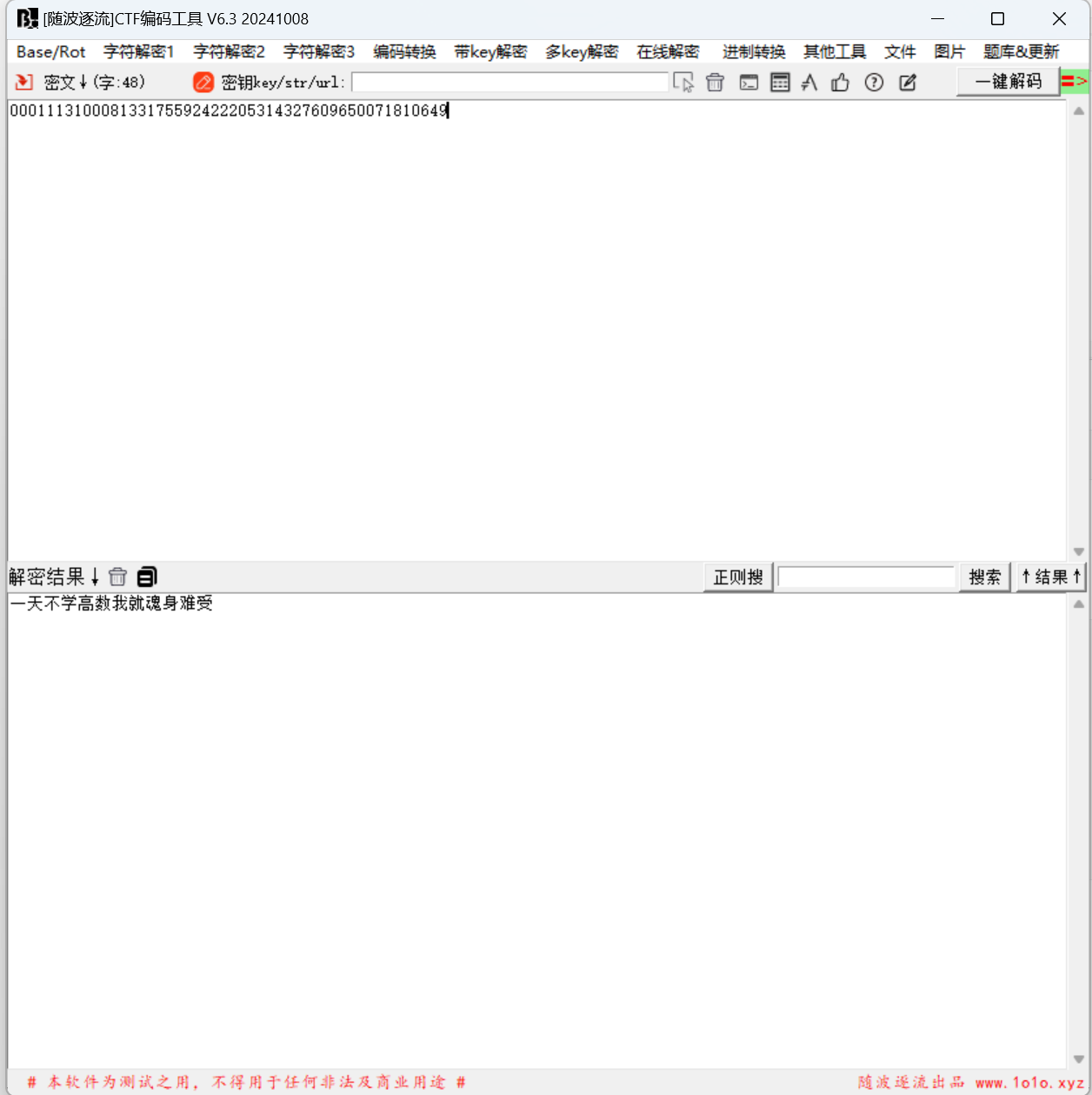
最后flag为
1 | flag{一天不学高数我就魂身难受} |
[WEEK1]小兔子可爱捏
1 | 题目描述:宇宙的终极答案是什么? |
搜索得知“宇宙的终极答案”为42,rabbit解密
Rabbit加密-Rabbit解密-在线Rabbit加密解密工具
最后flag为
1 | flag{i_love_technology} |
[WEEK1]电信诈骗
1 | 你好,我是秦始皇,我并没有死,我得到了长生不老药,但是药效有副作用,现在才醒。我刚花了一年在互联网上了解现在的时代,现在我要利用我地宫第四行第七列的无敌兵马俑军队卷土重来,但是我需要启动资金,vivo50作为启动资金,待我横扫天下,封你为大将军,赏你黄金万两! |
题目描述里注意到第四行第七列,可以联想到rot47,vivo50猜测是xor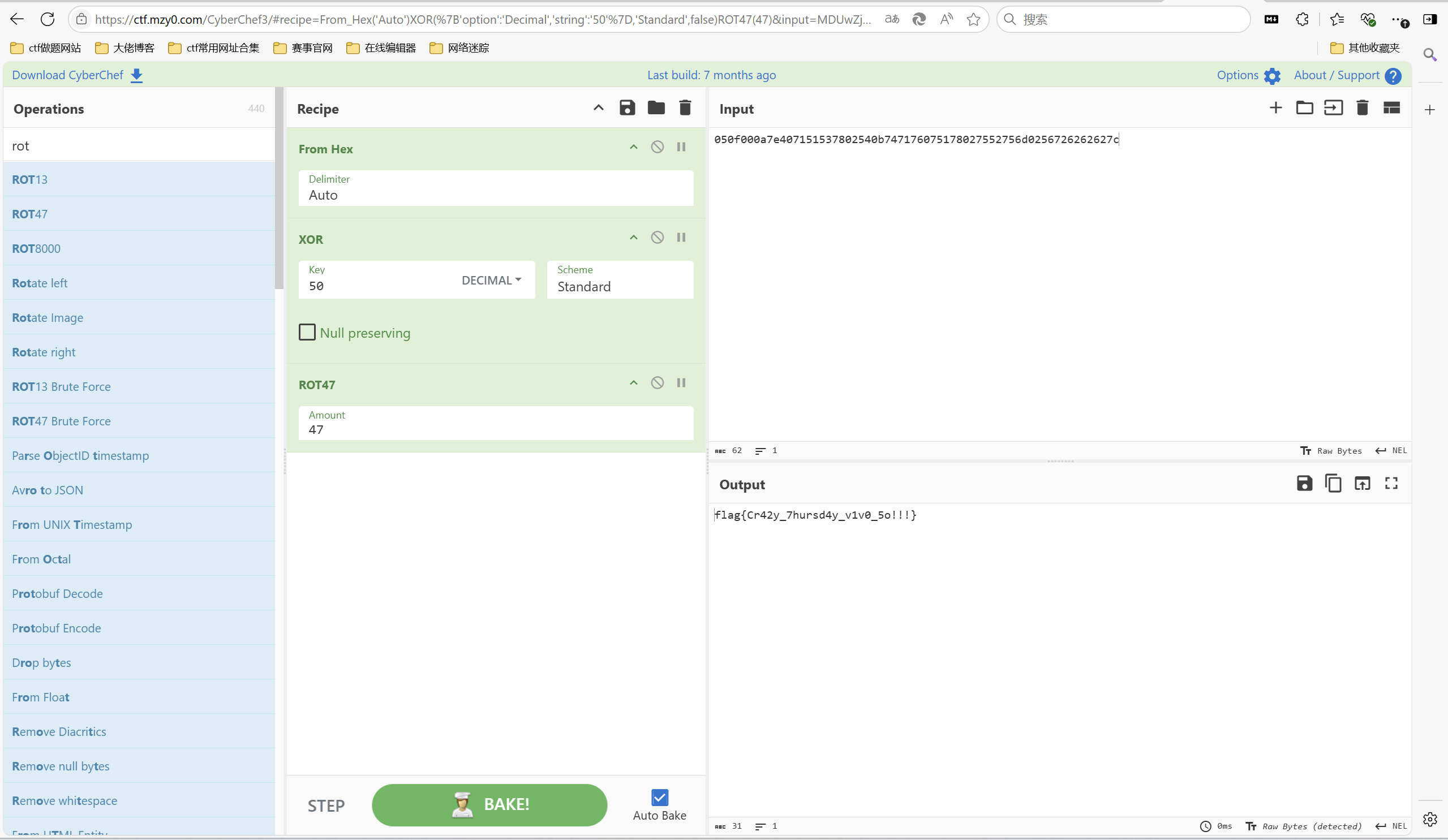
最后flag为
1 | flag{Cr42y_7hursd4y_v1v0_5o!!!} |
[WEEK1]what is m
1 | from Crypto.Util.number import bytes_to_long |
转字节
exp:
1 | from Crypto.Util.number import * |
运行得到flag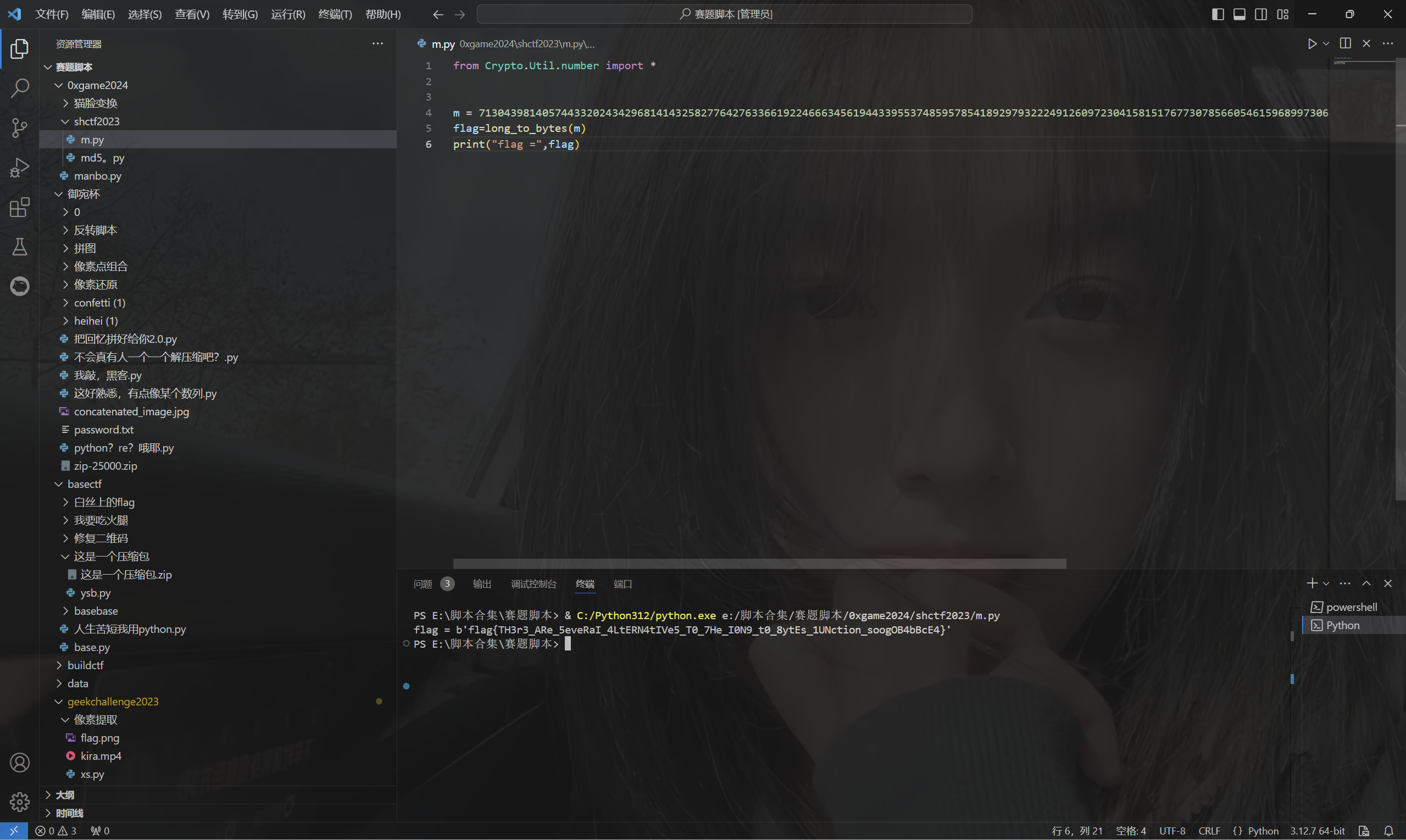
最后flag为
1 | flag{TH3r3_ARe_5eveRaI_4LtERN4tIVe5_T0_7He_I0N9_t0_8ytEs_1UNction_soogOB4bBcE4} |
[WEEK1]really_ez_rsa
1 | from Crypto.Util.number import getPrime, bytes_to_long |
rsa已知(p, q, e,c),求m题型
exp:
1 | import gmpy2 |
运行得到flag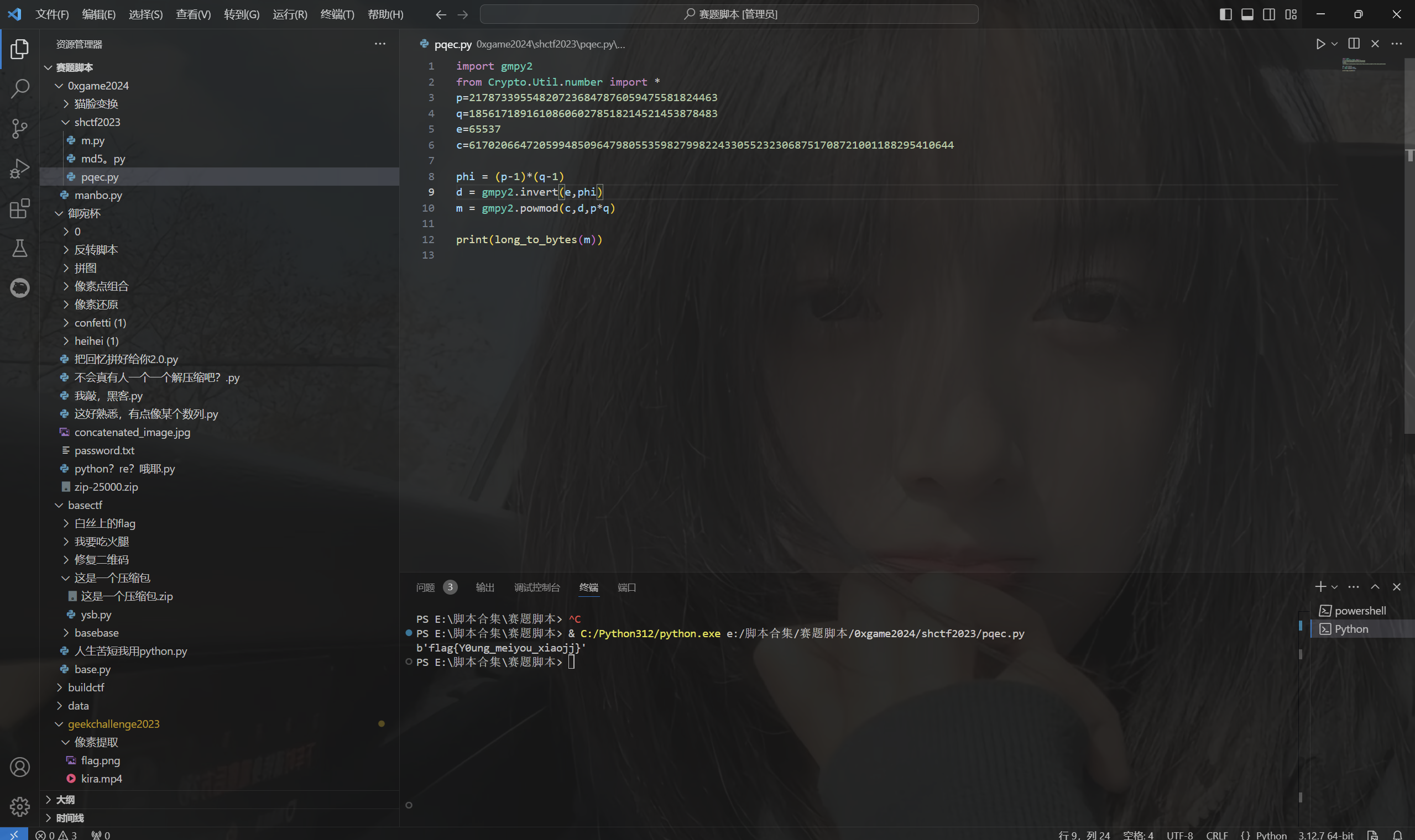
最后flag为
1 | flag{Y0ung_meiyou_xiaojj} |
[WEEK2]XOR
1 | n = 20810298530643139779725379335557687960281905096107101411585220918672653323875234344540342801651123667553812866458790076971583539529404583369246005781146655852295475940942005806084842620601383912513102861245275690036363402134681262533947475193408594967684453091957401932685922178406769578067946779033282889429596341714417295489842047781388337010440309434639274398589029236213499110100040841426995862849012466514170374143655264739023758914247116354182164550612494432327931655944868705959874670536031052370968354394583880324756639698871918124498442308334232127034553164826483441746719644515097123067550594588348951855987 |
已知n, p ^ q, e, c,直接高低位爆破
exp:
1 | import gmpy2 |
运行得到flag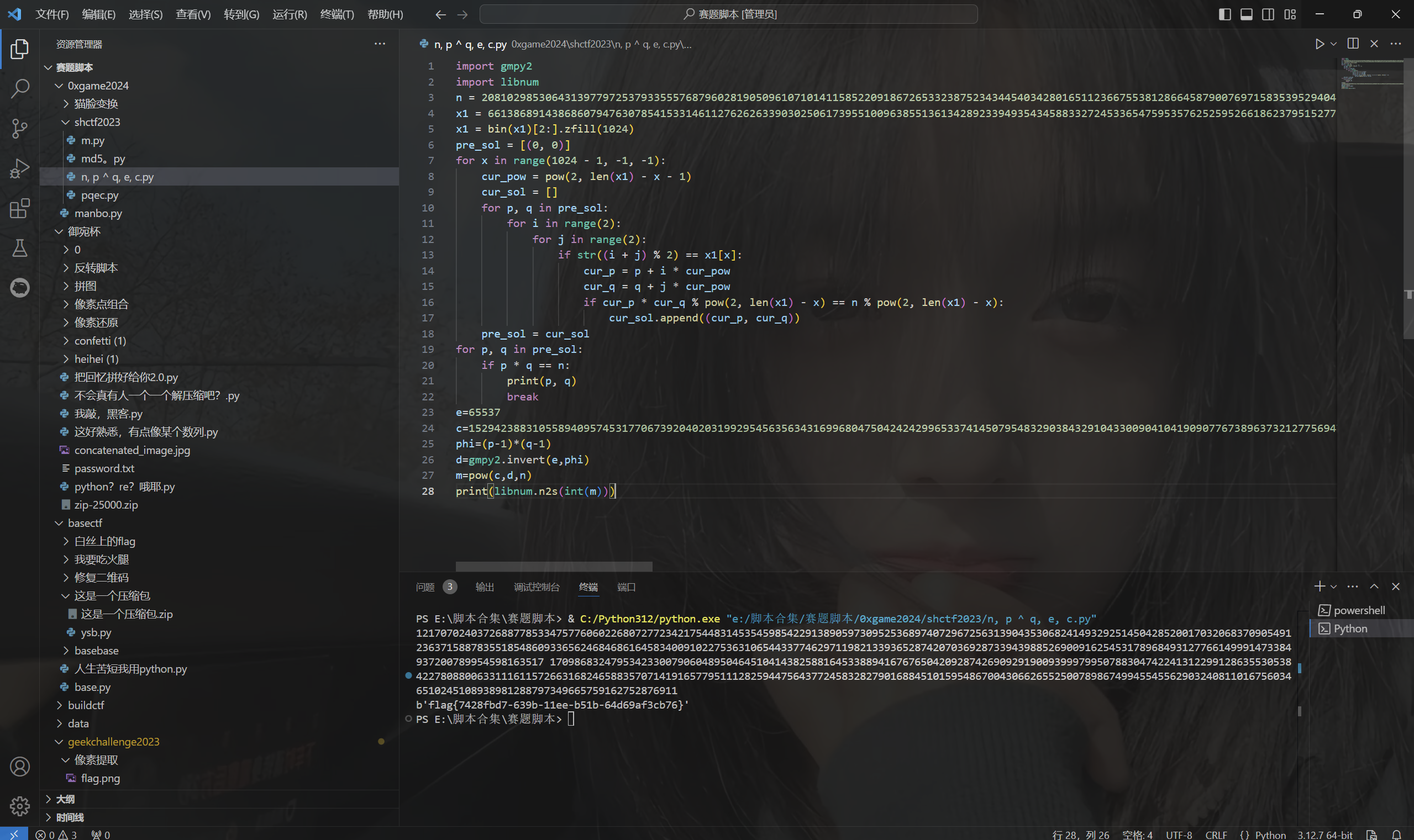
最后flag为
1 | flag{7428fbd7-639b-11ee-b51b-64d69af3cb76} |
[WEEK2]easymath
output.txt
1 | [288530505749272642500730917886204398531, 63547143998110685331032679758907988154, 15151206512028268617888756820805603406, 268092204209244869520724955865278855216, 261067075335188593563542448889694952077, 138067838531633886698552659065694918861, 201319433320428898153580935653793106657] |
task.py
1 | from Crypto.Util.number import * |
LCG,已知seed,但是不知道a,b,n
exp:
1 | from Crypto.Util.number import * |
运行得到flag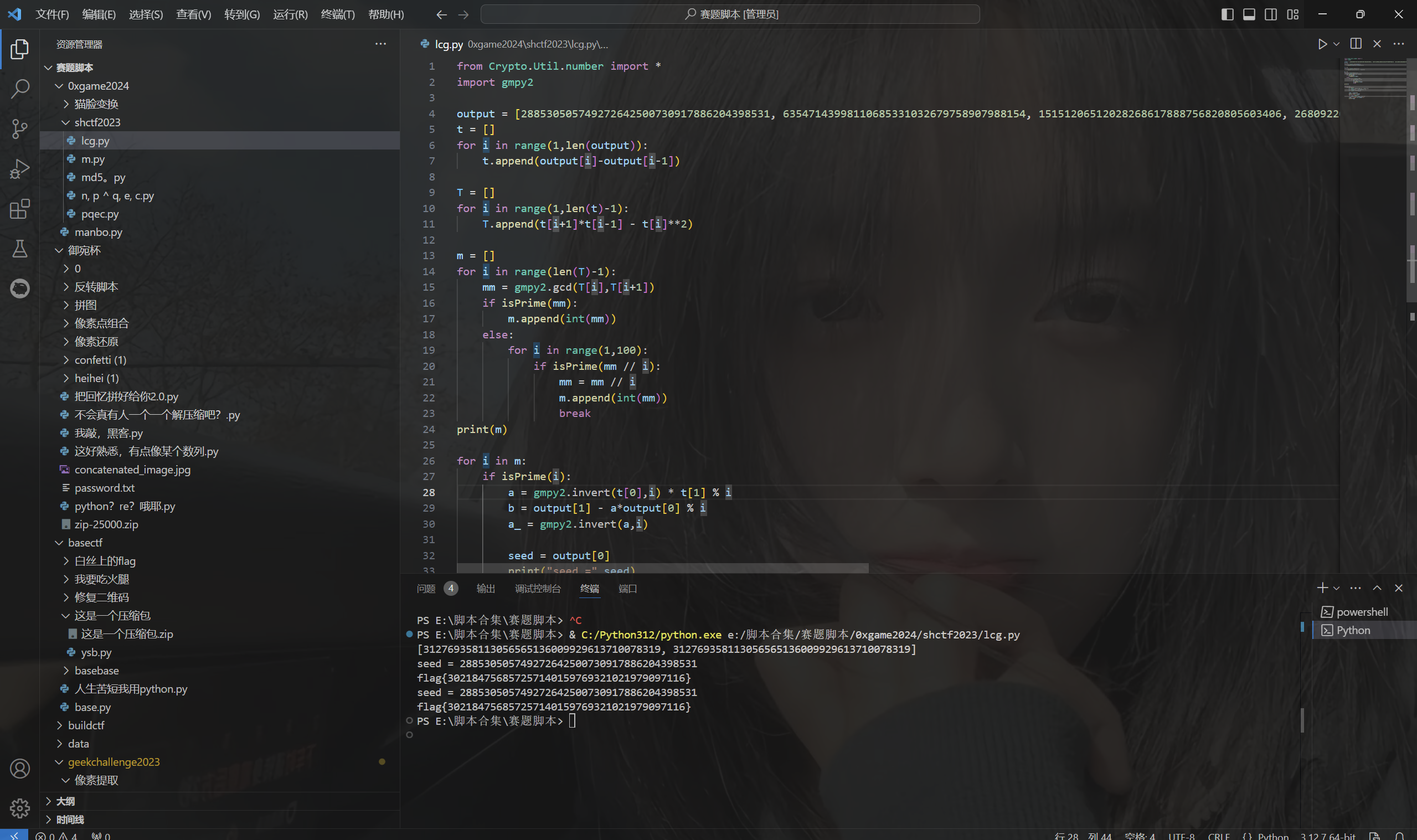
最后flag为
1 | flag{302184756857257140159769321021979097116} |
[WEEK2]ez_rsa
1 | # from flag import flag |
flag被分成两段进行加密,将第一段的n分解后发现n是由多个素因数相乘得出的,phi_n为所有素因数分别减一后相乘之后正常解RSA得出flag前半段,再采用共模攻击解出后半段拼接得出完整flag
exp:
1 | import libnum |
运行得到flag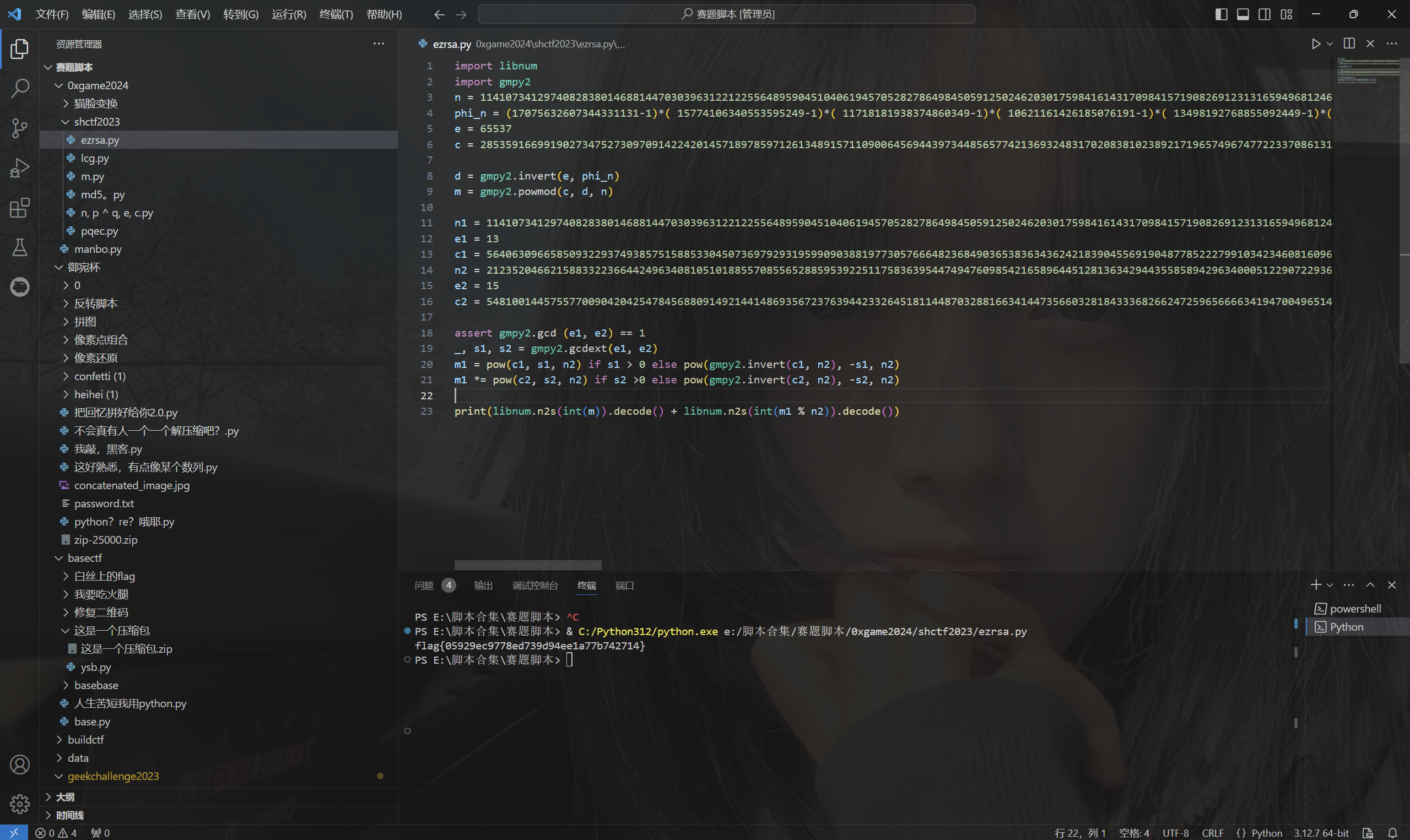
最后flag为
1 | flag{05929ec9778ed739d94ee1a77b742714} |
[WEEK2]e?
1 | p= 70724362259337647663584082414795381346569735601816096923682814277857463878289 |
e和ϕ(n)不互素
exp:
1 | import gmpy2 |
运行得到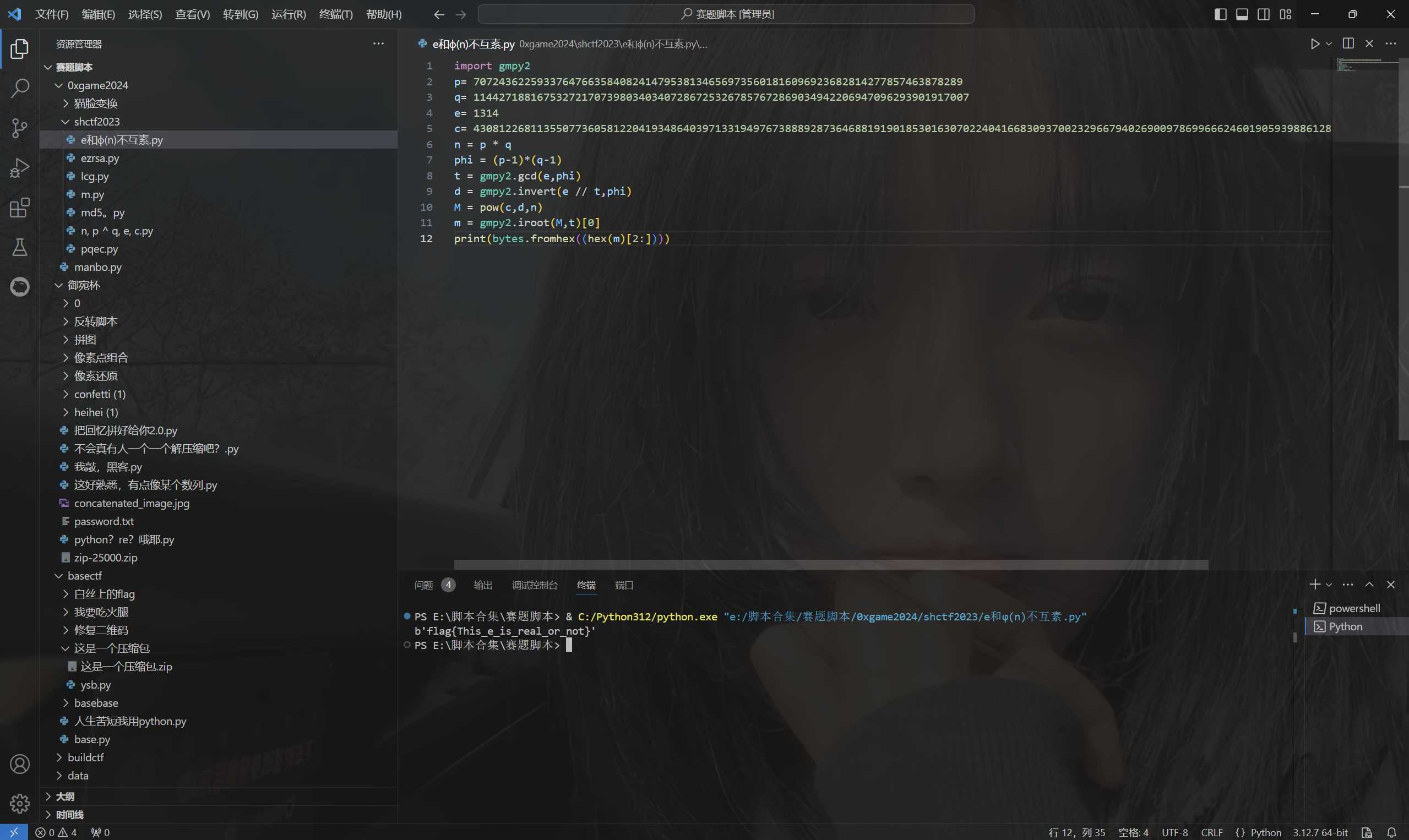
最后flag为
1 | flag{This_e_is_real_or_not} |
[WEEK2]factorizing_n
1 | n = 226515252384227990547287743140613580056836242860947832749754689048997071950972581790210817523352001702907675581567498443649554801433663166425134375454937126656357069687274036935331269594383360450823787099121079436459236734336130768046337169817940540921822023269188752420603975467384377614321048859304185067329741055517464271746238143742661897809442359331215501438861121047081117632626097939097519866099140569819965948998542652908170134545593659233229897003698175558888336706474178958535138595687148003367152624421106553412886263257022809480187410133186189435436294593588009551451899398811758511878324326255293307347560753524372663257044426744744426759970254203341706284024734042826158828749144322843934985927079504722440497388146240627249465363931951790326885478025237643 |
yafu分解后发现n为一个数的五次幂
exp:
1 | from Crypto.Util.number import * |
运行得到flag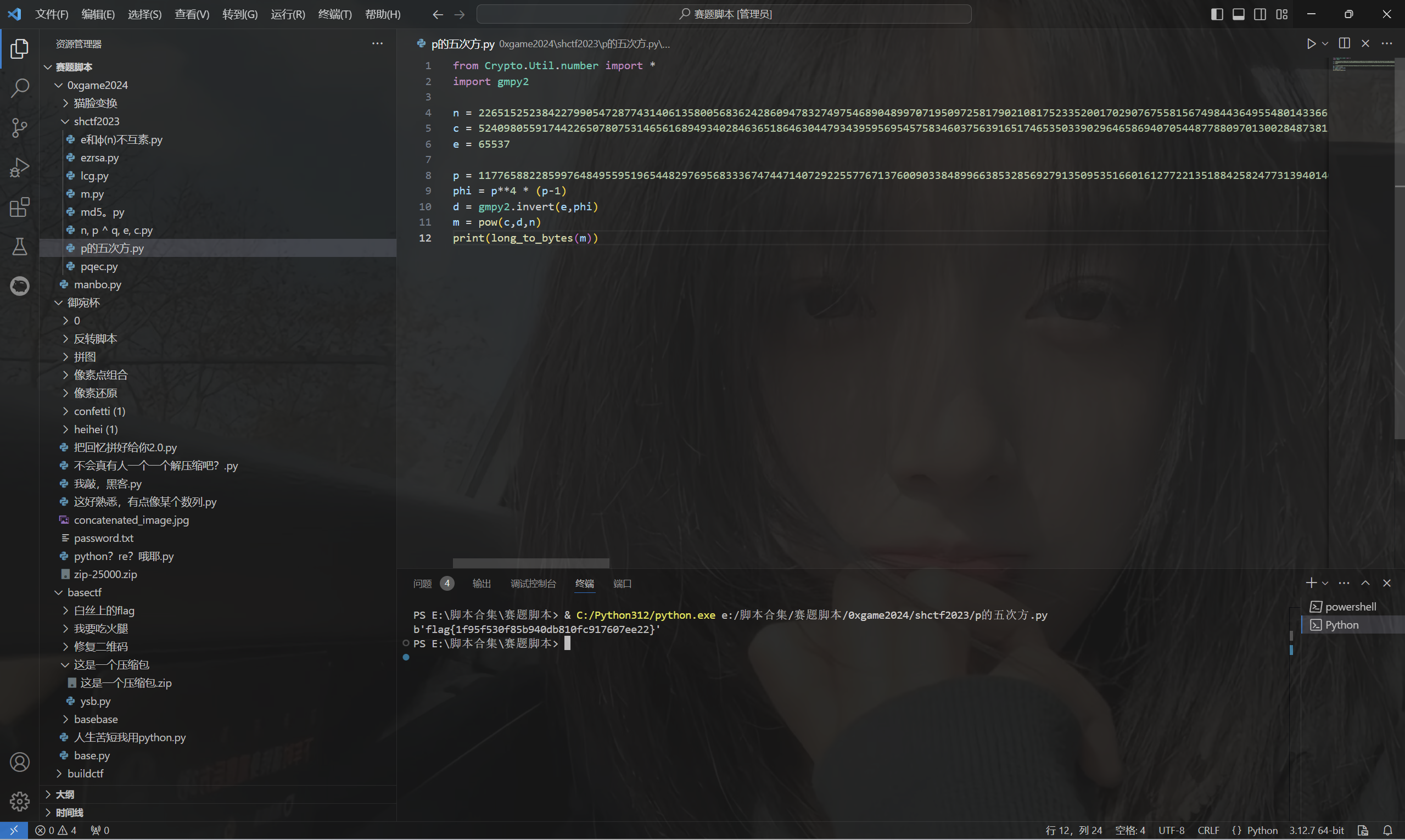
最后flag为
1 | flag{1f95f530f85b940db810fc917607ee22} |
[WEEK2]哈希猫
1 | import hashlib |
一堆hash,直接爆破
exp:
1 | import hashlib |
运行得到flag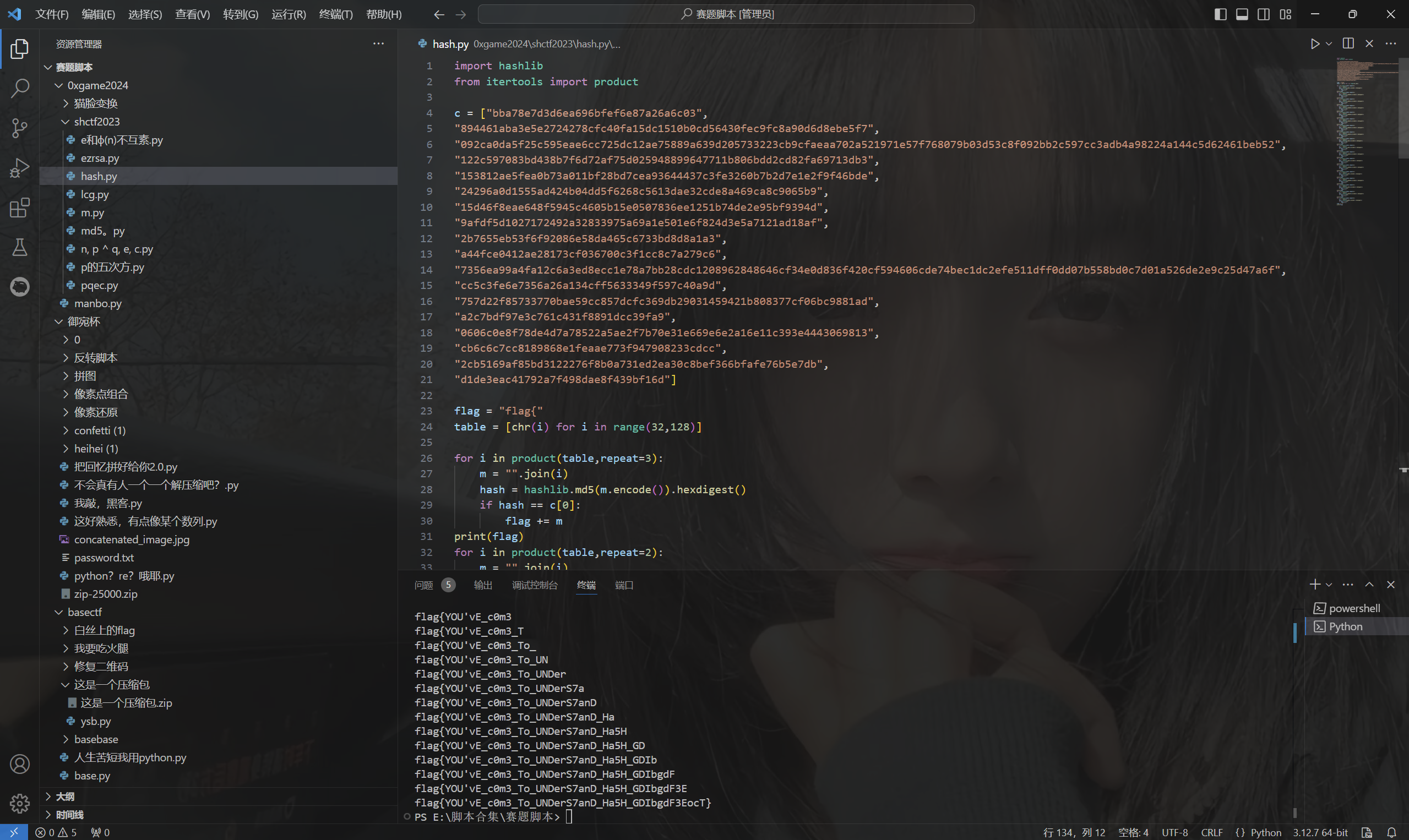
最后flag为
1 | flag{YOU'vE_c0m3_To_UNDerS7anD_Ha5H_GDIbgdF3EocT} |
[WEEK3]Classical Master
1 | import math |
频率分析:
在任何一种书面语言中,不同的字母或字母组合出现的频率各不相同。而且,对于以这种语言书写的任意一段文本,都具有大致相同的特征字母分布。比如,在英语中,字母E出现的频率很高,而X则出现得较少。类似地,ST、NG、TH,以及QU等双字母组合出现的频率非常高,NZ、QJ组合则极少。英语中出现频率最高的12个字母可以简记为“ETAOIN SHRDLU”
常见的频率分析的场景为破解替换密码。
普遍情况下26字母的频率分布如下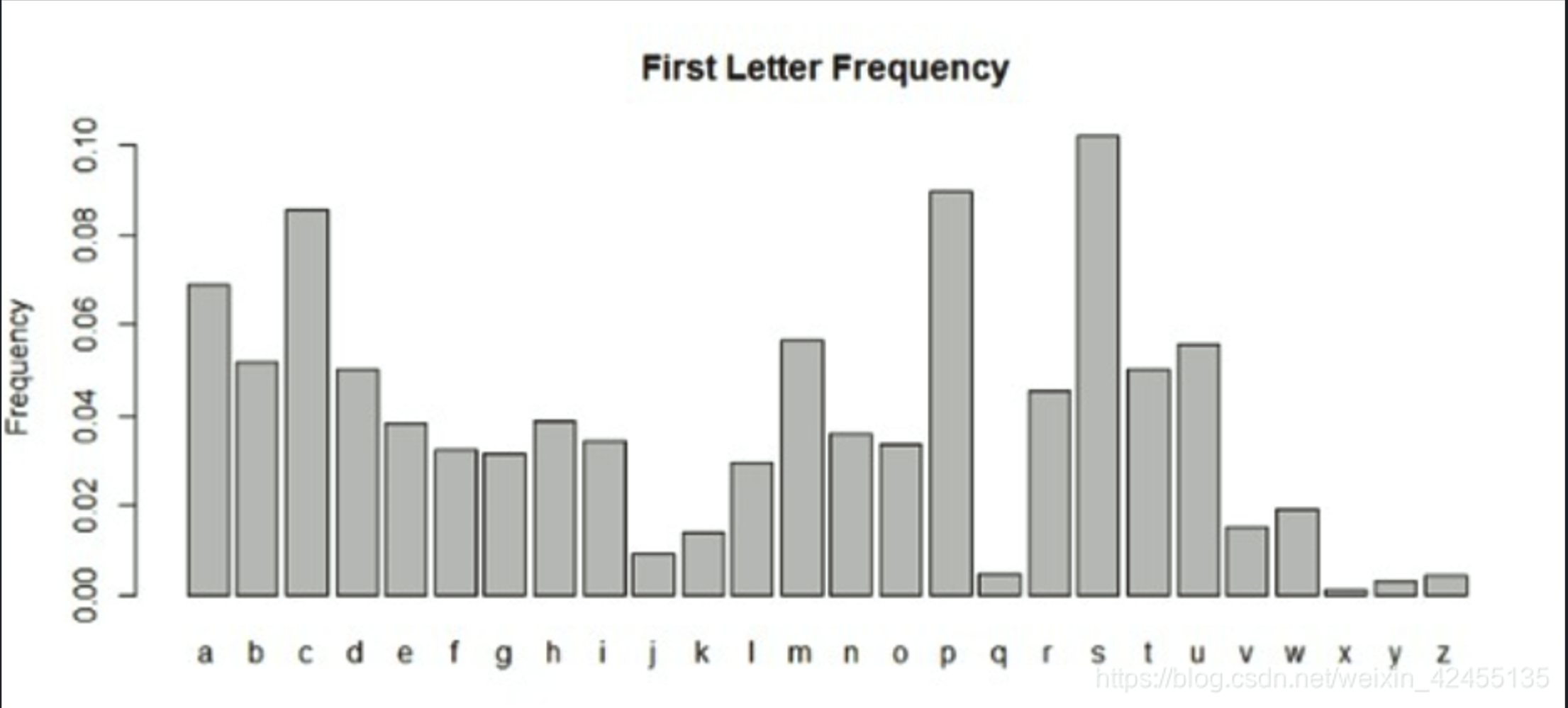
重合指数:
重合指数是衡量频率分布和均匀分布相似程度的度量。频率分析是经典密码分析里的重要工具,如果我们分别使用替换密码和维吉尼亚密码加密一段文本,我们可以发现维吉尼亚的频率分布更加平坦,而替换密码的频率分布更加“粗糙”。而重合指数正是将频率分布这种直观的视觉转换为数字表达式。
数学定义:
数学定义:其中f_i代表i字母的个数,N是字母总个数。
IC=\frac{\sum\limits_{i=A}^{i=Z}f_i(f_i-1)}{N(N-1)}
维基的解释:
重合指数又称重合概率,是指从一段密文种随机抽取两个字母,这两个字母相同的概率,已知一个完全随机的英文文本重合指数约为:0.0385;而有意义的英文文本重合指数CI约为0.065,从定义来看,肯定不是用用来破解凯撒,无论你怎么移动它的重合指数都不变。
拟重合指数exp:
1 | #去除非字母 |
运行得到flag
最后flag为
1 | flag{youaretherealmaster} |
[WEEK3]e=3
1 | from Crypto.Util.number import * |
多项式分解,把M当成多项式的未知数,那每个素数就是系数都是16比特的多项式.
N是三个素数的多项式相乘。因为54>16*3,所以可以恢复N的多项式的系数.
分解多项式不是难题,每个带入x=M就分解出p,q,r.
f(x) = a_{k-1}x^{k-1}+a_{k-2}x^{k-2}+…+a_1x^1+a_0
令x = M时,分别有p,q,r
所以N可以看作在M进制下的三个多项式相乘。用多项式分解可以得到三个多项式,再将M分别代入即可得到p,q,r
1 | if isPrime(prime) and (prime-1) % 3 == 0: |
再由于关键代码中prime-1 \mid 3 即p-1,q-1,r-1 与3都不互素,用有限域开根的办法,进行CRT的组合就能得到flag
p,q,r都可以表示为M进制,于是可以用多项式来分解N,因为e和phi不互素,所以用有限域开根,再用中国剩余定理
exp:
1 | from Crypto.Util.number import * |
运行得到flag
最后flag为
1 | flag{e1b7d2c2-e265-11eb-b693-98fa9b5bc5fe} |
[WEEK3]撤退!
1 | from Crypto.Util.number import * |
参考https://mp.weixin.qq.com/s/mrho95iae_jBHGxapEp2hg
首先解一个佩尔方程
这里直接暴力枚举求解
得到x,y
然后分析下enc1,enc2 由于n ^ 3超级大 不可能直接求离散对数吧。。。
注意到mod n ^ 3 考虑二项式展开
这样n的次数>=3的直接Mod意义下就消掉了
最后得到hb1,hb2的两个简单的<=2次的方程 考虑到模数3072bit
同余可以转等式 直接利用solve解方程即可(注意这里solve的用法 不是solve(…==0,x) 而是 solve(…,x))
exp:
1 | #sage |
运行得到flag
最后flag为
1 | flag{6c6eb27a-061b-baf4-4cae26-5a609588ce} |
[WEEK3]好好好!
1 | ***EGK*MAPZ**3TISLXYHW*B4*R*6CQV |
dp泄露,先还原m,然后爆破得到表,来解变表Base32
exp:
1 | import libnum |
运行得到flag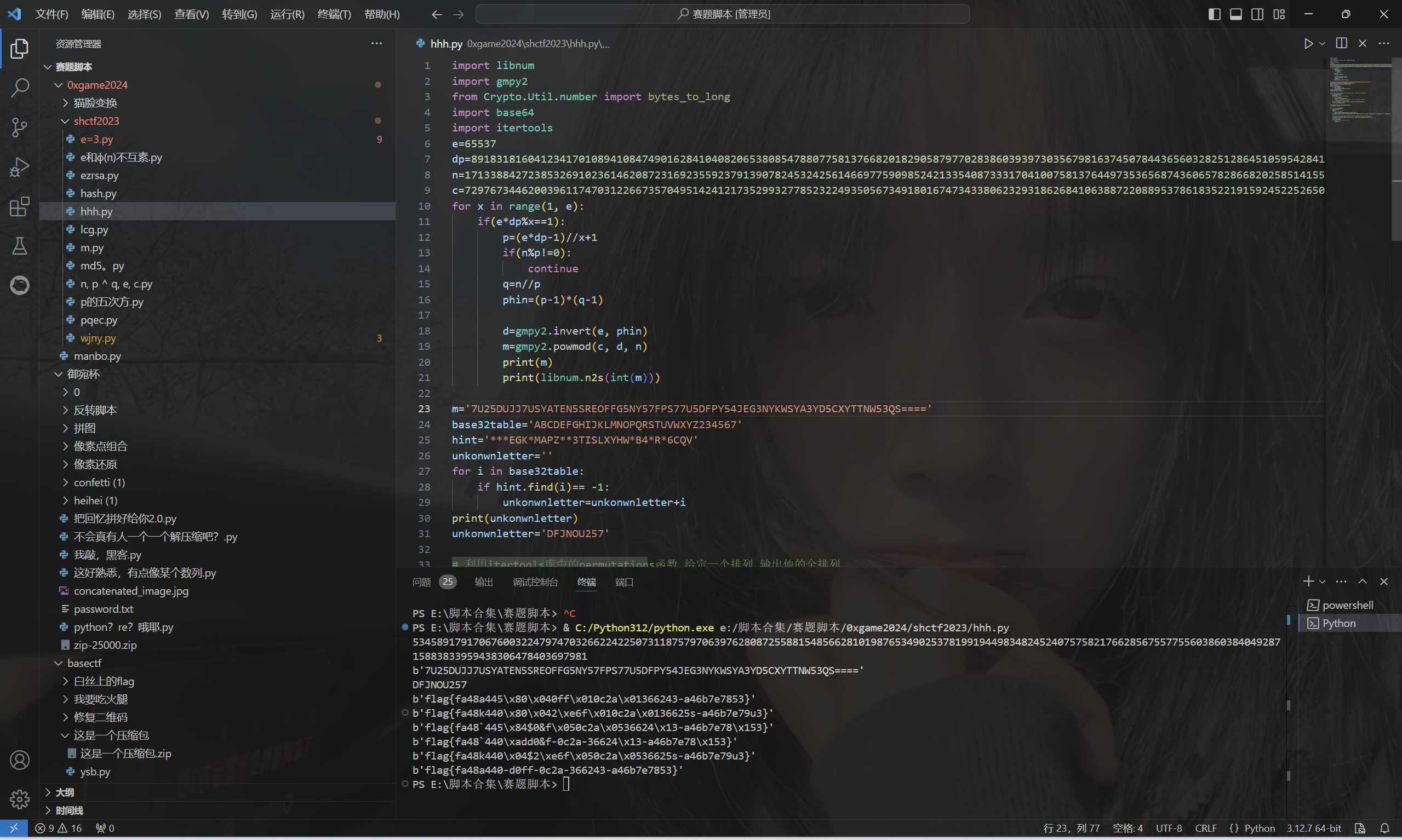
最后flag为
1 | flag{fa48a440-d0ff-0c2a-366243-a46b7e7853} |
[WEEK3]easyrsa
output.txt
1 | n1 = 105813626754830369767796578799226643889033227412658130226893708851110720416468059965713264658478299377654212587044247669928410442281831382577490105352633718272894531572352233211881056495752193201866649055622358234888531194346296702453105176147272971386928767457928148705433435309063146652094354833396307613911 |
task.py
1 | from Crypto.Util.number import * |
参考2023 贵阳大数据安全精英赛 — Crypto childrsa wp_贵州网络安全大赛childrsa-CSDN博客
两次rsa,可以根据leak1=(p2+q2)>>400求出得到p2,q2,然后求出leak2,再根据leak2求p1
exp:
1 | n1 = 105813626754830369767796578799226643889033227412658130226893708851110720416468059965713264658478299377654212587044247669928410442281831382577490105352633718272894531572352233211881056495752193201866649055622358234888531194346296702453105176147272971386928767457928148705433435309063146652094354833396307613911 |
运行得到flag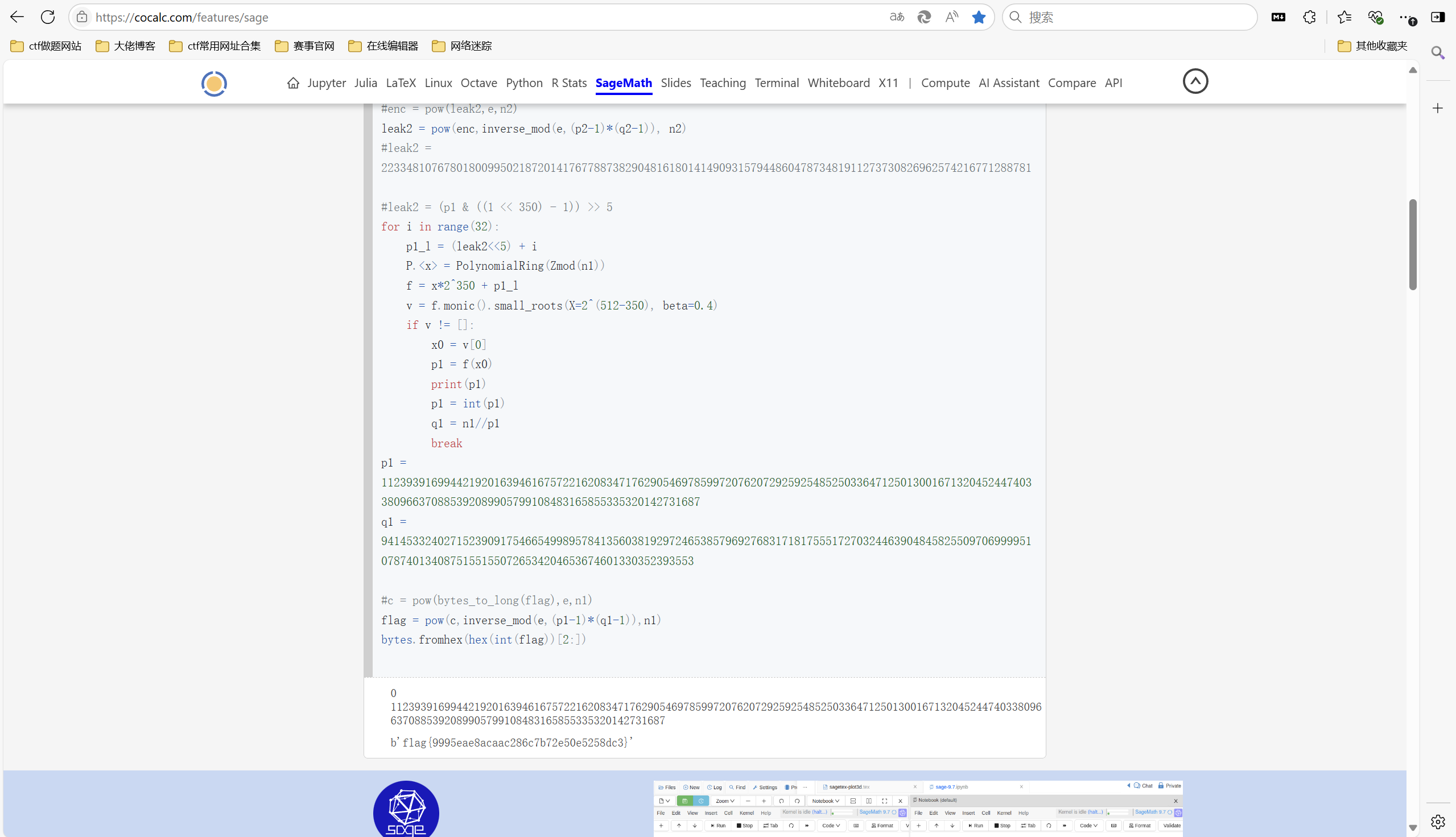
最后flag为
1 | flag{9995eae8acaac286c7b72e50e5258dc3} |
[WEEK3]ECC
1 | from Crypto.Util.number import bytes_to_long ,getPrime |
先解LCG得到椭圆曲线的参数,然后发现椭圆曲线的阶和p一样,运用SmartAttack
exp1:
1 | N = 1592666040773288237864960405116272477285413902052528659895355898525096633482218848317798659 |
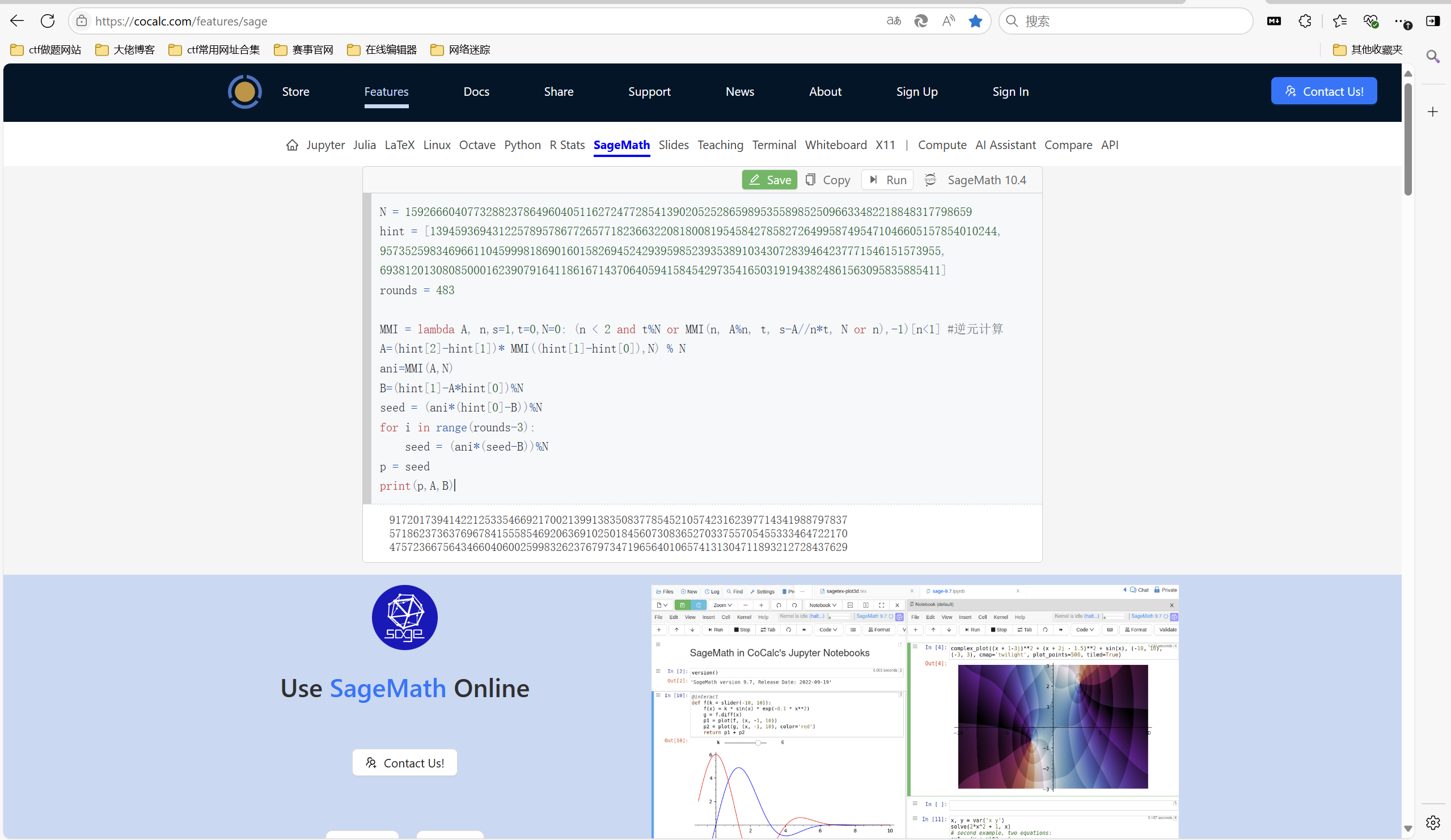
拿到p,发现 E.order()==p
椭圆曲线的阶和p相等
exp2:
1 | from Crypto.Util.number import long_to_bytes |
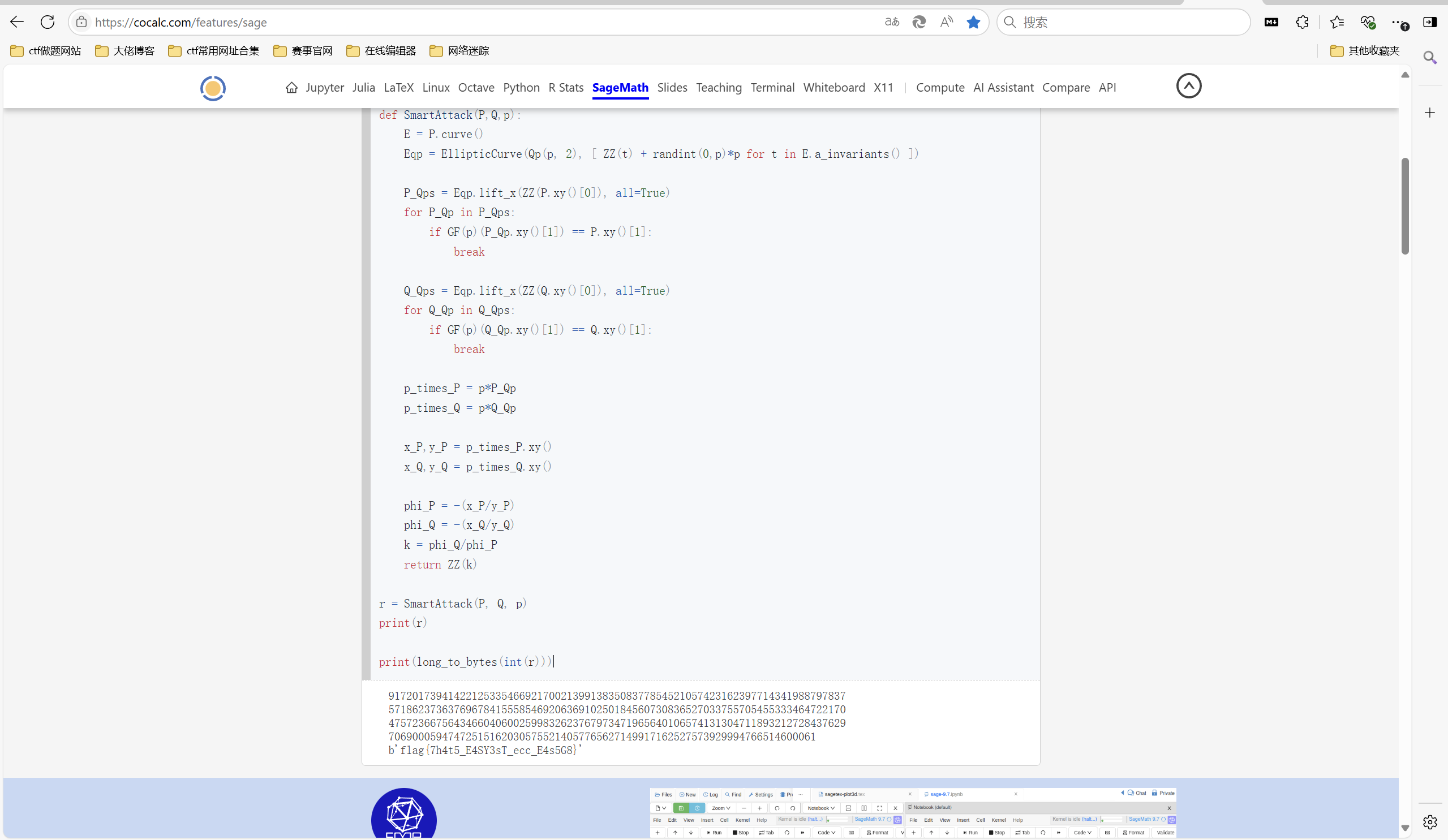
最后flag为
1 | flag{7h4t5_E4SY3sT_ecc_E4s5G8} |
SHCTF2024
[Week1] EzAES
题目描述:
1 | 最最简单的AES |
源码:
1 | from Crypto.Cipher import AES |
iv,key都给了直接解即可
exp:
1 | from Crypto.Cipher import AES |
运行得到flag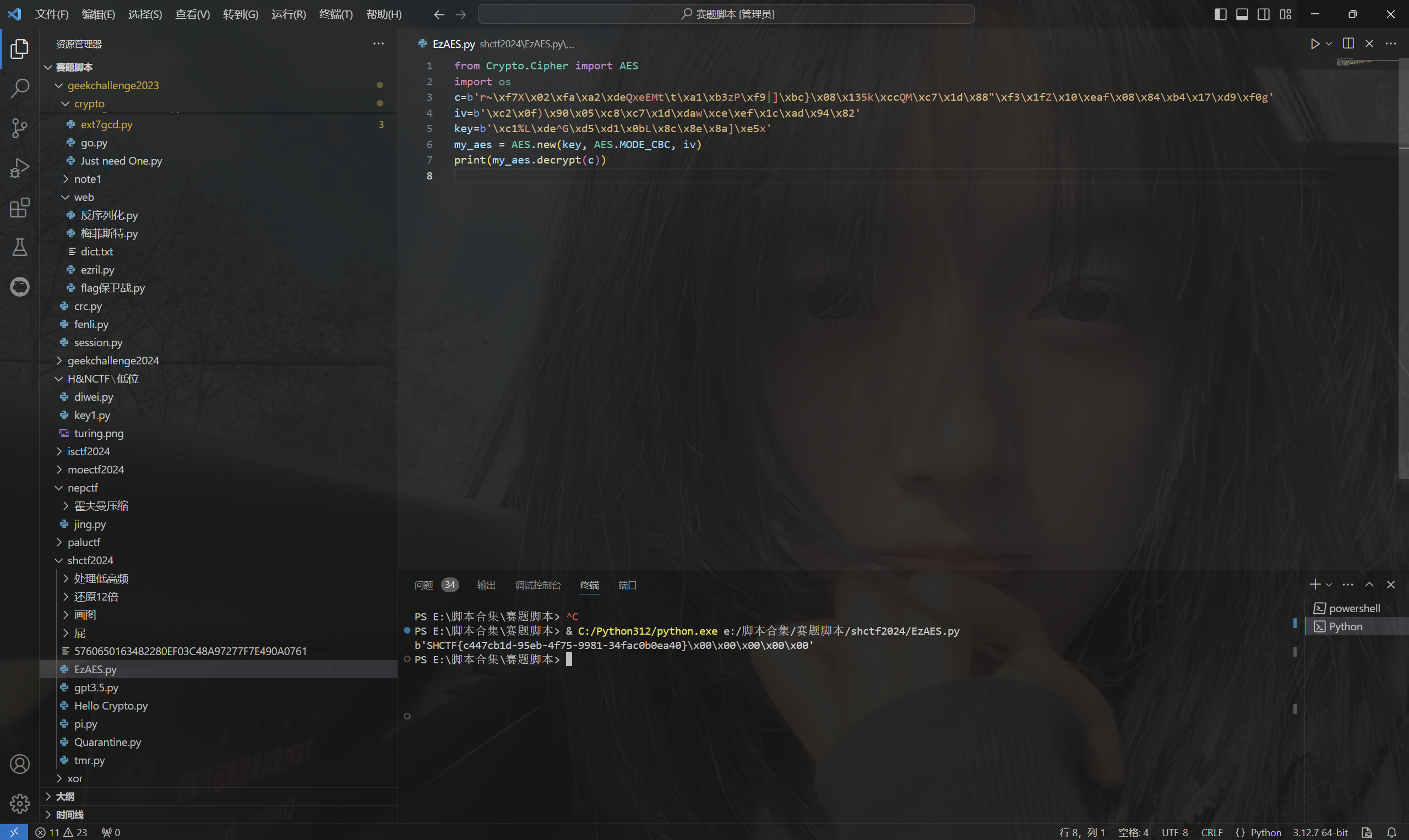
最后flag为
1 | SHCTF{c447cb1d-95eb-4f75-9981-34fac0b0ea40} |
[Week1] Hello Crypto
题目描述:
1 | 你好,现代密码学 |
源码:
1 | from Crypto.Util.number import bytes_to_long |
题目将bytes类型转换成了long,使用long_to_bytes()还原即可
exp:
1 | from Crypto.Util.number import * |
运行得到flag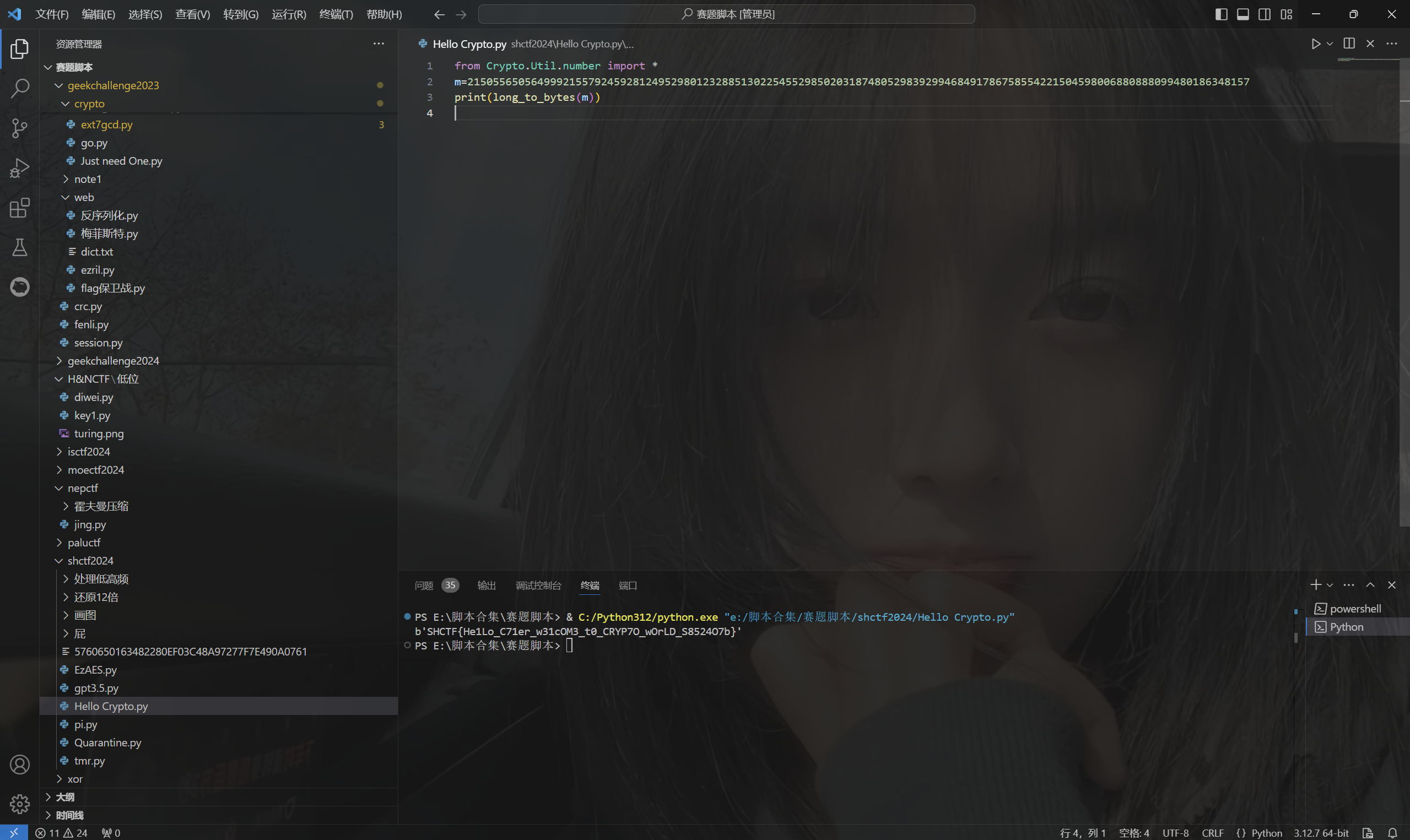
最后flag为
1 | SHCTF{He1Lo_C71er_w31cOM3_t0_CRYP7O_wOrLD_S8524O7b} |
[Week1] baby_mod
题目描述:
1 | 模 = mod |
源码:
1 | from Crypto.Util.number import * |
mp的位数很短,可以直接爆破,然后简单通过逆元运算还原一下p,q,最后解rsa即可
exp:
1 | c = 65265123447008258739823881253712618855743207785592071810644071874471454798965431864181558270515969975401779411159259620667145535502782388827453948759536453090157143513842262984080955436790285942593808080674810671659937071774640340301058624158681806442296843209117027874540870493389811029485723774603940459931 |
运行得到flag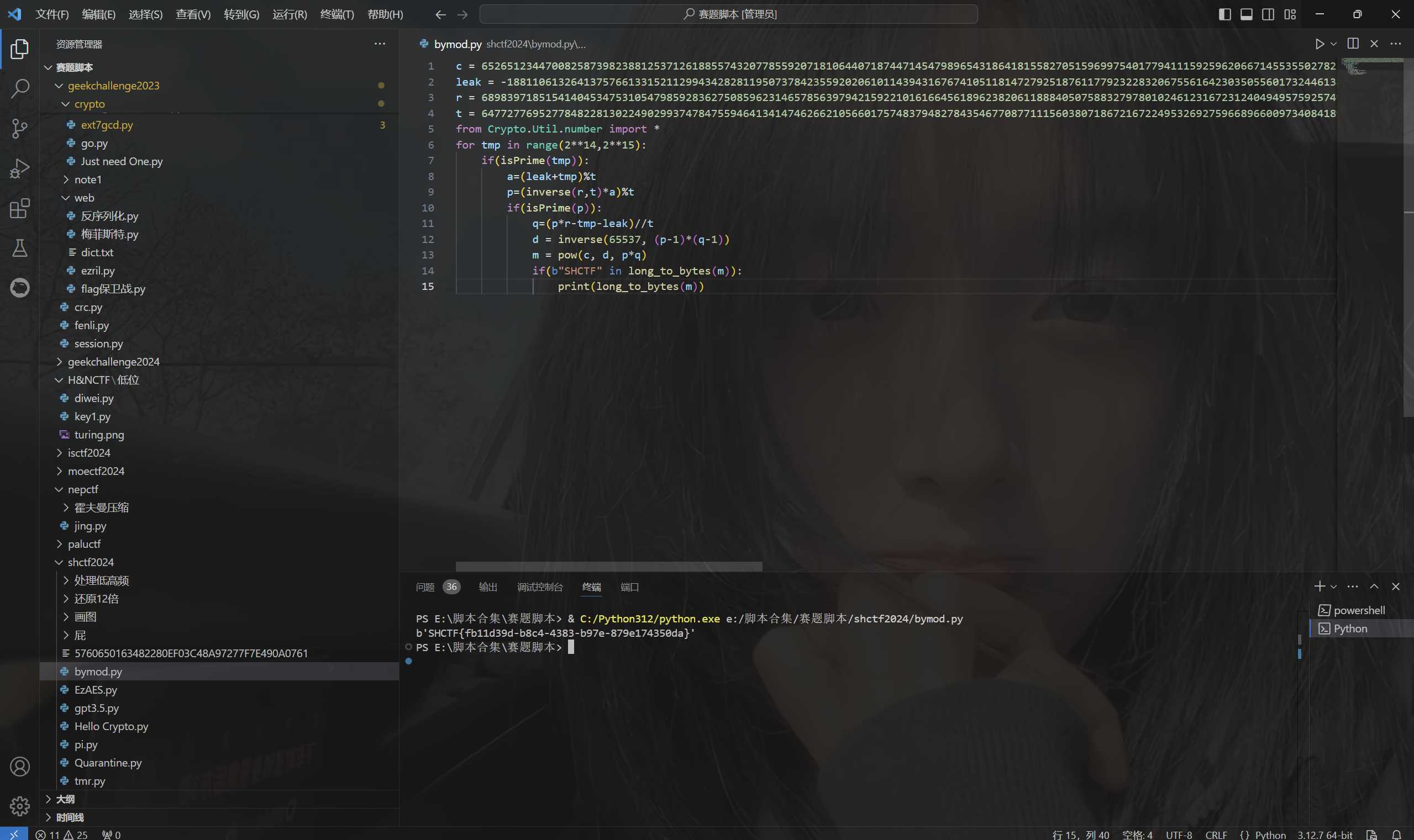
最后flag为
1 | SHCTF{fb11d39d-b8c4-4383-b97e-879e174350da} |
[Week1] d_known
题目描述:
1 | I have already given d |
源码:
1 | from Crypto.Util.number import * |
给了d,e没有给n,我们可以通过式子e*d=kphi+1去爆破k,然后计算p,q从而恢复n,phi在2048位左右,ed-1在2062位左右,所以k在14位左右
exp:
1 | c = 13998366132734013319249048018499721727403050055254830737165179815983174285094393811325317317707128169153747434539118667623037019064533046594022573065875581294785385142093123366582995660562519940300917436620199974944002032196285634314609637977477434533746886235396111536255895390881412677753832625863390895836662350922697007715599509322861755480647929903940260628645583640152138179517885654751583490965972388372271554280530740511905338458340643029412576307967139635209283971616883255921829012138299312649474227584899470833990216120417712813771473123864504615899719024784578351759126535133249810557879432468662111246756 |
运行得到flag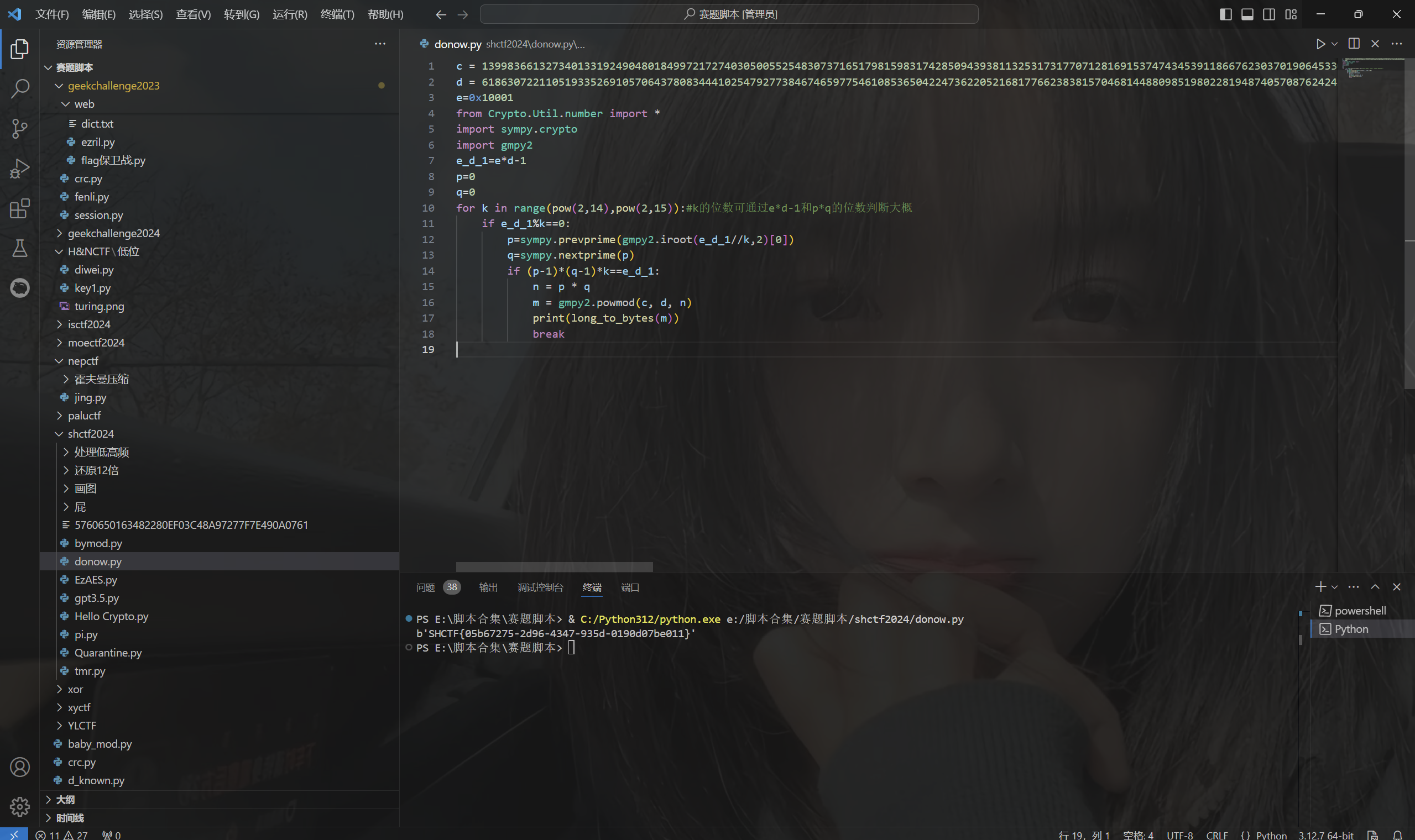
最后flag为
1 | SHCTF{05b67275-2d96-4347-935d-0190d07be011} |
[Week1] factor
题目描述:
1 | factor and combination |
源码:
1 | from Crypto.Util.number import * |
yahu可以分解N,然后调用函数排列组合一下n的所有情况解rsa即可
exp:
1 | c = 80038347277707557882787621949903452127505520309886916983104635131036184133624980068763353920983104291651397984336218086685818505948467 |
运行得到flag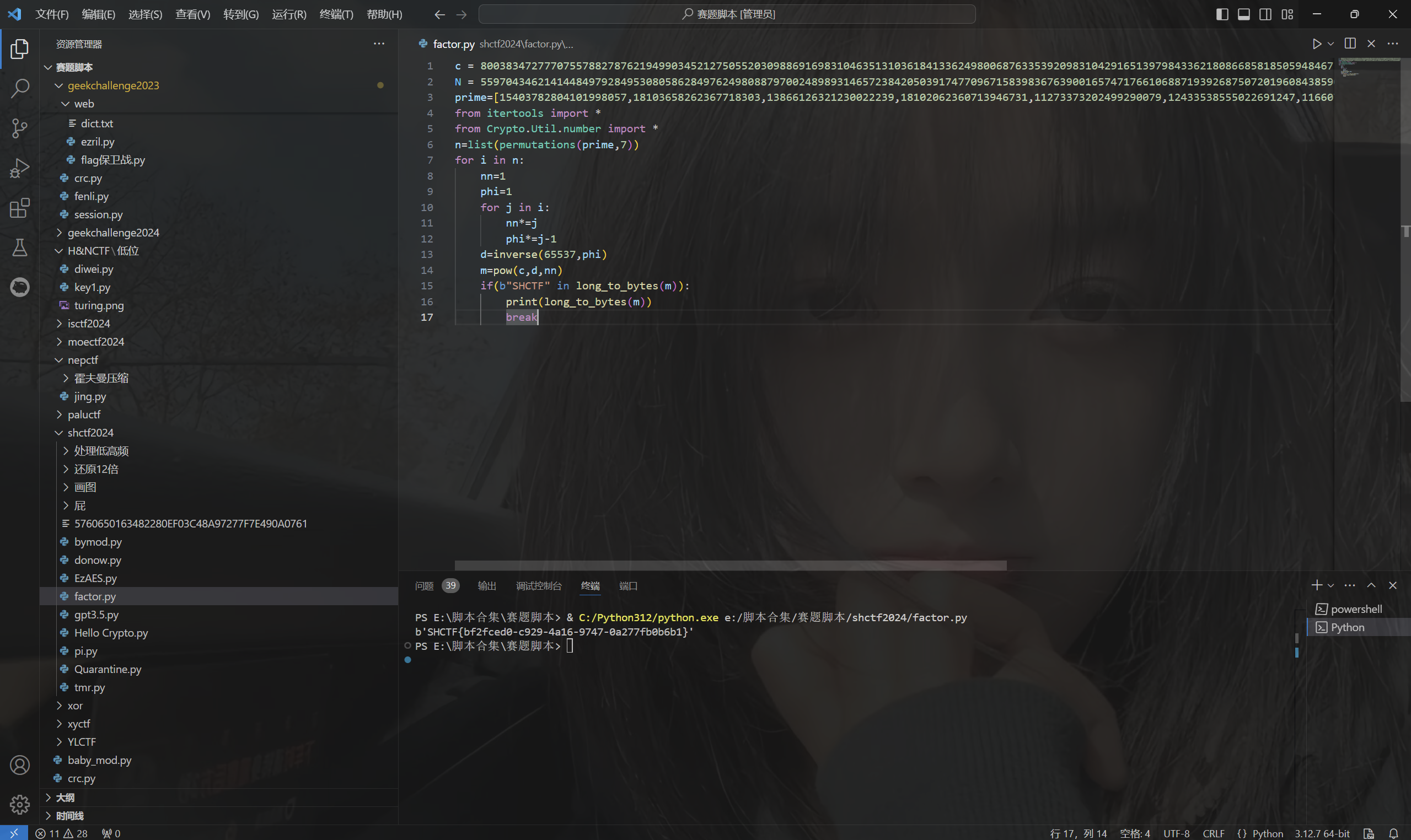
最后flag为
1 | SHCTF{bf2fced0-c929-4a16-9747-0a277fb0b6b1} |
[Week2] E&R
题目描述:
1 | ECC and RSA |
源码:
1 | #sage |
参考https://tangcuxiaojikuai.xyz/post/342113ee.html
「已知条件:」
- p 与 q 的反方向二进制的异或值,共256bit,记为pxorq
「搜索方式:」
- 从两端向中间搜索
- 每一次搜索,需利用当前 pxorq 两端的bit位。这是因为,pxorq 的当前最高位对应p的最高位及q的最低位,pxorq 的当前最低位对应p的最低位及q的最高位 (其中最高、最低均是对于当前搜索而言)
- 如果当前需搜索的最高位为”1”,则对应两种可能:p该位为1,q对应低位为0;p该位为0,q对应低位为1。剩下依此类推
「剪枝条件:」
- 将p、q未搜索到的位全填0,乘积应小于n
- 将p、q未搜索到的位全填1,乘积应大于n
- p、q 低 k 位乘积再取低 k 位,应与 n 的低 k 位相同
exp:
1 | from Crypto.Util.number import * |
运行得到
第二部分是ECC,曲线在模n上的阶不好直接算,而n = pq,那么我们可以分别构建在模p和模q上的曲线,然后分别计算其阶,进而得到曲线在模n上的阶,接下来就计算出e对于曲线的逆元求出点G,其横坐标即为flag部分
exp:
1 | from Crypto.Util.number import * |
运行得到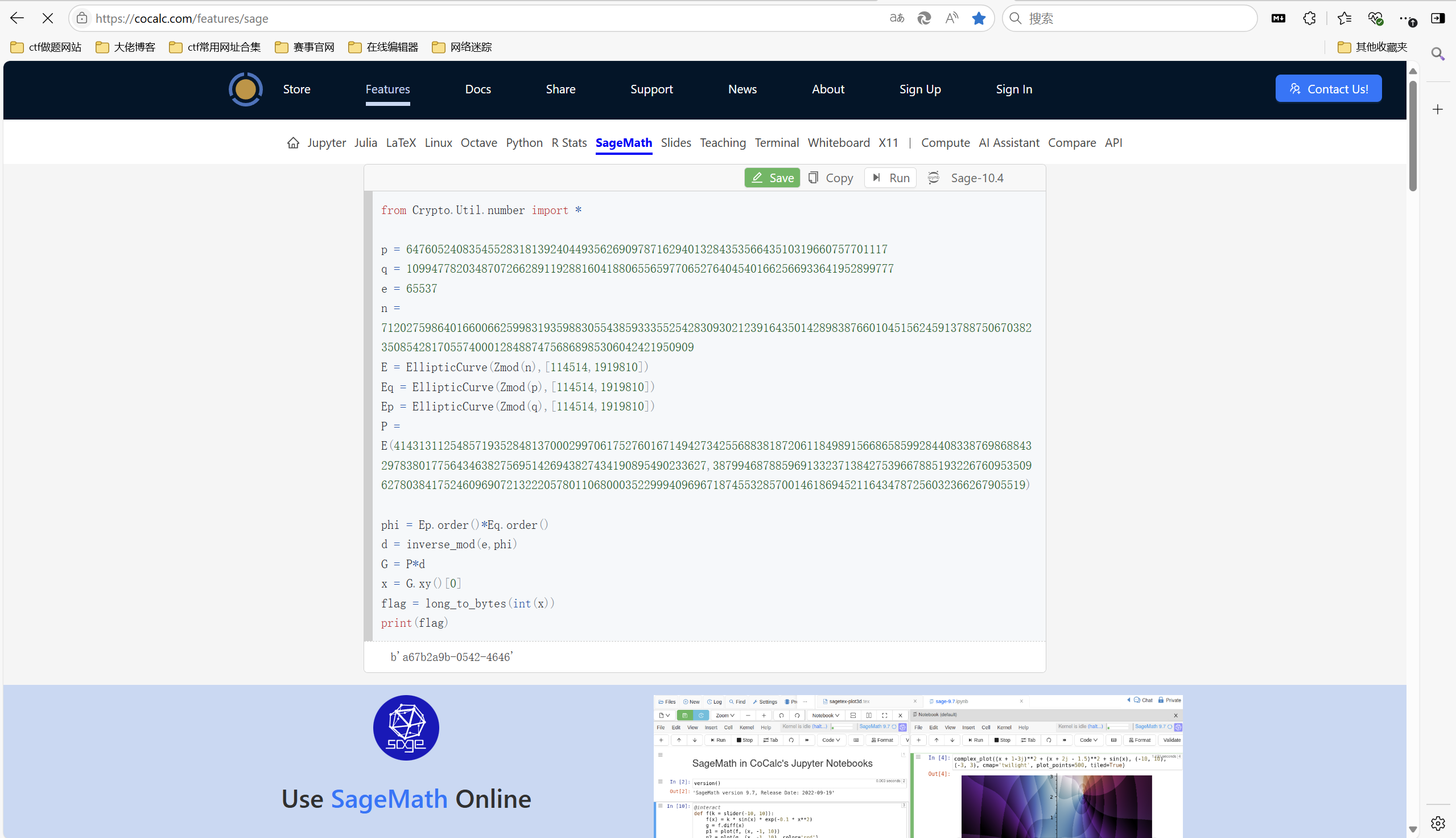
最后flag为
1 | SHCTF{a67b2a9b-0542-4646-908f-7c002c687387} |
[Week2] pading
题目描述:
1 | pading |
源码:
1 | from Crypto.Util.number import * |
cooper求解
exp:
1 | import libnum |
运行得到flag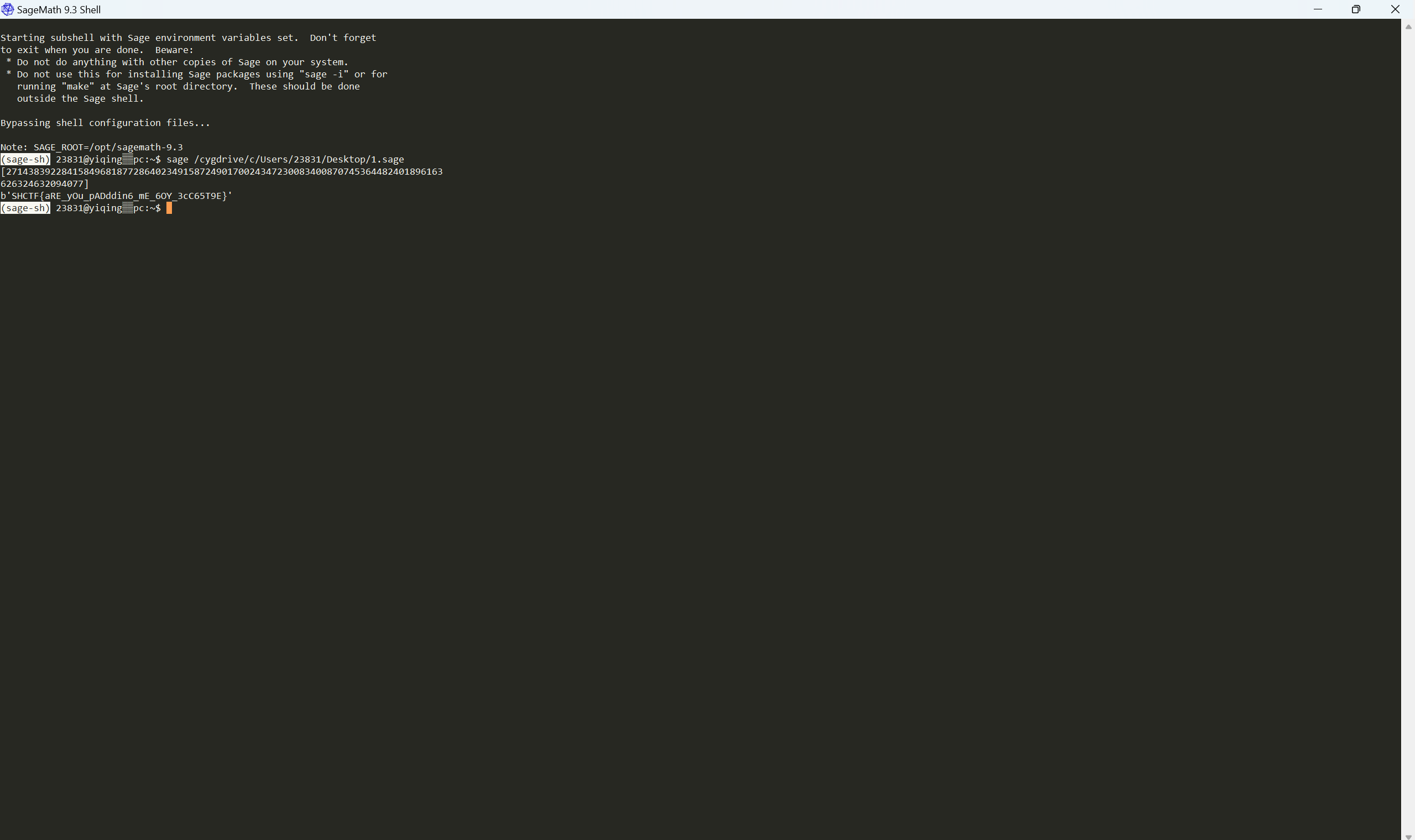
最后flag为
1 | SHCTF{aRE_yOu_pADddin6_mE_6OY_3cC65T9E} |
[Week2] worde很大
题目描述:
1 | 坏了,遍历不了了 |
源码:
1 | import gmpy2 |
dp泄露,e很大,使用费马小定理
exp:
1 | from Crypto.Util.number import * |
运行得到flag
最后flag为
1 | SHCTF{w0Rd_E_yoU_dlAN_DA_512AdE} |
[Week2] 魔鬼的步伐
题目描述:
1 | 在这光滑的地上摩擦,摩擦是魔鬼的步伐 |
源码:
1 |
|
p-1光滑
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到flag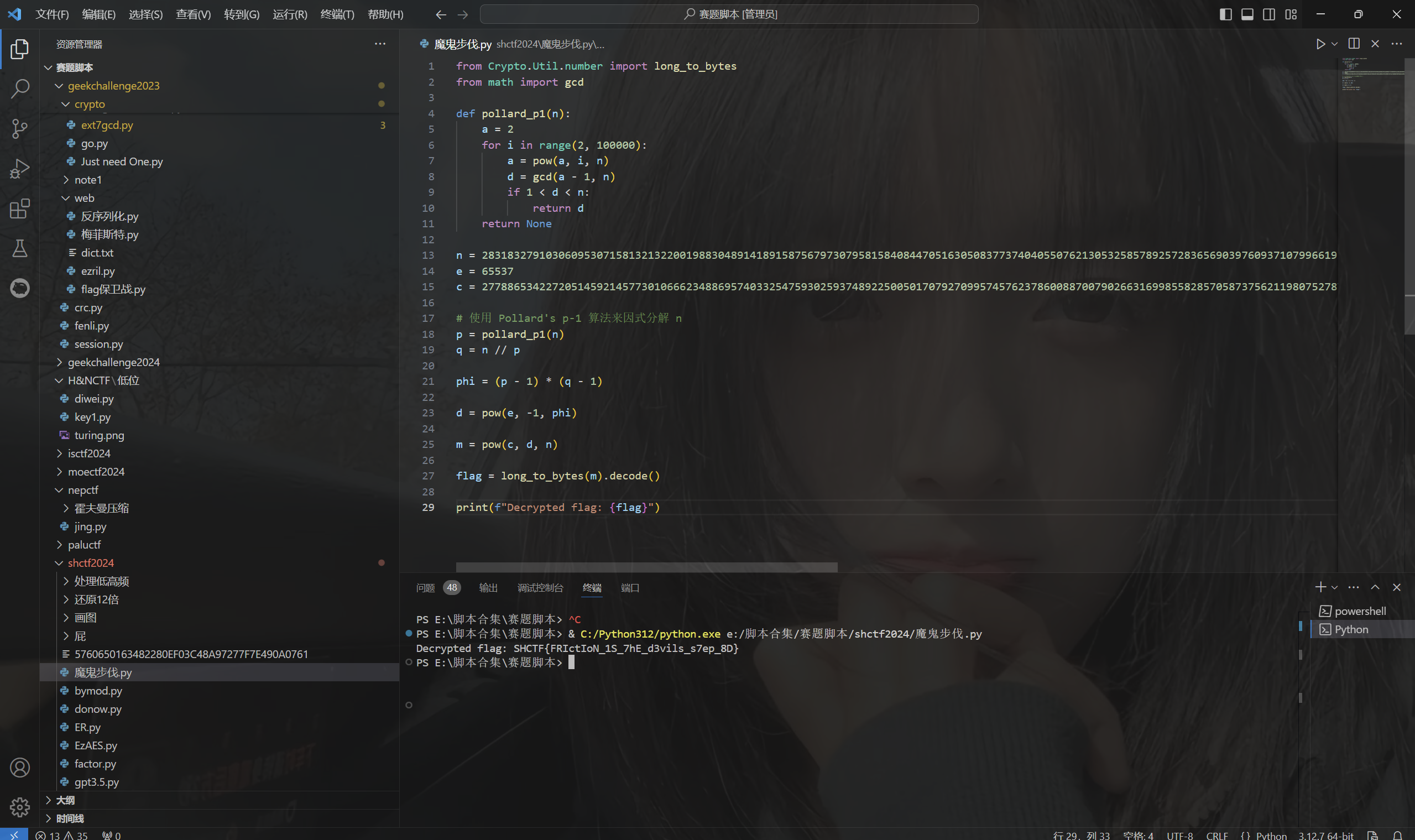
最后flag为
1 | SHCTF{FRIctIoN_1S_7hE_d3vils_s7ep_8D} |
[Week2]ezECC
题目描述:
1 | ecc简单哎 |
data.txt
1 | p = 9799485259524549113003780400336995829253375211044694607315372450399356814285244762186468904824132005209991983177601498069896166228214442123763065076327679 |
ezECC.py
1 | from Crypto.Util.number import * |
已知A1和C两个在曲线上的点和曲线的p值,根据曲线
y^2=x^3+ax+b mod p
两个式子相减求得a和b值。构造曲线,由于C = M+A2,且A2 = k*A1,A1和k值都已知。M = C-k*A1求得M的值。由于M的x坐标是明文m的下一个素数,爆破即可:
exp:
1 | from Crypto.Util.number import * |
运行得到flag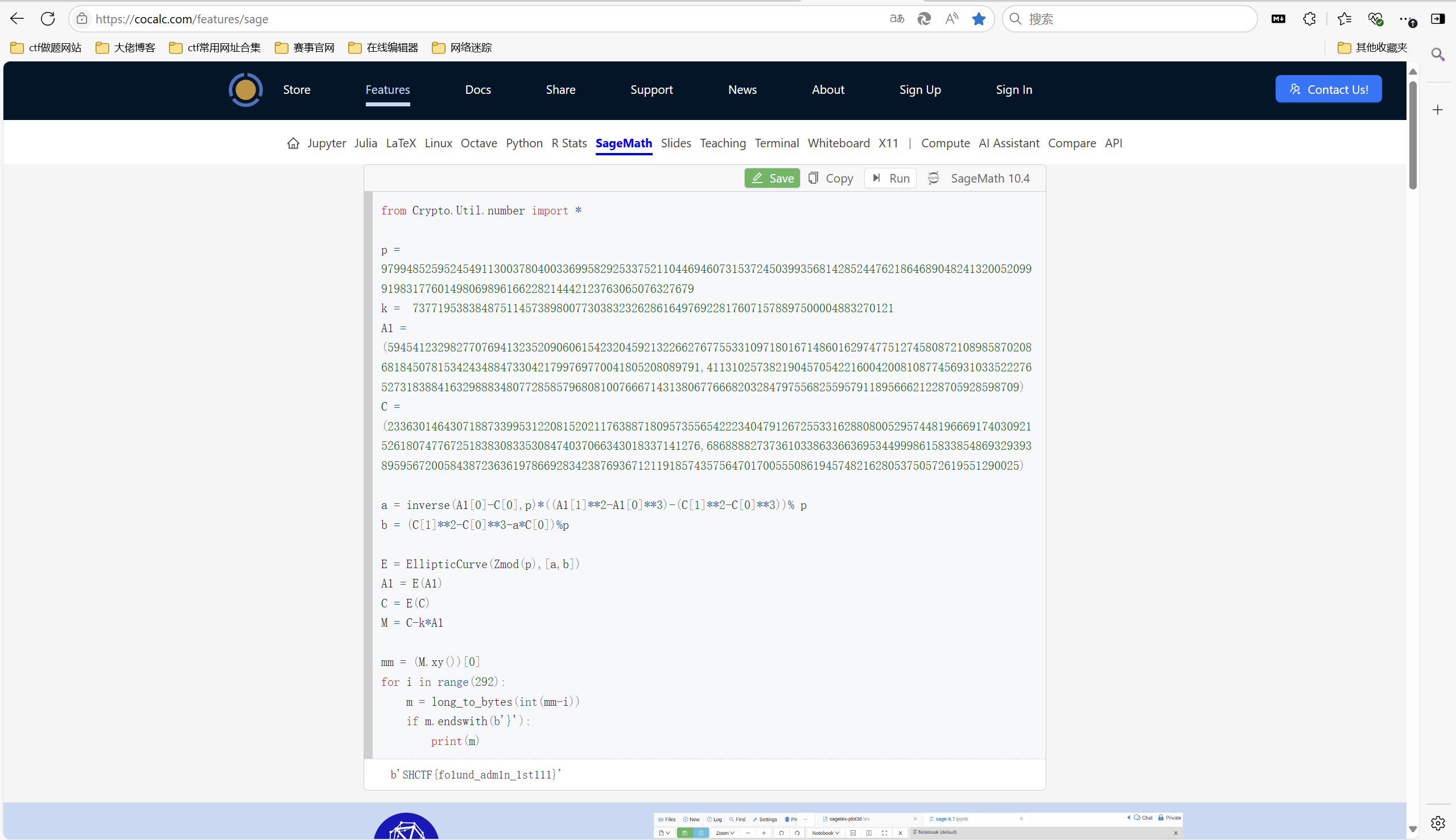
最后flag为
1 | SHCTF{fo1und_adm1n_1st111} |
[Week3] Approximate_n
题目描述:
1 | 知道n相似值,能怎么办呢 |
源码:
1 | from Crypto.Util.number import * |
参考https://eprint.iacr.org/2016/215.pdf
AGCD问题(The Approximate Common Divisor Problem, 近似最大公约数问题)
1 | 第一部分中返回了三个AGCD值,此时我们可以考虑使用传统的AGCD问题中的SDA丢番图格进行攻击 |
第二部分知道N2和N2_reveal的值,PACD问题。通过论文 Passive SSH Key Compromise via Lattices,我们可以知道PACD问题的解决手段,选取参数Qj(x)Qj(x)

exp:
1 | from Crypto.Util.number import * |
最后flag为
1 | SHCTF{APPROxiMaTE_n_H4PpY_7hE_NEW_GGag_2_Da} |
[Week3] Lattice
源码:
1 | import gmpy2 |
hint = xm^-1 mod n直接用hint和n造格 mhint = x + kn
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到flag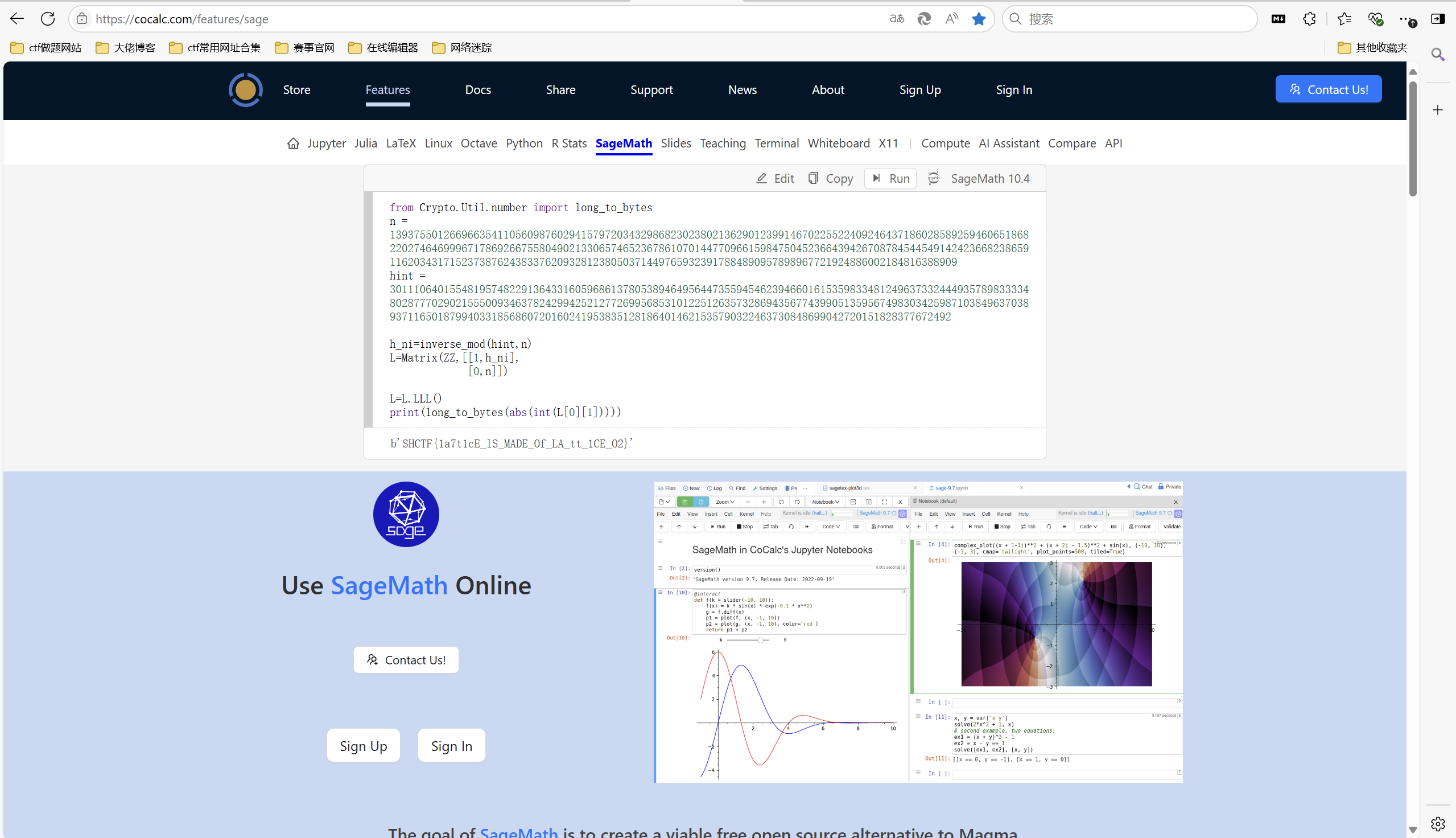
最后flag为
1 | SHCTF{1a7t1cE_lS_MADE_Of_LA_tt_1CE_O2} |
[Week3] Shamir
源码:
1 | from Crypto.Util.number import getPrime,bytes_to_long |
hamir门限,多项式最大系数为100,通过交互得到101个点的坐标,利用拉格朗日插值法得到这100个系数的值
exp:
1 | from pwn import * |
运行得到flag
最后flag为
1 | SHCTF{SHAmlr_No7_ShErLoCk_56dd9e0cb08c} |
[Week3] babyLCG
源码:
1 | from Crypto.Util.number import * |
参考
记 LCG 例题_# a = 73111197104586312977084921341458383051320481-CSDN博客
https://dexterjie.github.io/2024/07/16/%E6%B5%81%E5%AF%86%E7%A0%81/%E6%B5%81%E5%AF%86%E7%A0%81-LCG/
seed>>80有位移,应该要用格
2元cooper
exp:
1 | import itertools |
运行得到flag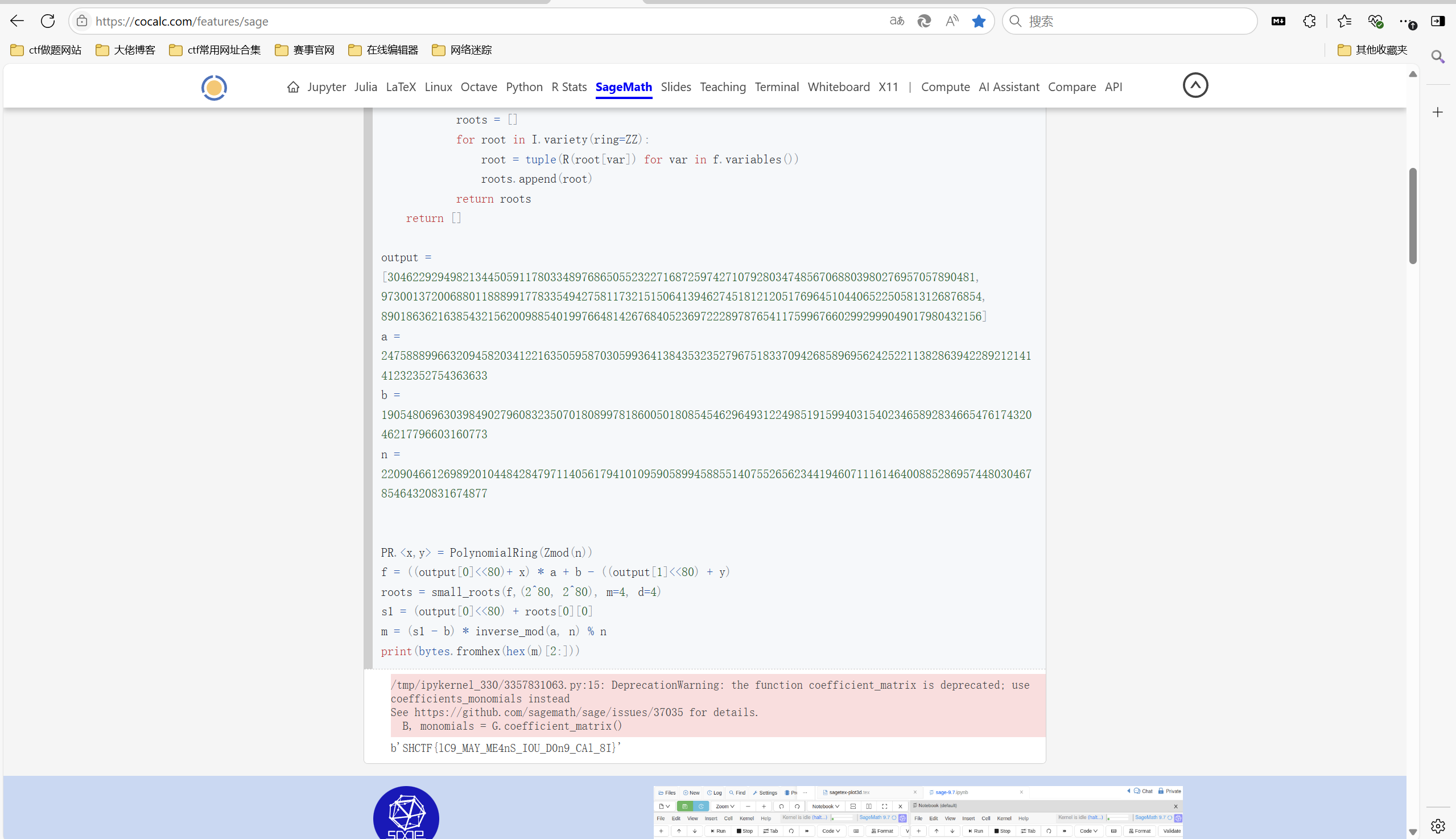
最后flag为
1 | SHCTF{lC9_MAY_ME4nS_IOU_D0n9_CAl_8I} |
[Week3] baby_lock
题目描述:
1 | 生蚝家里装了一个新款智能门锁,每次都要输入很长的密码,但你在偷窥的时候发现好像有一些规律? |
源码:
1 | class Random(object): |
本题考点的PRNG,是「Xorshift128Plus」
https://blog.securityevaluators.com/hacking-the-javascript-lottery-80cc437e3b7f
这个漏洞在v8的Math.random()中被发现(已修复)
https://github.com/v8/v8/tree/7a4a6cc6a85650ee91344d0dbd2c53a8fa8dce04 本题进行了一点点魔改
增加PoW算是提示不需要太多次的获取数值
实际上也只需要3个连续state,Z3求解即可
exp:
1 | import z3 |
[Week3] 大学×高中√
题目描述:
1 | 死去的高中数学知识突然攻击我!!! |
源码:
1 | from Crypto.Util.number import * |
参考第二届黄河流域网络安全技能挑战赛 | DexterJie’Blog

exp:
1 | #sage |
运行得到flag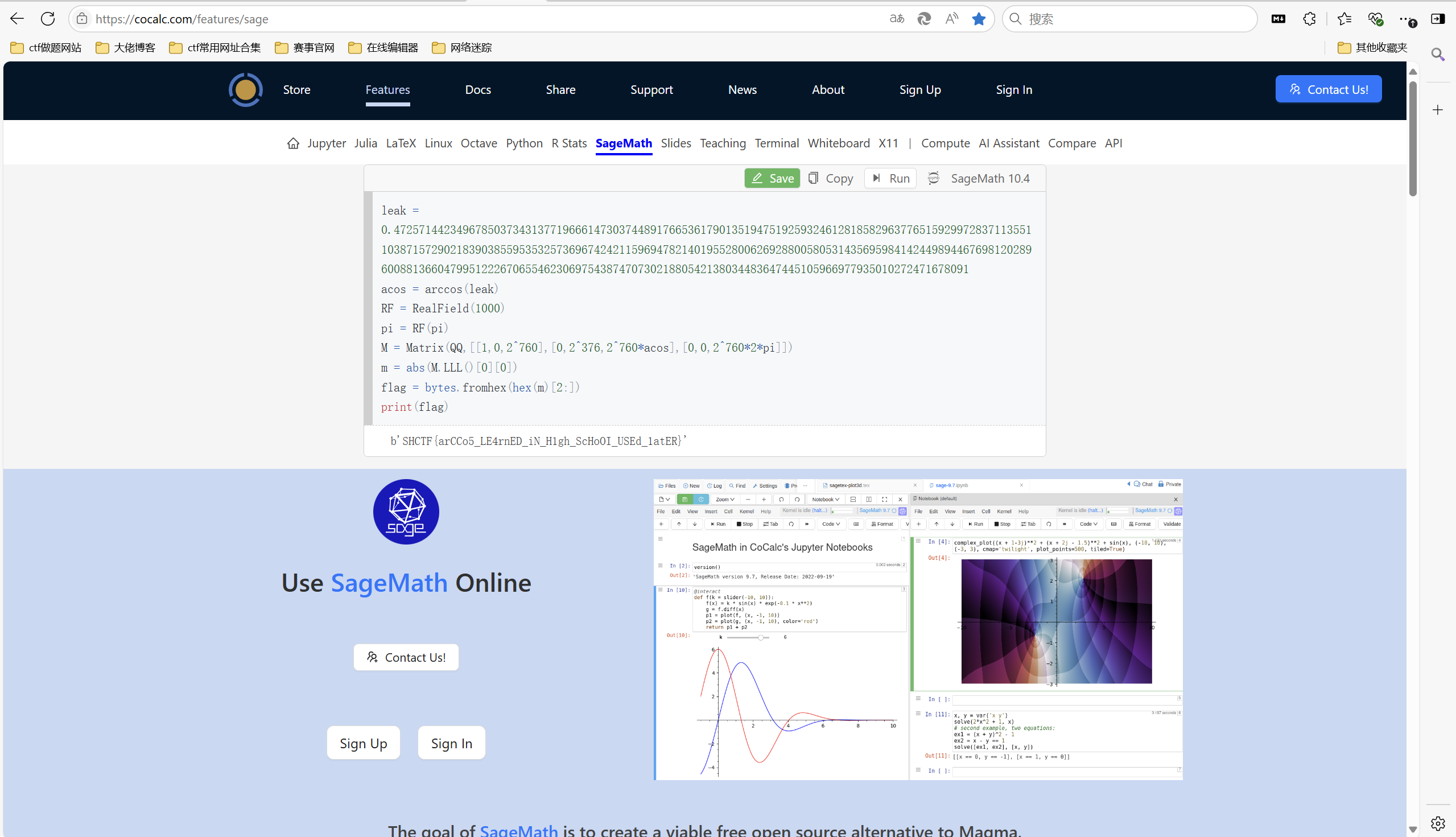
最后flag为
1 | SHCTF{arCCo5_LE4rnED_iN_H1gh_ScHoOI_USEd_1atER} |
[Week4] BabyHash1
题目描述:
1 | Magic Hash : ) |
源码:
1 | from Crypto.Cipher import AES |
利用矩阵的非交换性质构造的哈希函数
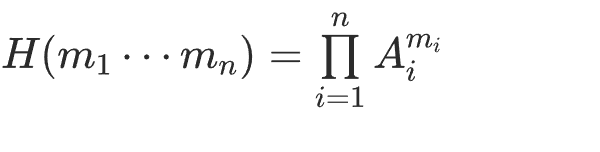
类似于一个乘法背包,但是不同于数域上的,这里很难找到统一的生成元,但是我们可以利用行列式做转换
即判断
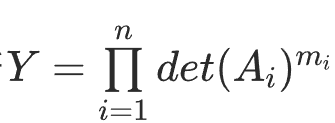
由哪些行列式的乘积构成,这样我们可将其视作一般的乘法背包,但是问题在于题目中选择的 p 不够光滑,我们需要选择其中光滑的那部分求解离散对数。
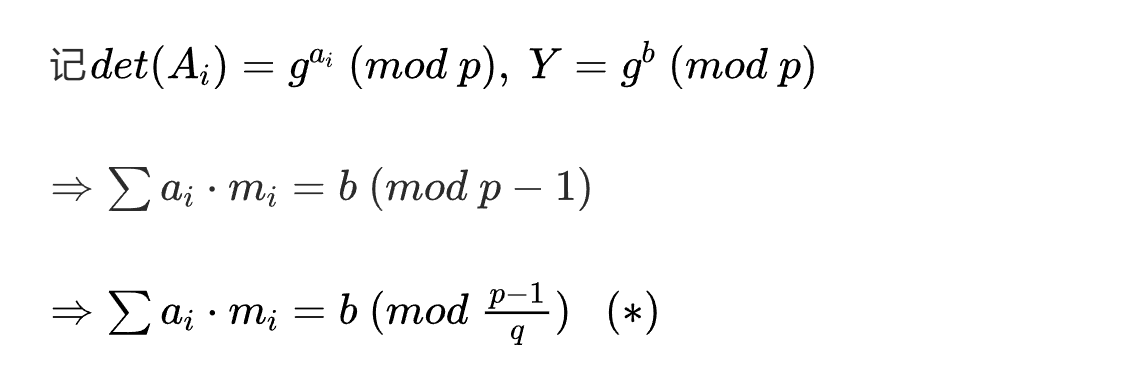
故只需要得到
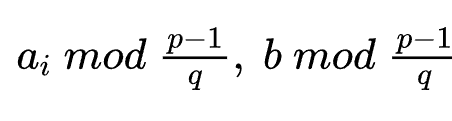
即可,这两者我们均可以在光滑阶下进行求解。
最终利用 (*) 式构造格通过 LLL 还原 key 并解密。
exp:
1 | from Crypto.Cipher import AES |
最后flag为
1 | SHCTF{master_of_the_linear_algebra} |
[Week4] BabyHash2
题目描述:
1 | Magic Hash : ) |
Algebra Hash 比较经典的攻击方式
利用矩阵的非交换性质构造的哈希函数
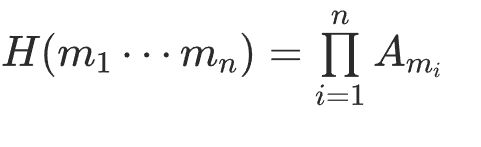
其中
构造碰撞的关键在于能否找到单位阵在 A0,A1下的非平凡分解,显然

注意到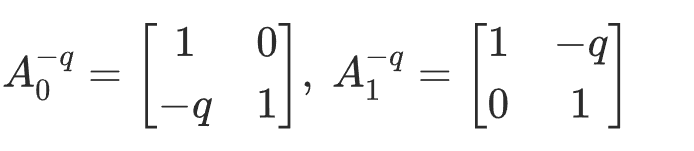

exp:
1 | from Crypto.Util.number import * |
最后flag为
1 | SHCTF{ez_att@ck_2_th15_weak_hash} |
[Week4] MT19937
data.txt
1 | [1212937457, 714280275, 2934808054, 289447810, 634020656, 2582053193, 2648476152, 3584472561, 2877037797, 1051288028, 3007240724, 3583122714, 2377373219, 2233668169, 2300136290, 4277363949, 572508719, 3707687803, 868724505, 2234515288, 2182162330, 2354654192, 3676064525, 16386761, 1934246009, 396534601, 3406538372, 1978740790, 51554945, 1642830773, 3255471879, 249329746, 1871028531, 1670146144, 3955249559, 3523216280, 4225679888, 1979625069, 1711120506, 4224015378, 2357192253, 1437719734, 1861766583, 252037050, 3805173581, 3845899039, 239338040, 3335618070, 1909354144, 2380236080, 3120658839, 2738735651, 1749563272, 4028406006, 198730175, 4095736523, 2224365497, 1850797931, 123559677, 277130374, 1547602417, 2312967225, 1064405558, 620877831, 4182002366, 2717144120, 2424475877, 1261886189, 2666842961, 1250633055, 1445939400, 2496676732, 46718503, 1726056600, 2892333819, 3874613567, 2801764620, 3279121957, 62950328, 14090298, 3016963976, 235881318, 1152787765, 3549713637, 3184265794, 461262349, 1835258817, 706701716, 366259495, 2484440259, 2306336615, 2418024433, 107268664, 3018120752, 3915797798, 1685880034, 2782876985, 2876720582, 3803172243, 1745503879, 1965535595, 2831775453, 3139448870, 770826076, 559187920, 4292272948, 86904027, 1821662944, 58381562, 250790584, 2122997254, 2937312684, 3225034461, 1493971528, 913420791, 2911905254, 2938402784, 1430747115, 2654595902, 3315197237, 602765188, 1471009311, 3788529131, 913593424, 3280524381, 1554400422, 3250536147, 3480550436, 821401975, 3216026683, 762420368, 1733854366, 2395038075, 533527872, 3040490234, 2855012365, 2984904790, 2830464734, 2200935030, 523059886, 3795772367, 2905400361, 667720140, 3155311553, 1860651089, 1053555607, 2889478721, 1812821011, 3391980212, 3433665687, 2480476597, 1319654037, 1076583906, 2287201297, 966928688, 2542225146, 2246098689, 3117124345, 1844896511, 3104215564, 1303510082, 2924158615, 3648677443, 3308489255, 3809196505, 3199516268, 2254502655, 2126047470, 1763846642, 3851973930, 1280609700, 2415985988, 1312349771, 2103486452, 4229394974, 1937464844, 2763672456, 1366425769, 1532462738, 1864298394, 1203192658, 3679892306, 4138733297, 39437090, 1317880030, 132948638, 2315846286, 3394291148, 3207221552, 3834885856, 2367158425, 3183864791, 3303289072, 519407526, 4127464161, 1556426685, 2427155757, 2010011401, 2823249259, 3638339516, 2266010959, 345885116, 471672470, 2713191580, 731238671, 1694687550, 2523761501, 3533913138, 163820753, 1829608711, 587056408, 1129980234, 3642159144, 2546599527, 758703728, 1713442774, 1864598338, 2763096157, 2308766766, 1132350895, 2776604596, 1921085522, 1409581297, 2643399928, 3285649744, 1248611904, 2694186262, 2676127368, 2579578748, 3784393865, 2655293049, 1378866508, 1251610536, 1048557165, 3045231444, 4236456301, 2496231577, 4118010676, 3079411364, 2425576144, 2431718306, 543894373, 118186072, 2594647421, 1833894329, 3876640493, 1916631983, 2765860034, 3905895682, 2207230275, 2554838603, 3199831939, 2516271151, 3080023814, 3594335532, 1197450849, 2621744299, 447615180, 1616950869, 3109651542, 2553431350, 4165466937, 2130063794, 1459492895, 1141470511, 948009682, 325807524, 1681494454, 3137320840, 4219461371, 609761579, 942363481, 2404858793, 1697226342, 830264373, 230968933, 831865647, 4164463522, 2968510743, 1464271639, 1397831008, 2559413030, 3515044508, 772056268, 3152446673, 3117754594, 833212973, 4252629747, 2565179775, 3005093783, 3595030314, 4042182692, 298671165, 3183128227, 3429794312, 4122368172, 1900961662, 3589294443, 3190786481, 1744404482, 1921785452, 3011999869, 642164068, 3695788414, 2275346981, 1428956574, 2697326707, 2202213004, 3287889517, 919861723, 726410498, 337174656, 2417998504, 2752587611, 3856581958, 141509063, 1762431188, 2065705145, 2031960873, 1892209091, 2395039500, 1058479586, 1537034270, 502217054, 3102018820, 1433274316, 1372952271, 2918921770, 239909451, 1398298200, 2339489735, 372558373, 2263872236, 2426192905, 337209508, 3983991978, 2574803724, 2837664572, 1569892789, 2625063195, 3262762020, 24150029, 2016099290, 2239153990, 85602273, 973040529, 2956276779, 4218049523, 2043716624, 2788573458, 1218787308, 939708241, 2861205992, 2427634523, 4128874493, 2326852266, 2593724377, 1680473968, 2763572707, 4240616686, 2863701585, 3551633590, 1765256405, 2110583291, 357590304, 2511138801, 859903599, 35591840, 3786321031, 3559501147, 3107666783, 2356867678, 1369801910, 2488594855, 2148205170, 3944224524, 2219844222, 466009157, 2328231114, 2777059464, 1585865212, 2871297568, 2558165993, 1561563095, 438633926, 2619385032, 2185942244, 2501145168, 2161107203, 912485991, 3956413626, 4065963551, 1527306118, 378382496, 1016367697, 82832444, 2484726280, 867566307, 1037338825, 4291735272, 901722138, 3956112428, 1060890097, 4210262544, 2525835262, 786274933, 2563584713, 2738164238, 3438656534, 564065202, 3288501195, 1074332184, 2947775555, 3790174897, 3607901153, 2332098514, 3648669449, 3879104921, 3983960923, 548882335, 1817587379, 1555057777, 2705918139, 2755720626, 2706833366, 2947946695, 3082750952, 2323554320, 1804494628, 1677086381, 2771841028, 2470056271, 3431120732, 4073503495, 2929631518, 80800254, 605951710, 1664206366, 2498279527, 360922649, 2590660538, 3724444465, 3559953317, 3002864163, 3369368155, 1569518356, 3831143803, 4184782515, 1602338537, 2640186368, 2864951447, 514648741, 887020932, 166121609, 476244781, 2238614863, 3039706334, 3586500526, 3038068930, 3989751746, 3699955508, 3559348520, 884358906, 444882591, 3769021913, 3665754928, 1911261614, 1234192084, 3450557803, 3232410240, 494096069, 660552292, 1365481833, 520081058, 1027987838, 3165505556, 1257833693, 2146291679, 3634622224, 589123893, 1195030125, 1602406253, 772753497, 2661121530, 2938530200, 1070706826, 3890477657, 2112901265, 4253917692, 2291562806, 67613984, 2608069358, 1726139310, 3018885048, 367067728, 3838771641, 1357927847, 2616452172, 722979624, 4153031784, 607660099, 3164865398, 3199368055, 1885230388, 1055777913, 3475913336, 1546318749, 578282810, 1558944130, 2955660875, 2214838829, 4202836988, 1405916968, 2593459723, 3648360966, 3644813488, 598912719, 876098814, 355483438, 685352898, 4099087273, 2983380912, 450980374, 2753208777, 429297943, 3462109454, 3134522829, 2064548393, 2200750558, 4247753845, 251220053, 1556849099, 2022648175, 3563632884, 2175932589, 1463719656, 1887673611, 3541708446, 3033219582, 3255799816, 534398633, 3481196045, 825005812, 1629237540, 640085217, 899503755, 3105157116, 488231507, 2708835929, 2648663900, 2048030022, 1503411342, 4059850866, 1281156549, 3171426598, 2637361895, 1110841056, 606897504, 3001264062, 912267483, 148124465, 202684836, 1425732680, 3637635336, 1455737055, 2977077407, 54987379, 1056796337, 1832170261, 1870208138, 4074249428, 2993704297, 381772606, 2362720677, 2164369676, 250156737, 3409786877, 1590821450, 2959971180, 3682255149, 302283211, 4204651015, 1294232346, 3088162584, 4209012441, 784333825, 1275400791, 885466807, 1249631254, 1236809354, 2627231325, 2391839654, 1638467843, 2797229961, 3799496431, 237846505, 3432655604, 1690038717, 1493561006, 4229115929, 3784624191, 2891696687, 3557702324, 1120718375, 2593253432, 1415584860, 551110044, 1510986691, 3267929936, 2341598281, 247215742, 3192053018, 2856032615, 3290505354, 907961089, 4128700570, 4195745607, 2035634741, 1047086449, 216435127, 1997121891, 3391563810, 2813128796, 1517545322] |
源码:
1 | import hashlib |
参考
浅析MT19937伪随机数生成算法-安全客 - 安全资讯平台
MT19937伪随机数算法,生成范围在 [232−1][232−1] 的均匀分布的32位整数,该算法的周期为219937−1219937−1,故名为 MT19937
最简单的题/(ㄒoㄒ)/~~
两部分,第一部分就是最常见的已知MT19937 的624组32比特连续随机数,预测后续的随机数问题
第二部分就是当已知超过397组连续的32位比特随机数,预测625位之后32比特随机数问题
当获得连续n个(398<=n<=624)完整的伪随机数输出单元序列时,可以对从624-n个伪随机数输出单元后的,连续n-397个输出进行预测。即下一次Twist后的对应单元。
1 | 输入:随机数输出序列R1[] |
exp:
1 | from Crypto.Util.number import * |
运行得到flag
最后flag为
1 | SHCTF{TH1s_1s_YoU5_5TART_WAY_0F_CTF} |
[Week4] baby_rsa
题目描述:
1 | 只有中间未知? |
源码:
1 | #https://github.com/jvdsn/crypto-attacks |
论文题 34940373.pdf
已知的条件是d的高位和低位,猜测d是512bit
直接借用大佬脚本
exp:
1 | from Crypto.Util.number import * |
最后flag为
1 | SHCTF{If_people_do_not_believe_that_mathematics_is_simple,it_is_only_because_they_do_not_realize_how_complicated_life_is.} |
[Week4] siDH
output.txt
1 | P1=(3722377589495565619388409947786216655637784681305941494147641084588810631146007176891913880271007127410796381111369183814847421656105900790804342643108*x + 8802687499644901060050022727432797409089156524380319488542634490587555795650045132570968389279817924873049502727897060507742746276768059101617693509917 , 3719477936206364187390068985145413157800621156741491559595580900652585286439418248577575633342364501408686579893456793185782751143171546872666909621050*x + 11747436493943707843147767337329761069262174137296210697323632536020627422974942280457502098526627796314363833333722260721915312017545212458579310144482) |
源码:
1 | #!/usr/bin/env sage |
又学到了,这个是SIDH(超奇异同源Diffie-Hellman秘钥交换算法),一种后量子安全秘钥交换协议
Castryck-Decru攻击是一种针对Supersingular Isogeny Diffie-Hellman (SIDH)协议的密钥恢复攻击。该攻击由Wouter Castryck和Thomas Decru于2022年提出,旨在利用椭圆曲线上的扭点信息和秘密同态的度数来计算所需的同态。攻击的核心在于利用椭圆曲线上的小非标量自同态的存在性,从而在多项式时间内恢复出用于生成秘密同态的整数。
论文原文: 975.pdf
p=2a∗3b−1p=2a∗3b−1
其中pp在EB1最后面找到
1 | p = 13175843156907117380839252916199345042492186767578363998445663477035843932020761233518914911546024351608607150390087656982982306331019593961154237431807 |
分解找到aa,bb
\begin{array} \ a_1 = 250 \ b_1 = 159 \ a_2 = 486 \ b_2 = 301 \end{array}
构造椭圆曲线,后面有点超模了
(sage-build)$ sage sol1.sage –parallel
1 | import public_values_aux |
(sage-build)$ sage sol2.sage –parallel –sandwich
1 | import public_values_aux |
sol3.py
1 | from Crypto.Util.number import * |
最后flag为
1 | SHCTF{The essence of mathematics is its freedom.} |