天权信安&catf1ag
简单隐写
下载附件
binwalk分离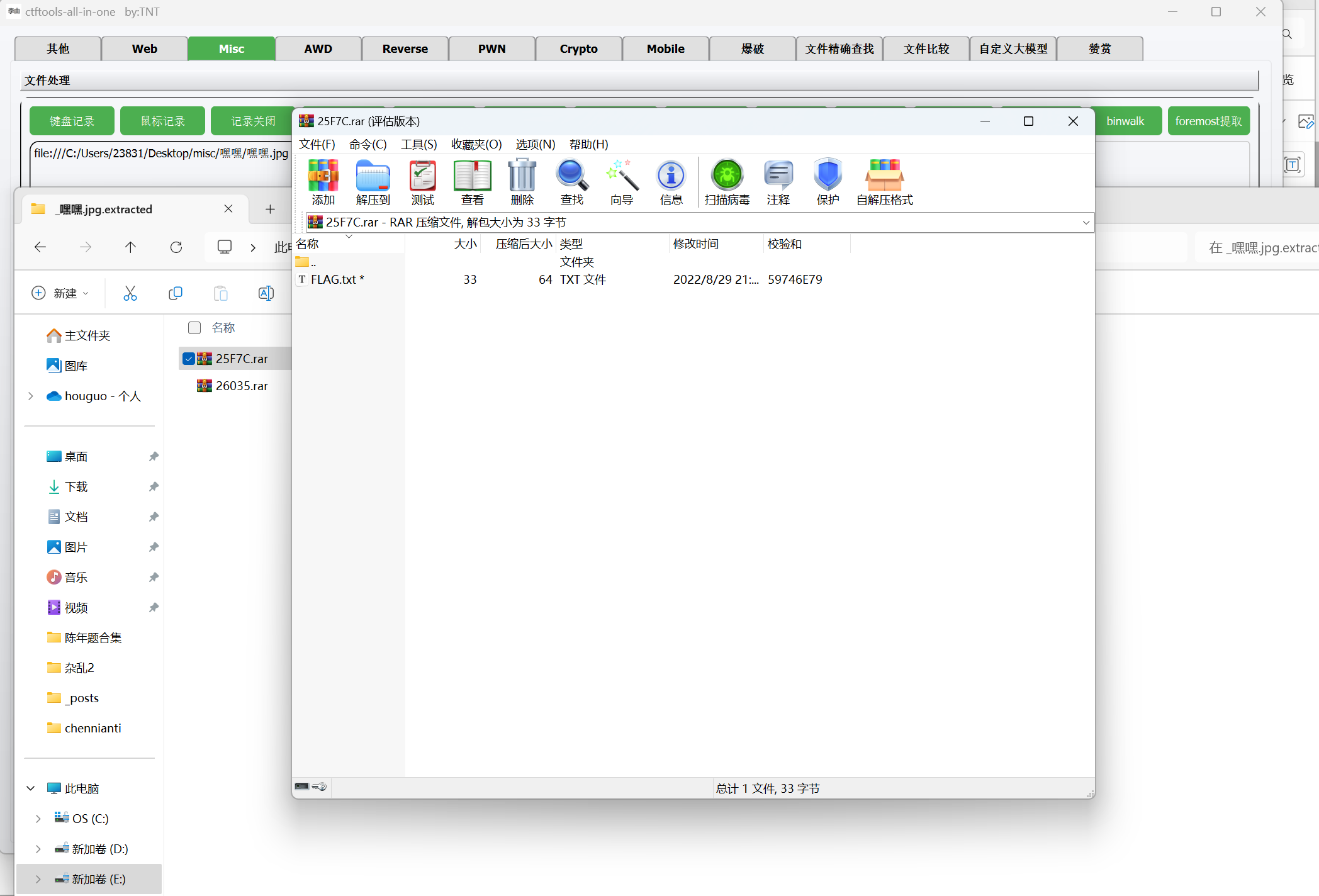
使用jphs无密码得到一个txt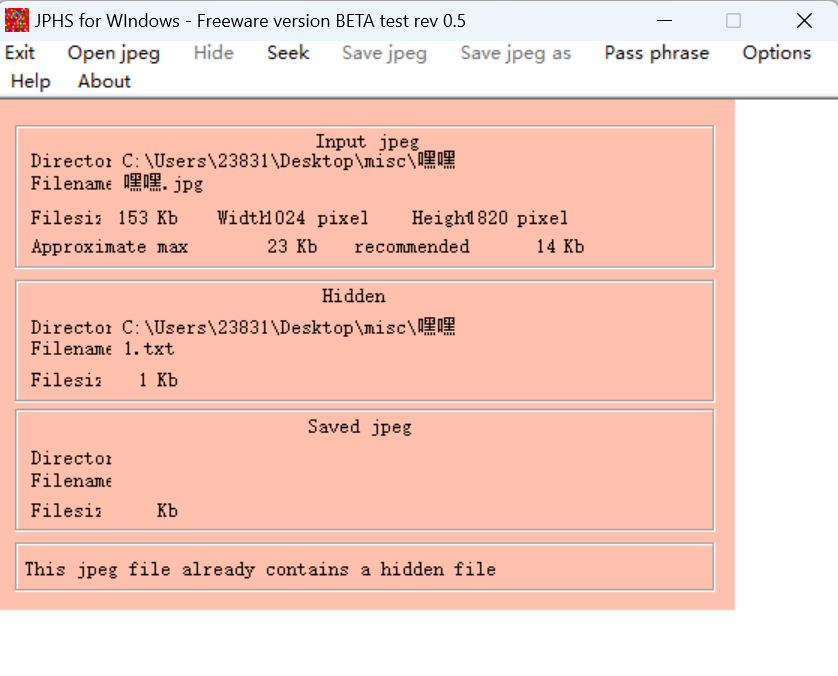
查看1.txt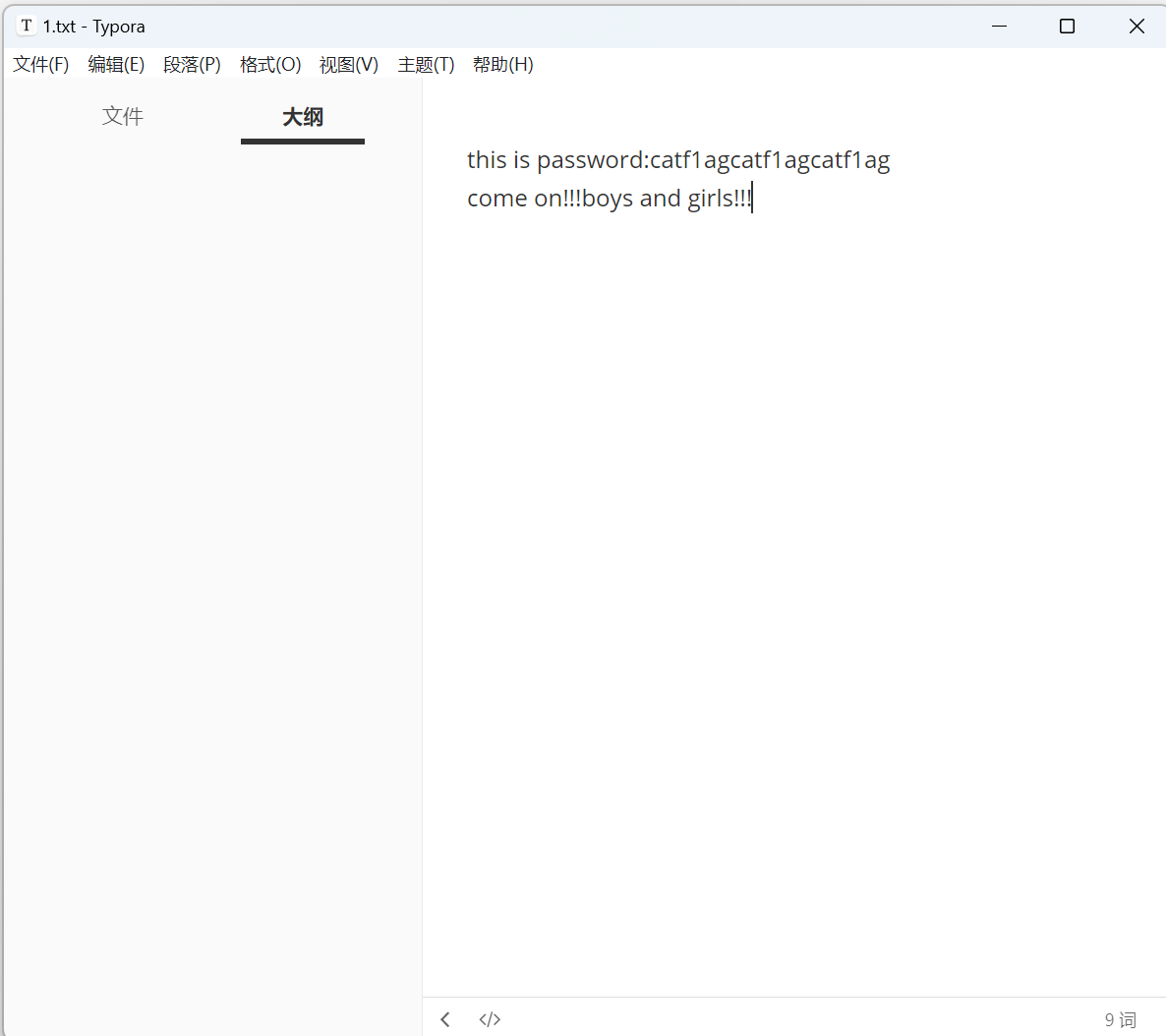
得到压缩包密码,解压压缩包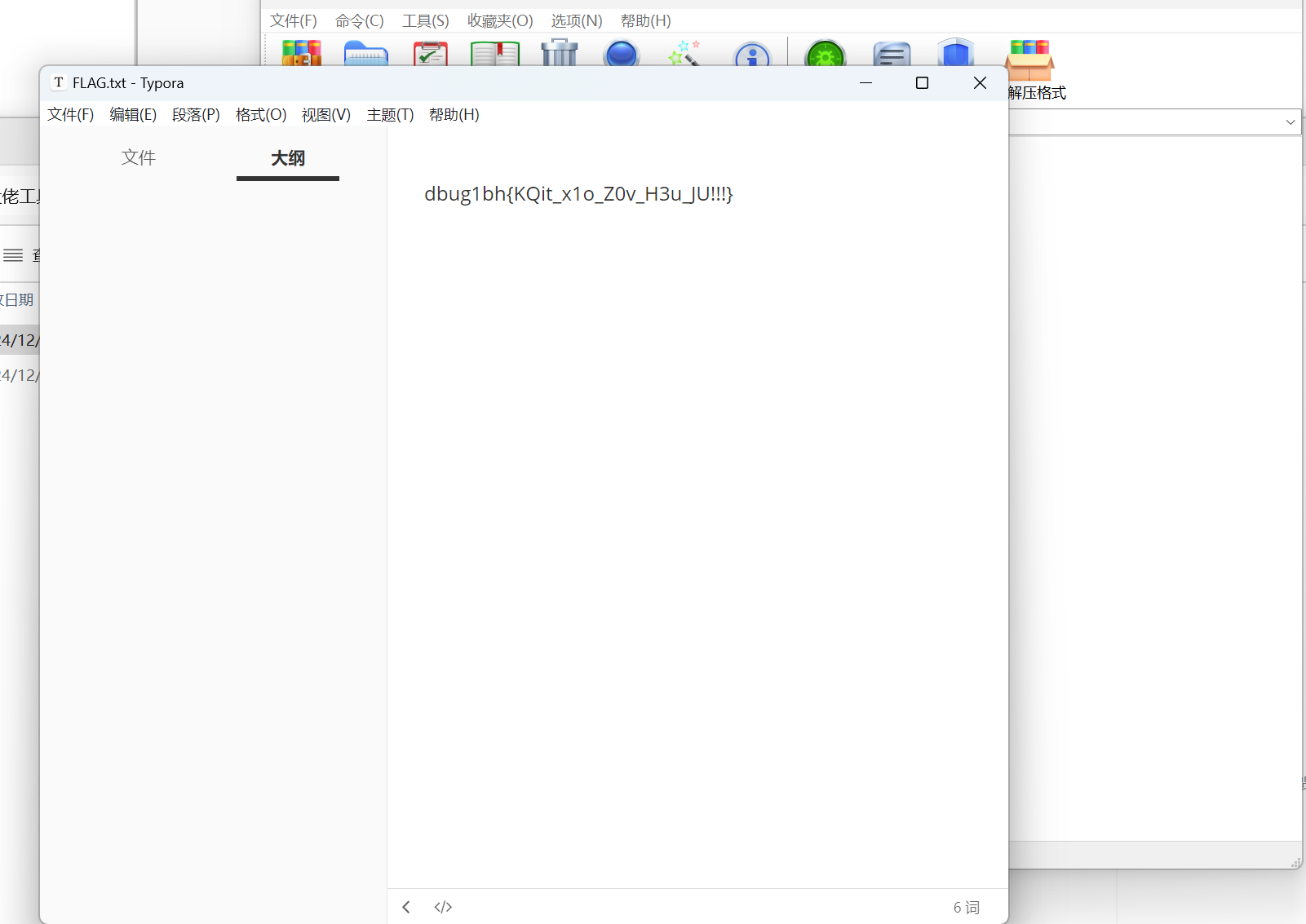
随波逐流一把梭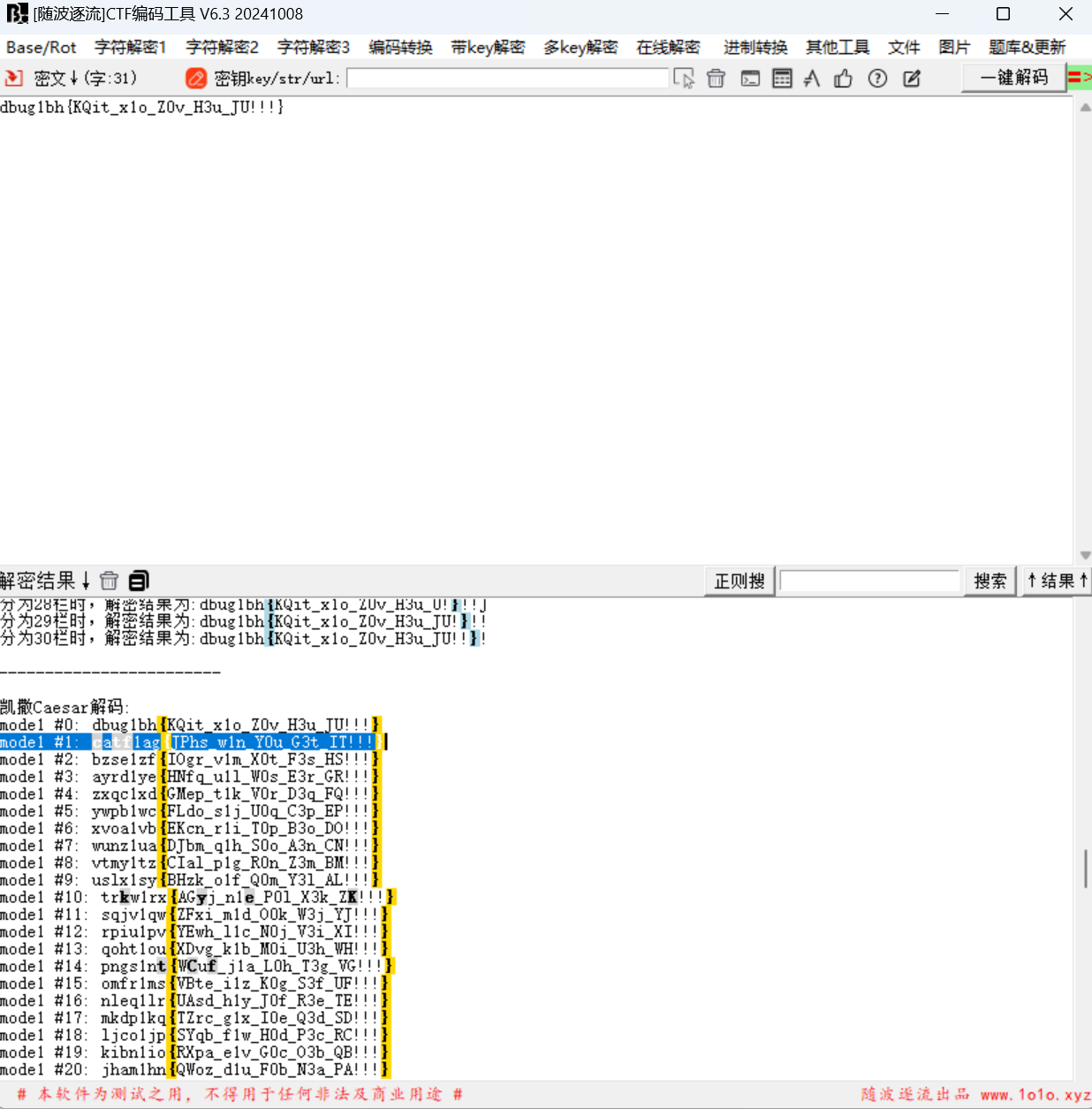
最后flag为
1 | catf1ag{JPhs_w1n_Y0u_G3t_IT!!!} |
十位马
下载附件
010查看文件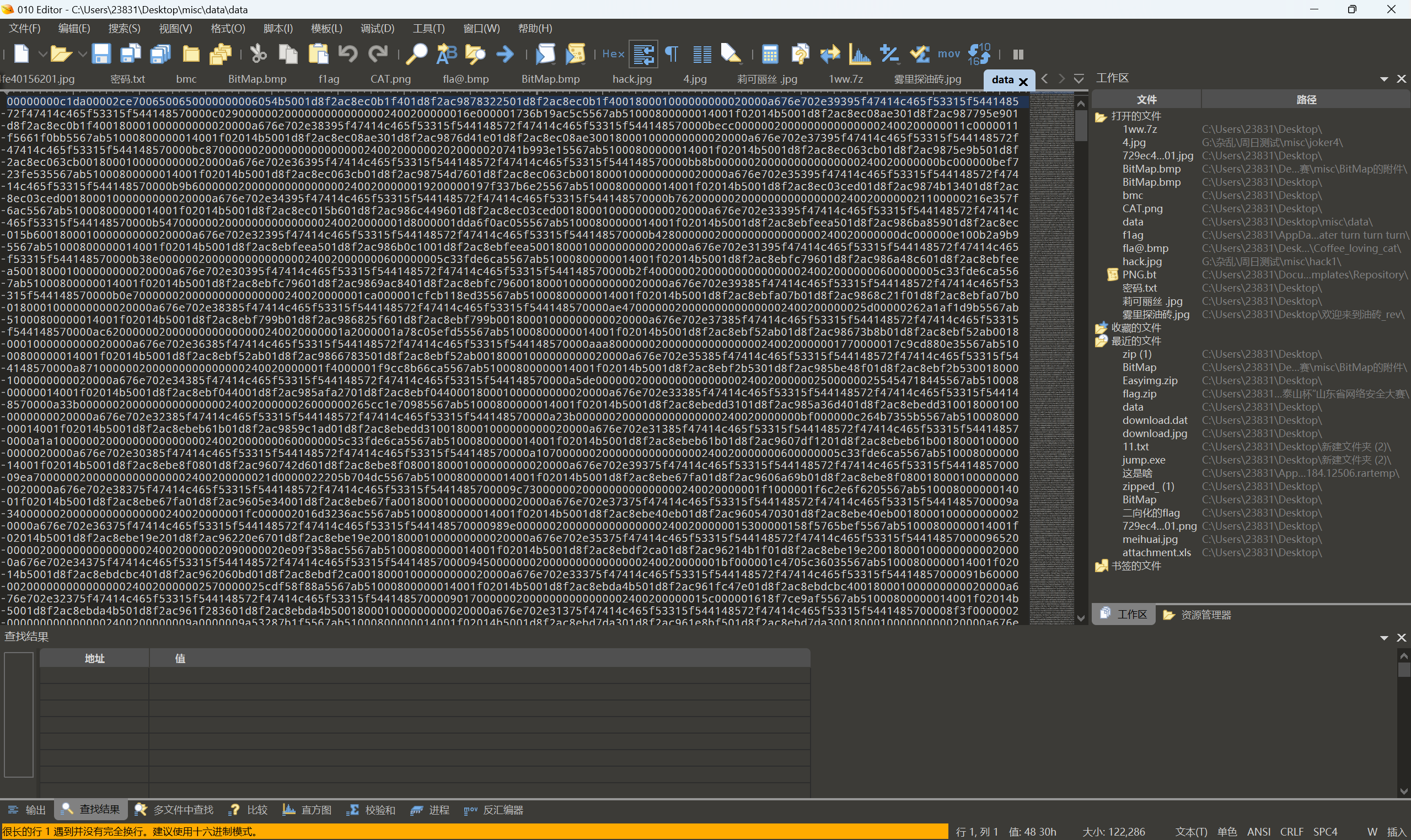
十六进制解码试试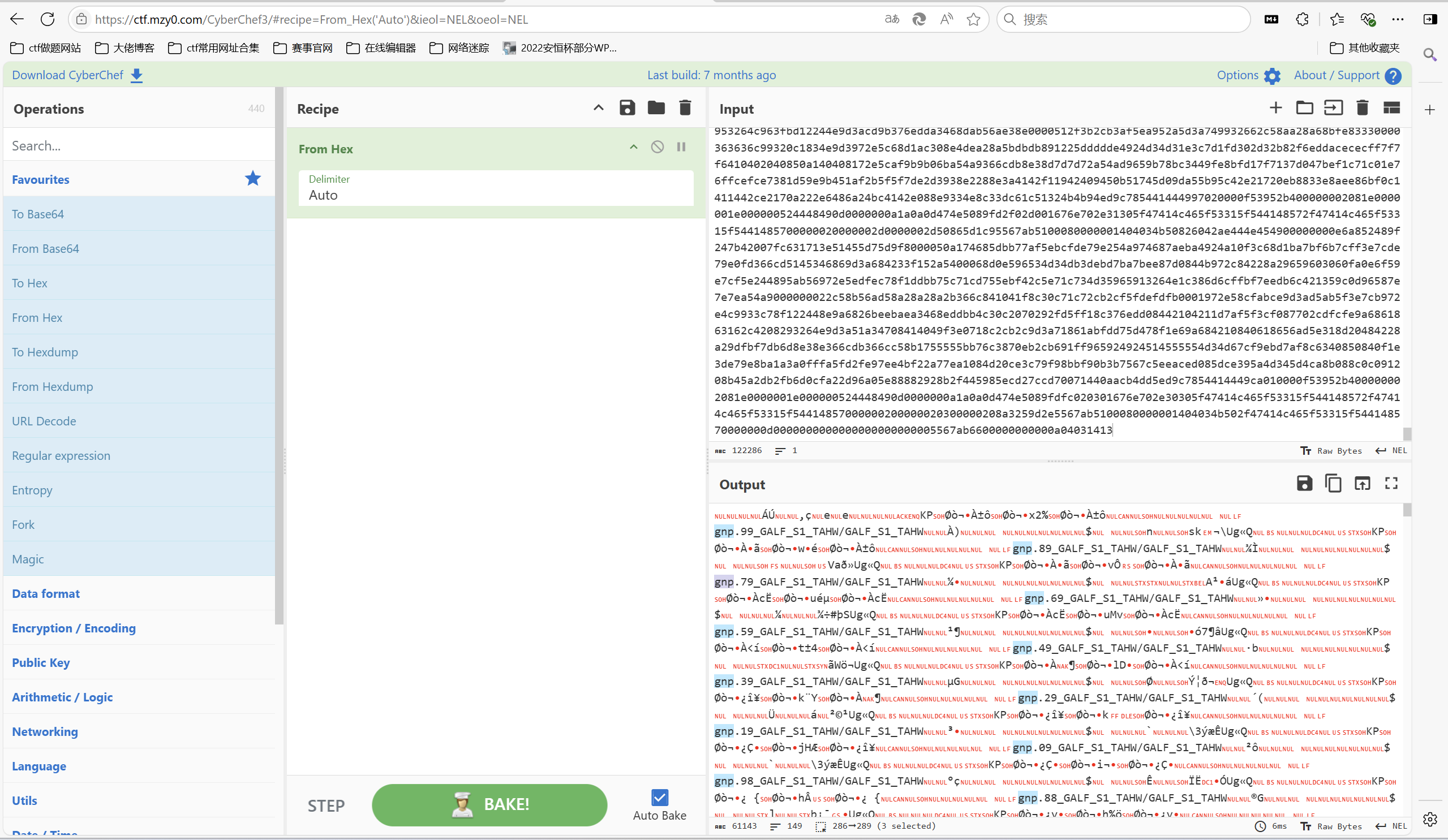
发现是png文件,不过是反过来了
reverse后改前前两个字节
exp:
1 | with open('E:\\脚本合集\\赛题脚本\\陈年题\\swm\\data','r') as f: |
运行得到
改前前两个字节,赛博厨子一把梭
保存并解压压缩包
montage拼图
1 | montage *.png -tile 10x10 -geometry +0+0 flag.png |
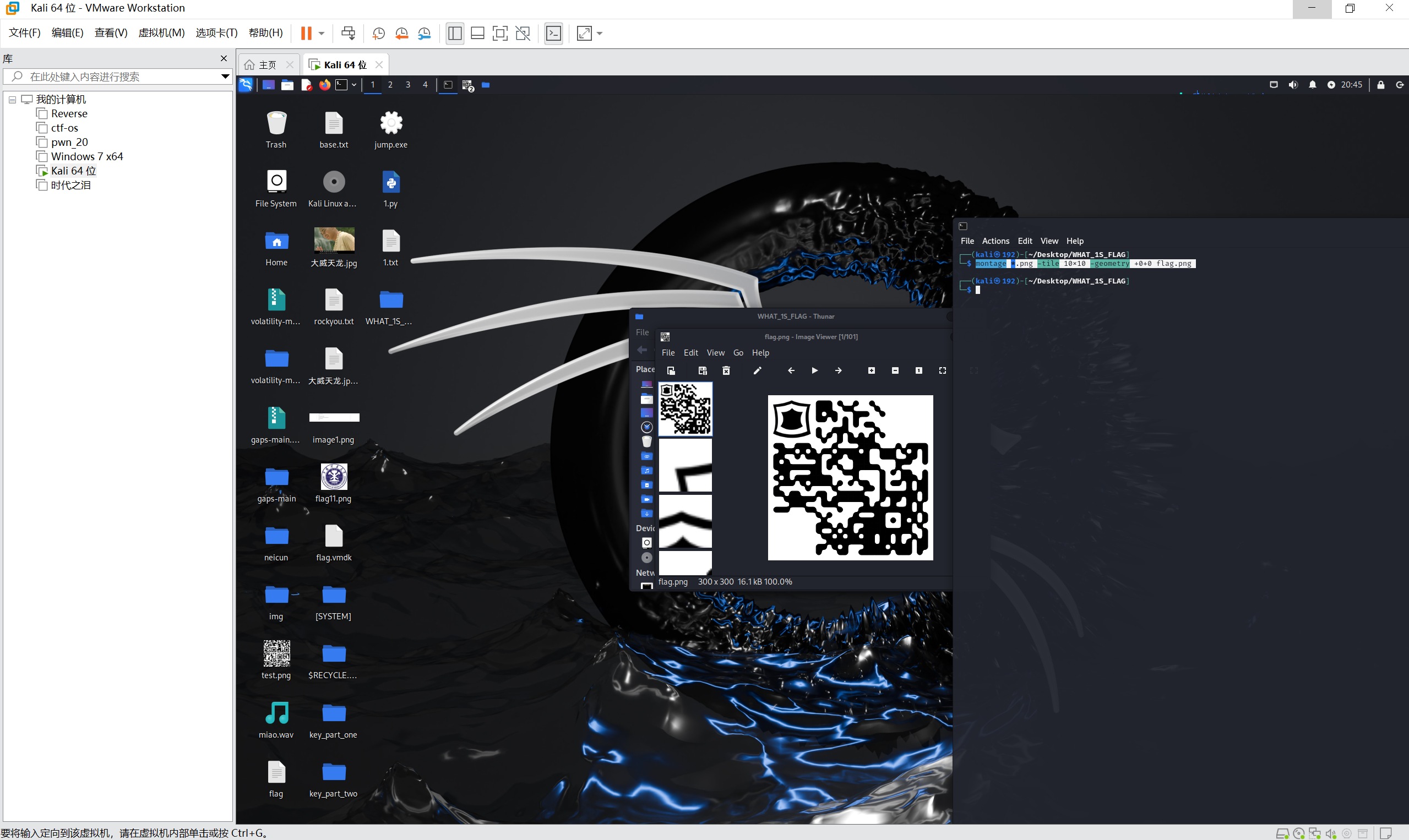
ps补上定位码
扫描二维码得到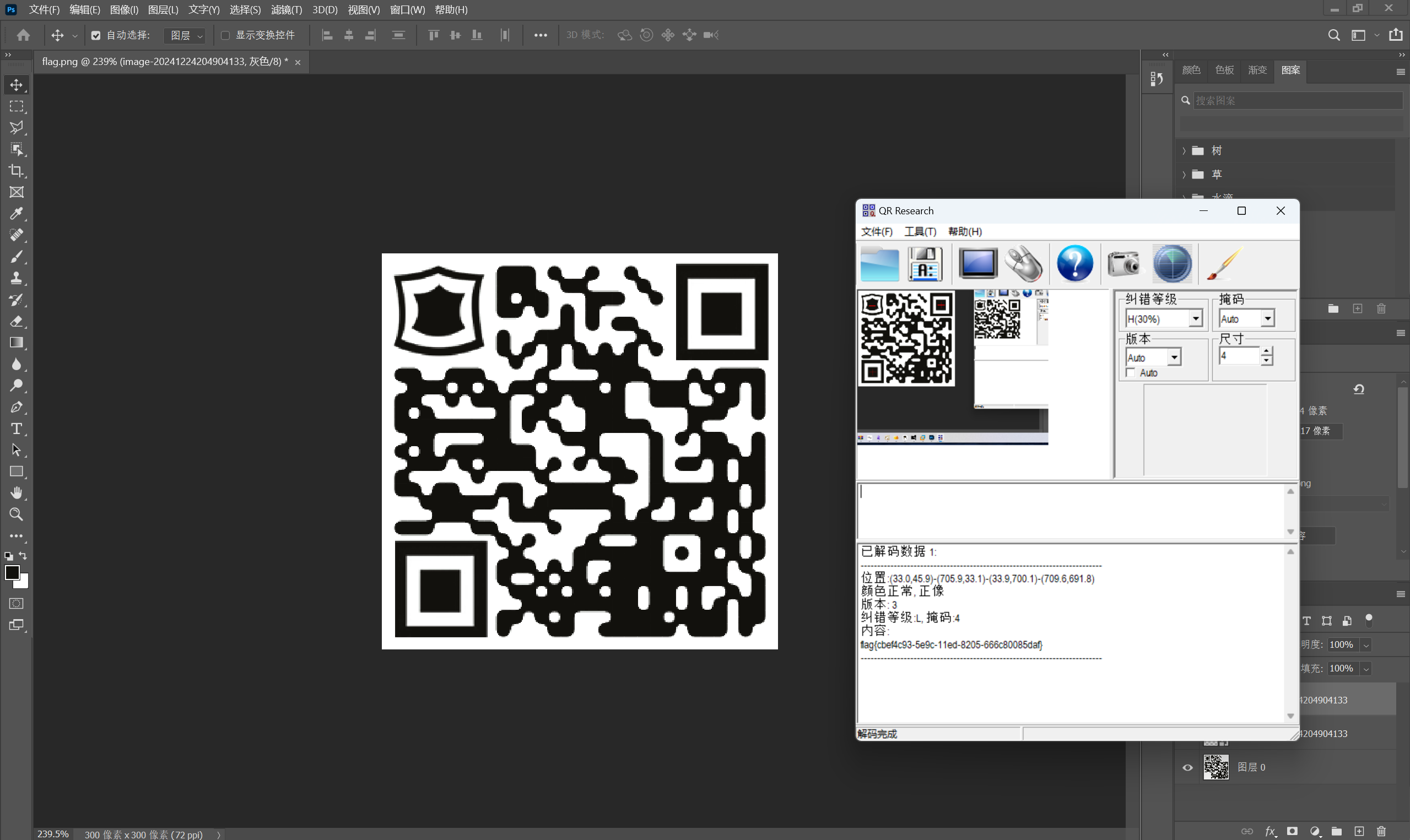
最后flag为
1 | flag{cbef4c93-5e9c-11ed-8205-666c80085daf} |
反方向的钟
题目描述:
1 | 听一万遍反方向的钟能回到过去吗 |
下载附件
查看音频文件发现是周杰伦的反方向的钟,查看频谱以及尝试各种音频隐写都没什么发现
根据题目描述
听一万遍《反方向的钟》能回到过去吗”,可以得到10000的倒数为1/10000
所以压缩包密码为
1 | 1/10000 |
解压压缩包得到一个无后缀文件,010查看文件
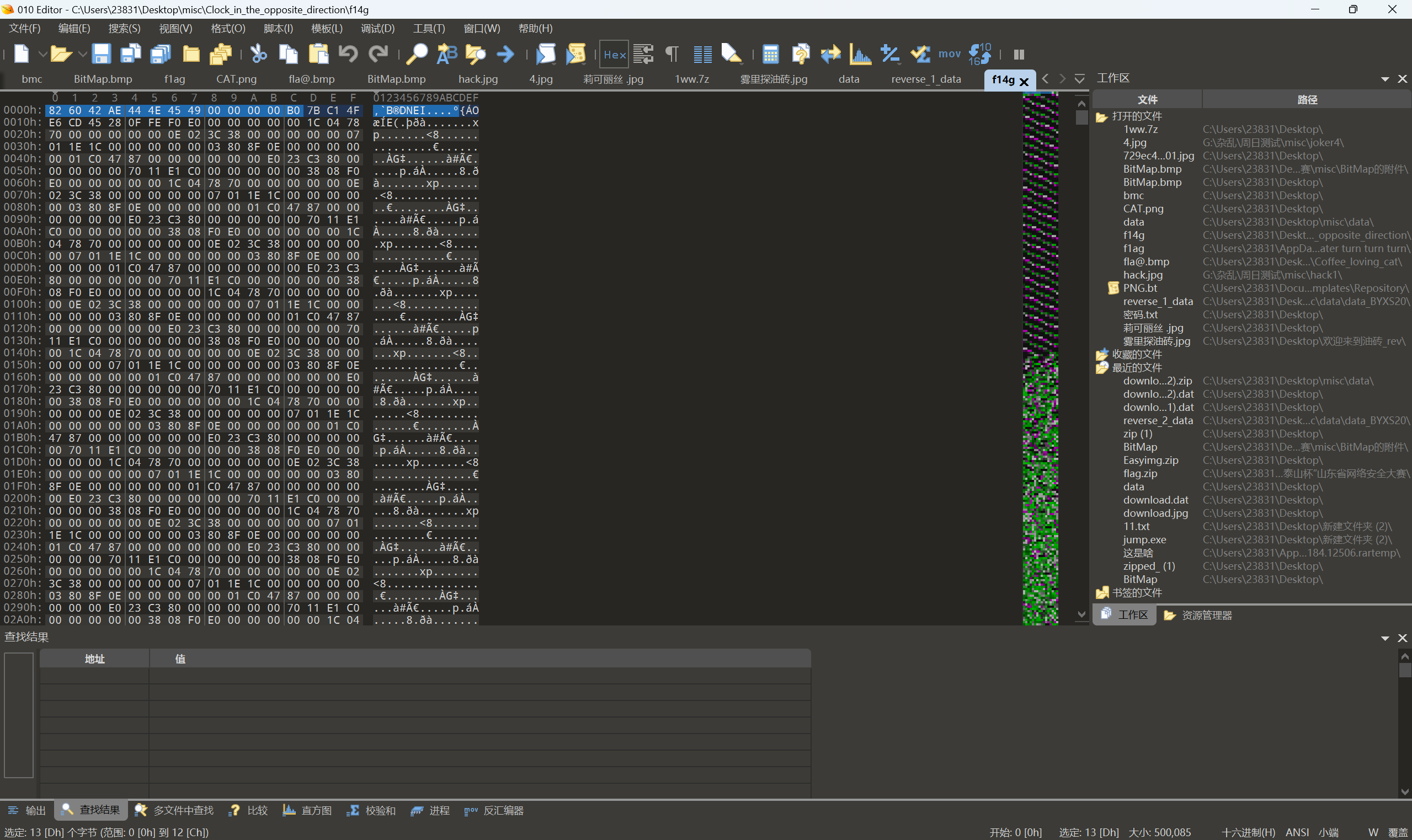
看到这些乱码是文件被逆序直接reverse然后补全png文件头
保存并查看图片
将音乐倒放末尾得到一段钢琴音乐,简谱为1433223(之前学过音乐听出来的)
cloacked-pixel隐写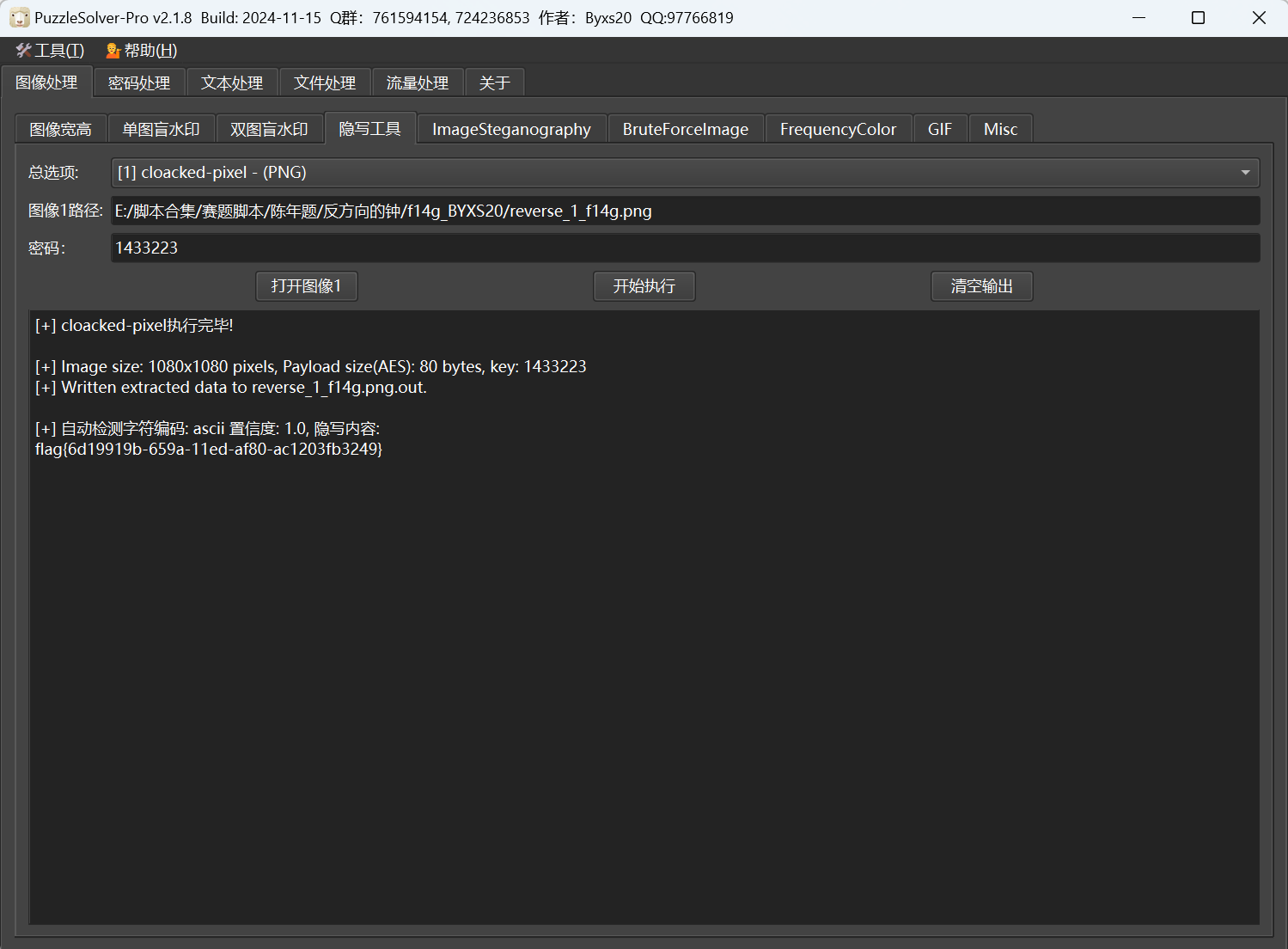
最后flag为
1 | flag{6d19919b-659a-11ed-af80-ac1203fb3249} |
ez_misc
下载附件
查看pass.txt
1 | password is 米糊油 |
查看文件夹发现是原神游戏,猜测密码是yuanshen
解压压缩包得到
010查看系统文件 config.Sys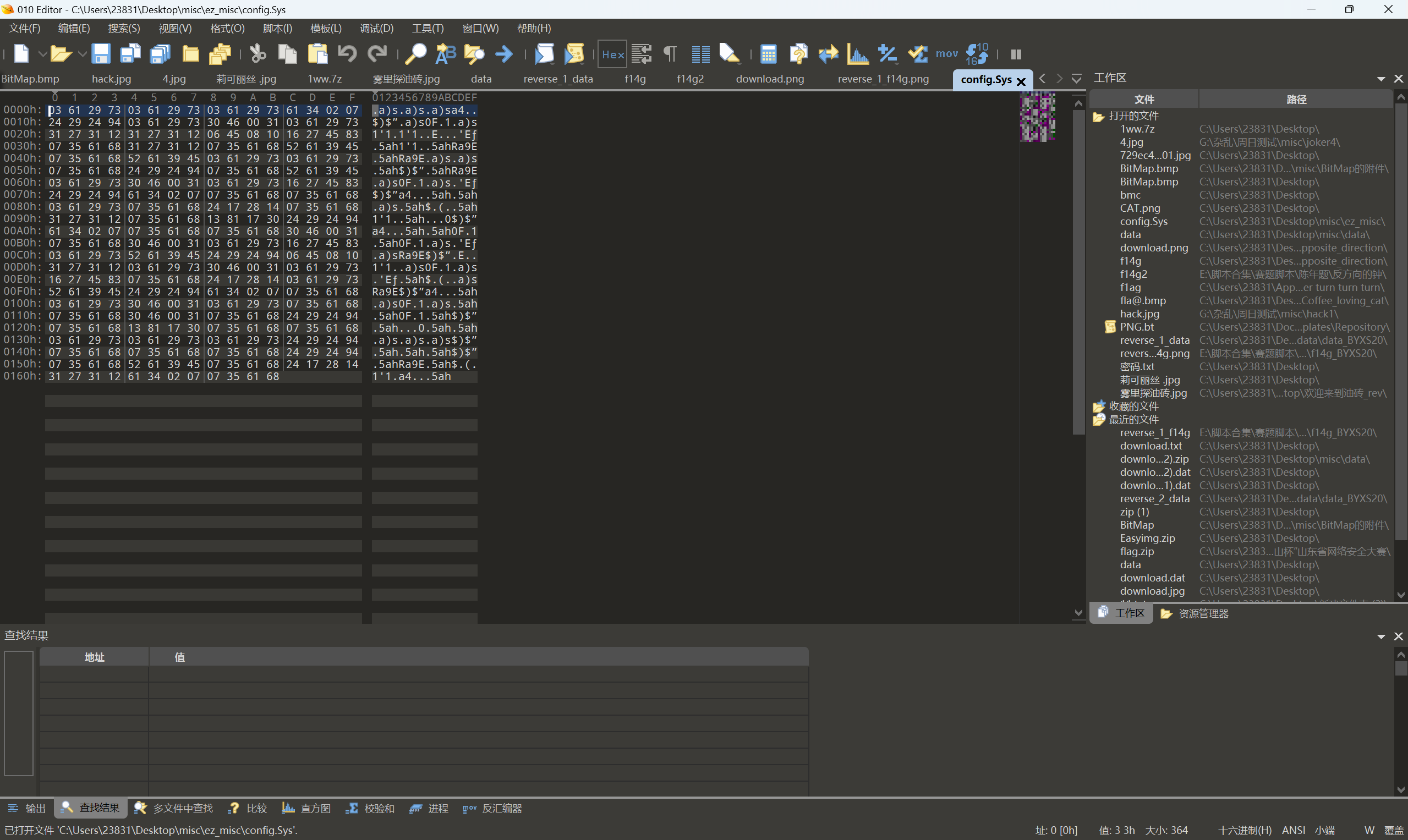
将16进制数四个字符串一组之后加空格进行中文电码解密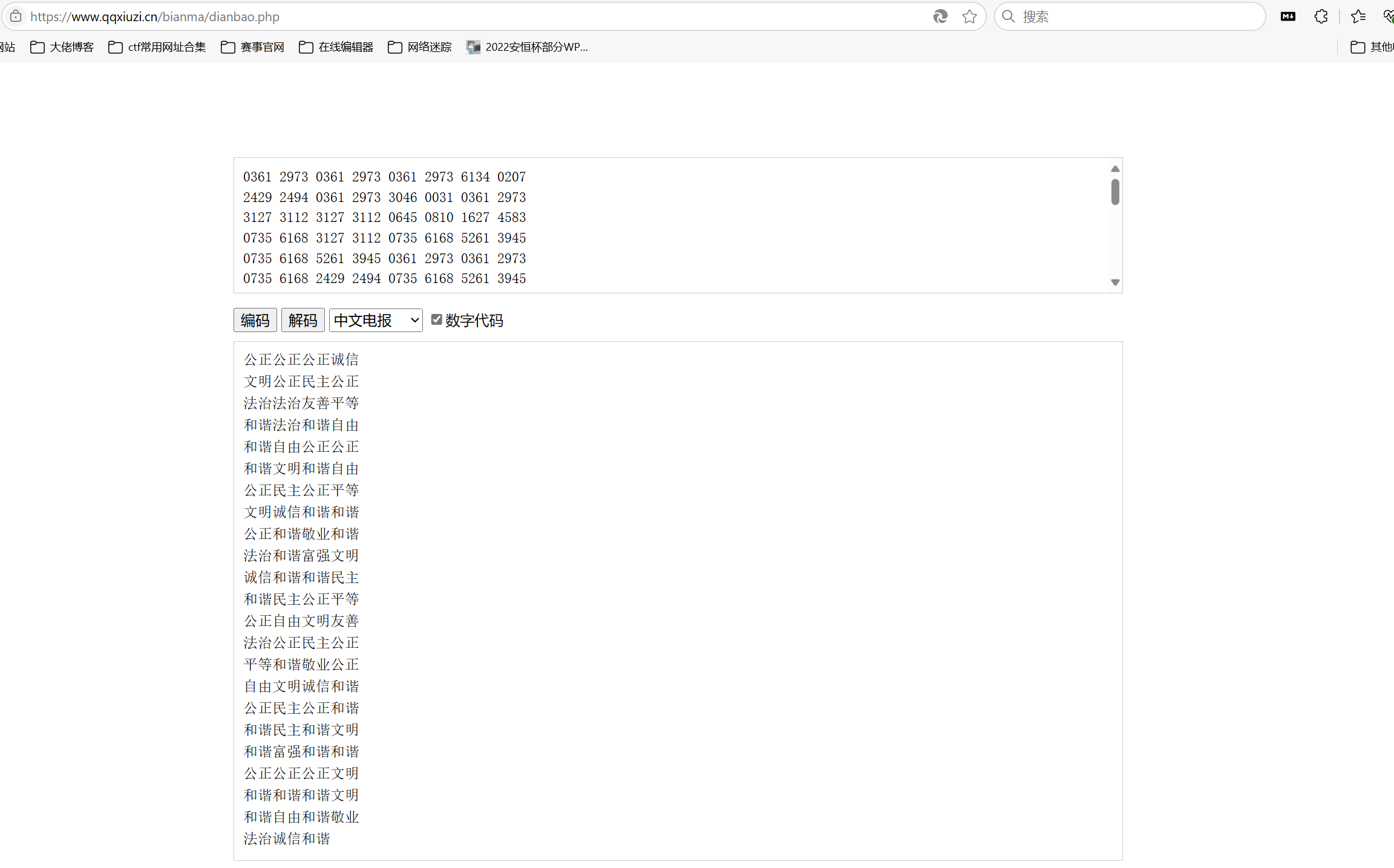
核心价值观解密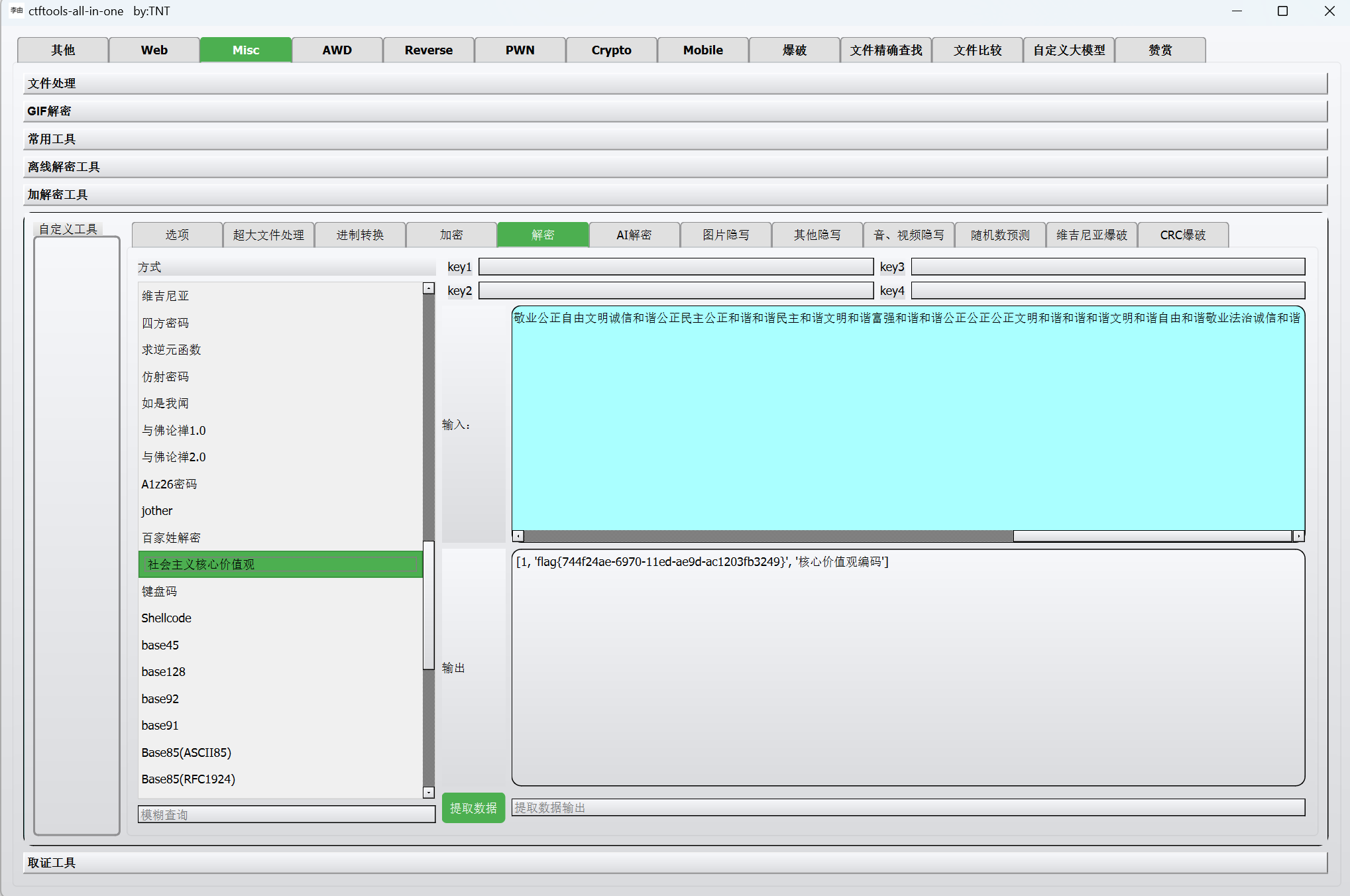
最后flag为
1 | flag{744f24ae-6970-11ed-ae9d-ac1203fb3249} |
Wind water turn turn turn
下载附件
010查看文件
发现是zip文件,改后缀.zip
word文件,打开乱码,还是010查看吧
发现是逆序zip,提取下来reverse得到zip,snow隐写得到flag
最后flag为
1 | flag{ffd81975-648c-11ed-b5fe-ac1203fb3249} |
Devil’s Eighty Hammer
下载附件
爆破压缩包密码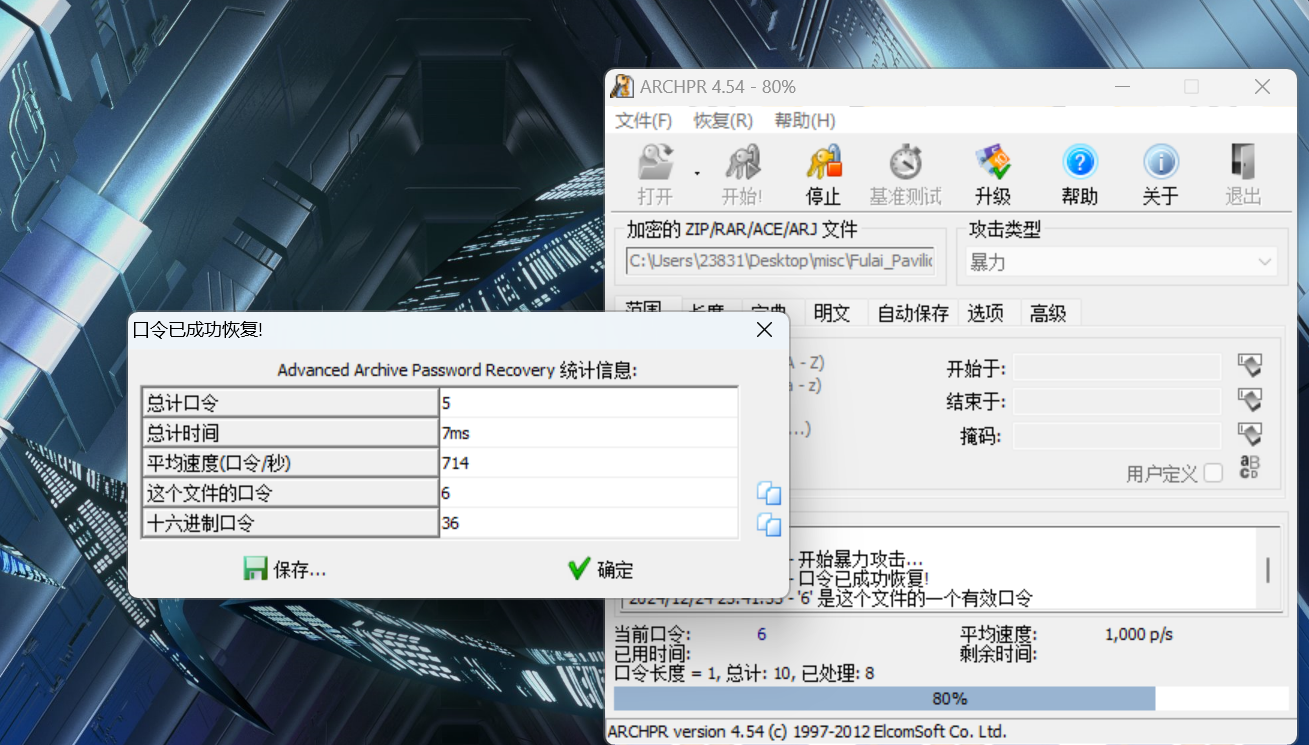
解压压缩包得到无后缀文件,010查看
去掉连接符得到长字符串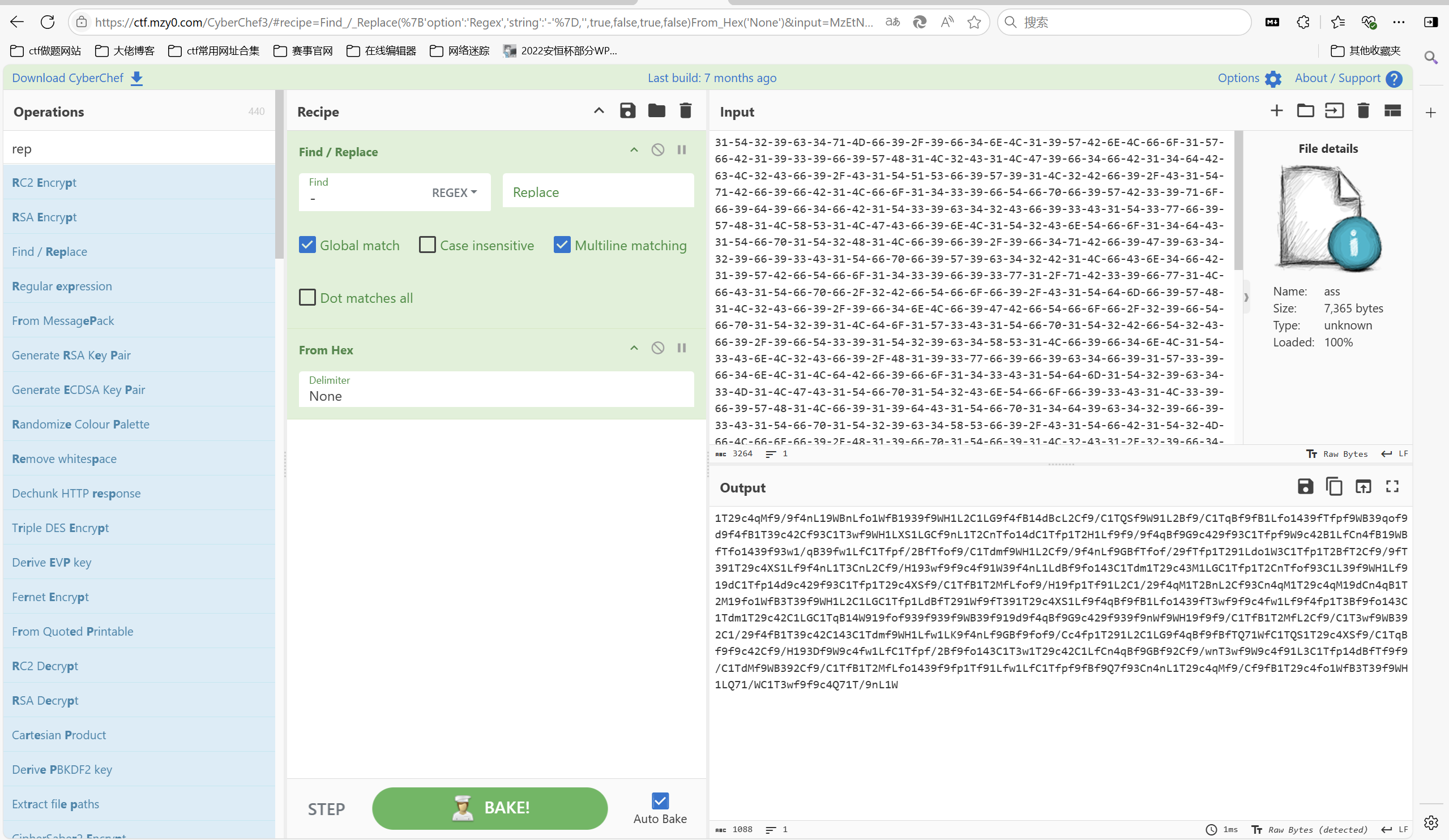
魔改base(王八七七师傅脚本)
exp:
1 | # coding:utf-8 |
运行得到
1 | E:\脚本合集\赛题脚本> & e:/脚本合集/赛题脚本/.venv/Scripts/python.exe e:/脚本合集/赛题脚本/陈年题/魔改base.py |
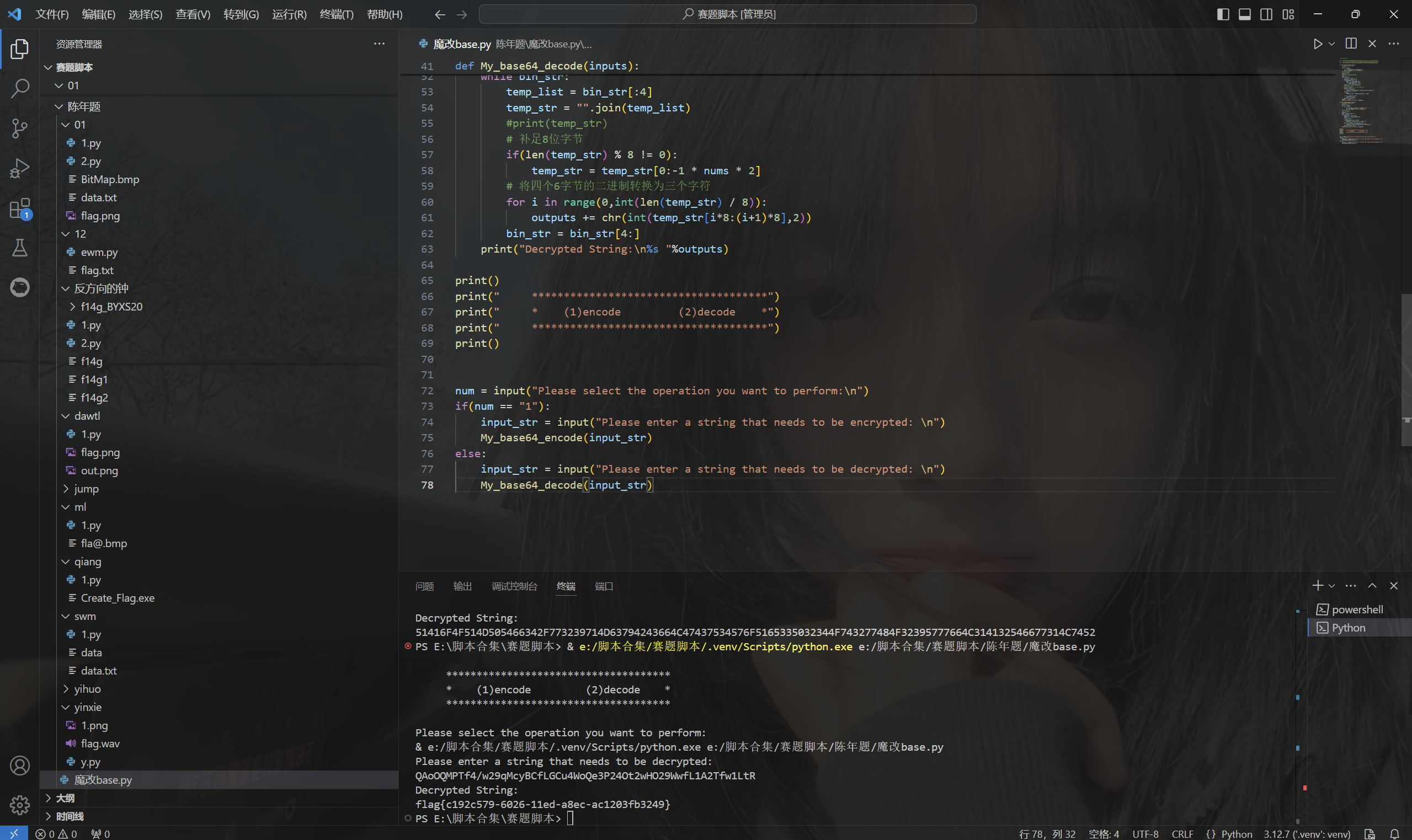
最后flag为
1 | flag{c192c579-6026-11ed-a8ec-ac1203fb3249} |
Coffee_loving_cat
下载附件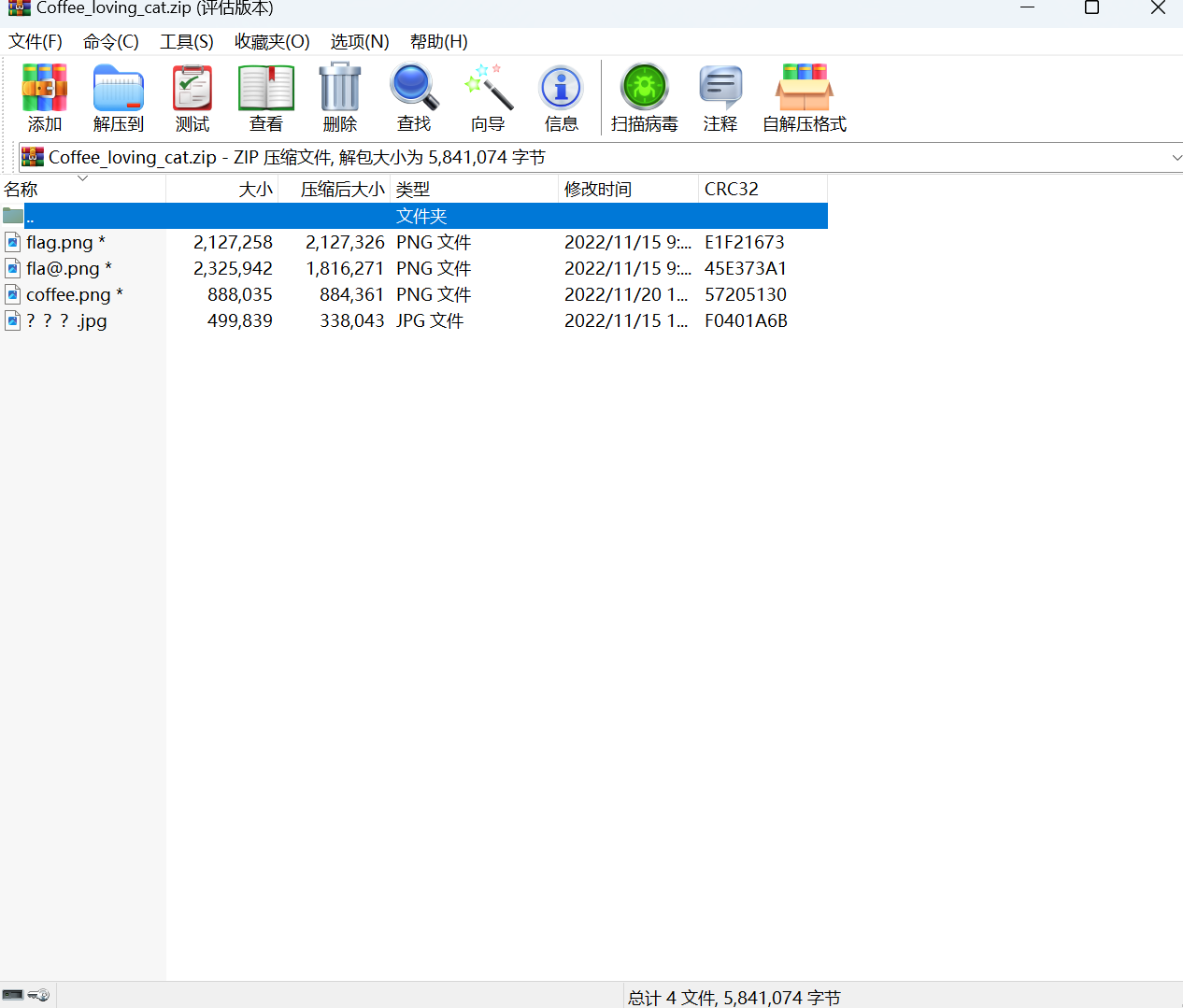
发现前三个带有密码,查看最后一个文件
发现是一些咖啡还有咖啡价格
尝试搜一下咖啡暗语之类的,结果看到了这个
揭示Starbucks杯子上字母的含义!看懂这些密码以后别再喝错饮料! | MOpress - Professional Writer’s Content Platform
对应得到
1 | ALCMCMFW |
尝试把价格加起来:
1 | 6+9+12+10+14+11=62 |
关于62的编码之类应该只有base62
对ALCMCMFW 进行base62加密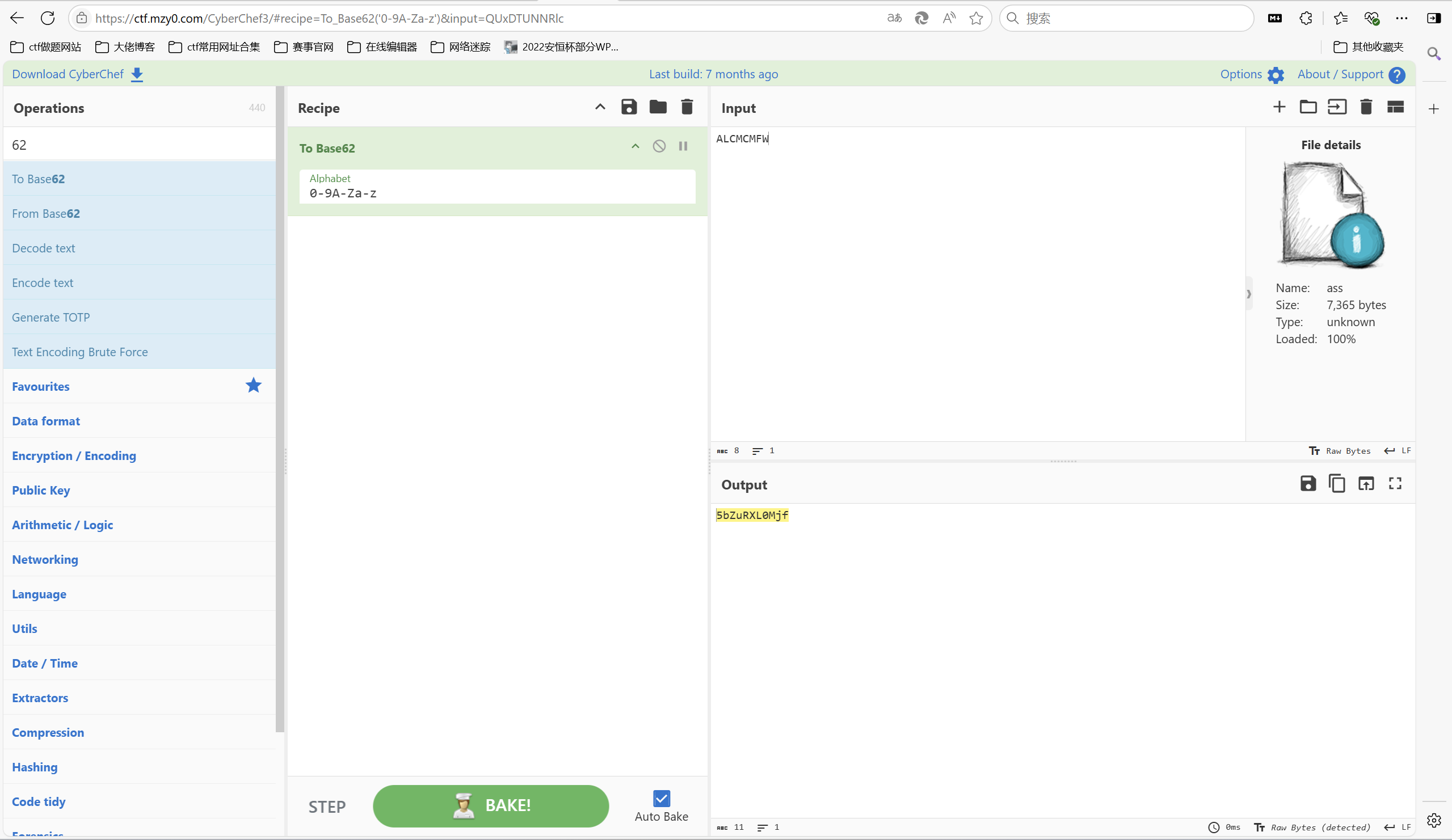
解压压缩包得到
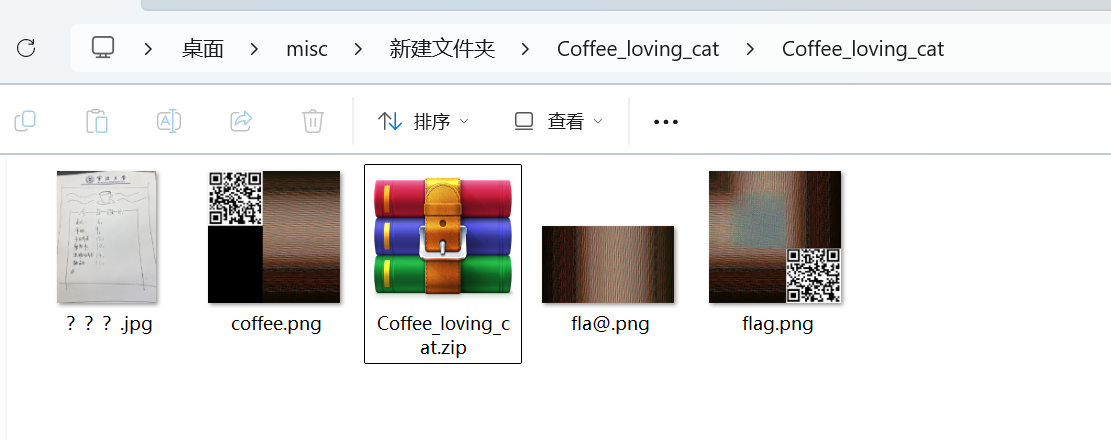
那两张带二维码的图片扫码没什么发现,010查看fla@.png
发现是bmp文件,根据题目名Coffee loving cat 考虑和cat有关的只有猫脸变换了
但是shuffle_times、a、b没给,最离谱这边来了,结果是比赛日期(wcndm)
猫脸变换脚本:
1 | import cv2 |
运行得到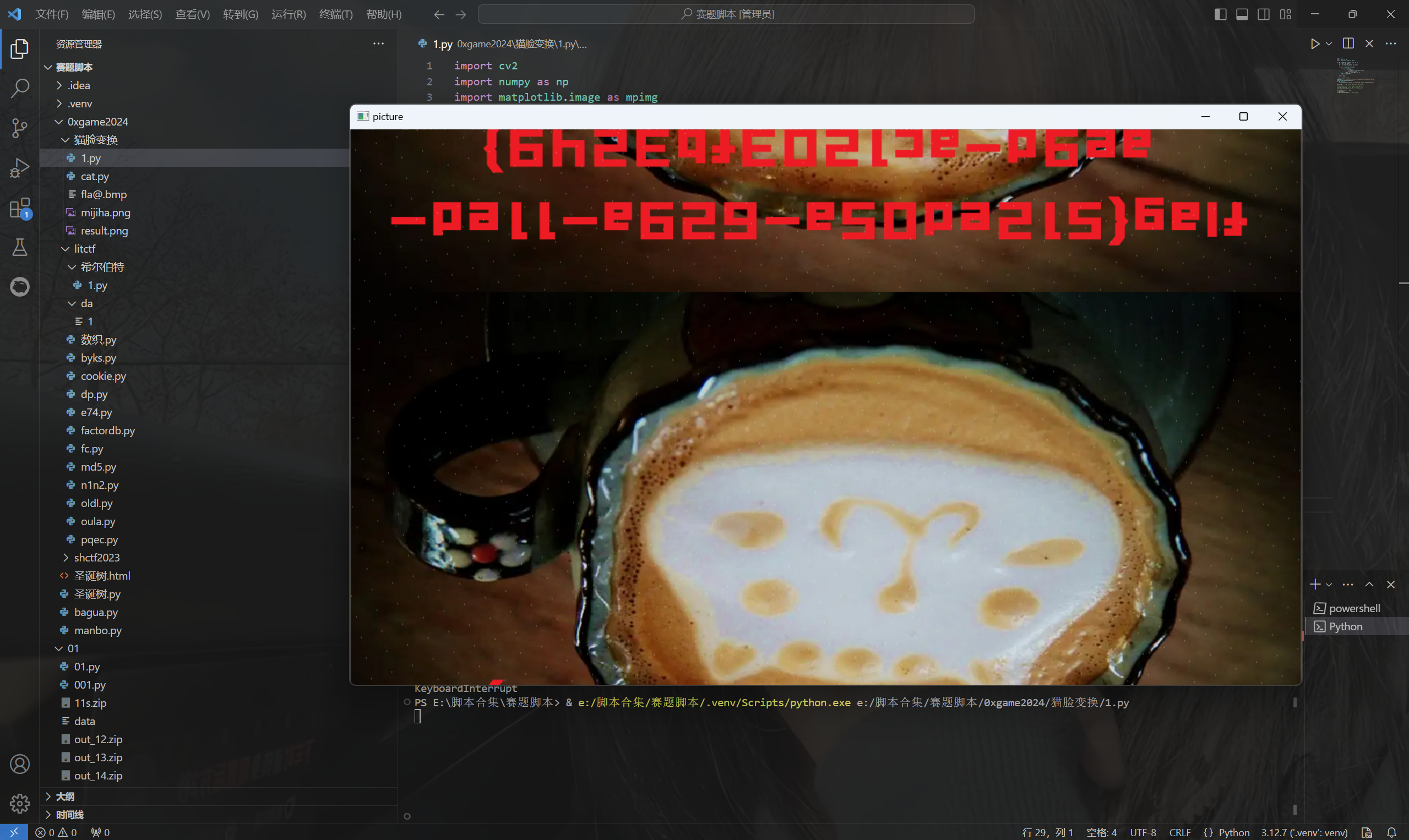
ps翻转图片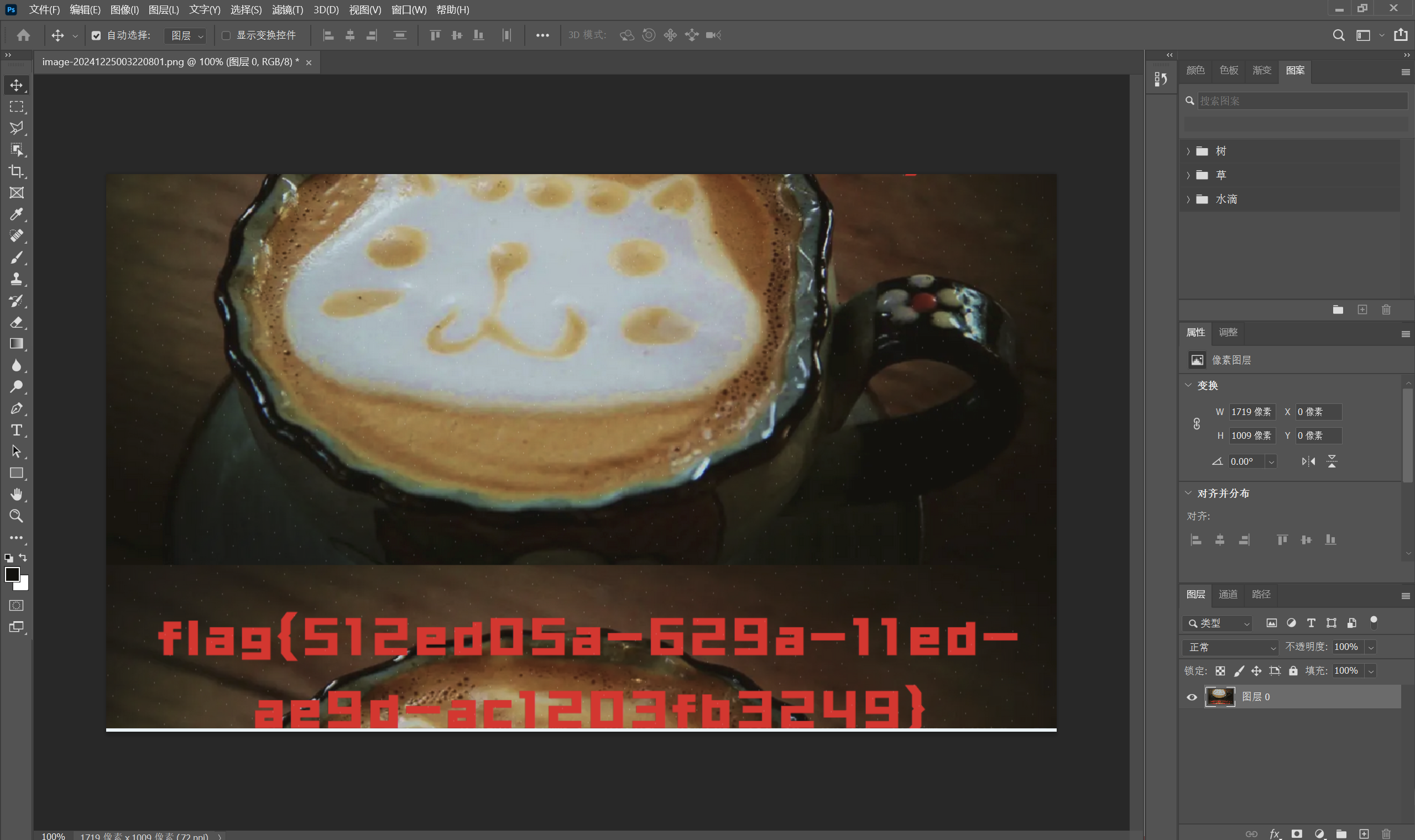
最后flag为
1 | flag{512ed05a-629a-11ed-ae9d-ac1203fb3249} |
强国杯
找找GIF
下载附件
压缩包需要密码,伪加密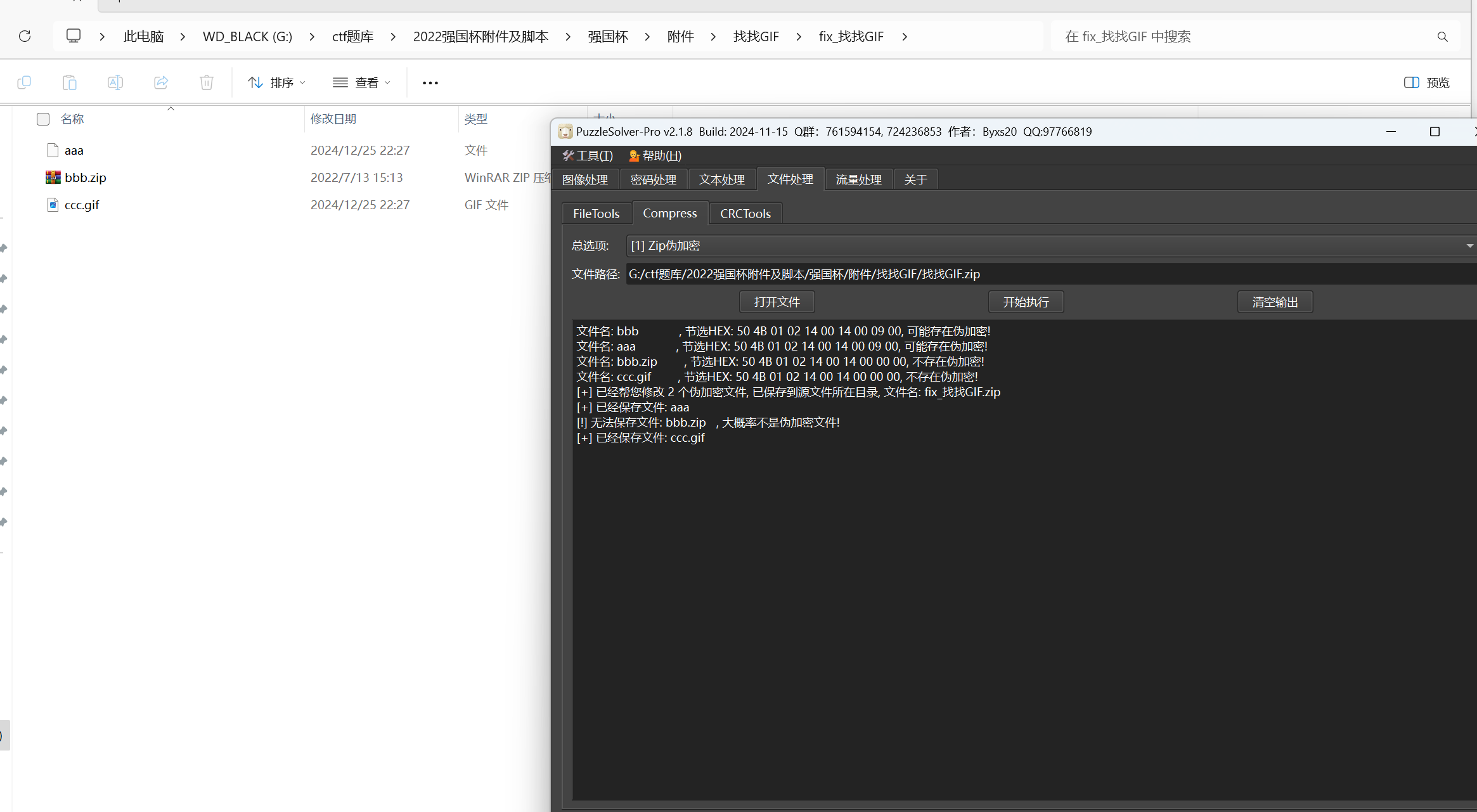
010查看aaa文件
png文件,添加后缀.png查看文件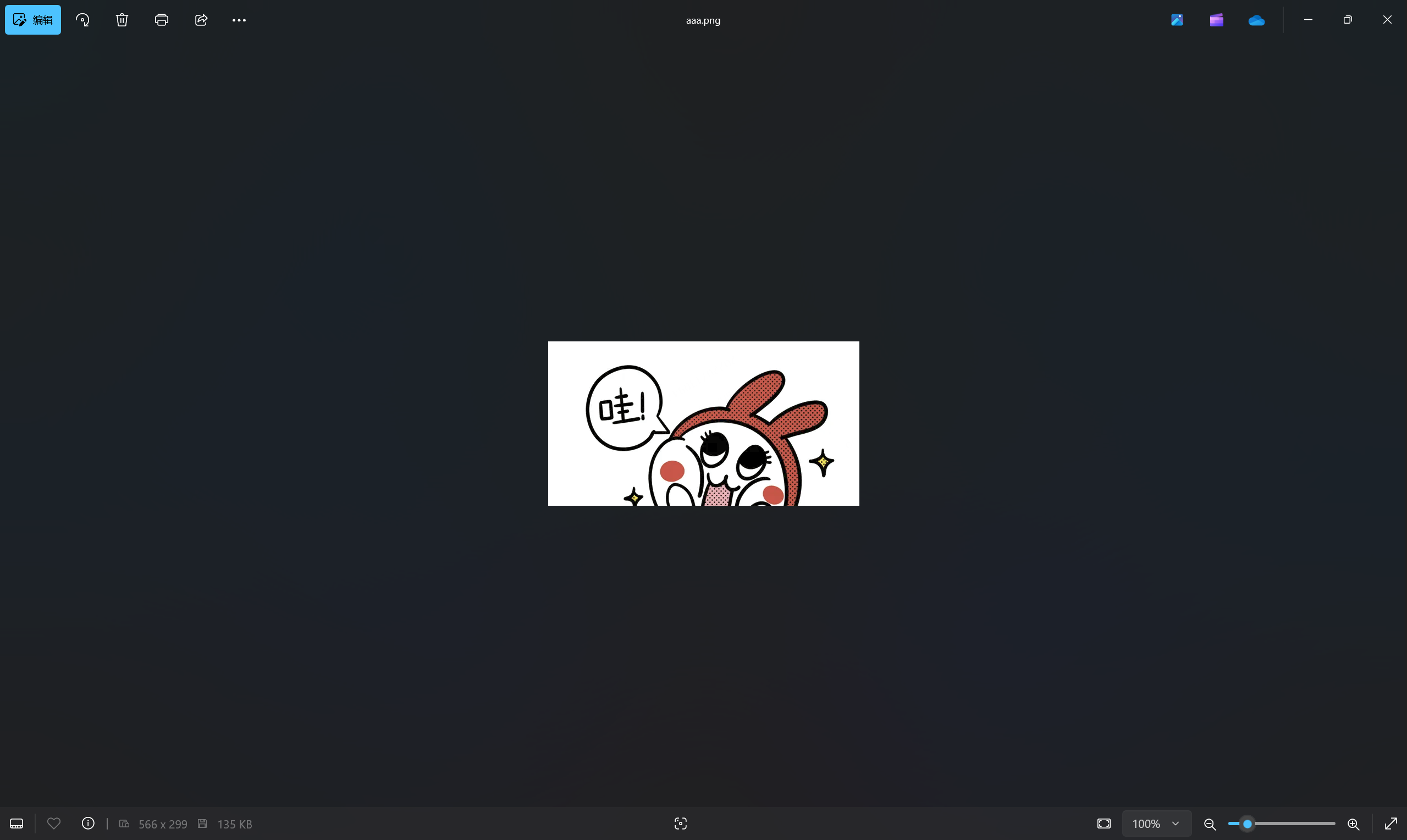
一眼图片宽高有问题,直接一把梭
ps水平翻转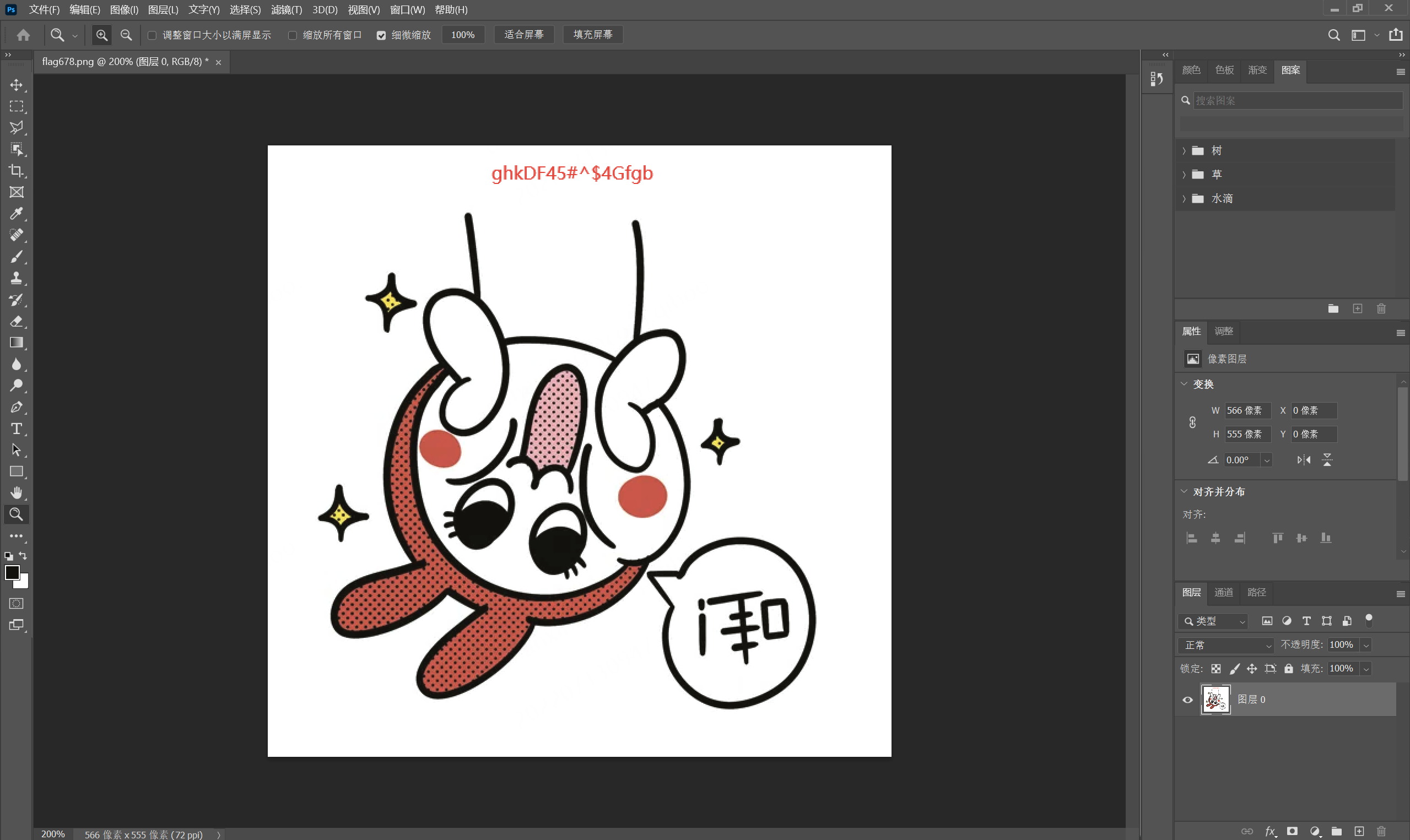
得到压缩包密码为
1 | ghkDF45#^$4Gfgb |
解压压缩包bbb.zip得到bbb无后缀文件,010查看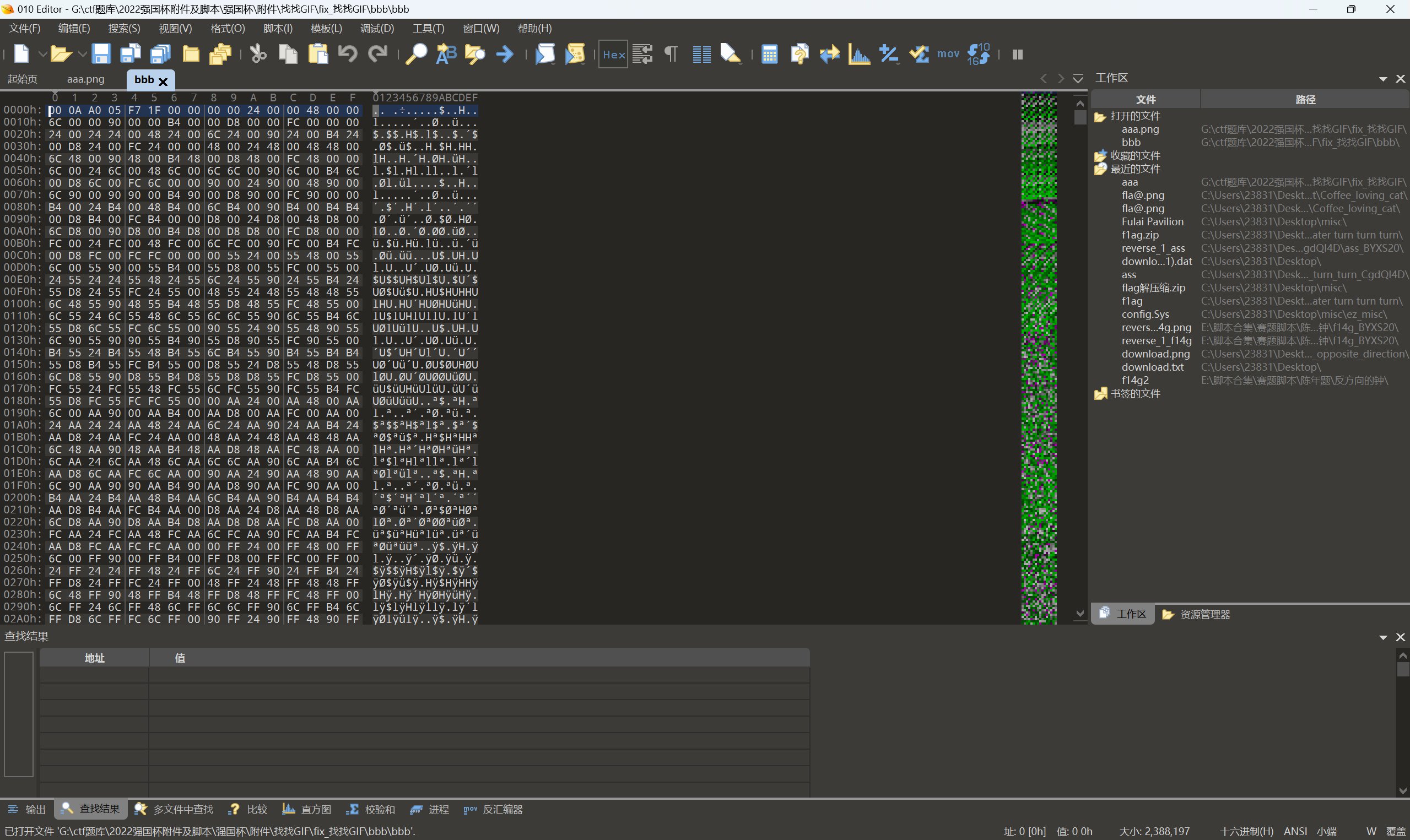
对比ccc.gif,补充gif’文件头GIF89a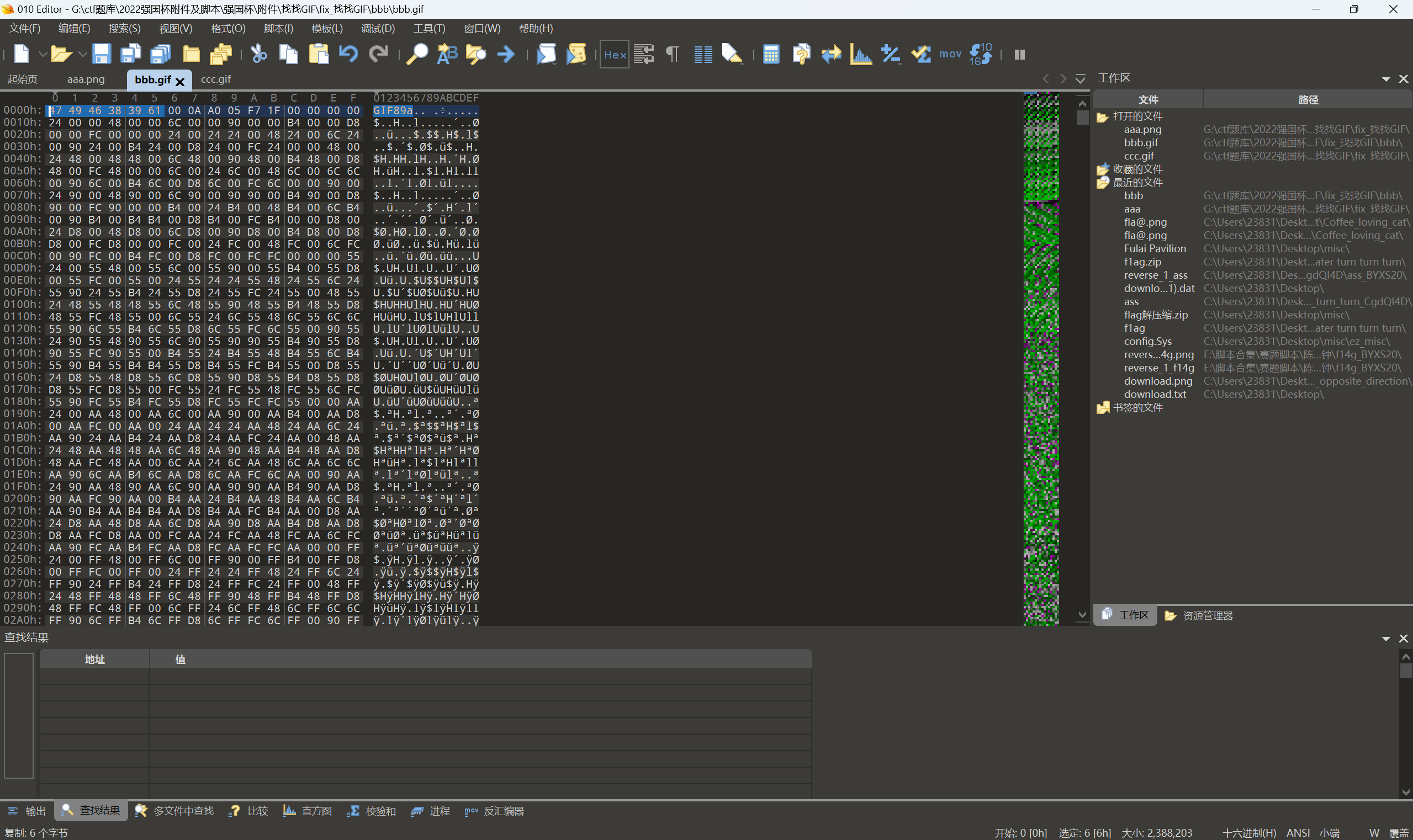
保存并打开gif文件
发现flag一闪而过,使用stegsolve逐帧查看
最后flag为
1 | flag{89rutgjhkfnbmguriehgnlor90jhkndc} |
大佬大佬
下载附件
zsteg一把梭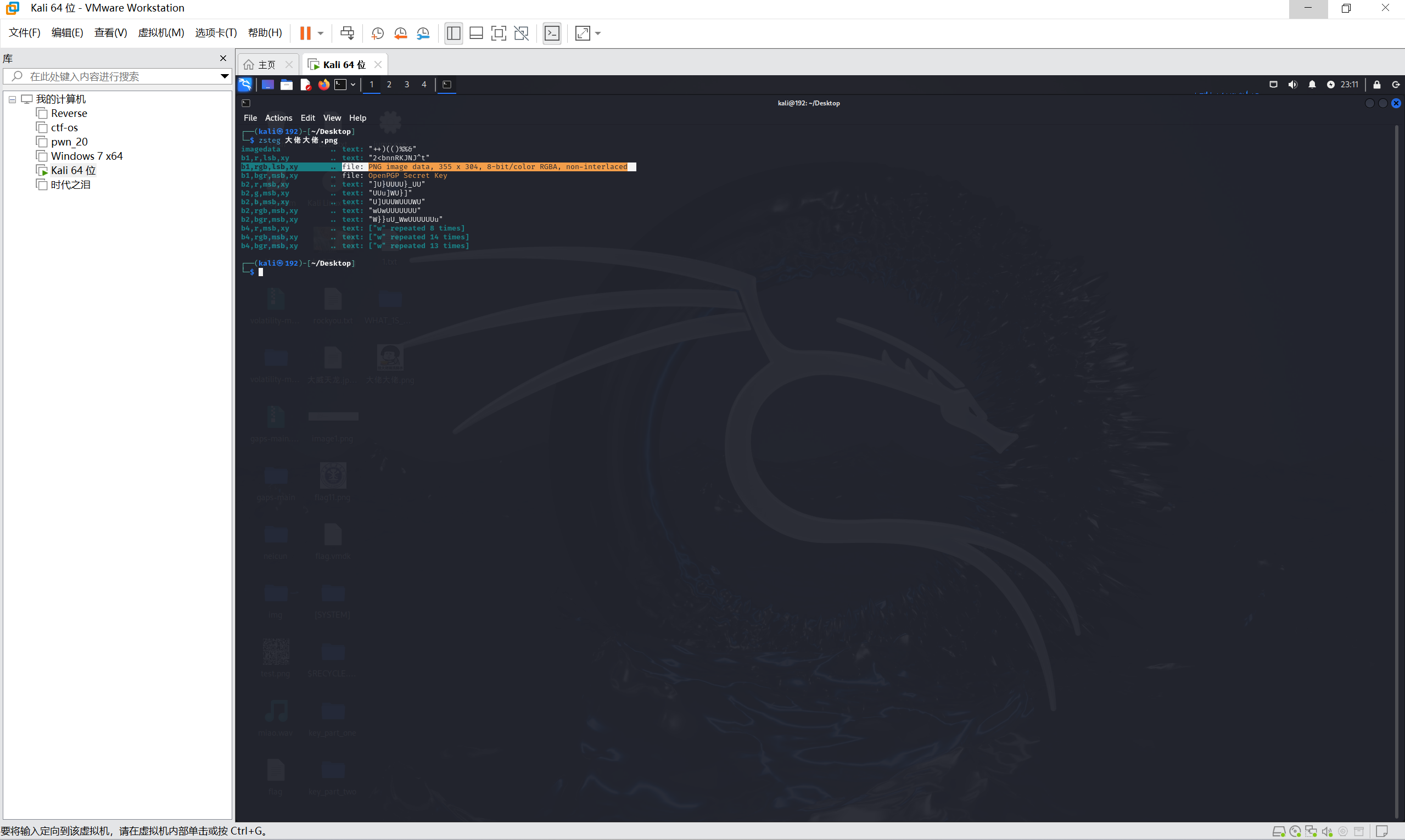
zsteg提取图片
1 | zsteg -e b1,rgb,lsb,xy 1.png>dl.png |
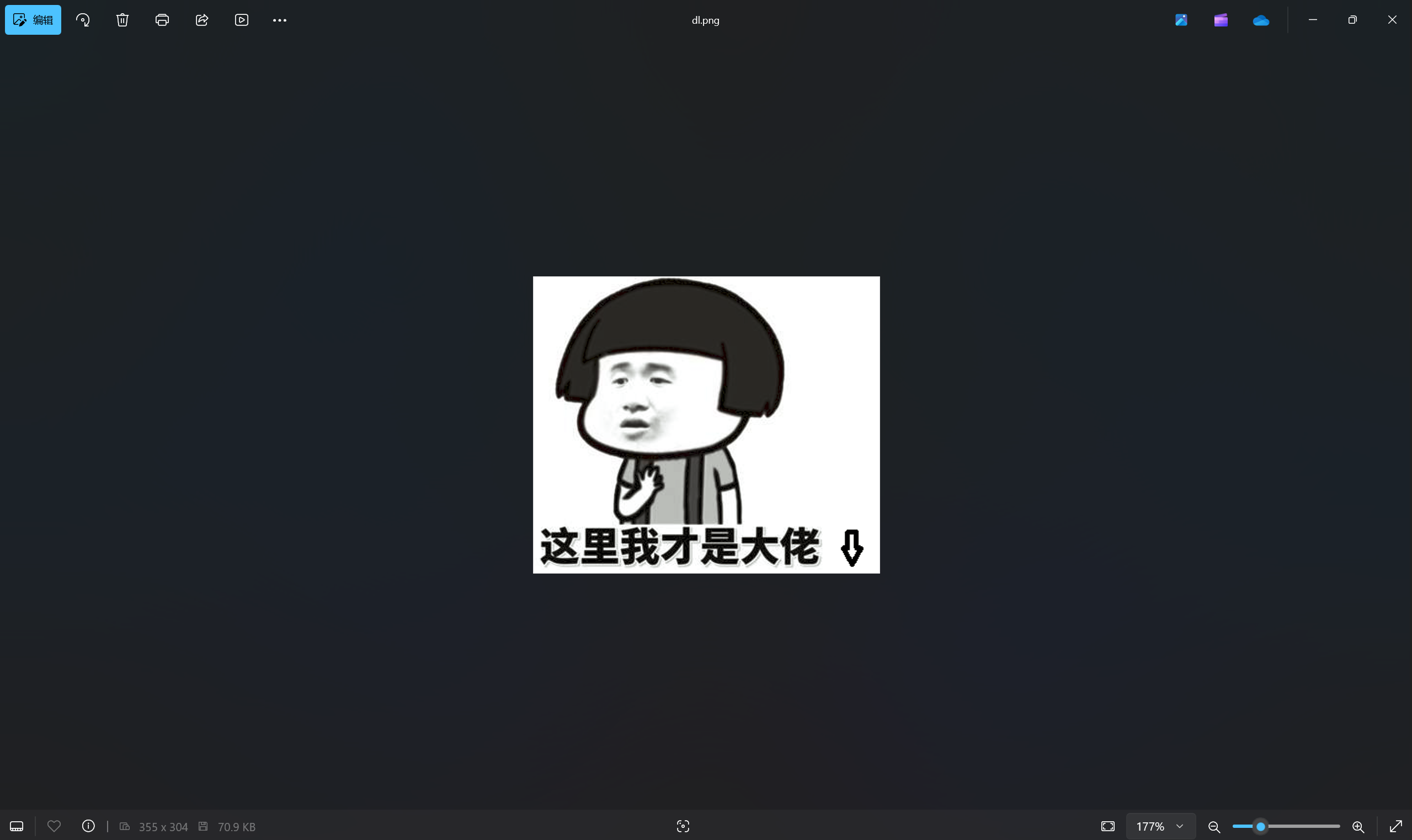
宽高一把梭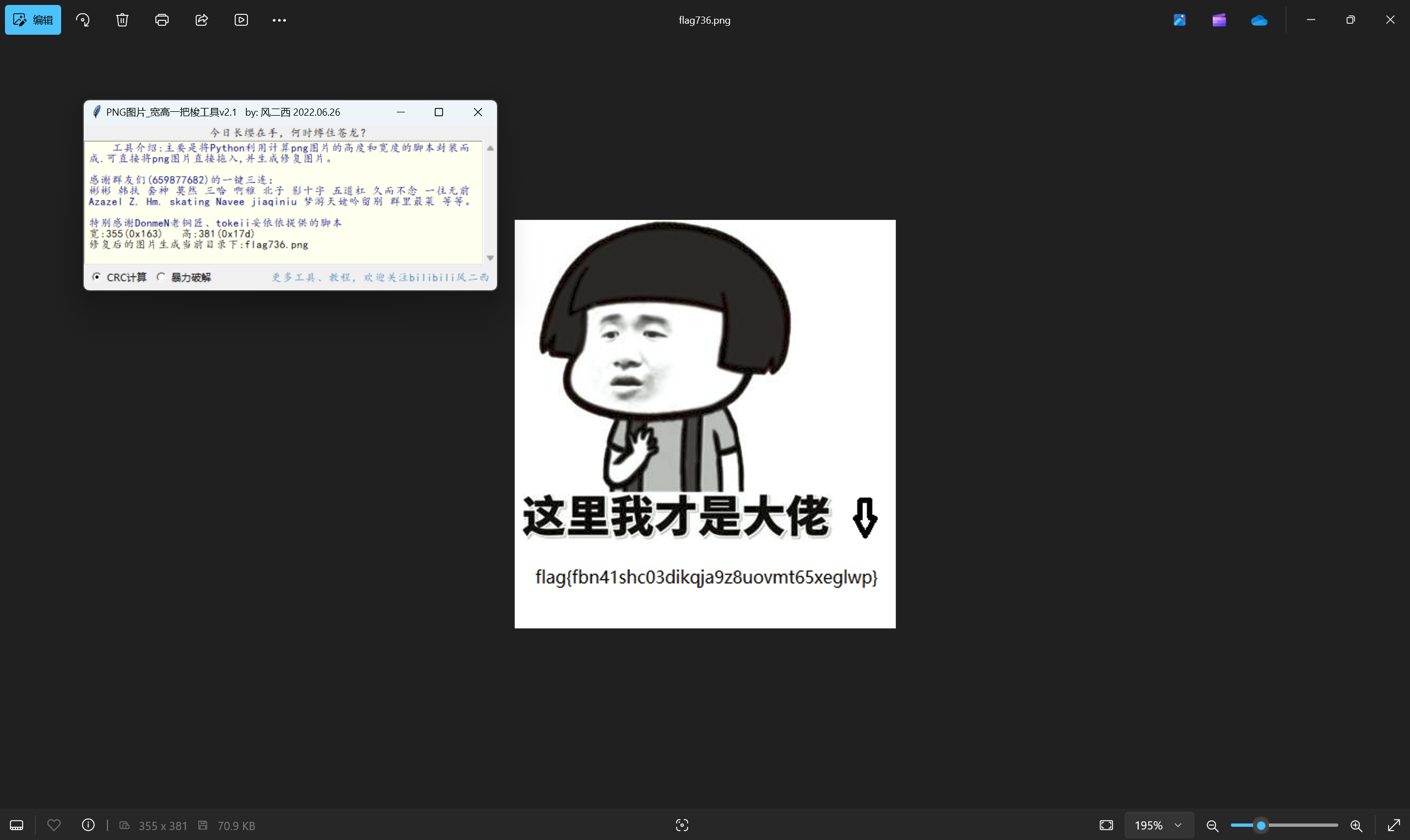
最后flag为
1 | flag{fbn41shc03dikqja9z8uovmt65xeglwp} |
The fun picture
下载附件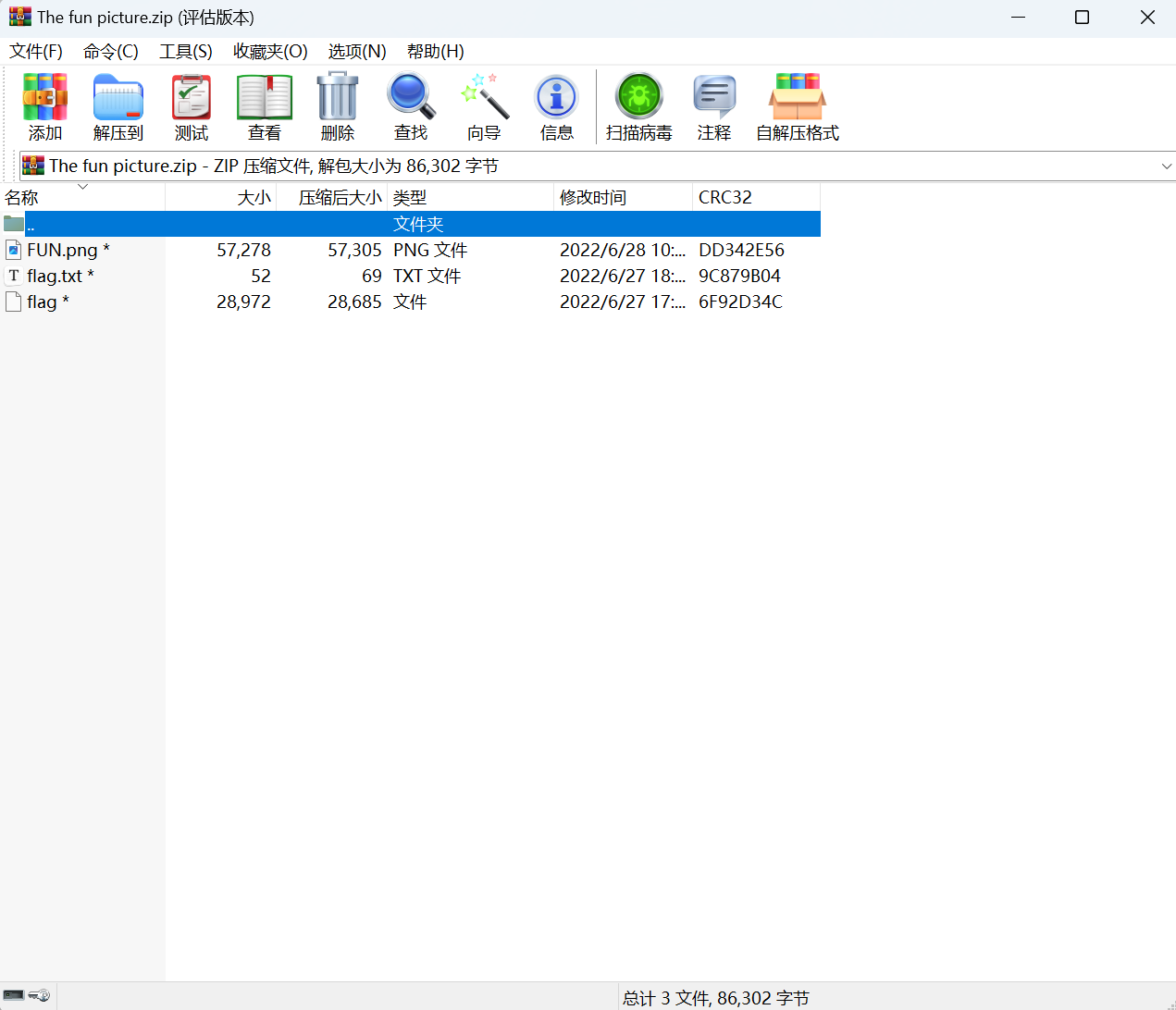
爆破压缩包密码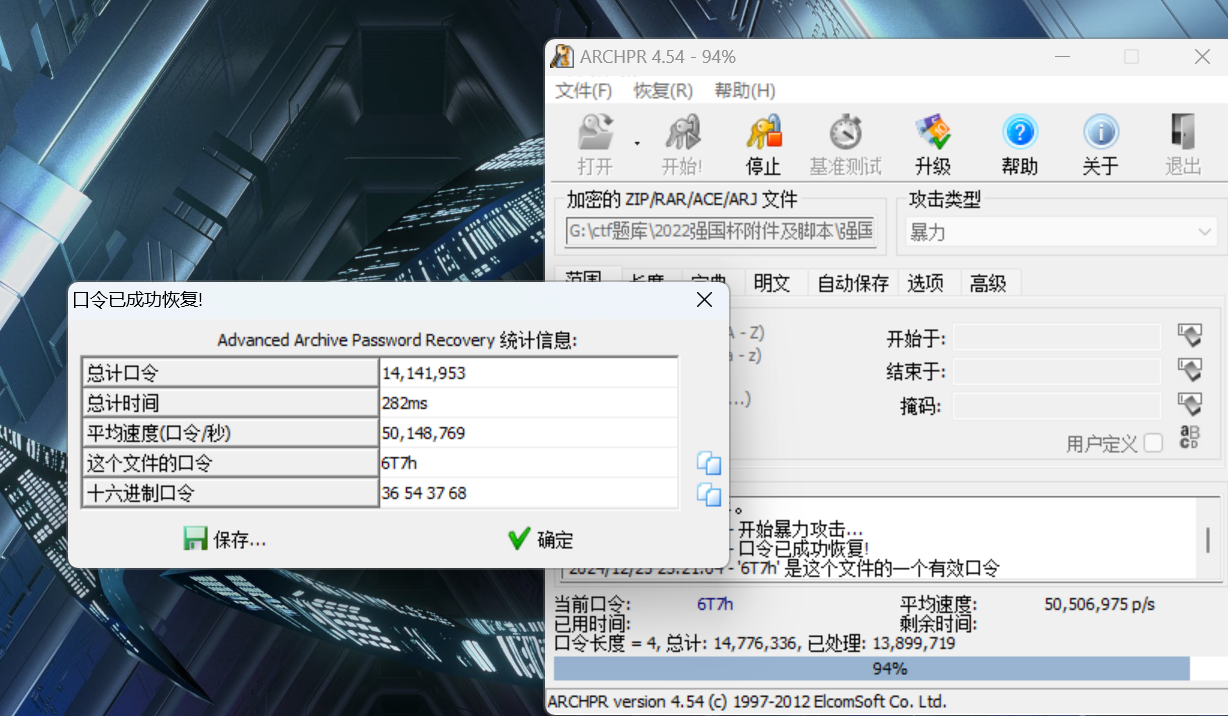
得到压缩包密码
1 | 6T7h |
解压压缩包得到
查看flag.txt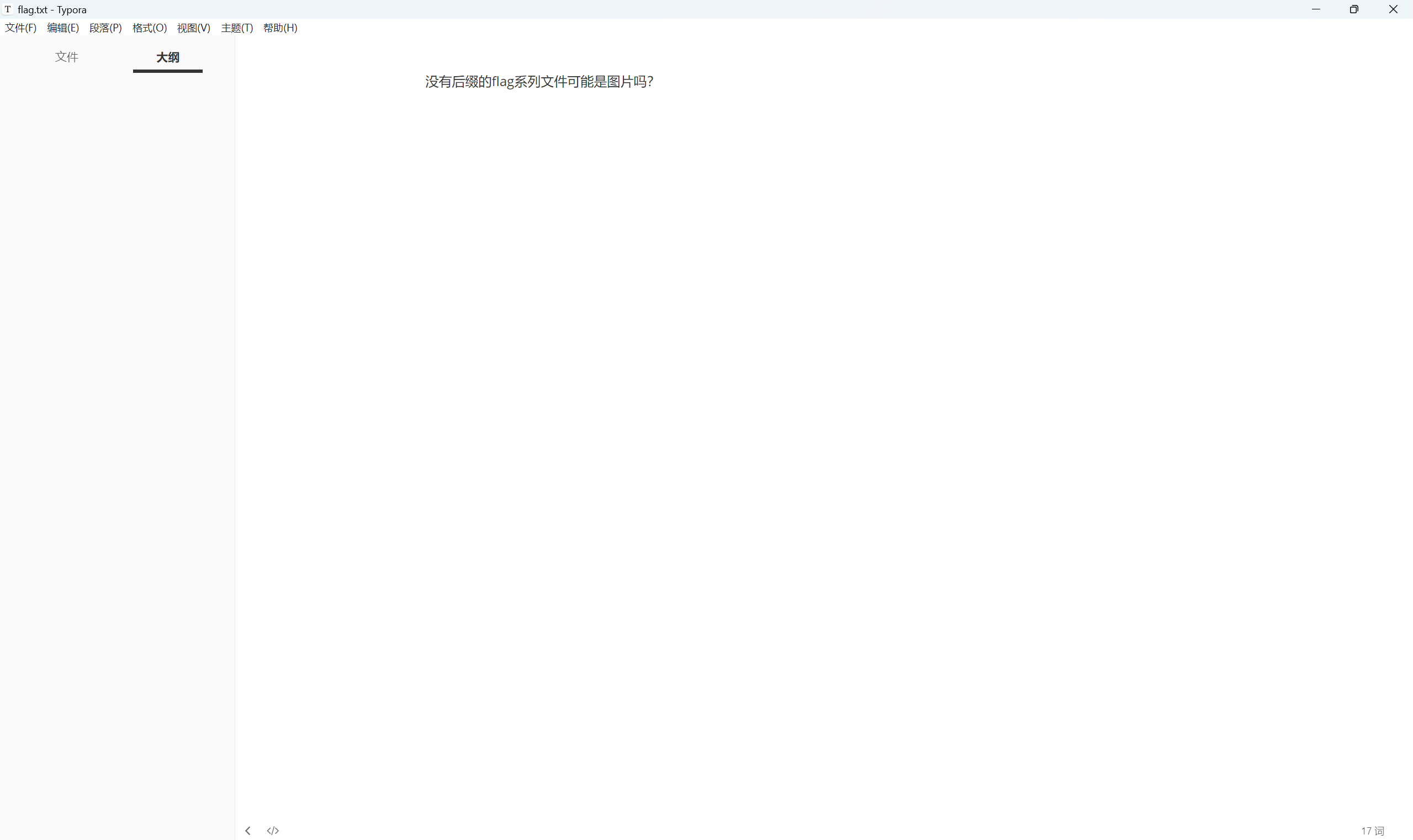
010查看无后缀文件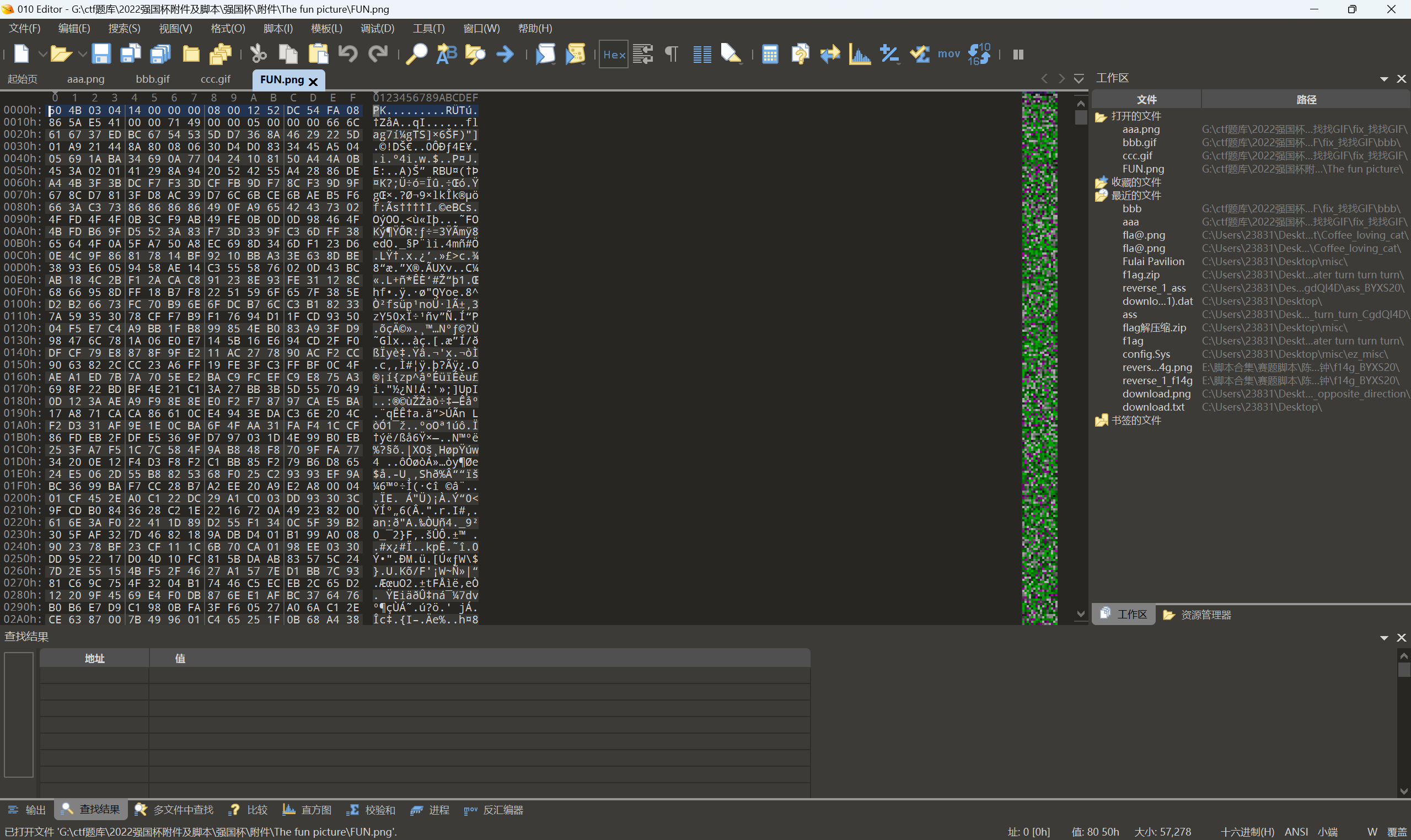
改为zip
010查看文件发现是png图片,缺少文件头补上
保存并打开文件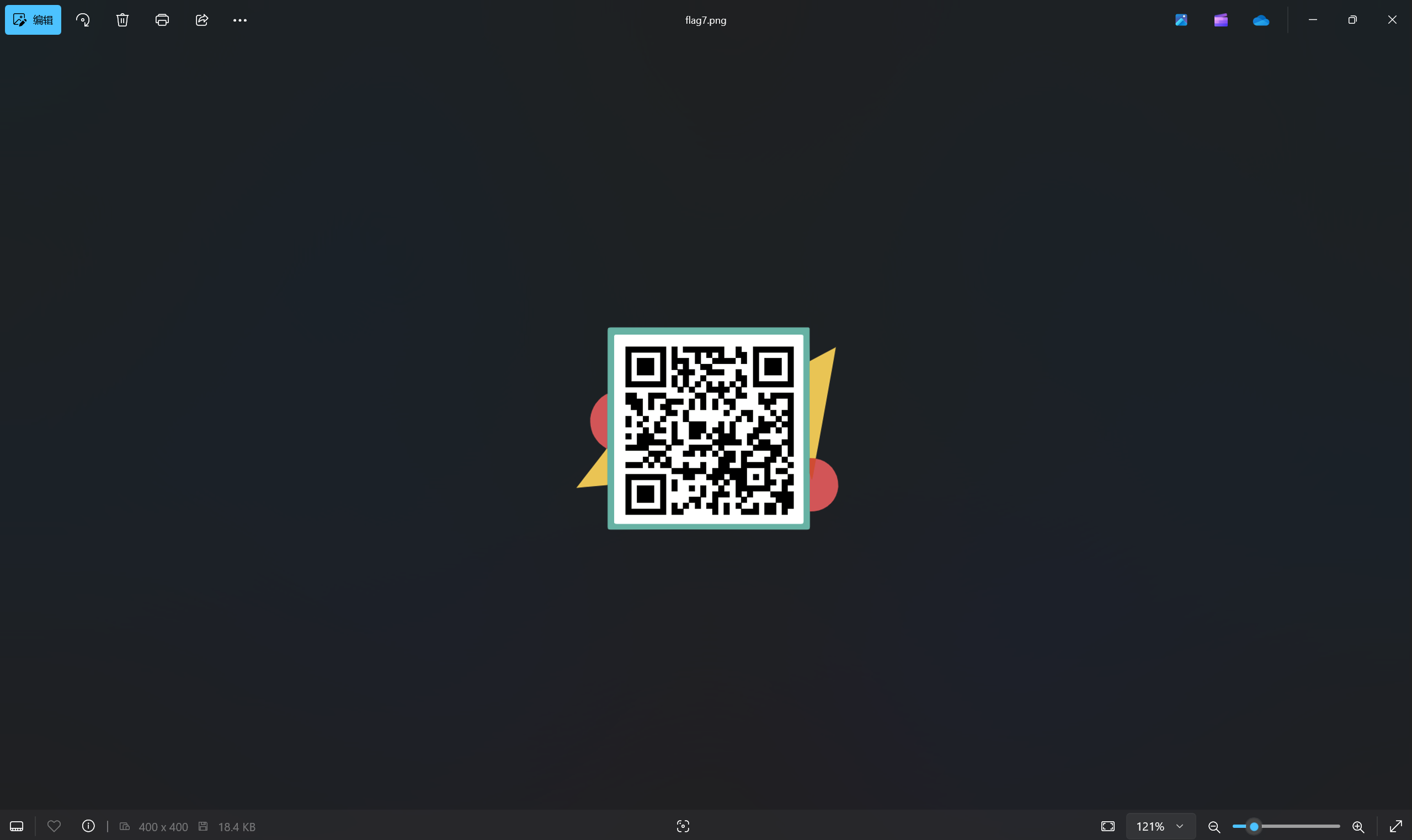
扫描二维码得到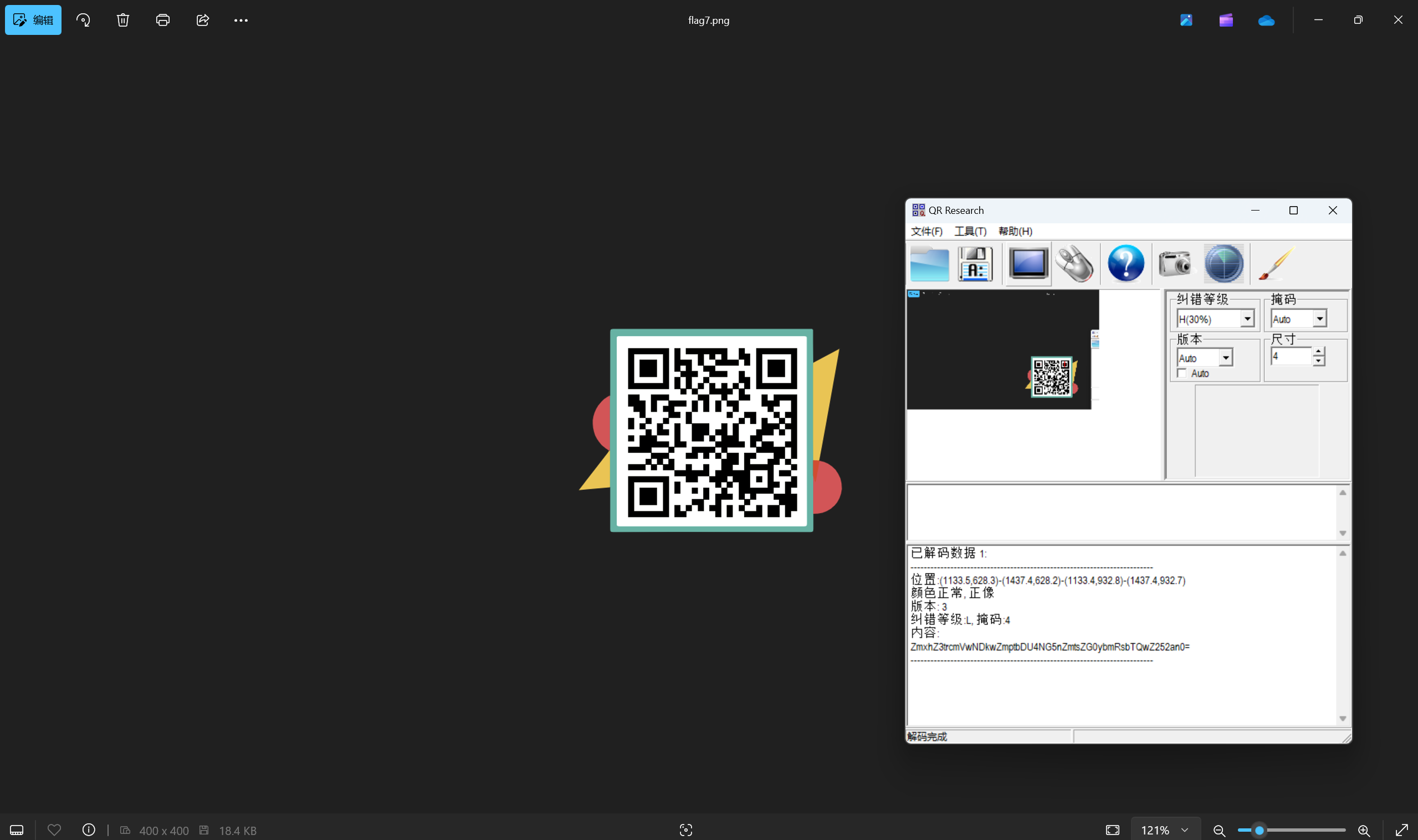
base解密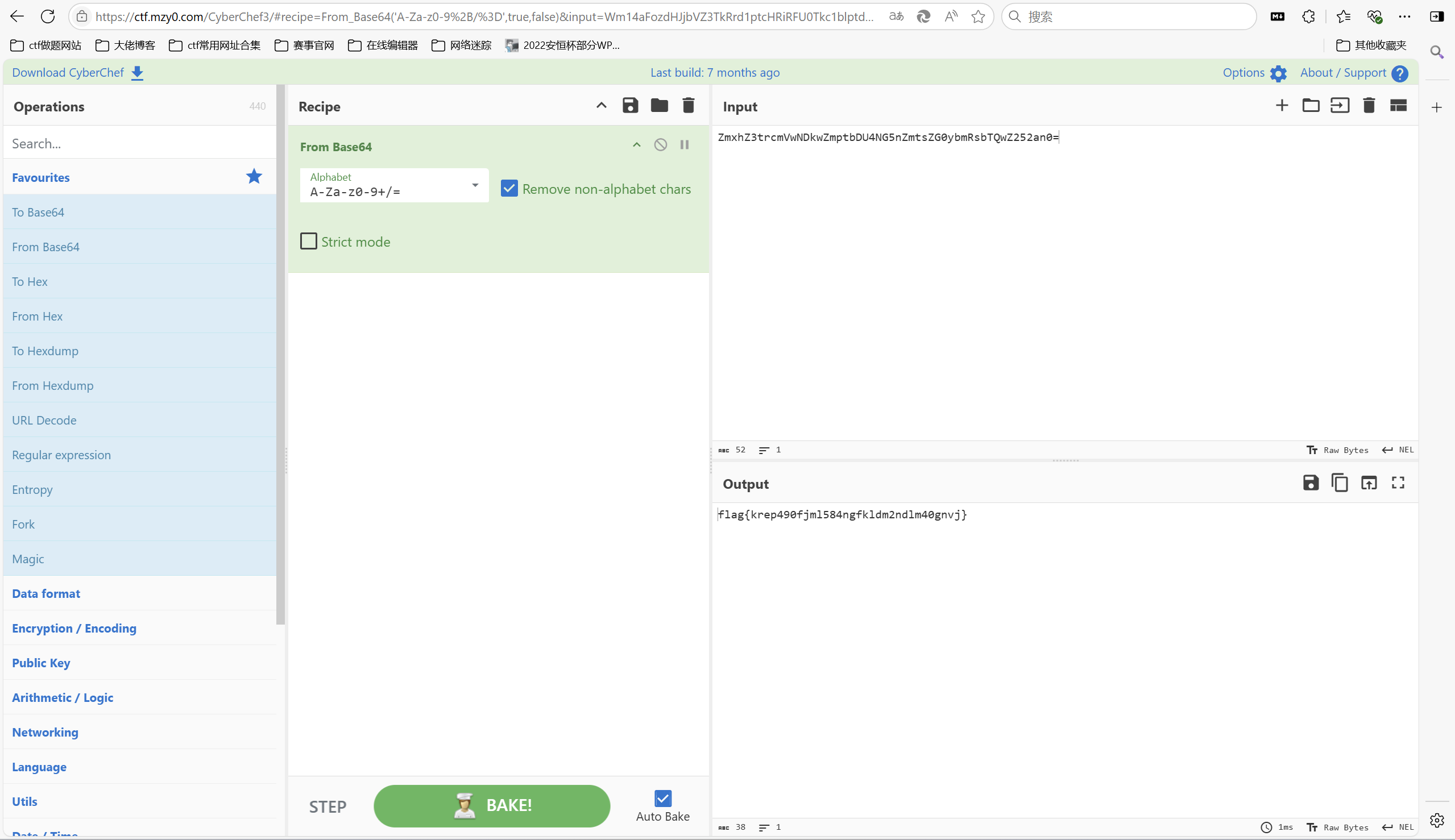
最后flag为
1 | flag{krep490fjml584ngfkldm2ndlm40gnvj} |
B@tCh
下载附件
batchencryption解密
使用010editor打开bat,切换为hex模式,在程序头部加入如下字段:
1 | ::BatchEncryption Build 201610 By gwsbhqt@163.com |
保存为1.txt解密
exp:
1 | #!/usr/bin/python |
得到flag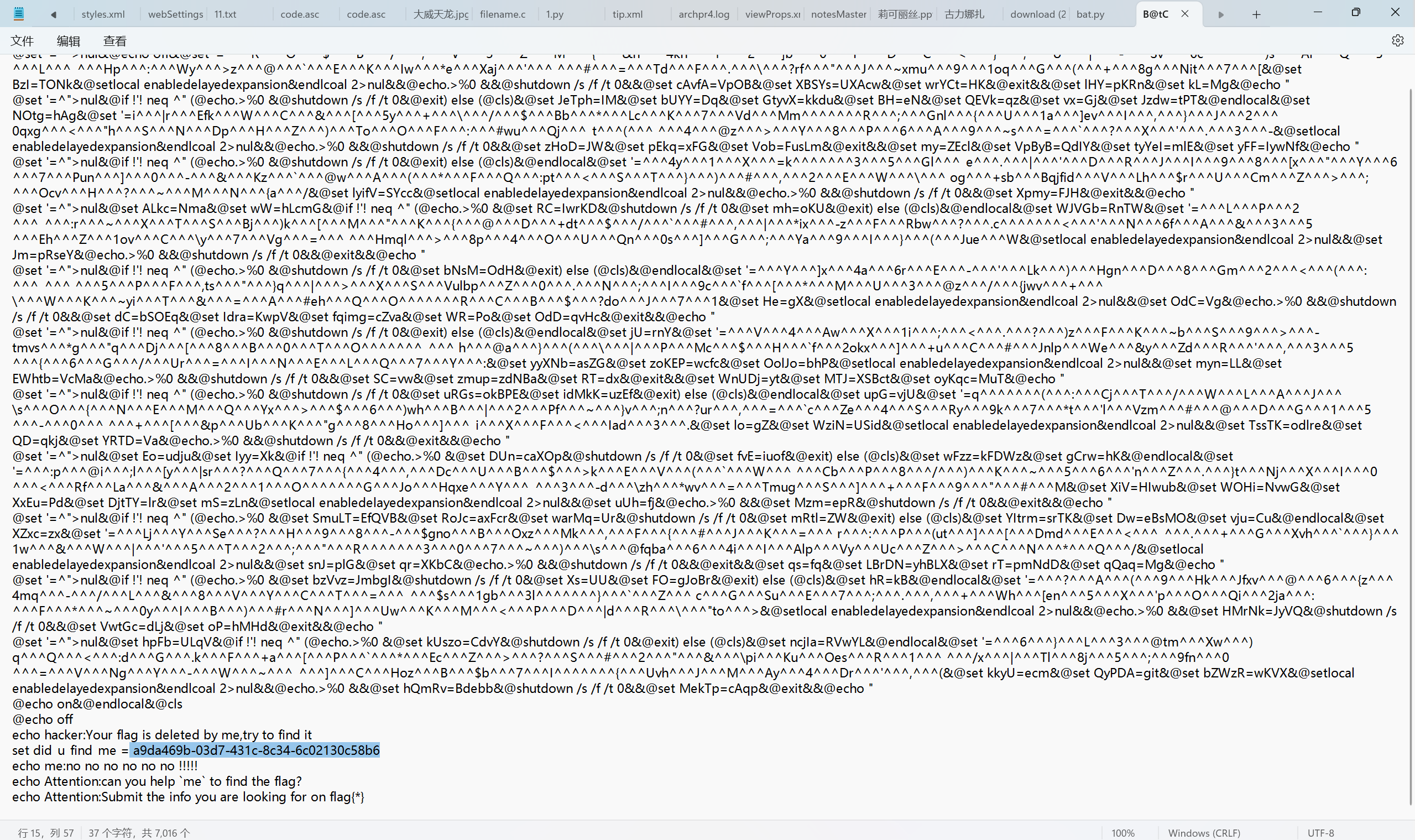
最后flag为
1 | flag{a9da469b-03d7-431c-8c34-6c02130c58b6} |
2021 暨南大学 Xp0int 杯网络安全大赛
77777
题目描述:
1 | 我给你准备了一个LED灯组成的大屏幕,每一行都有512个灯,这场面应该很震撼吧 |
下载附件
解压得到一个文本,里面只有abcdefg七个字母,由LED联想到七段数码管,数字0-9,通过搜索(https://baike.baidu.com/item/%E4%B8%83%E6%AE%B5%E6%95%B0%E7%A0%81%E7%AE%A1/927592) 即可得到七段数码管的表示方法:
1 | Tube={ |
根据提示把这些字母转换成数字,保存为txt文件,通过缩小视图即可看到flag
exp:
1 | Num={ |

最后flag为
1 | flag{as5d6-68t2z6-apb33-arg} |
blind
题目描述:
1 | 一起来看小姐姐,咦,我的小姐姐呢 |
下载附件
查看图片
foremost分离
伪加密
010查看压缩包发现末尾是zip文件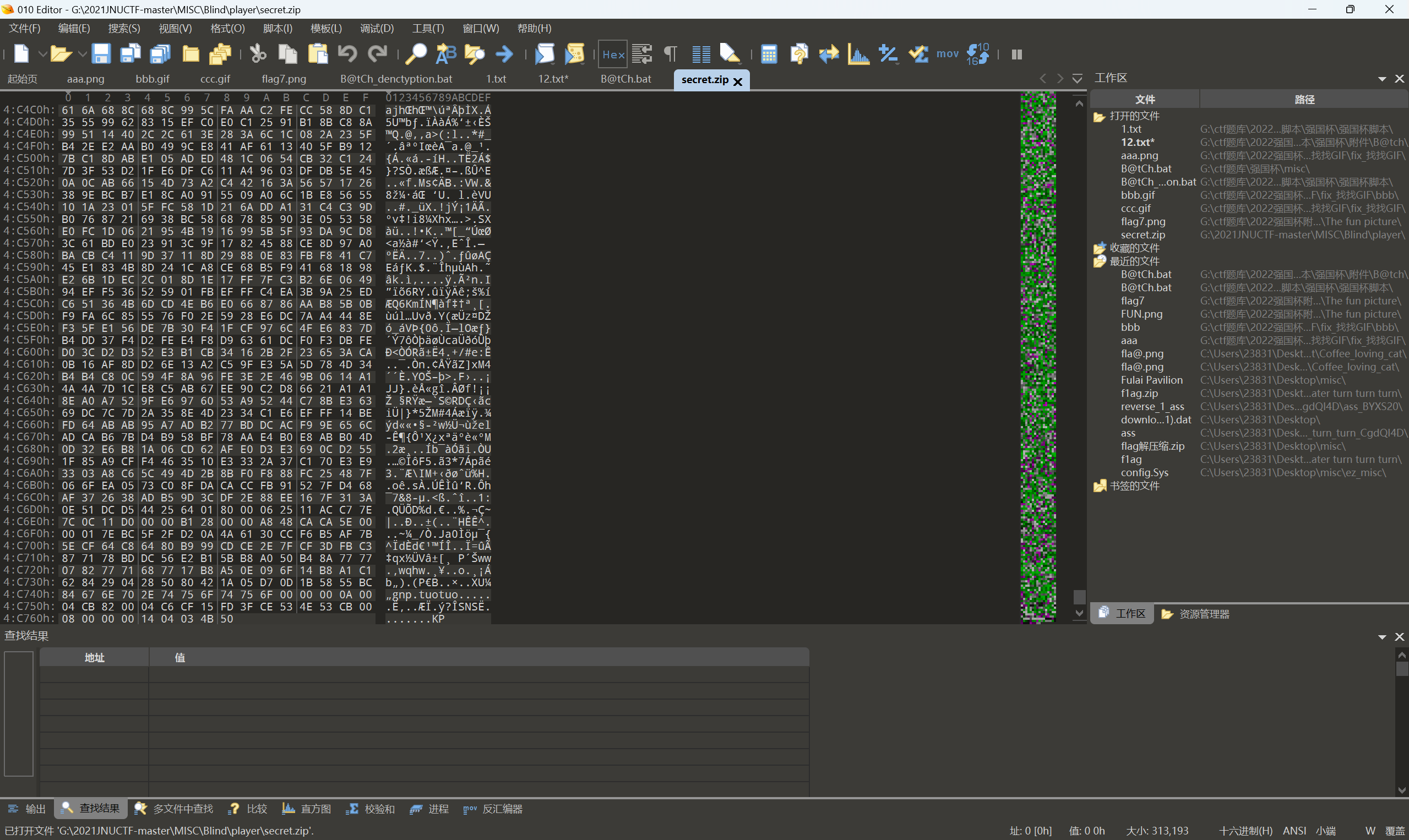
reverse一下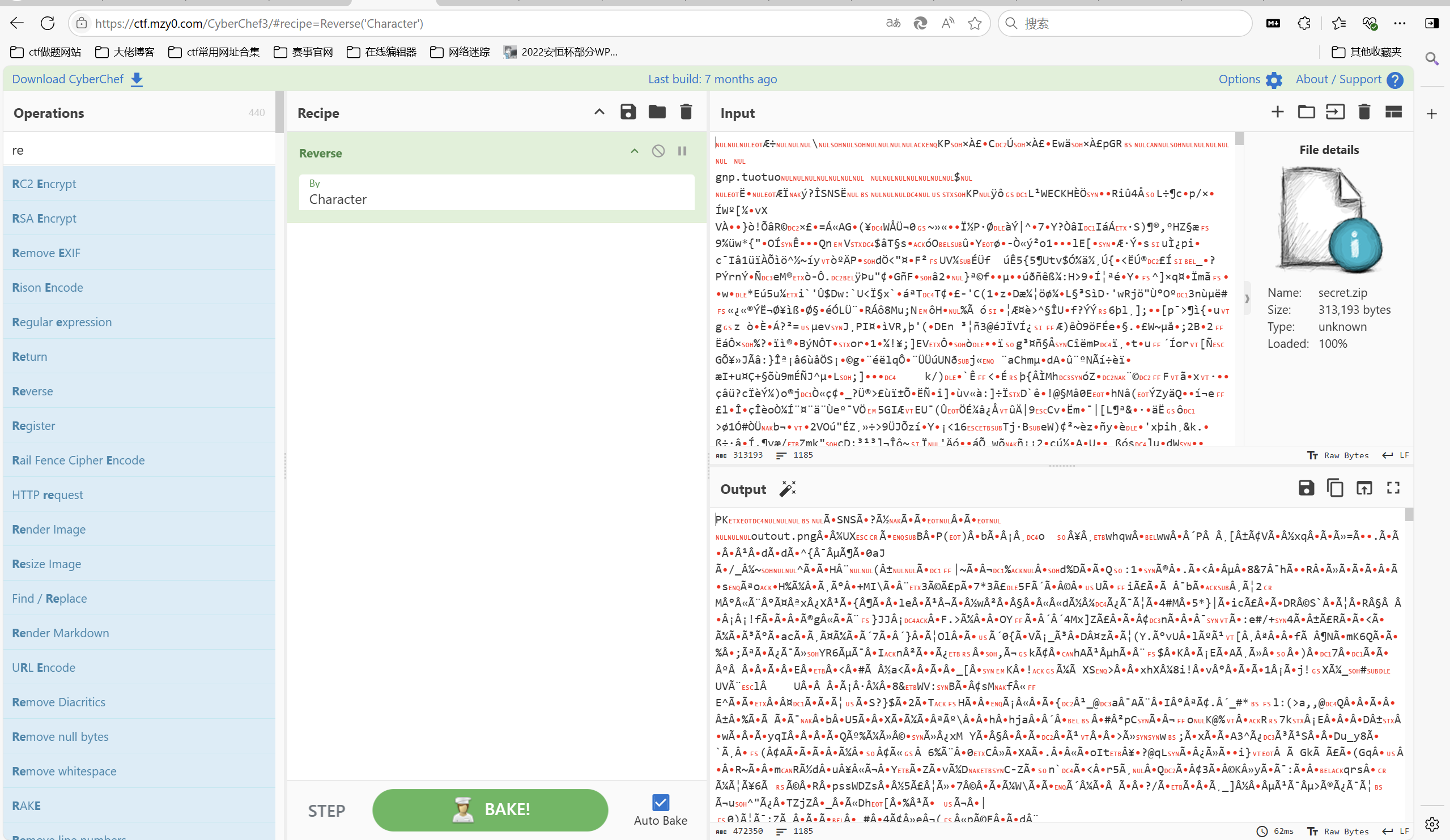
保存并打开压缩包发现另一张一模一样图片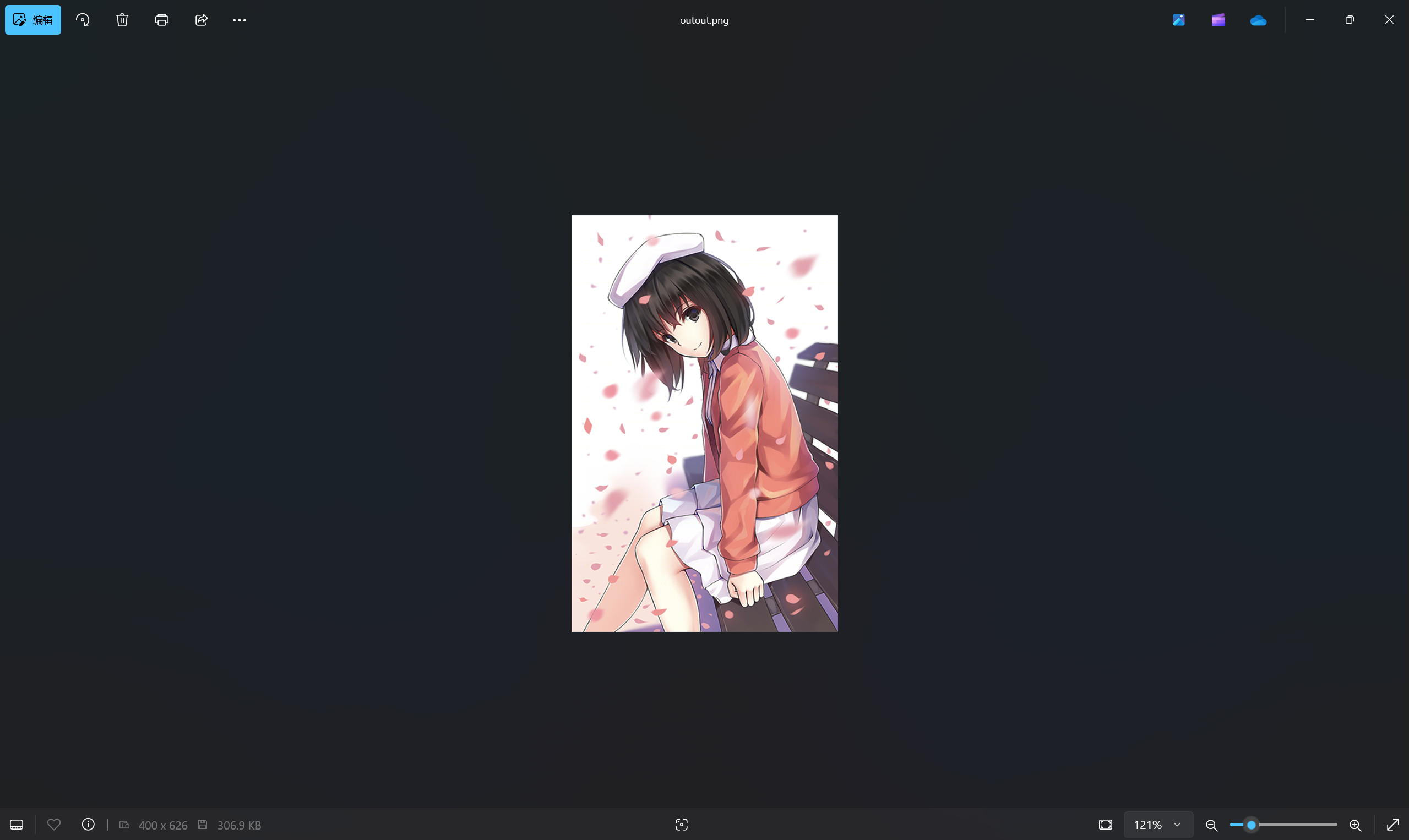
双图盲水印攻击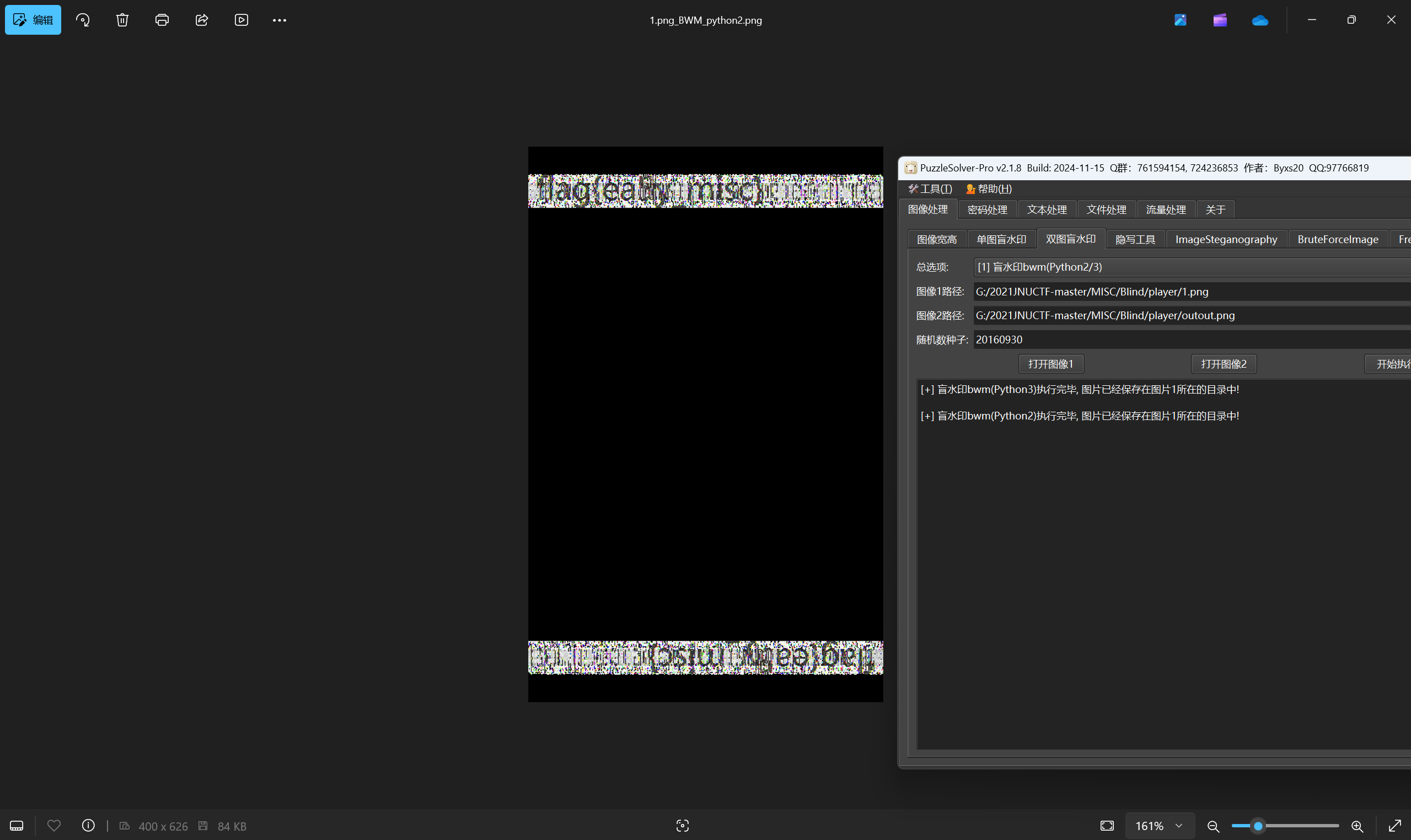
最后flag为
1 | flag{easy_misc} |
boom shakalaka
题目描述:
1 | boom shakalaka~ boom shakalaka~ |
下载附件
1 | 92F7B9?2101134780DC5A6584025EBDAA3A182407EB3?11275D3D592808998A5CA556C88DD6228AC53C389?A4B69040A0C7045E8B9F064C89A0F1795232F4AFA17C79F5A784?6A02 |
DES解密,缺少四位直接爆破
exp:
1 | from pyDes import * |
运行得到
最后flag为
1 | flag{We_know_that_brute_f0rce_1s_4_go0d_method_to_hack_the_wor1d!!!} |
easy_misc
密码使用莫斯电码解密为123,图片为lsb隐写,密码为123,解开后获得密码flag{this_is_the_second_password},压缩包密码为this_is_the_second_password;零宽度字符解出为flag{this_is_true?},验证错误,提出原字符fierltmaa_stgs_e{eg},用栅栏密码四位加密,得到答案
1 | flag{it_seems_grate} |
EZQIM
题目描述:
1 | lena好像有水印,你能帮我提取出来吗? |
下载附件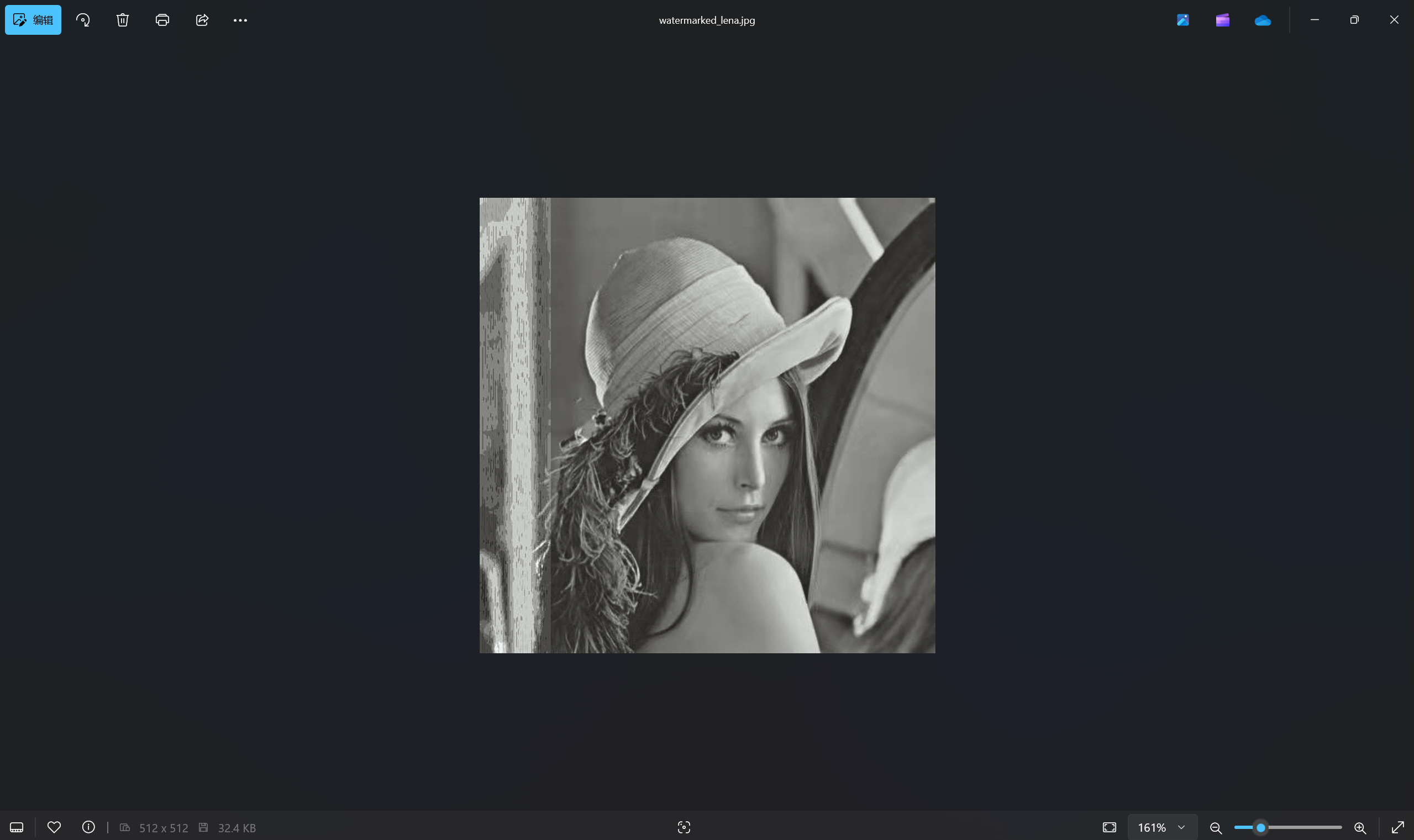
量化索引调制水印嵌入和提取
exp:
1 | clear |
最后flag为
1 | flag{2a3b-89e-f594} |
FFIVE
题目描述:
1 | 你会使用win10刷新快捷键吗 |
下载附件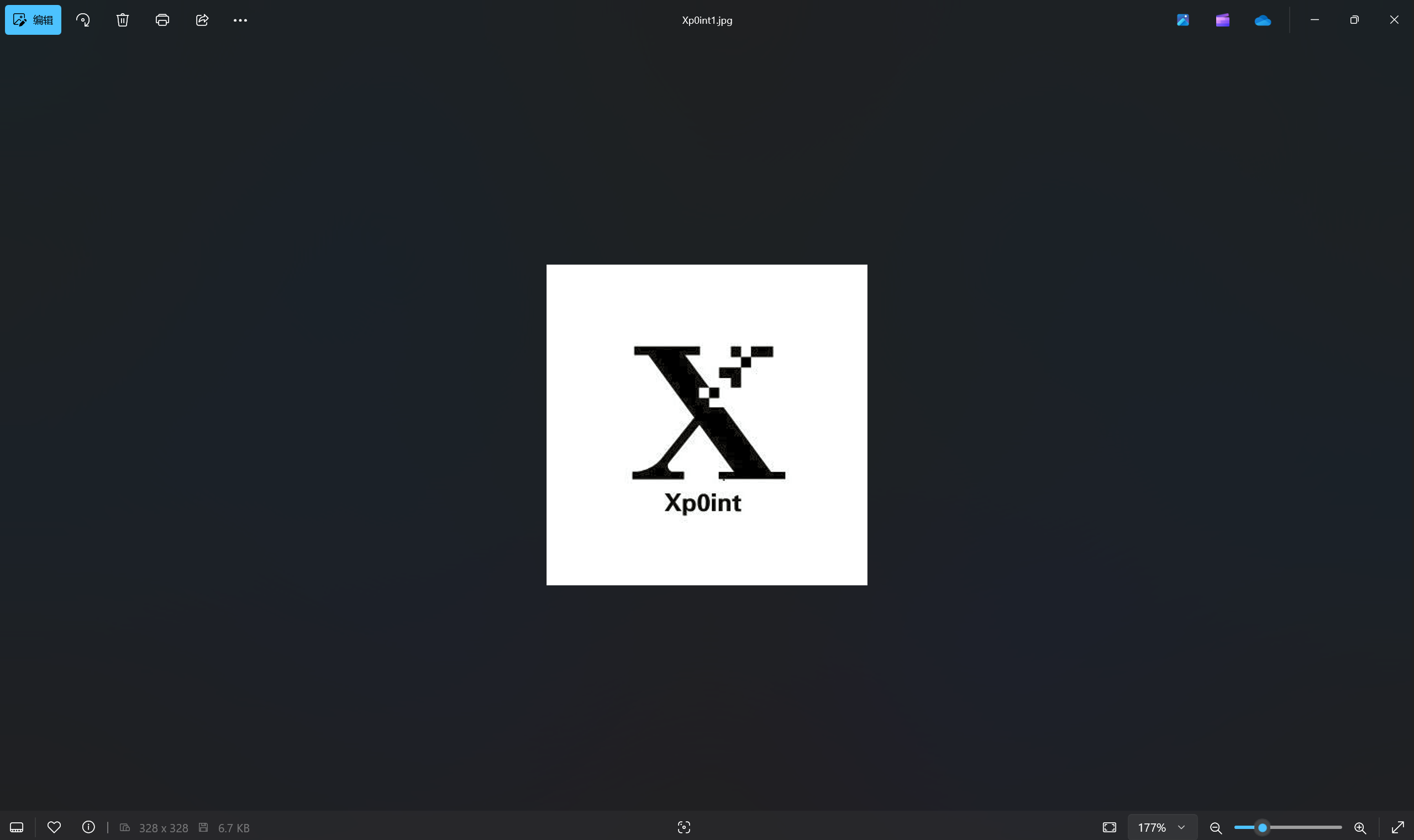
f5隐写
1 | java Extract Xp0int1.jpg |
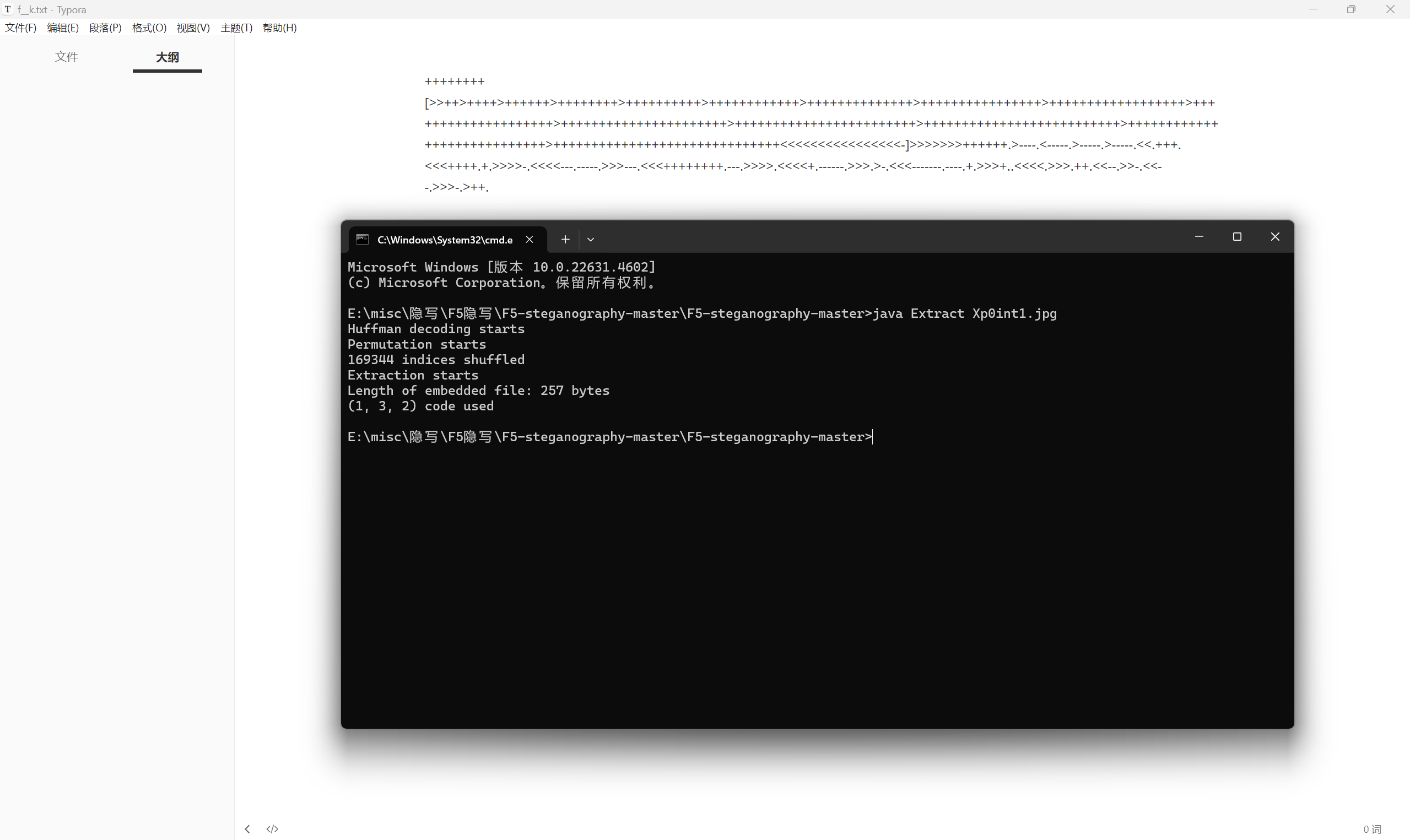
brainfuck解密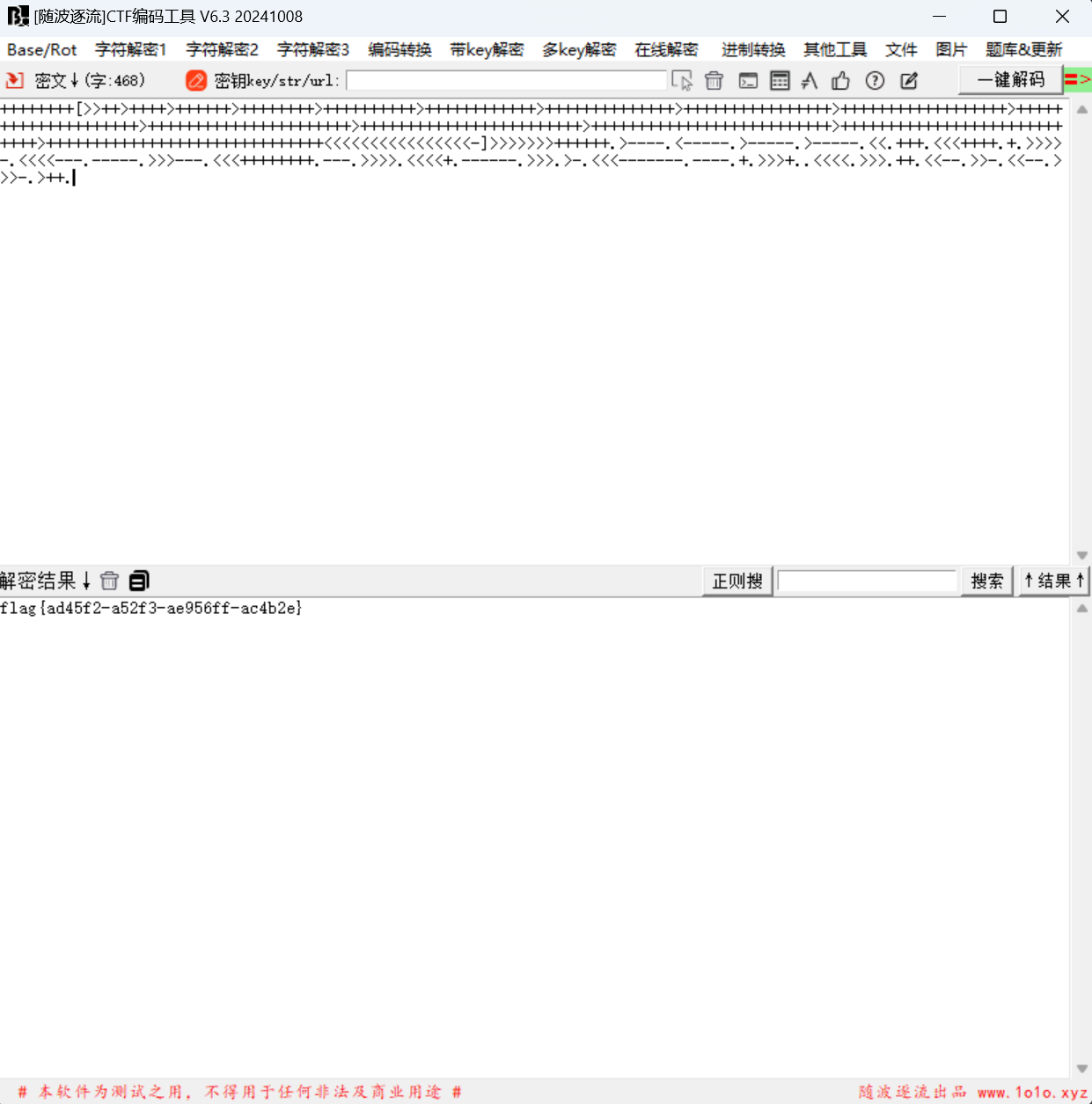
最后flag为
1 | flag{ad45f2-a52f3-ae956ff-ac4b2e} |
fgo
下载附件
拼图
exp:
1 | import cv2 |
运行得到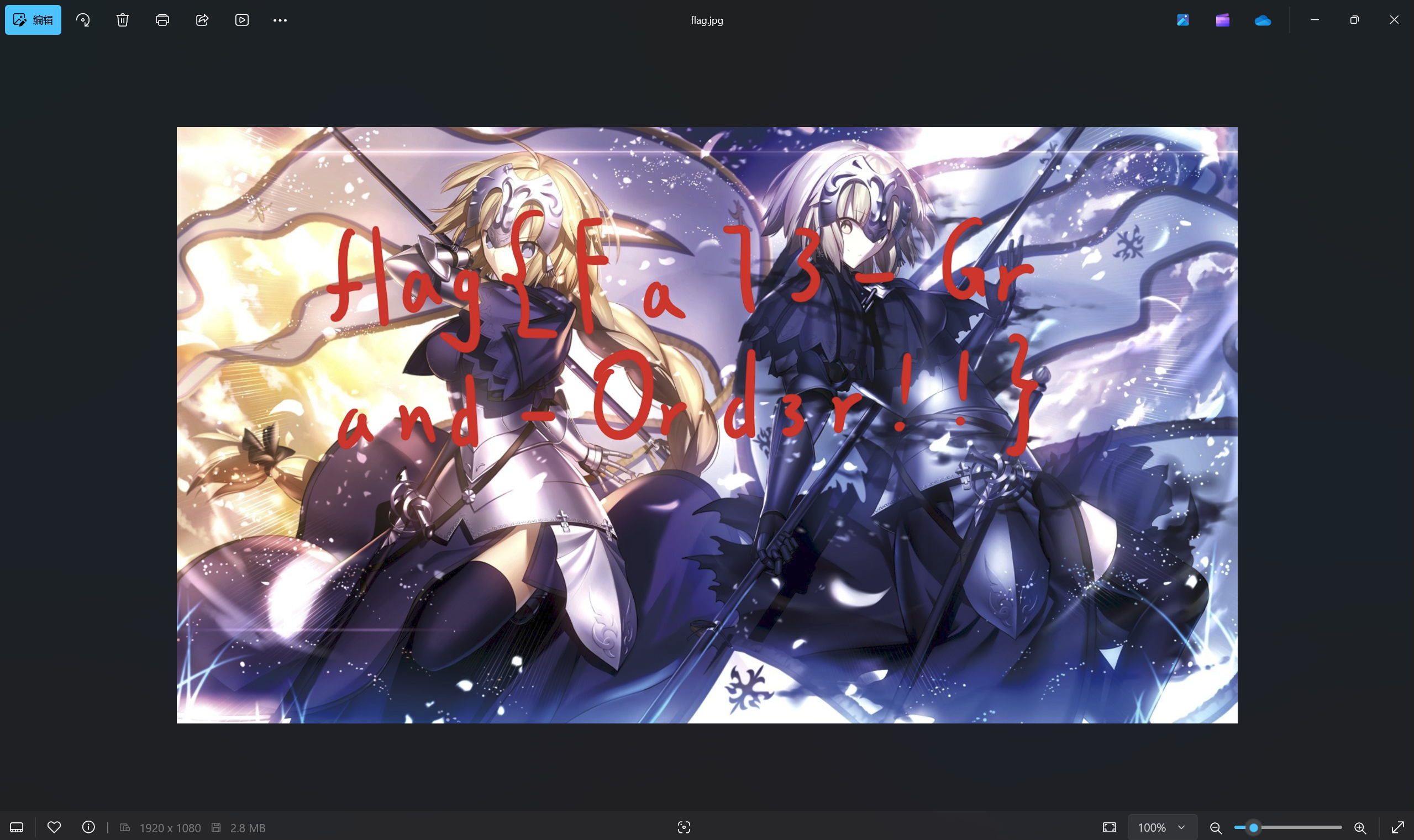
最后flag为
1 | flag{Fa73-Grand-Ord3r!!} |
misc???
下载附件
加密源码
1 | import cv2 |
解密exp
1 | import pickle |
最后flag为
1 | flag{m1sc_rev_1s_excited_???} |
zero_width
零宽隐写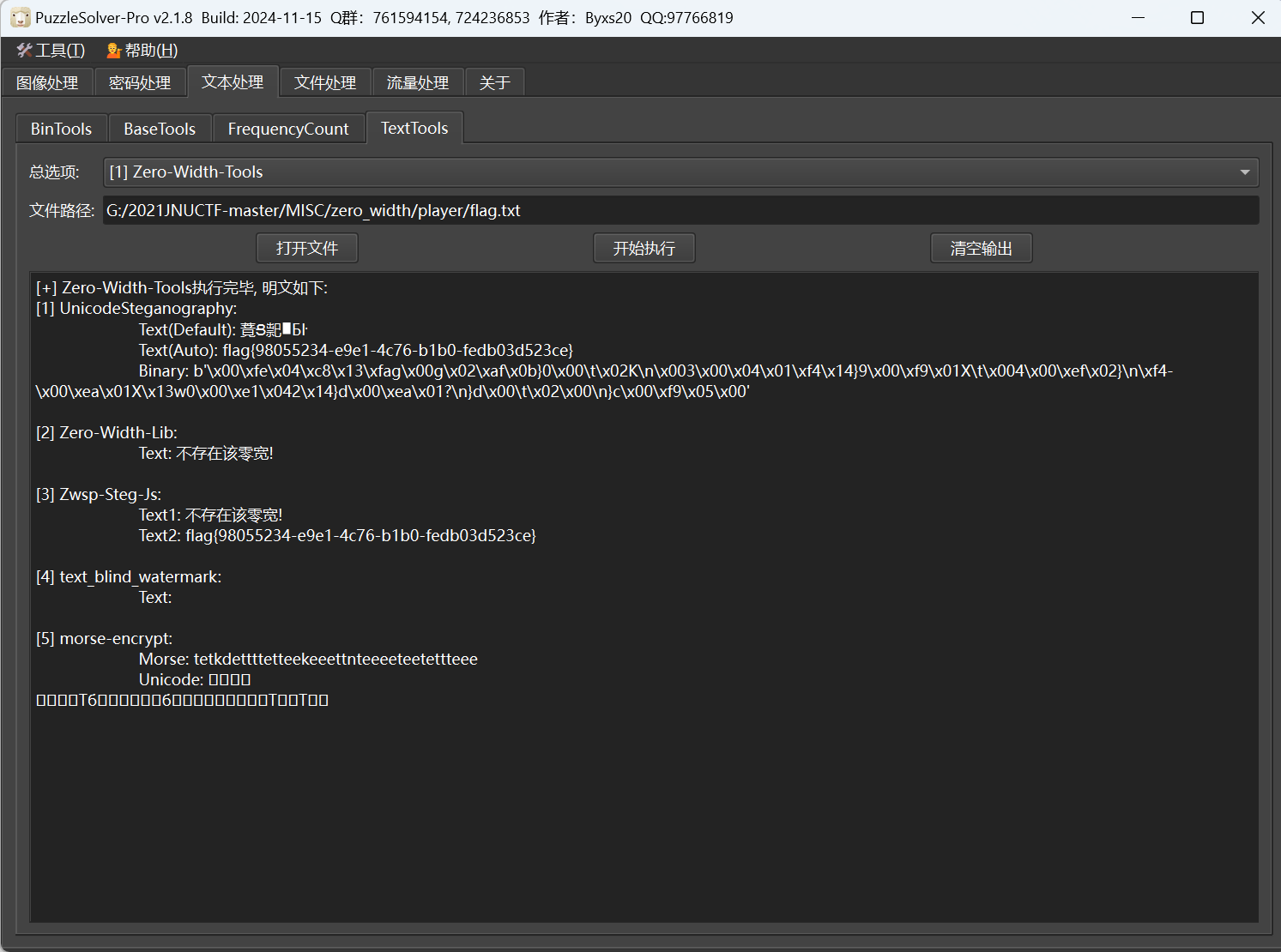
最后flag为
1 | flag{98055234-e9e1-4c76-b1b0-fedb03d523ce} |



