[GKCTF 2021]0.03
题目描述:
1 | 我的真心值三分吗 |
下载附件
文件名提示disk直接挂载,密码为311223313313112122312312313311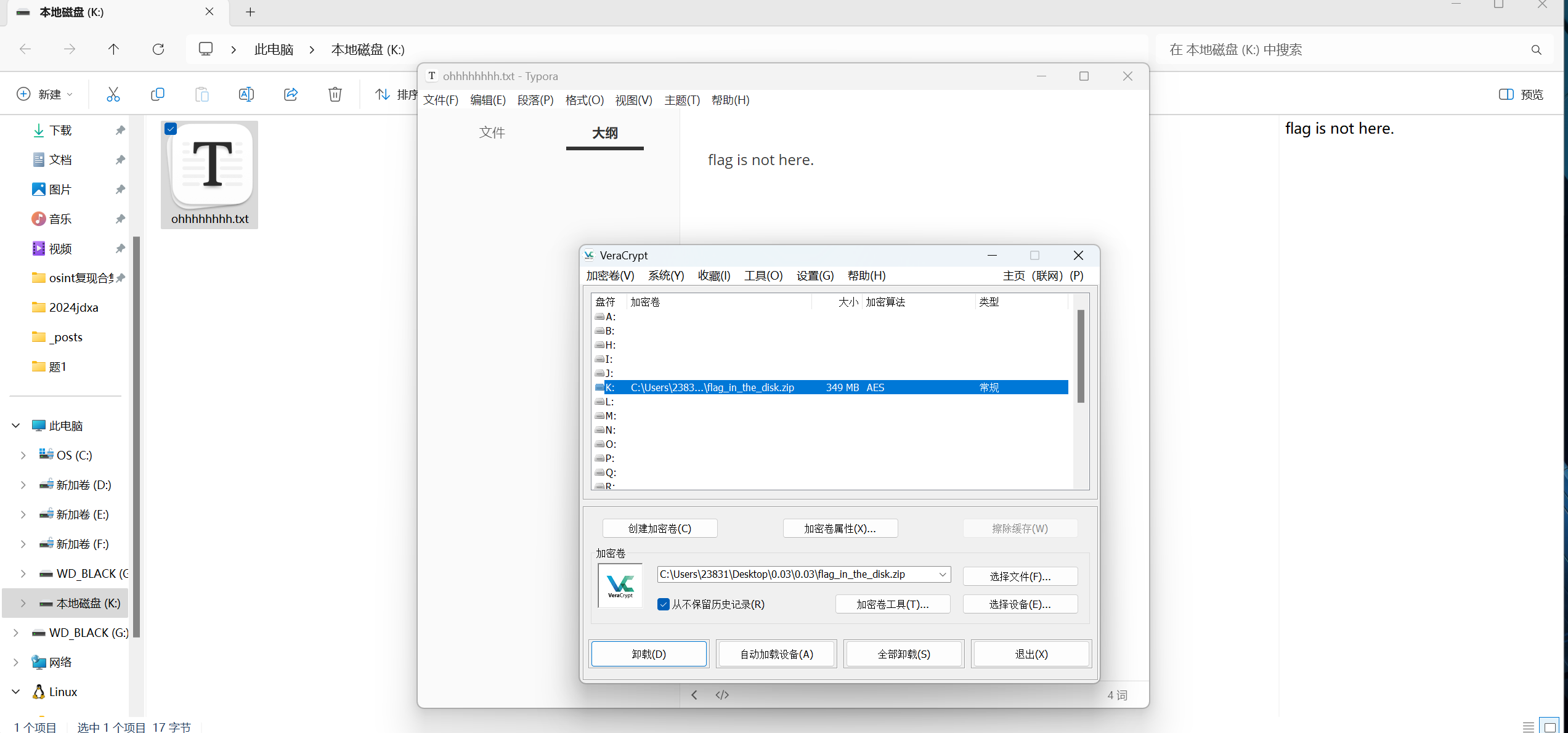
假flag
用ntfsstreamseditor扫描一下文件夹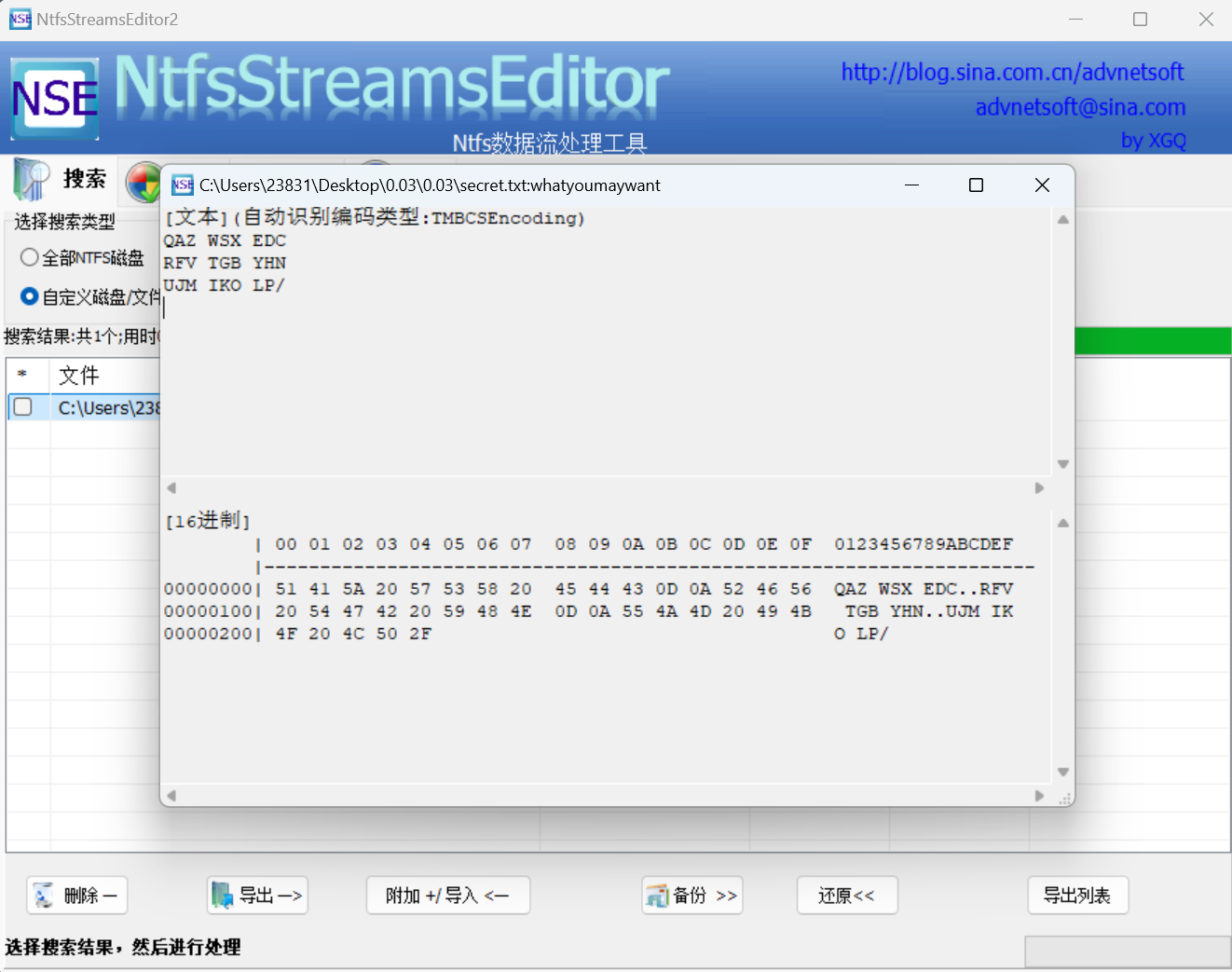
三分密码
1 | QAZ WSX EDC |
最后密码为EBCCAFDDCE,挂载磁盘得到flag
最后flag为
1 | flag{85ec0e23-ebbe-4fa7-9c8c-e8b743d0d85c} |
[NewStarCTF 公开赛赛道]最后的流量分析
题目描述:
1 | So Easy!分析出黑客获取的机密文件内容! |
下载附件
盲注流量
1 | tshark -r sqli.pcap -T fields -Y "http.request.method==GET or frame.len>765" -e "frame.len" -e "http.request.uri.query.parameter" > data.txt |
脚本处理
1 | from urllib.parse import * |
最后flag为
1 | flag{c84bb04a-8663-4ee2-9449-349f1ee83e11} |
[羊城杯 2020]image_rar
下载附件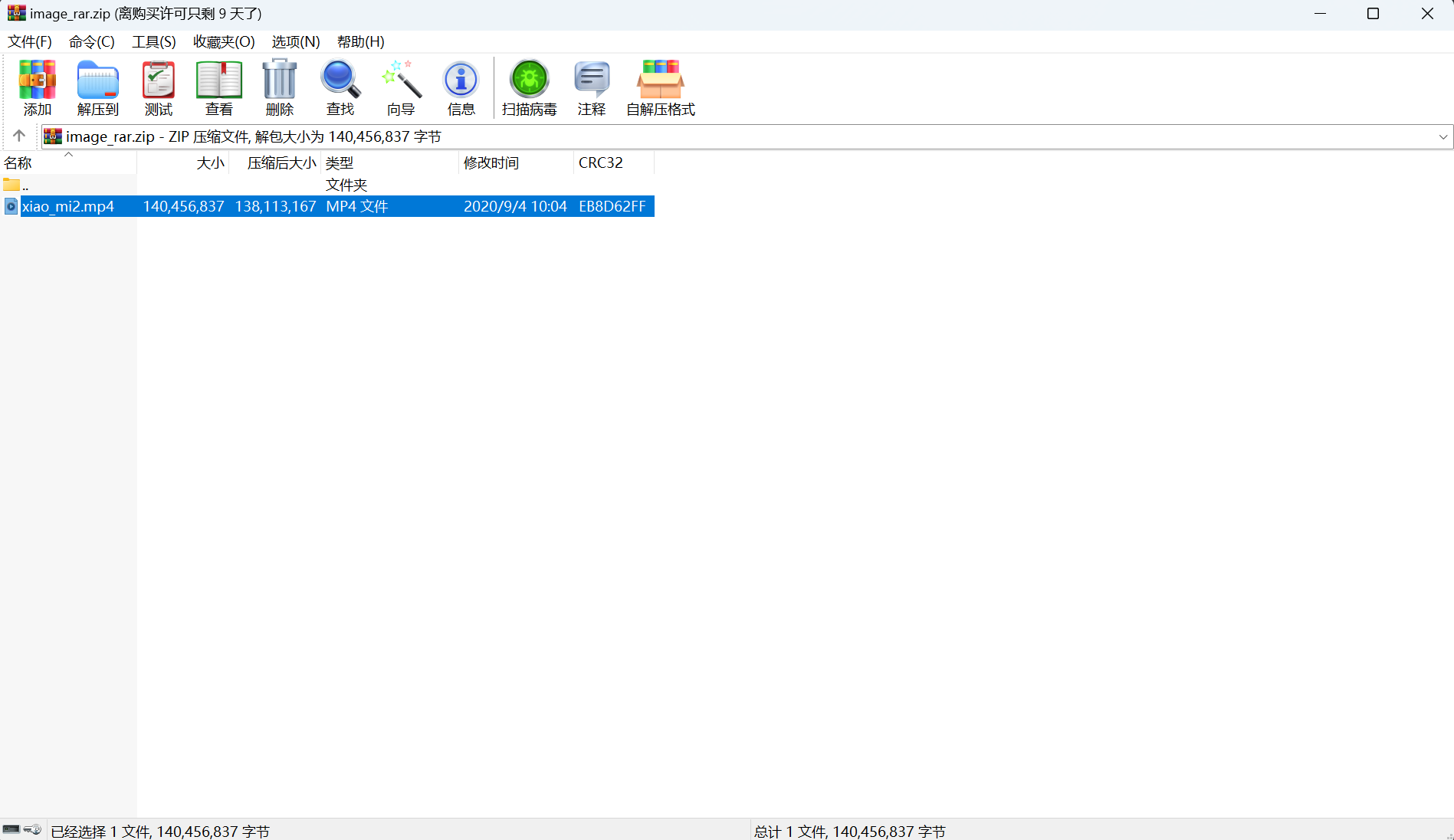
改后缀.zip查看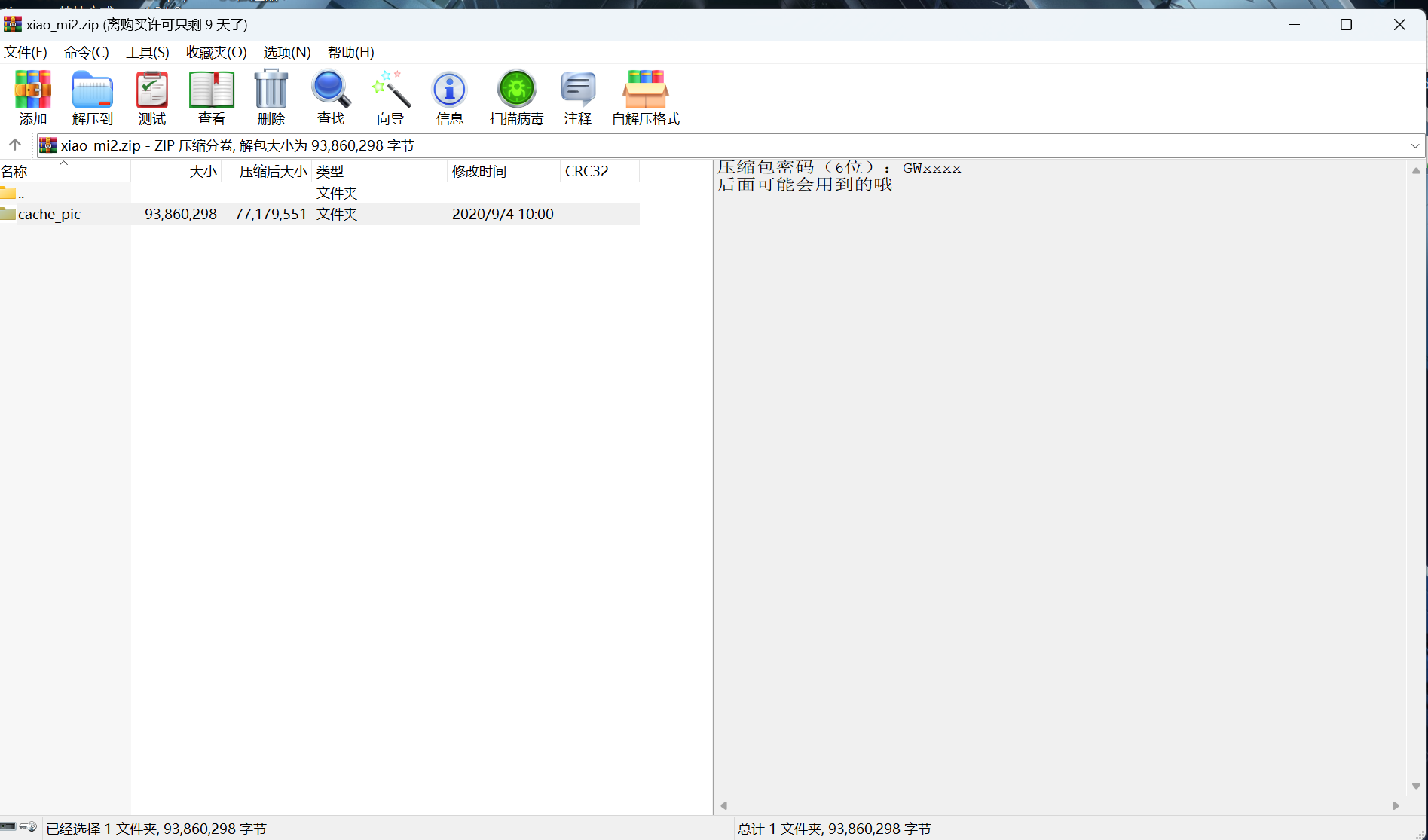
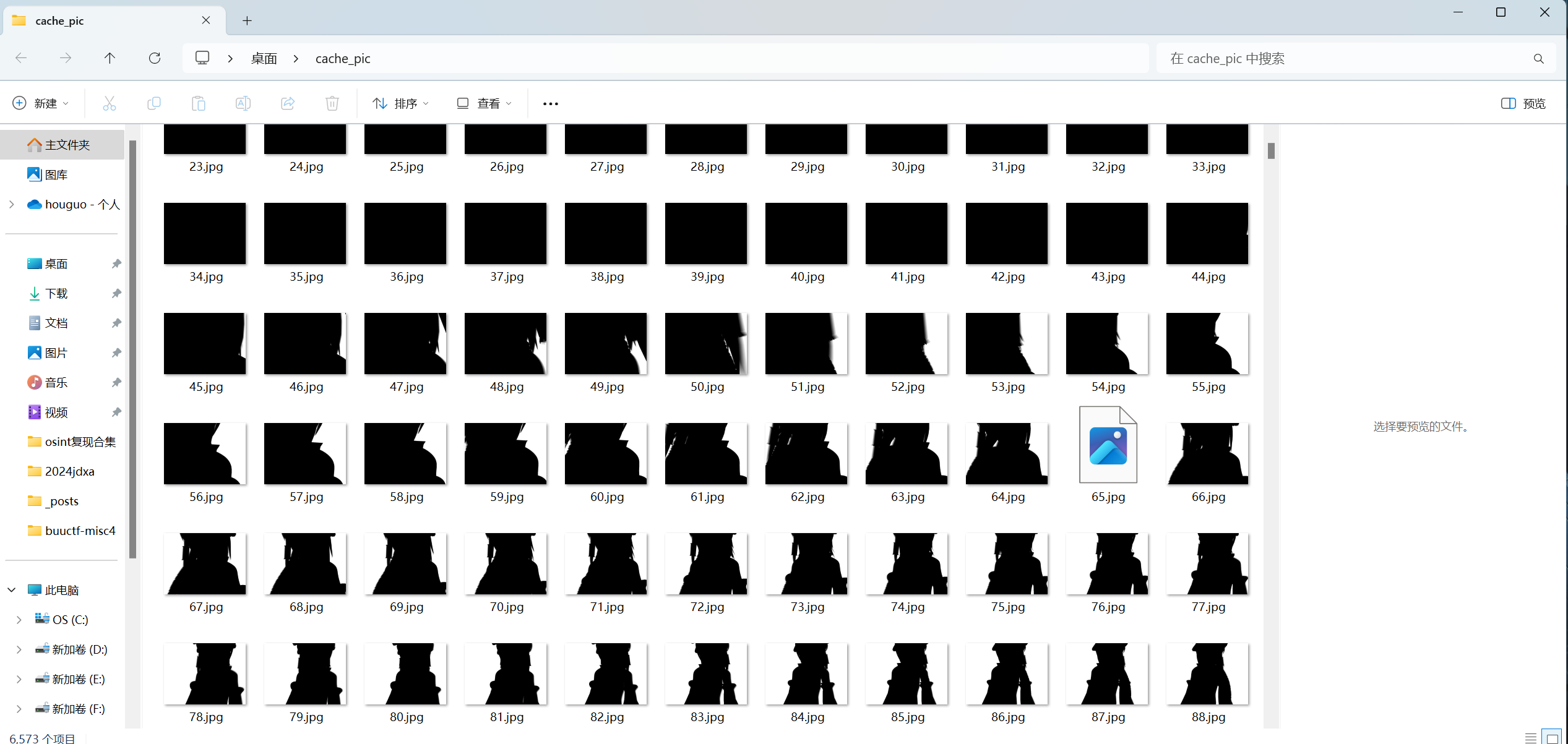
发现65图片不正常,010查看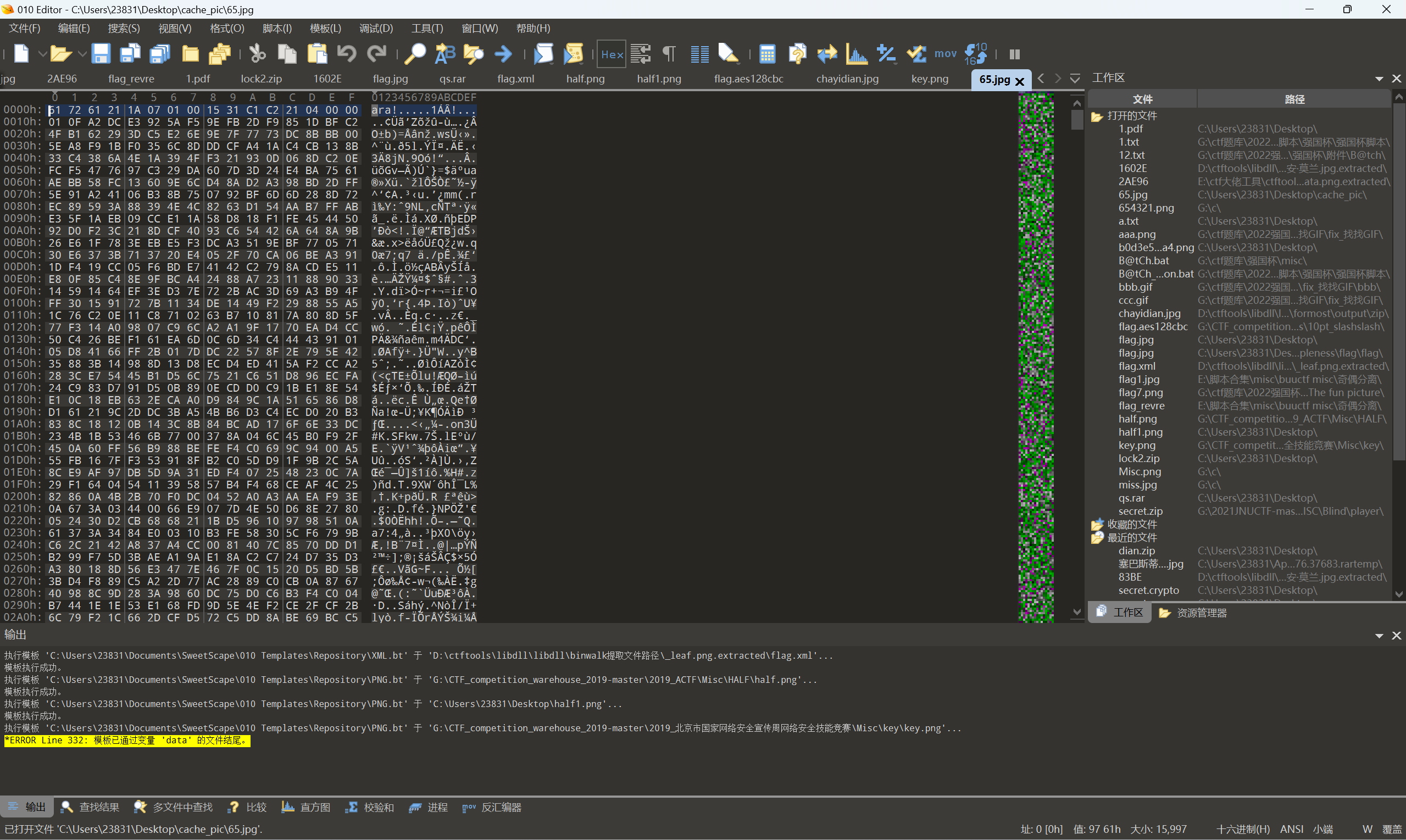
rar文件,修改为52 61 72 21,解压需要密码
配合john+hashcat爆破
1 | rar2john 65.rar |
得到密码GW5!3#,解压得到一个叫flag的文件,010查看: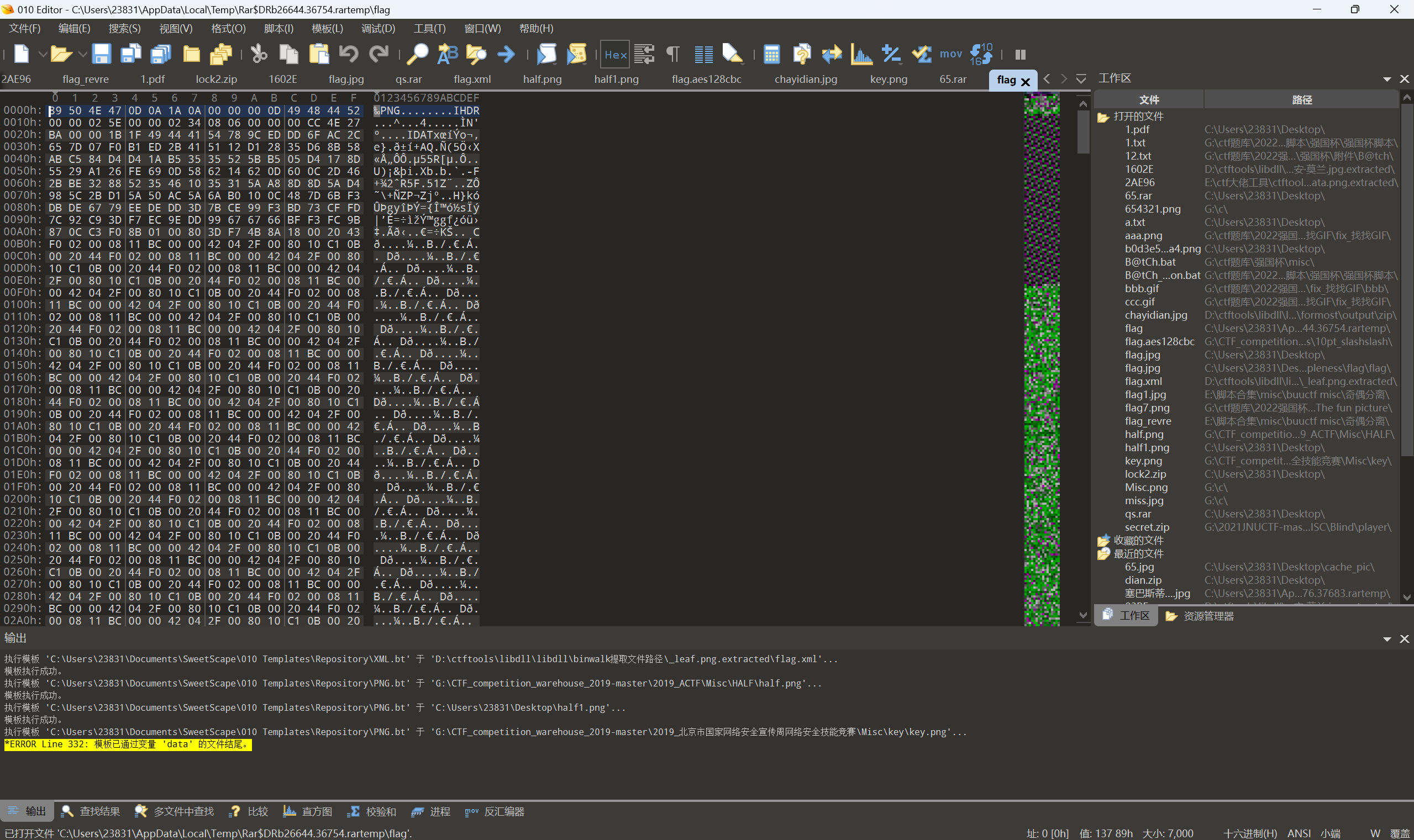
保存为png文件查看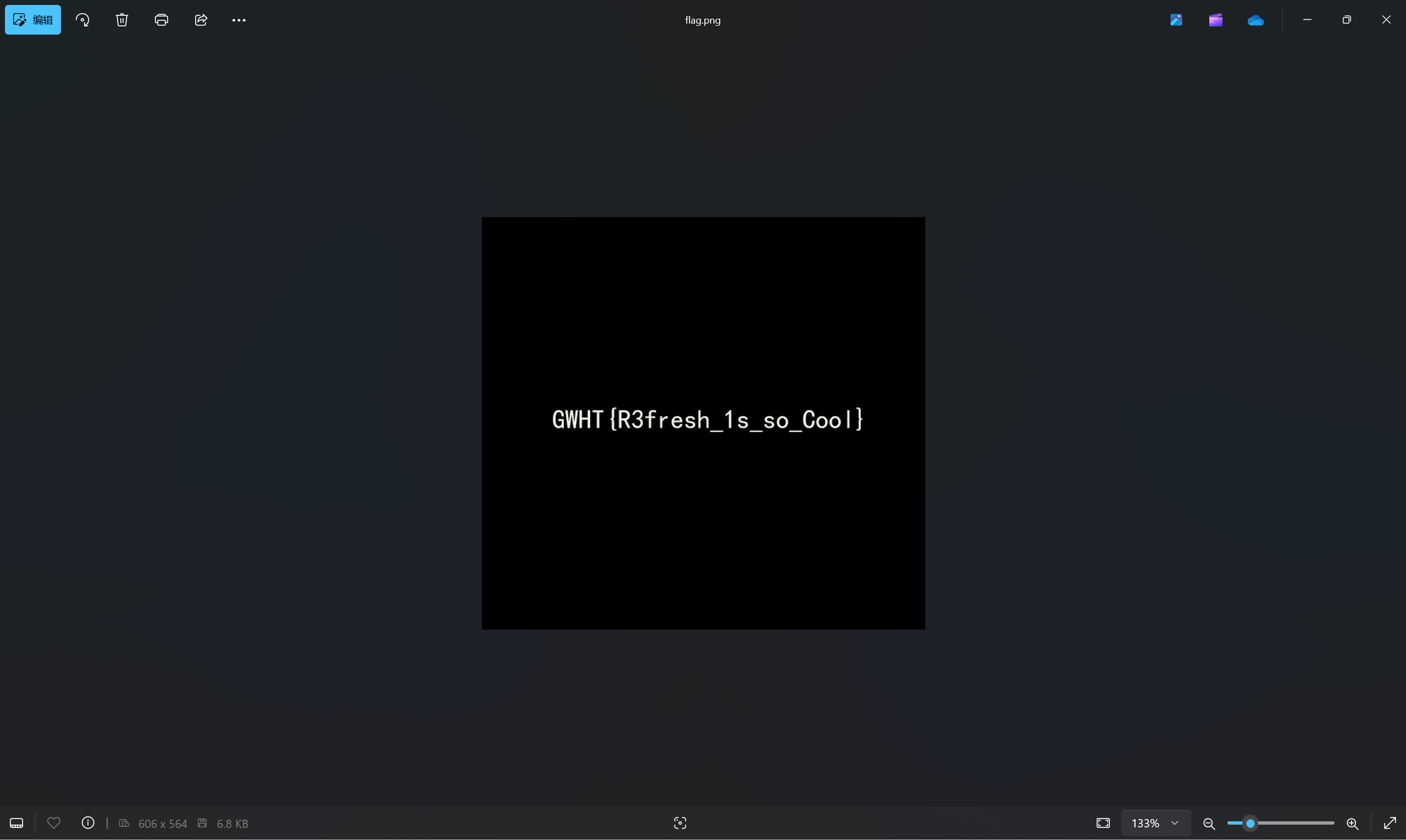
最后flag为
1 | flag{R3fresh_1s_so_Cool} |
[QCTF2018]picture
下载附件
带key的lsb隐写 密码为wwjkwywq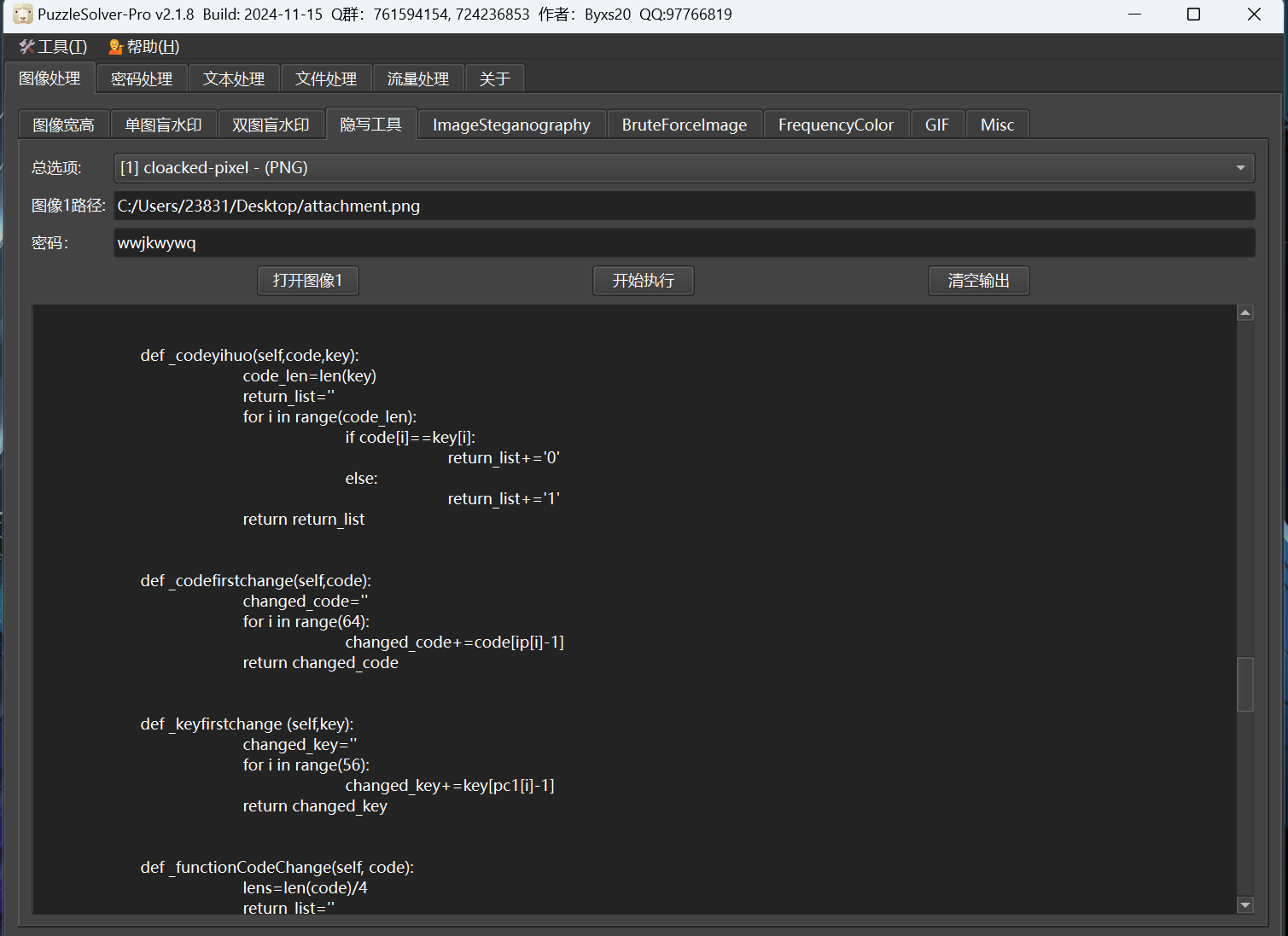
des解码
1 | # _*_ coding:utf-8 _*_ |
运行得到
最后flag为
1 | flag{eCy0AALMDH9rLoBnWnTigXpYPkgU0sU4} |
[XMAN2018排位赛]ppap
下载附件
tcp追踪流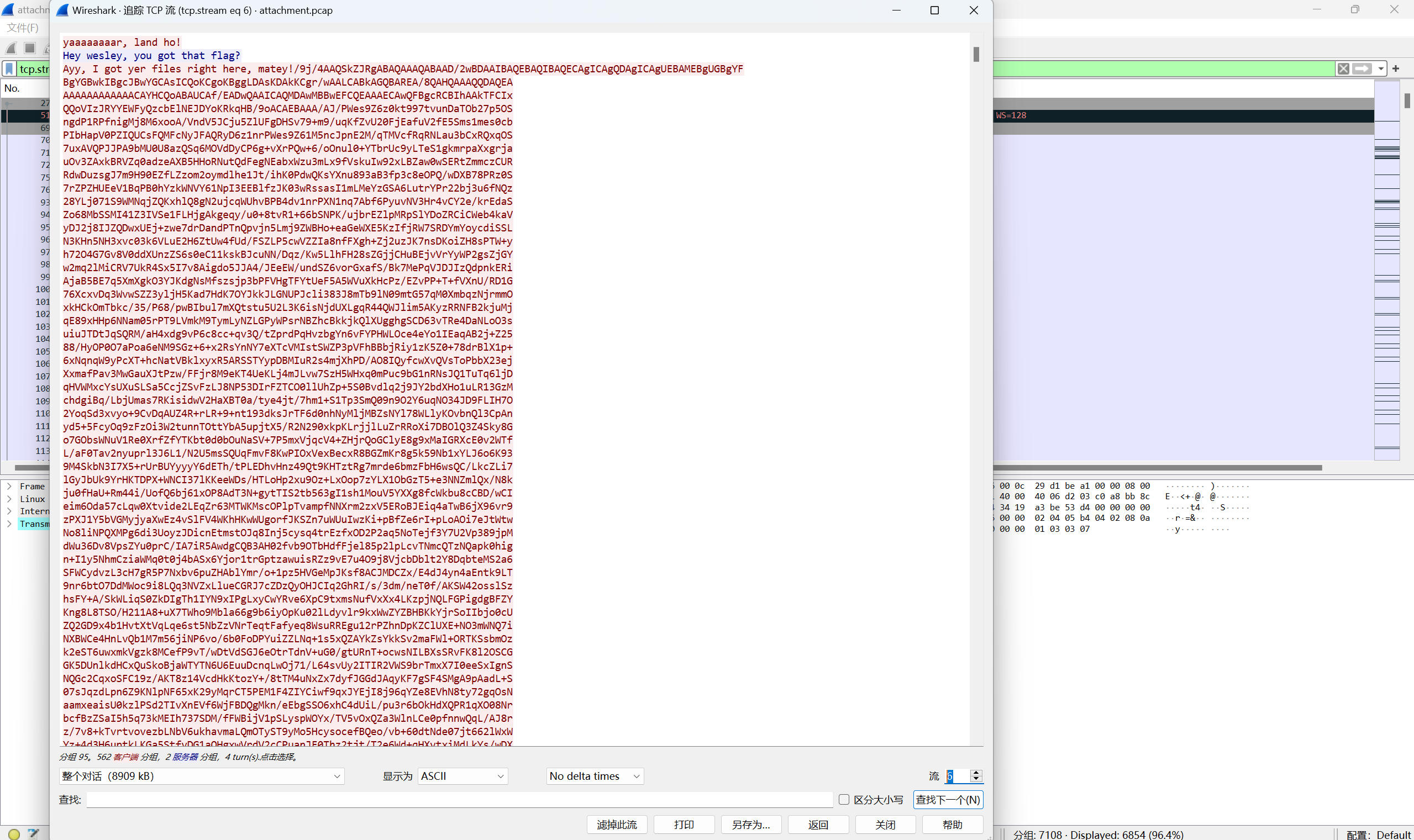
base转图片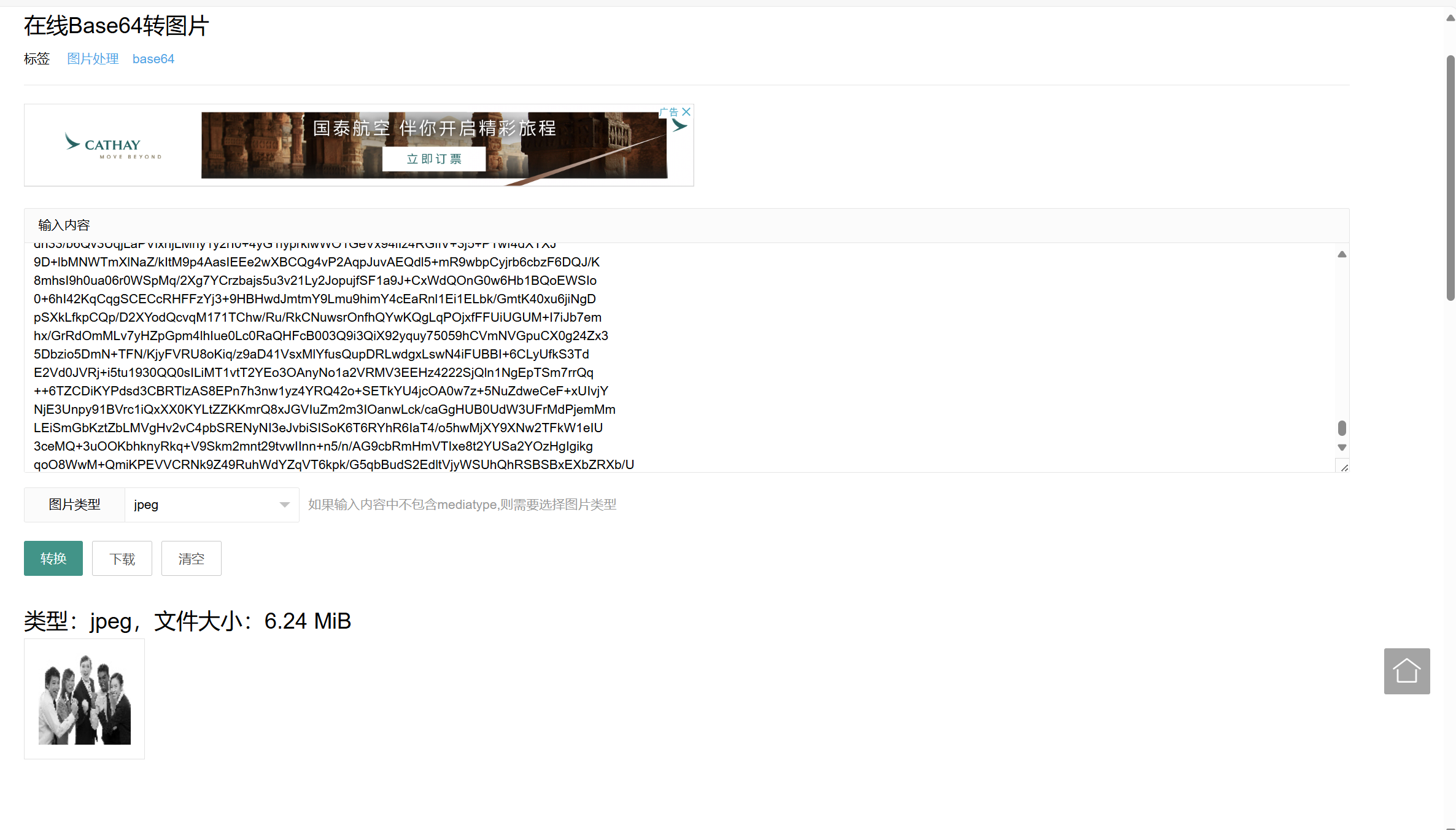
base解码第二段
使用这个网站破解密码:https://passwordrecovery.io/zip-file-password-removal/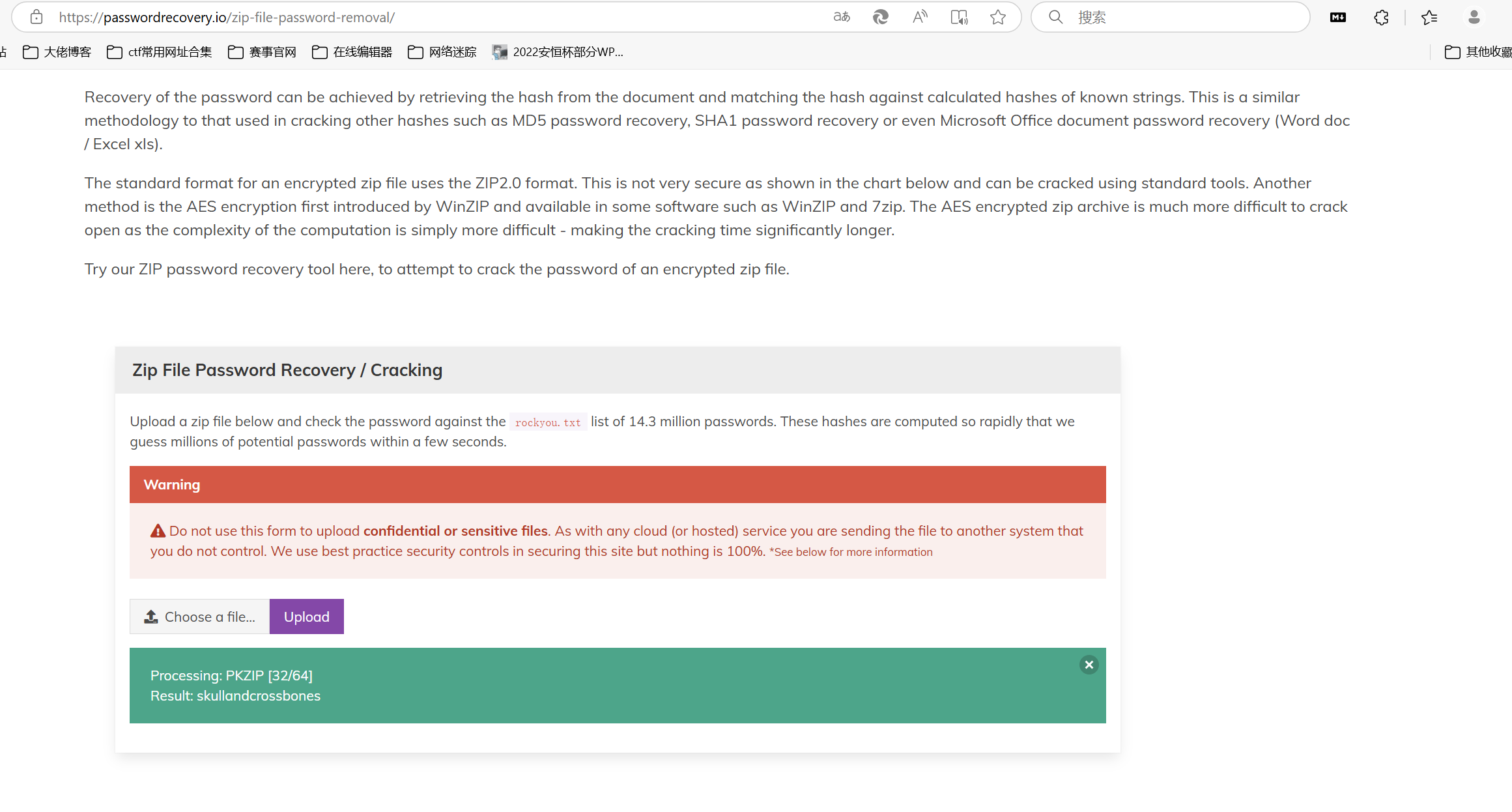
得到密码:skullandcrossbones
解压得到flag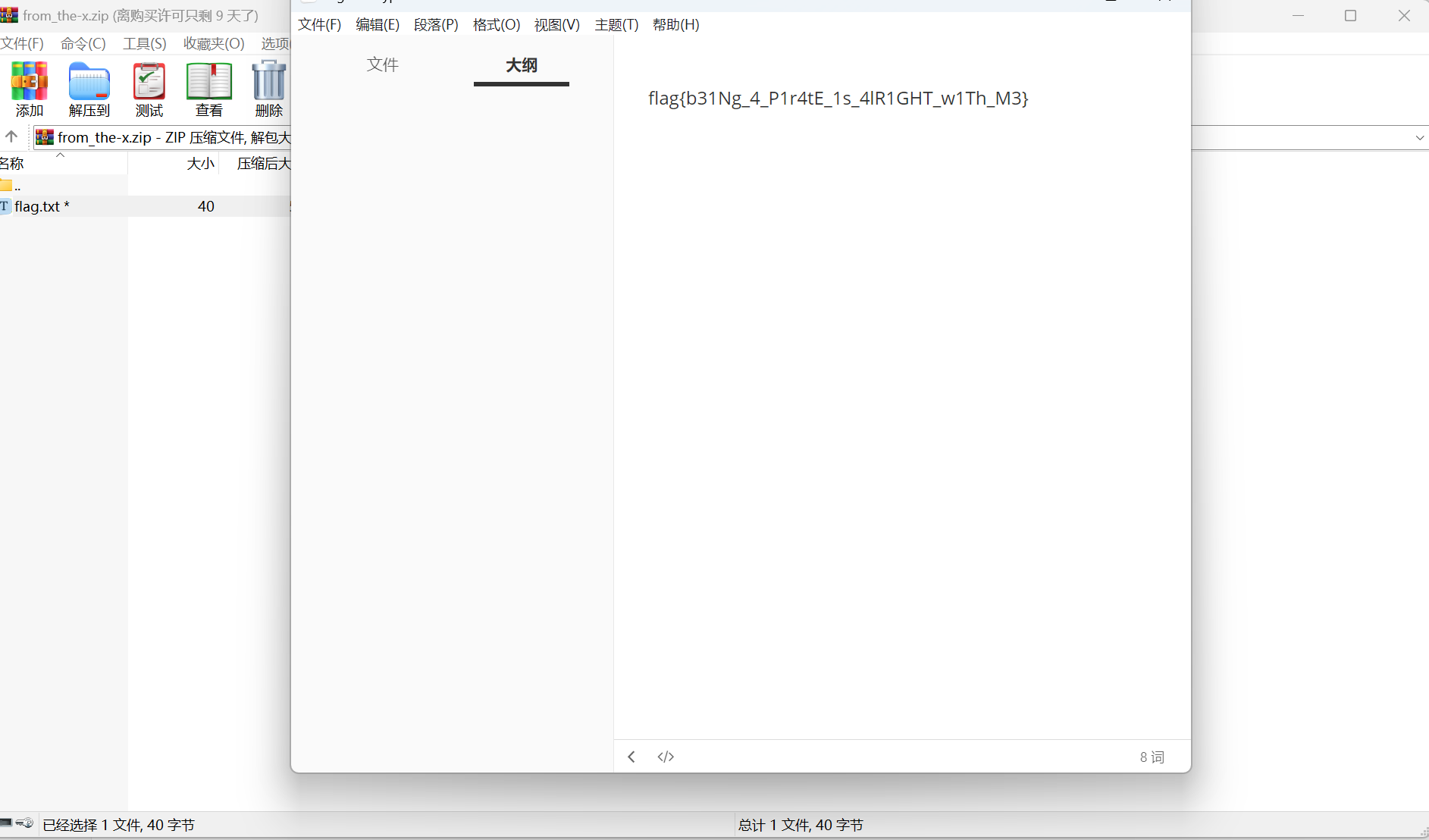
最后flag为
1 | flag{b31Ng_4_P1r4tE_1s_4lR1GHT_w1Th_M3} |
[CFI-CTF 2018]Kadyrov’s Cat
题目描述:
1 | A man from the soviet union has sent you two strange documents. Find the identity of the man as well as his location. |
下载附件
查看图片属性发现坐标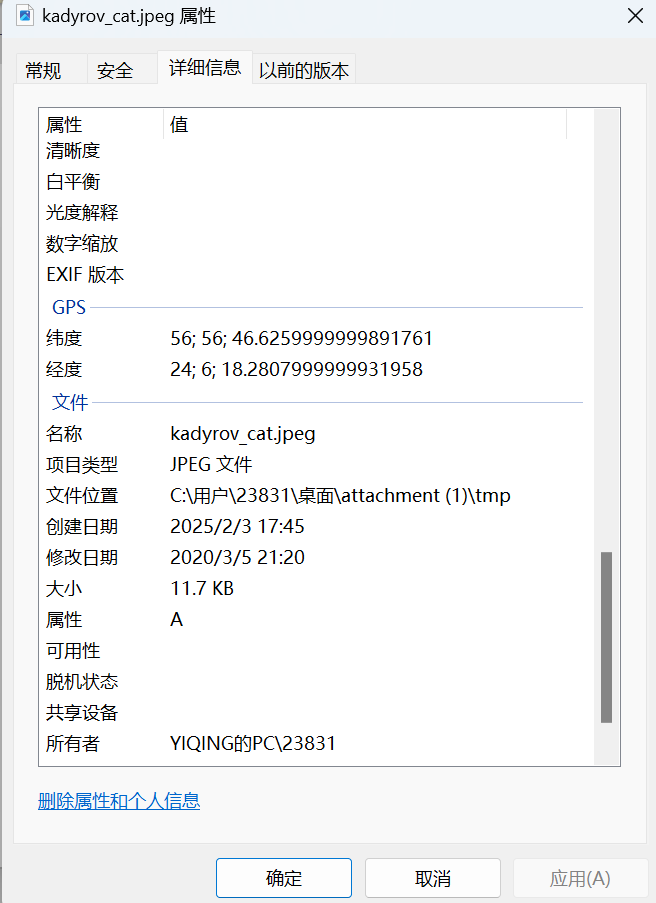
在线坐标转换
在线经纬度转换工具_经纬度转度分秒格式_度分秒转经纬度格式 - 一起看地图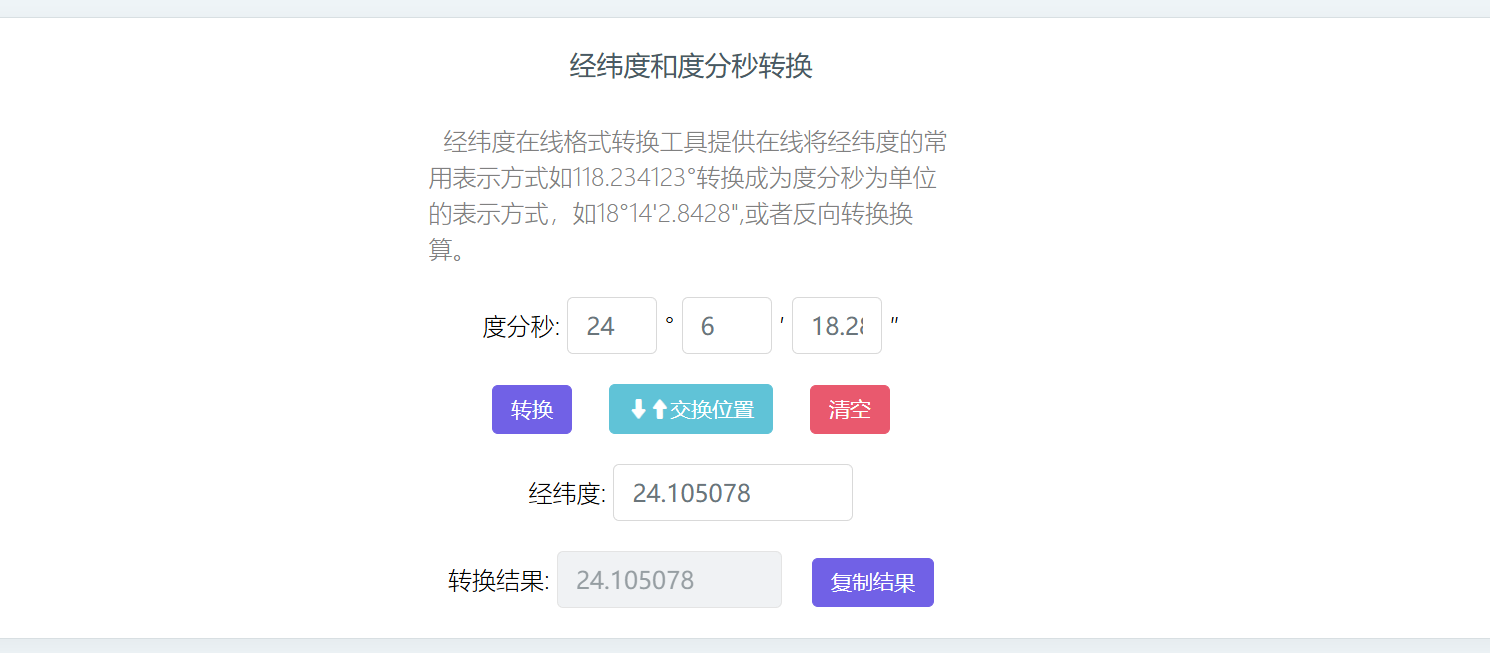
24.105078,56.946007
百度地图查看城市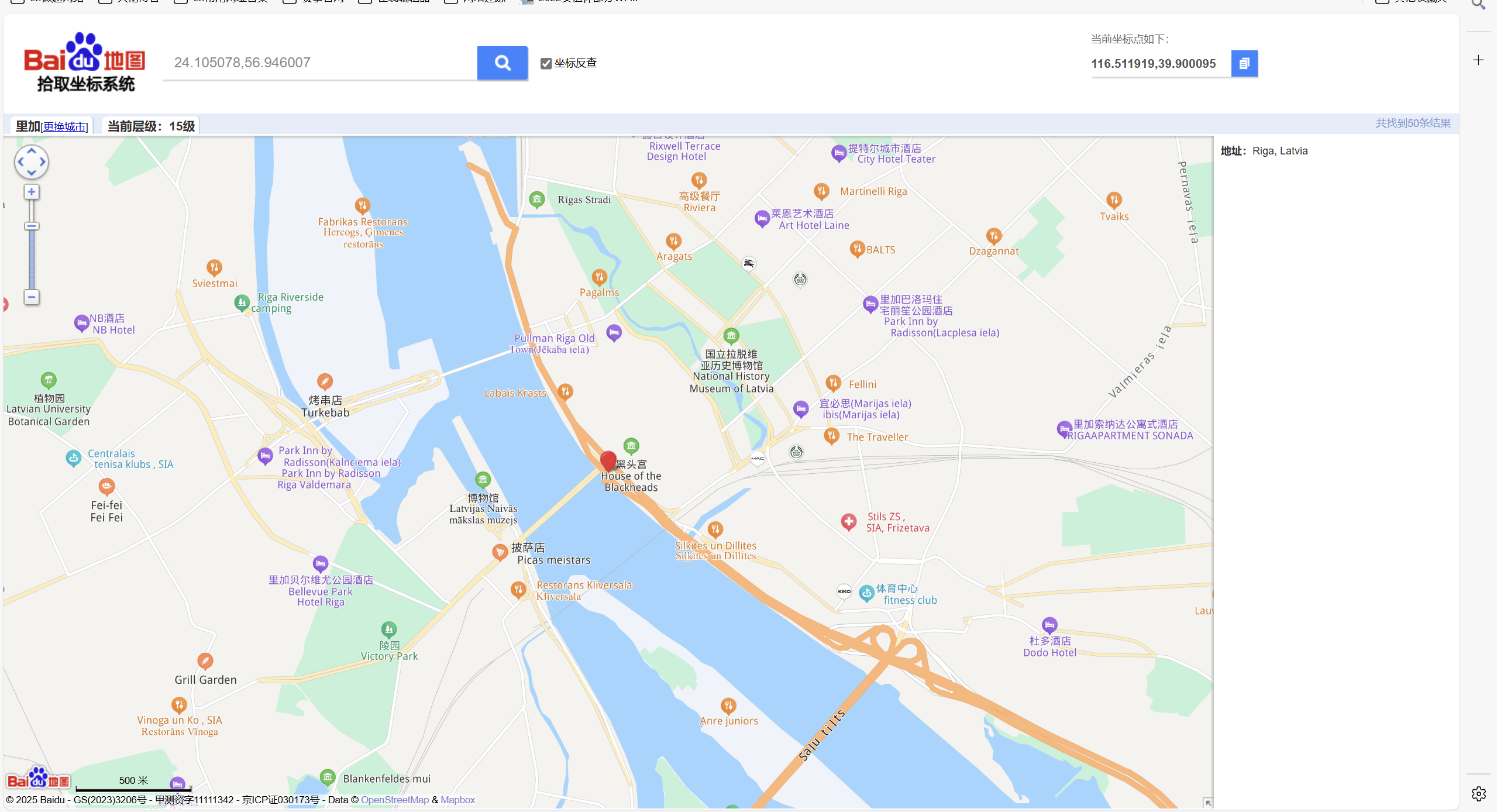
打开message.pdf,在文档属性里找到作者的姓名:Kotik Kadyrov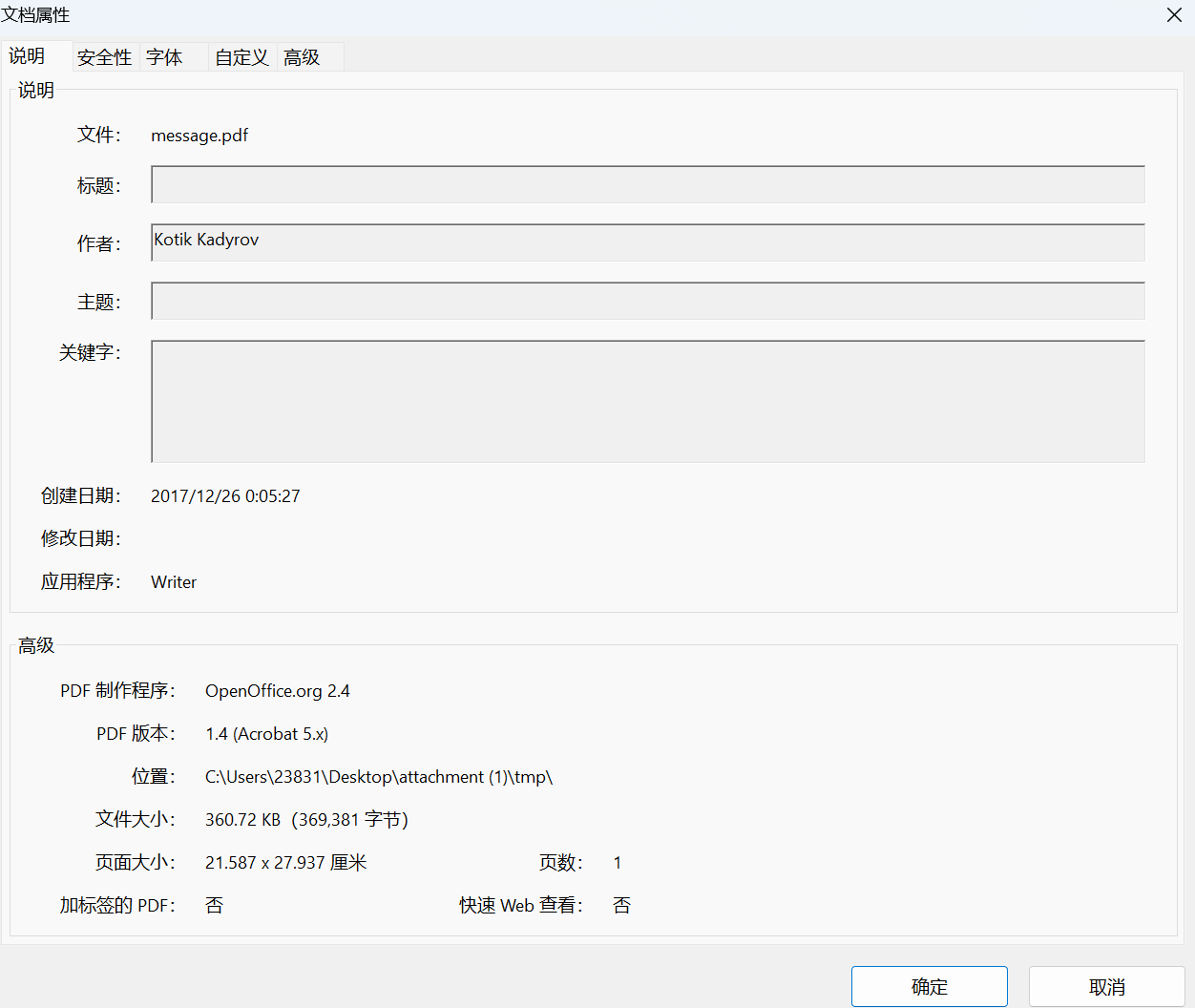
最后flag为
1 | flag{Kotik_Kadyrov_of_Riga} |
[SUCTF2019]protocol
下载附件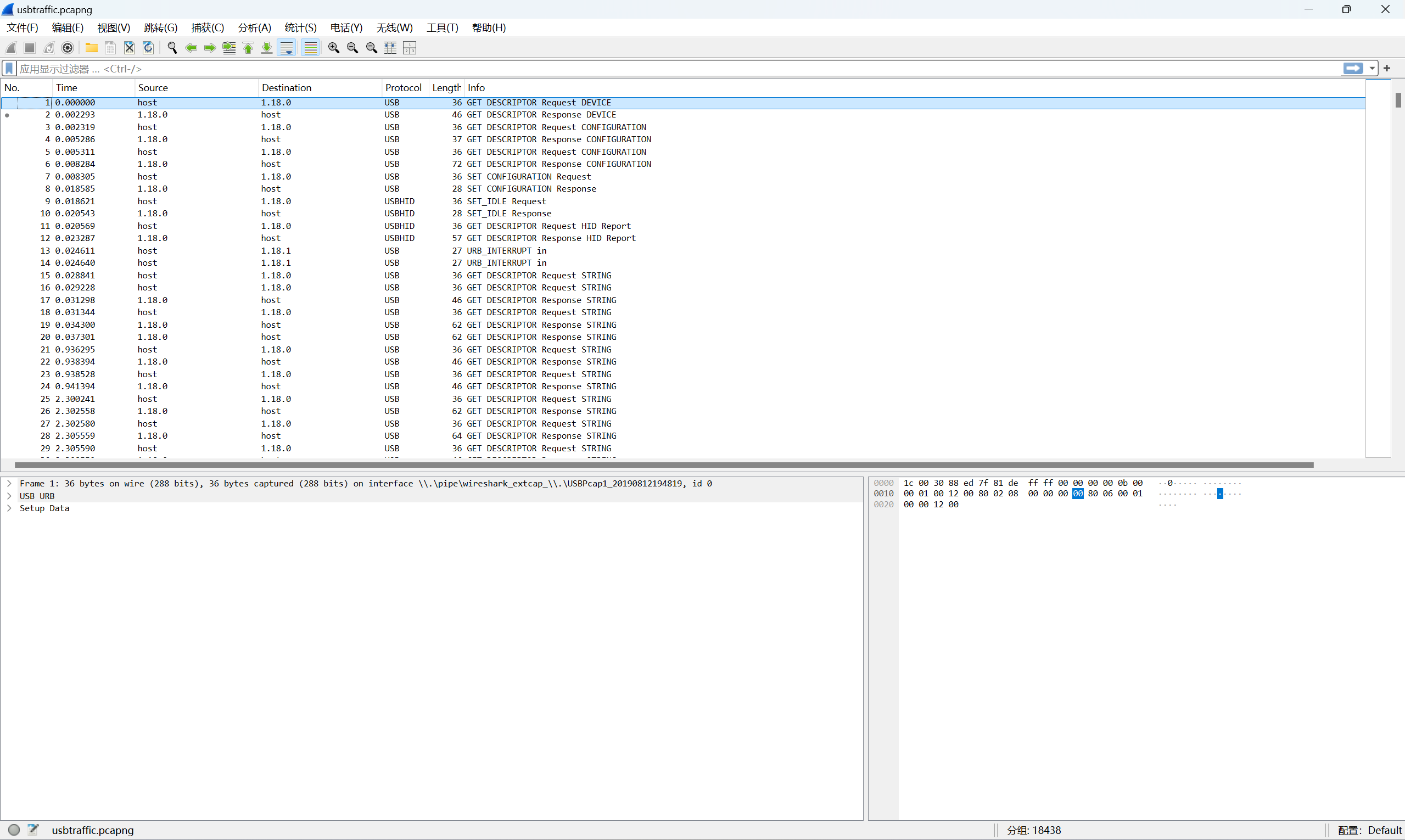
foremost分离得到一些图片
返回wireshark中,排长度,从大小为7845开始,提取信息,前十五个(因为图片中前十五个有字)是
1 | 04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a |
再从第十六个开始向后数十个(因为有十张黑图)
1 | 06 07 0e 04 01 0d 00 02 0b 09 |
有字的图片的对应大小就是
1 | 04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a |
对照有字的图的数据,找出与黑色图片相同数据的位置,即可以找到黑色图片对应的字
1 | 第一张是06,那么在有字的图片数据中是第九个,所以对应的就是s(需要镜像) |
最后flag为
1 | flag{My_usb_pr0toco1_s0_w3ak} |
[*CTF2019]She
下载附件
新建一个项目,将项目中的Game.rxproj文件放入She游戏文件夹中,再用工具打开这个文件,就可以对游戏进行编辑了
点击 工具 => 数据库 ,把怪物的数值都修改到最小,角色的搞成最大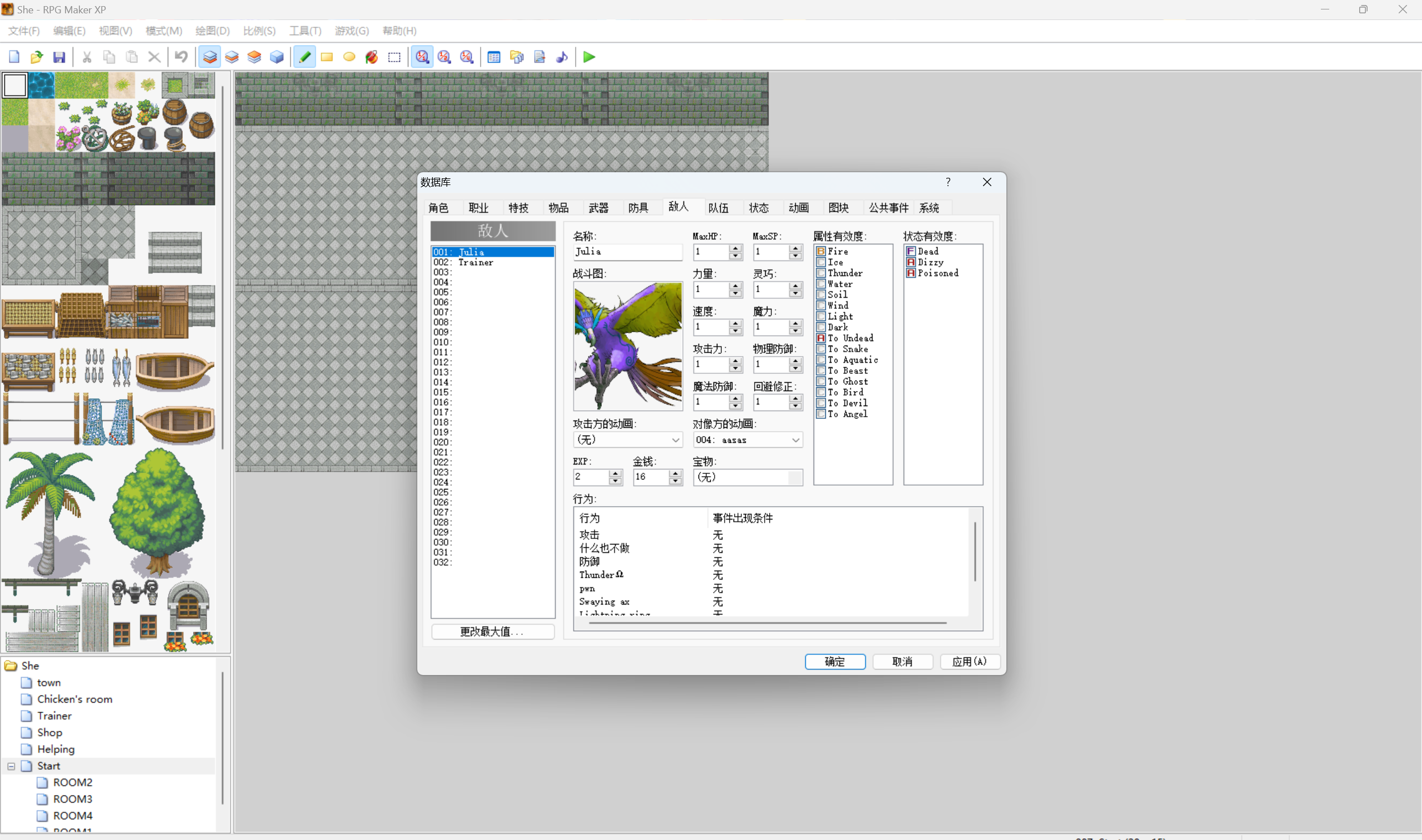
开挂后,怪鸟就被秒杀了,继续后面的游戏,进入一扇门后一直往右走,会有很多门,房间里面有箱子,但是门打不开,而且碰到面的怪物就死了。
继续开挂,修改游戏数据,选择场景,点击蓝色方块,编辑事件。把怪物删掉
然后我们从第一个门开始打开门,发现打不开然后挨个尝试,按照该顺序获取到的数值是371269(第几个门),按照房间顺序排列得到213697。(第一个门是2,第二个门给的数字是1以此类推)
将213697进行md5加密
最后flag为
1 | flag{d6f3fdffbcb462607878af65d059f274} |
[NewStarCTF 2023 公开赛道]隐秘的图片
下载附件
双图异或得到二维码
扫描二维码得到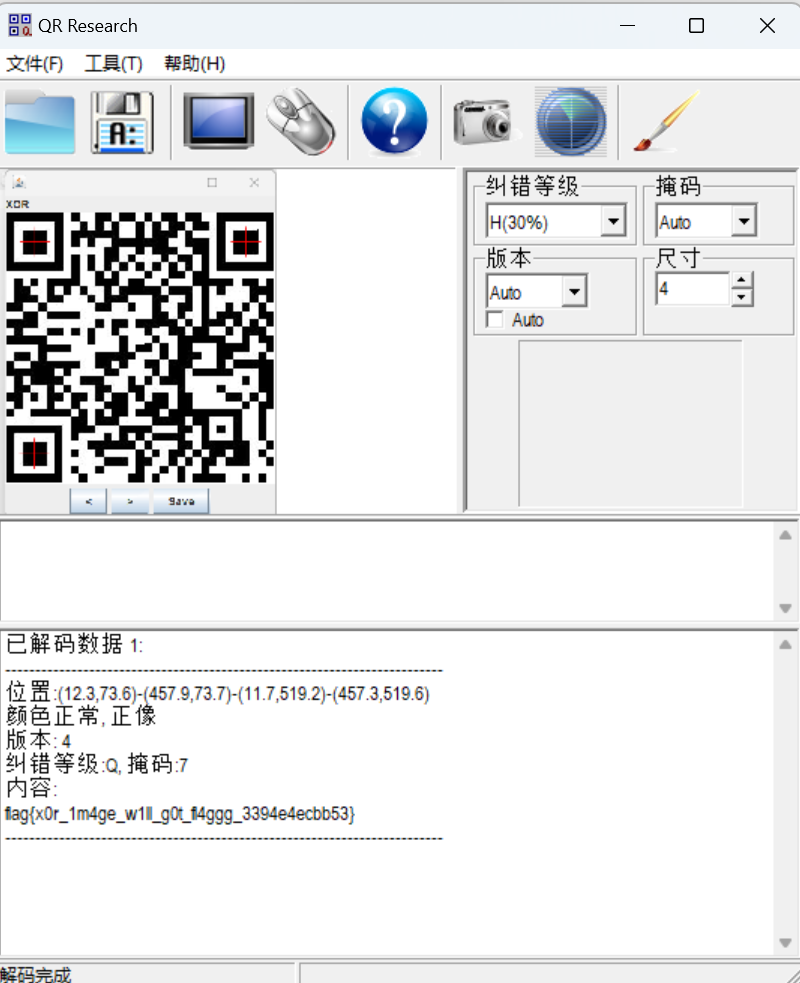
最后flag为
1 | flag{x0r_1m4ge_w1ll_g0t_fl4ggg_3394e4ecbb53} |
[De1CTF2019]Mine Sweeping
下载附件
扫雷游戏
直接破解
用dnspy打开Assembly-CSharp.dll
文件路径:\Mine Sweeping\Mine Sweeping_Data\Managed\
找到使游戏结束的代码段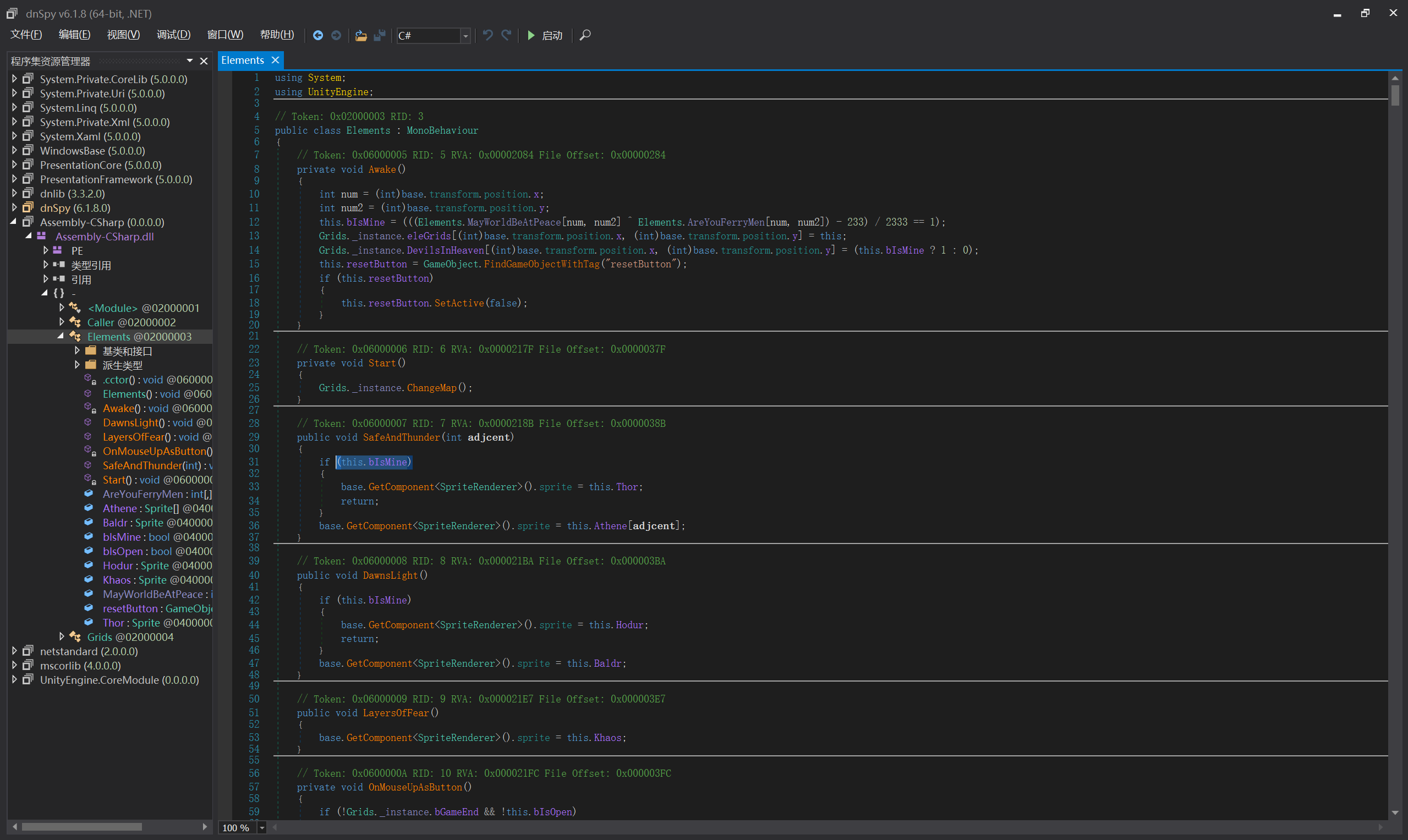
将this.bIsMine改成false
保存后重新打开游戏,,把所有的块都点开后,会出现一个二维码,(可以下载一个速点器),二维码扫出来是一个网址,打开网址就有flag
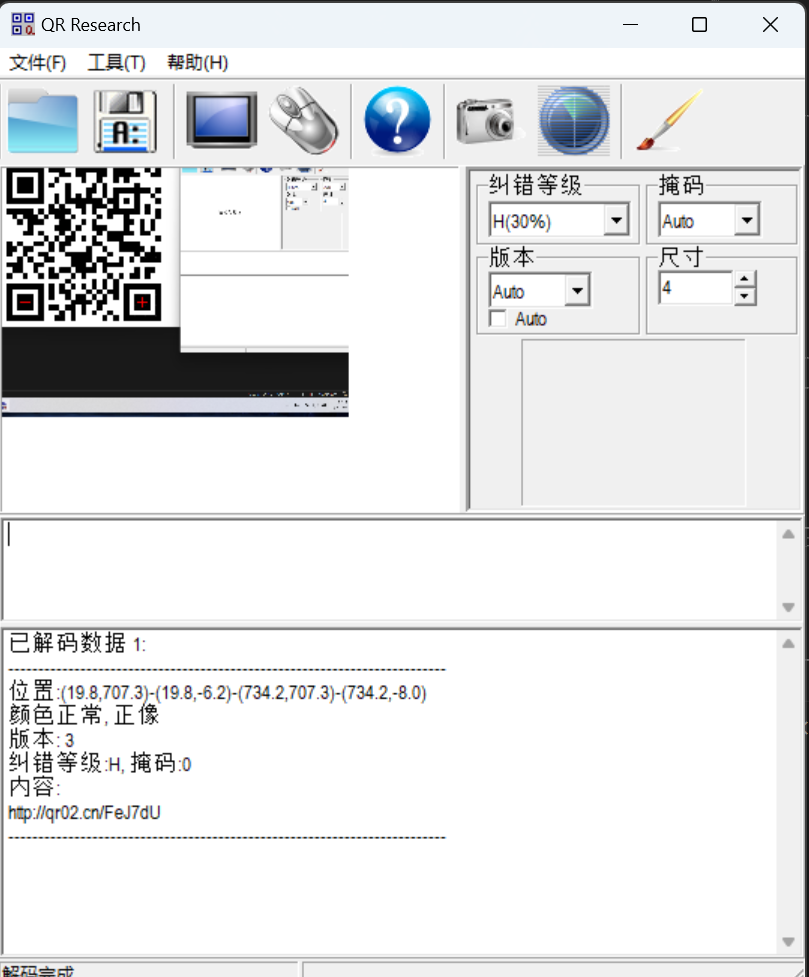
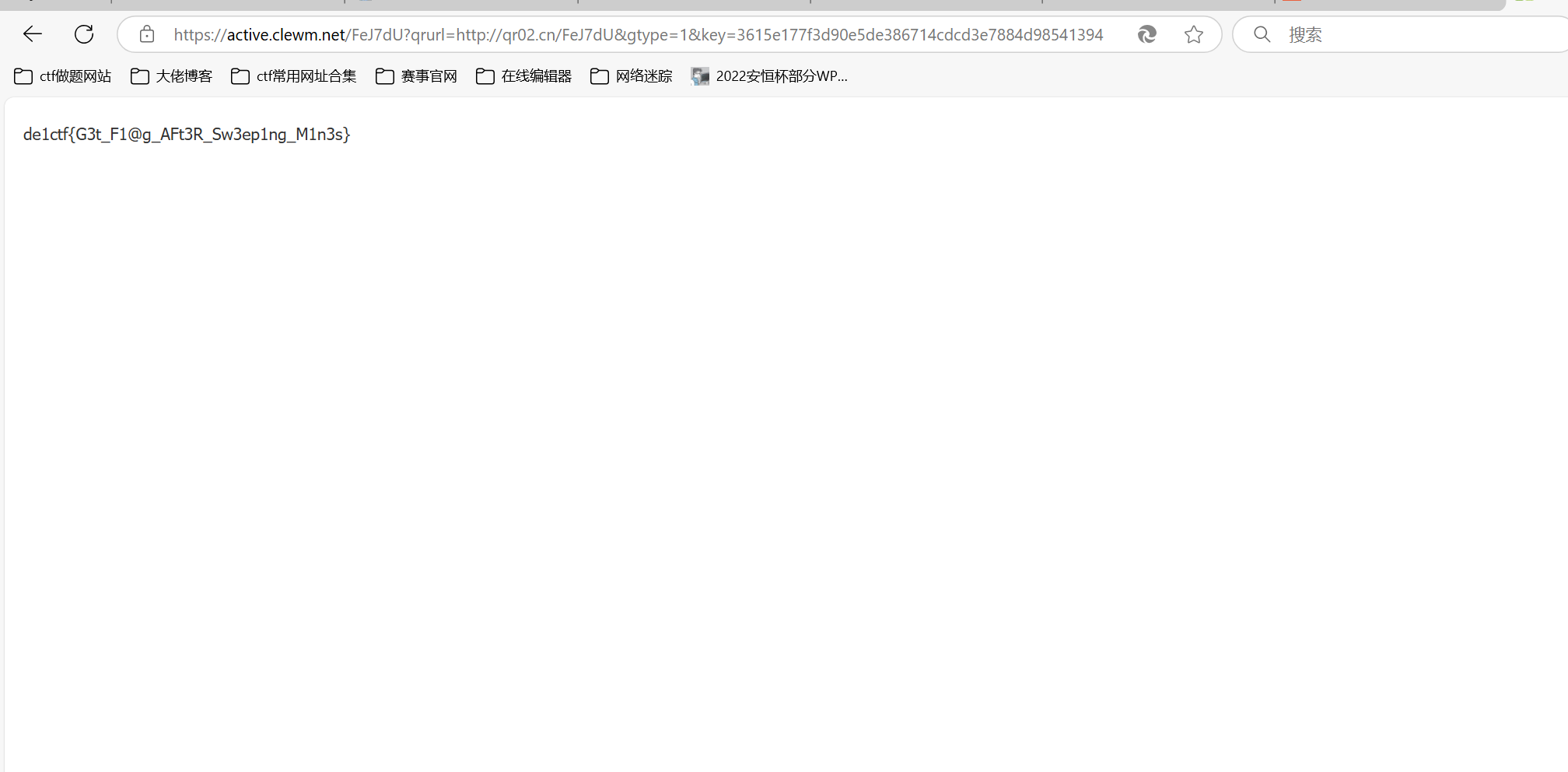
最后flag为
1 | flag{G3t_F1@g_AFt3R_Sw3ep1ng_M1n3s} |
[RoarCTF2019]forensic
lovemem一把梭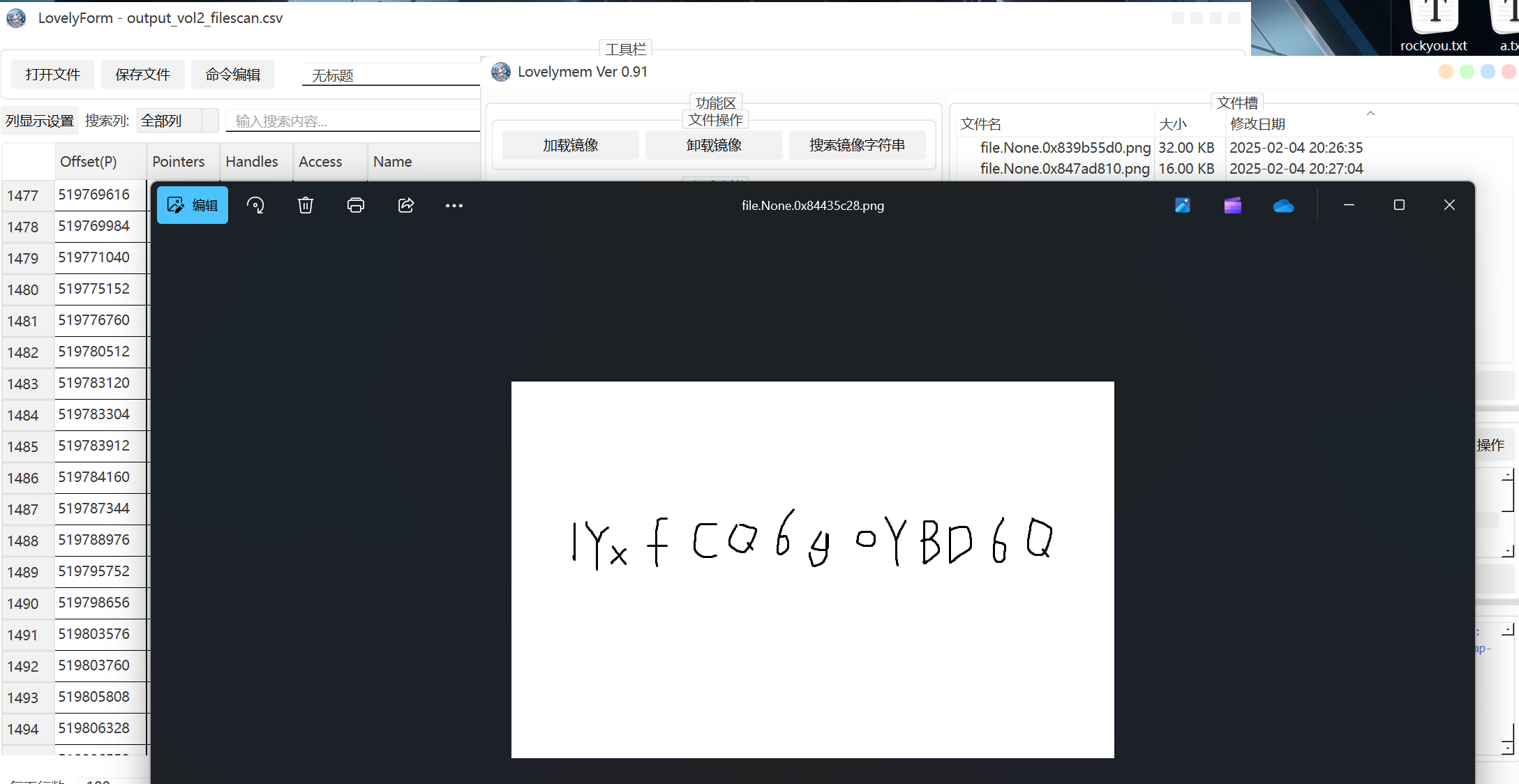
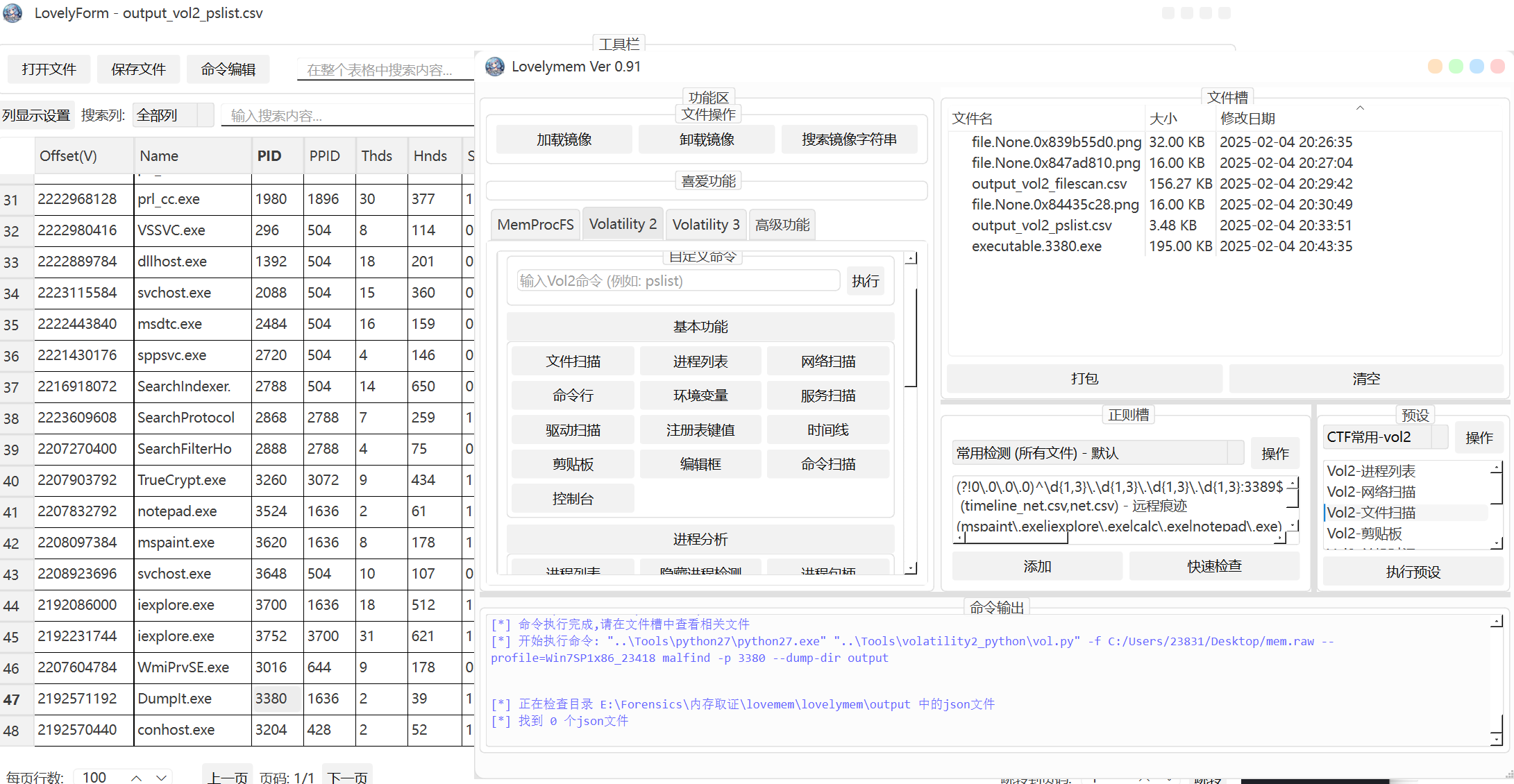
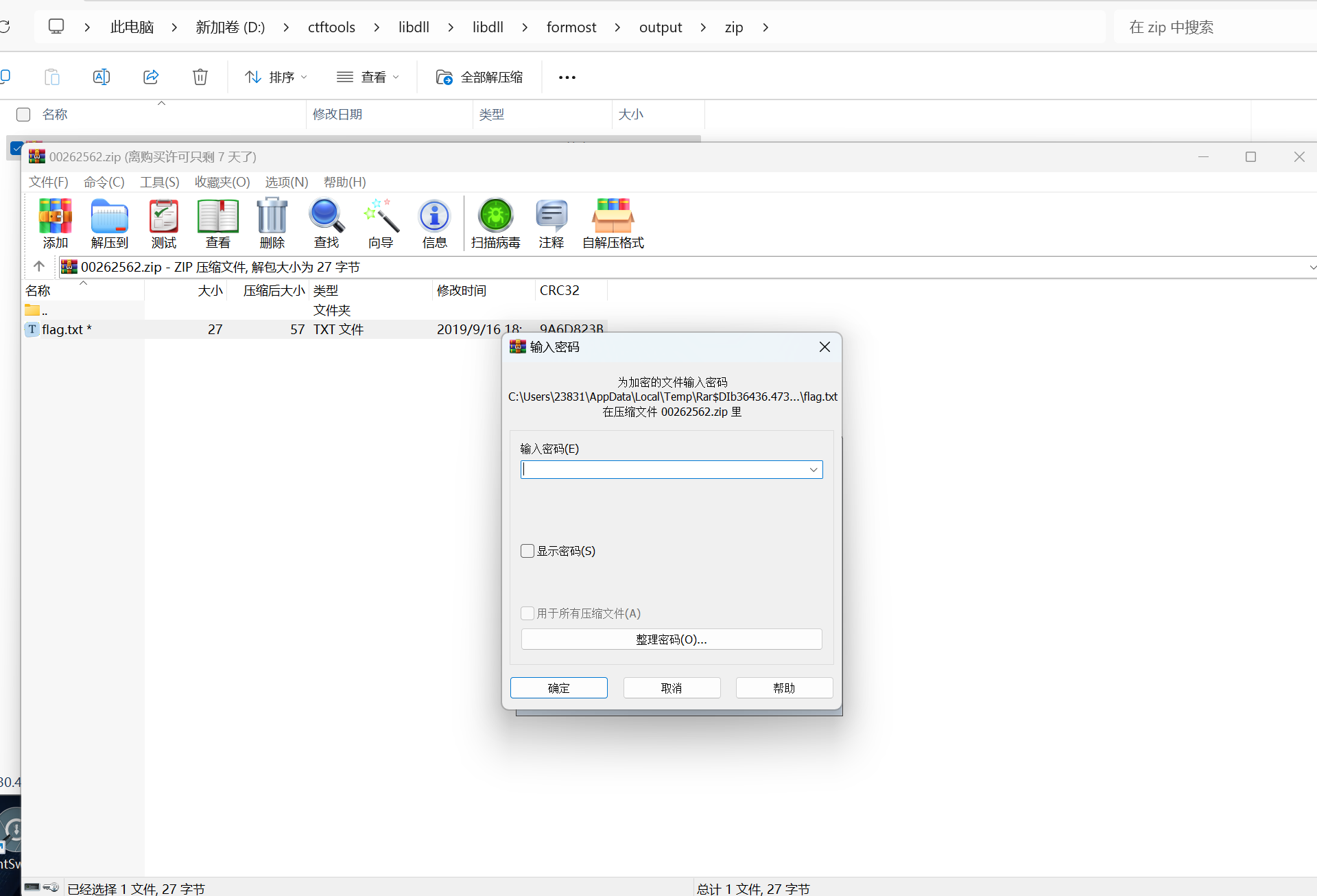
v
最后flag为
1 | flag{wm_D0uB1e_TC-cRypt} |
[*CTF2019]babyflash
下载附件
jPEXS Free Flash Decompiler反编译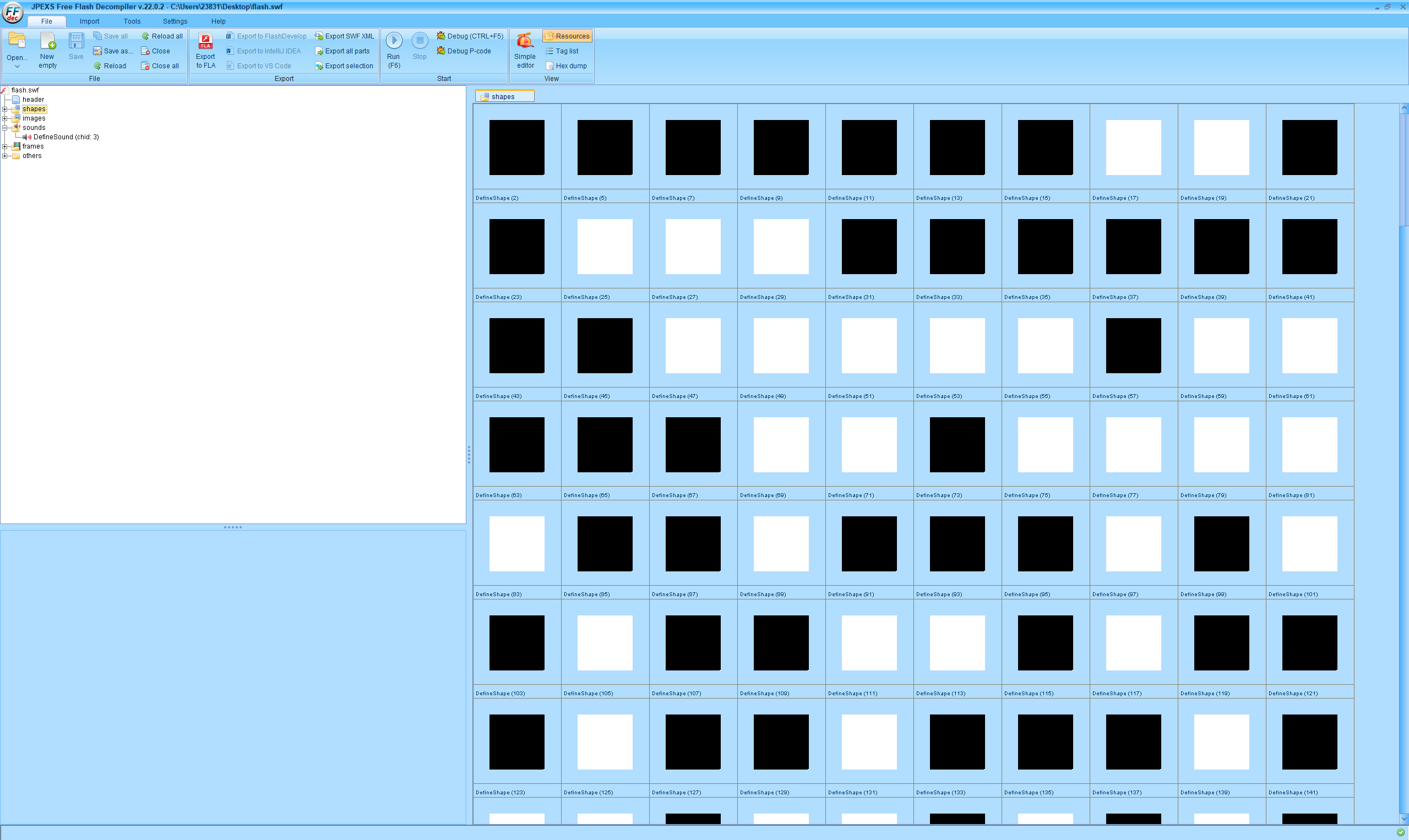
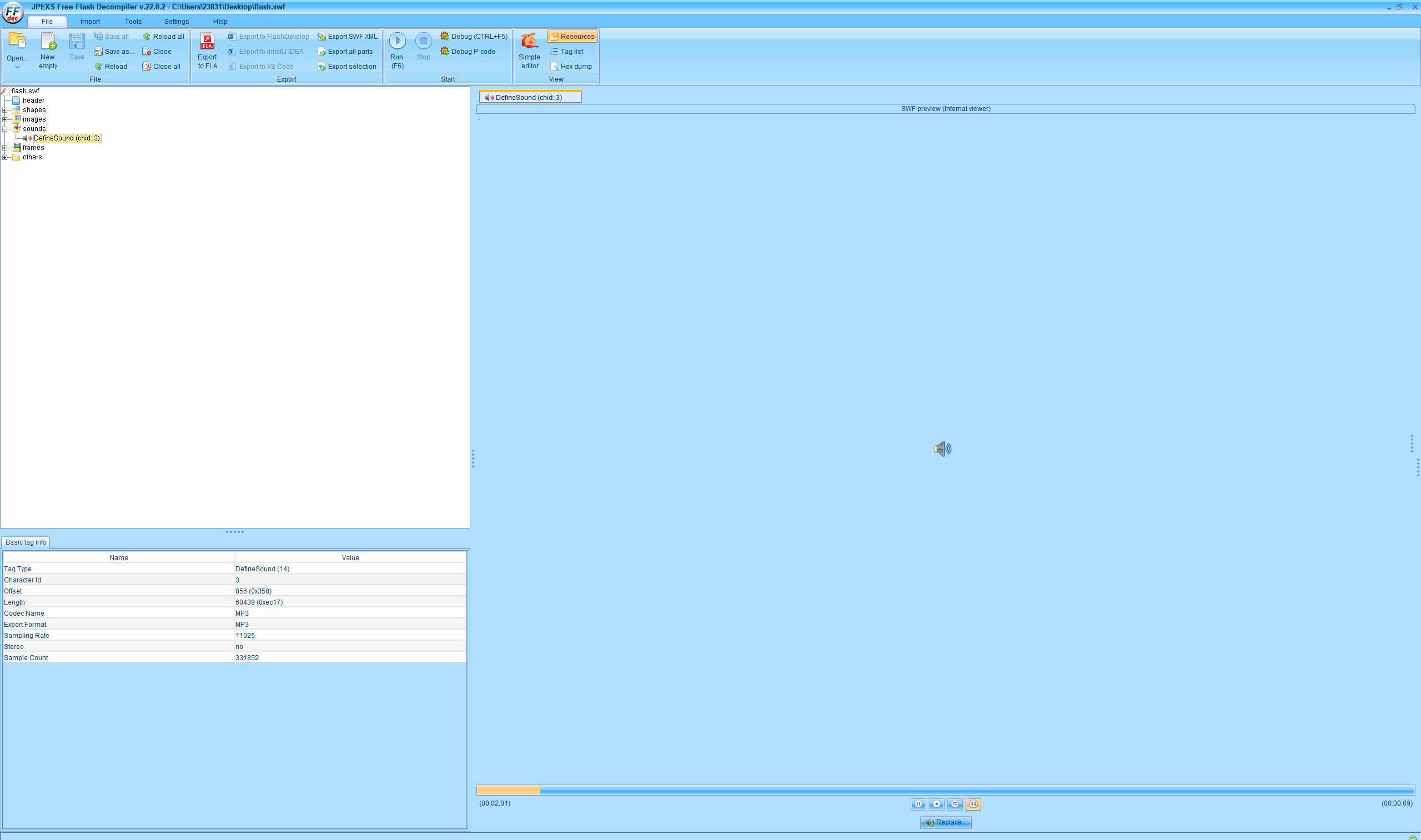
MP3文件用Audacity查看频谱图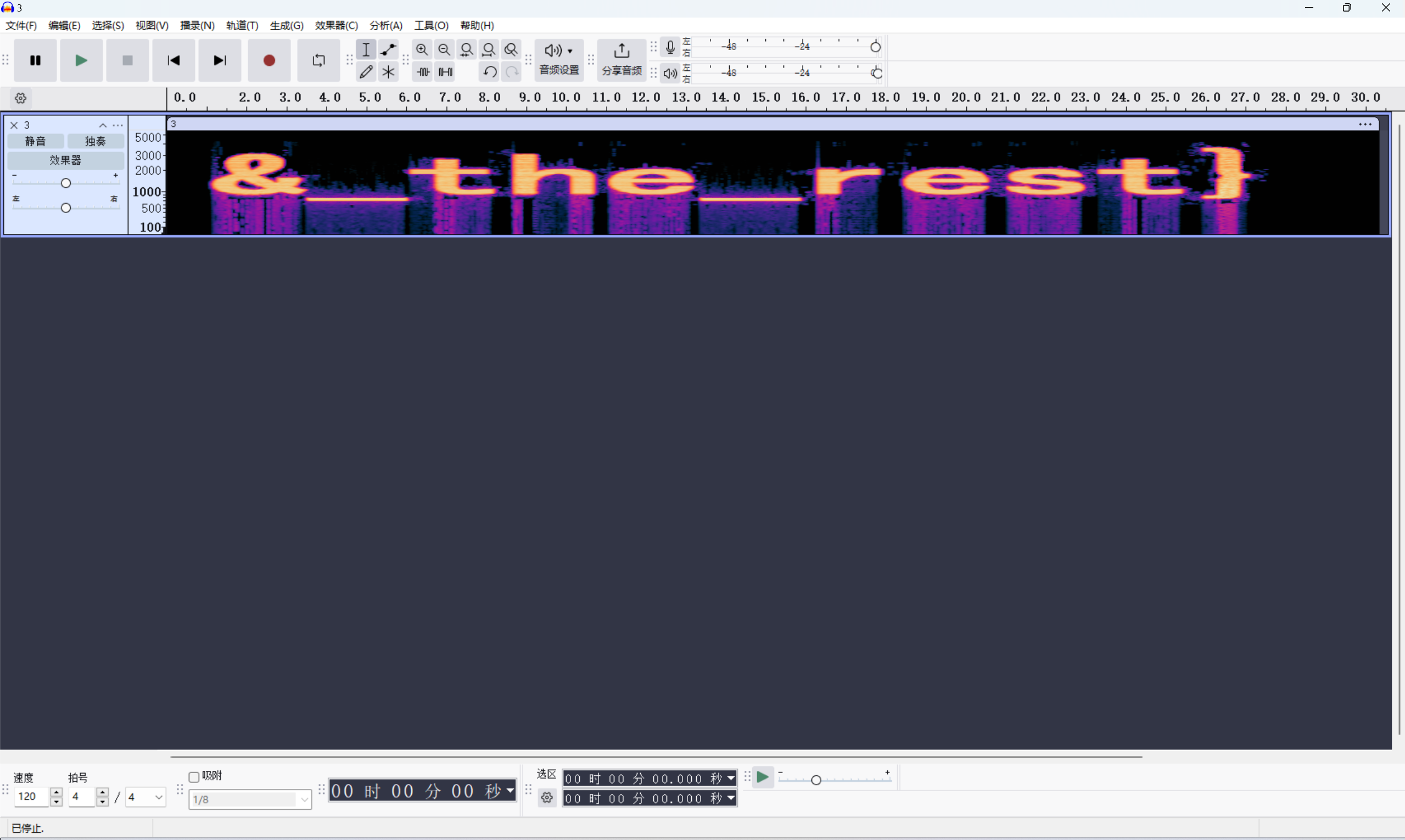
441张图片,应该是二维码,一张黑色图代表一个1,白色代表一个0,得到二进制数据然后按照21x21遇1填黑色,遇0填白色得到一张二维码
1 | from PIL import Image |
扫描二维码得到
1 | *ctf{half_flag_& |
最后flag为
1 | flag{halfflag&&_the_rest} |
[网鼎杯 2020 青龙组]虚幻2
解法请看
https://www.bilibili.com/video/BV1AK4y1t7T1/?t=997
[网鼎杯2020-青龙组]部分题解+笔记(未完成) – 「配枪朱丽叶。」
[NewStarCTF 2023 公开赛道]机密图片
zsteg一把梭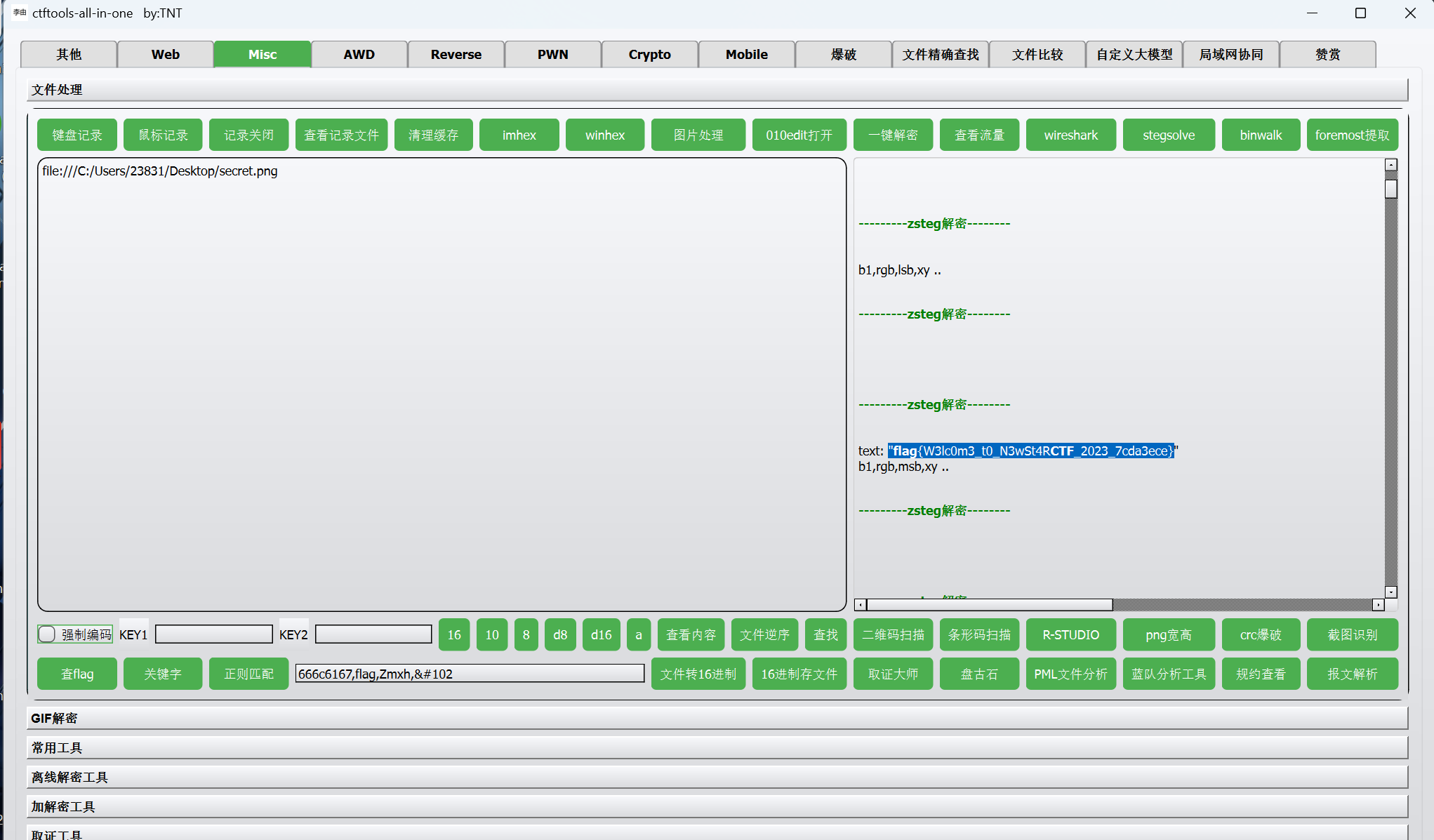
[NewStarCTF 2023 公开赛道]阳光开朗大男孩
下载附件
secret.txt
1 | 法治自由公正爱国公正敬业法治和谐平等友善敬业法治富强公正民主法治和谐法治和谐法治法治公正友善敬业法治文明公正自由平等诚信平等公正敬业法治和谐平等友善敬业法治和谐和谐富强和谐富强和谐富强平等友善敬业公正爱国和谐自由法治文明公正自由平等友善敬业法治富强和谐自由法治和谐法治和谐法治和谐法治法治和谐富强法治文明公正自由公正自由公正自由公正自由 |
核心价值观解码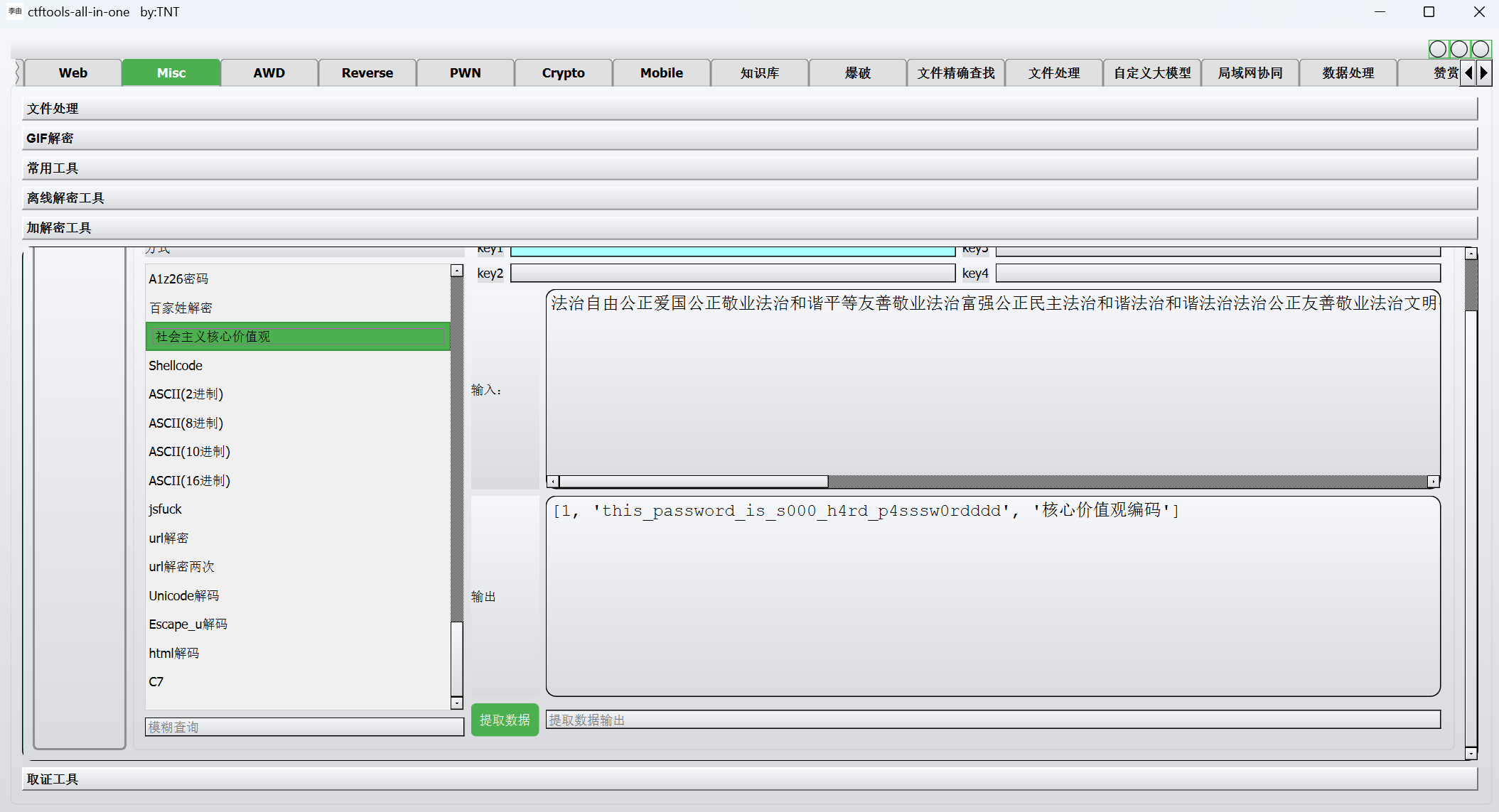
flag.txt
1 | 🙃💵🌿🎤🚪🌏🐎🥋🚫😆😍🌊⏩🔬🚹✉☀☺🚹🐅🎤🛩💵🌿🌊🚰😊🌊✉🐎❓🎈🌉👑🎅📮🥋👣🕹🚪☀🔄🚫🐍❓🐍😊☀🔬🍍🤣🎈🥋🙃👑🌏🐎🌊📮😂💵🏹👉❓😇🍴💧☺💵😁☃👉🎅👁☂🌿👉🍴🌪👌🍴🍵🖐😇🍍😀🗒🗒 |
emjio-aes解码
最后flag为
1 | flag{3m0ji_1s_s0000_1nt3rest1ng_0861aada1050} |
[NewStarCTF 2023 公开赛道]CyberChef’s Secret
下载附件
1 | 来签到吧!下面这个就是flag,不过它看起来好像怪怪的:-) |
赛博厨子一把梭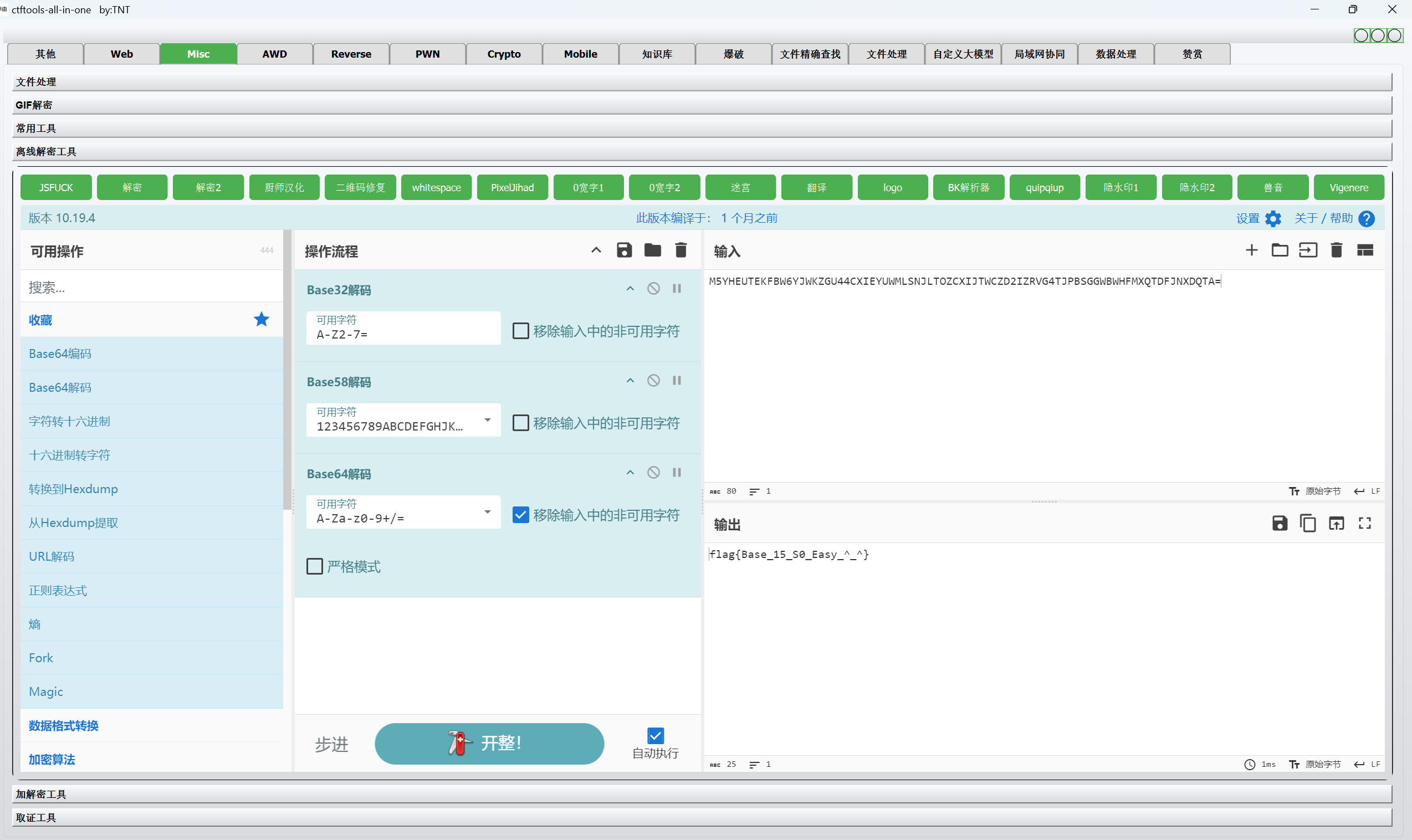
最后flag为
1 | flag{Base_15_S0_Easy_^_^} |
[b01lers2020]image_adjustments
下载附件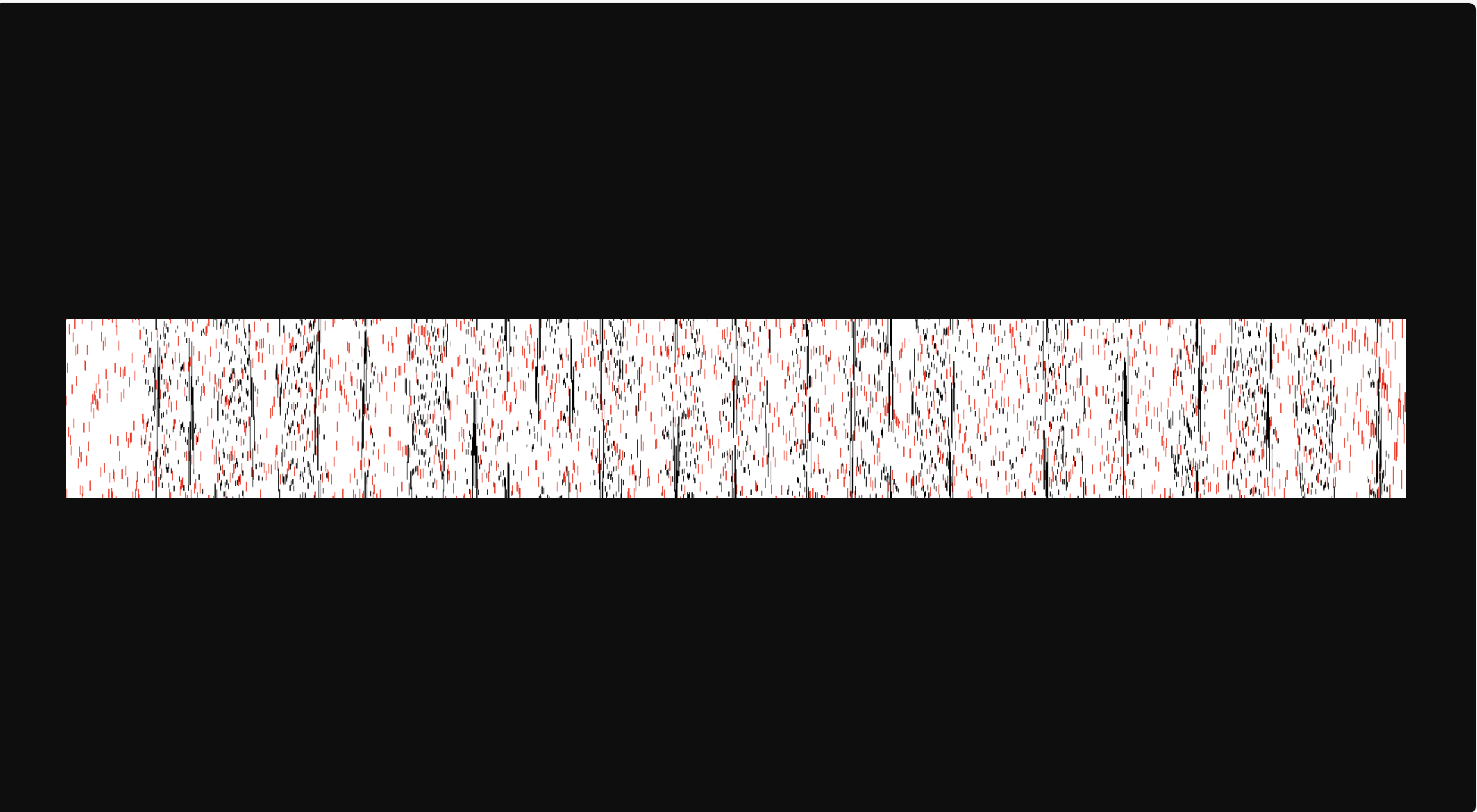
高度随机变换,需要进行还原,还原时可以利用红色部分进行对齐
1 | #!/usr/bin/env python3 |
运行得到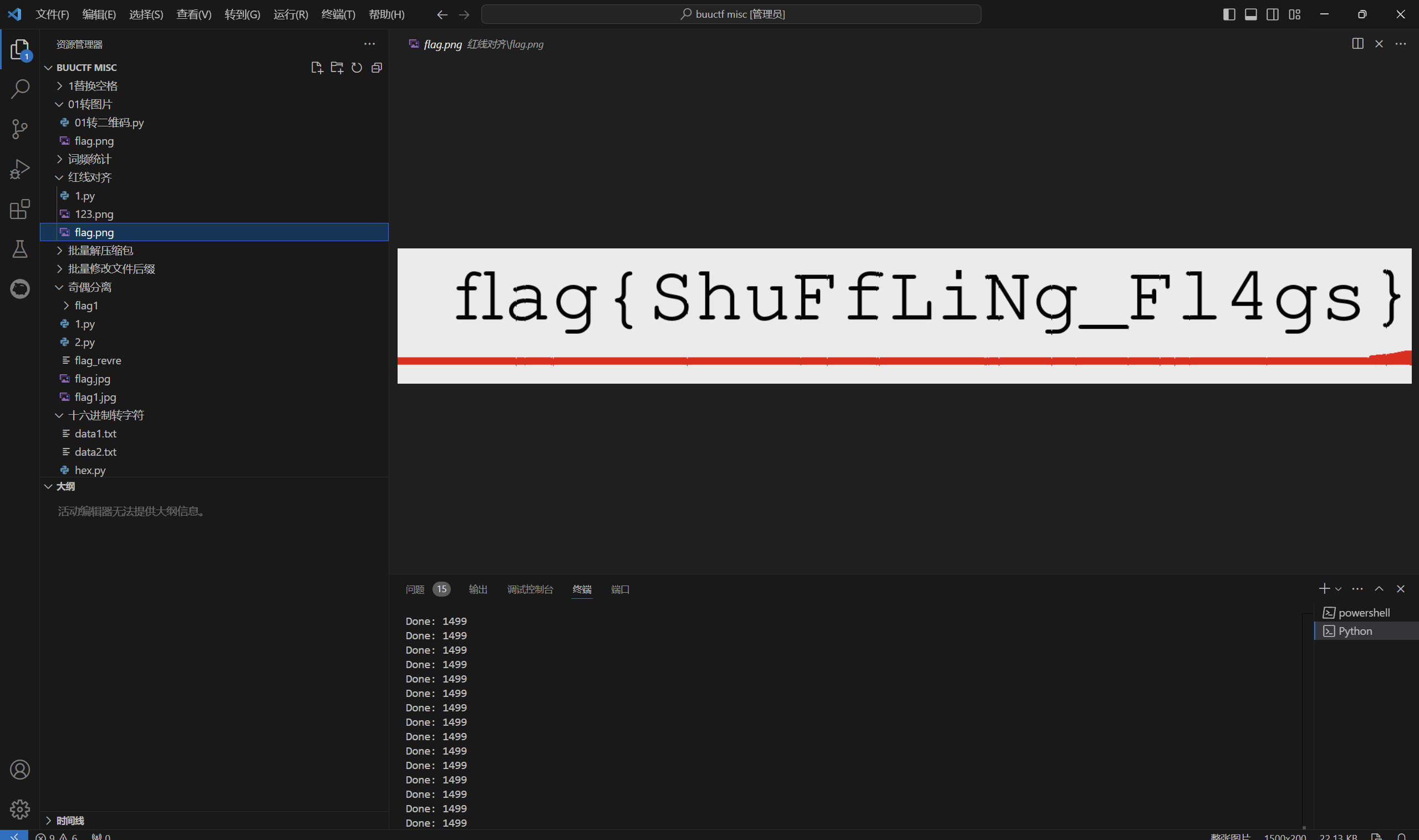
最后flag为
1 | flag{ShuFfLiNg_Fl4gs} |
[GKCTF 2021]银杏岛の奇妙冒险
下载附件
游戏题,直接找文件信息
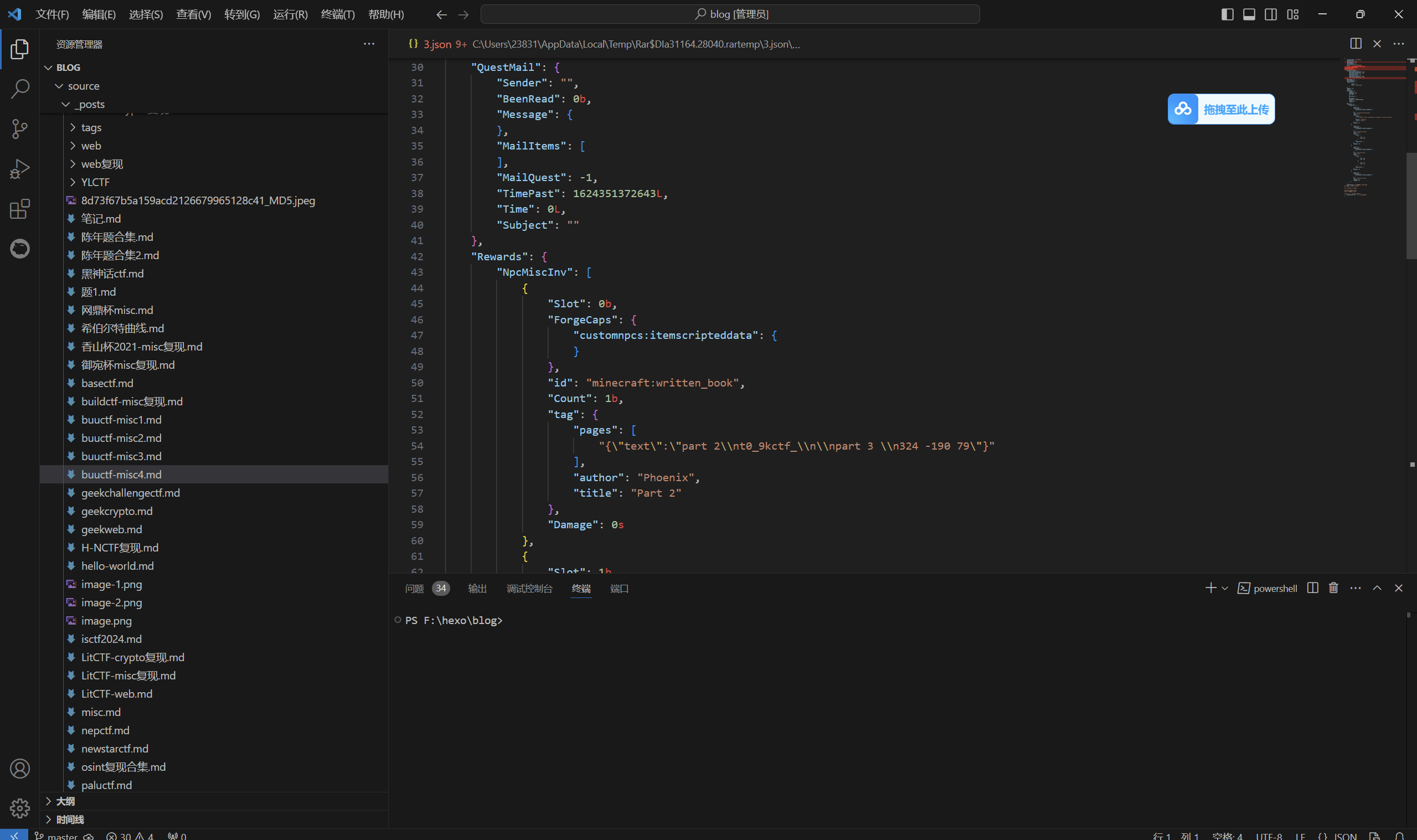
….省略
最后flag为
1 | flag{w3lc0me_t0_9kctf_2021_Check_1n} |
静静听这么好听的歌
下载附件
给的txt文件是matlab脚本,是把一个bmp的位图写进wav文件里
1 | fid=fopen('33.wav','rb'); |
用脚本解出原图
1 | import numpy as np |
运行得到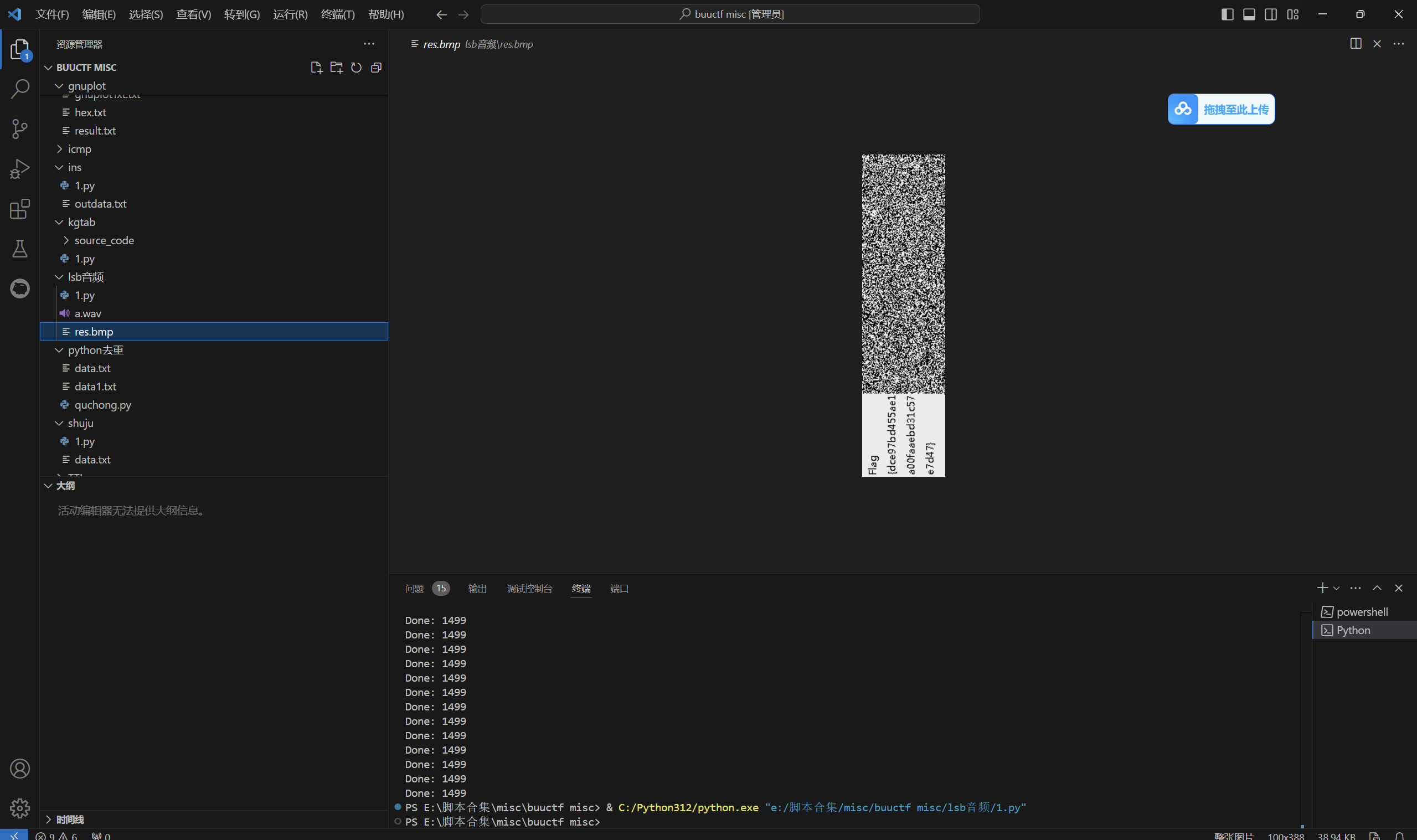
最后flag为
1 | flag{dce97bd455ae1a00faaebd31c57e7d47} |
[INSHack2018]GCorp - Stage 1
tcp追踪流
base解码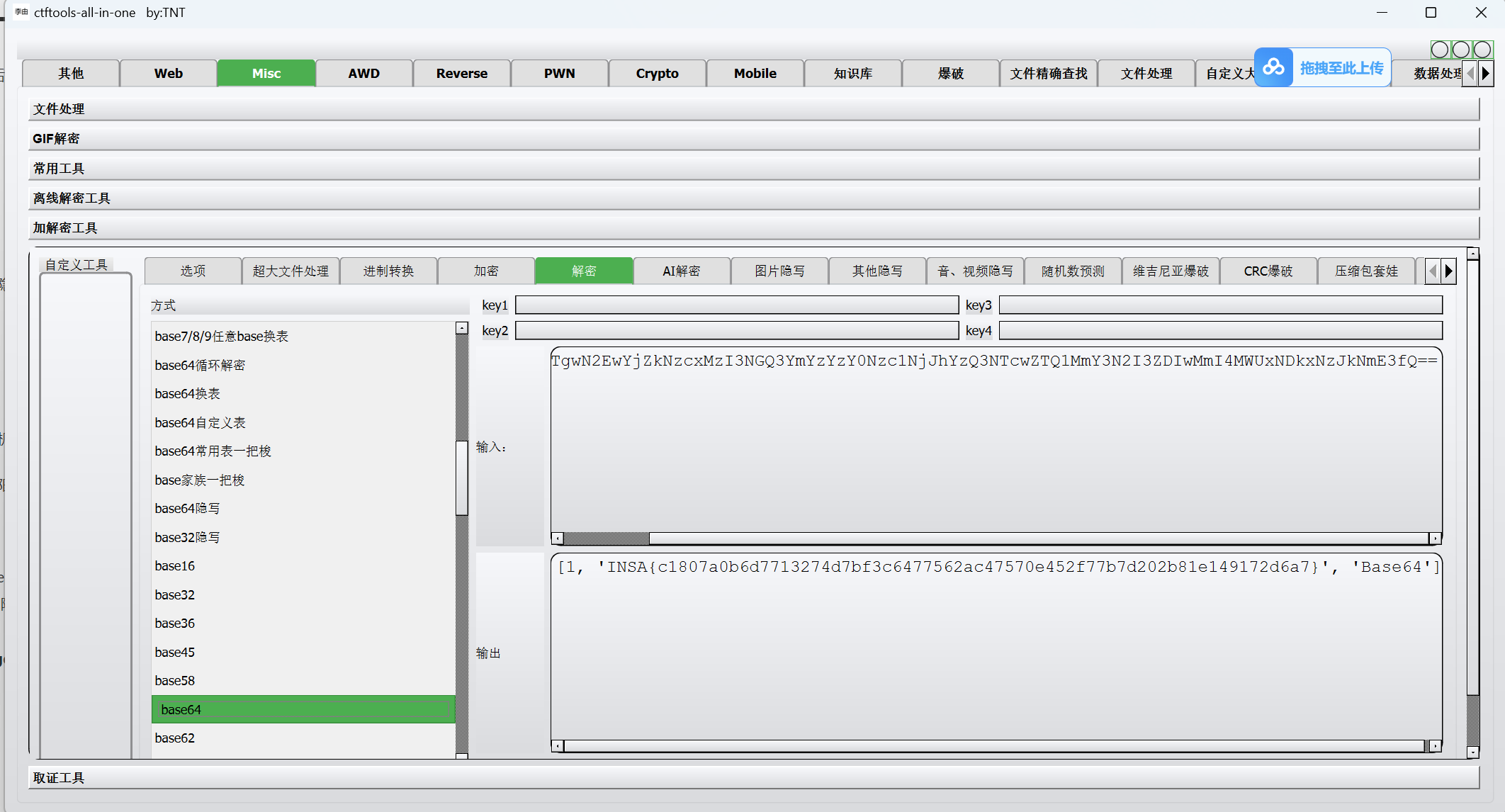
最后flag为
1 | flag{c1807a0b6d7713274d7bf3c6477562ac47570e452f77b7d202b81e149172d6a7} |
[NewStarCTF 2023 公开赛道]大怨种
gif提取帧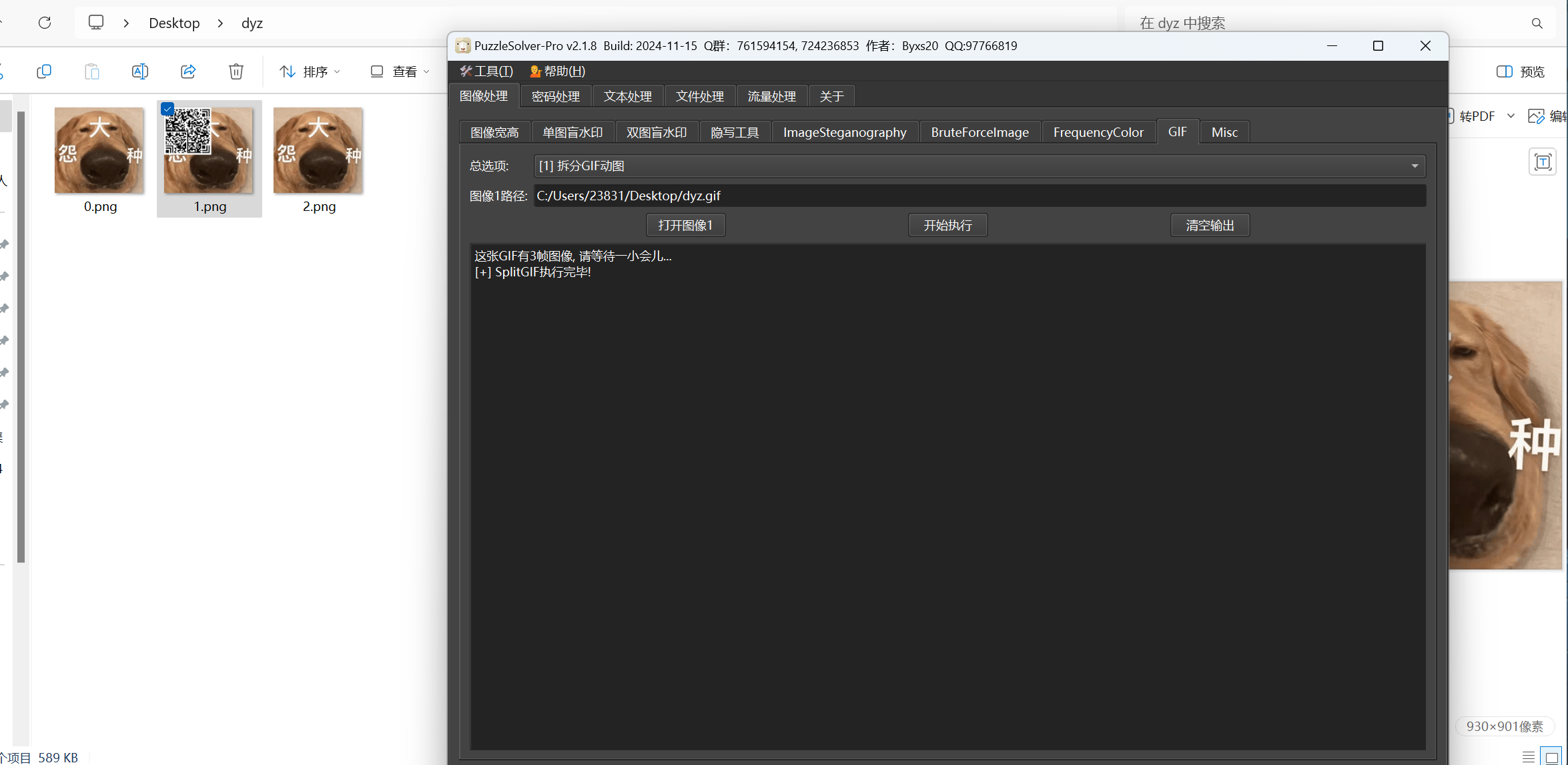
汉信码扫描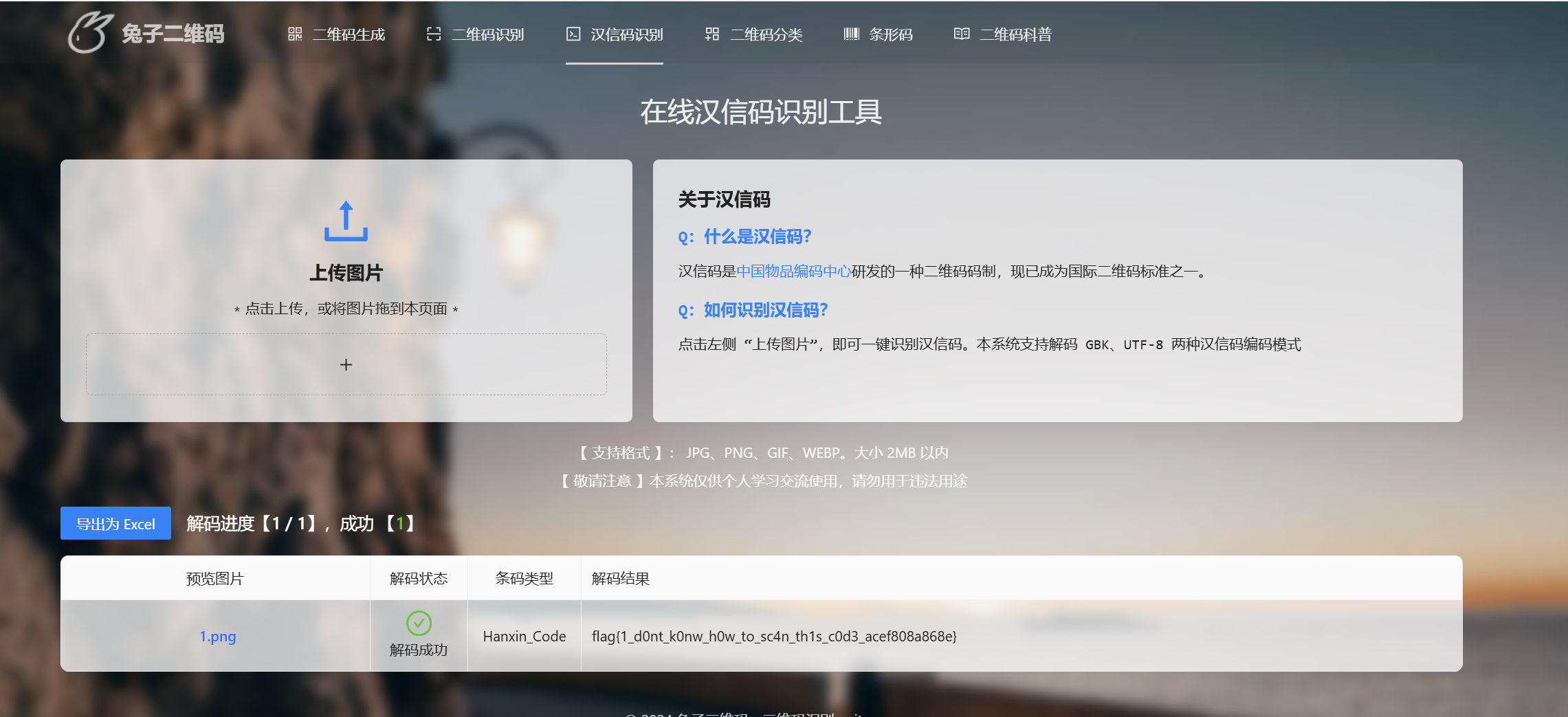
最后flag为
1 | flag{1_d0nt_k0nw_h0w_to_sc4n_th1s_c0d3_acef808a868e} |
[SWPU2019]Android1
安卓逆向
关键代码
1 | char *Aa(void) |
每个函数的v3与对应的十六进制数异或得到的字符串
1 | Aa = "MWa" |
最后flag为
1 | flag{YouaretheB3ST} |
[RCTF2019]printer
打印机流量
请看
从一道题学习打印机流量(RCTF2019-Printer)_rctf2019]printer-CSDN博客
[NewStarCTF 2023 公开赛道]新建Word文档
下载附件
找到新佛曰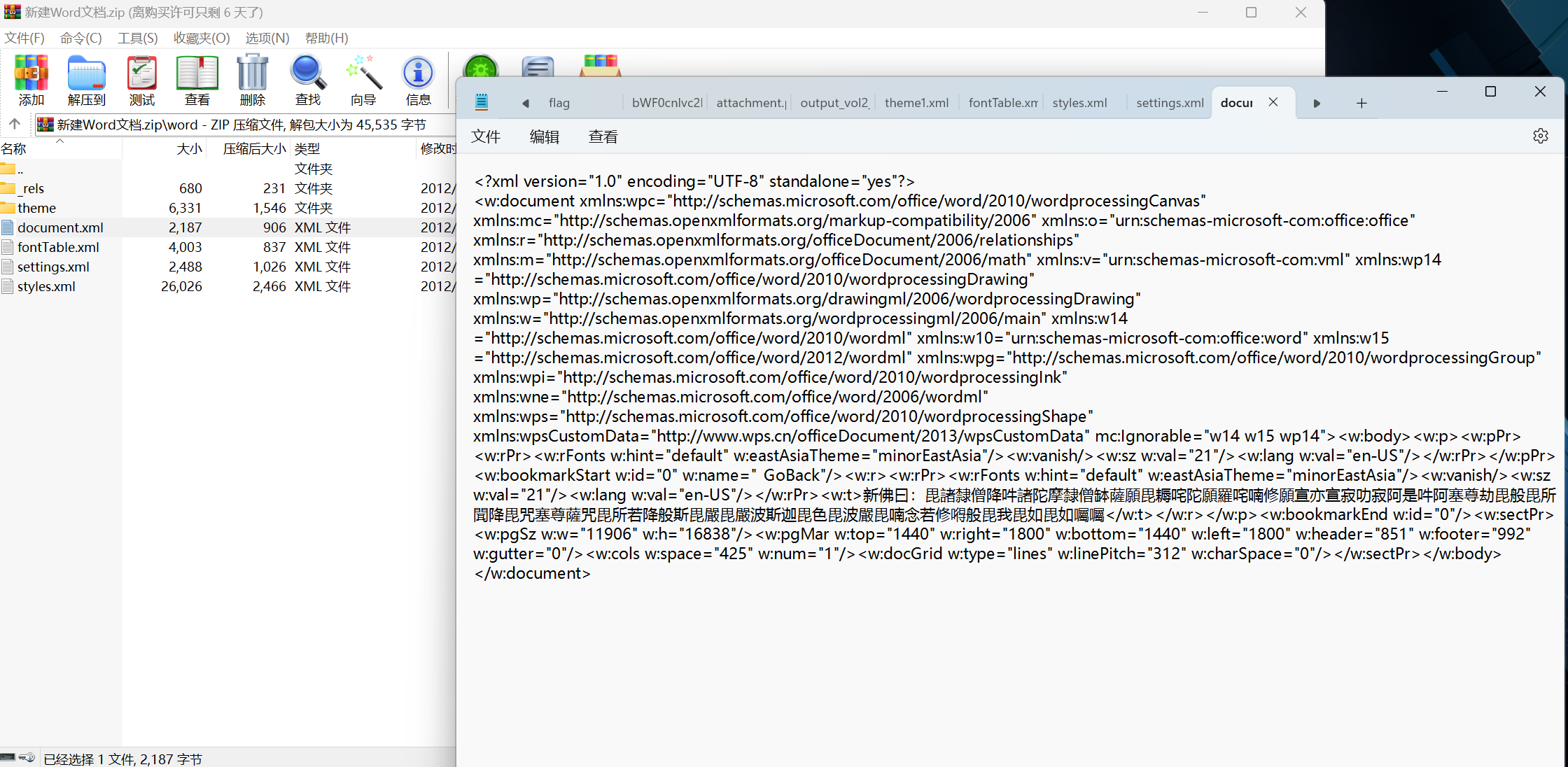
解码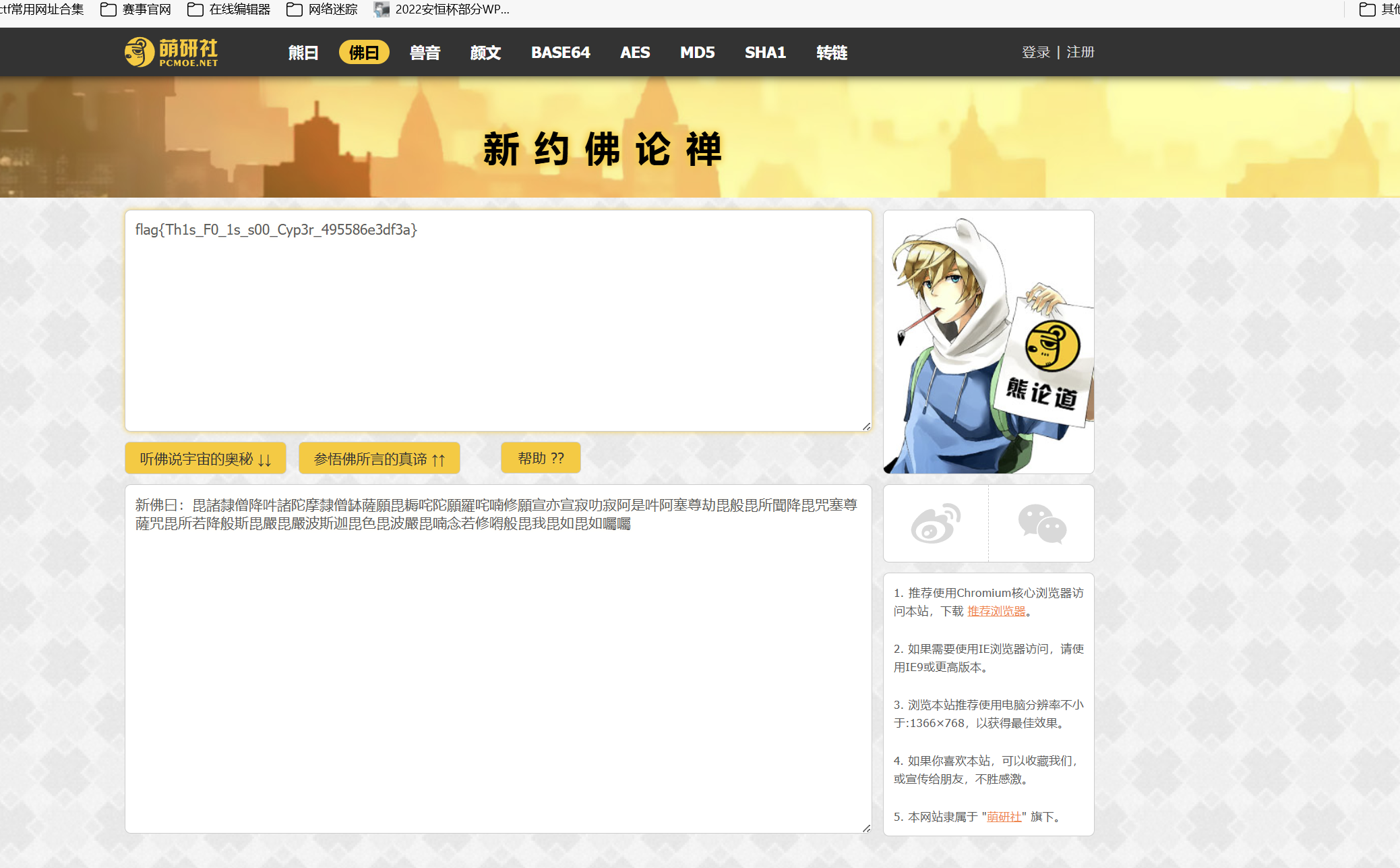
最后flag为
1 | flag{Th1s_F0_1s_s00_Cyp3r_495586e3df3a} |
[watevrCTF 2019]Polly
1 | -510233931851656757*x**56/710998587804863451854045647463724949736497978881168458687447040000000000000 + 28538582555324529581*x**55/25392806707316551851930201695133033919160642102898873524551680000000000000 - 361611288555263491*x**54/421055535502492258043032818391295177534479825940370161664000000000000 + 2189223797409040145903*x**53/5129859940872030677157616504067279579628412546040176469606400000000000 - 3001755643562030554208767*x**52/19357962041026530857198552845536904074069481305811986677760000000000000 + 78238787580756843015401*x**51/1781188998990295441405829301208769237584604463177400320000000000000 - 116104436553238240592813791*x**50/11496527230247656900485565886772482623174748513067073536000000000000 + 127279887341335237997305957*x**49/65694441315700896574203233638699900703855705788954705920000000000 - 20305349569334865003353693141*x**48/64170394447571083344765063383345446352972606387257344000000000000 + 755344461848261566273335985217*x**47/16909766104427515205715118053719408160580619250696192000000000000 - 8730828190255482707329907709523*x**46/1583041933180448232024394030560965870352228185171558400000000000 + 76555149545632714960652198194597*x**45/127331633755818662141092563327729863484853136633364480000000000 - 1602375720398047527703588216319184983*x**44/27479475110939521552978869398000199787640242135105536000000000000 + 114295162137526589722365996075069211717*x**43/22572425983986035561375499862643021254133056039550976000000000000 - 13848681865733026134505571948717935637*x**42/34996009277497729552520154825803133727338071379148800000000000 + 153346974308020314565759178978111441*x**41/5485267911833499929862093232884503719018506485760000000000 - 520024520896904430645934556087134499251423*x**40/290210808642664098728215918067635743104754738266112000000000000 + 583372437848702106759949552819801879184581*x**39/5580977089282001898619536885916071982783744966656000000000000 - 46031013908208473758789005123614987736509587*x**38/8272977802935673402659548795593236115655904303513600000000000 + 7353657867840940108498978410191786786833213*x**37/27150699353263793020311260526078188024353353891840000000000 - 92499773752352276492046888338669680452103462189*x**36/7657889561176967262139073481714360724817612636160000000000000 + 4100551582505375935469899571343423946185109603489*x**35/8296047024608381200650662938523890785219080355840000000000000 - 1895954357110172205089772212408286791708615900917*x**34/102036942013899875729927939885587961529432539136000000000000 + 43118050173835025743884479345094473671998423653*x**33/67129567114407812980215749924728922058837196800000000000 - 22765966699209423168314620580071311613337850078228970157*x**32/1114243406791786642970813103550620539901403327365120000000000000 + 2164682230392596021581197470695955891436192181935306391*x**31/3617673398674631957697445141398118636043517296640000000000000 - 920699702649221064972928655611480860602416008467275417*x**30/57052913814223586429637127677963161285274107904000000000000 + 686056125302514633652788467458025065050820545750401507*x**29/1711587414426707592889113830338894838558223237120000000000 - 3138304869574821781724911760498738183508227936479448972609*x**28/342317482885341518577822766067778967711644647424000000000000 + 1270675513242488953141124524513884117237971552020405481903*x**27/6583028517025798434188899347457287840608550912000000000000 - 35251878159156858646651490873547468067999378927697697003224477*x**26/9428213442084348517445341645428327645319566616166400000000000 + 640581045258286772319400657438117285194045922802459043053203*x**25/9620625961310559711678920046355436372775067975680000000000 - 72656459972106788902891971241582058202821865848124369081172639*x**24/66716462086011457208029806848269051769244352512000000000000 + 154039473157326645352130477125406816808322554770621702623189519*x**23/9427326164327705909830298793777148619567136768000000000000 - 1082910009287427089558040173029448590098449209287440350613671*x**22/4822161720883737038276367669451226915379609600000000000 + 24188920823778246702349239533423129779289240972762319245699197*x**21/8570296513025187190754817085251953290515578880000000000 - 2312064026649698678901994207690698059469649821996032406197587664228741*x**20/71419066189405618046396886086957233654685736370176000000000000 + 862370556128011088565191676373092759230061876592574879284609935706793*x**19/2550680935335914930228460217391329773381633441792000000000000 - 32072107483702086982352528206453150709858865925578274033380368180437*x**18/10002670334650646785209647911338548130908366438400000000000 + 1529698138827681013559573339316154298621053459717691815776842419379*x**17/55570390748059148806720266174103045171713146880000000000 - 222611348623707141383036923098732823232255364898093370342989110678452081*x**16/1044260259473944837992951668521686390518442885120000000000000 + 19351471406694225111369749822067705924291211128650839886054241035573*x**15/13048686203253171864759230125976987935703040000000000000 - 788448884149338619773551061237815179858025448137798058040565357883017969*x**14/85480045326791055697402842485438742223090876416000000000000 + 1073836757430890424151052096696872926581023064319957457780403520628397*x**13/21054198356352476772759320809221365079579033600000000000 - 13037261936583491232564987358021148191312145269662640728042654537466177*x**12/52337322240932848864901859644270462537564160000000000000 + 193553176960028089077524490434690010049391798907017144709511622501501*x**11/181523857324358216783809467780676473323520000000000000 - 68187858129806282947338026458215966993811977794098721136854363544114709*x**10/17205436276727086314158740721145118396514304000000000000 + 8945934592679151193925448392874011400632217576523903097012117504044751*x**9/707334602487669104026526007424854867412254720000000000 - 1869710221567968463761175994053678221652715546983576126590166640405599343*x**8/54712331502421205196451786674312523994337902592000000000 + 150097834583670559919903774847355537654811358204762610127392287652832711*x**7/1954011839372185899873278095511161571226353664000000000 - 887795495236087230655513134787312551397755543548982957604351894153*x**6/6324332742830674887191952972548659841433600000000 + 325850556958534026053020666873255701298636569528110069255986051*x**5/1611756757211697568252622935684799553945600000 - 1383255113415521659958099444243664043564187251342510179583421*x**4/6303358038091792437823864786842855398400000 + 1288933044552801369576288324542563196552750611910520778643*x**3/7696407860917939484522423427158553600000 - 58143815812249254268696937296354052881595701176023*x**2/732857216672564586715802770080000 + 76949958412245985708257714245417562997*x/4439171857433454741600 + 119 |
x=0时得到119,对应的ascii码字符是w,所以flag应该就是把x从0开始,把计算结果转换成字符
1 | import sympy |
运行得到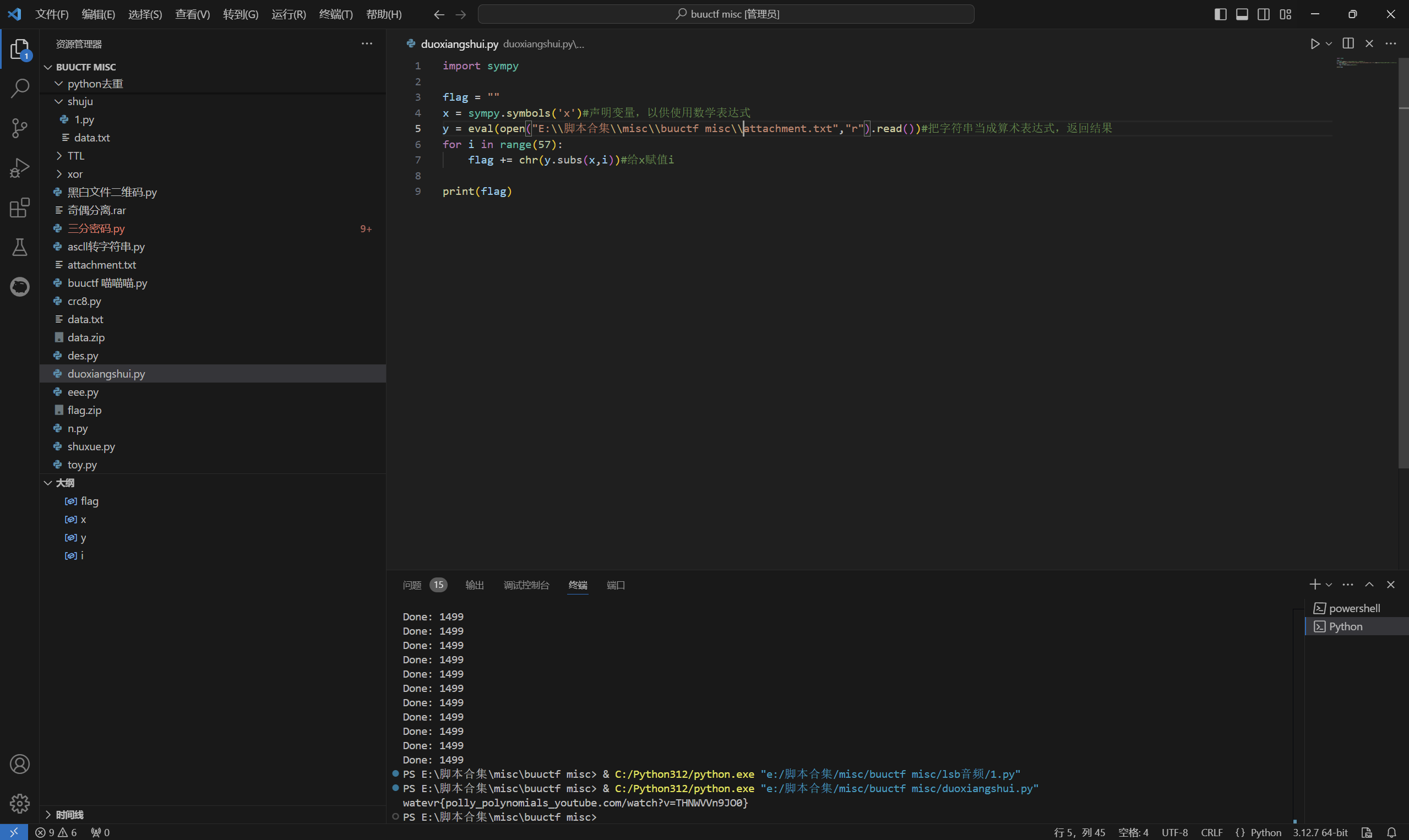
最后flag为
1 | flag{polly_polynomials_youtube.com/watch?v=THNWVVn9JO0} |
[INSHack2019]Crunchy
参考
https://blog.csdn.net/caozhk/article/details/53407845
大佬脚本
1 | n = 17665922529512695488143524113273224470194093921285273353477875204196603230641896039854934719468650093602325707751568 |
最后flag为
1 | flag{41322239} |
Weird_List
下载附件
1 | [120] |
一个没后缀的文件,用010打开,好多组数据,但加起来都是120,其中1特别多,把是1的地方画出来
1 | s =[ |
最后flag为
1 | flag{93ids_sk23a_p1o23} |
[NewStarCTF 2023 公开赛道]压缩包们
加上后缀.zip,修复压缩包flag.zip,发现一串base64编码
SSBsaWtlIHNpeC1kaWdpdCBudW1iZXJzIGJlY2F1c2UgdGhleSBhcmUgdmVyeSBjb25jaXNlIGFuZCBlYXN5IHRvIHJlbWVtYmVyLg==
解码得到密码提示:6位纯数字,爆破得到密码:232311,解压压缩包得到flag
最后flag为
1 | flag{y0u_ar3_the_m4ter_of_z1111ppp_606a4adc} |
[BSidesSF2020]toast-clicker1
jadx查看apk文件,发现一共有22个数字,猜测可能是每个数字偏移0-22
1 | a= '67, 83, 68, 120, 62, 109, 95, 90, 92, 112, 85, 73, 99, 82, 53, 99, 101, 92, 80, 89, 81, 104' |
最后flag为
1 | flag{Bready_To_Crumble} |
[b01lers2020]minecraft_purdue
[BUUCTF:b01lers2020]minecraft_purdue - B0mbax - 博客园
[BSidesSF2019]bWF0cnlvc2hrYQ
从一道CTF题目到非对称加密GPG/PGP的学习 | m0re的小站
[NewStarCTF 2023 公开赛道]空白格
解密即可
Whitelips the Esoteric Language IDE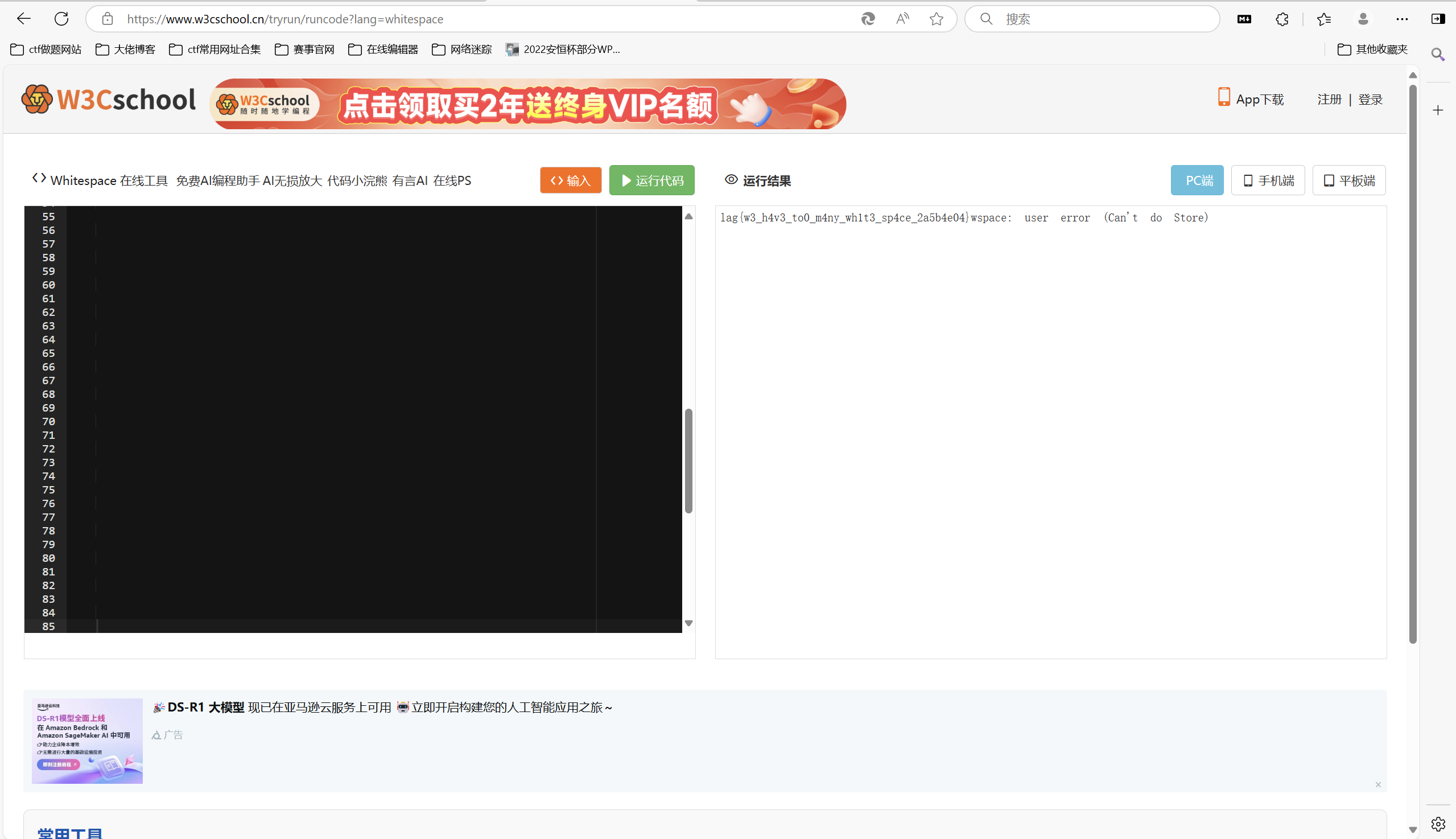
最后flag为
1 | flag{w3_h4v3_to0_m4ny_wh1t3_sp4ce_2a5b4e04} |
[GWCTF2019]math
nc连接环境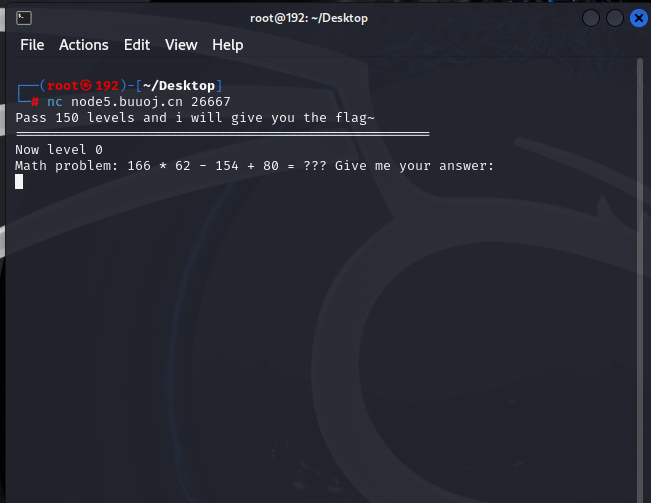
计算150次
exp:
1 | from pwn import * |
[NPUCTF2020]回收站
AccessData FTK Imager挂载得到flag
[NewStarCTF 公开赛赛道]还是流量分析
题目描述:
1 | 救赎之道,就在其中。 Flag格式:flag{WebShell-Key值_机密文件内容} 例如:flag{d8ff731bdba84bf5_sercet} P.S:请注意Key值并非密码! |
WebShell-Key
1 | @session_start(); |
在tcp.stream eq 35发现读取secret
1 | <?php |
php在线运行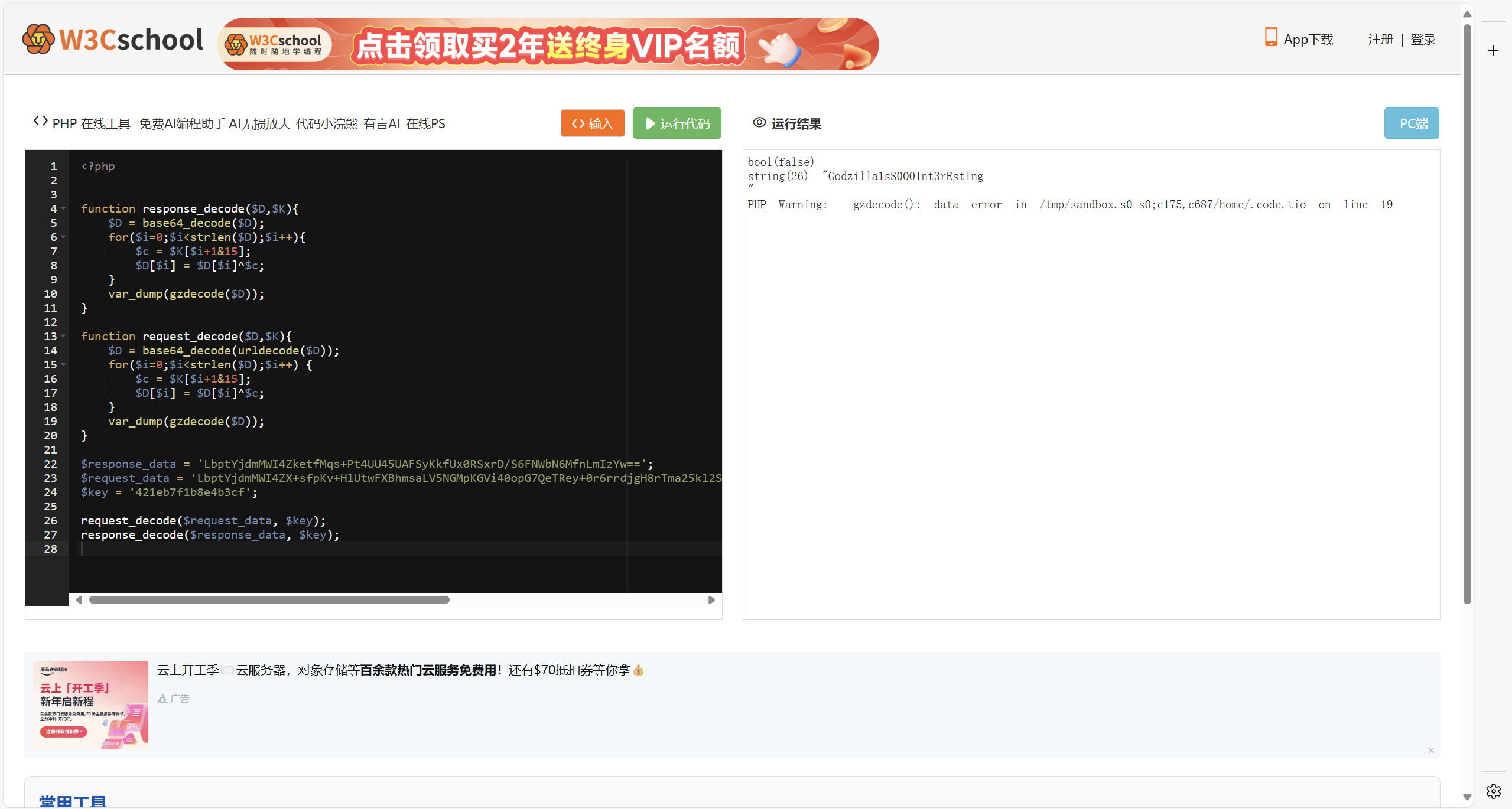
最后flag为
1 | flag{421eb7f1b8e4b3cf_Godzilla1sS000Int3rEstIng} |
[NewStarCTF 2023 公开赛道]Nmap
题目描述:
1 | 请给出Nmap扫描得到所有的开放端口用英文逗号分隔,端口号从小到大排列。 例如flag{21,22,80,8080} |
过滤tcp.flags.syn == 1 and tcp.flags.ack == 1
最后flag为
1 | flag{80,3306,5000,7000,8021,9000} |
[BSidesSF2020]mpfrag
下载附件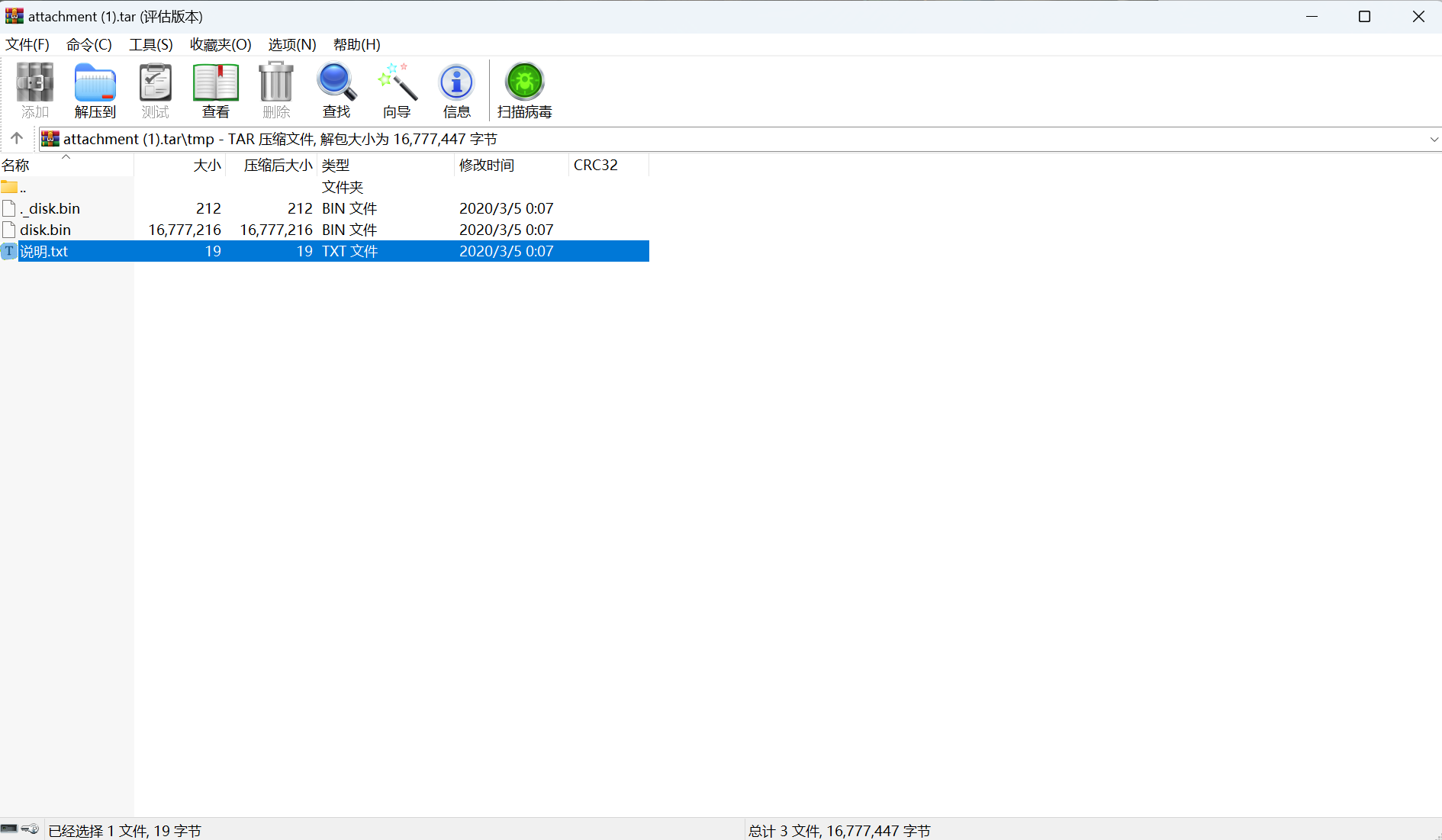
挂载文件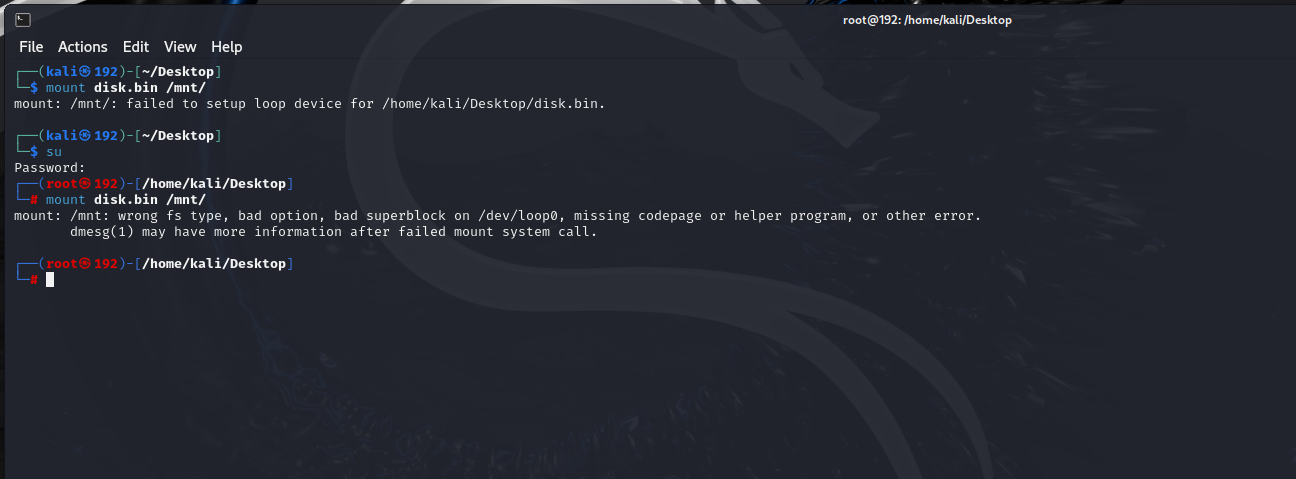
提示超级块损坏
用备用块修复。备用块在文件系统的8193块(ext2 的默认块大小是1k)
dd提取备用块
1 | dd if=disk.bin bs=1024 skip=8193 count=1 of=disk2.bin |
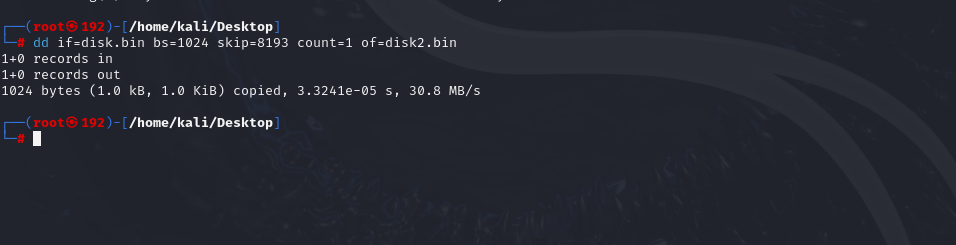
把备用块放入disk.bin
1 | dd if=disk2.bin of=disk.bin bs=1024 conv=notrunc seek=1 |
fls列出文件系统中所有文件
1 | fls disk.bin |
cloud_key.mpeg已经被删除了,尝试修复并提取
1 | blkls disk.bin > unalloc.bin |
1 | hexdump -C unalloc.bin | egrep '^.....[048c].. 00 00 01 ba' | head |
dd if=unalloc.bin bs=1 skip=10240 of=out.mpeg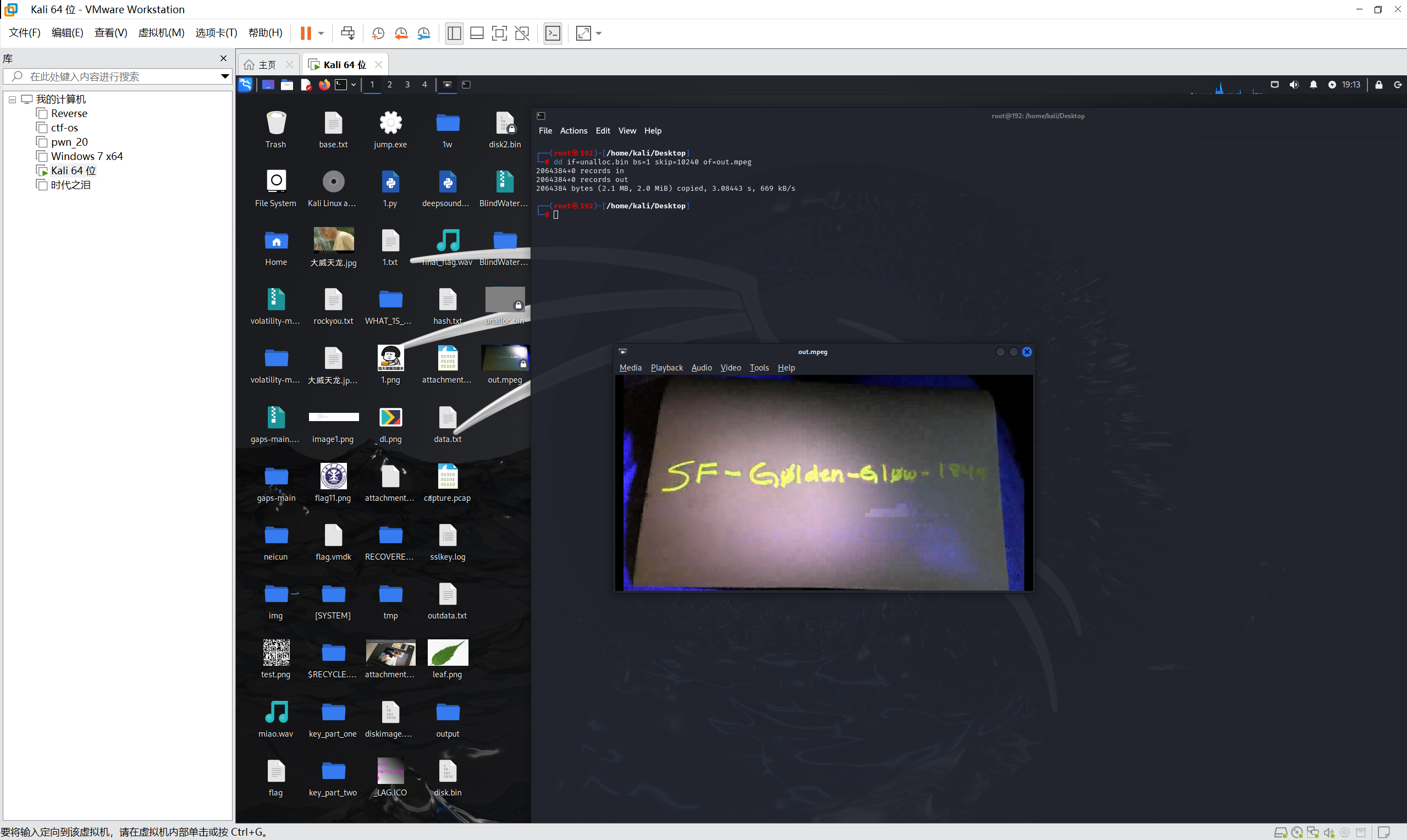
提取压缩包
1 | icat disk.bin 29 > cloud.zip |
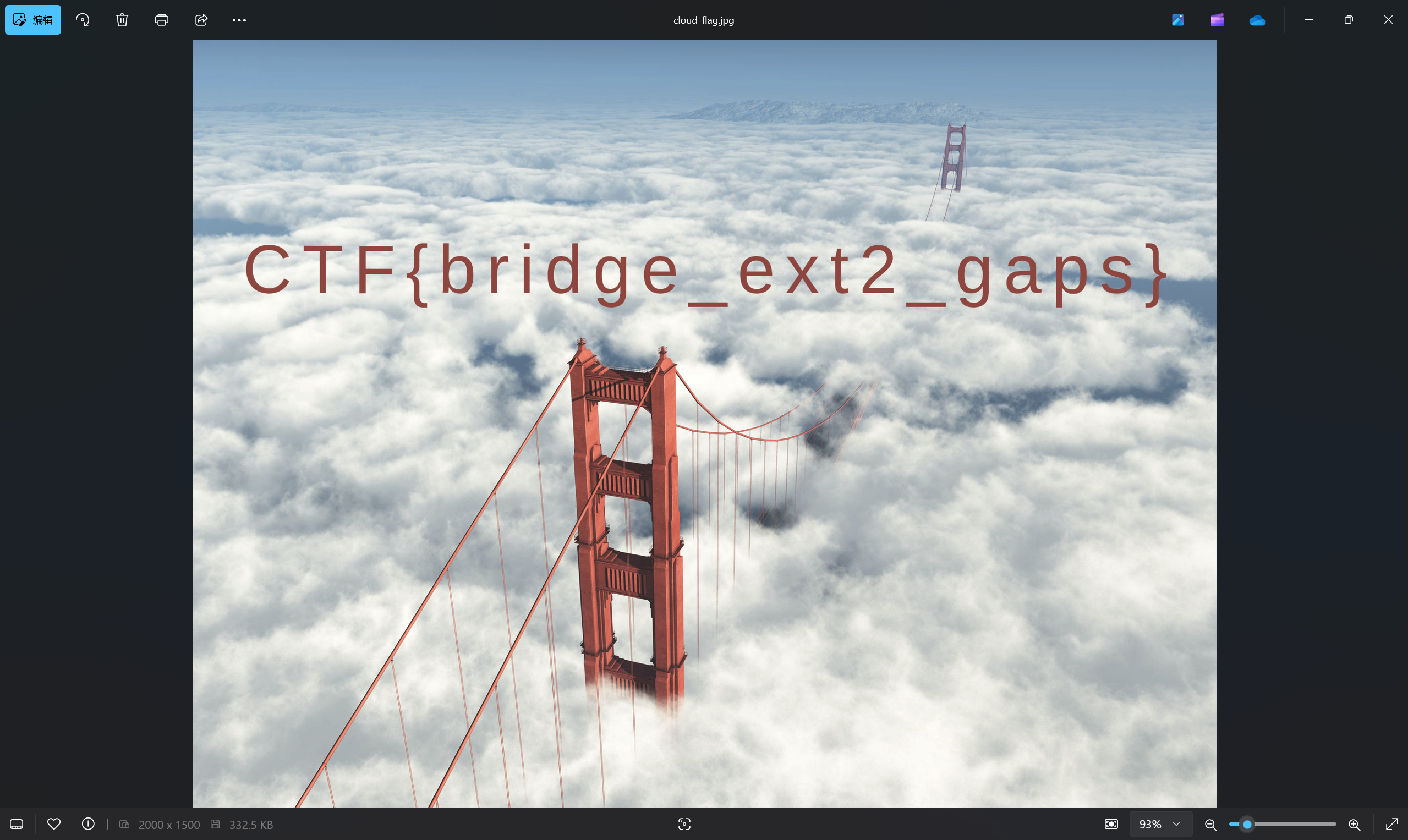
最后flag为
1 | flag{bridge_ext2_gaps} |
[NewStarCTF 2023 公开赛道]永不消逝的电波
题目描述:
1 | 或许有节奏的声音中传递着一些信息;flag请按照flag{}的格式进行提交,涉及字母均为小写 |
一眼摩斯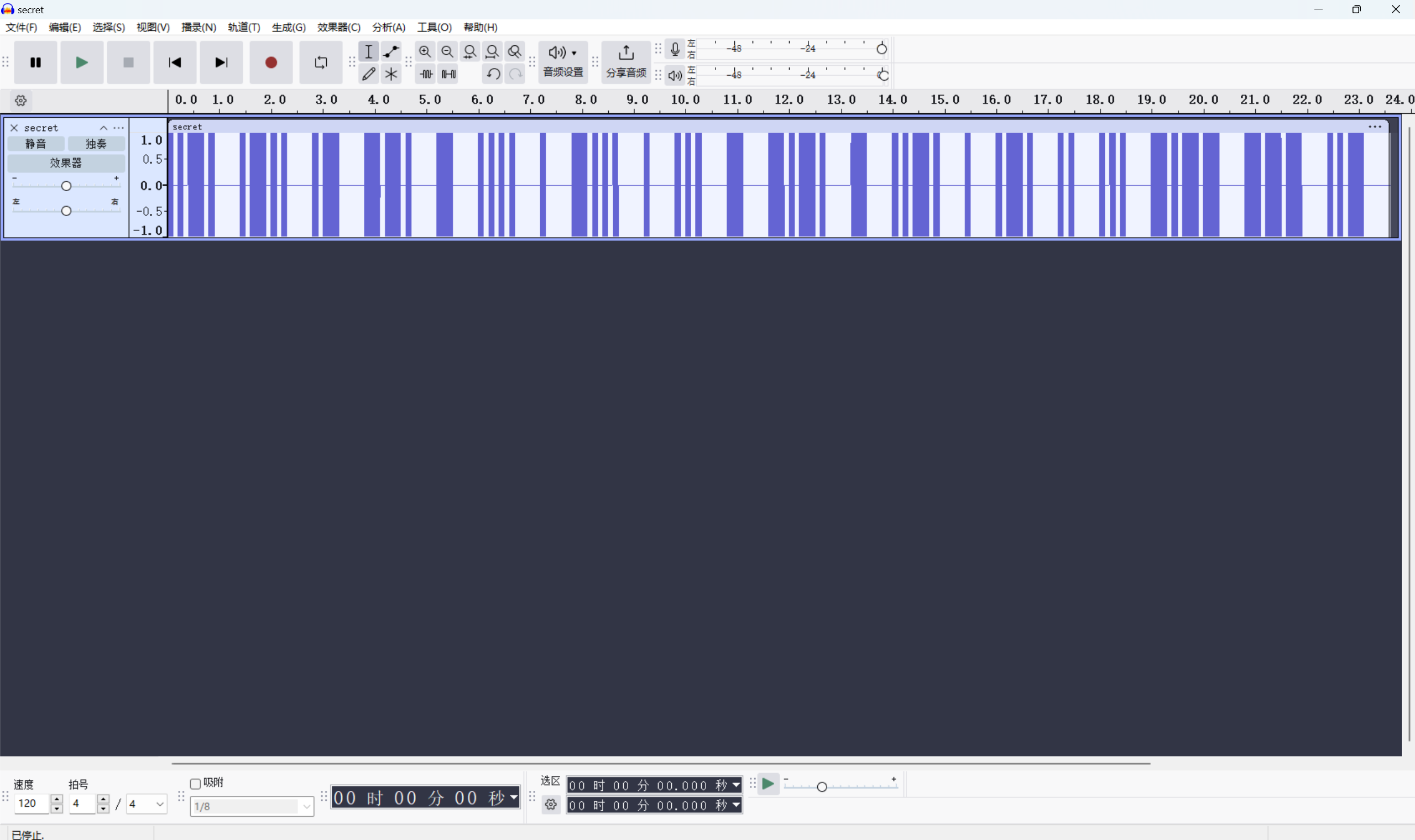
整理为
1 | ..-. .-.. .- --. - .... . -... . ... - -.-. - ..-. . .-. .. ... -.-- --- ..- |
摩斯解密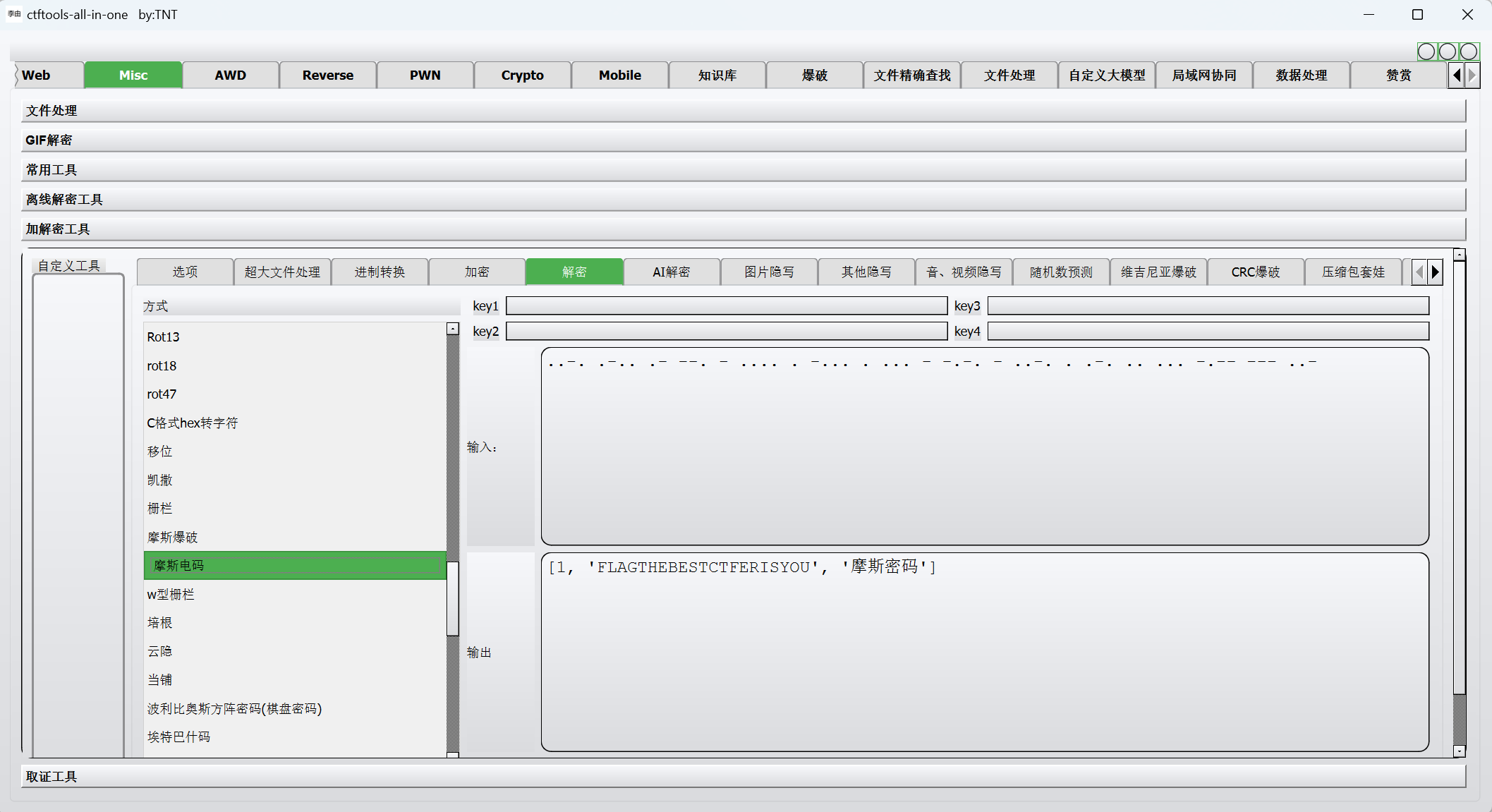
[UTCTF2020]dns-shell
请看大佬博客
洞拐洞拐洞洞拐
题目描述:
1 | 这是一道高难度的MISC题 尽管答题,做的出来算我输 注意:得到的 flag 请包上 flag{} 提交 |
下载附件
黑色为1,白色为0,进行python处理
1 | from PIL import Image |
得到
赛博厨子一把梭得到wav文件
查看音频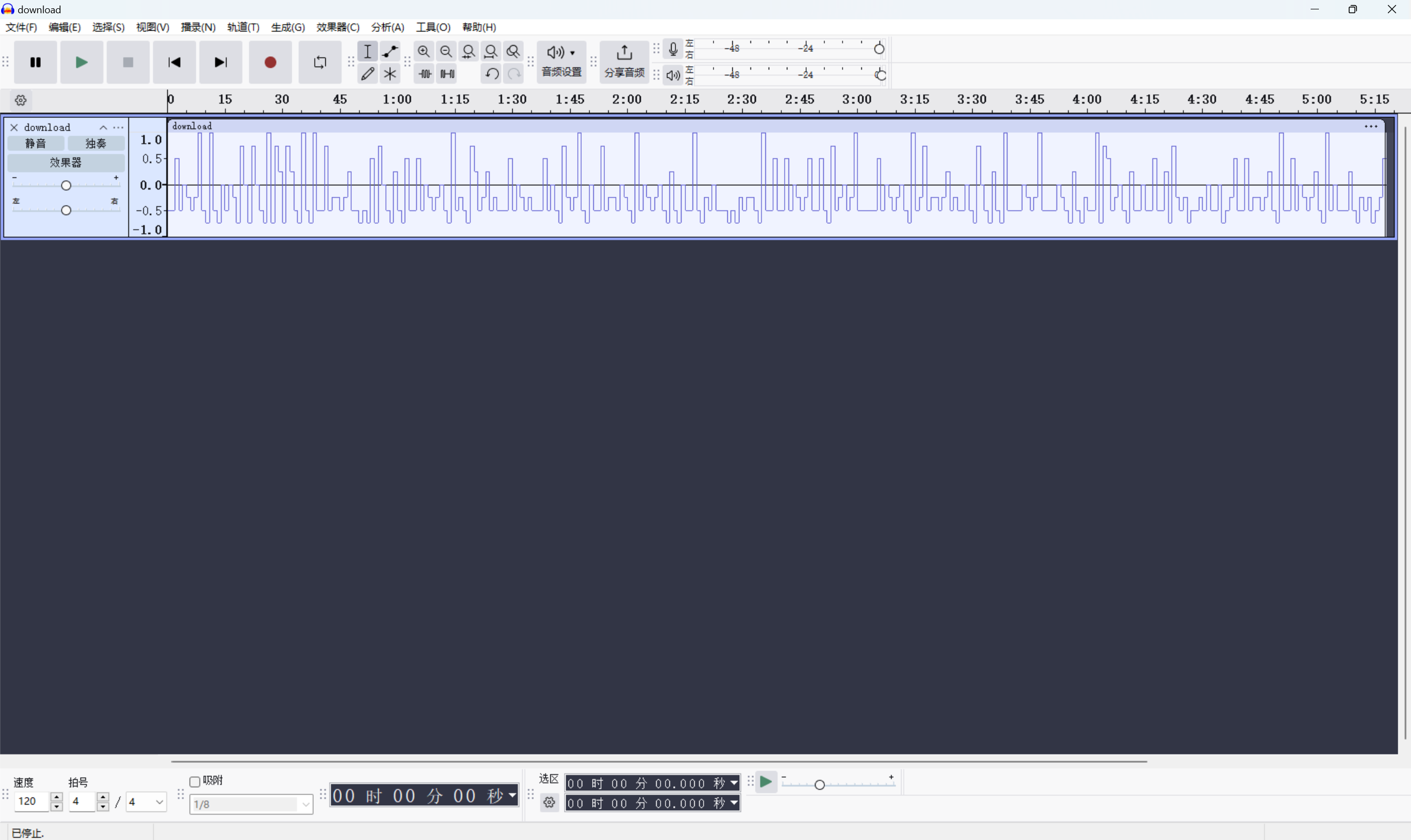
每秒有十帧,共有八种不同的高度,发现每段只有 8 种可能:-0.75 -0.5 -0.25 0.0 0.25 0.5 0.75 1.0
八进制,转换前半部分得到 115132127107 ,如果按3个拆分,可以得到 77 90 87 71 ,都属于Ascii 可打印字符,用Python 脚本进行转换,代码如下:
1 | import wave |
运行得到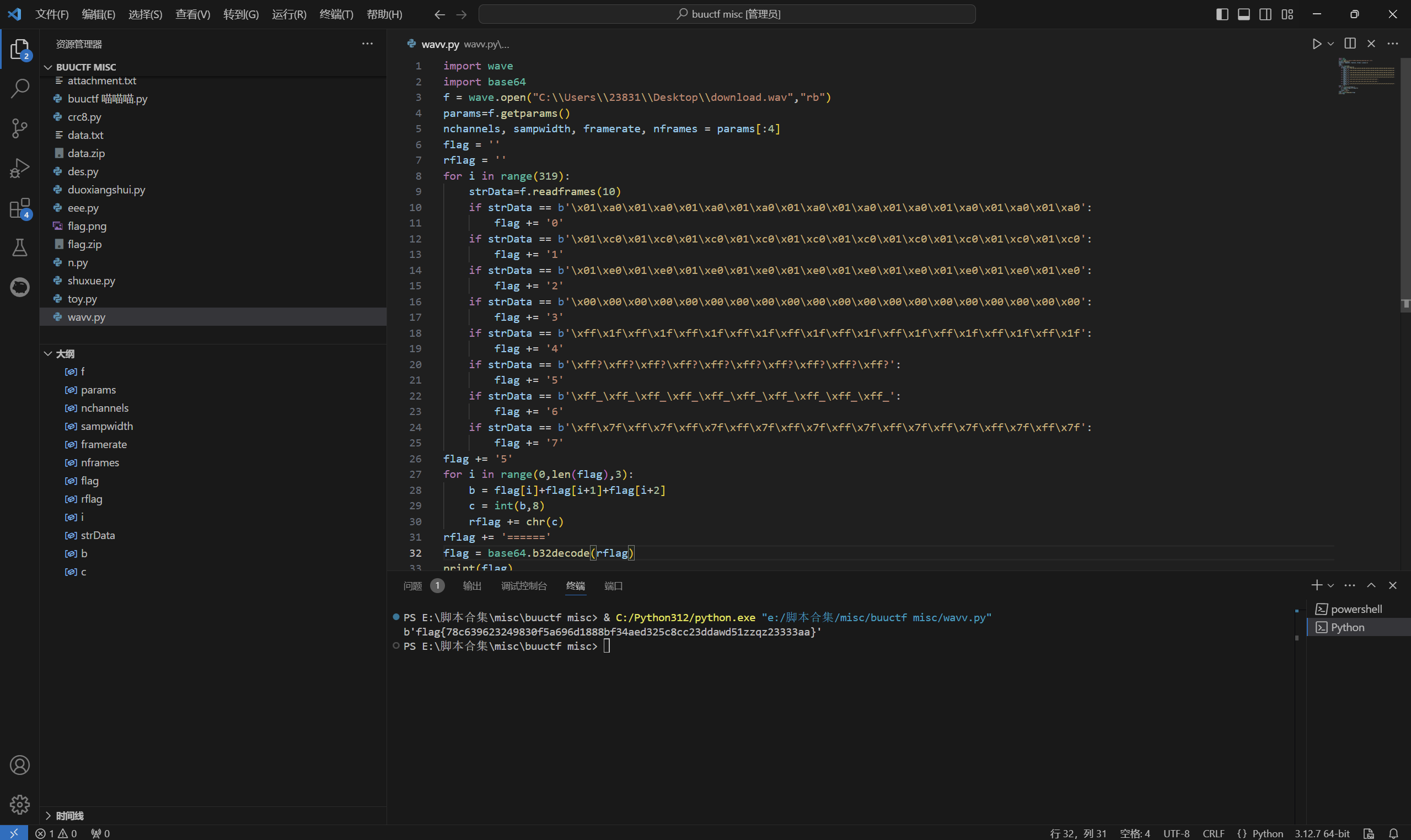
最后flag为
1 | flag{78c639623249830f5a696d1888bf34aed325c8cc23ddawd51zzqz23333aa} |
[HITCON2018]ev3basic
请看
ev3_basic——HITCON CTF 2018_ev3basic-CSDN博客
[RoarCTF2019]davinci_cipher
题目描述:
1 | 达芬奇偷偷把key画了下来,你能找到key然后解开密码吗? |
下载附件
flag.txt
1 | U+1F643U+1F4B5U+1F33FU+1F3A4U+1F6AAU+1F30FU+1F40EU+1F94BU+1F6ABU+1F606U+1F383U+1F993U+2709U+1F33FU+1F4C2U+2603U+1F449U+1F6E9U+2705U+1F385U+2328U+1F30FU+1F6E9U+1F6A8U+1F923U+1F4A7U+1F383U+1F34DU+1F601U+2139U+1F4C2U+1F6ABU+1F463U+1F600U+1F463U+1F643U+1F3A4U+2328U+1F601U+1F923U+1F3A4U+1F579U+1F451U+1F6AAU+1F374U+1F579U+1F607U+1F374U+1F40EU+2705U+2709U+1F30FU+23E9U+1F40DU+1F6A8U+2600U+1F607U+1F3F9U+1F441U+1F463U+2709U+1F30AU+1F6A8U+2716 |
unicode解密得到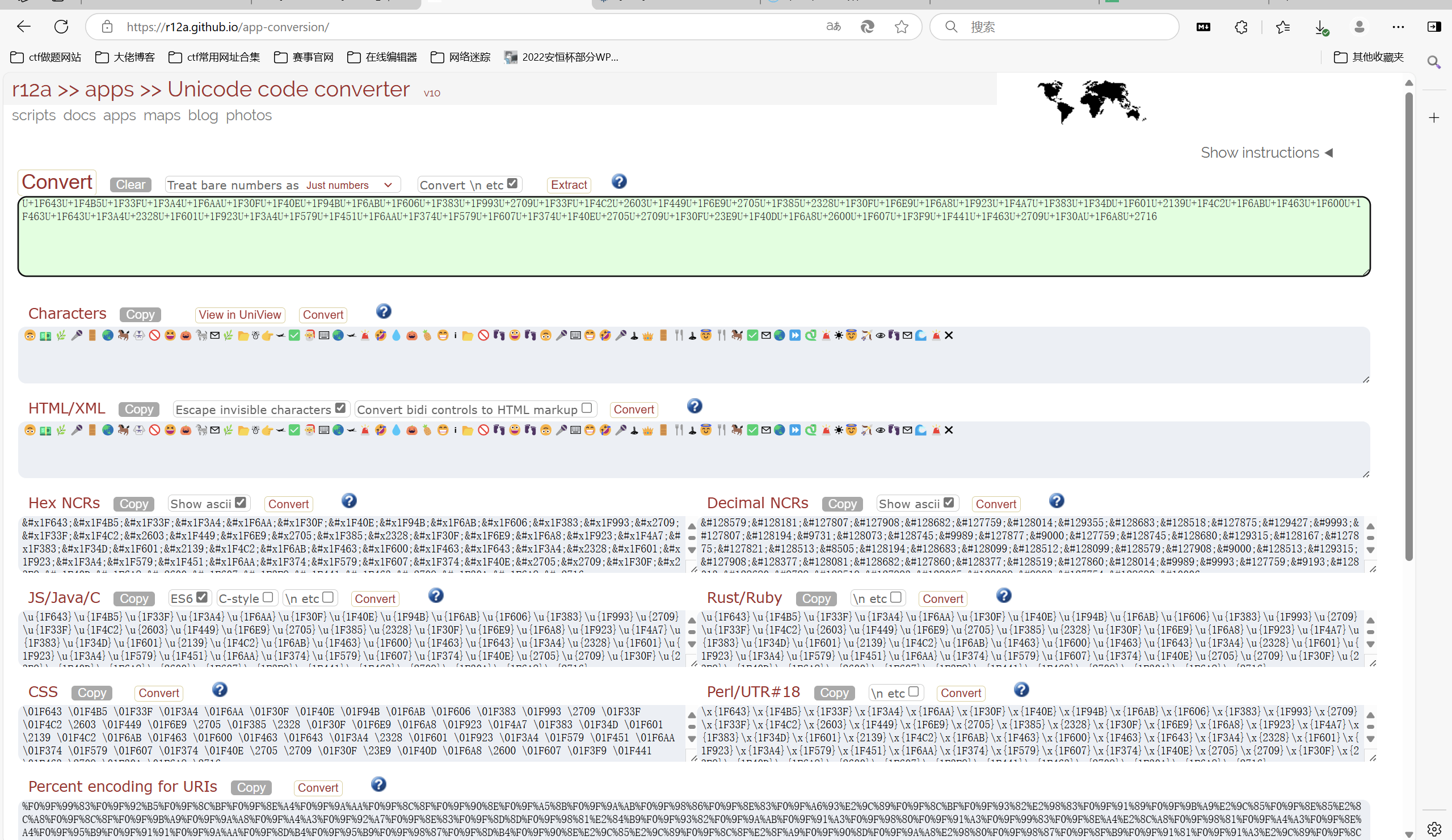
数位板流量
1 | import os |
得到字符串:
1 | MONA_LISA_IS_A_MAN |
emoji解密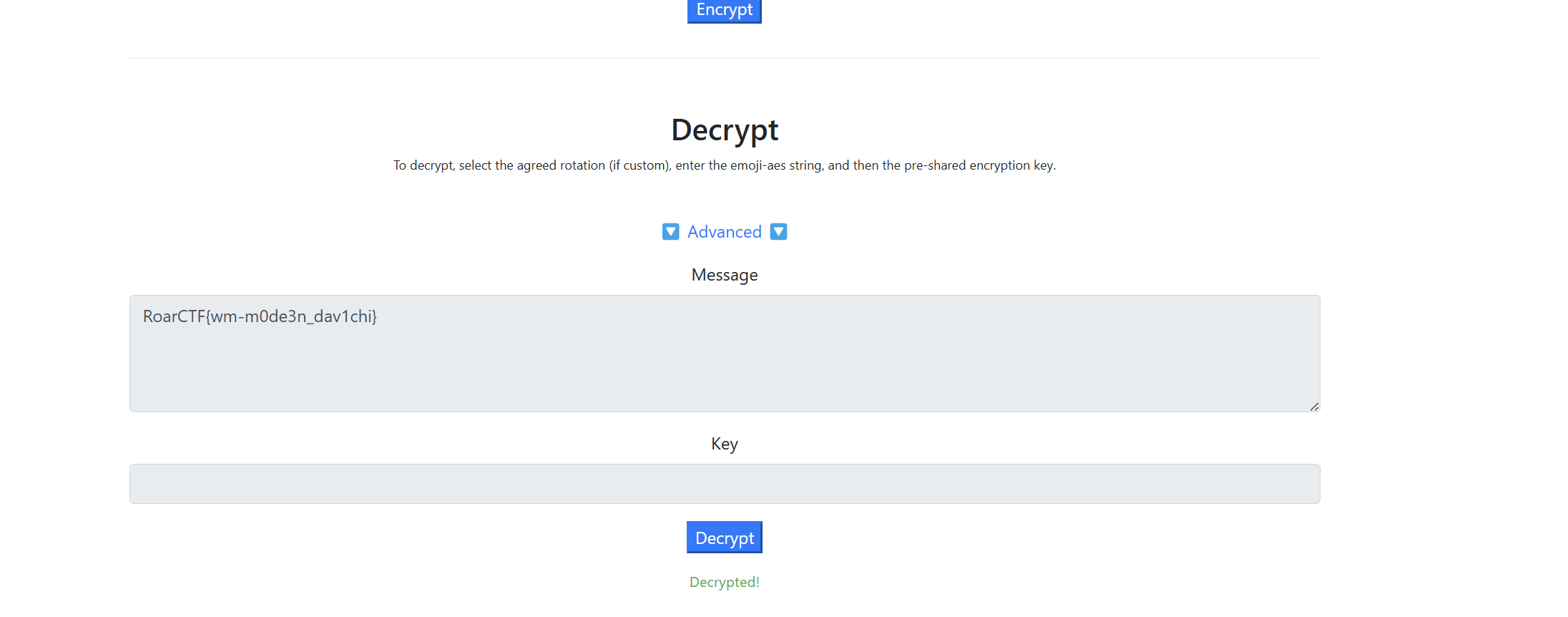
最后flag为
1 | flag{wm-m0de3n_dav1chi} |
[NewStarCTF 2023 公开赛道]base!
下载附件
1 | bXkgc291bCdzIHRoZSBza3nigJTigJRteSBmbHlpbmcgc291bCF= |
base隐写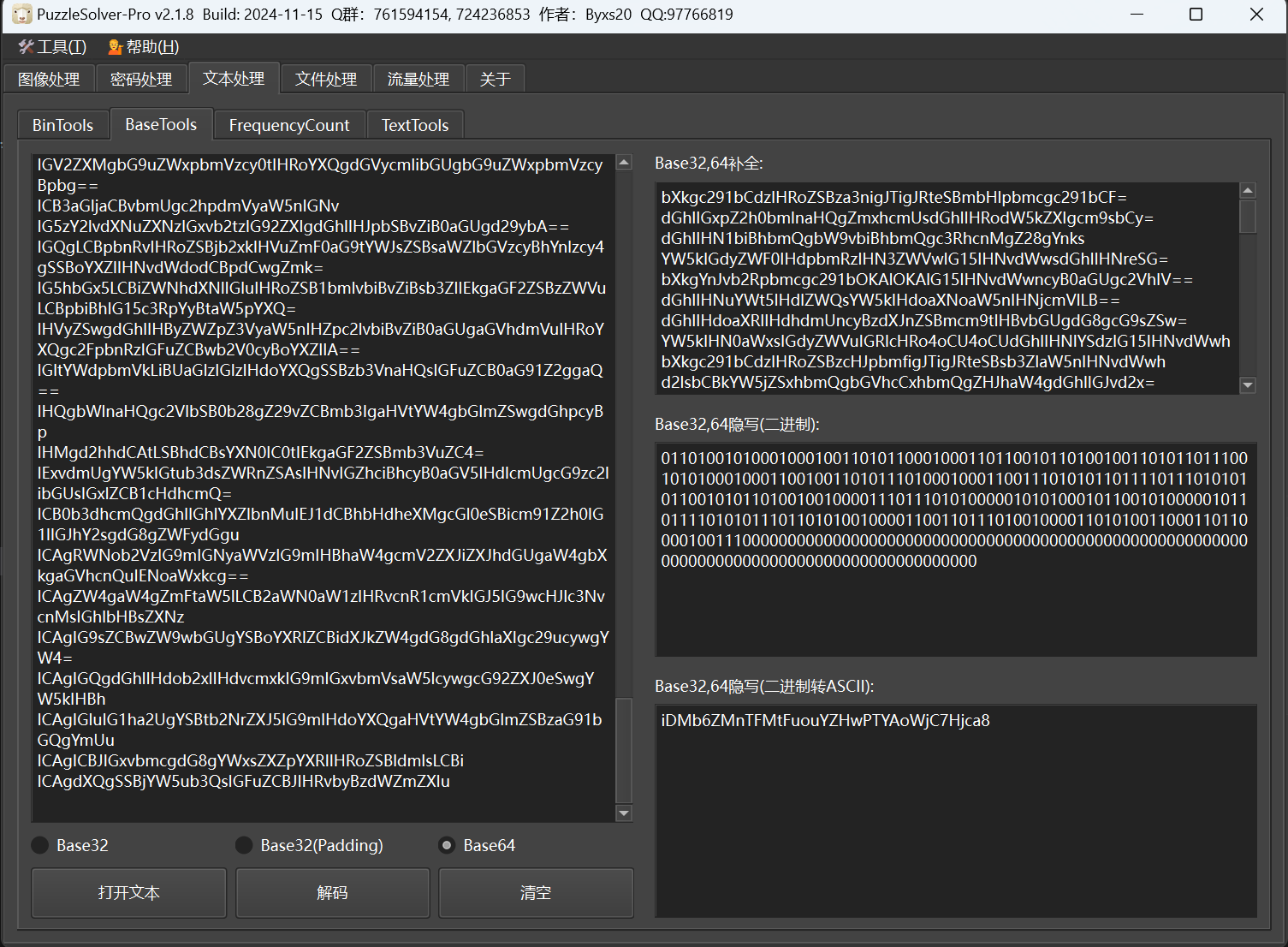
base58解密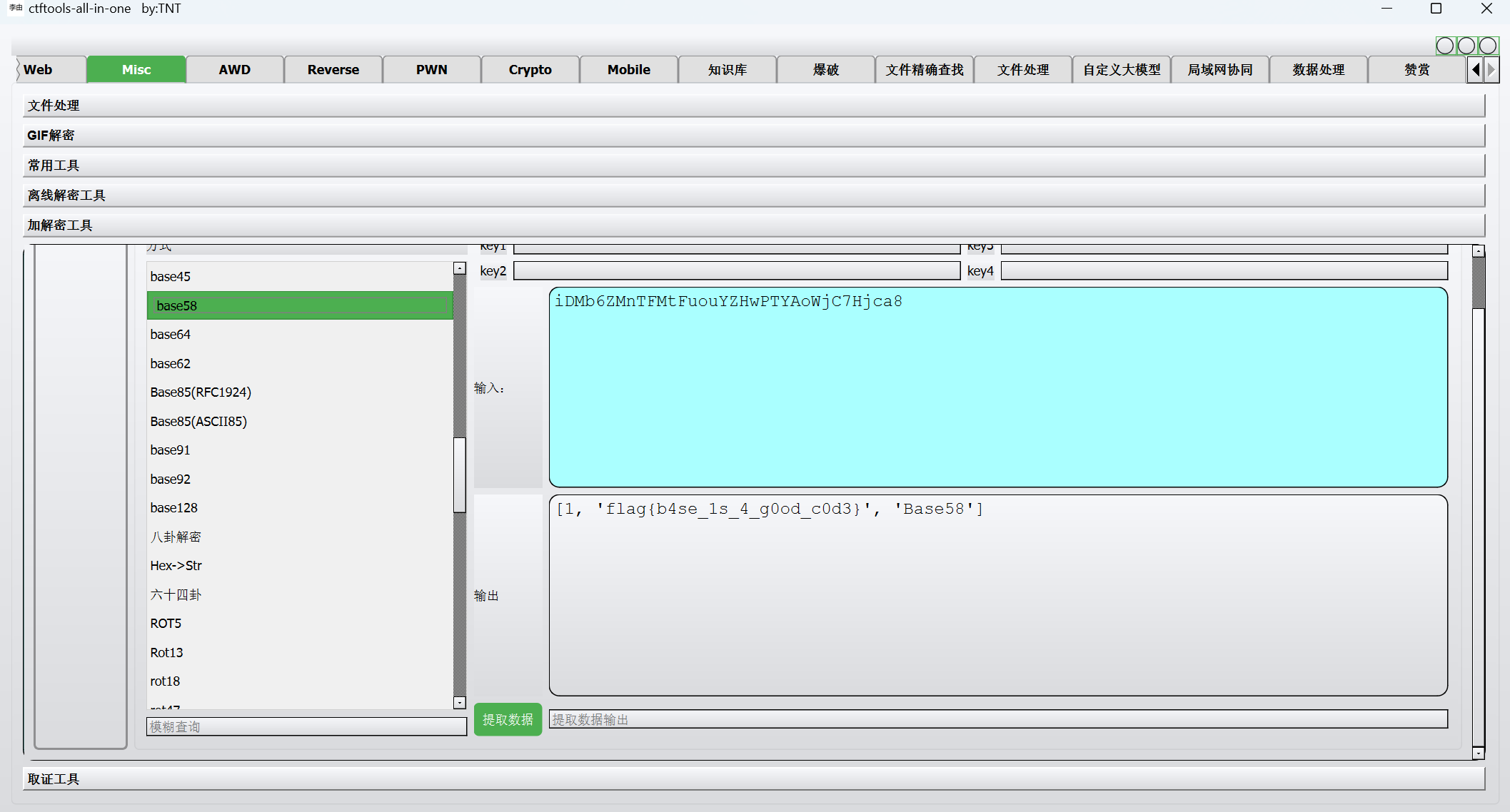
最后flag为
1 | flag{b4se_1s_4_g0od_c0d3} |
[NewStarCTF 2023 公开赛道]R通大残
下载附件
r通道全选,stegsolve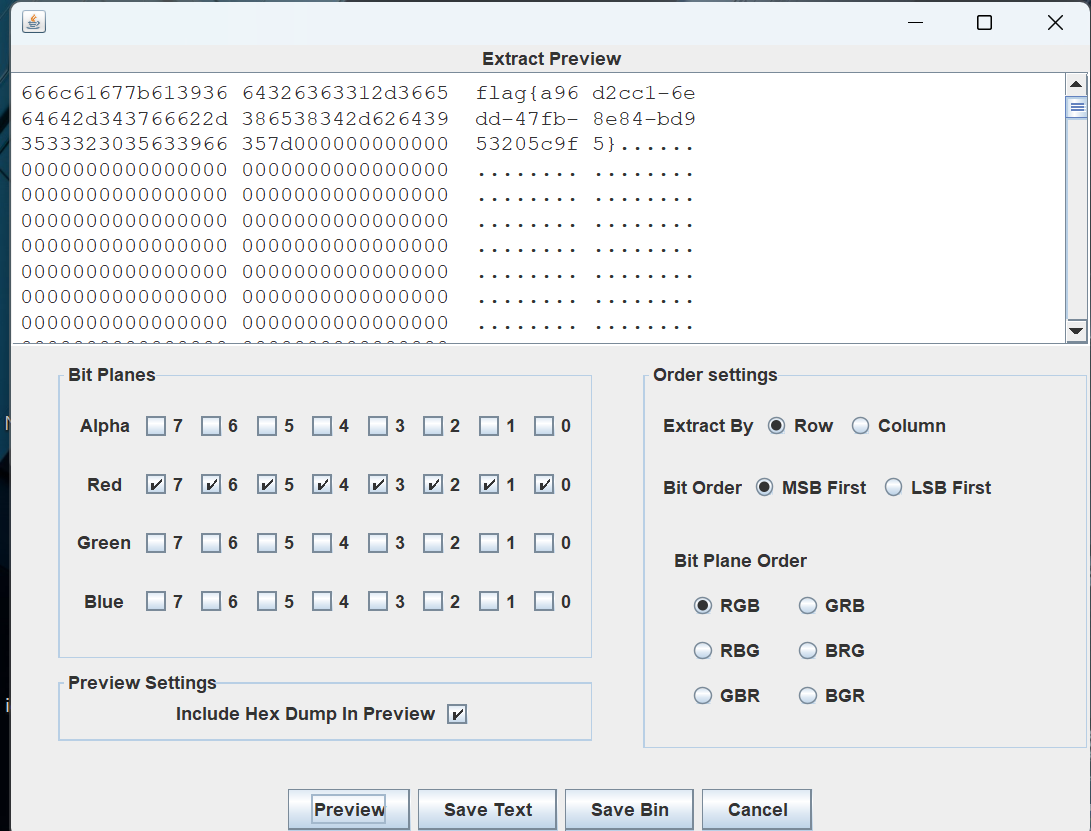
最后flag为
1 | flag{a96d2cc1-6edd-47fb-8e84-bd953205c9f5} |
[NewStarCTF 2023 公开赛道]2-分析
题目描述:
1 | 但你心中仍然有一种不祥的预感,这时你的同事告诉你这台服务器已经被攻击者获取到了权限,需要你尽快去还原攻击者的攻击路径,调查清楚攻击者是如何获取到服务器权限的。;FLAG格式flag{md5(攻击者登录使用的用户名_存在漏洞的文件名_WebShell文件名)};例如flag{testuser_123.php_shell.php},将括号内的内容进行md5编码得到flag{58aec571c731faae1369b461d3927596}即为需要提交的Flag |
找到用户名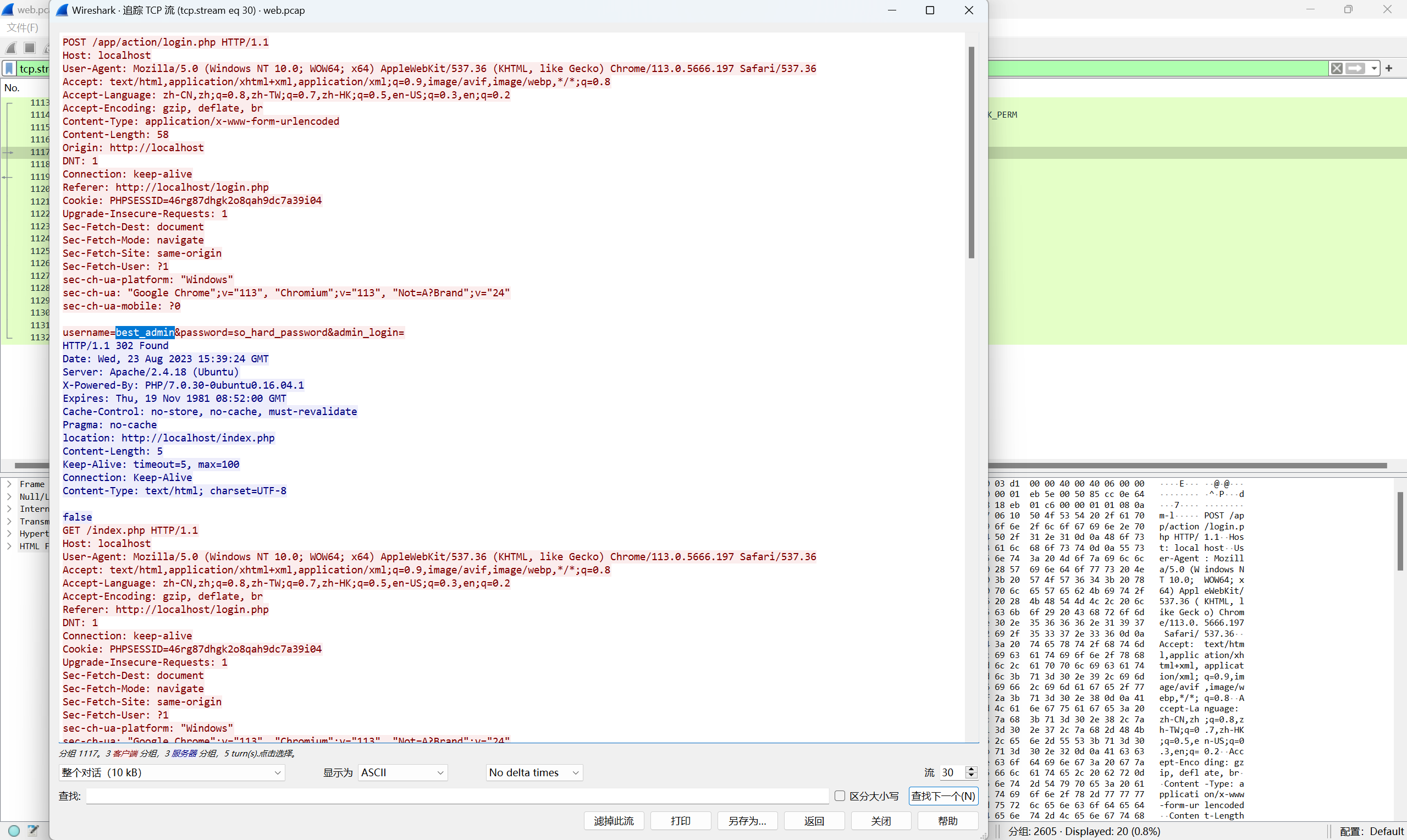
index.php?page=/../../../../usr/share/php/pearcmd&+config-create+/&+/var/www/html/wh1t3g0d.php
这里是在漏洞文件里进行了远程木马的上传,木马文件为wh1t3g0d.php,漏洞文件为index.php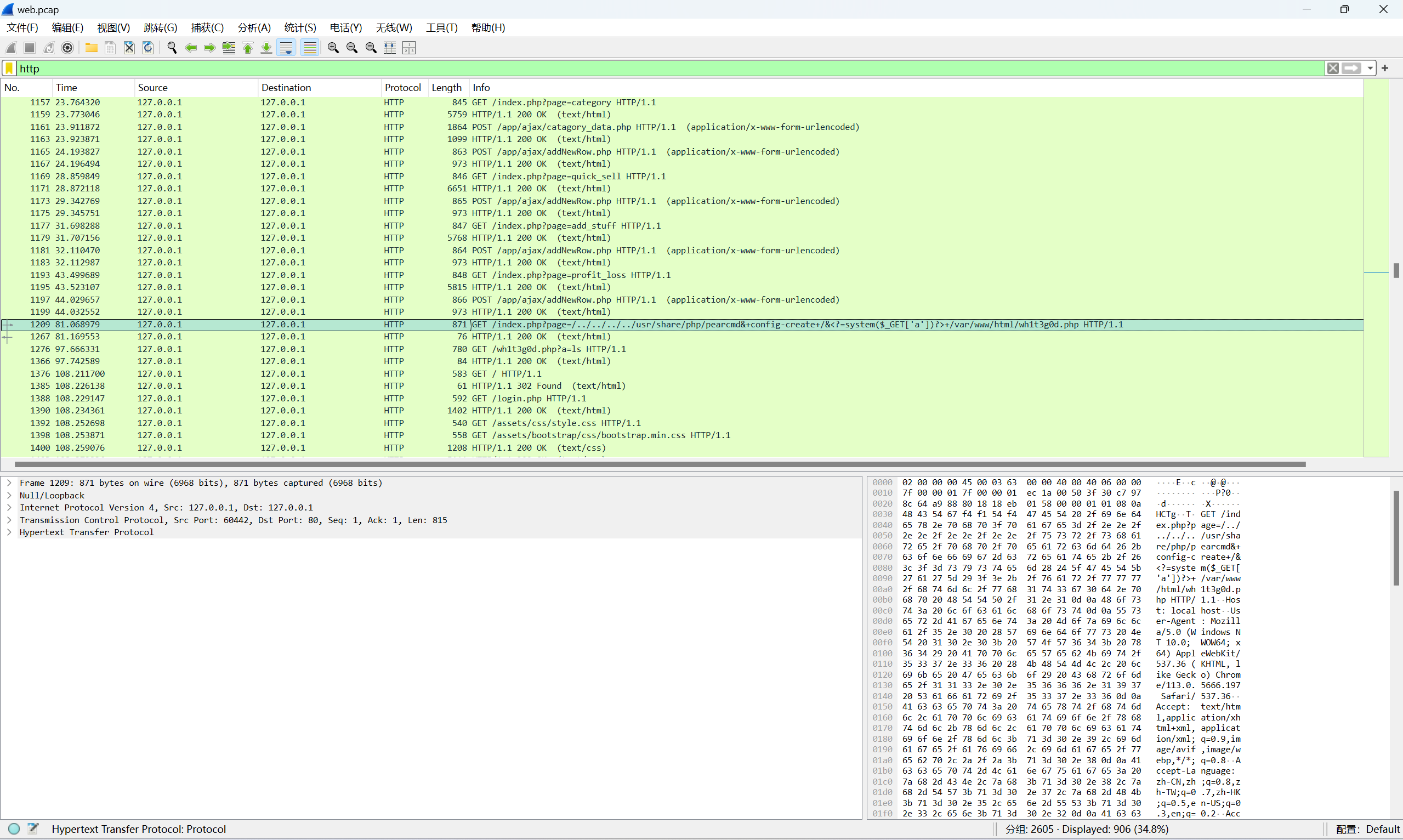
1 | shell文件:wh1t3g0d.php |
md5加密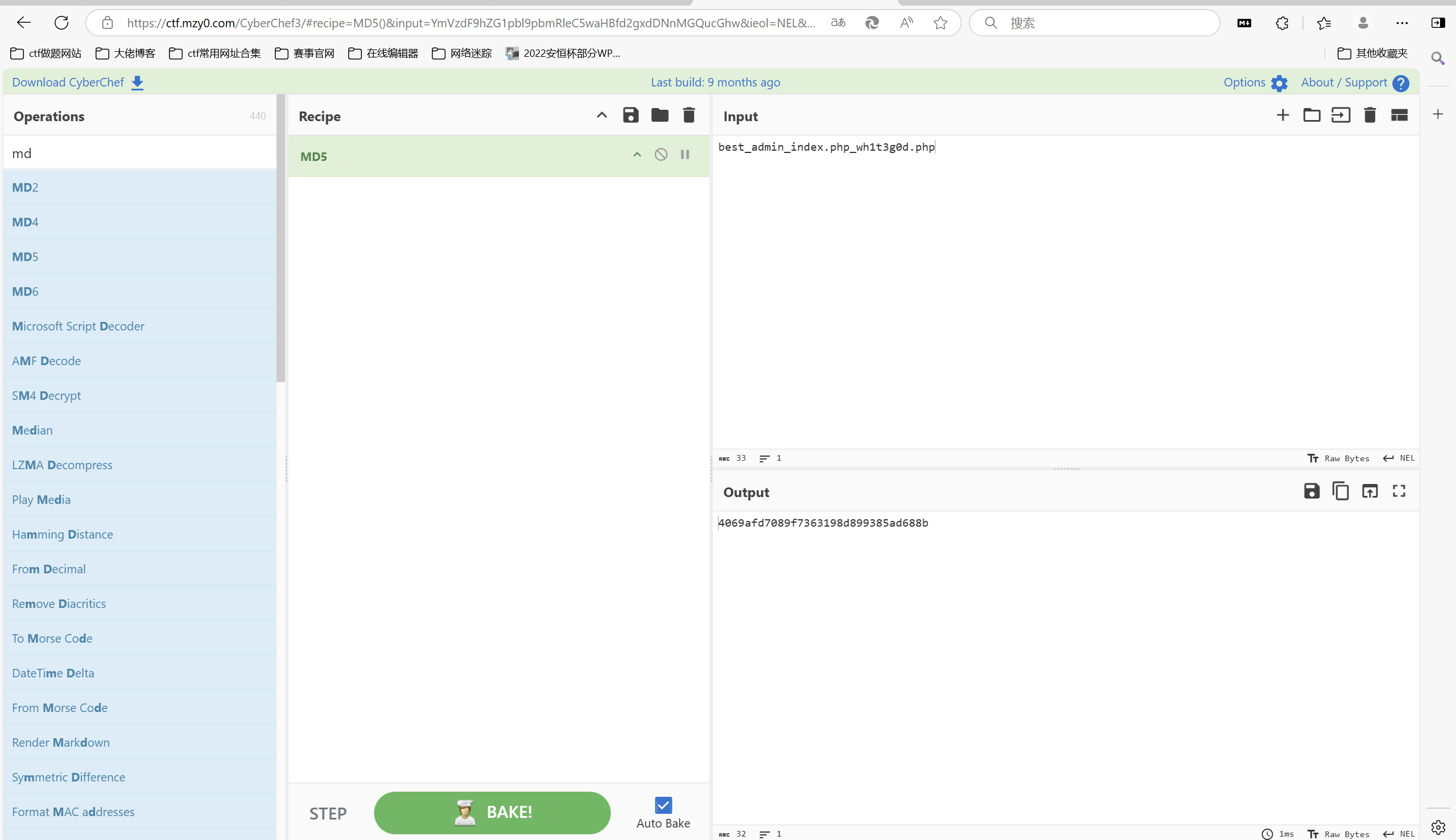
最后flag为
1 | flag{4069afd7089f7363198d899385ad688b} |
[NewStarCTF 2023 公开赛道]隐秘的眼睛
静默之眼一把梭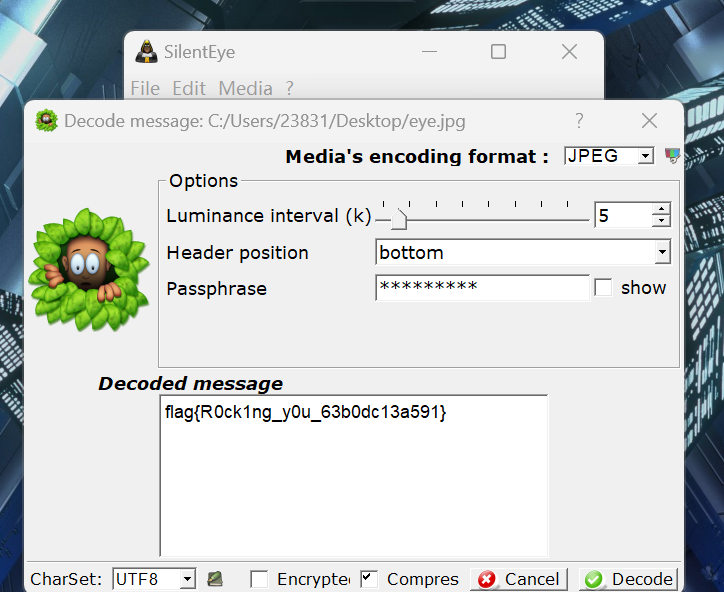
最后flag为
1 | flag{R0ck1ng_y0u_63b0dc13a591} |
[V&N2020 公开赛]拉胯的三条命令
1 | tcpdump -n -r nmapll.pcapng 'tcp[13] = 18' | awk '{print $3}' | sort -u |
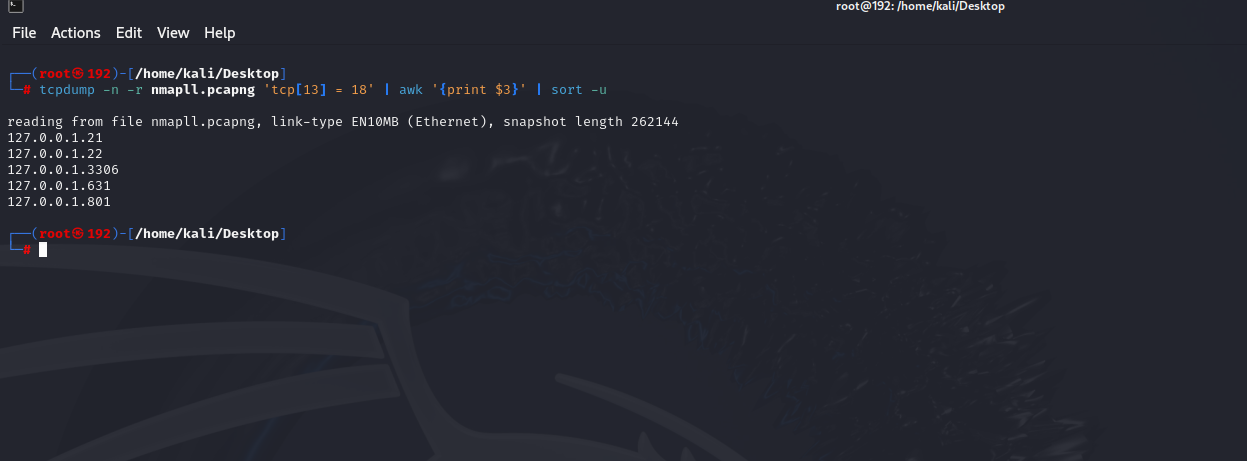
最后flag为
1 | flag{21226318013306} |
[NPUCTF2020]HappyCheckInVerification
下载附件
得到一个破损的二维码跟mp4视频,通过手动的方式修复二维码
扫描二维码得到
1 | flag{this_is_not_flag} |
通过||分隔符得到base16解密内容
1 | E68BBFE4BD9BE68B89E6A0BCE79A84E5A7BFE58ABFE59CA8E69C80E5908E32333333 |
根据之前提示 use base64 发送了手机号码base64encode的结果,然后返回了一段音频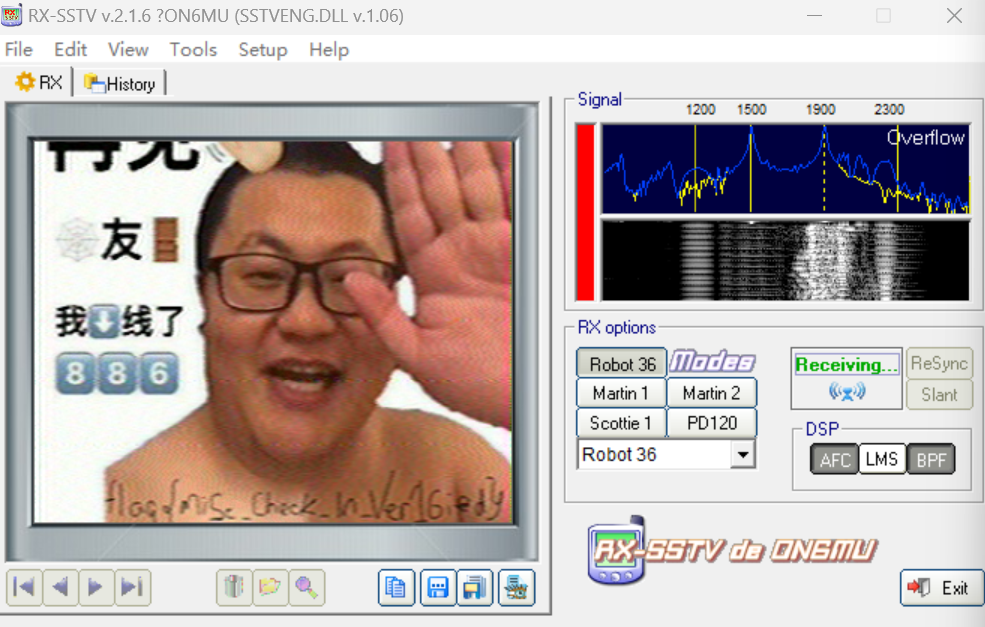
最后flag为
1 | flag{miSc_ChecK_In_Ver16ied} |
[RoarCTF2019]TankGame
坦克大战游戏
1 | import hashlib |
NewStarCTF 公开赛赛道]WebShell!
题目描述:
1 | 溯源攻击者窃取的文件内容!他用了蚁剑诶? Flag格式为:flag{WebShell密码_黑客获取的用户名_机密文件内容} 例如flag{cmd_root_secret} |
webshell密码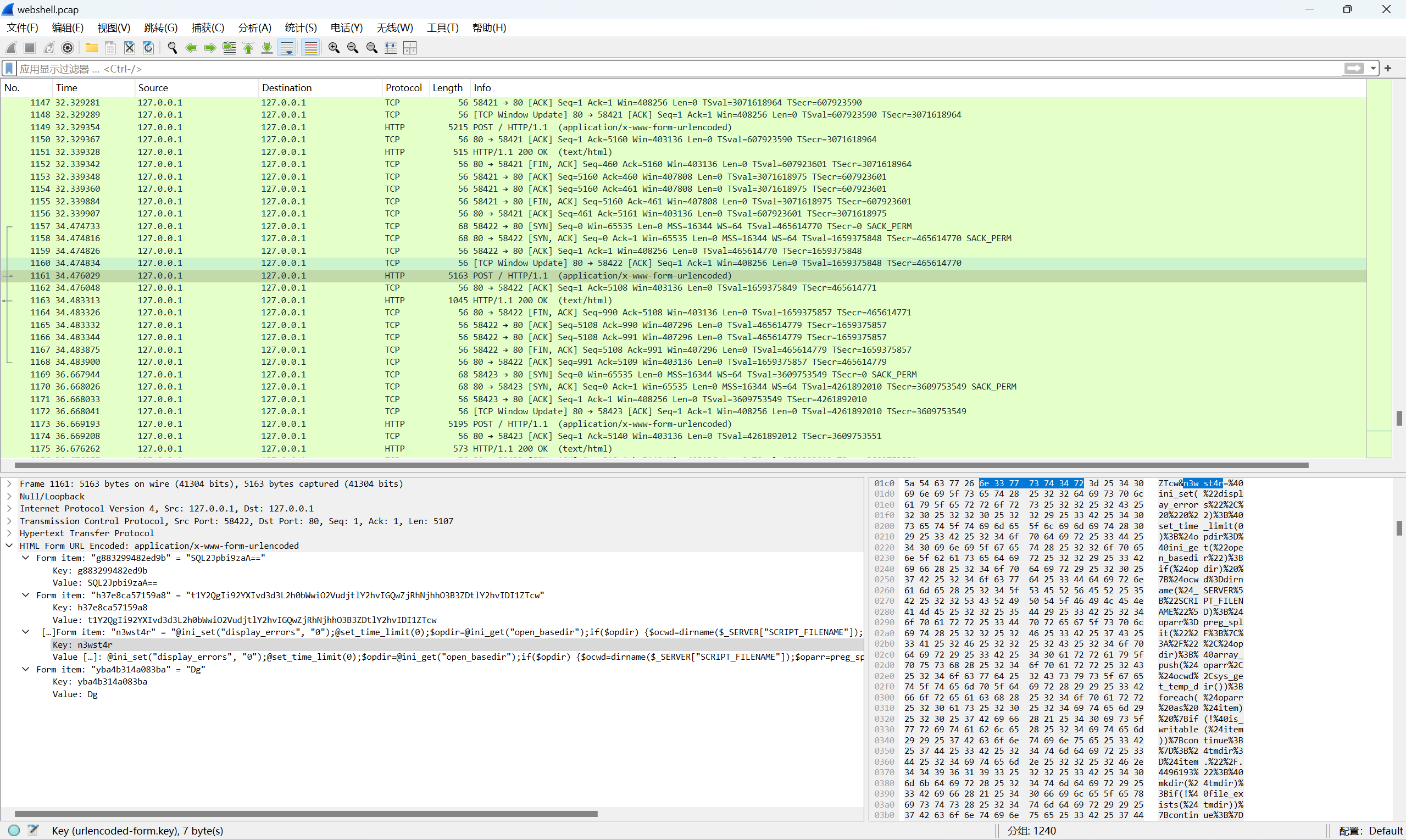
黑客获取的用户名:www-data
机密文件内容:Y0UAr3G00D
最后flag为
1 | flag{n3wst4r_www-data_Y0UAr3G00D} |
[2022DASCTF MAY 出题人挑战赛]神必流量
nata一把梭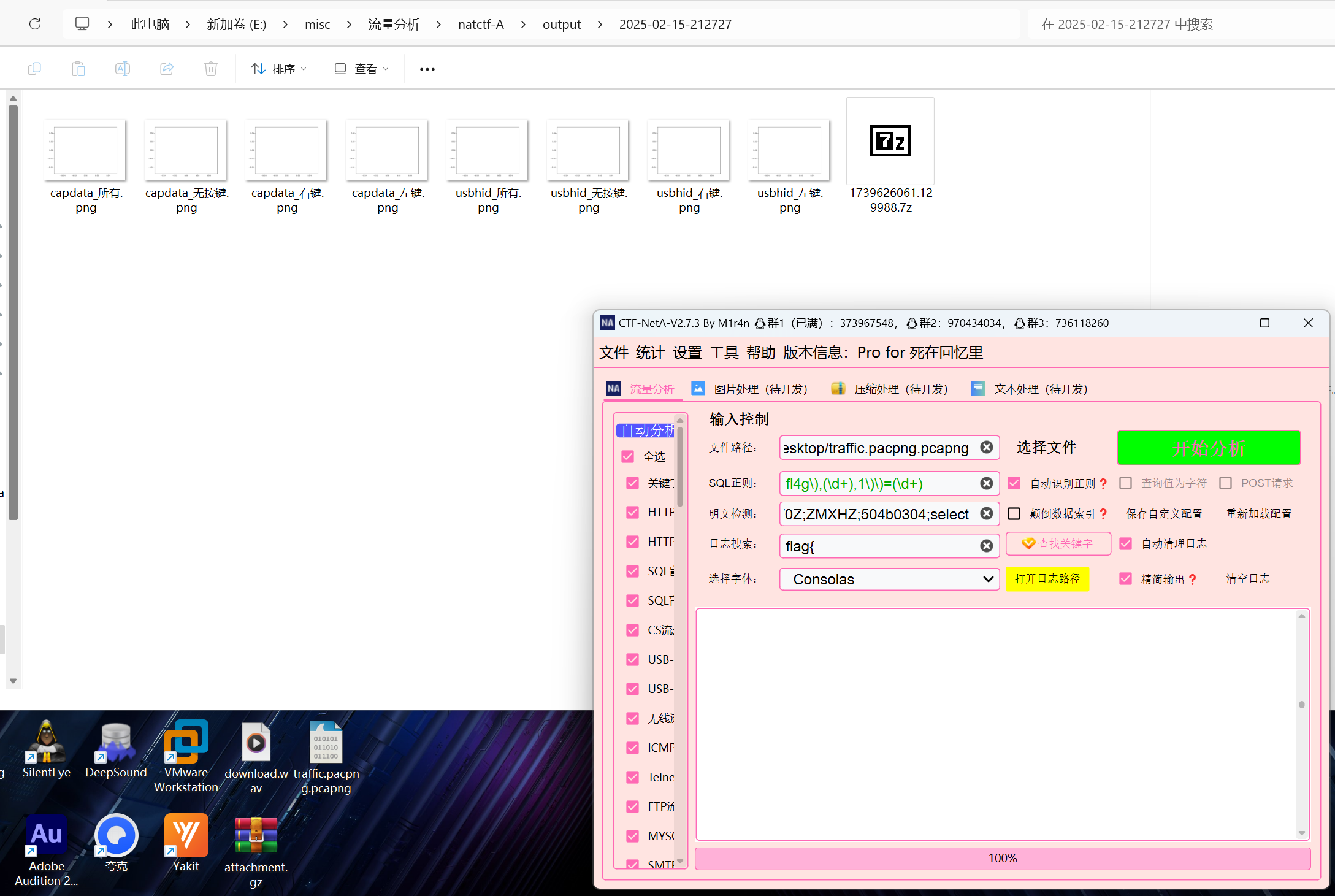
弱密码123456解压7z文件
https://drive.google.com/file/d/140MxBVh-OGvQUuk8tmOw4Xm8it9utIzo/view
打开是一个链接,是Google云盘的两个文件,下载需要科学上网
得到一个main.exe和output.txt,尝试运行exe文件
逆向分析exe文件
参考http://www.snowywar.top/?p=3323
最后flag为
1 | flag{6f938f4c-f850-4f04-b489-009c2ed1c4fd} |
[NewStarCTF 公开赛赛道]Whats HTTP
tcp追踪流得到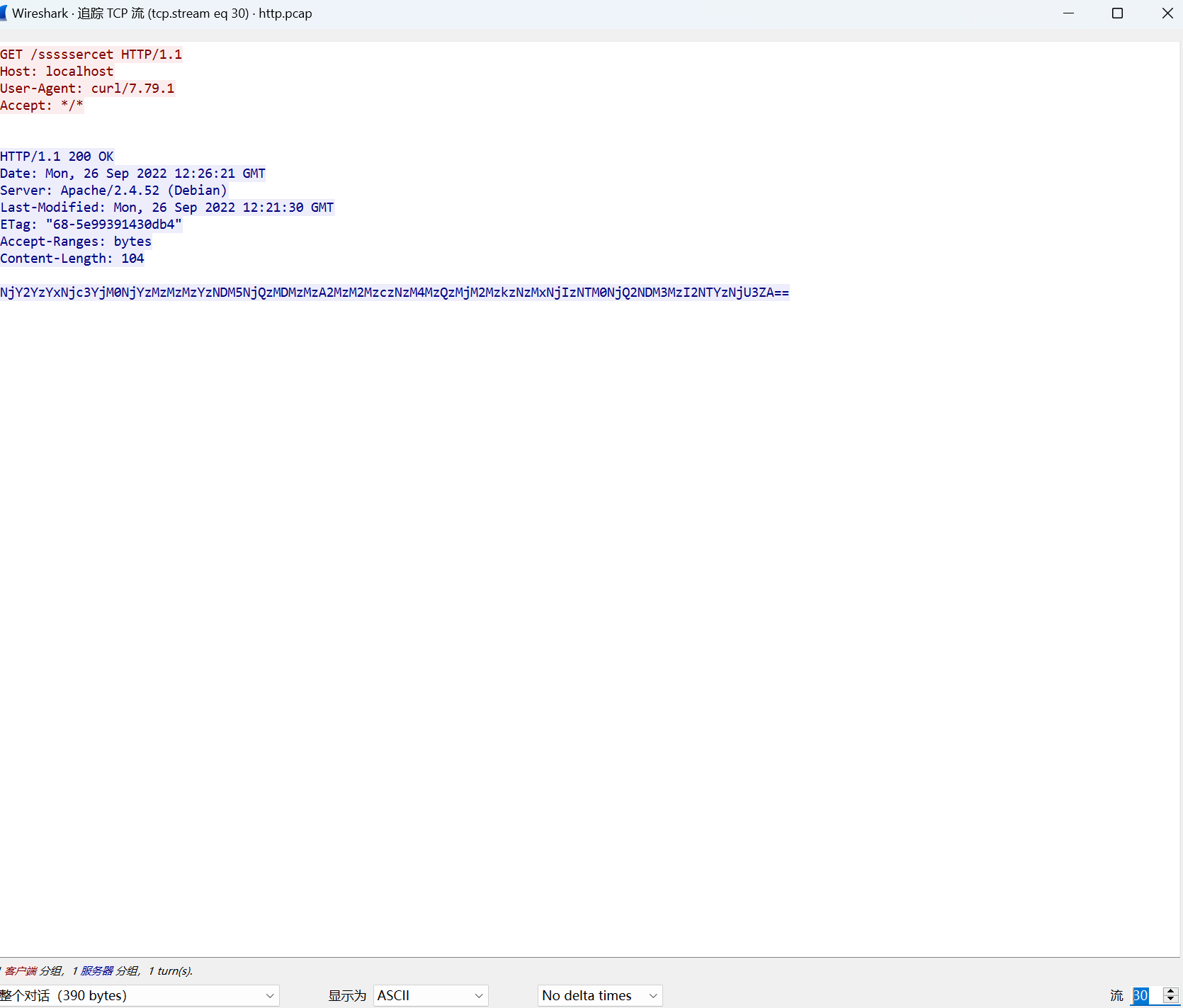
赛博厨子一把梭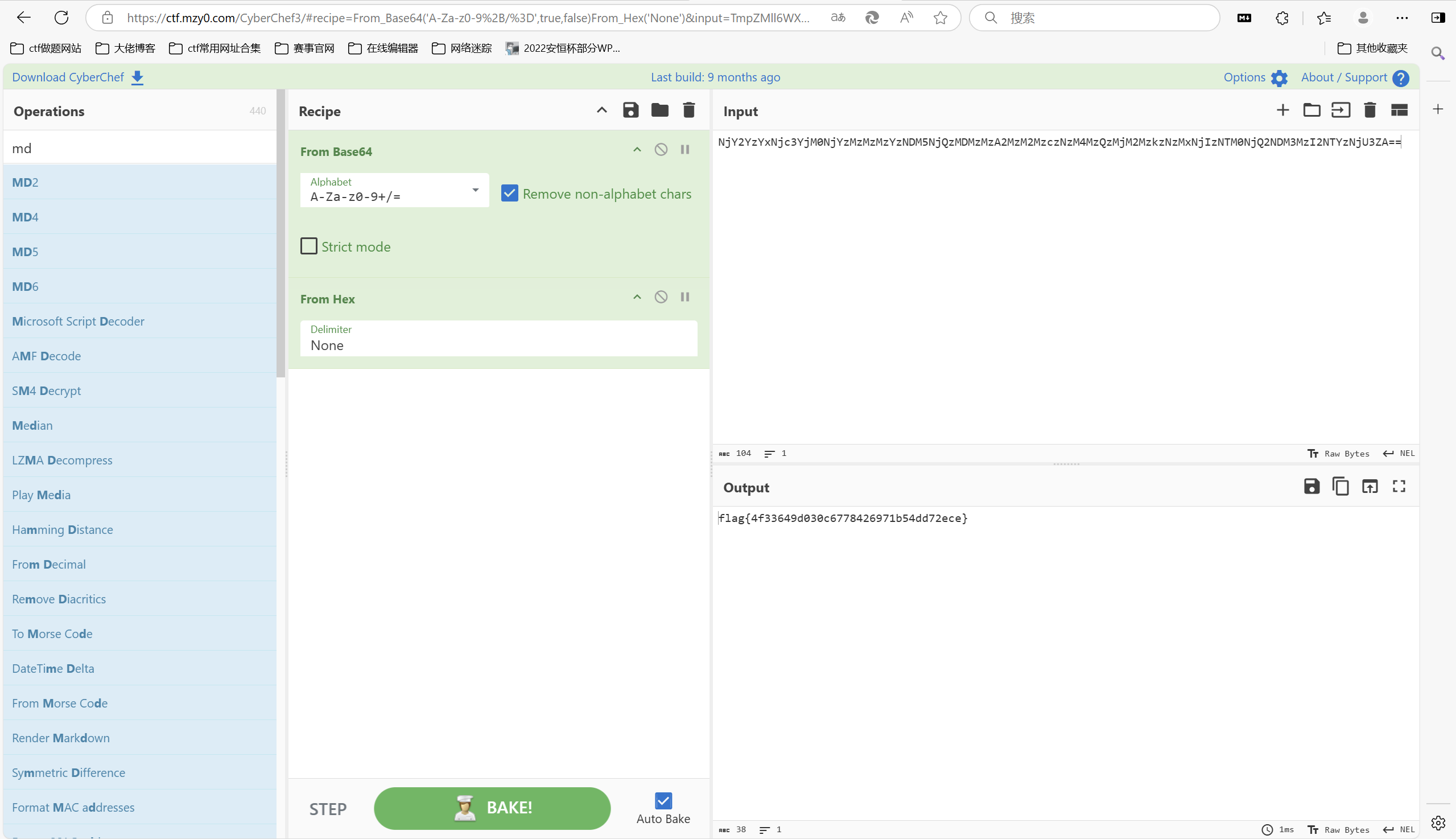
最后flag为
1 | flag{4f33649d030c6778426971b54dd72ece} |
[QCTF2018]Noise
请看
[NPUCTF2020]OI的梦
1 | OI の梦 |
矩阵快速幂
exp:
1 | def mulMatrix(x, y): |
最后flag为
1 | flag{5174} |
[NewStarCTF 2023 公开赛道]依旧是空白
宽高一把梭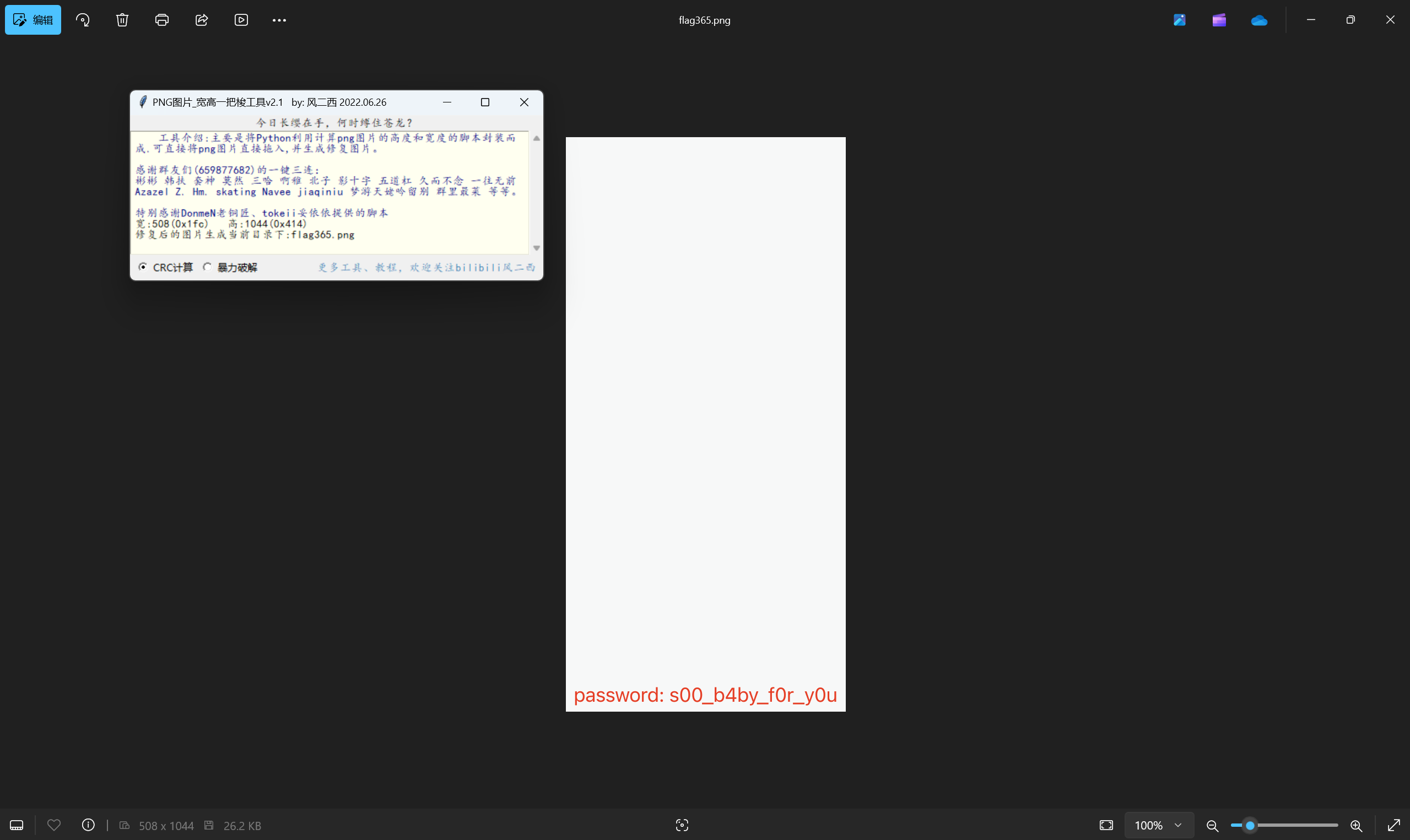
snow隐写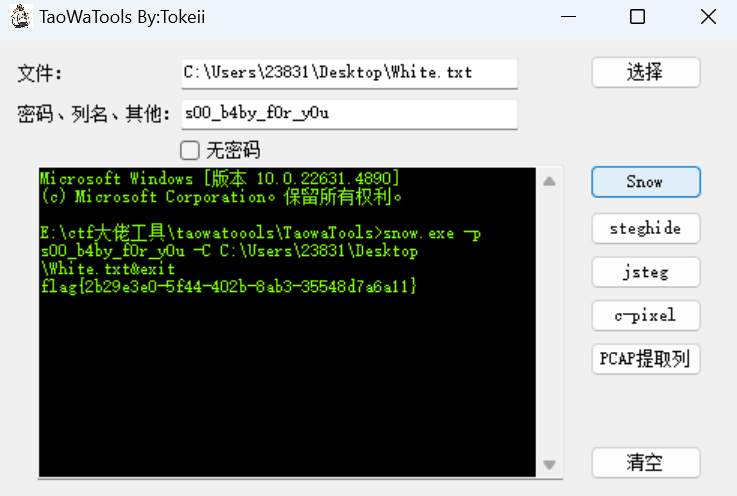
最后flag为
1 | flag{2b29e3e0-5f44-402b-8ab3-35548d7a6a11} |
[NewStarCTF 2023 公开赛道]键盘侠
键盘流量natA一把梭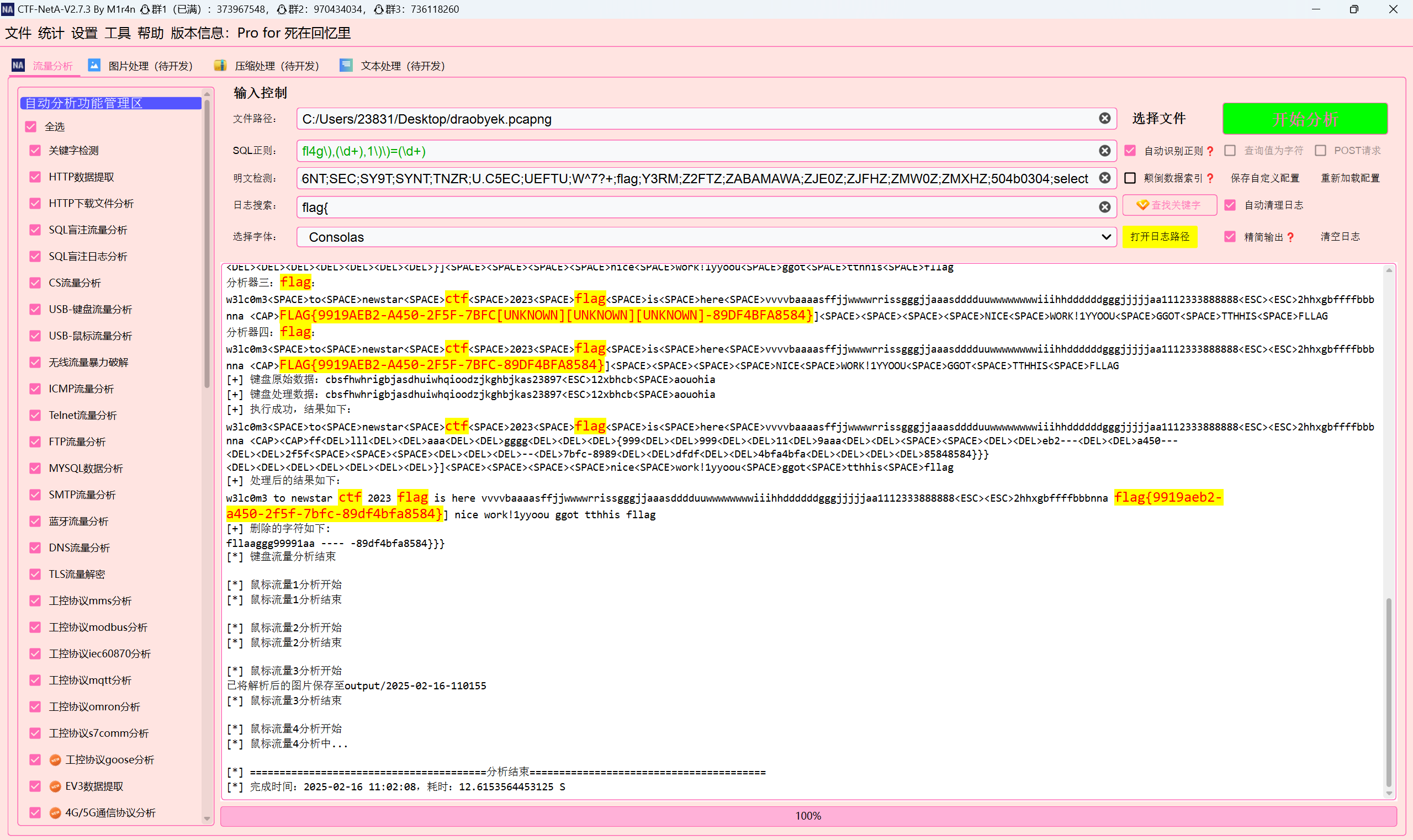
最后flag为
1 | flag{9919aeb2-a450-2f5f-7bfc-89df4bfa8584} |
[NewStarCTF 2023 公开赛道]1-序章
sql盲注的log
直接脚本处理
1 | # [NewStarCTF 2023 公开赛道]1-序章 |
[SWPU2019]Android3
安卓逆向不太会,直接看大佬博客吧
[SWPU2019] Android3 - WXjzc - 博客园
[SWPU2019]Android2
[SWPU2019] Android2 - WXjzc - 博客园
[NewStarCTF 2023 公开赛道]滴滴滴
下载附件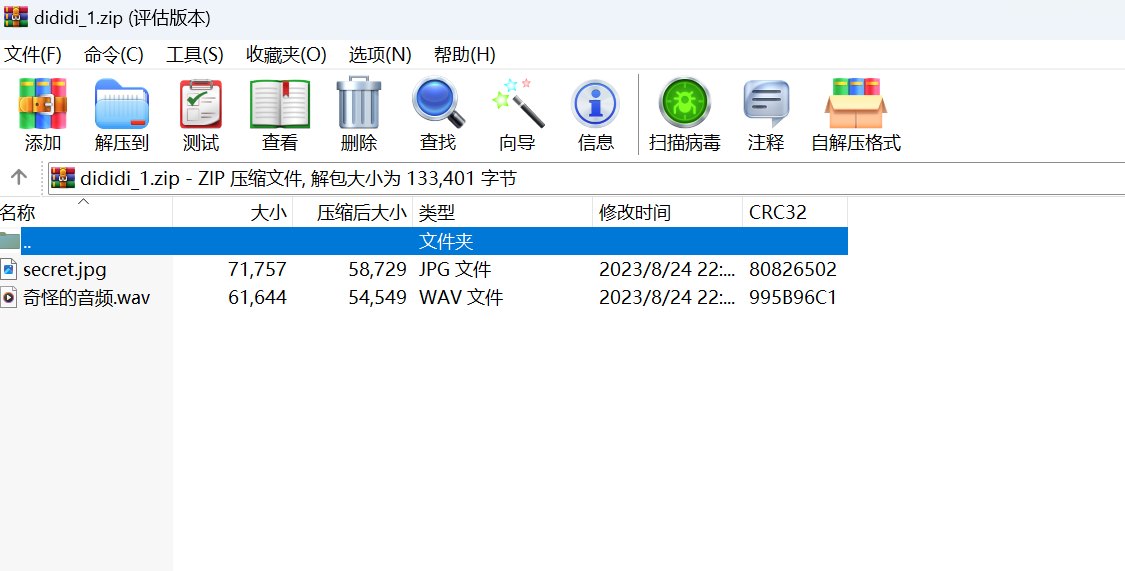
音频是拨号声音,dtmf2num处理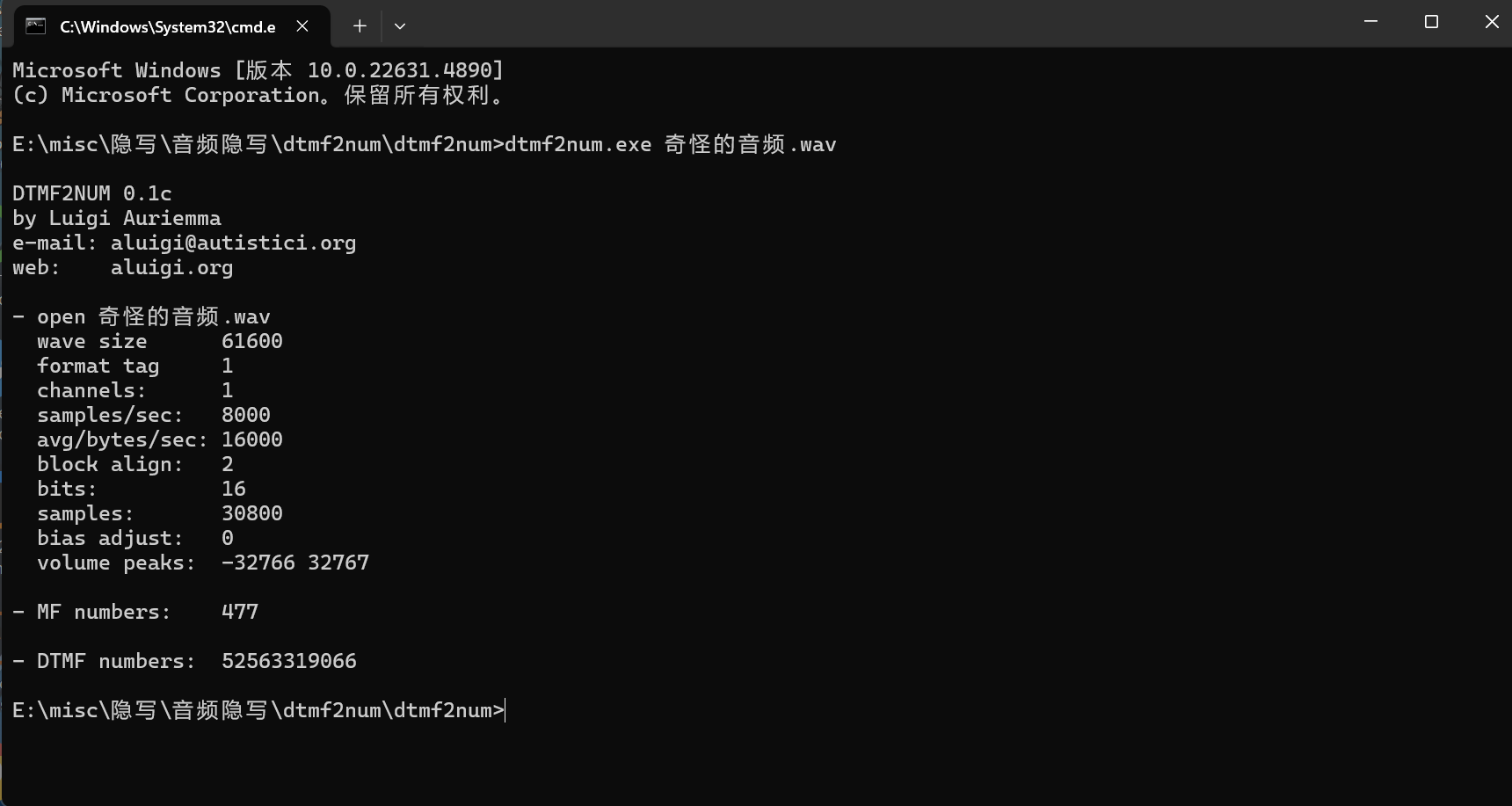
steghide隐写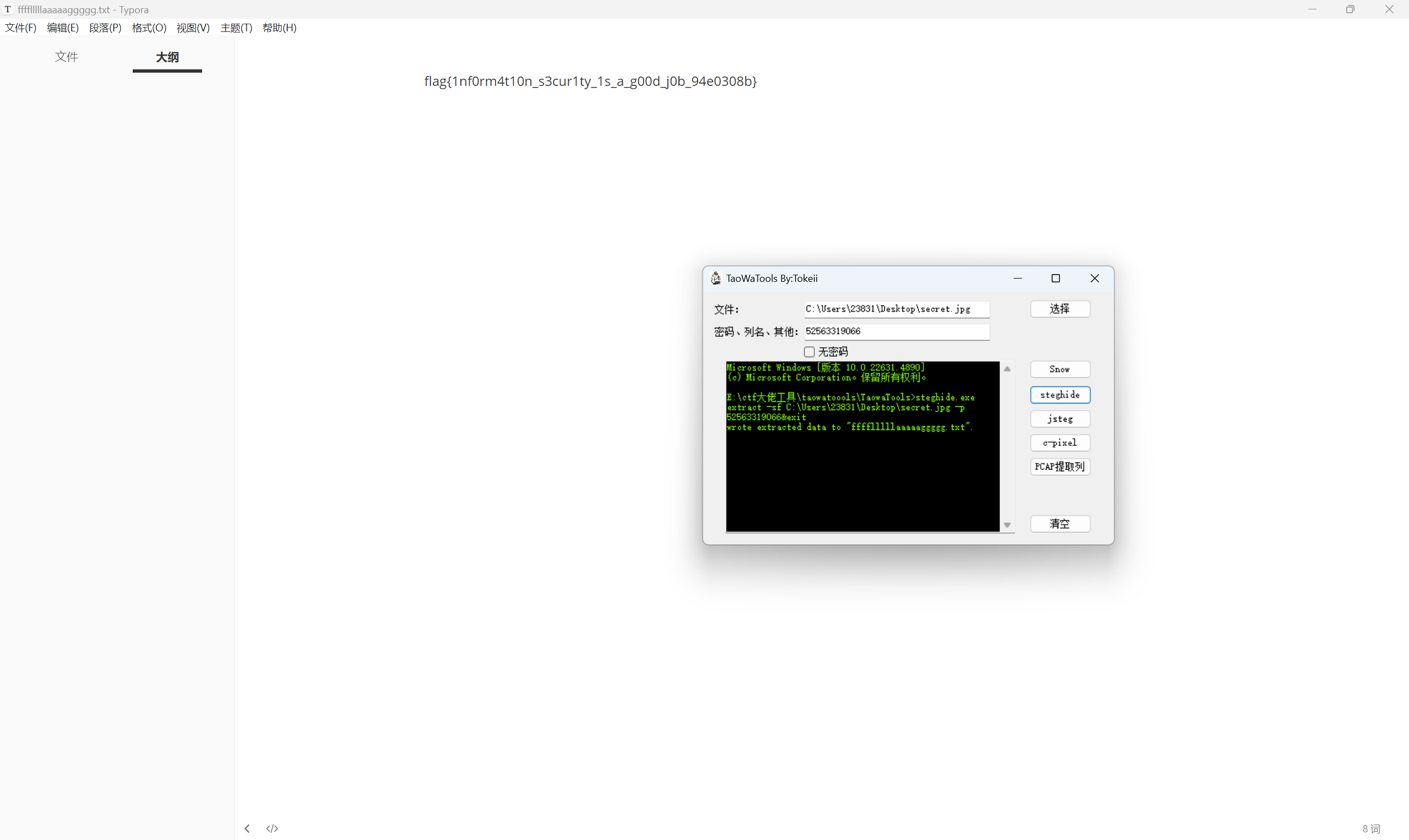
最后flag为
1 | flag{1nf0rm4t10n_s3cur1ty_1s_a_g00d_j0b_94e0308b} |
[NewStarCTF 2023 公开赛道]3-溯源
题目描述:
1 | 在调查清楚攻击者的攻击路径后你暗暗松了一口气,但是攻击者仍控制着服务器,眼下当务之急是继续深入调查攻击者对服务器进行了什么操作,同时调查清楚攻击者的身份,请你分析攻击者与WebShell通讯的流量获取攻击者获取的相关信息,目前可以得知的是攻击者使用了冰蝎进行WebShell连接。 Tip:沿着前序题目的进度分析会更符合逻辑,或许有助于解题 FLAG格式:flag{攻击者获取到的服务器用户名_服务器内网IP地址} 例如flag{web_10.0.0.3} |
冰蝎流量
请看NewStarCTF2023week4-溯源_ctf 冰蝎-CSDN博客
[INSHack2019]Yet Another RSA Challenge - Part 2
1 | from sympy.ntheory import isprime |
[SCTF2019]Maze
大佬脚本
1 | from bs4 import BeautifulSoup |
[BJDCTF 2nd]最简单的misc-y1ng
伪加密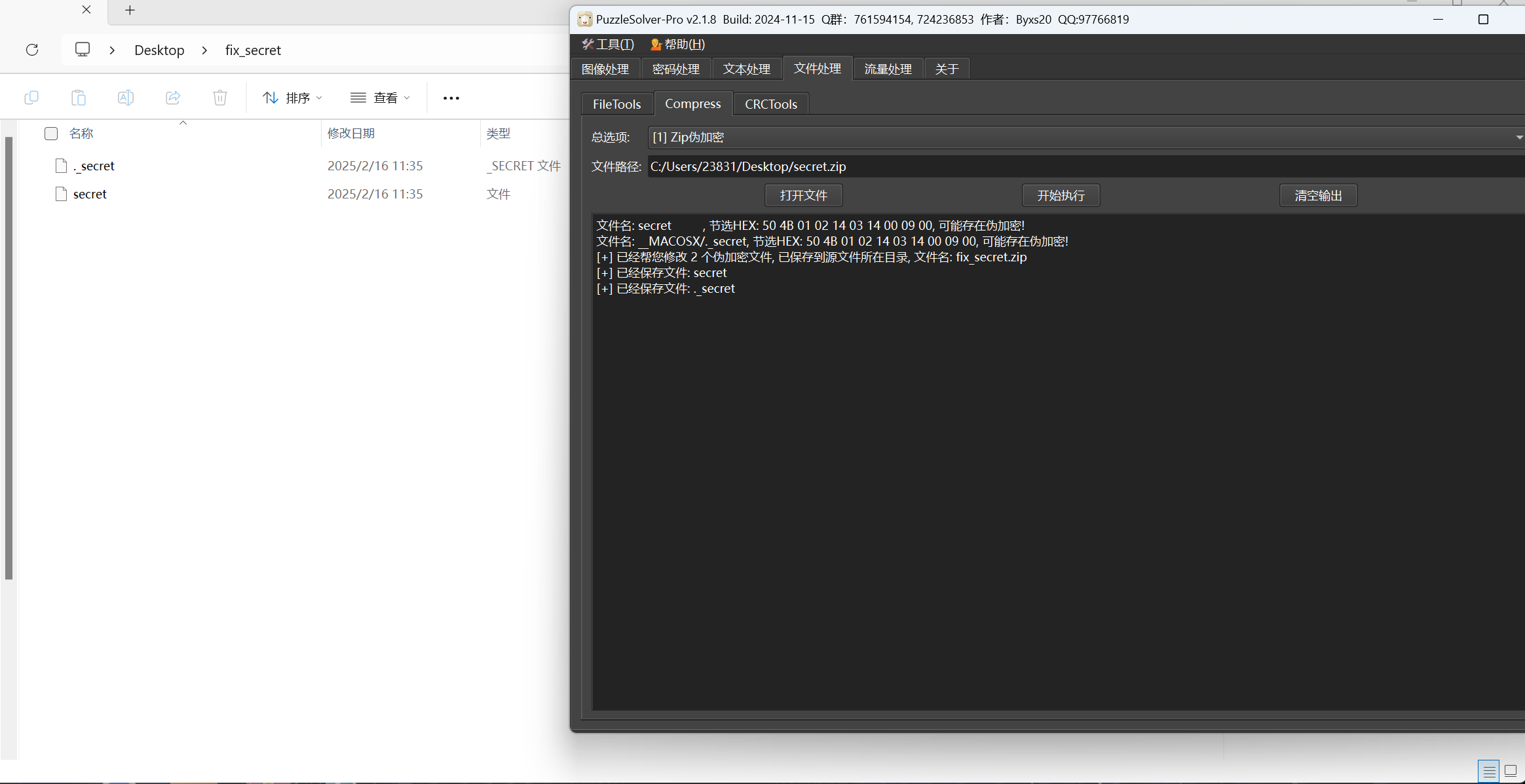
文件png缺少文件头,添加文件头
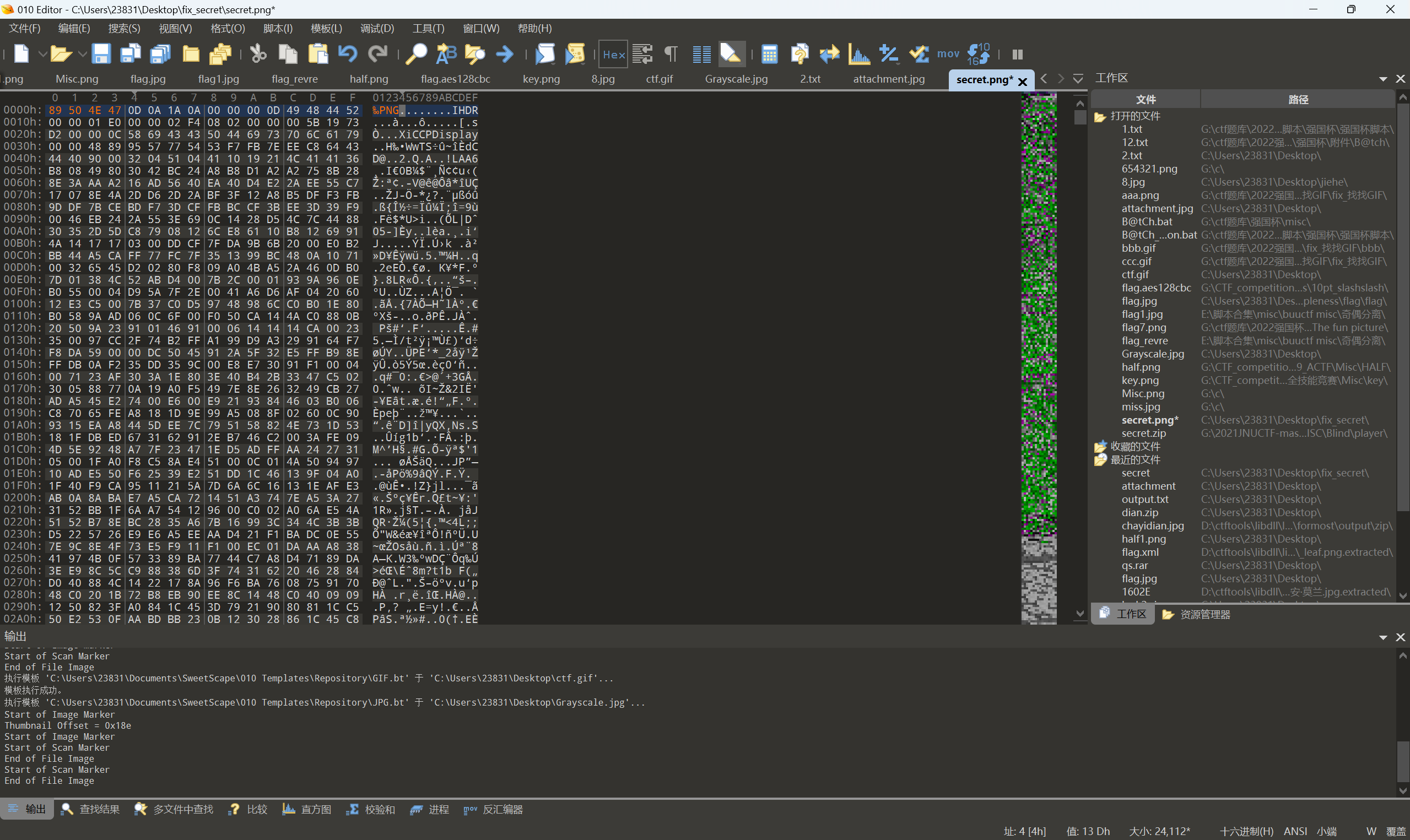
保存并打开文件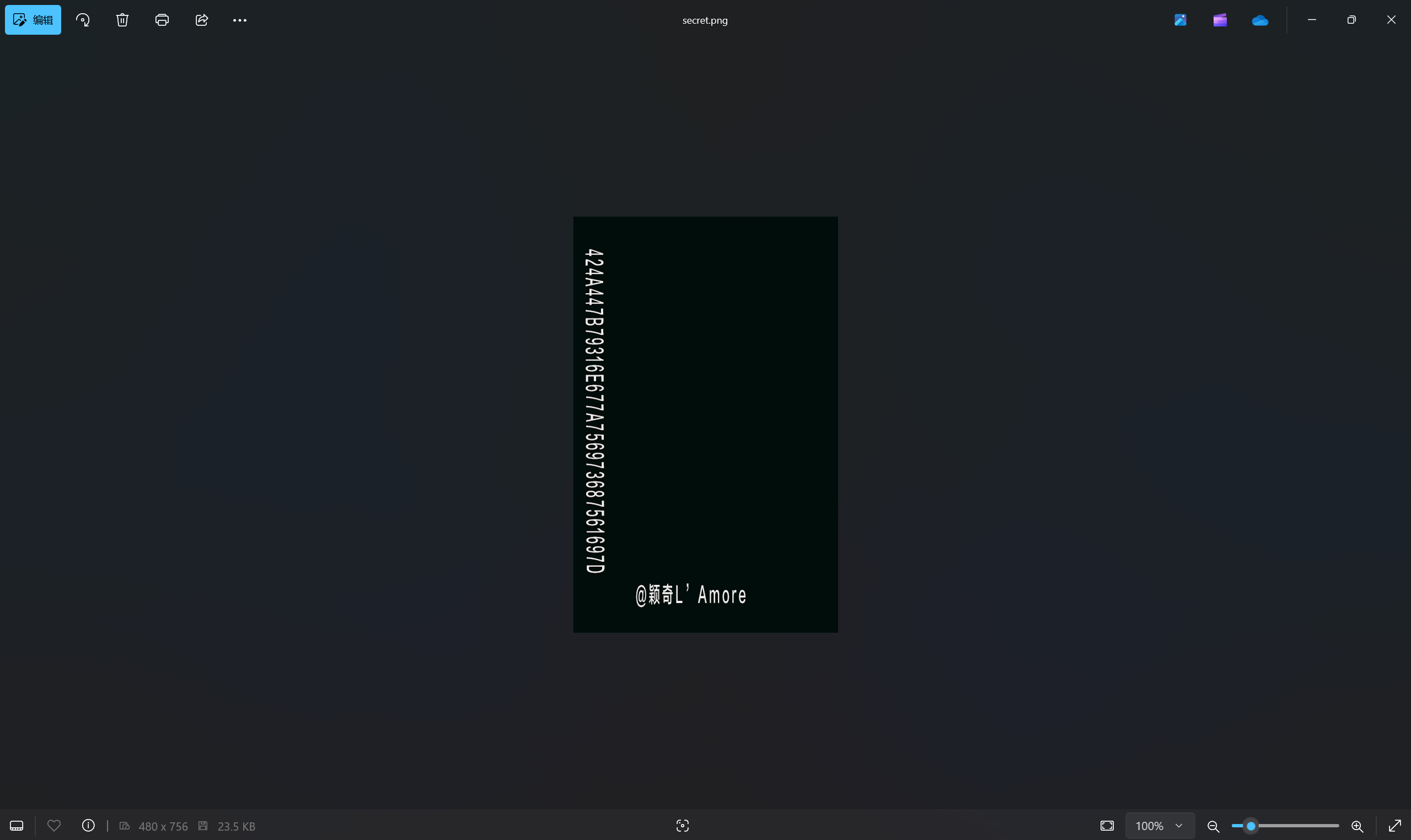
hex解码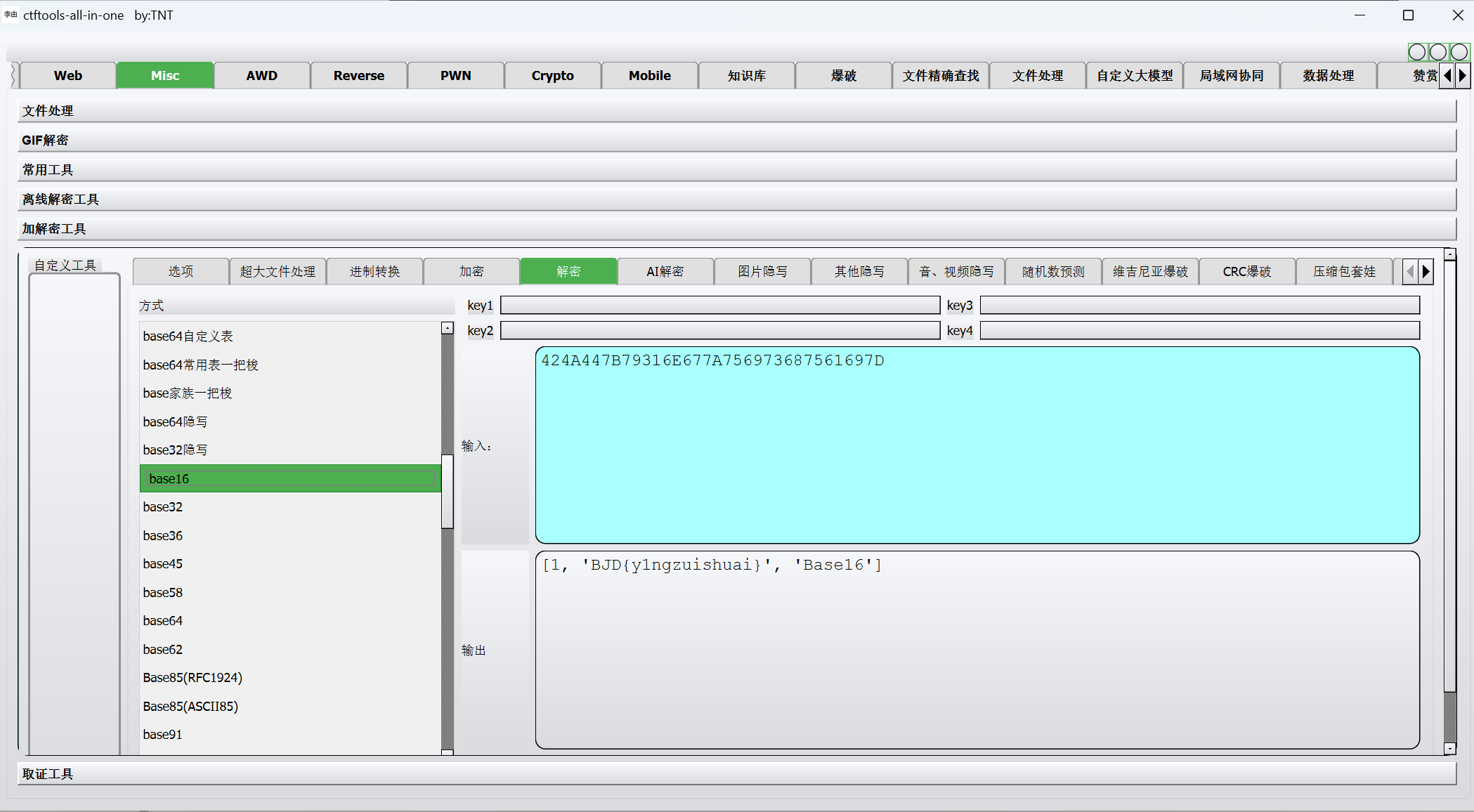
最后flag为
1 | flag{y1ngzuishuai} |



