到底为了什么
https://blog.csdn.net/m0_51198141/article/details/134817629
[2020 新春红包题]2
附件已经没有了
[BSidesSF2020]magic
ctf-2020-release/magic/solution/solution.txt at master · BSidesSF/ctf-2020-release
[CFI-CTF 2018]FlagCollection 🚩
2018-CFI-CTF/FlagCollection/README.md at master · CFI-UL/2018-CFI-CTF
[NewStarCTF 公开赛赛道]Yesec no drumsticks 2
零宽解密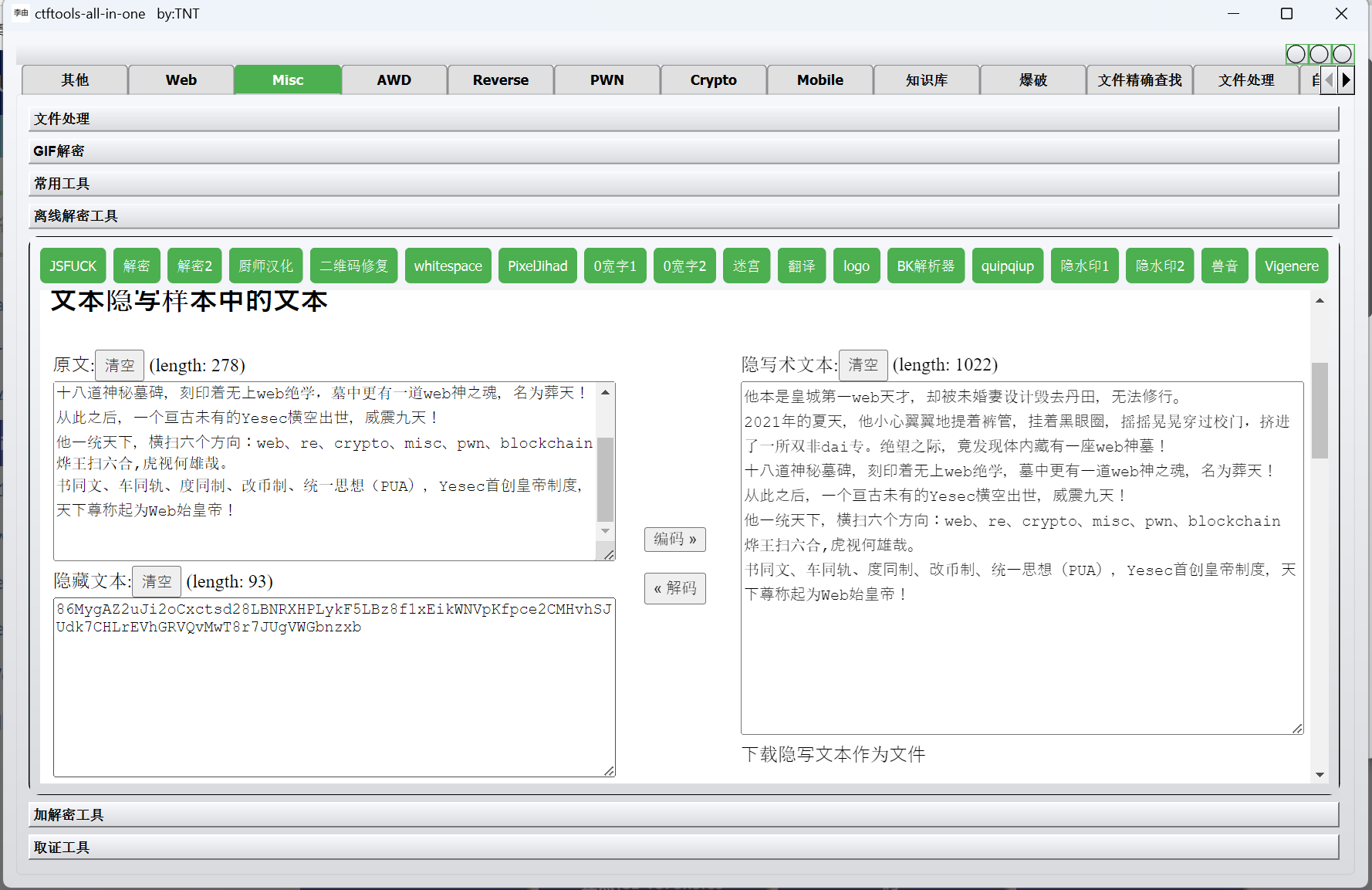
赛博厨子一把梭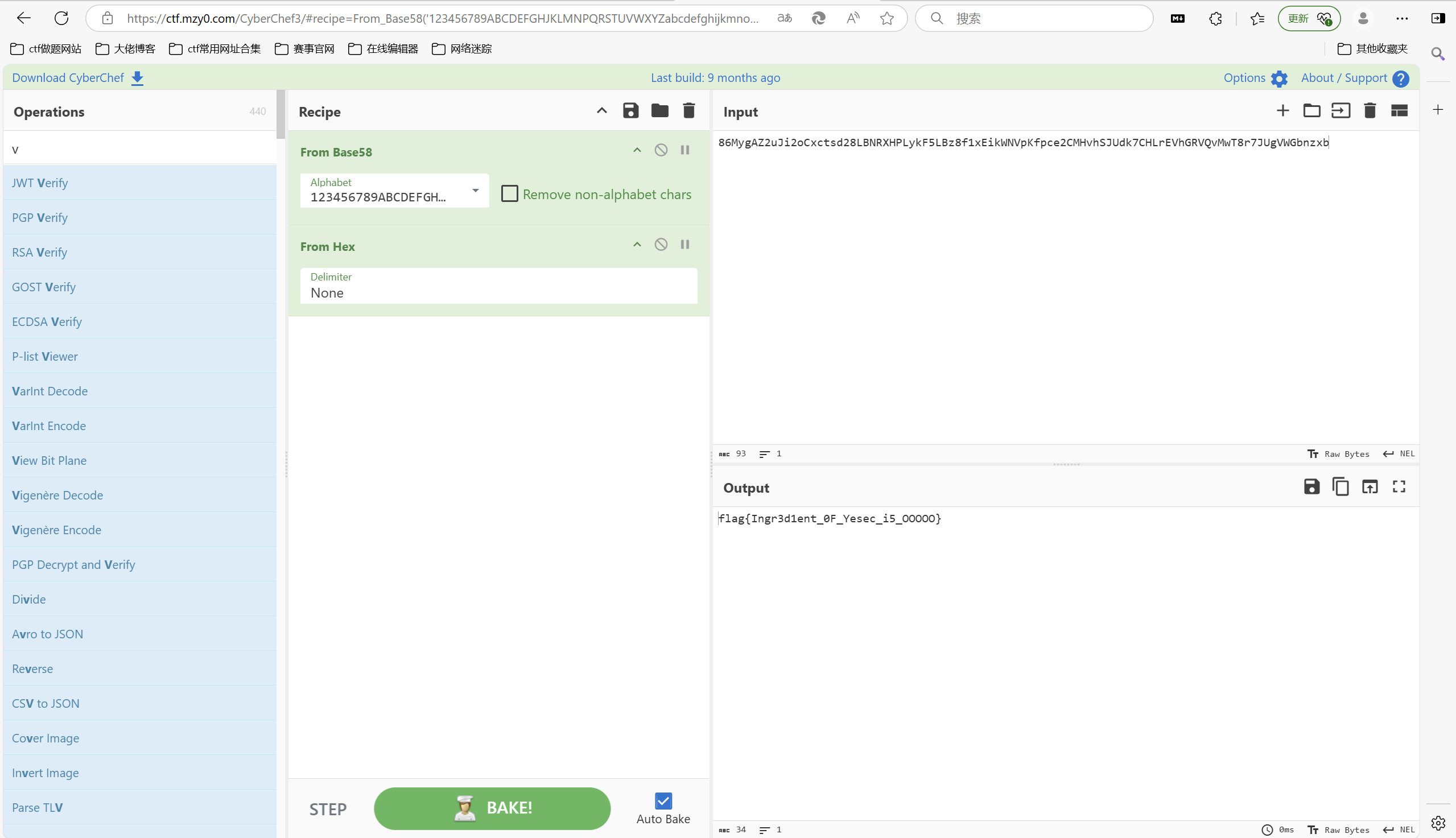
最后flag为
1 | flag{Ingr3d1ent_0F_Yesec_i5_OOOOO} |
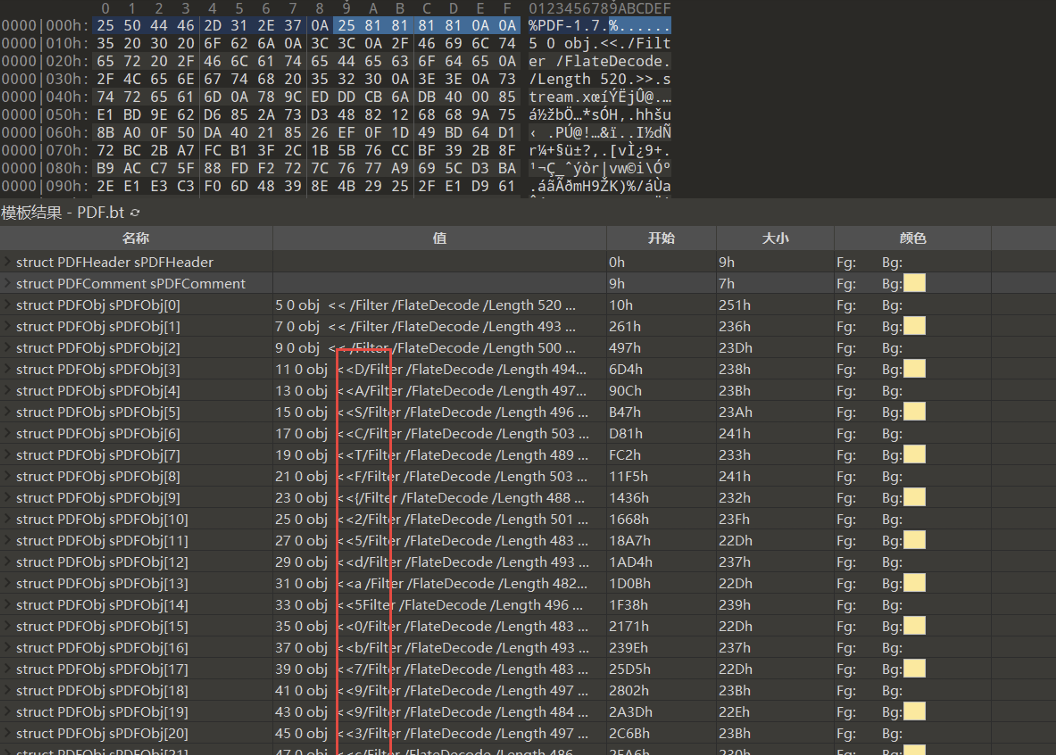
[NewStarCTF 公开赛赛道]奇怪的PDF 2
发现base编码提取
1 | with open('strange2.pdf.lnk', 'rb') as f: |
.cab文件打开
最后flag为
1 | flag{It_1s_a_fak3_but_r3al_PDF} |
[DASCTF X 0psu3十一月挑战赛|越艰巨·越狂热]IceTea
蚁剑流量发现hex编码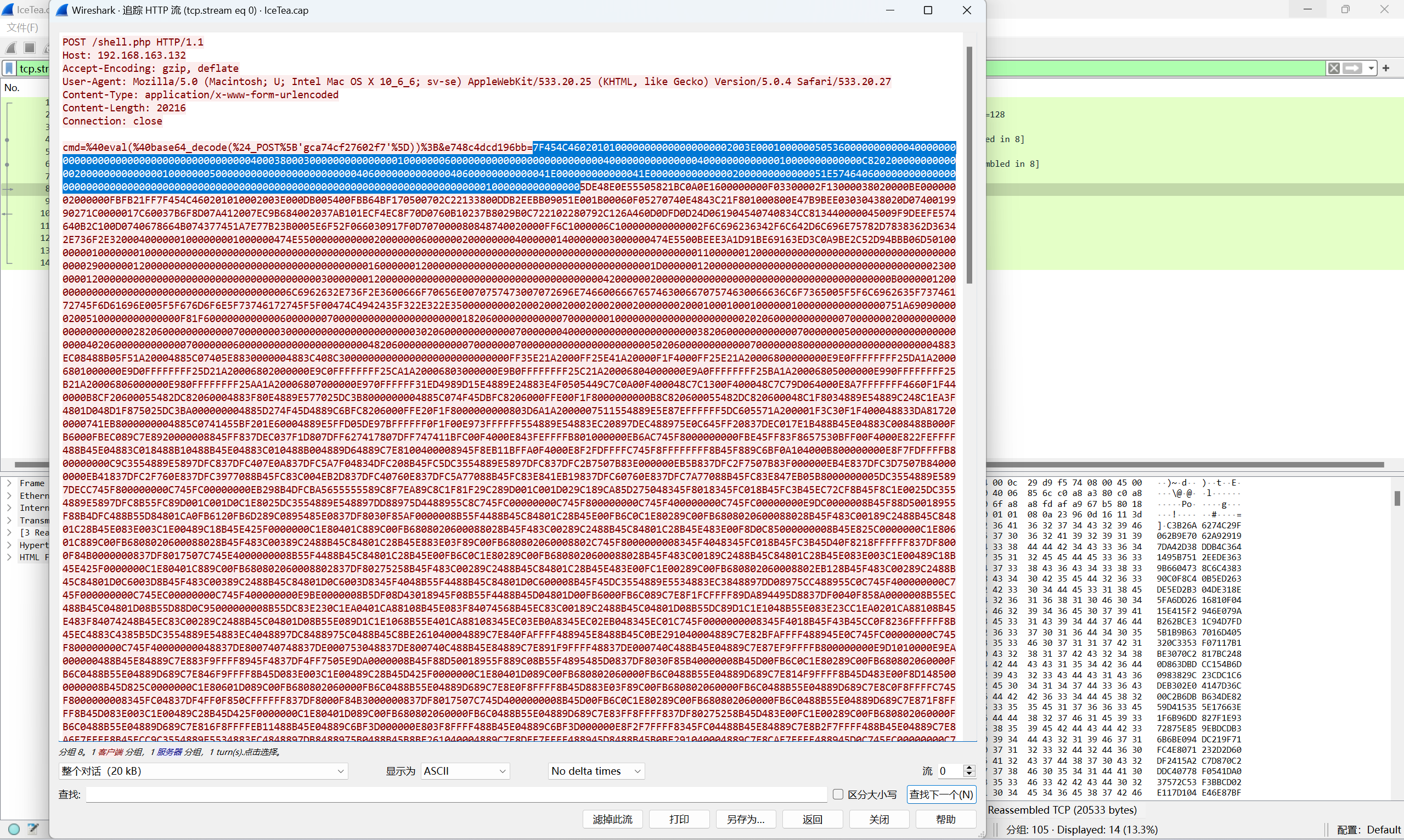
赛博厨子解密得到elf文件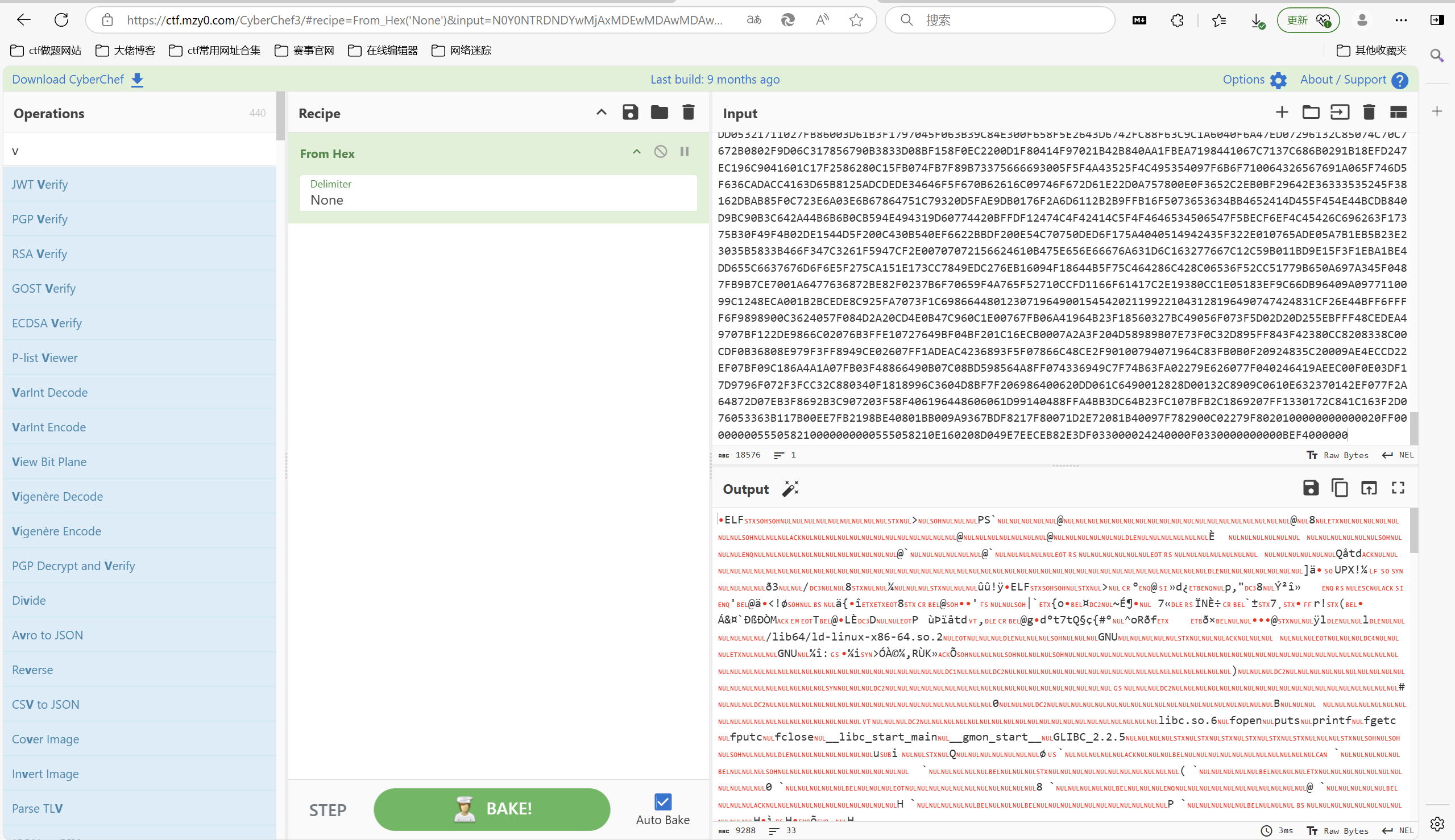
找到这个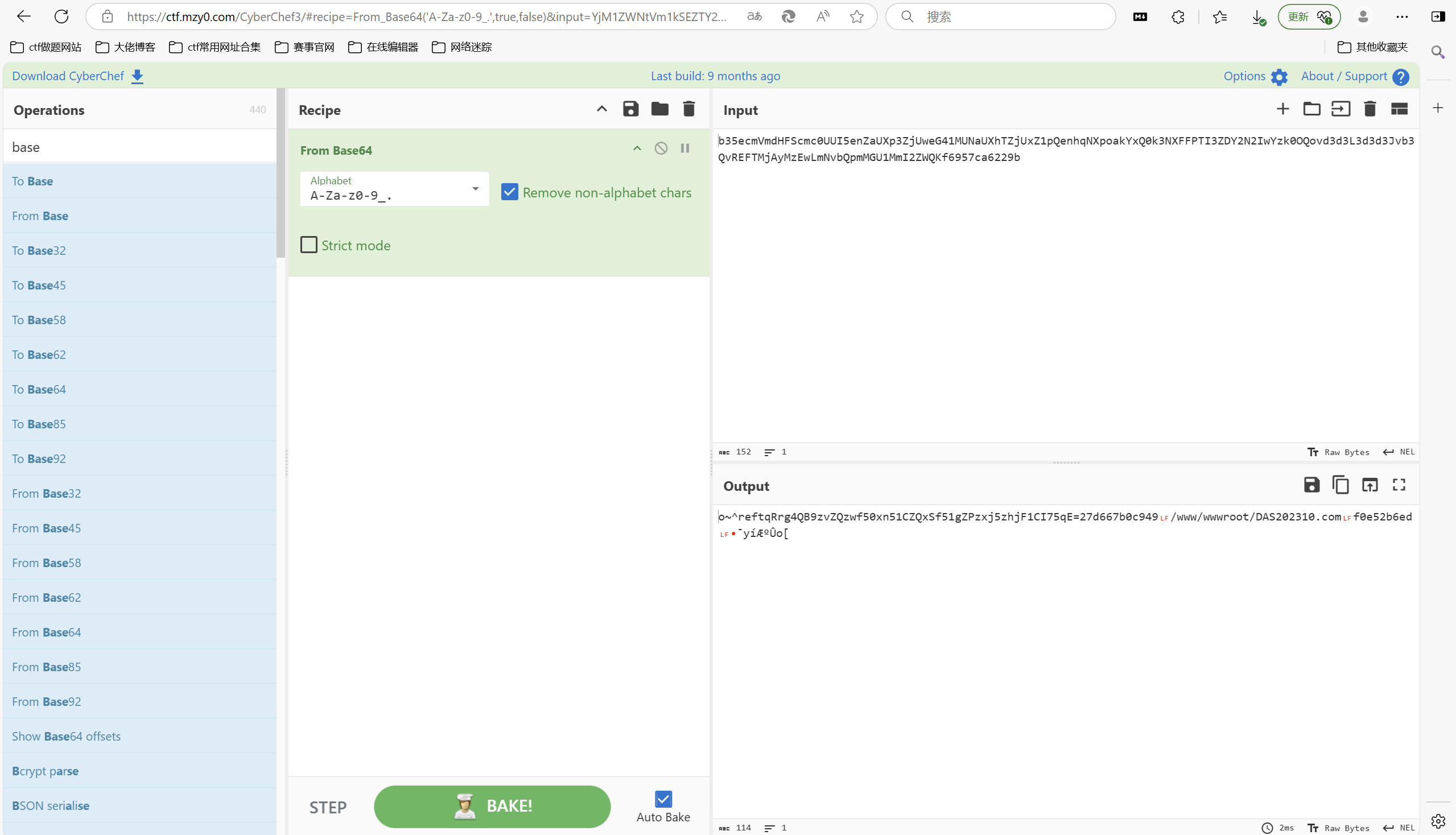
解密得到flag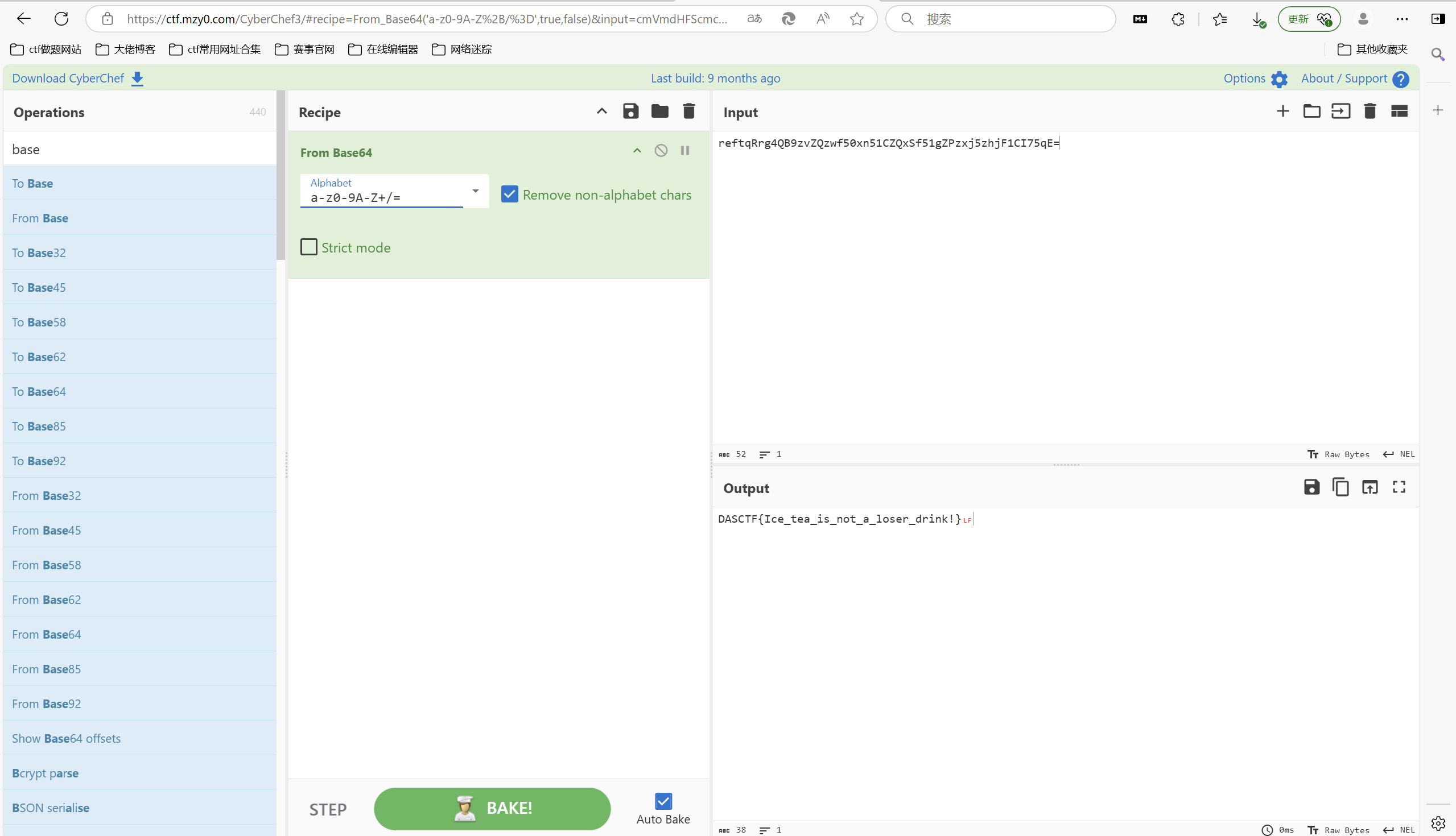
最后flag为
1 | flag{Ice_tea_is_not_a_loser_drink!} |
[INSHack2017]lost-file
INS’HACK 2017 - Forensics 225 Lost File
[Dest0g3 520迎新赛]OCR
宽高一把梭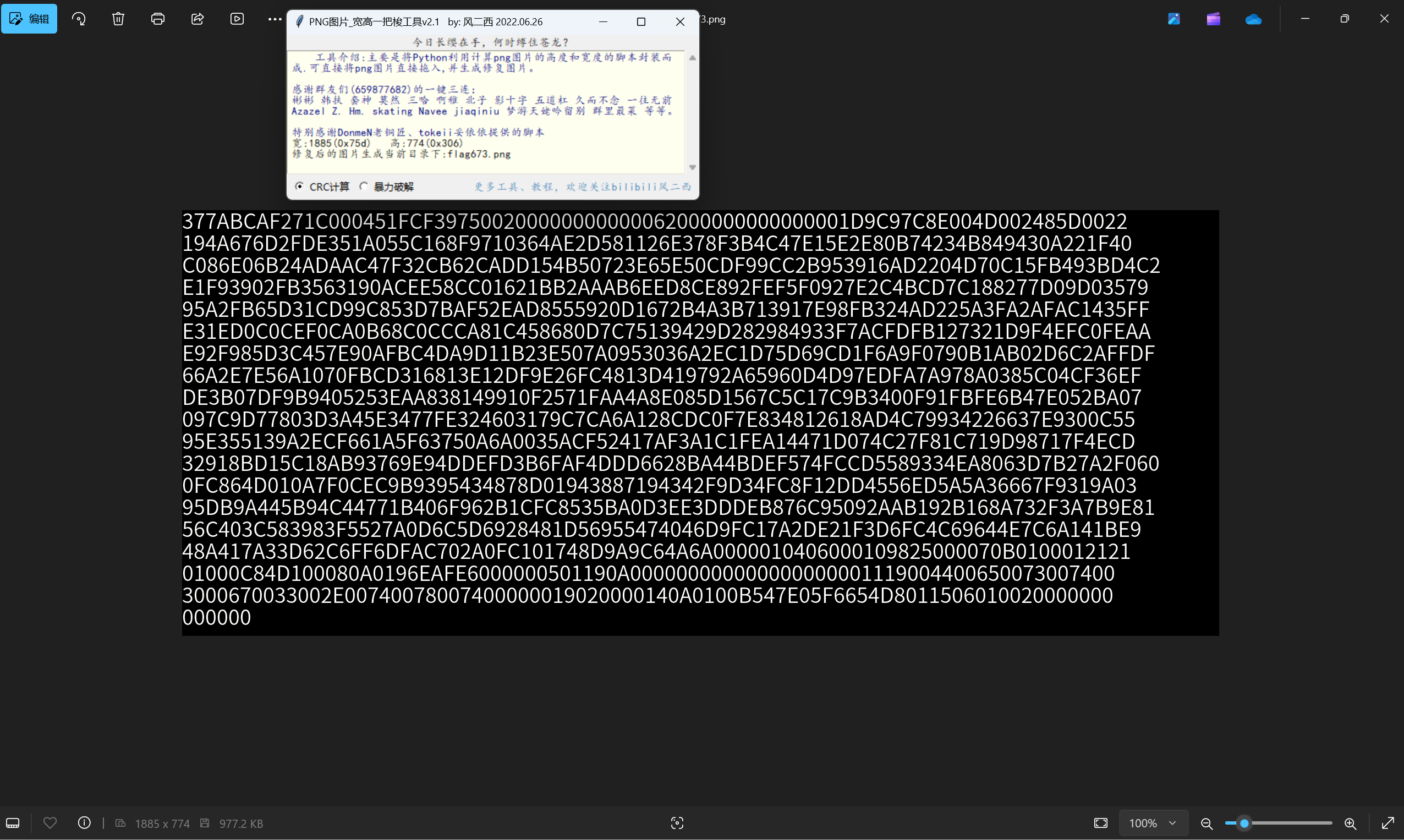
qrc识别得到hex,解密得到7z文件
1 | RGVzdDBnM3szNDUxMjA5OC0zMzA5LTc3MTItODg2NS03ODM0NjAyMjE2NDd9 |
解密得到
1 | Dest0g3{34512098-3309-7712-8865-783460221647} |
[DASCTF X 0psu3十一月挑战赛|越艰巨·越狂热]ez_forensics
看我朋友博客就行
[DASCTF X 0psu3十一月挑战赛|越艰巨·越狂热_dasctf x 0psu3十一月挑战赛|越艰巨·越狂热]ezfastjson-CSDN博客
[GKCTF X DASCTF应急挑战杯]你知道apng吗
和此题做法一致
[GKCTF 2021]你知道apng吗
[VNCTF2022公开赛]仔细找找
下载附件
先寻找像素点之间的间隔,然后拼接在一起生成新的图片
1 | from re import L |
运行得到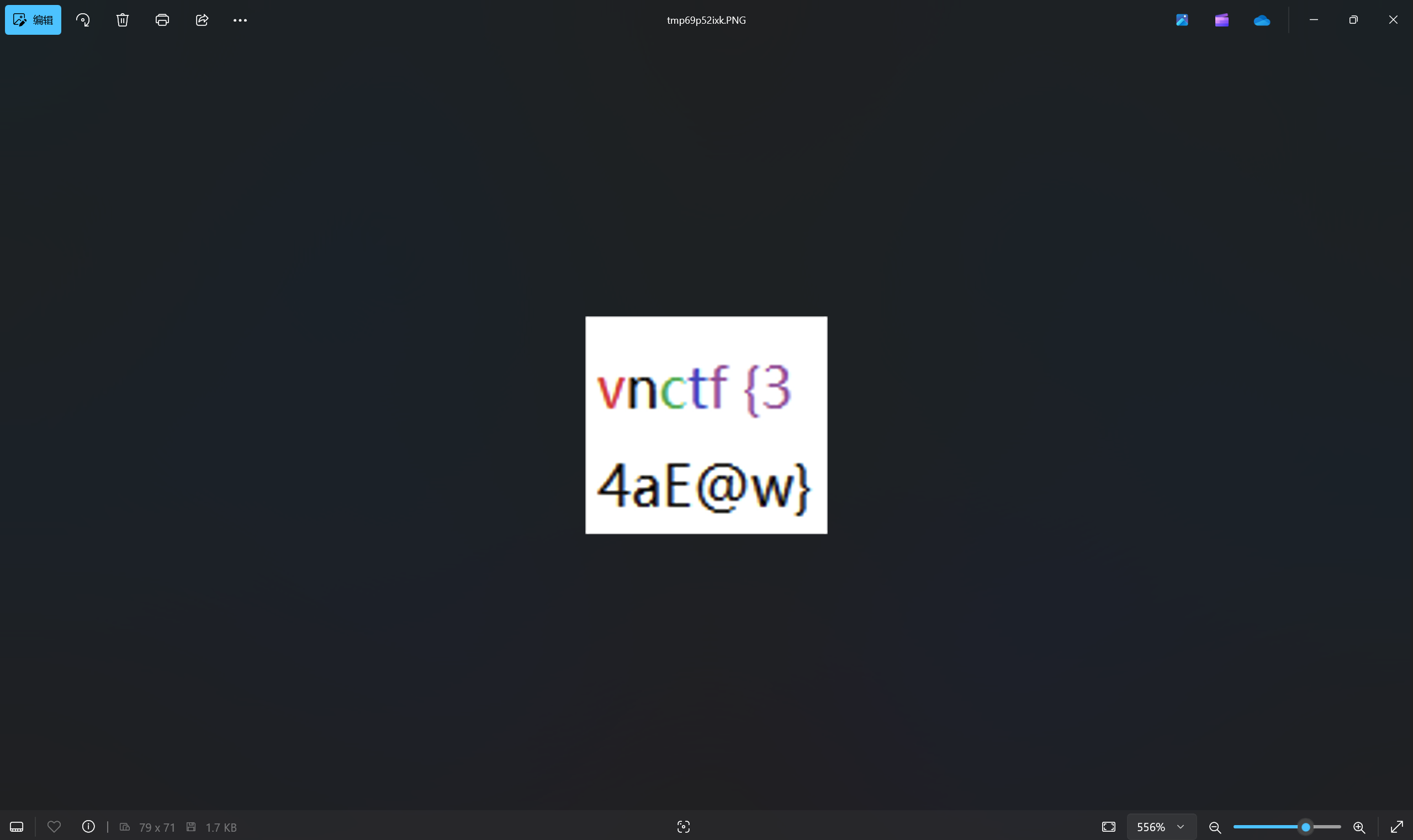
最后flag为
1 | flag{34aE@w} |
[DASCTF X GFCTF 2022十月挑战赛!]滴滴图
题目描述:
1 | 真真假假,你不会全部相信吧? |
jpg其实是个png,而且文件尾有个zip,分离后得到压缩包和一段unicode编码的字符,解个码得到压缩包密码:this_is_paSS
得到一张小羊图,crc错误,脚本爆破宽高得到原图,看到是假密码(this_is_not_PASSWORD),再联系题目描述,把假密码当真密码,发现对了,于是成功解开一开始的压缩包
音频文件听出来是摩斯密码,但是有点怪,audacity分析一下发现左右声道不一样,右声道为干扰,因此只关注左声道,解码后再解一层hex得到flag
[GWCTF2019]fun
剪刀石头布
1 | from pwn import * |
[陇原战”疫”2021网络安全大赛]soEasyCheckin
1 | MU2WEOLCGNSTOYLEHA4WKNJZGI4GGZJYMIYDSMDFHA4DOYLBMU3TSNDCGFSTKYRZMIZWKN3BMQ4DSZJVMI4WEM3FG5QWIOBZMU4DQN3BMFSTOOJUMIYWKNTCGM4TKZJWMIZGEYTFGU4GMODCMU2TSNRYGRSTKYRZMIZWKN3BMQ4DSZJVMI4WEM3FG5QWIOBZMU3GEMBZGFSTIYRYMJRGKNJYGVQWGZJWMFSGCM3FGY4TKYLDMU2GEOBZMFSTKOJSHBRWKODCGA4TAZJWHE3DQN3FGY4TQODFMU2WEOLCGNSTOYLEHA4WKNZYHBRDCZJVHFRGEZDFGU4DKYLDMU3GCZDBGNSTMOJVMFRWKNDCHA4WCZJVHA2WCY3FGZQWIYJTMU4GCZRZMFSTIYTGMEYWKOBYG5QWCZJXHE2GEMLFGU4TEODDMU4GEMBZGBSTMYRQHEYWKNDCHBRGEZJVMI4WEM3FG5QWIOBZMU3TQODCGFSTKOLCMJSGKNJYGVQWGZJWMFSGCM3FGY4TKYLDMU2GEOBZMFSTKOBVMFRWKNTBMRQTGZJVMI4WEM3FG5QWIOBZMU2TSMRYMNSTQYRQHEYGKNRZGY4DOZJWHE4DQZLFHA4DOYLBMU3TSNDCGFSTKODGHBRGKNJZGY4DIZJVHA2WCY3FGZQWIYJTMU2TQNLBMNSTMYLEMEZWKNRZGVQWGZJUMI4DSYLFGU4TEODDMU4GEMBZGBSTQOBXMFQWKNZZGRRDCZJWHE3DQN3FGY4TQODFMU2TQZRYMJSTKOJWHA2GKNTCGM4TKZJWMIZGEYTFHA4DOYLBMU3TSNDCGFSTKODGHBRGKNJZGY4DIZJVHA2WCY3FGZQWIYJTMU2TQNLBMNSTMYLEMEZWKNJYMY4GEZJVHE3DQNDFGY4TKYLDMU2GEOBZMFSTKOBVMFRWKNTBMRQTGZJYMFTDSYLFGRRGMYJRMU4DQN3BMFSTOOJUMIYWKNJYGVQWGZJWMFSGCM3FGZRDGOJVMU3GEMTCMJSTKOJSHBRWKODCGA4TAZJVHEZDQY3FHBRDAOJQMU2WEOLCGNSTOYLEHA4WKNRZGVQWGZJUMI4DSYLFGZRDGOJVMU3GEMTCMJSTKYRZMIZWKN3BMQ4DSZJVHA2WCY3FGZQWIYJTMU3GEMBZGFSTIYRYMJRGKNJYGVQWGZJWMFSGCM3FHBQWMOLBMU2GEZTBGFSTQOBXMFQWKNZZGRRDCZJVHEZDQY3FHBRDAOJQMU3DSNRYG0$TMOJYHBSWKNLCHFRDGZJXMFSDQOLFGU4GMODCMU2TSNRYGRSTQOBXMFQWKNZZGRRDCZJVHA2WCY3FGZQWIYJTMU3TQODCGFSTKOLCMJSGKNJYGVQWGZJWMFSGCM3FGZRDAOJRMU2GEODCMJSTKOBVMFRWKNTBMRQTGZJVHBTDQYTFGU4TMOBUMU3TQODCGFSTKOLCMJSGKNJZGI4GGZJYMIYDSMDFHA4DOYLBMU3TSNDCGFSTKYRZMIZWKN3BMQ4DSZJWHE2WCY3FGRRDQOLBMU2TQNLBMNSTMYLEMEZWKNRZGVQWGZJUMI4DSYLFGU4TEODDMU4GEMBZGBSTQOBXMFQWKNZZGRRDCZJWMIZTSNLFGZRDEYTCMU4GCZRZMFSTIYTGMEYWKNJZGI4GGZJYMIYDSMA= |
前半段
1 | MU2WEOLCGNSTOYLEHA4WKNJZGI4GGZJYMIYDSMDFHA4DOYLBMU3TSNDCGFSTKYRZMIZWKN3BMQ4DSZJVMI4WEM3FG5QWIOBZMU4DQN3BMFSTOOJUMIYWKNTCGM4TKZJWMIZGEYTFGU4GMODCMU2TSNRYGRSTKYRZMIZWKN3BMQ4DSZJVMI4WEM3FG5QWIOBZMU3GEMBZGFSTIYRYMJRGKNJYGVQWGZJWMFSGCM3FGY4TKYLDMU2GEOBZMFSTKOJSHBRWKODCGA4TAZJWHE3DQN3FGY4TQODFMU2WEOLCGNSTOYLEHA4WKNZYHBRDCZJVHFRGEZDFGU4DKYLDMU3GCZDBGNSTMOJVMFRWKNDCHA4WCZJVHA2WCY3FGZQWIYJTMU4GCZRZMFSTIYTGMEYWKOBYG5QWCZJXHE2GEMLFGU4TEODDMU4GEMBZGBSTMYRQHEYWKNDCHBRGEZJVMI4WEM3FG5QWIOBZMU3TQODCGFSTKOLCMJSGKNJYGVQWGZJWMFSGCM3FGY4TKYLDMU2GEOBZMFSTKOBVMFRWKNTBMRQTGZJVMI4WEM3FG5QWIOBZMU2TSMRYMNSTQYRQHEYGKNRZGY4DOZJWHE4DQZLFHA4DOYLBMU3TSNDCGFSTKODGHBRGKNJZGY4DIZJVHA2WCY3FGZQWIYJTMU2TQNLBMNSTMYLEMEZWKNRZGVQWGZJUMI4DSYLFGU4TEODDMU4GEMBZGBSTQOBXMFQWKNZZGRRDCZJWHE3DQN3FGY4TQODFMU2TQZRYMJSTKOJWHA2GKNTCGM4TKZJWMIZGEYTFHA4DOYLBMU3TSNDCGFSTKODGHBRGKNJZGY4DIZJVHA2WCY3FGZQWIYJTMU2TQNLBMNSTMYLEMEZWKNJYMY4GEZJVHE3DQNDFGY4TKYLDMU2GEOBZMFSTKOBVMFRWKNTBMRQTGZJYMFTDSYLFGRRGMYJRMU4DQN3BMFSTOOJUMIYWKNJYGVQWGZJWMFSGCM3FGZRDGOJVMU3GEMTCMJSTKOJSHBRWKODCGA4TAZJVHEZDQY3FHBRDAOJQMU2WEOLCGNSTOYLEHA4WKNRZGVQWGZJUMI4DSYLFGZRDGOJVMU3GEMTCMJSTKYRZMIZWKN3BMQ4DSZJVHA2WCY3FGZQWIYJTMU3GEMBZGFSTIYRYMJRGKNJYGVQWGZJWMFSGCM3FHBQWMOLBMU2GEZTBGFSTQOBXMFQWKNZZGRRDCZJVHEZDQY3FHBRDAOJQMU3DSNRYG0 |
base解码
1 | e5b9b3e7ad89e5928ce8b090e887aae794b1e5b9b3e7ad89e5b9b3e7ad89e887aae794b1e6b395e6b2bbe58f8be59684e5b9b3e7ad89e5b9b3e7ad89e6b091e4b8bbe585ace6ada3e695ace4b89ae5928ce8b090e69687e6988ee5b9b3e7ad89e788b1e59bbde585ace6ada3e695ace4b89ae585ace6ada3e8af9ae4bfa1e887aae794b1e5928ce8b090e6b091e4b8bbe5b9b3e7ad89e788b1e59bbde585ace6ada3e695ace4b89ae585ace6ada3e5b9b3e7ad89e5928ce8b090e69687e6988ee887aae794b1e58f8be59684e585ace6ada3e585ace6ada3e695ace4b89ae5928ce8b090e887aae794b1e69687e6988ee58f8be59684e6b395e6b2bbe887aae794b1e58f8be59684e585ace6ada3e585ace6ada3e58f8be59684e695ace4b89ae585ace6ada3e8af9ae4bfa1e887aae794b1e585ace6ada3e6b395e6b2bbe5928ce8b090e5928ce8b090e5b9b3e7ad89e695ace4b89ae6b395e6b2bbe5b9b3e7ad89e585ace6ada3e6b091e4b8bbe585ace6ada3e8af9ae4bfa1e887aae794b1e5928ce8b090e69688 |
hex解码
1 | 平等和谐自由平等平等自由法治友善平等平等民主公正敬业和谐文明平等爱国公正敬业公正诚信自由和谐民主平等爱国公正敬业公正平等和谐文明自由友善公正公正敬业和谐自由文明友善法治自由友善公正公正友善敬业公正诚信自由公正法治和谐和谐平等敬业法治平等公正民主公正诚信自由和谐斈 |
核心价值观解码
1 | SET{Qi2Xin1Xie2Li4-Long3Yuan |
后半段
1 | YHBSWKNLCHFRDGZJXMFSDQOLFGU4GMODCMU2TSNRYGRSTQOBXMFQWKNZZGRRDCZJVHA2WCY3FGZQWIYJTMU3TQODCGFSTKOLCMJSGKNJYGVQWGZJWMFSGCM3FGZRDAOJRMU2GEODCMJSTKOBVMFRWKNTBMRQTGZJVHBTDQYTFGU4TMOBUMU3TQODCGFSTKOLCMJSGKNJZGI4GGZJYMIYDSMDFHA4DOYLBMU3TSNDCGFSTKYRZMIZWKN3BMQ4DSZJWHE2WCY3FGRRDQOLBMU2TQNLBMNSTMYLEMEZWKNRZGVQWGZJUMI4DSYLsFGU4TEODDMU4GEMBZGBSTQOBXMFQWKNZZGRRDCZJWMIZTSNLFGZRDEYTCMU4GCZRZMFSTIYTGMEYWKNJZGI4GGZJYMIYDSMA= |
base解码
1 | 6988ee5b9b3e7ad89e58f8be59684e887aae794b1e585ace6ada3e788b1e59bbde585ace6ada3e6b091e4b8bbe585ace6ada3e58f8be59684e788b1e59bbde5928ce8b090e887aae794b1e5b9b3e7ad89e695ace4b89ae585ace6ada3e695ace4b89ae5928ce8b090e887aae794b1e6b395e6b2bbe8af9ae4bfa1e5928ce8b090 |
hex解码
1 | 平等友善自由公正爱国公正民主公正友善爱国和谐自由平等敬业公正敬业和谐自由法治诚信和谐 |
核心价值观解码
1 | Zhan4Yi4 |
最后flag为
1 | flag{Qi2Xin1Xie2Li4-Long3Yuan2Zhan4Yi4} |
[NewStarCTF 公开赛赛道]qsdz’s girlfriend 3
xshell连接
1 | 1.cat /etc/passwd >passwd |
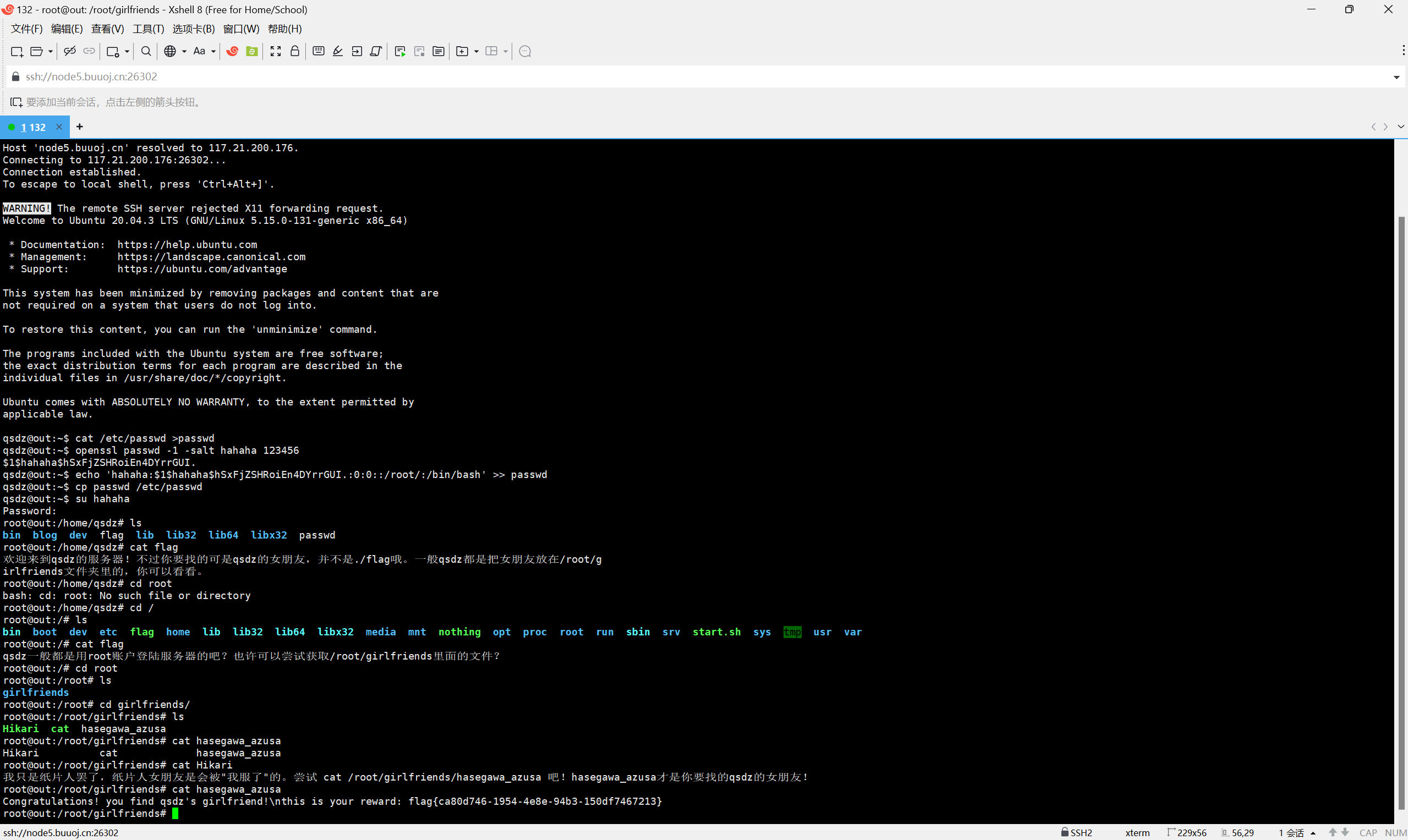
最后flag为
1 | flag{ca80d746-1954-4e8e-94b3-150df7467213} |
[watevrCTF 2019]Blurred Image
watevrCTF-2019/challenges/forensics/blur_image/writeup.md at master · wat3vr/watevrCTF-2019
[b01lers2020]matryoshka
b01lers-ctf-2020/misc/200_matryoshka at master · b01lers/b01lers-ctf-2020
[DASCTF Oct X 吉林工师 欢迎来到魔法世界~]魔法秘文
魔法密文 Writeup| DASCTF Oct X 吉林工师_dasctf oct writeup-CSDN博客
[NewStarCTF 公开赛赛道]qsdz’s girlfriend 4
下载附件
魔女文字对照
翻译得到使用malbolge语言
最后flag为
1 | flag{Esol4ng_1s_es0} |
[INSHack2017]dga
inshack-2017/challenges/misc/dga-75/writeup.md at master · HugoDelval/inshack-2017
[羊城杯 2020]badapple
用Au打开音频,把前一段和歌曲混在一起的摩斯密码和后一段声音很小的摩斯密码经放大后都手动提取出来,解码之后得到一串数字和加号,把每个ASCII码转字符
1 | 101,99,111,110,100,50,99,111,109,101,115,104,116,116,112,58,47,47,49,50,57,46,50,48,52,46,49,56,57,46,50,53,52,58,54,54,54,54,47,109,111,111,110,47,32,71,87,72,84,123,102,105,114,115,116,49,97,112,112,101,97,114,115,104,101,114,101,95,115 |
js文件里发现了一个字符串,再右键查看页面源代码,又翻到了一个字符串注释
解码最后拼接
1 | first1appearshere_second2comes_third3isnttheend_youwin! |
[Dest0g3 520迎新赛]codegame
1 | code='THISISTHEPASSWORD' |
emoji解码
1 | flag{9f68f334-017a-4201-92df-dddcc145334d} |
[NewStarCTF 2023 公开赛道]Easymem
flag第一部分
mimikatz插件读取
1 | 83-5032-1056- |
flag2在桌面
flag3画图里
1 | flag{45a527fb-2f83-5032-1056- 0b949b63a947} |
[UTCTF2020]gb
UTCTF 2020 - GameBoy TAS (pwn/reversing) · Daniel Brodsky
[GKCTF X DASCTF应急挑战杯]FireFox Forensics
参考[GKCTF 2021]FireFox Forensics
[DASCTF Oct X 吉林工师 欢迎来到魔法世界~]魔法信息
提取压缩包,用010editor打开看看