[LitCTF 2023]只需要nc一下~
题目描述:
1 | 现成的shell nc一下就好了~ |
nc连接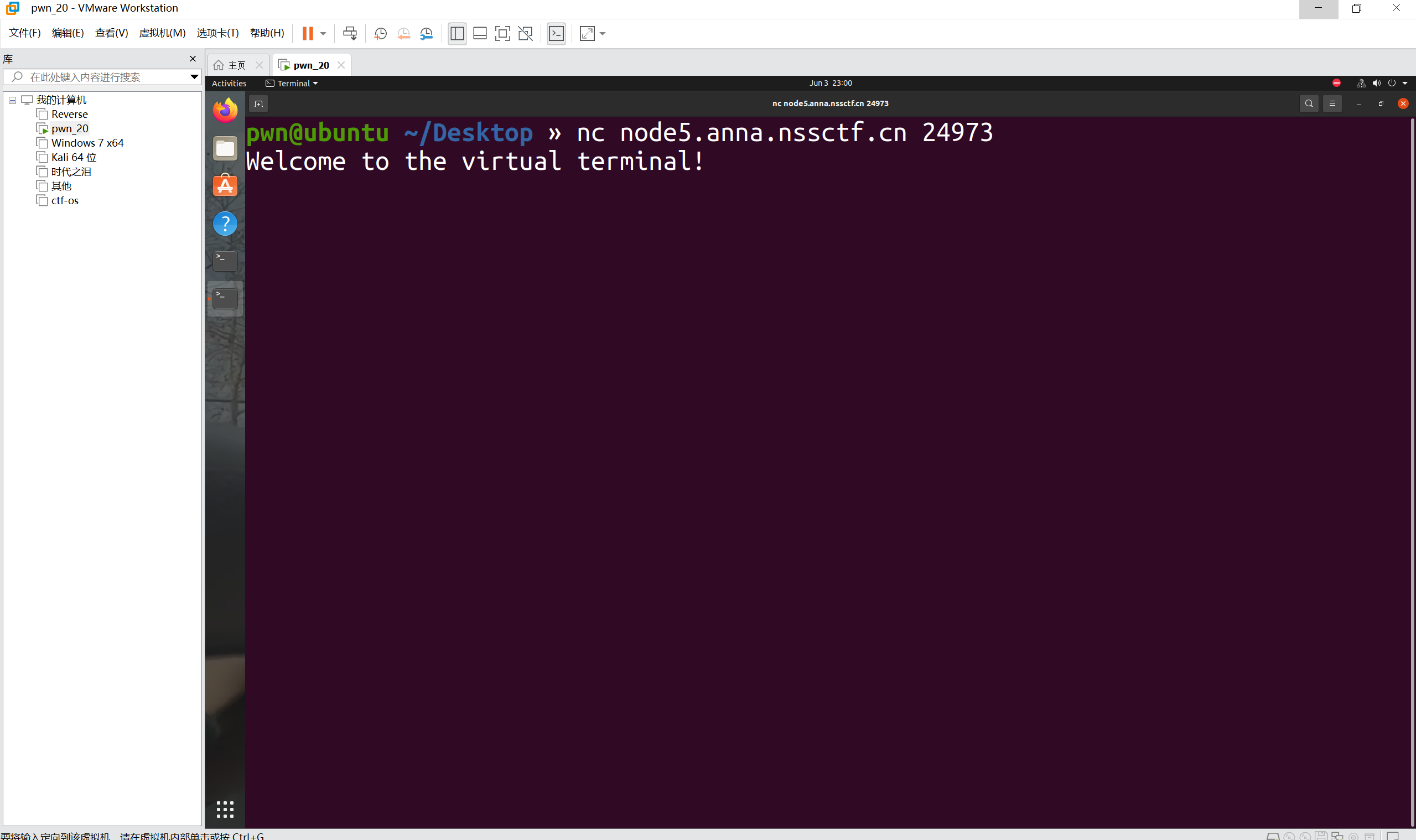
cat flag试试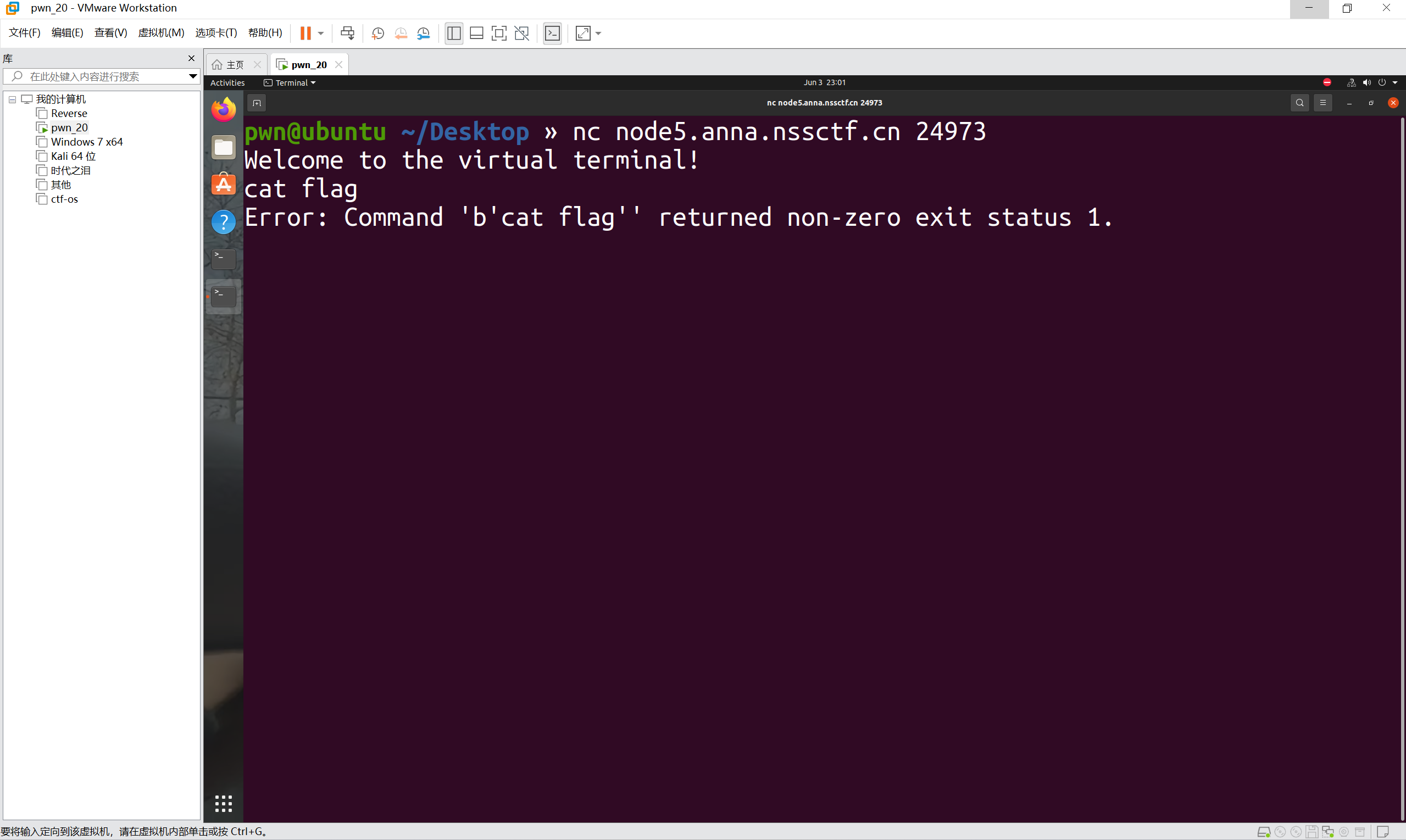
ls试一下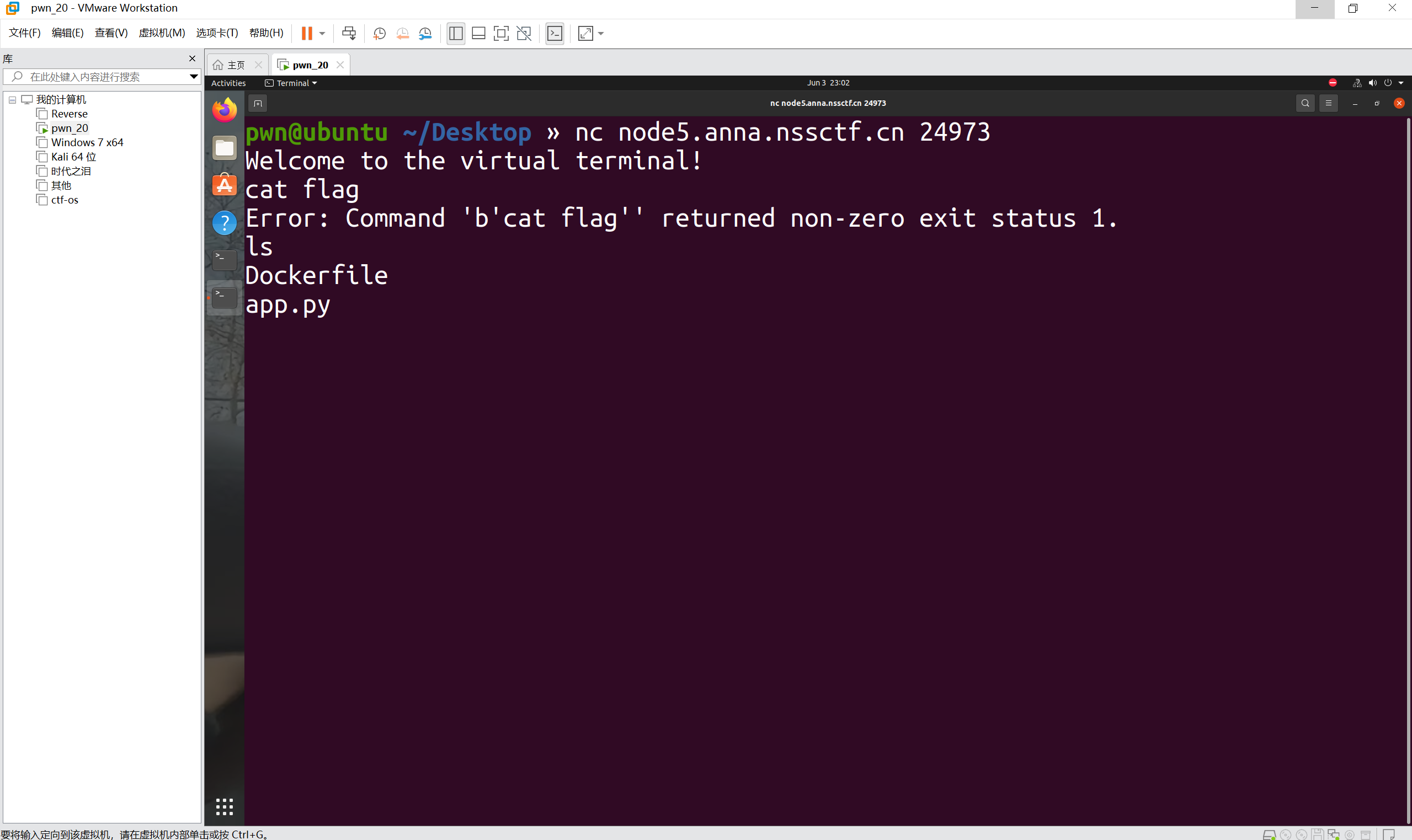
查看dockerfile文件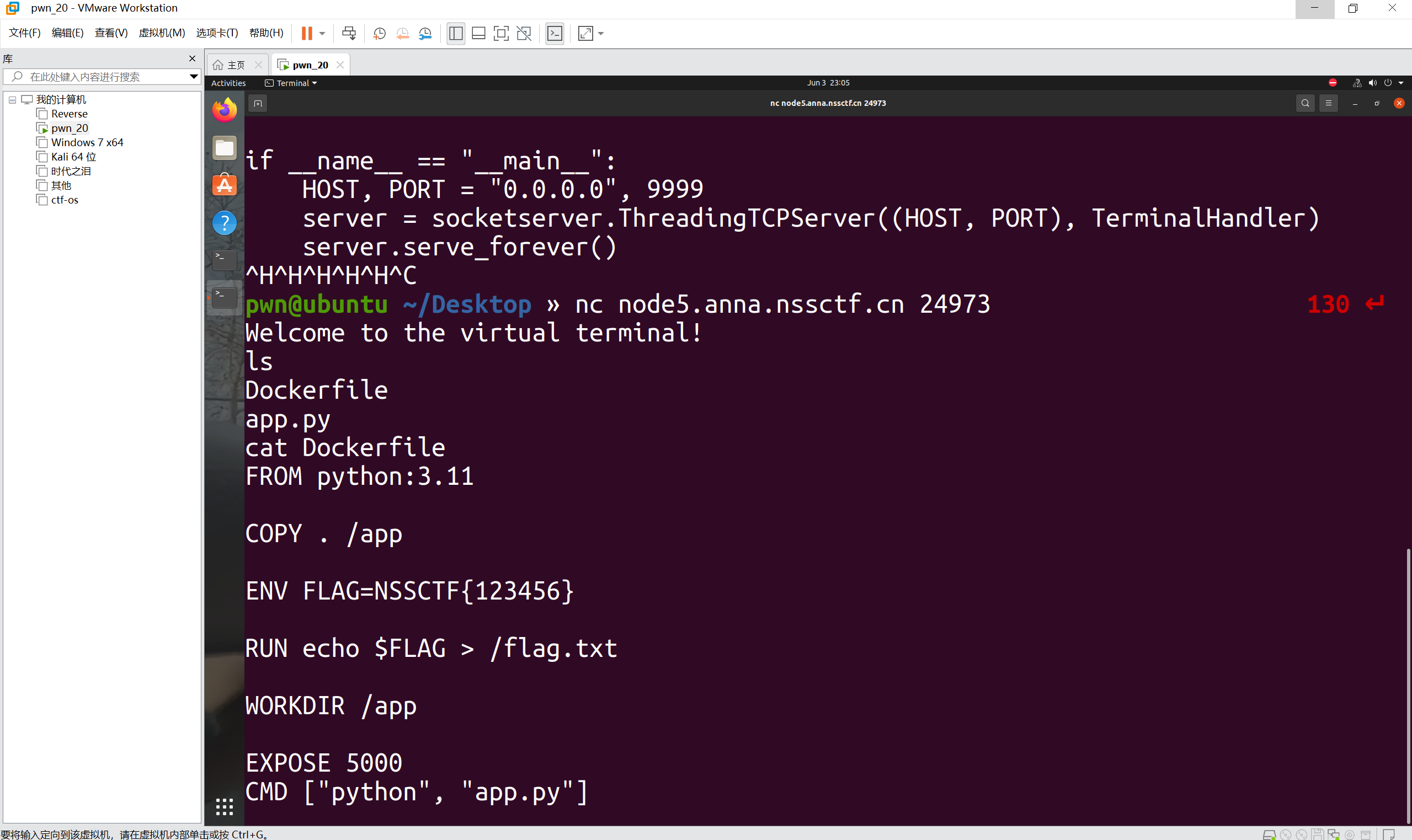
得到假flag
看到这条命令
1 | echo $FLAG > /flag.txt |
将环境变量 $FLAG 的值输出到 /flag.txt文件中
直接输入
1 | echo $FLAG |
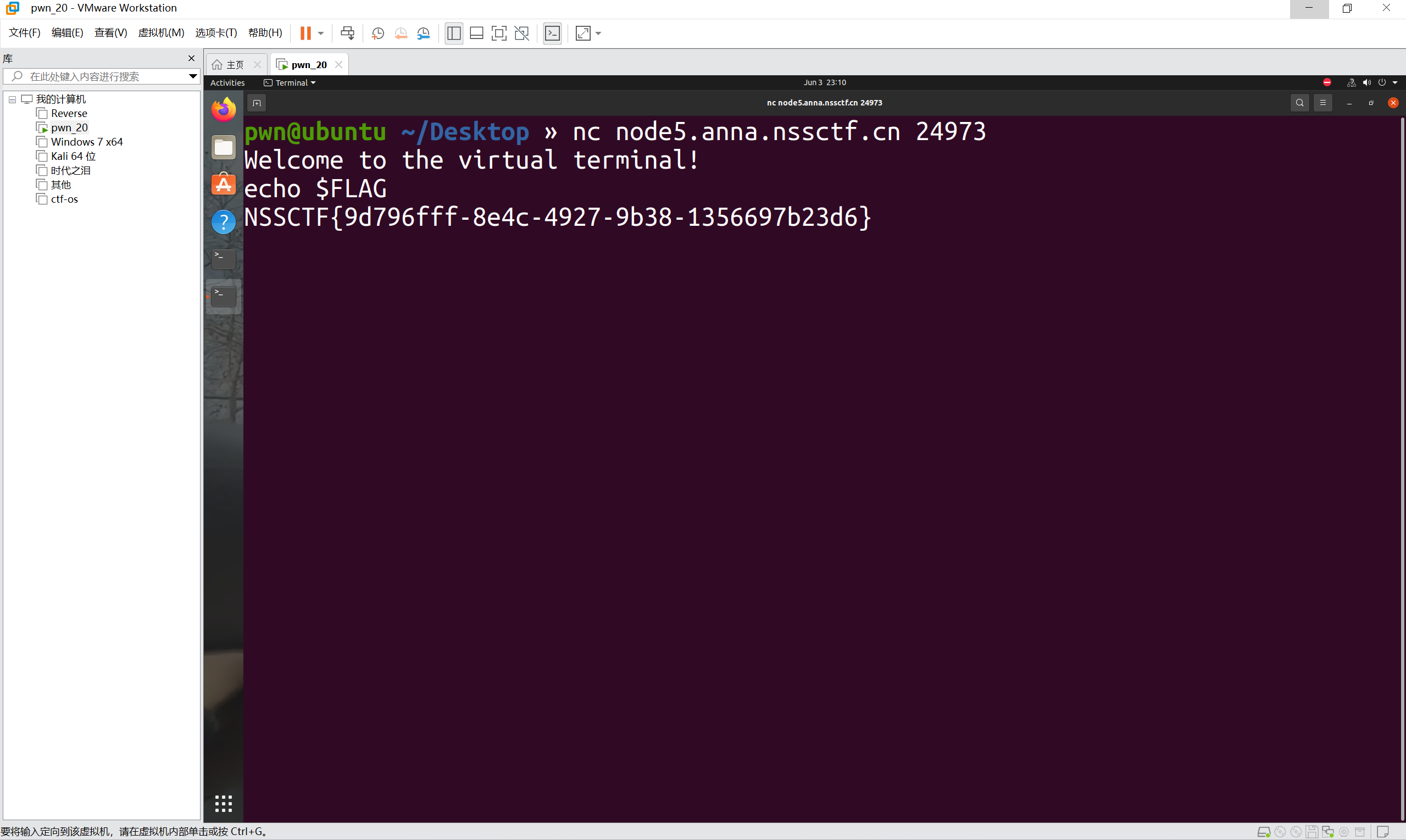
也可以直接输入环境变量
1 | env |
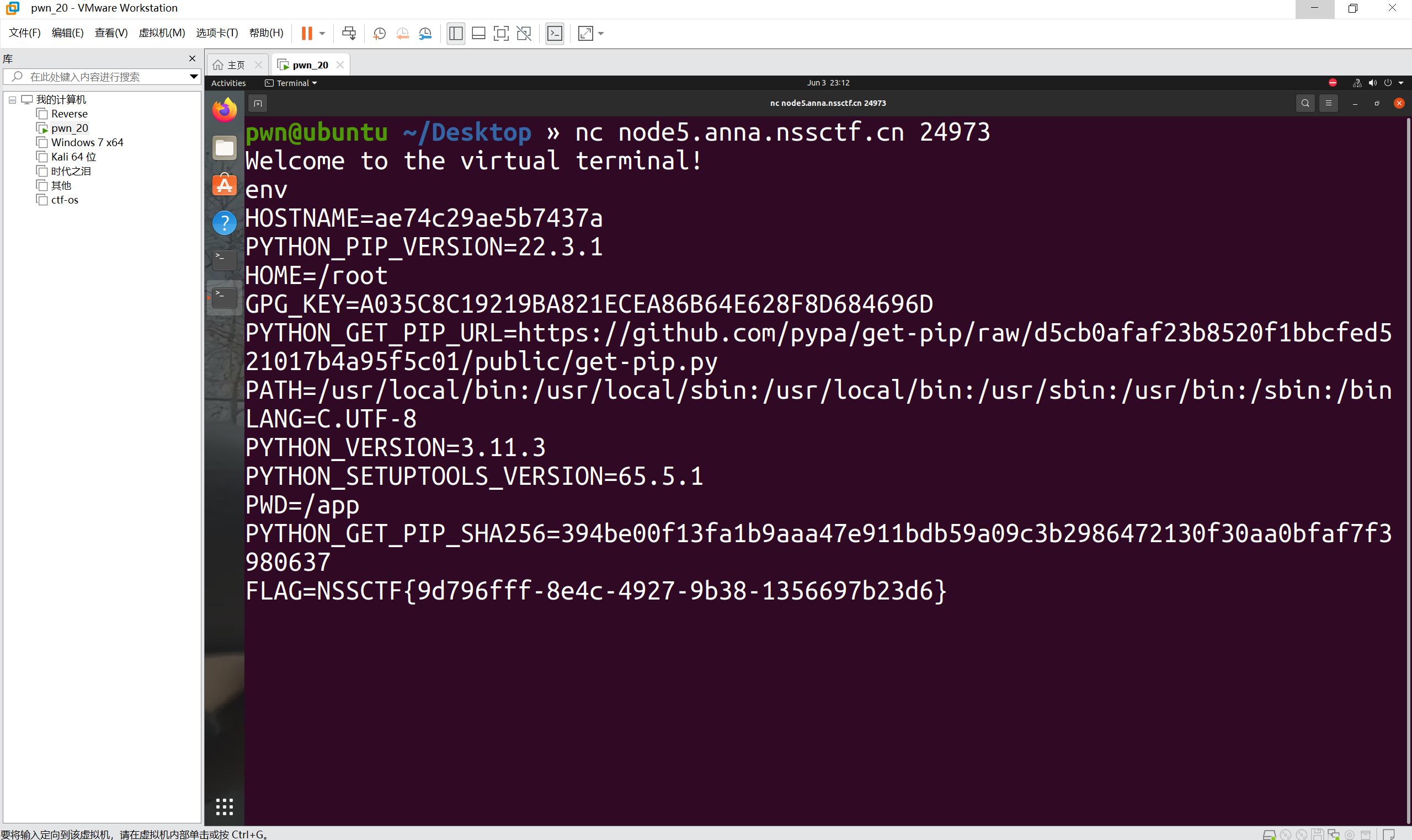
最后flag为
1 | NSSCTF{9d796fff-8e4c-4927-9b38-1356697b23d6} |
[LitCTF 2023]口算题卡
题目描述:
1 | 来点小学生喜欢的x 不会算错吧? |
nc连接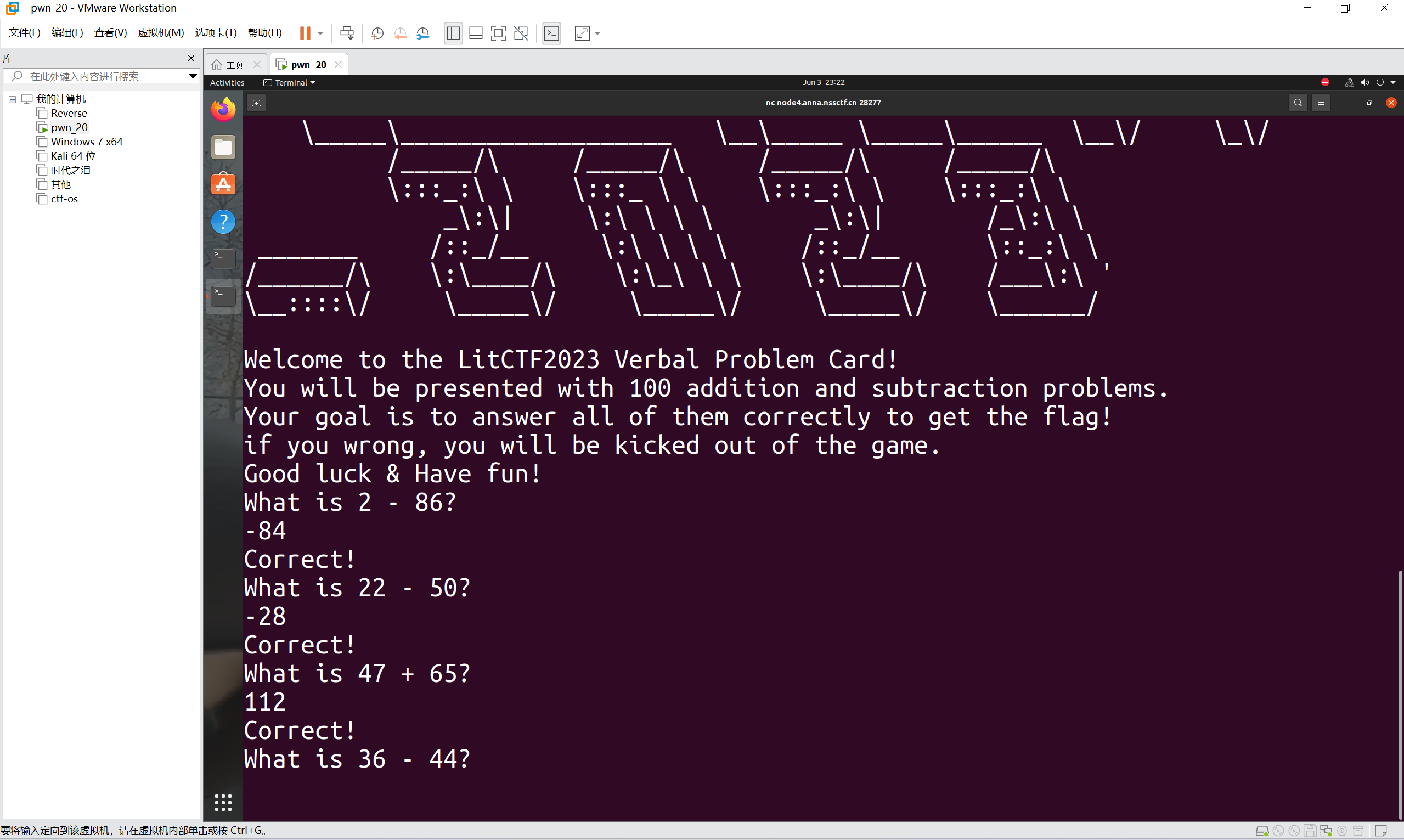
口算题
做完100道加减法题目后就可以得到Flag
直接使用pwntools库进行交互
exp:
1 | from pwn import * |
运行得到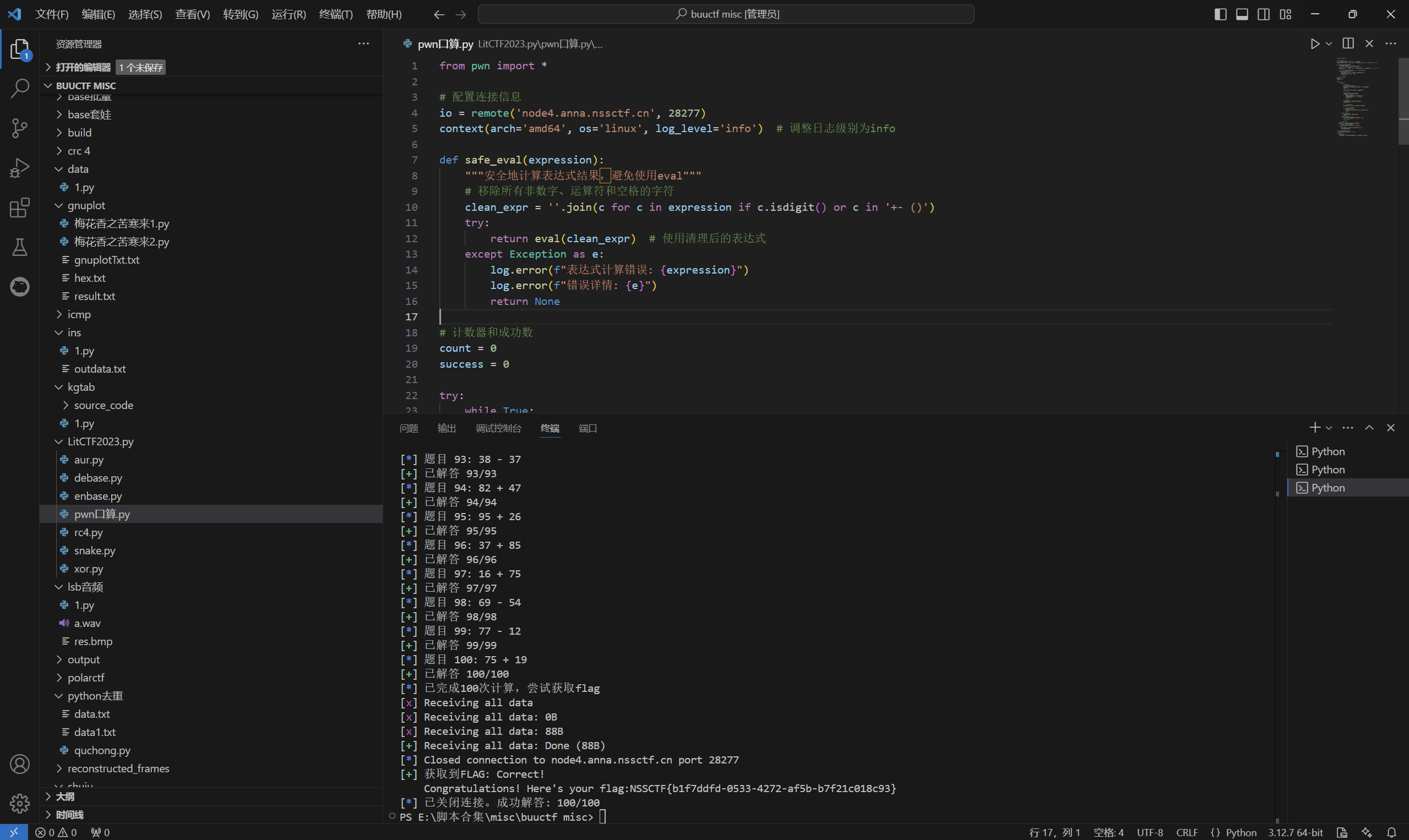
最后flag为
1 | NSSCTF{b1f7ddfd-0533-4272-af5b-b7f21c018c93} |
[LitCTF 2023]狠狠的溢出涅~
ret2libc题目
exp:
1 | from pwn import * |
运行得到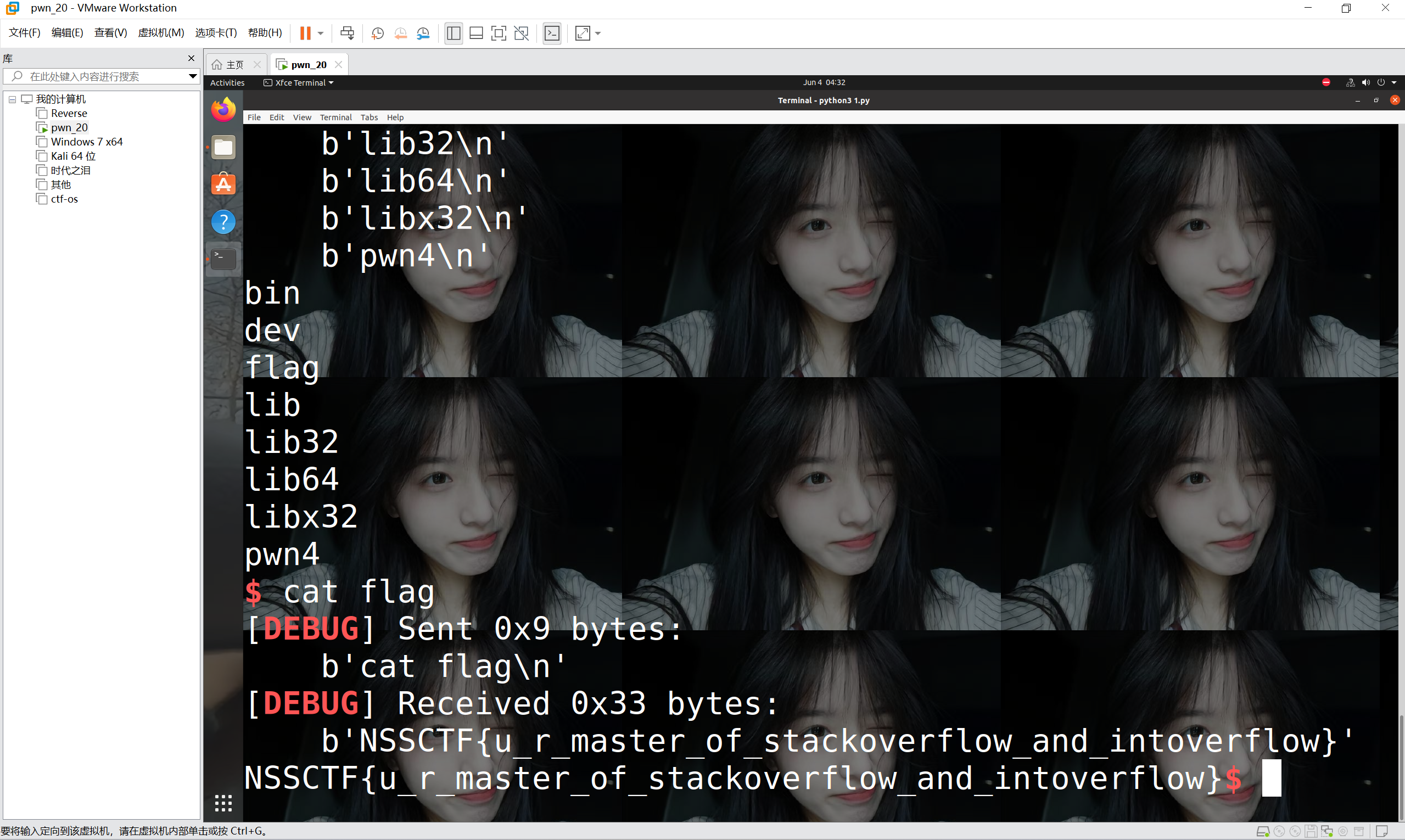
最后flag为
1 | NSSCTF{u_r_master_of_stackoverflow_and_intoverflow} |
[LitCTF 2023]ezlogin
\x00截断
exp:
1 | #!/bin/env python3 |
运行得到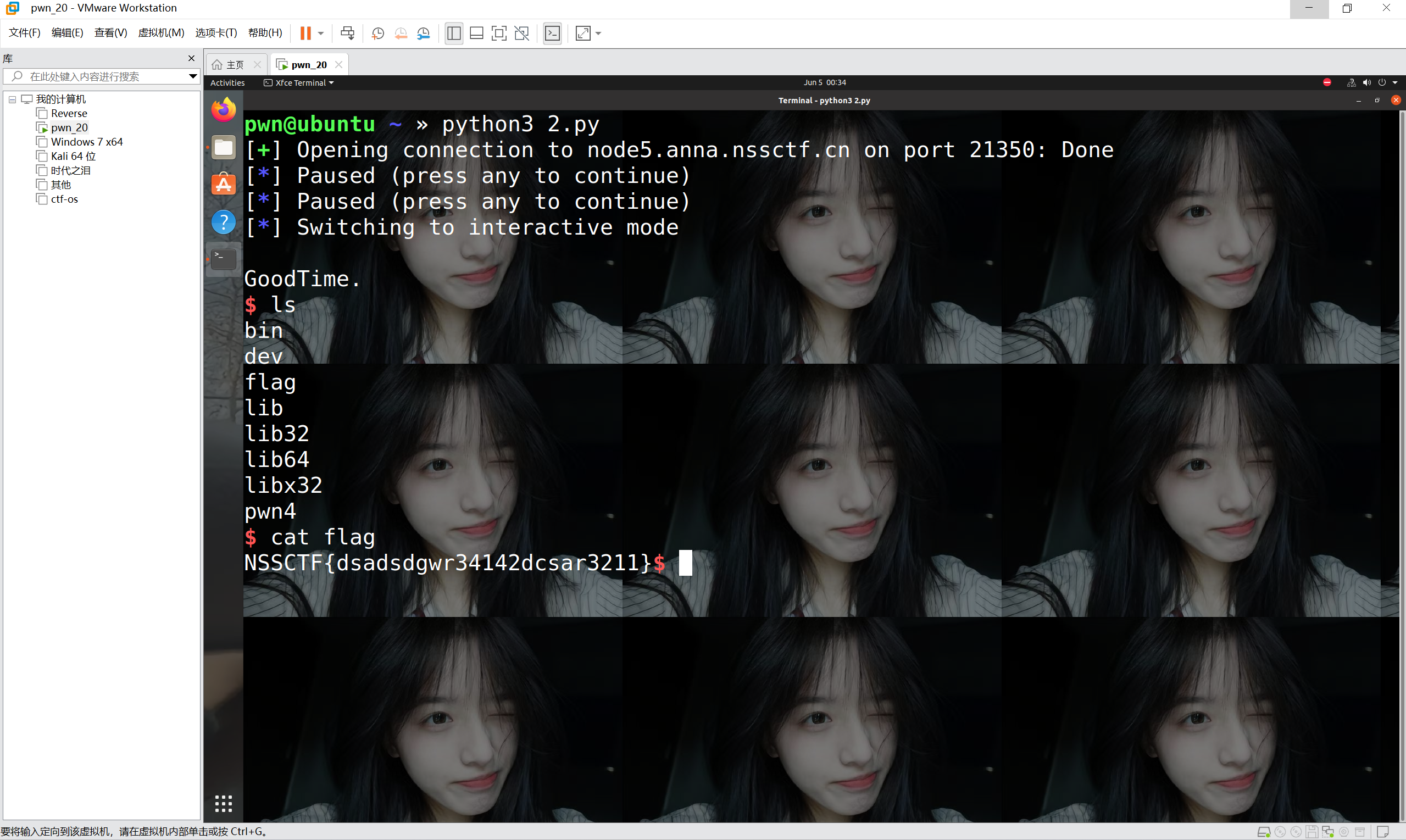
最后flag为
1 | NSSCTF{dsadsdgwr34142dcsar3211} |



