[LitCTF 2023]世界上最棒的程序员
下载附件
运行文件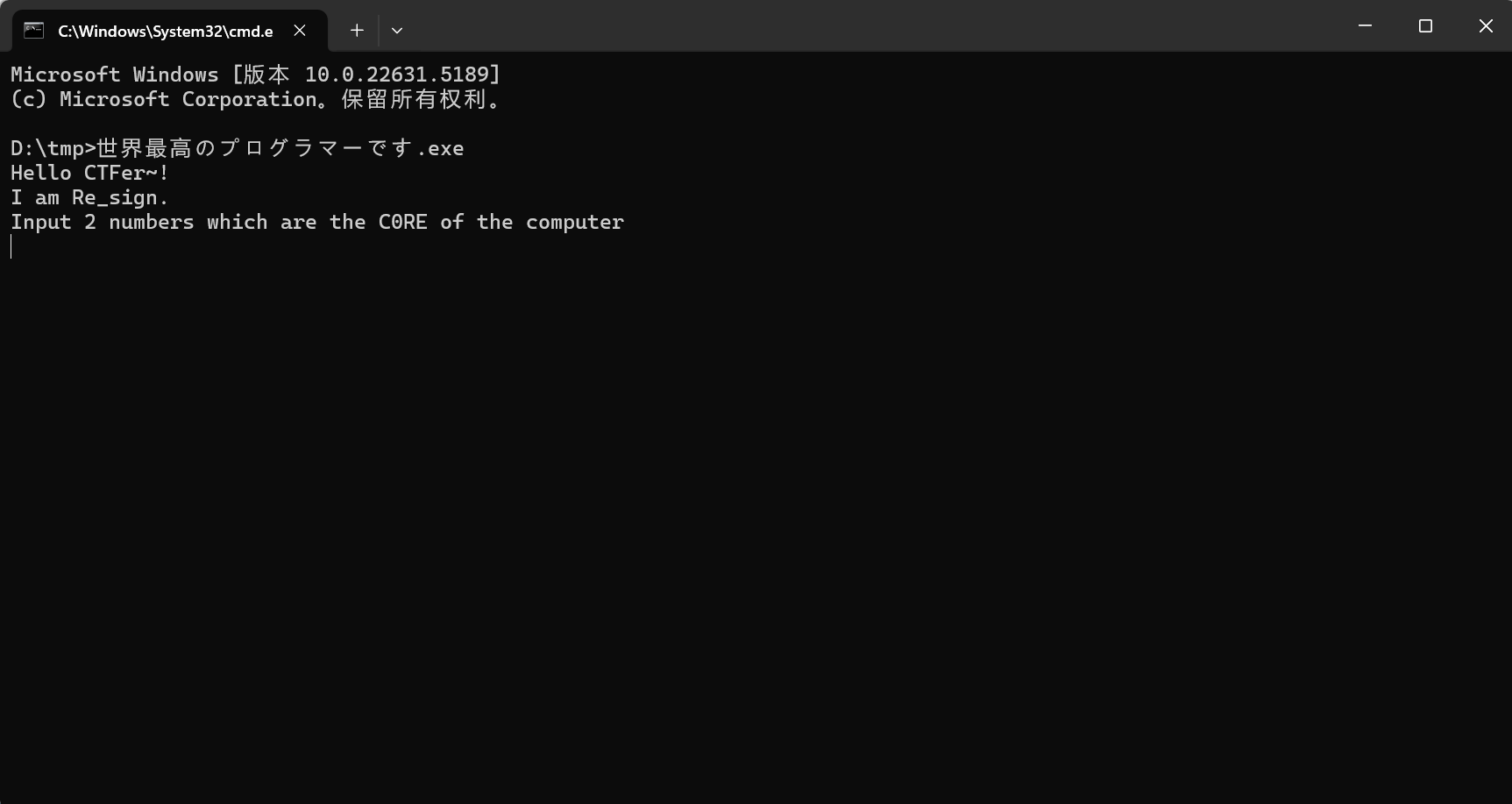
查壳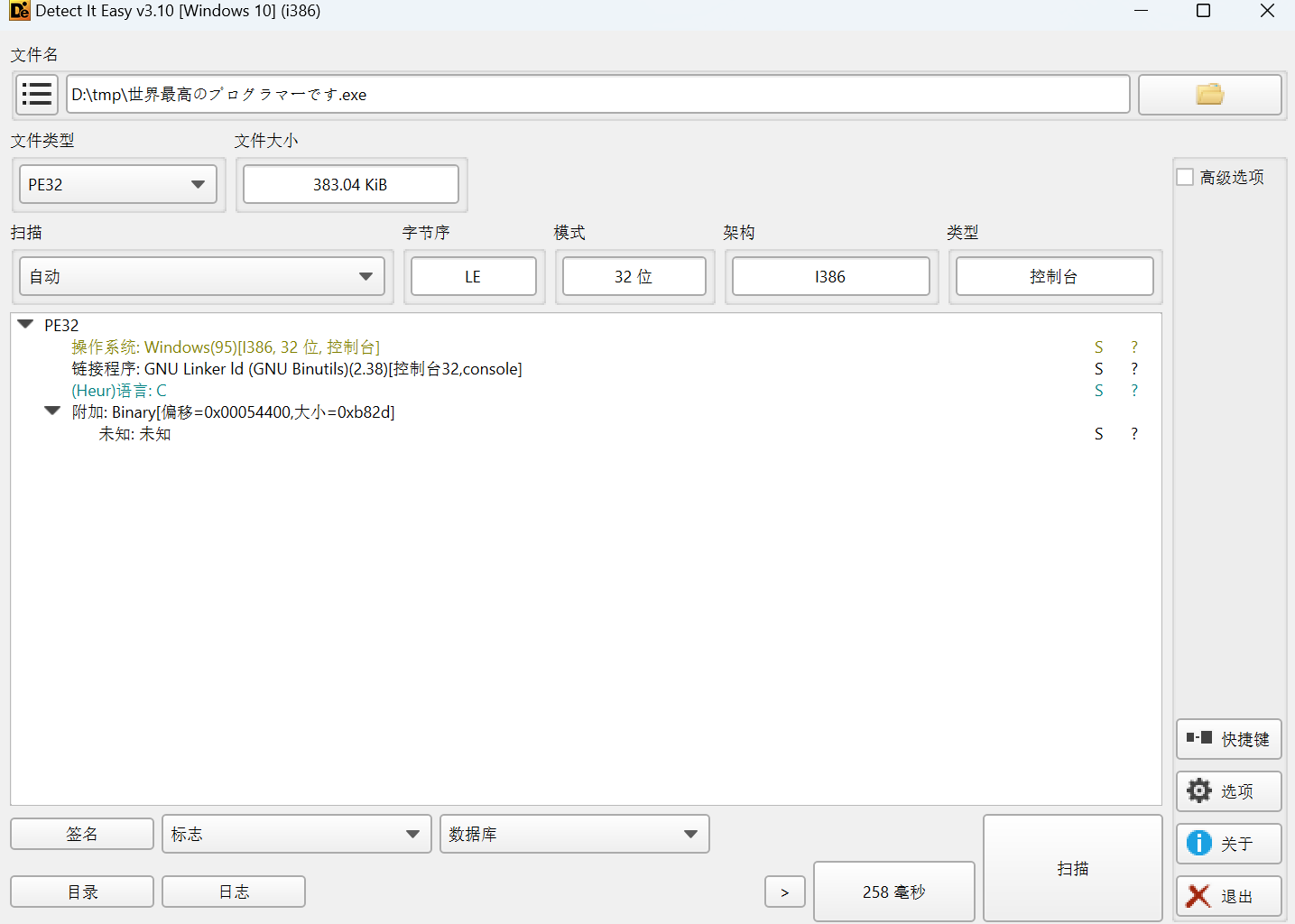
32位
IDA32载入文件,F5快捷键查看主函数main的伪代码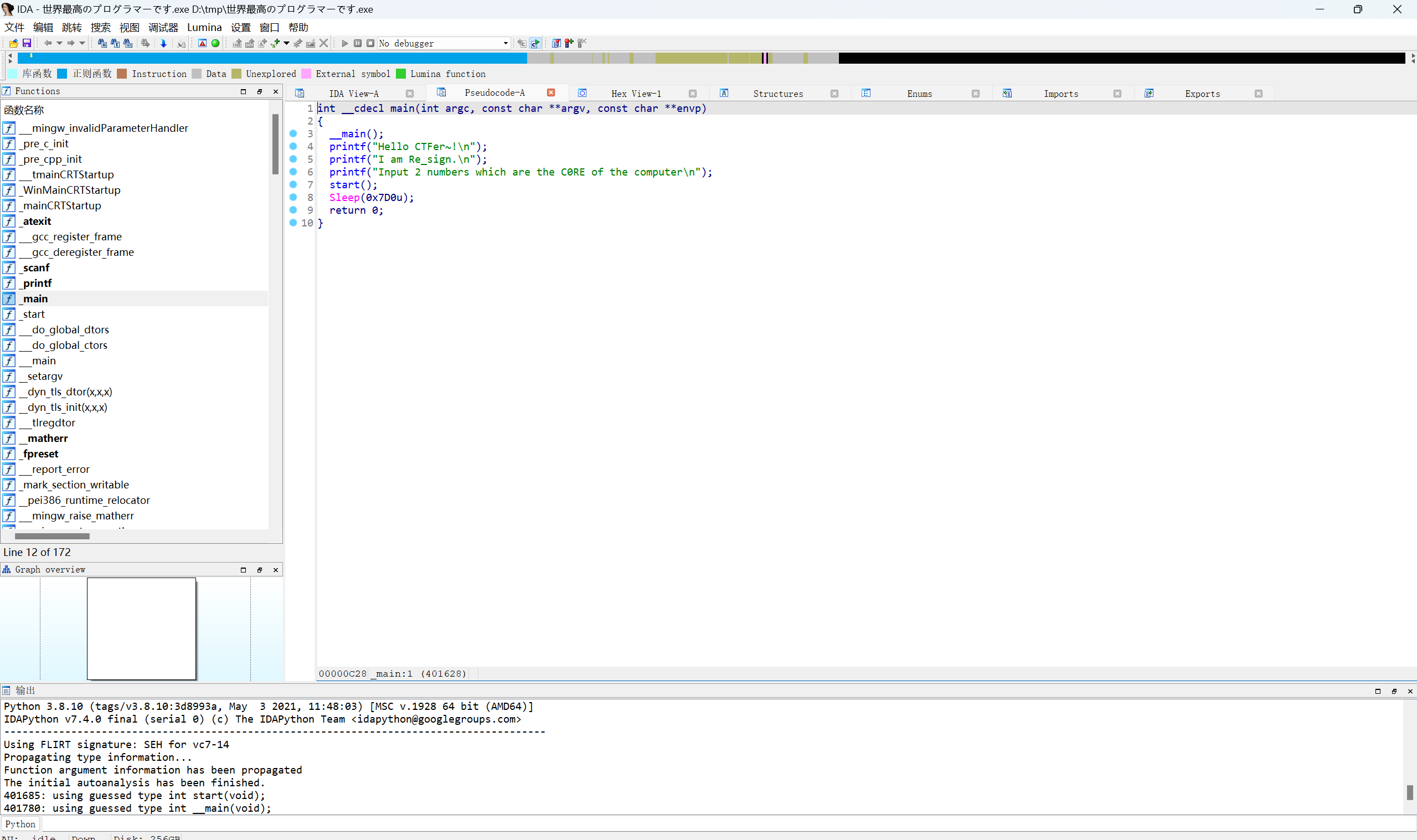
得到关键逻辑代码
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
跟进start函数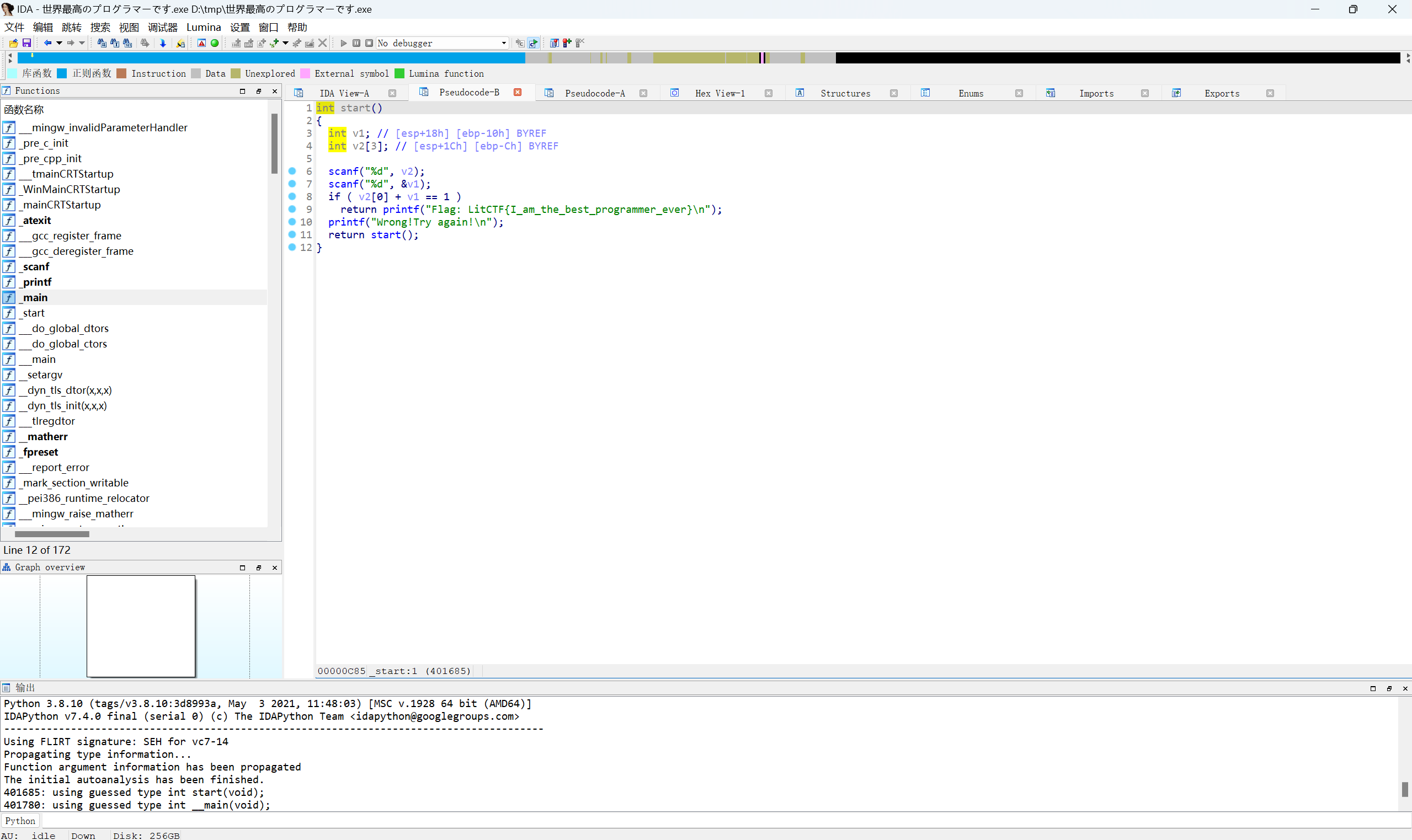
得到关键代码以及flag
1 | int start() |
代码大致意思是让用户输入两个整数,使得它们的和等于 1。如果满足条件,程序会输出 flag,否则会提示错误并递归调用自身重新开始
满足条件如下
1 | 0+1=1 |
以第一个为例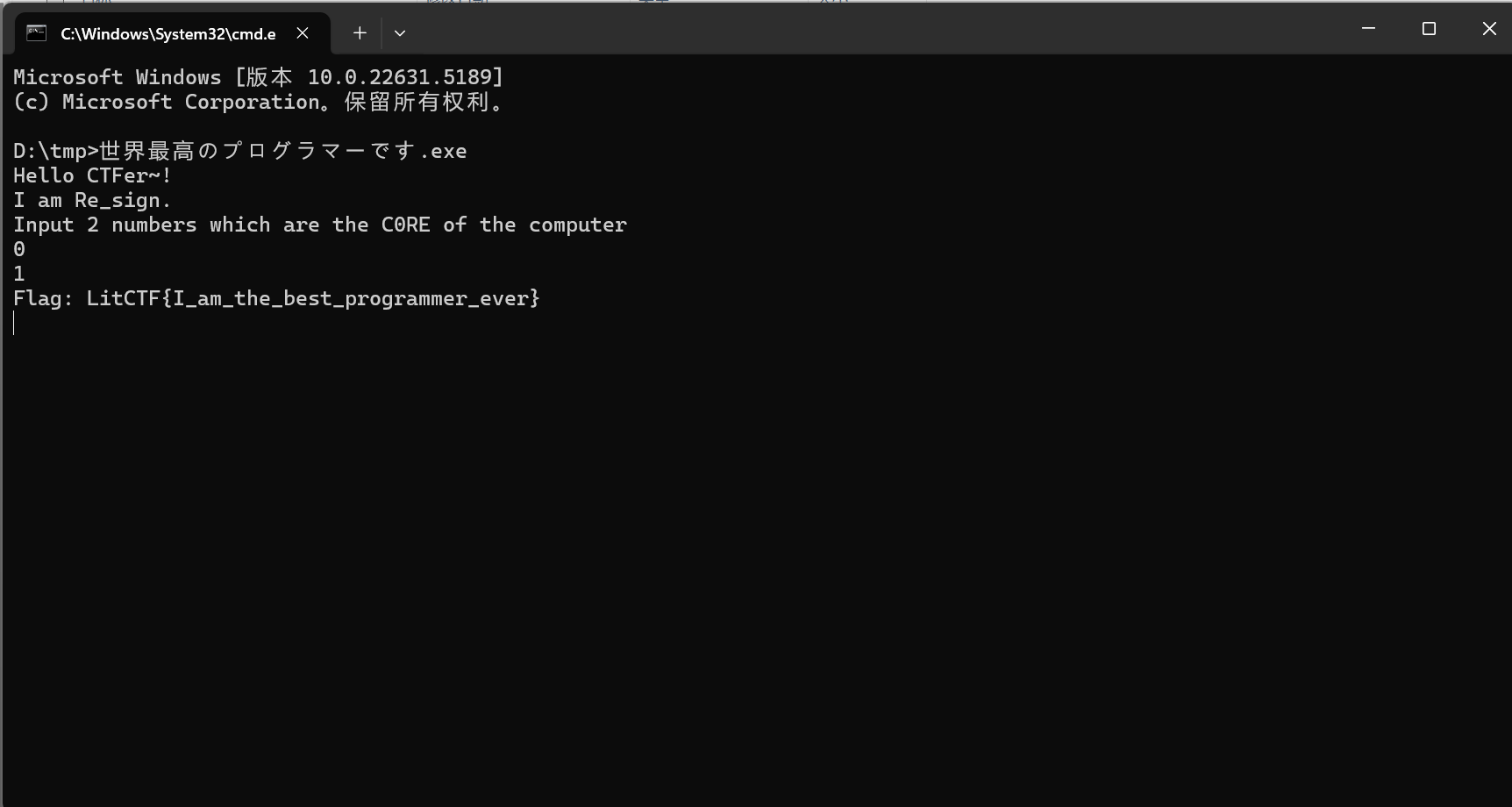
查看字符串也可以拿到flag
快捷键:shift+F12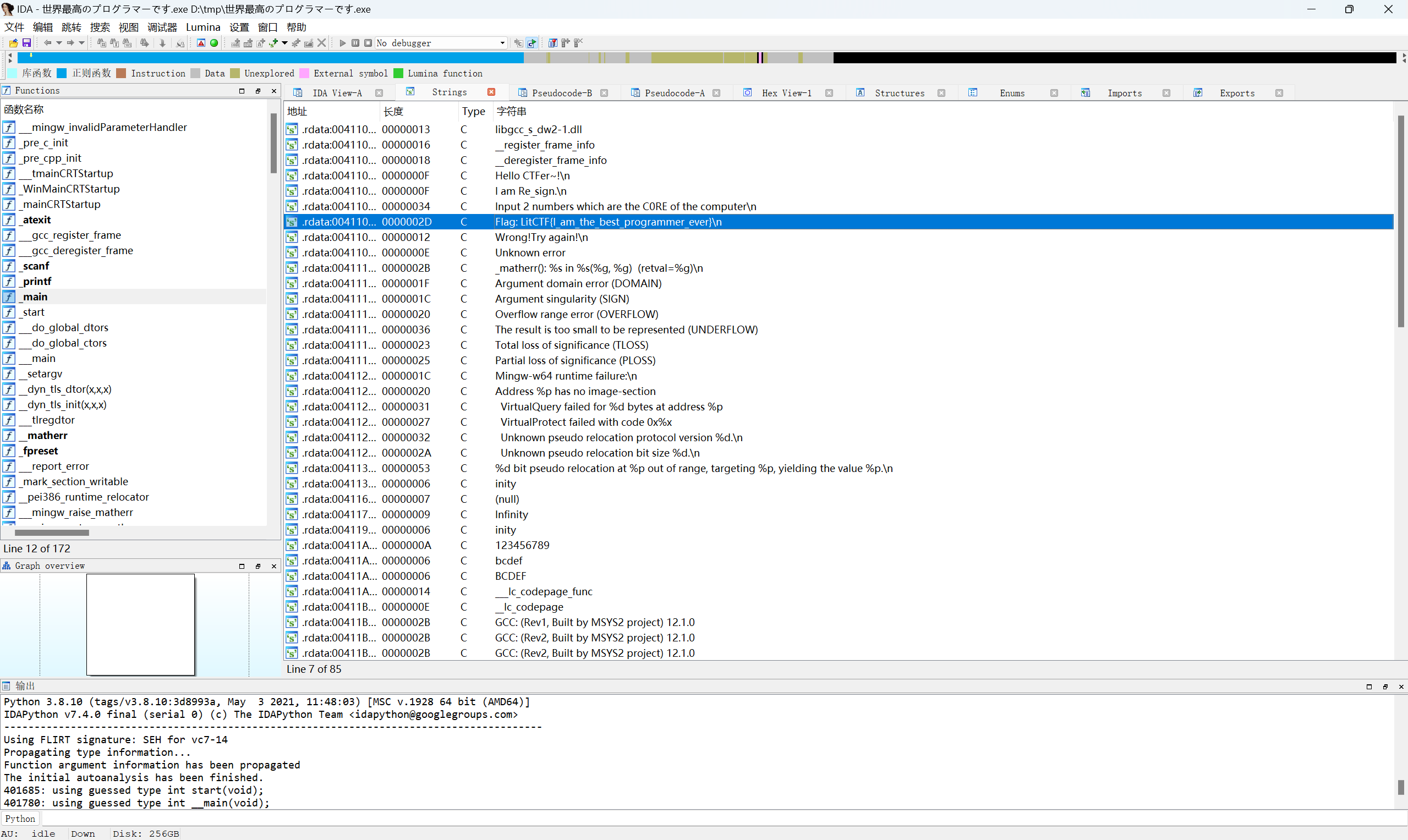
最后flag为
1 | LitCTF{I_am_the_best_programmer_ever} |
[LitCTF 2023]ez_XOR
下载附件
运行文件
需要我们输入正确的flag进行判断是否正确
查壳
32位
IDA32载入文件,F5快捷键查看主函数main的伪代码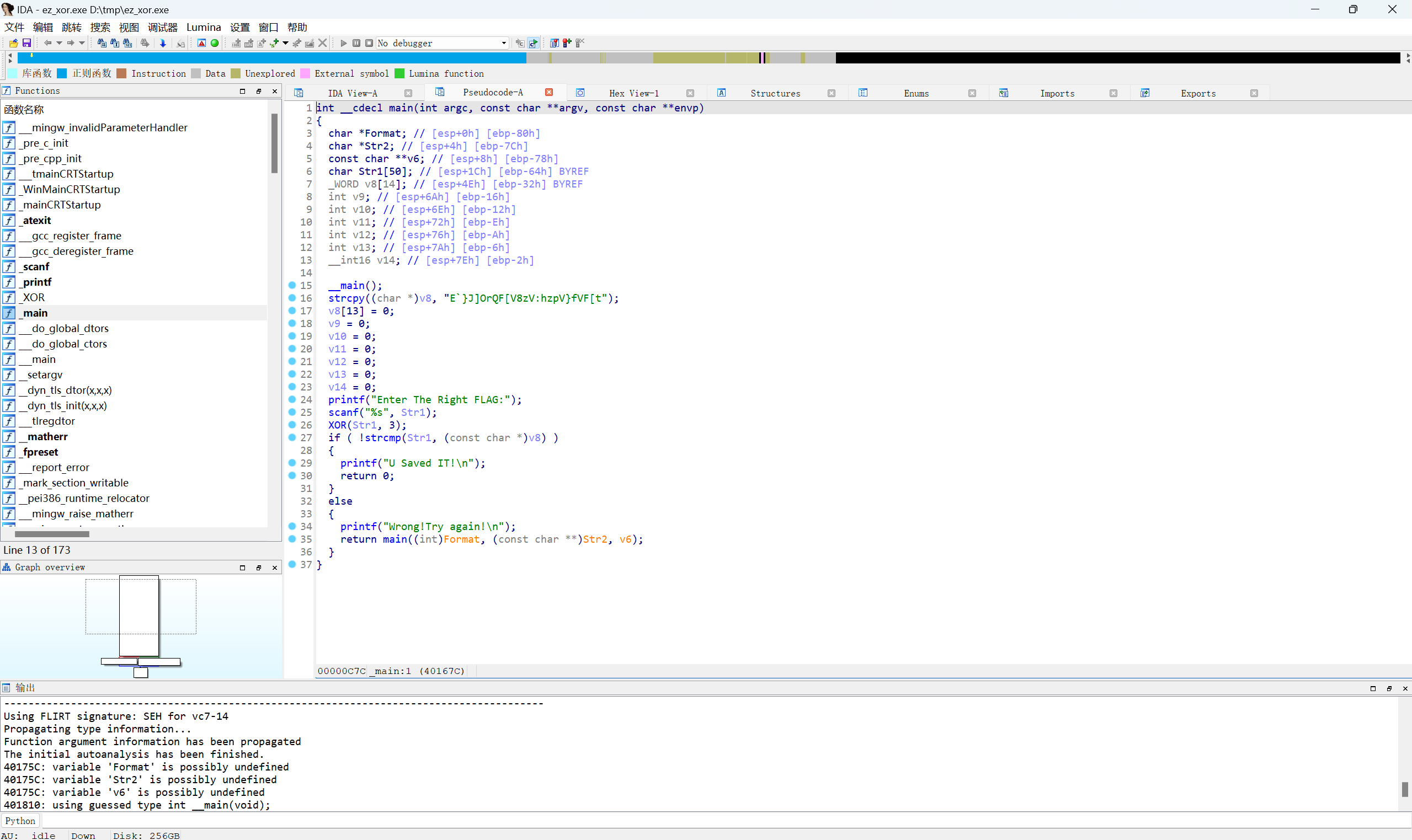
得到关键代码
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
关键在这
1 | XOR(Str1, 3); |
跟进XOR函数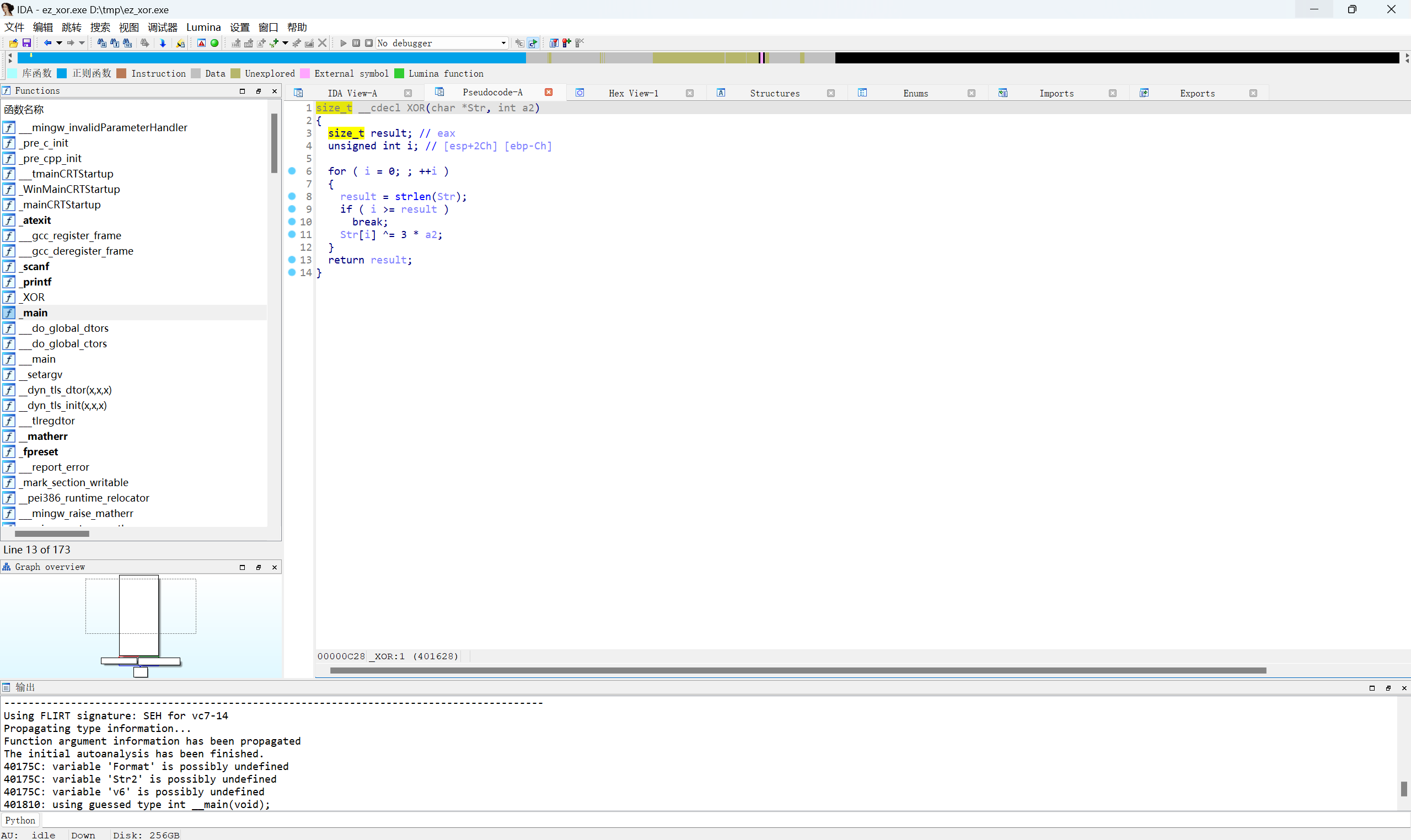
关键代码
1 | size_t __cdecl XOR(char *Str, int a2) |
传入的参数,3就是函数内的a2,字符串逐个与(3*a2)异或,也就是和9进行XOR
exp:
1 | a = b'E`}J]OrQF[V8zV:hzpV}fVF[t' |
运行得到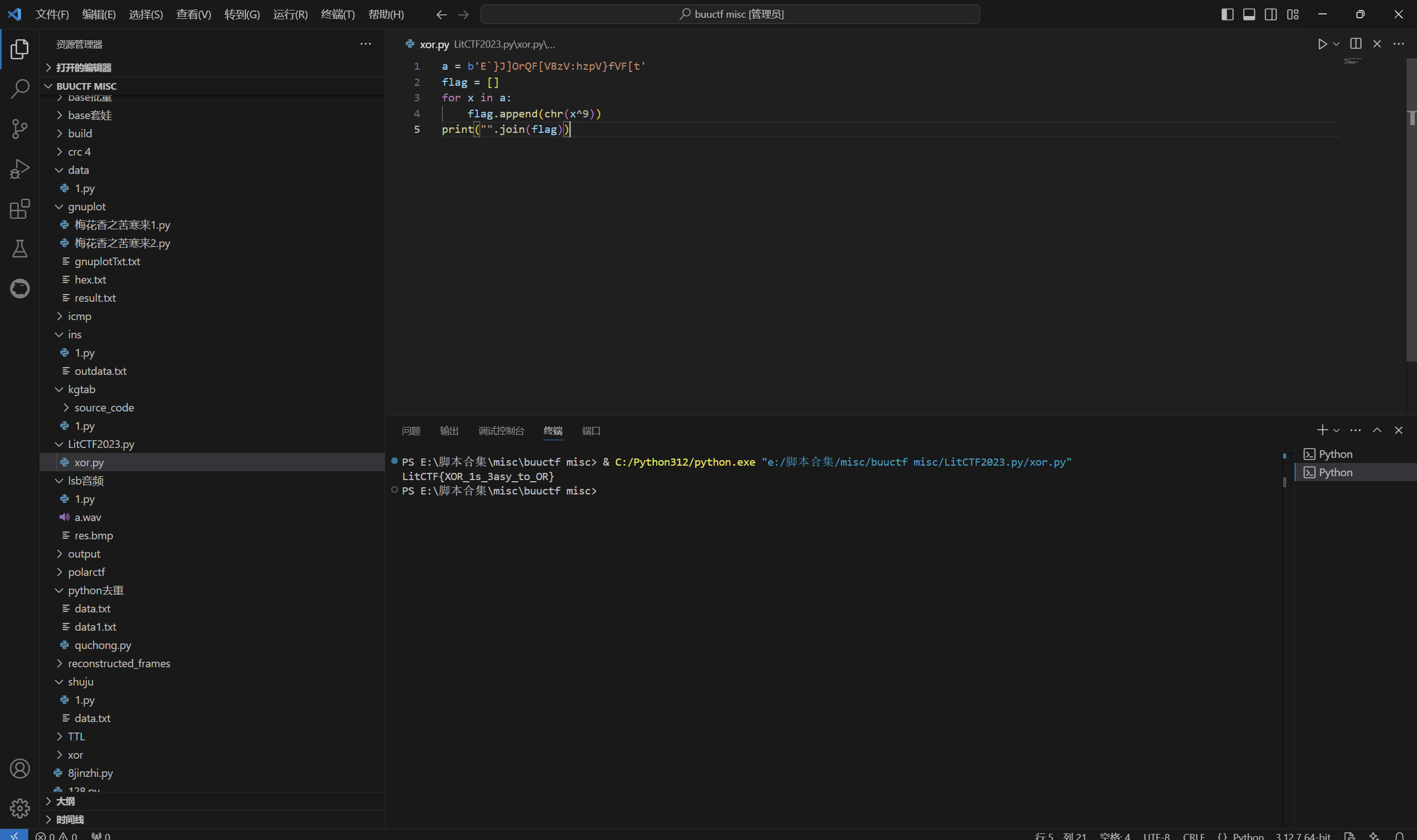
也可以直接赛博厨子一把梭
最后flag为
1 | LitCTF{XOR_1s_3asy_to_OR} |
[LitCTF 2023]enbase64
下载附件
运行文件
报错了,显示libgcc_s_dw2-1.dll缺失,下载一个libgcc_s_dw2-1.dll文件复制到这个文件的下边
运行文件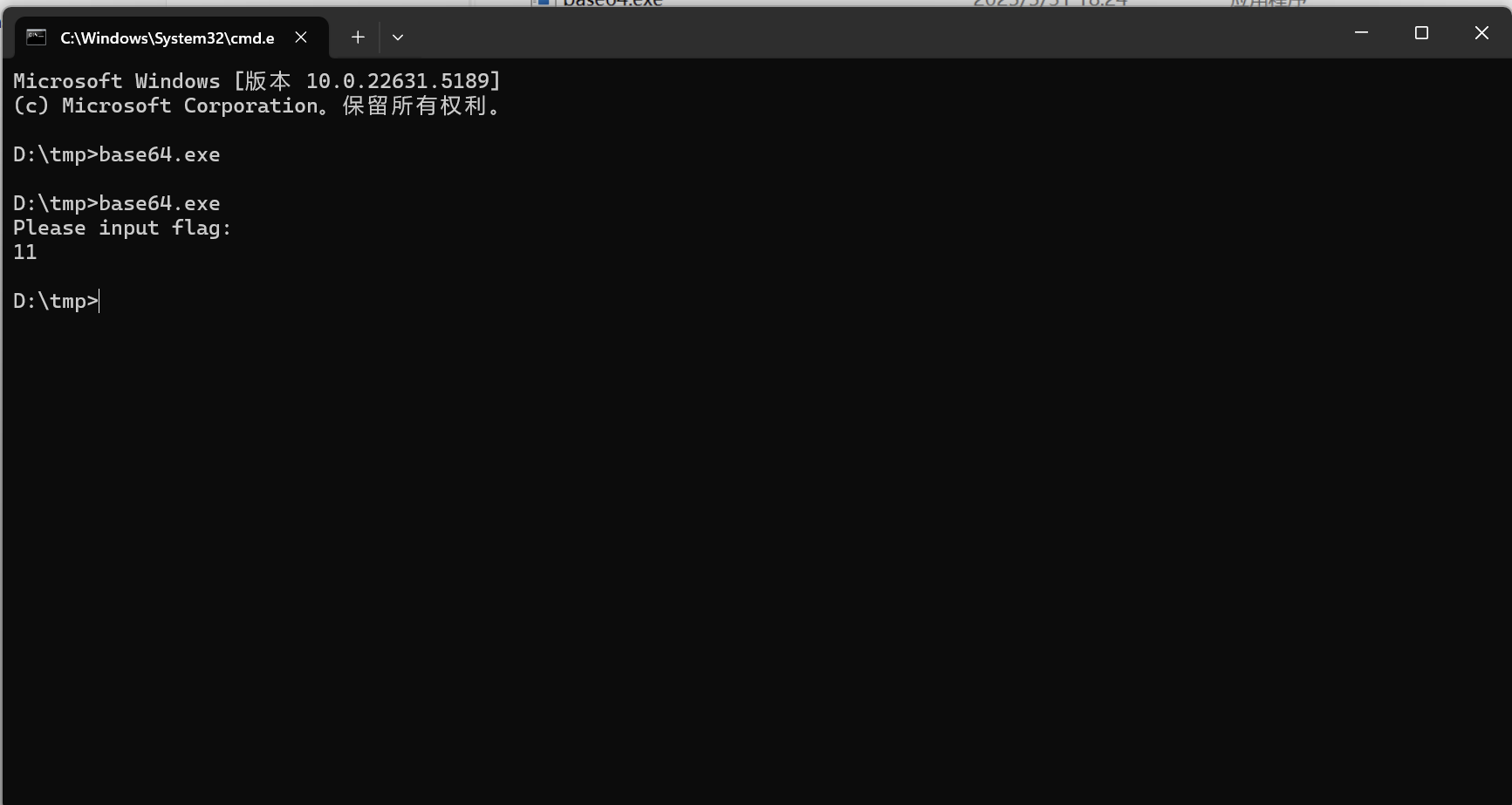
需要我们输入正确的flag判断是否正确
查壳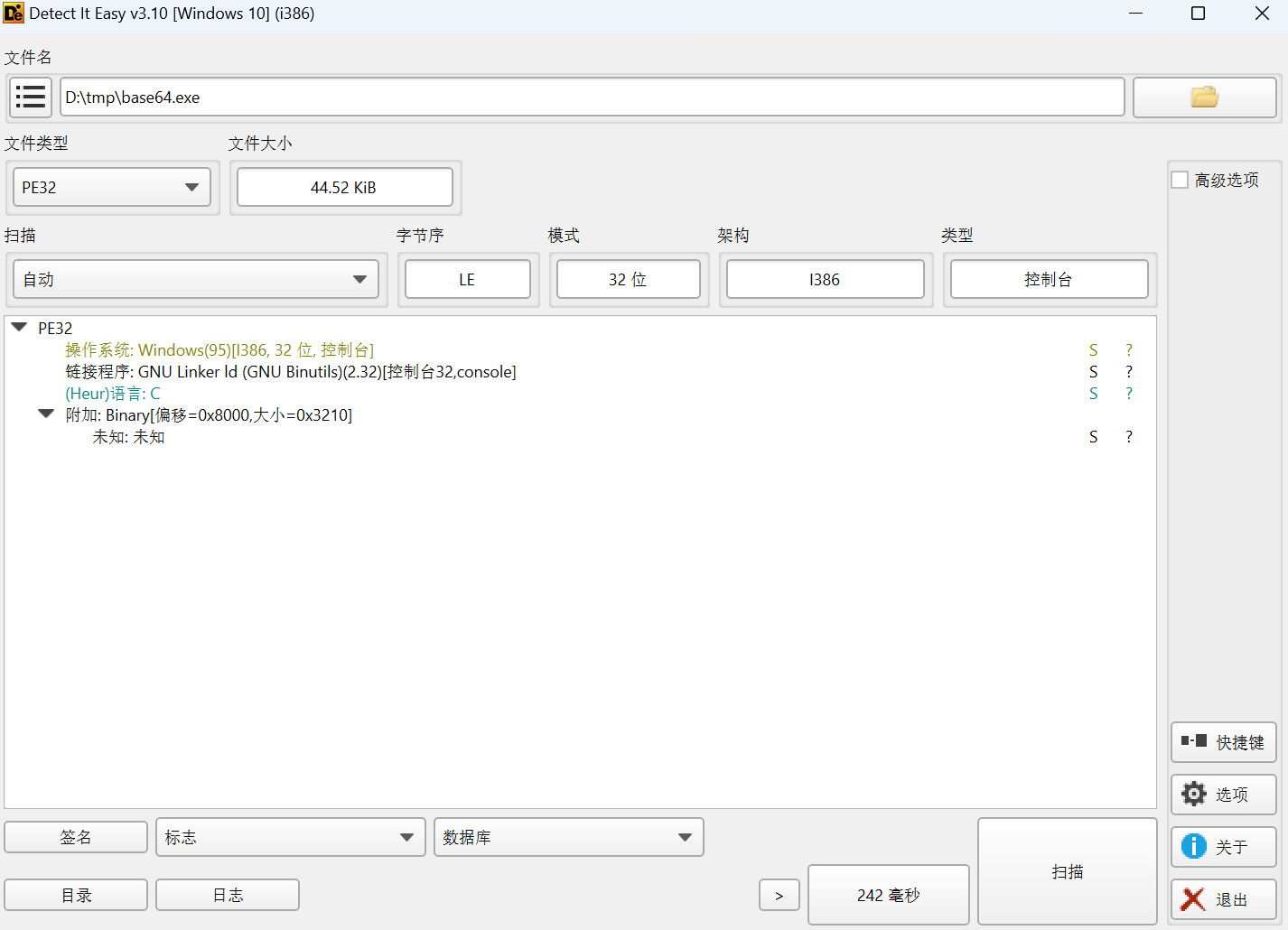
32位
ida载入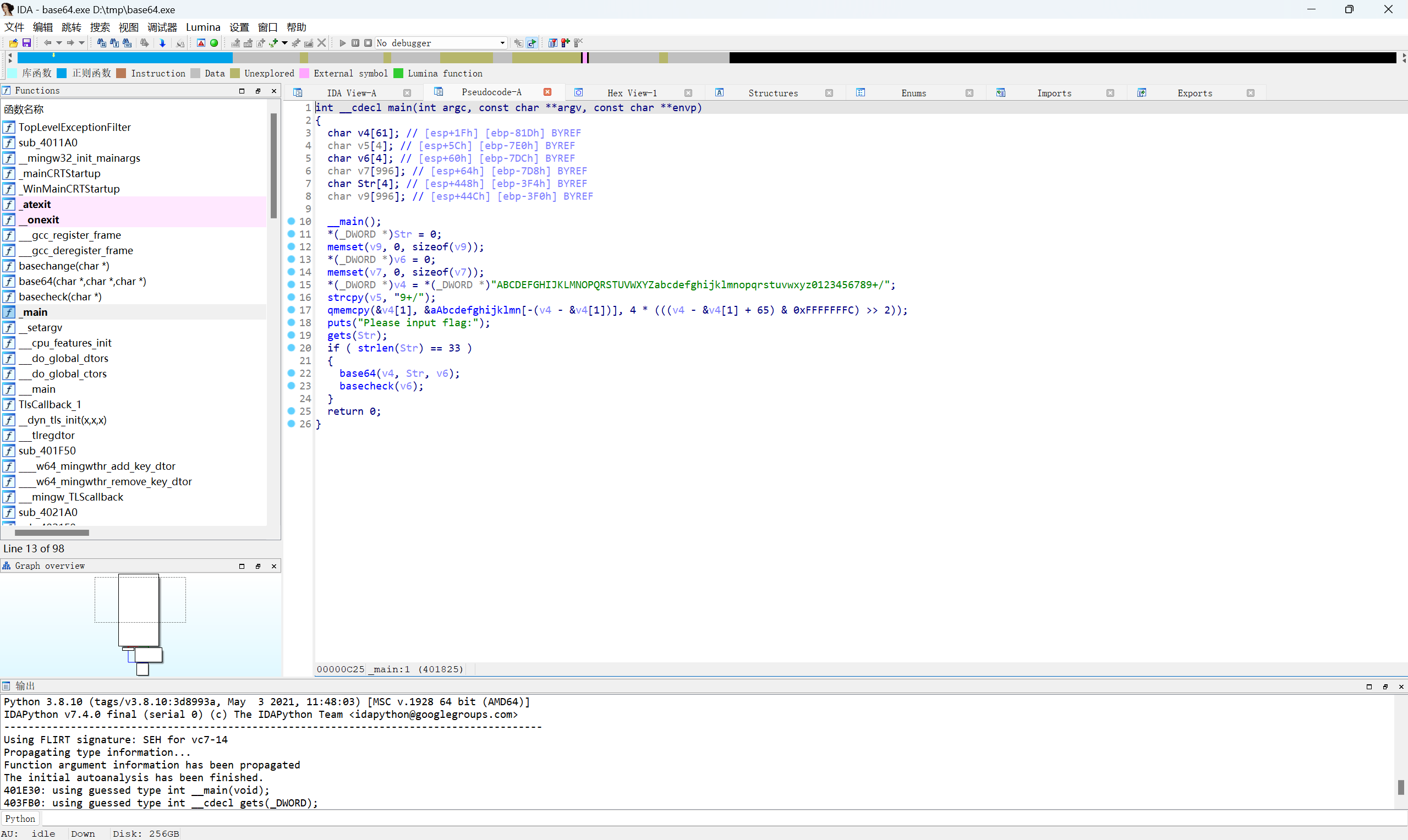
很明显的base加密特征
1 | if ( strlen(Str) == 33 ) |
输入长度为33
跟进base函数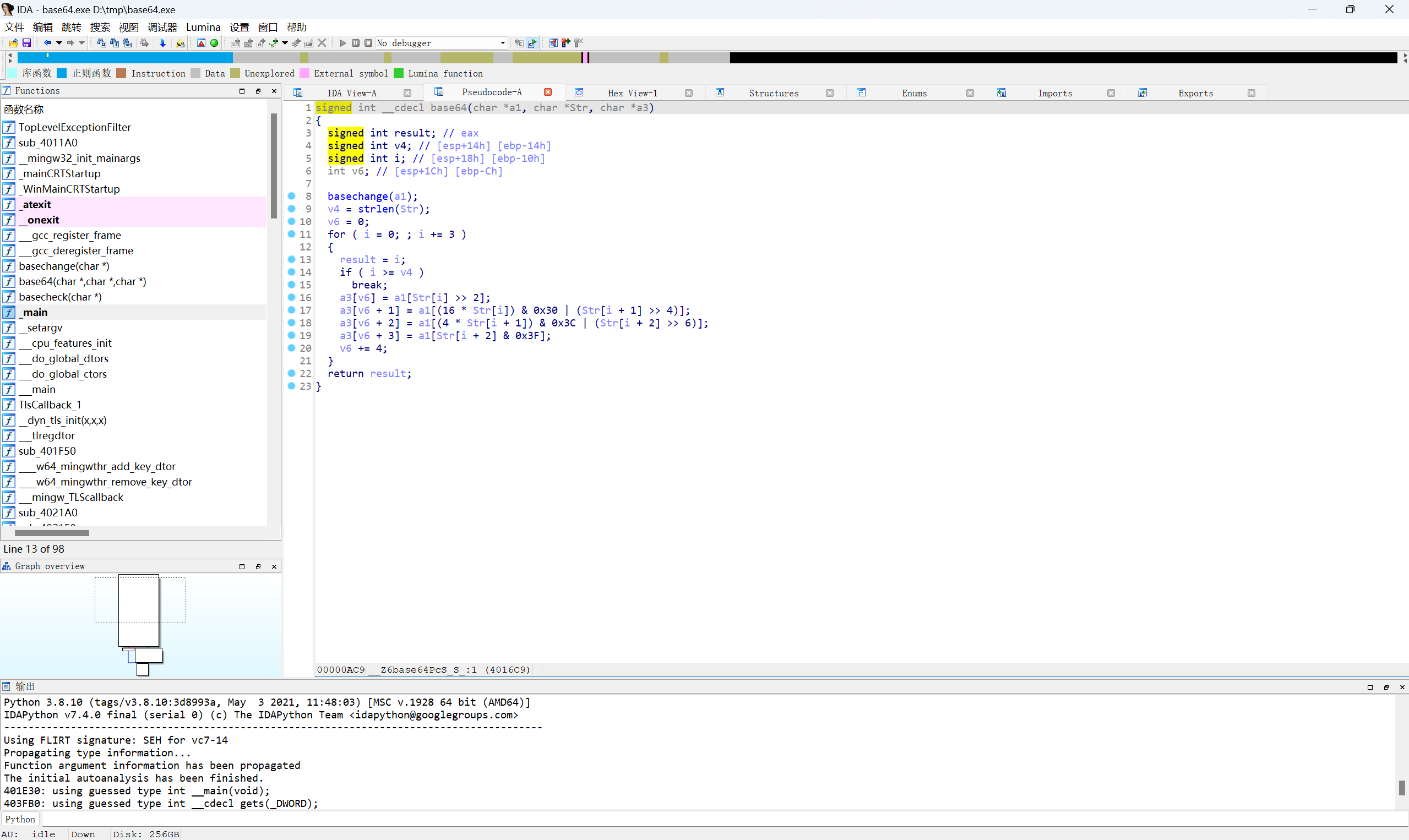
发现是对表进行了处理,进行basechange函数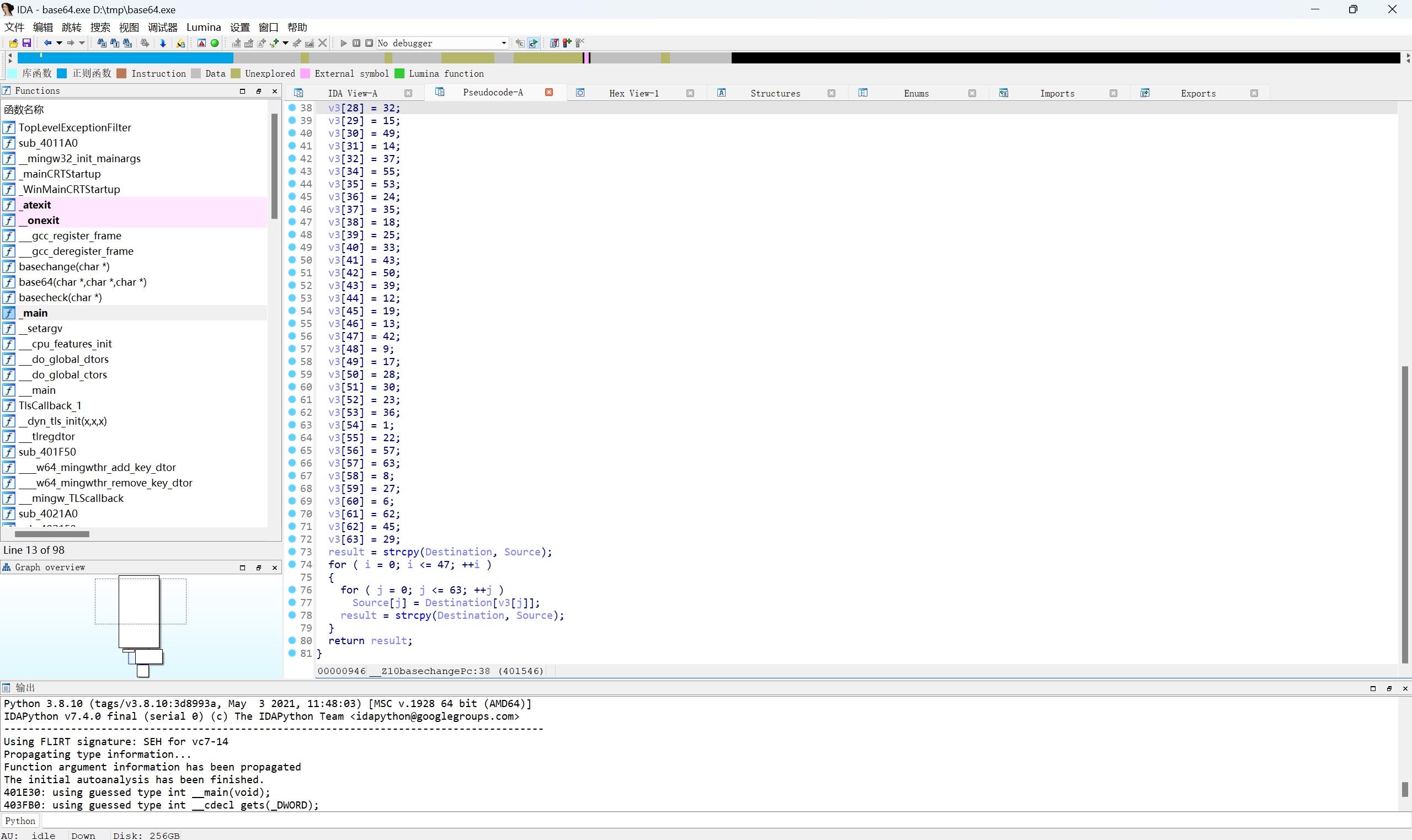
发现换表换了48次
base换表需要找到码表
IDA动态调试
首先下断点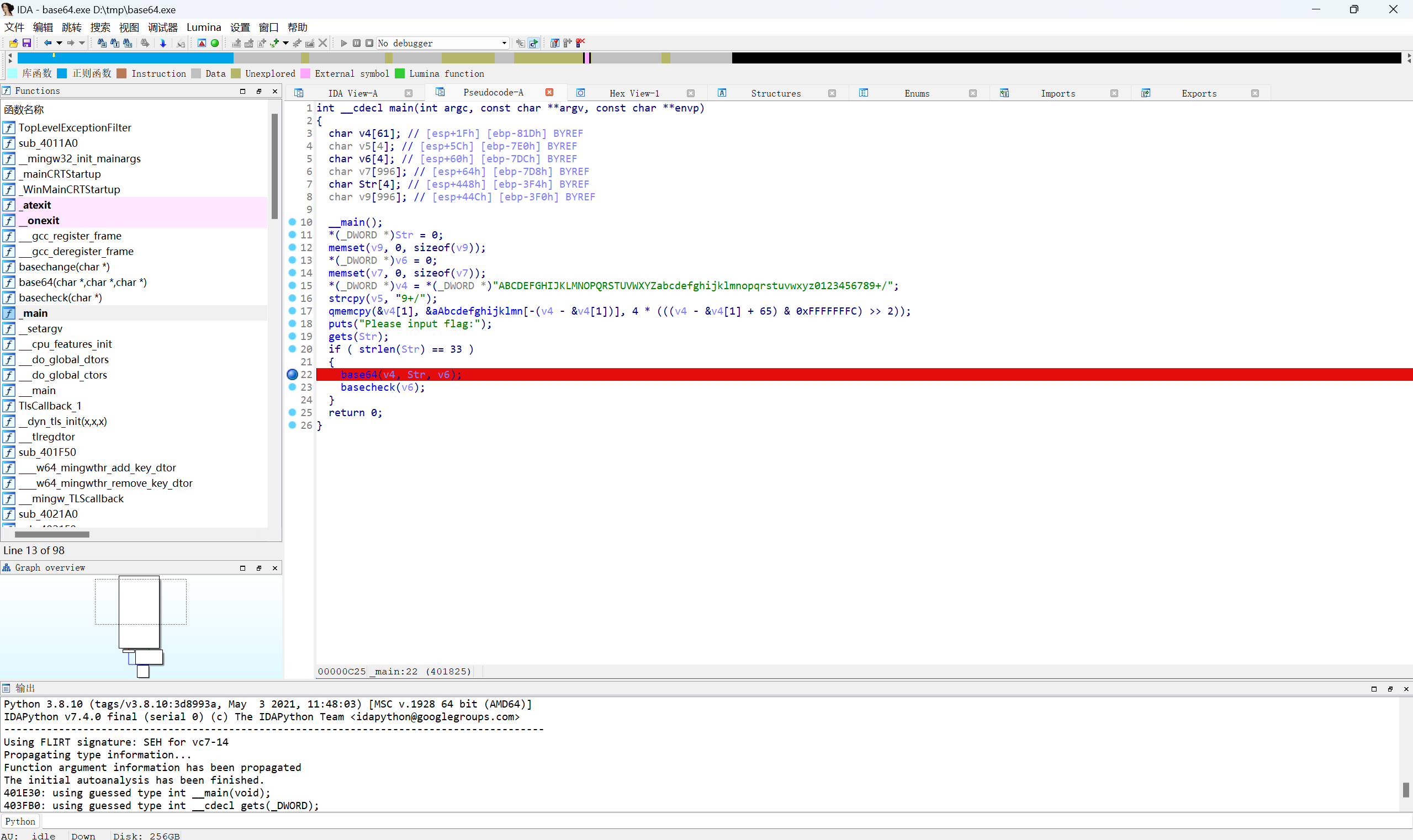
Local Windows debugger调试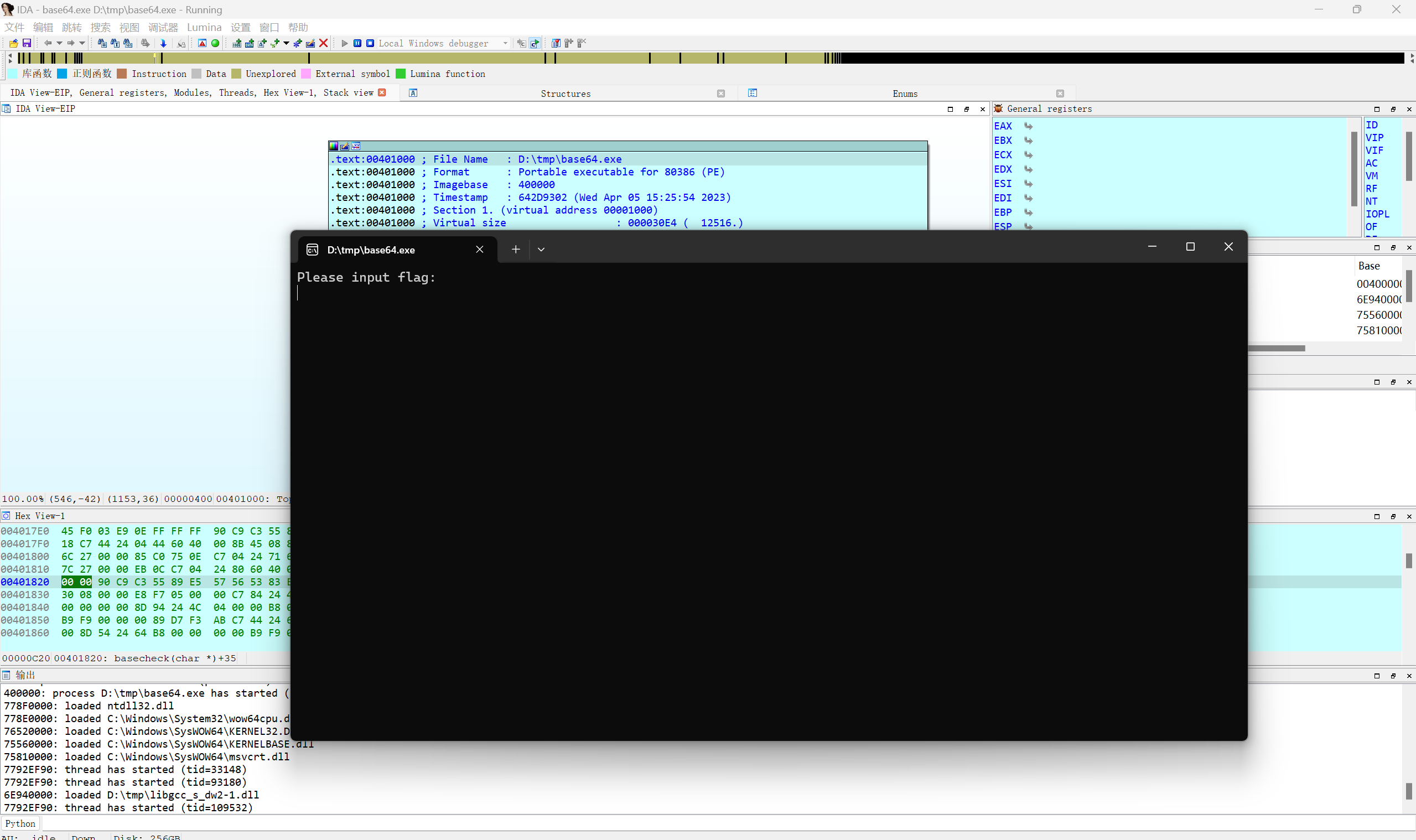
输入33个字符
1 | aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa |
跟进base函数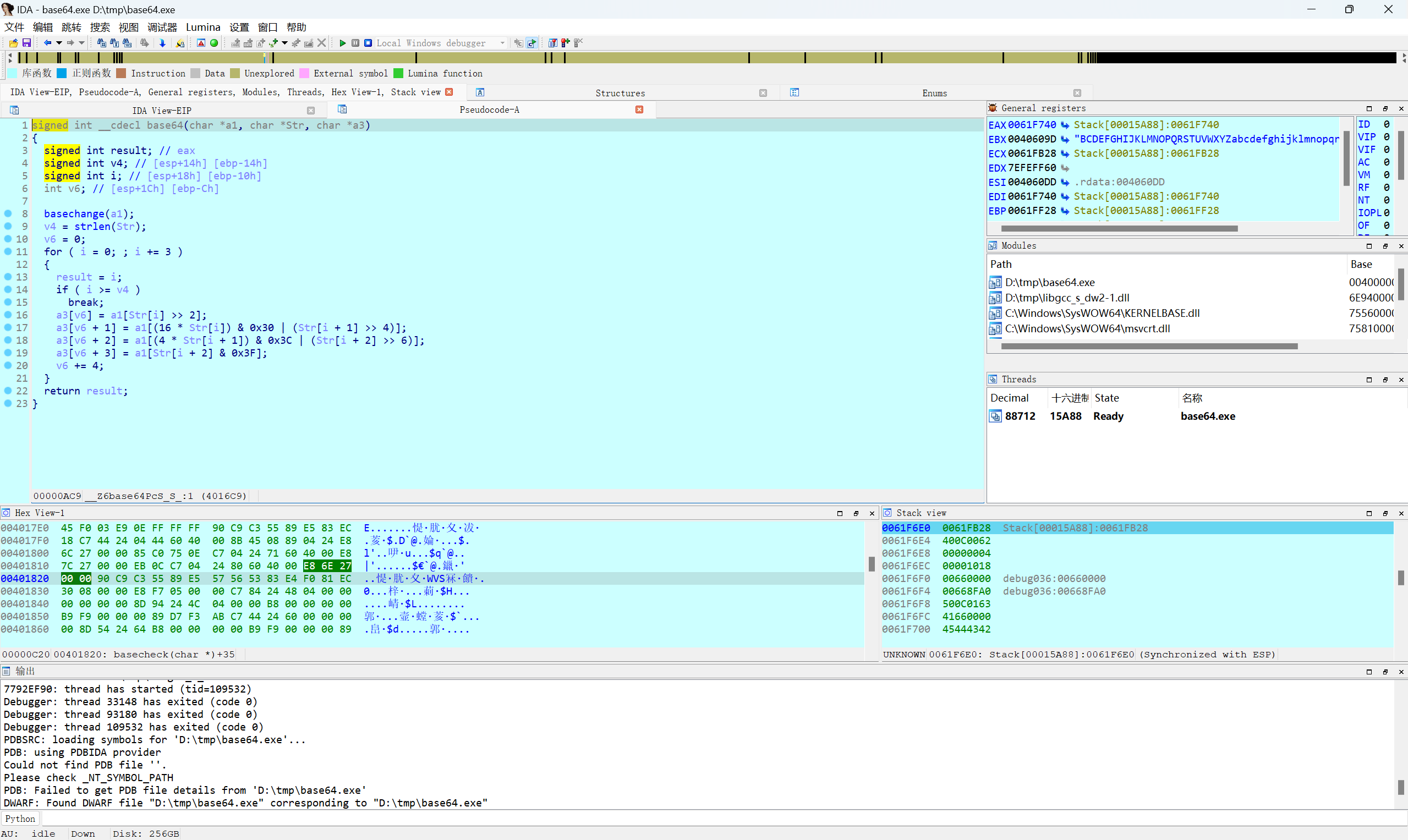
F8 单步步过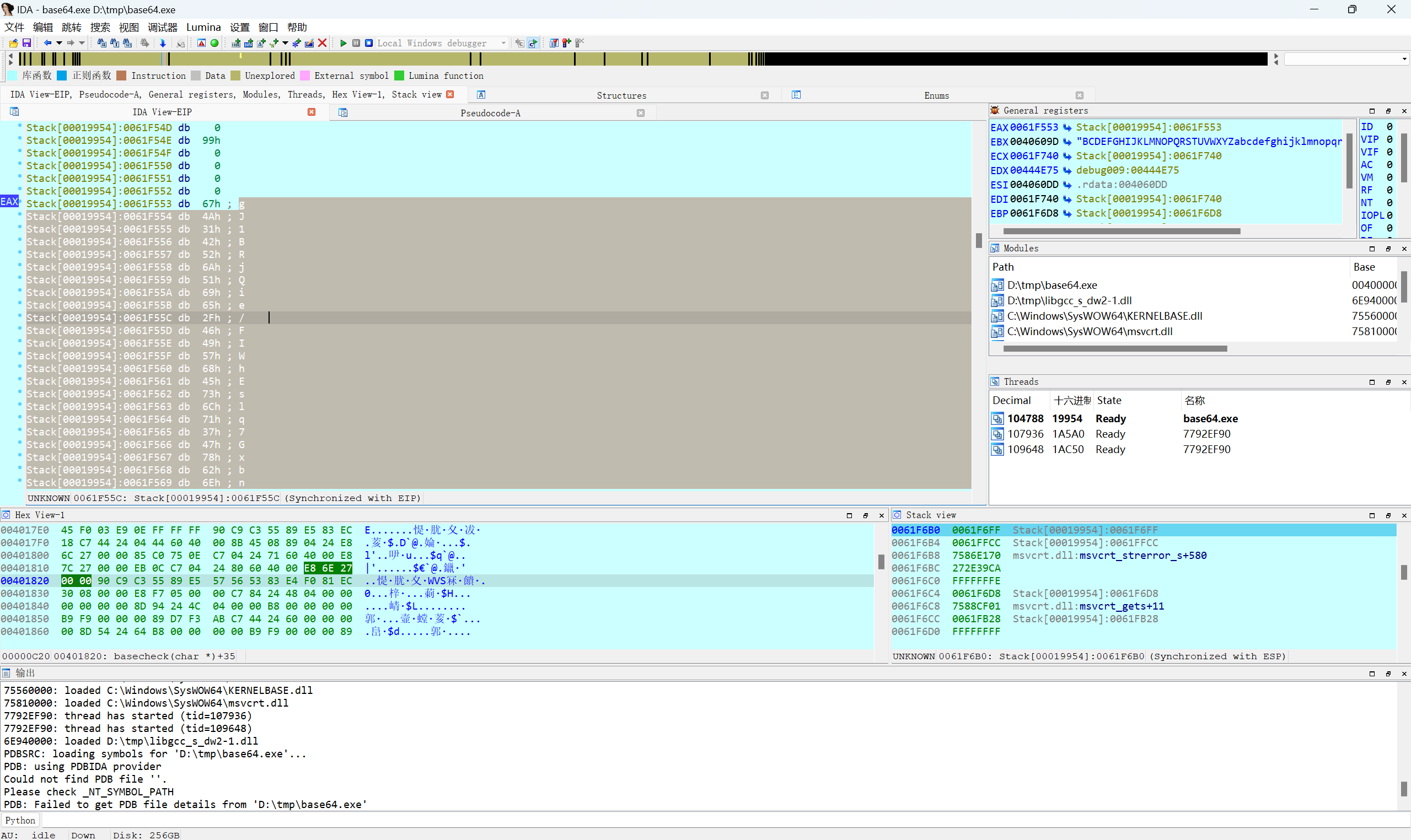
shift+e提取字符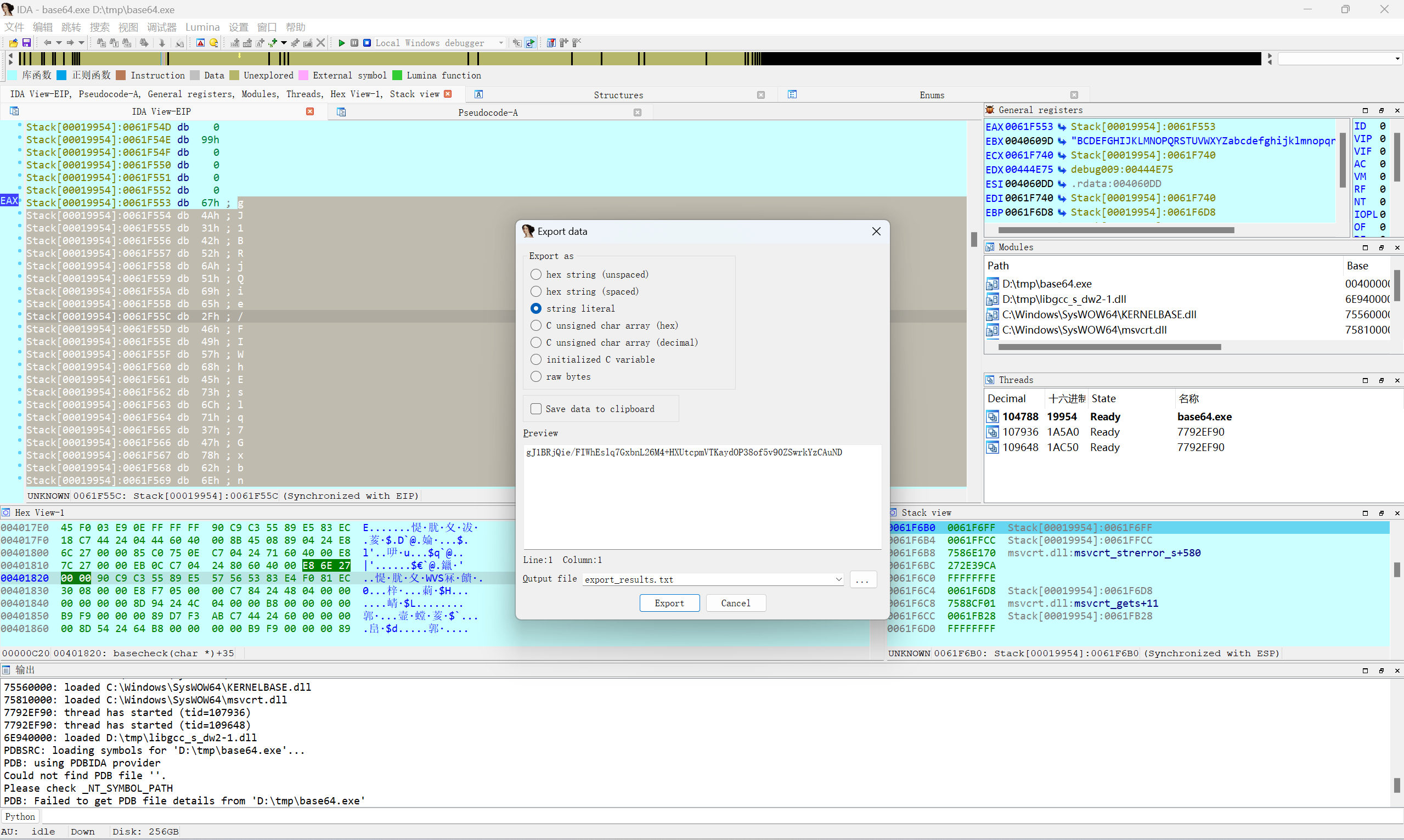
得到
1 | gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuND |
找到密文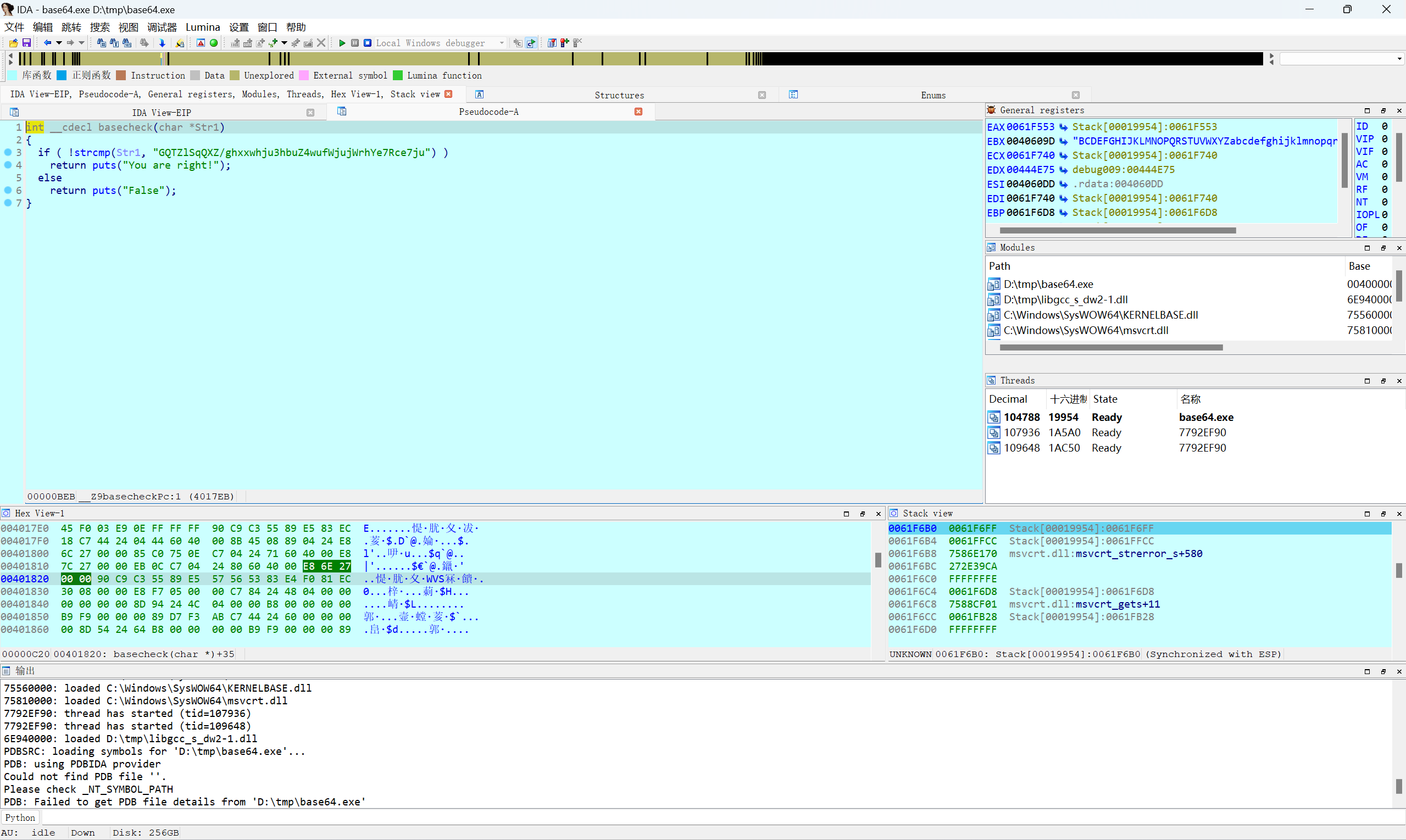
得到
1 | GQTZlSqQXZ/ghxxwhju3hbuZ4wufWjujWrhYe7Rce7ju |
base换表
exp:
1 | import base64 |
运行得到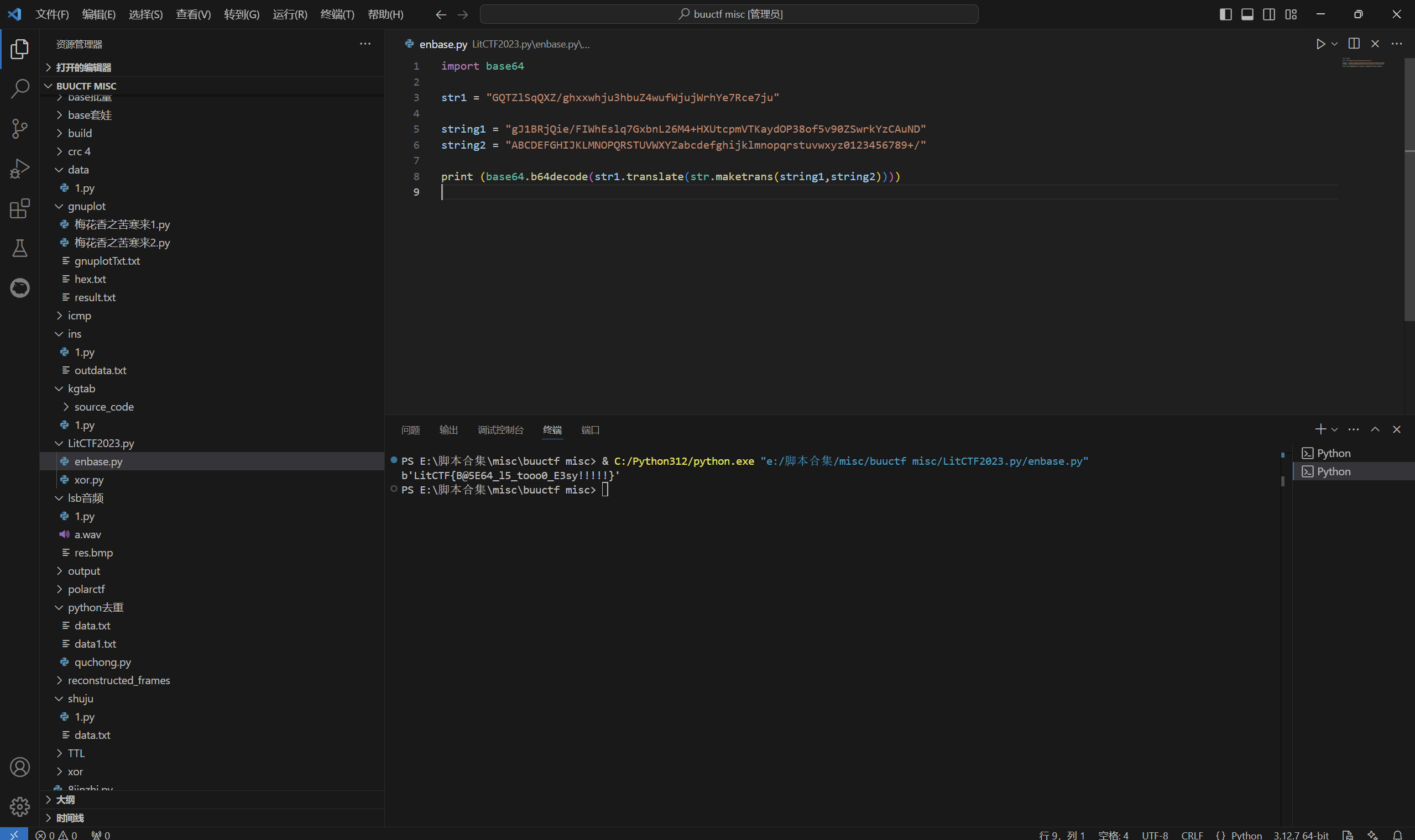
也可以赛博厨子一把梭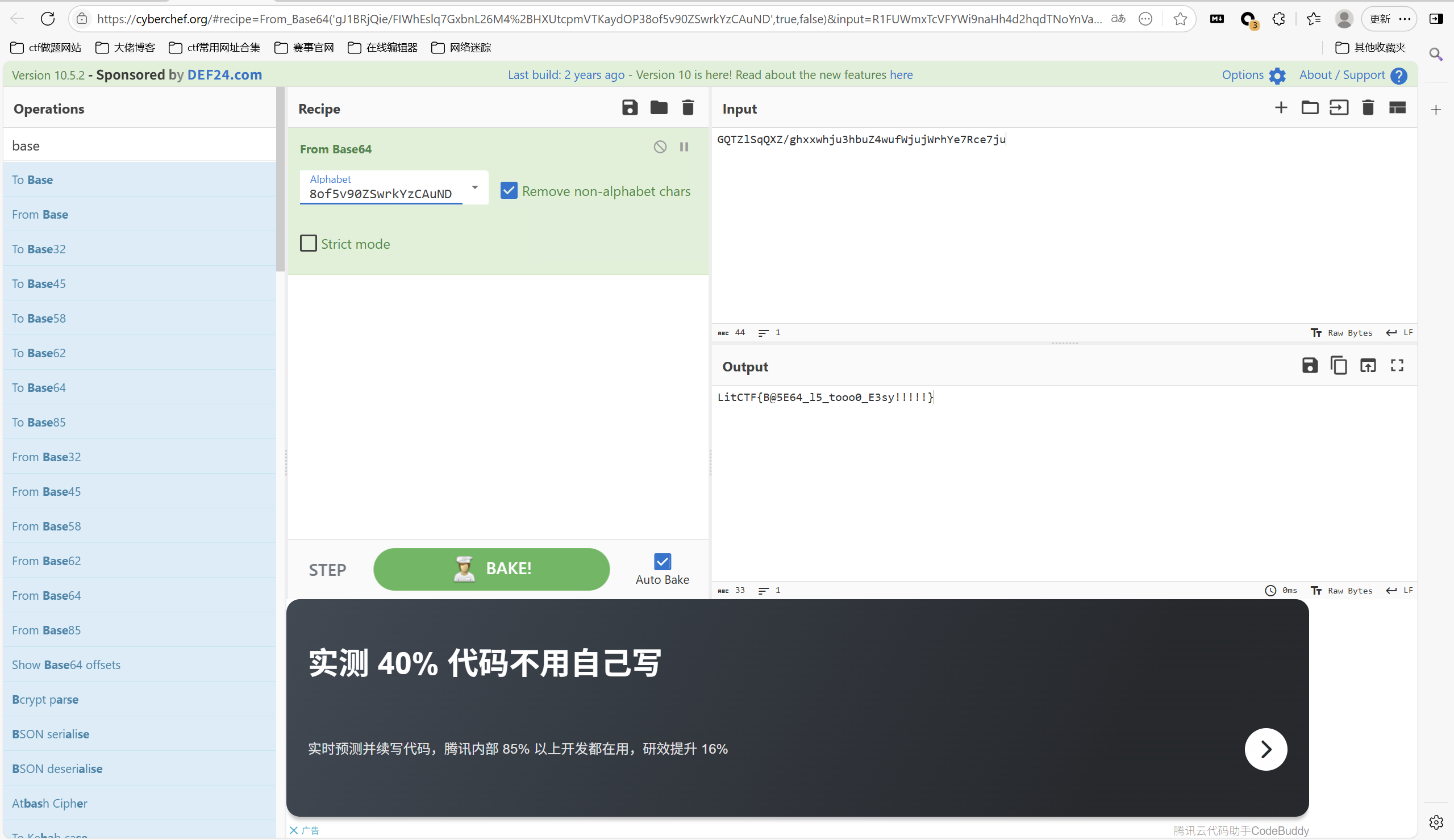
最后flag为
1 | LitCTF{B@5E64_l5_tooo0_E3sy!!!!!} |
[LitCTF 2023]snake
下载附件
pyc文件,直接uncompyle6反编译
提示文件头错误
010查看
pyc文件的magic number是根据编译的python版本而变化的
题目是37,应该是py3.7编译
对照magic number表
1 | enum PycMagic { |
010修改
保存重新进行反编译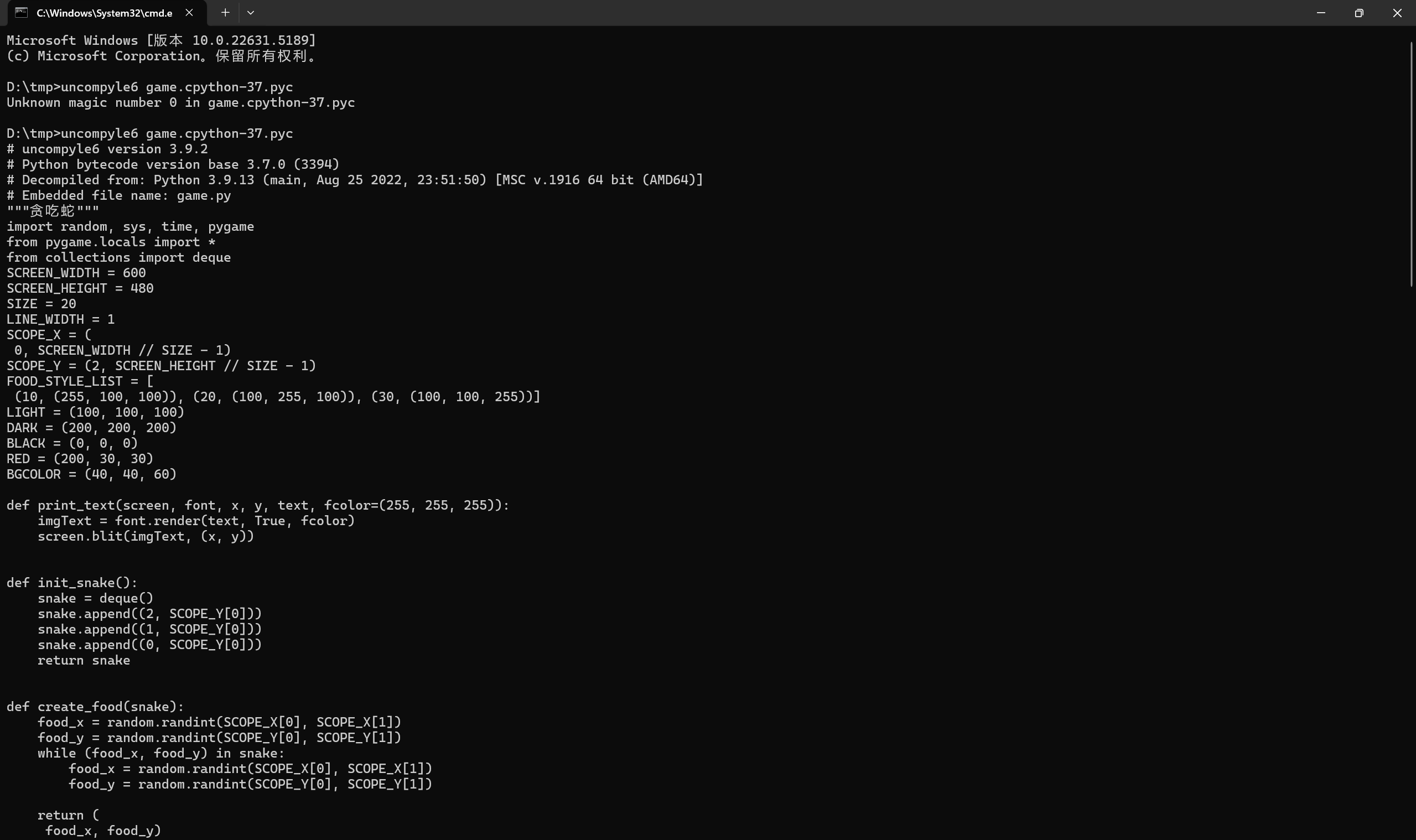
完整代码
1 | """贪吃蛇""" |
关键代码
1 | if score > 1000: |
exp:
1 | flag = [ |
运行得到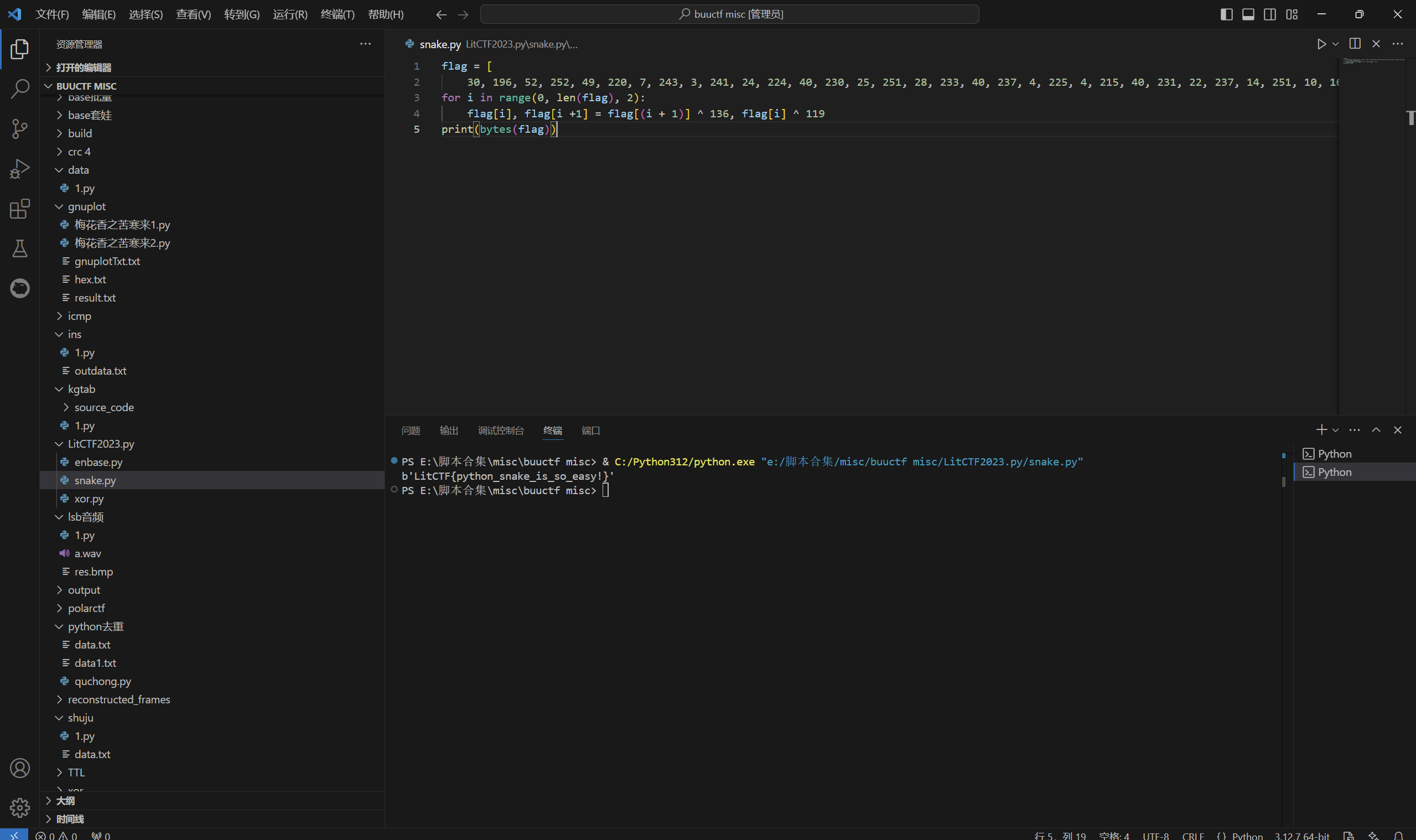
最后flag为
1 | LitCTF{python_snake_is_so_easy!} |
[LitCTF 2023]程序和人有一个能跑就行了
下载附件
运行exe文件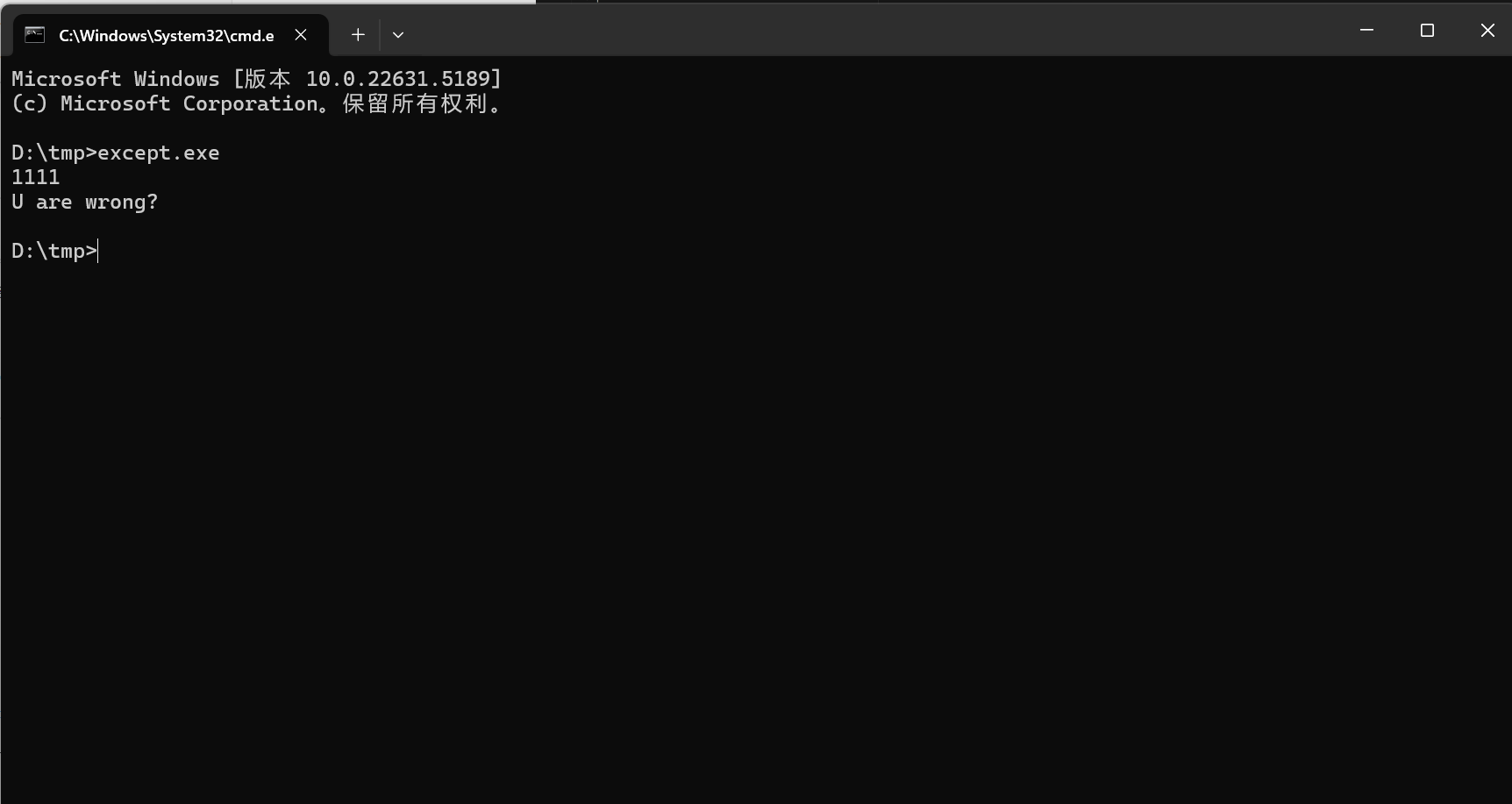
应该也是判断输入正确的flag
查壳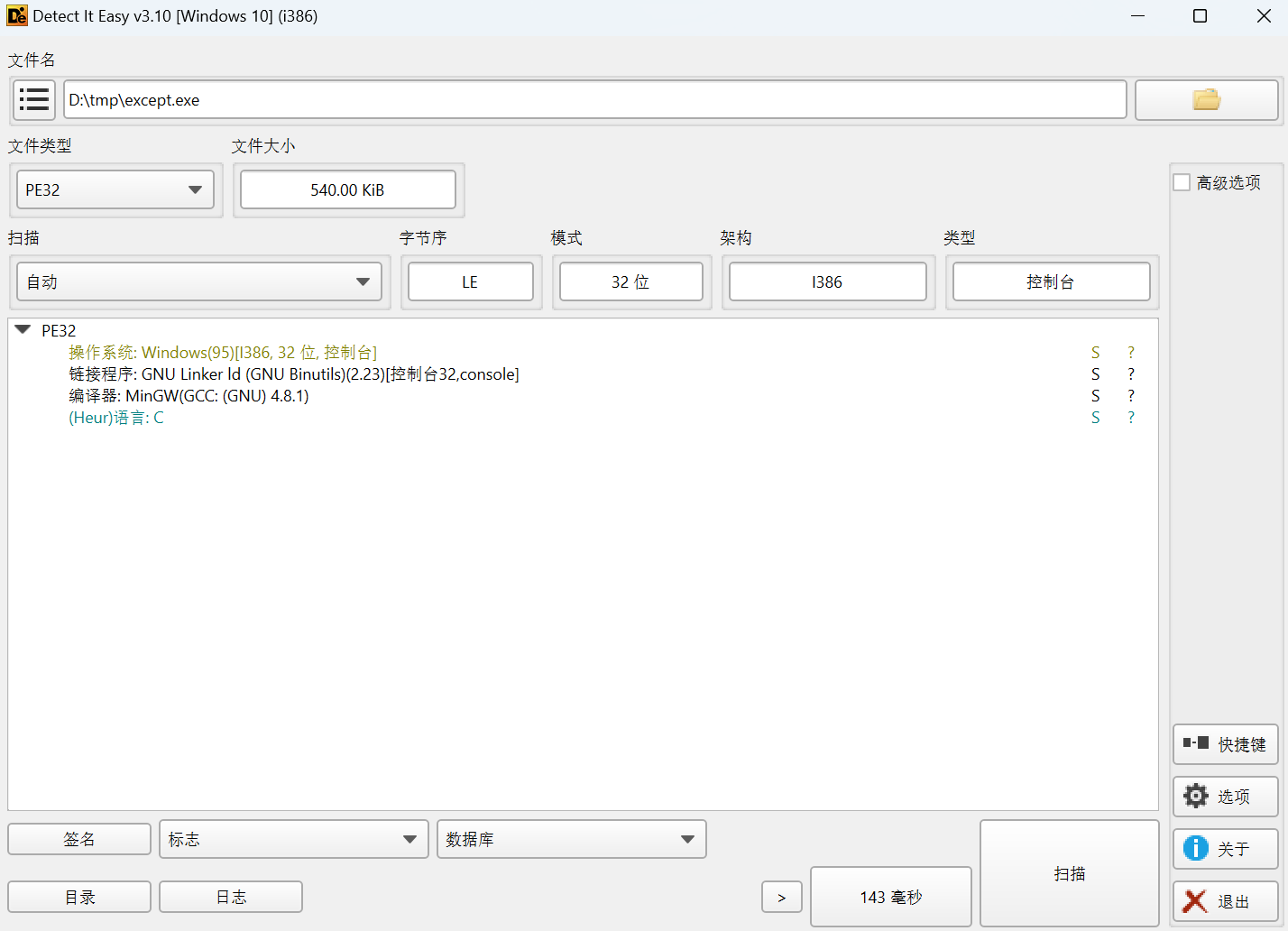
32位
IDA载入查看main函数的伪代码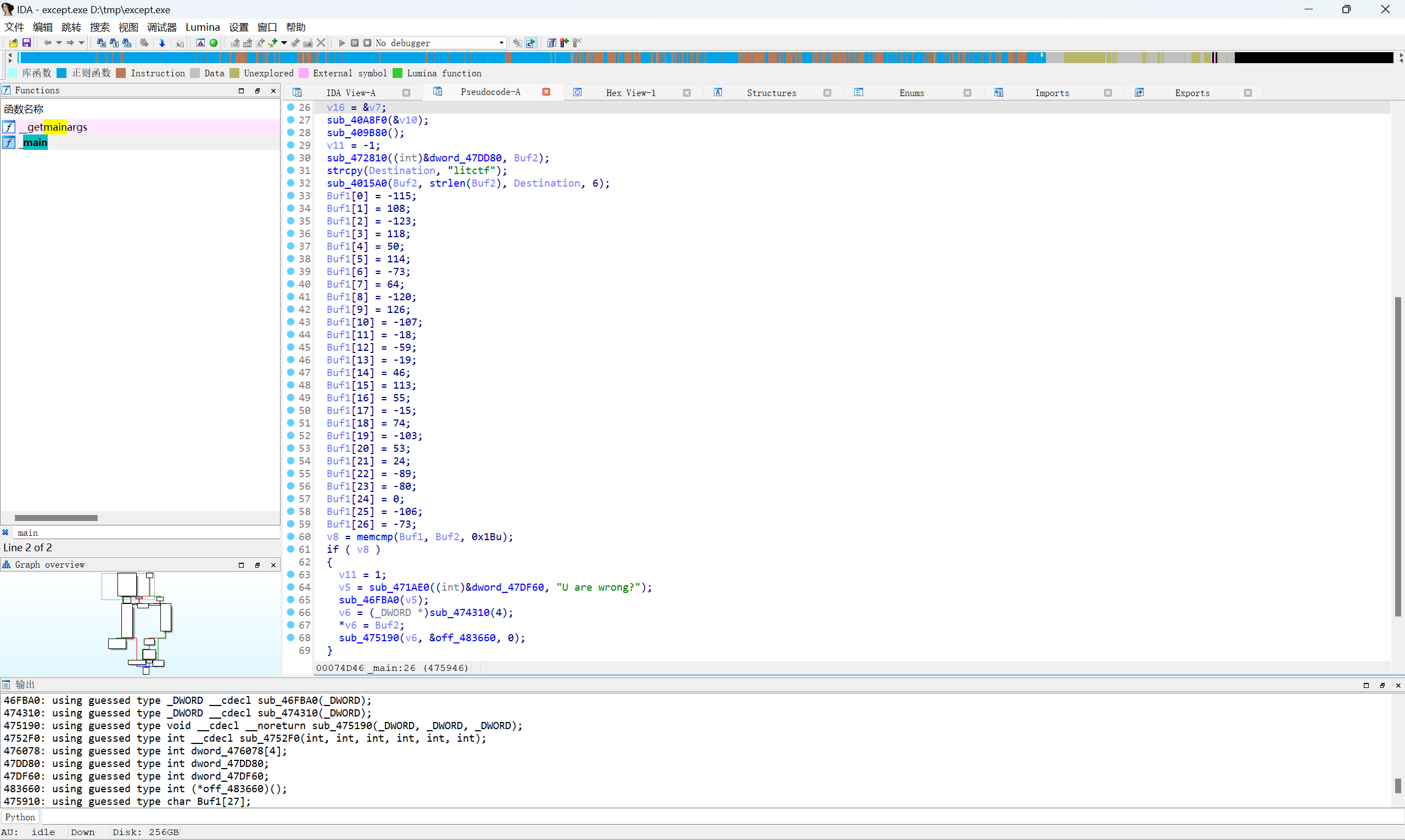
看到litctf
跟进sub_4015A0函数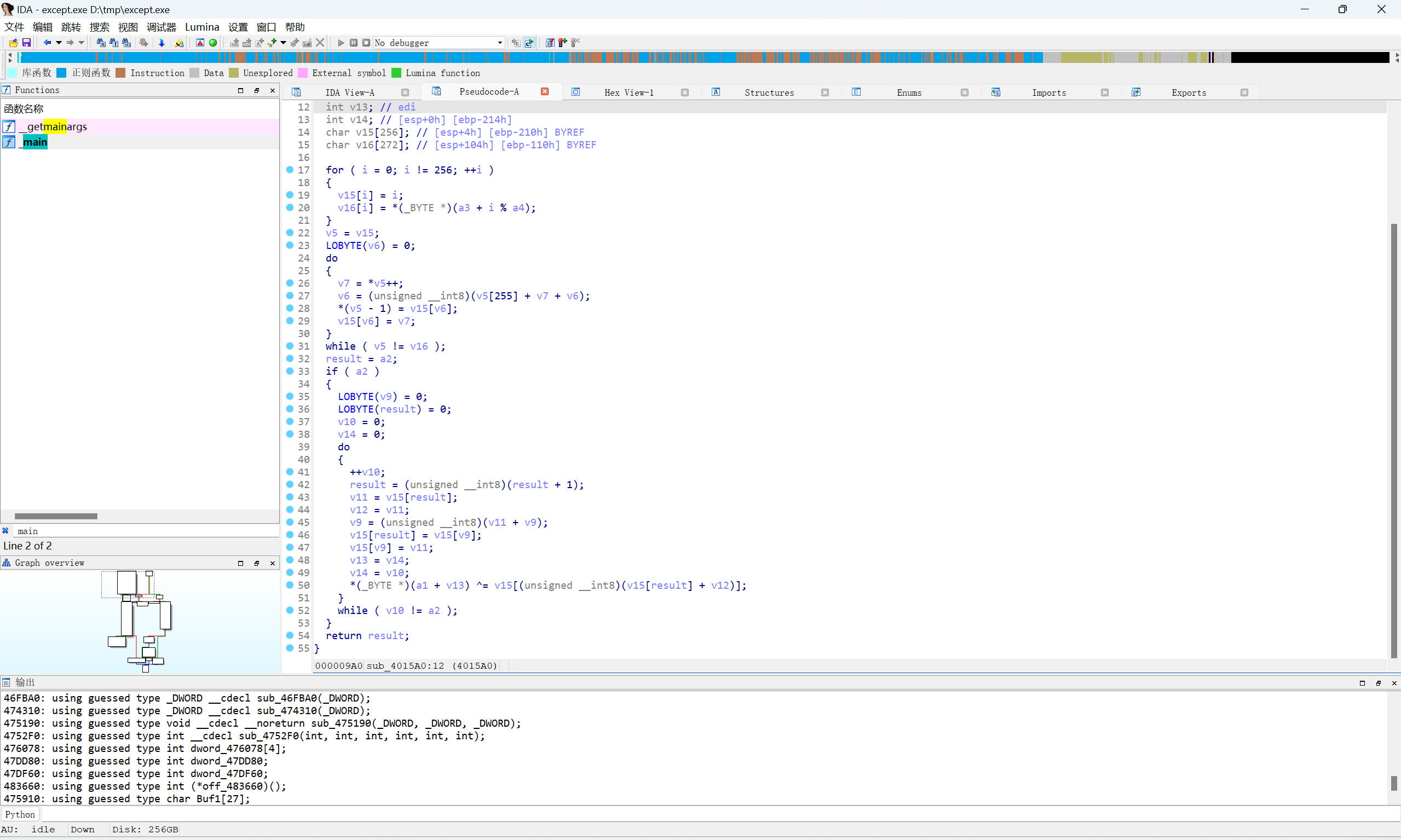
这是rc4加密的特征
1 | 1.有很多取模操作 |
密文整理统一十六进制数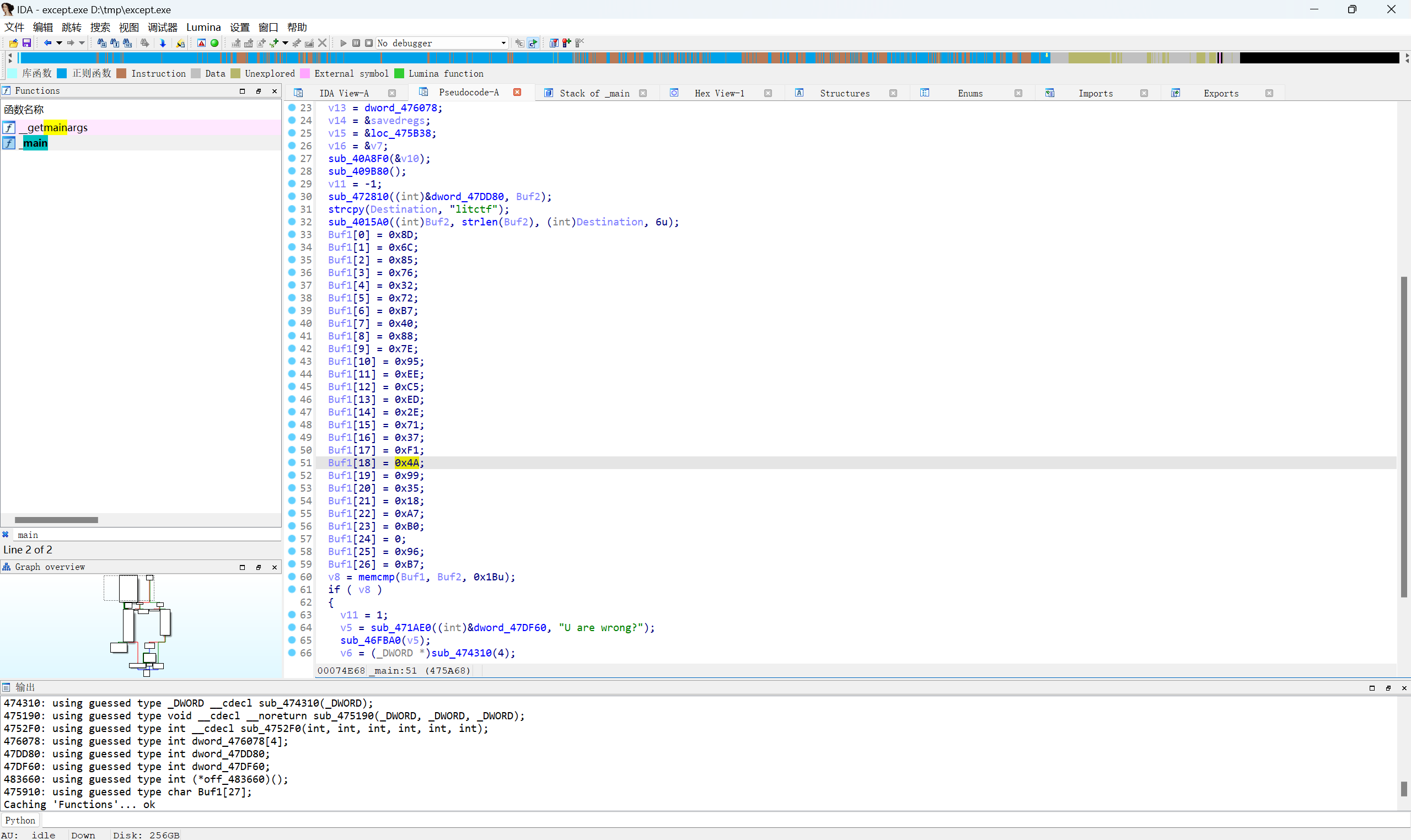
得到
1 | 0x8D, 0x6C, 0x85, 0x76, 0x32, 0x72, 0xB7, 0x40, 0x88, 0x7E, 0x95, 0xEE, 0xC5, 0xED, 0x2E, 0x71, 0x37, 0xF1, 0x4A,0x99, 0x35, 0x18, 0xA7, 0xB0, 0, 0x96, 0xB7 |
找一个rc4解密的脚本,密钥是litctf
exp:
1 | def rc4_init(s_box, key, key_len): # rc4初始化函数,产生s_box |
运行得到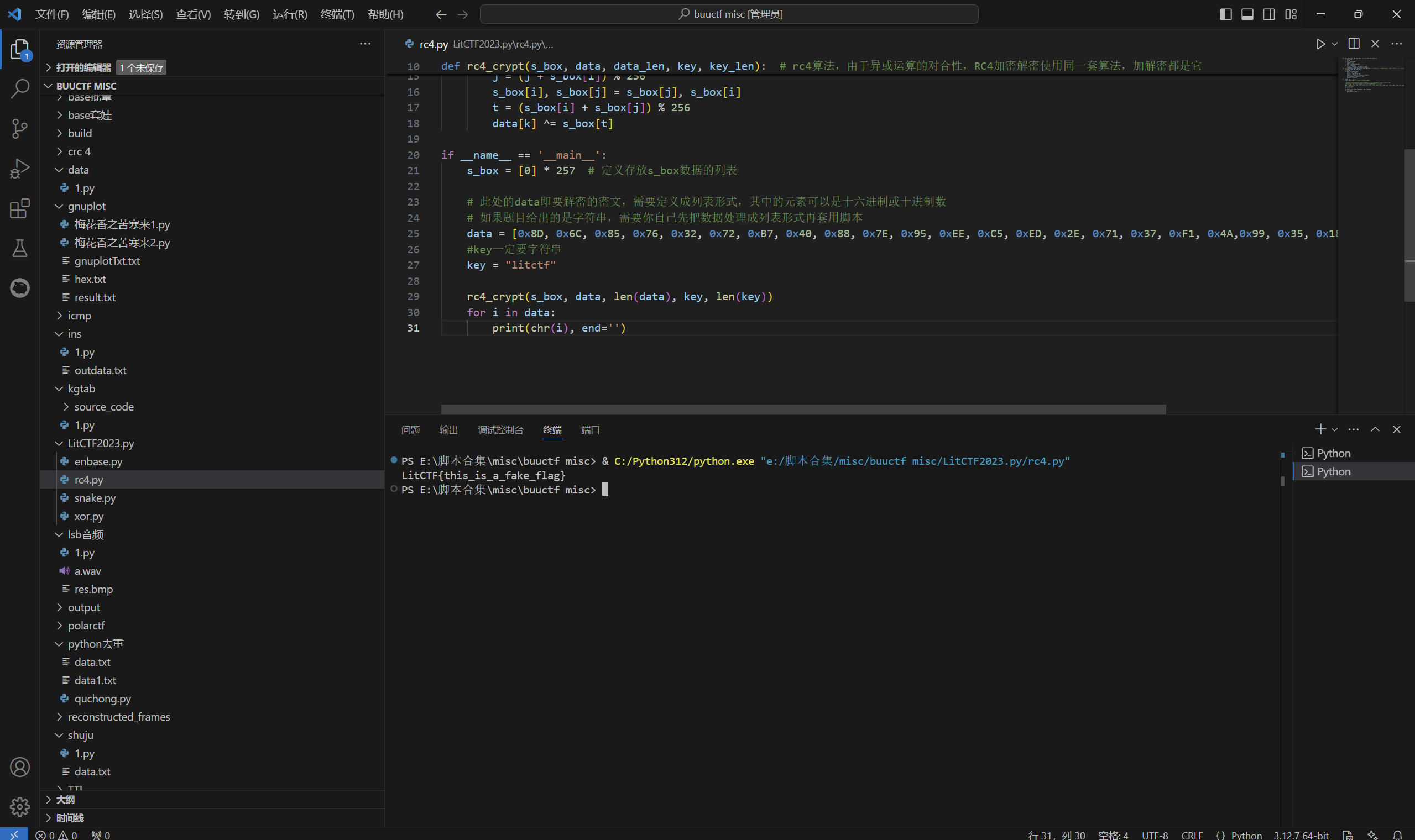
得到的是假flag
查看main函数汇编界面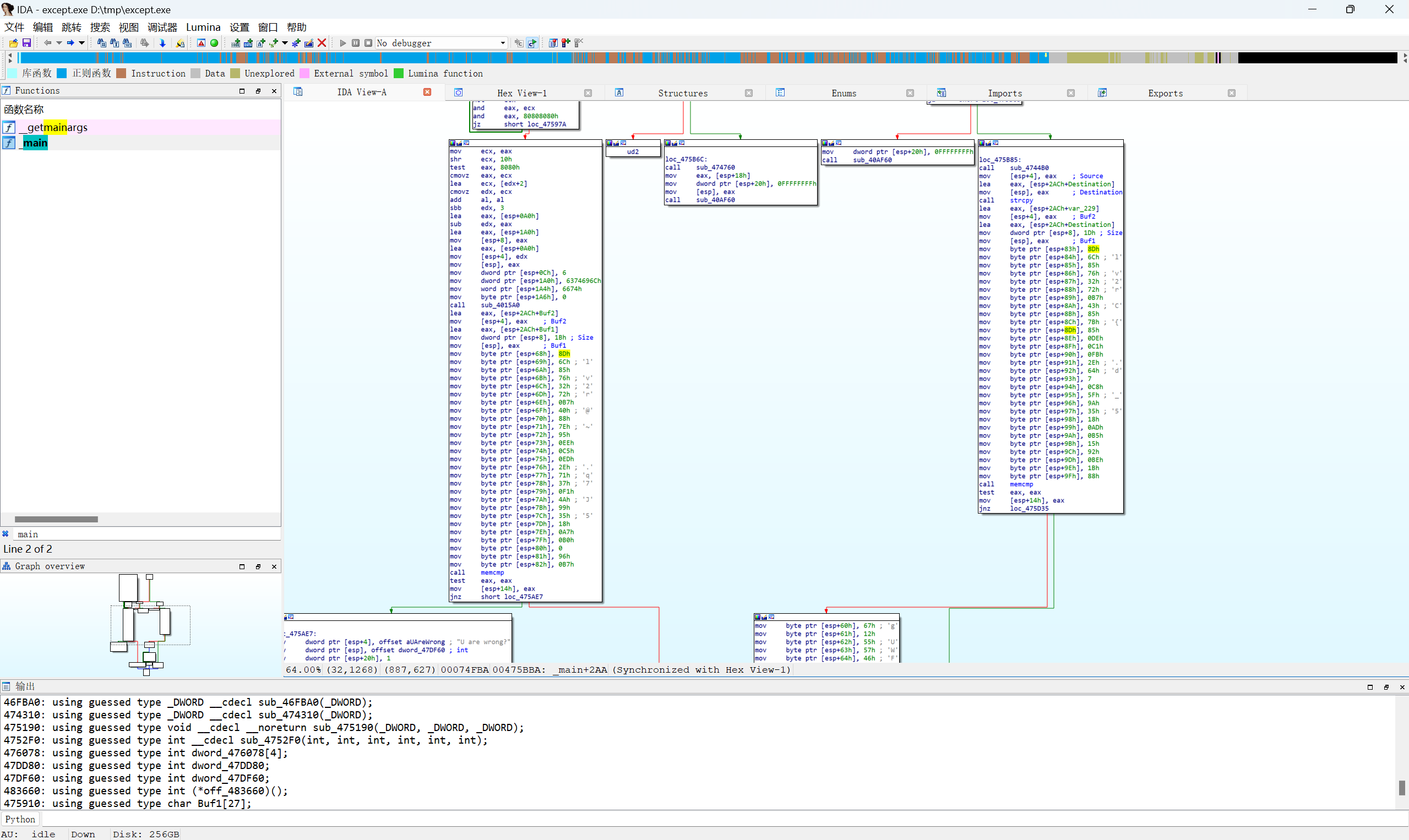
发现有两段密文,第一段就是我们左边解过的
查看右边的密文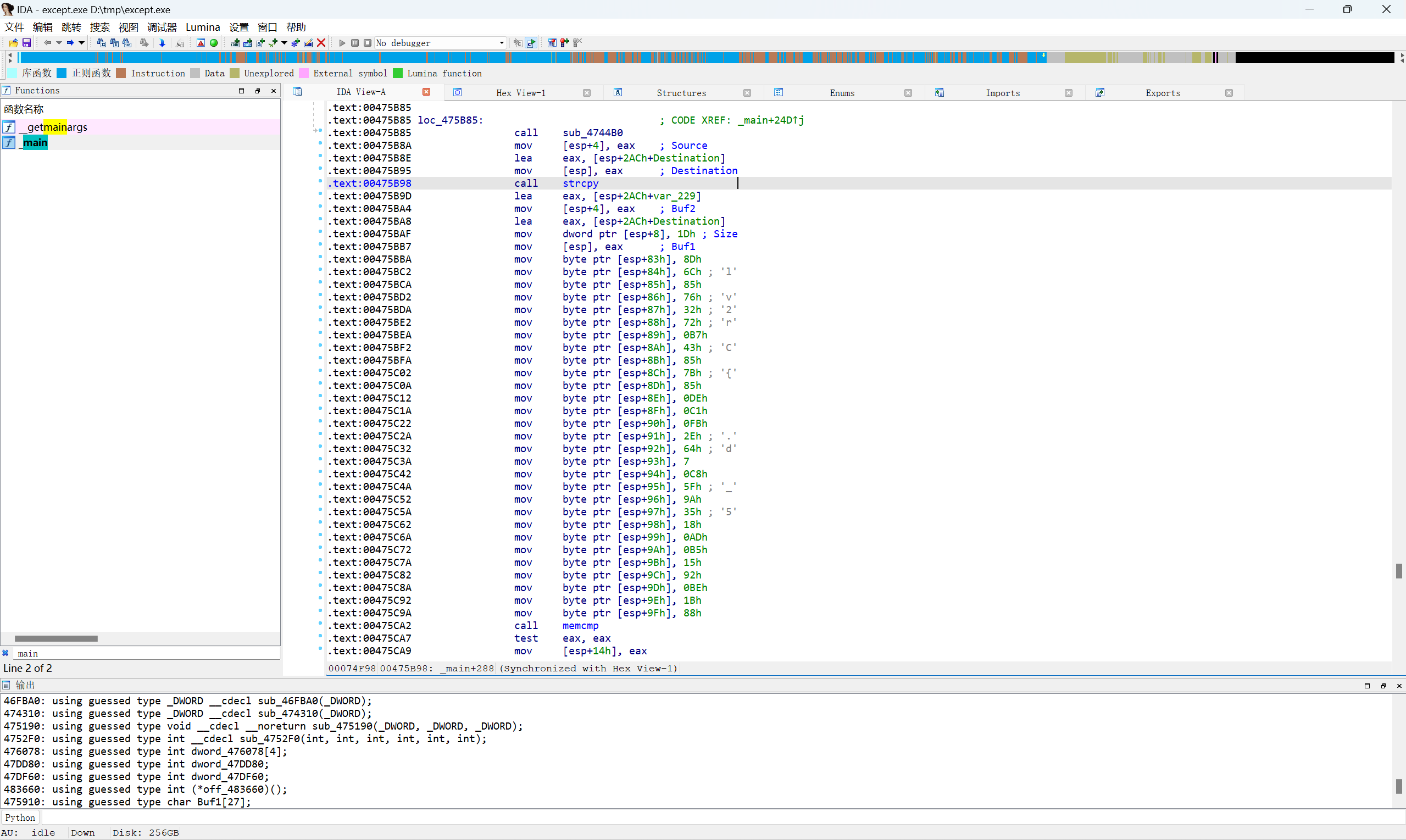
提取
1 | 0x8D, 0x6C, 0x85, 0x76, 0x32, 0x72, 0xB7, 0x43, 0x85, 0x7B, 0x85, 0xDE, 0xC1, 0xFB, 0x2E, 0x64, 0x07, 0xC8, 0x5F, 0x9A, 0x35, 0x18, 0xAD, 0xB5, 0x15, 0x92, 0xBE, 0x1B, 0x88 |
重新运行脚本得到flag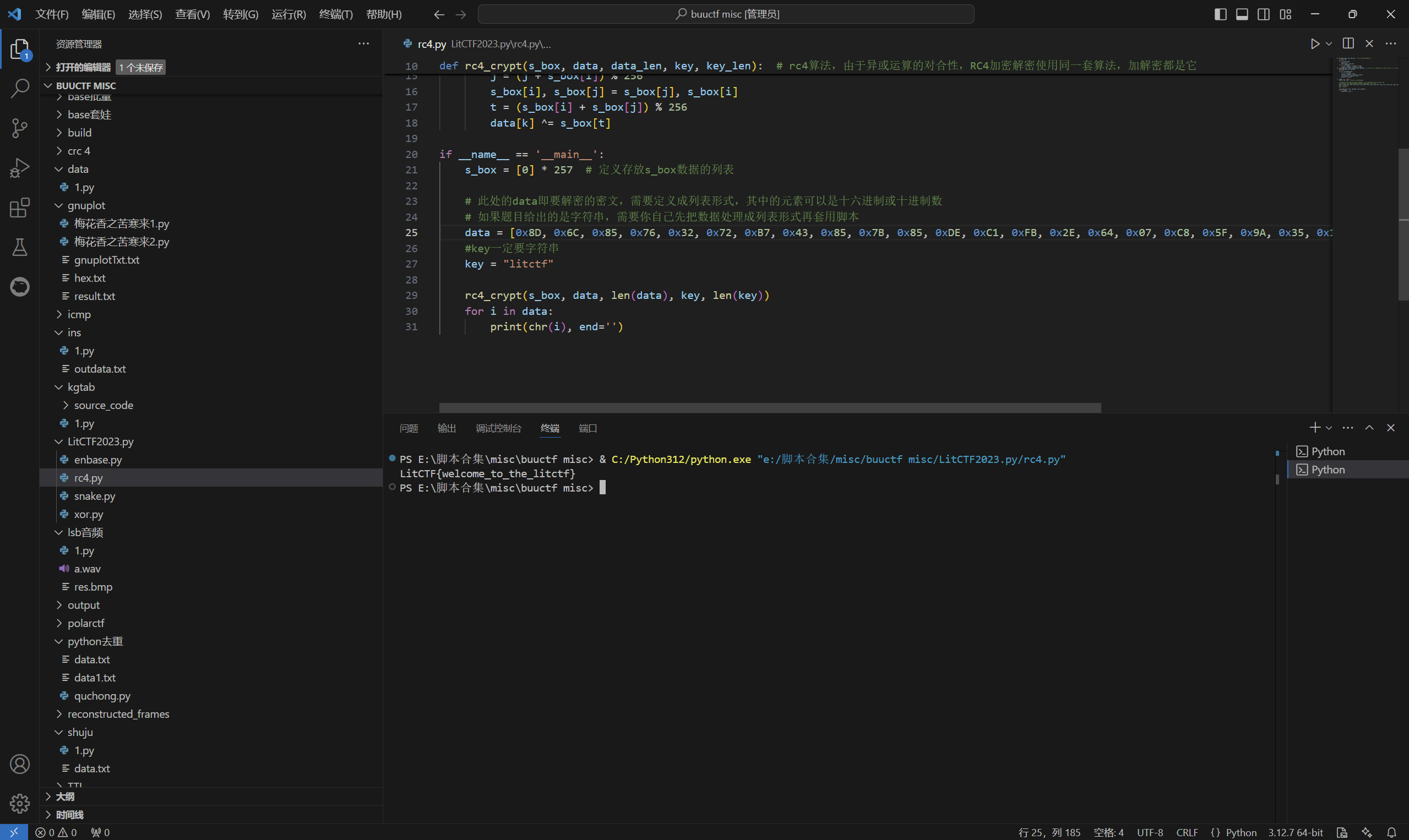
最后flag为
1 | LitCTF{welcome_to_the_litctf} |
[LitCTF 2023]debase64
题目描述:
1 | Do you know debase64? |
下载附件
运行文件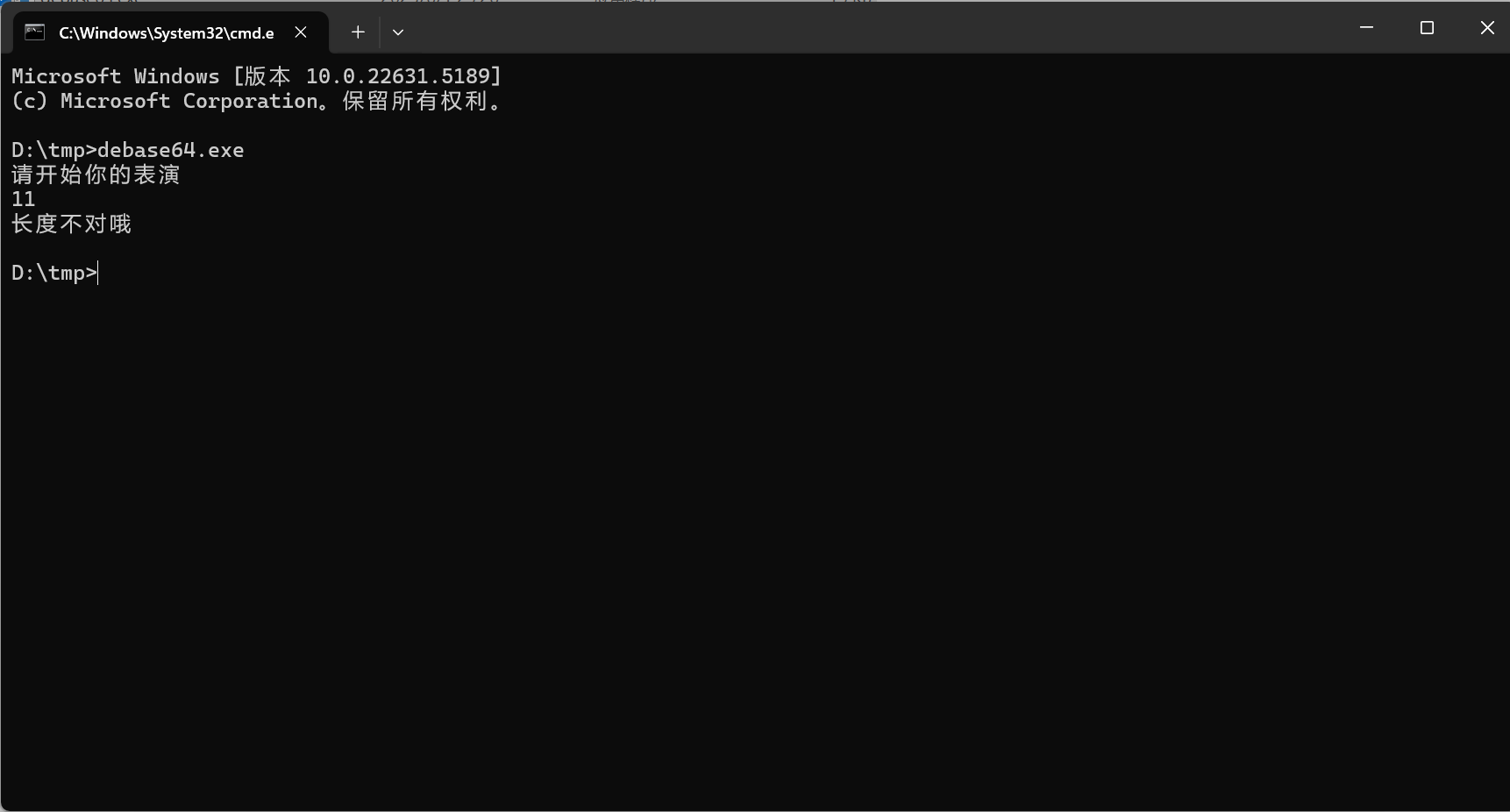
应该是限制输入长度
查壳
32位
IDA载入文件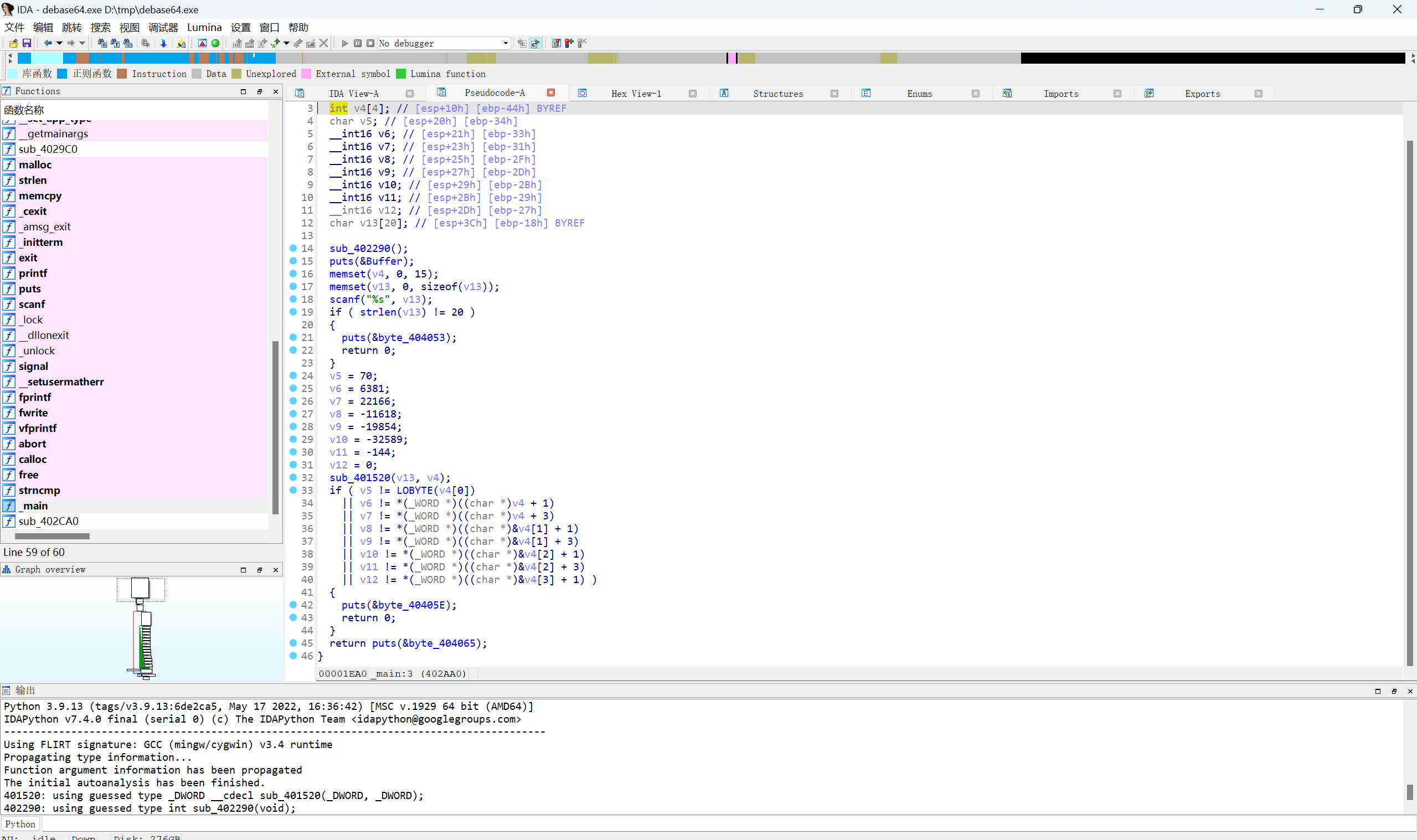
首先看到是输入长度是20,然后通过函数sub_401520对输入进行处理
跟进sub_401520函数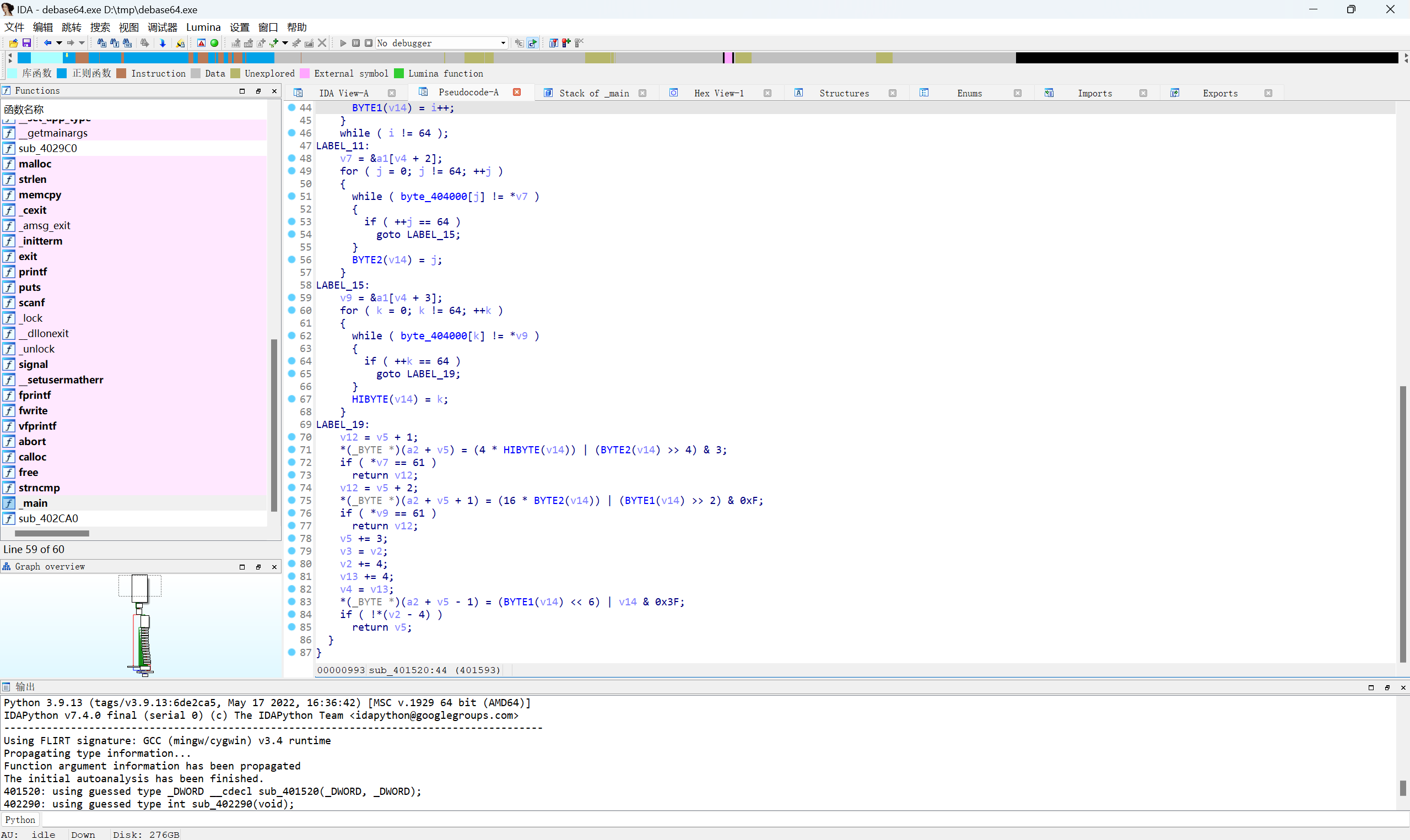
关键代码
1 | LABEL_19: |
base64解密,首先转base编码,然后四位一组逆序输出
找到密文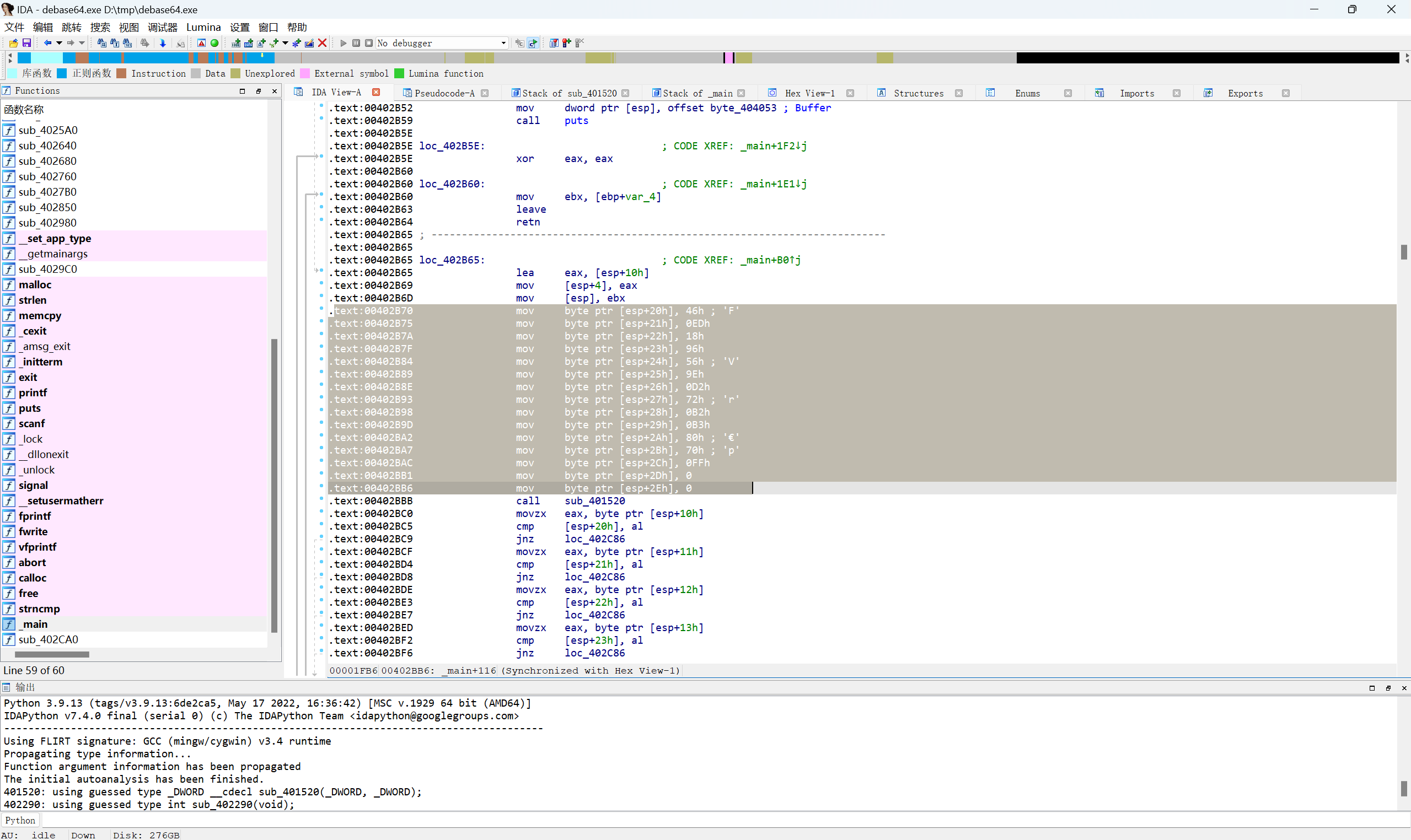
提取出密文
1 | 0x46, 0xED, 0x18, 0x96, 0x56, 0x9E, 0xD2, 0x72, 0xB2, 0xB3, 0x80, 0x70, 0xFF |
exp:
1 | import base64 |
运行得到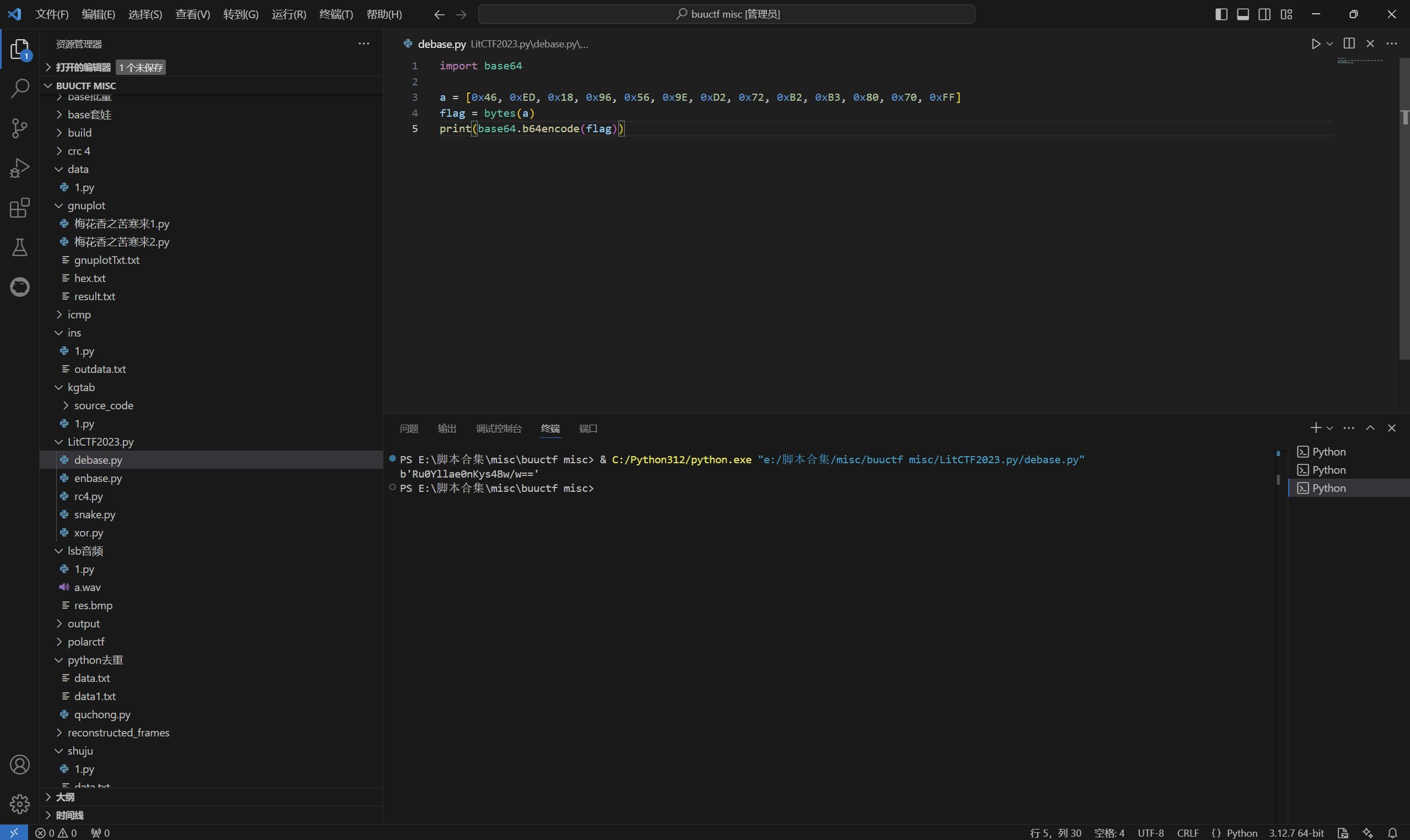
根据提示:
1 | flag最后有3个= |
整理得到
1 | Ru0Yllae0nKys4Bw/w== |
里面的/w是错的,需要爆破一下
exp:
1 | import hashlib |
运行得到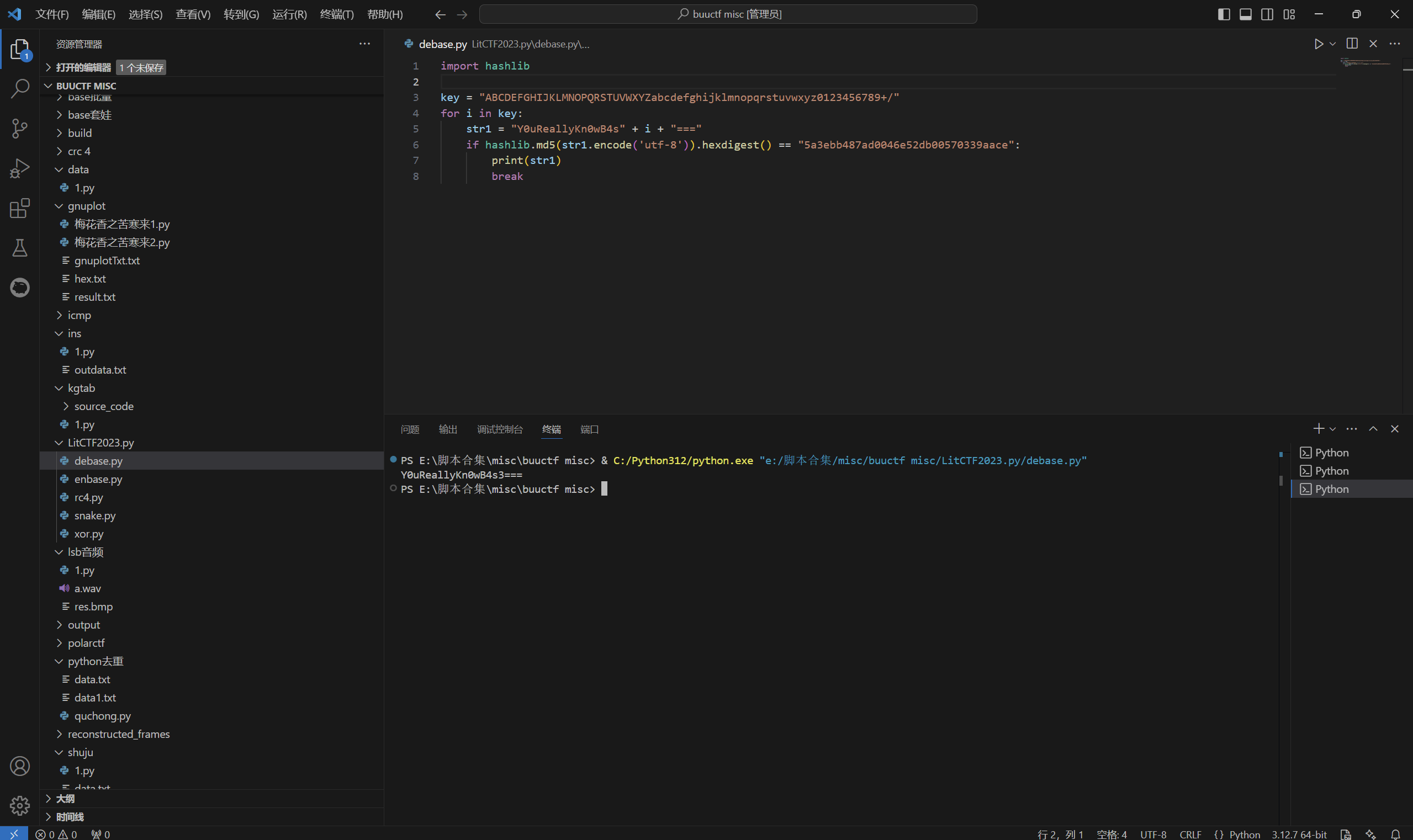
最后flag为
1 | LitCTF{Y0uReallyKn0wB4s3===} |
[LitCTF 2023]For Aiur
下载附件
是个游戏exe,直接pyinstxtractor解包
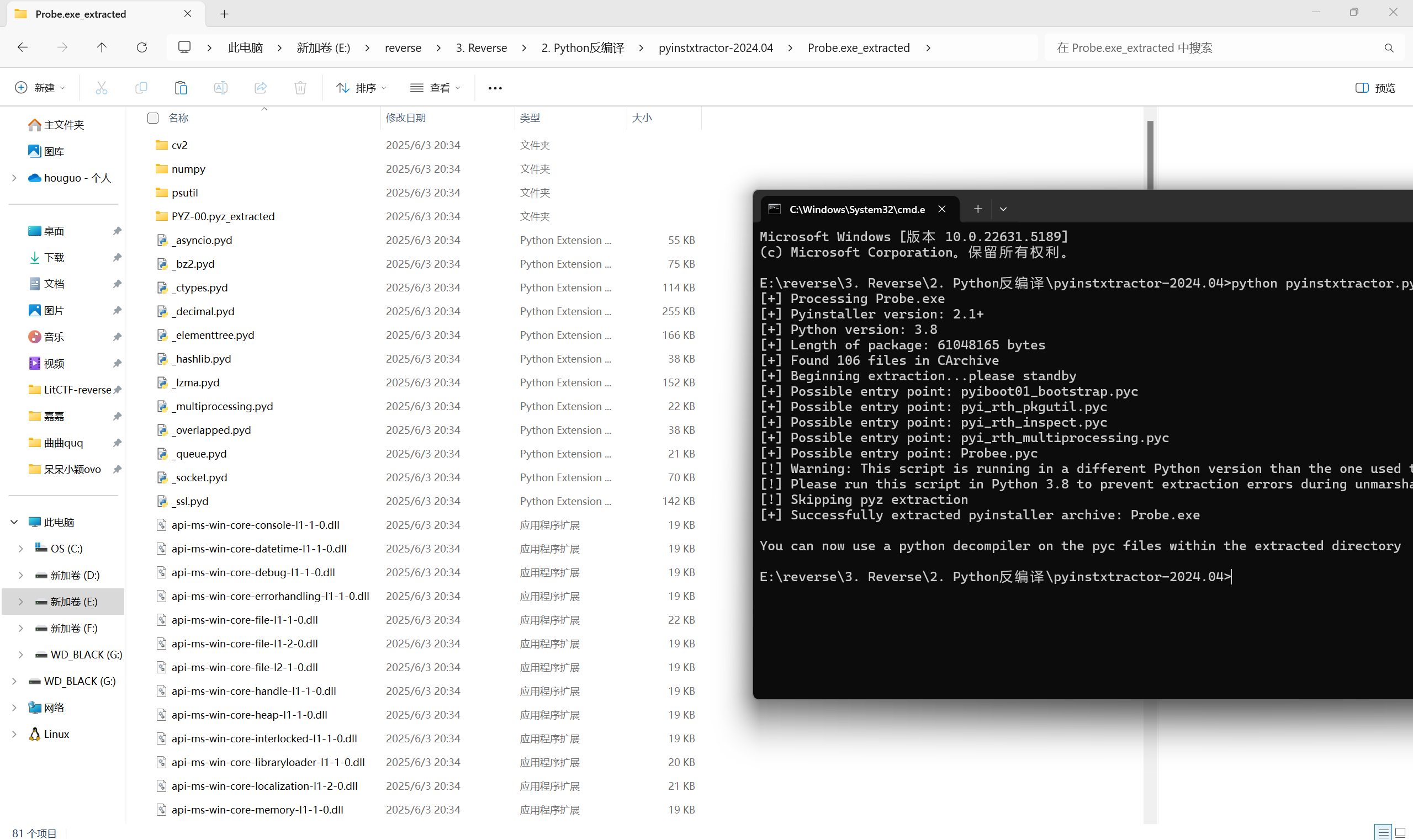
反编译
代码
1 | #!/usr/bin/env python |
发现check函数
回去找到ch.pyc进行反编译
1 | # uncompyle6 version 3.9.0 |
exp:
1 | enc = [ |
运行得到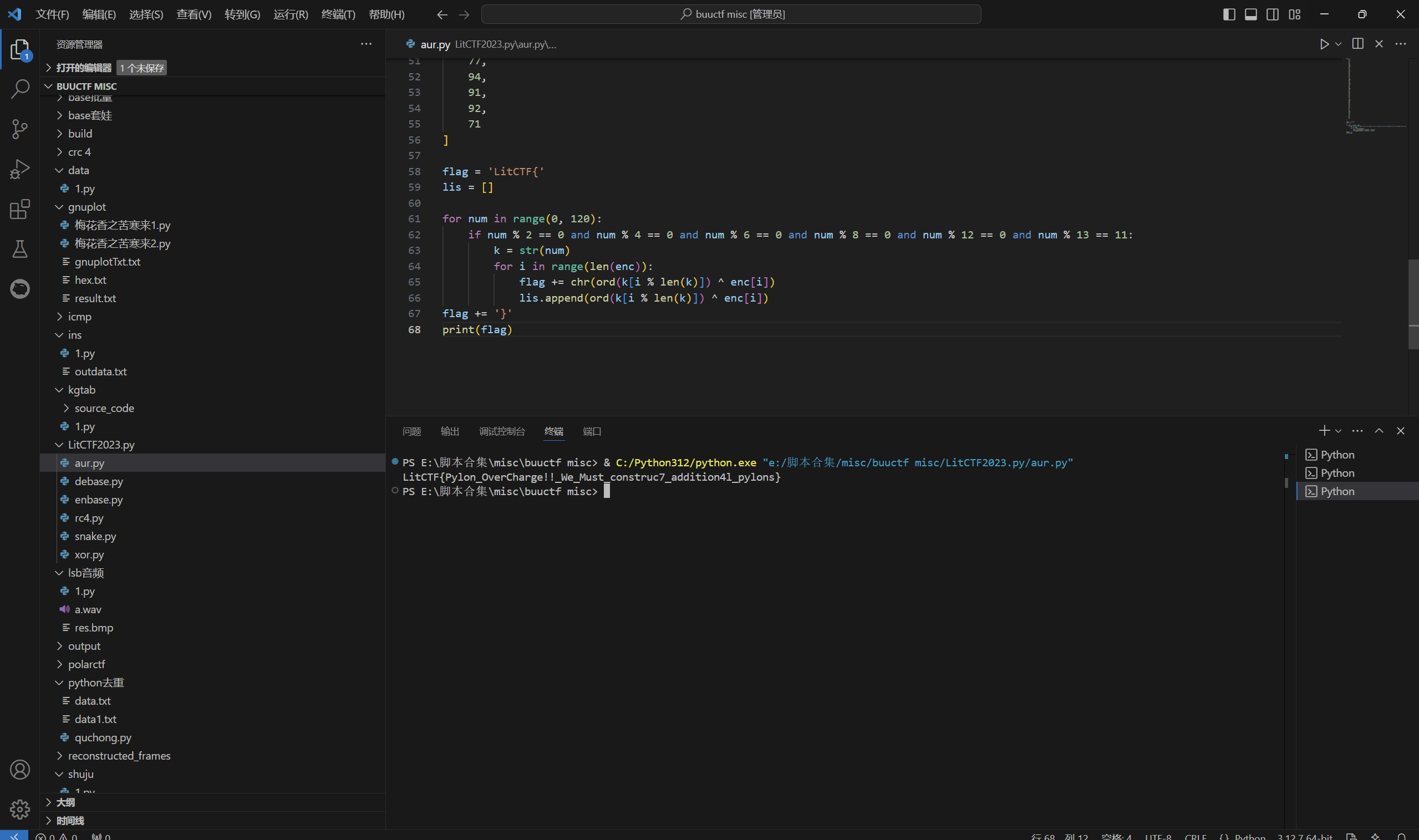
最后flag为
1 | LitCTF{Pylon_OverCharge!!_We_Must_construc7_addition4l_pylons} |



